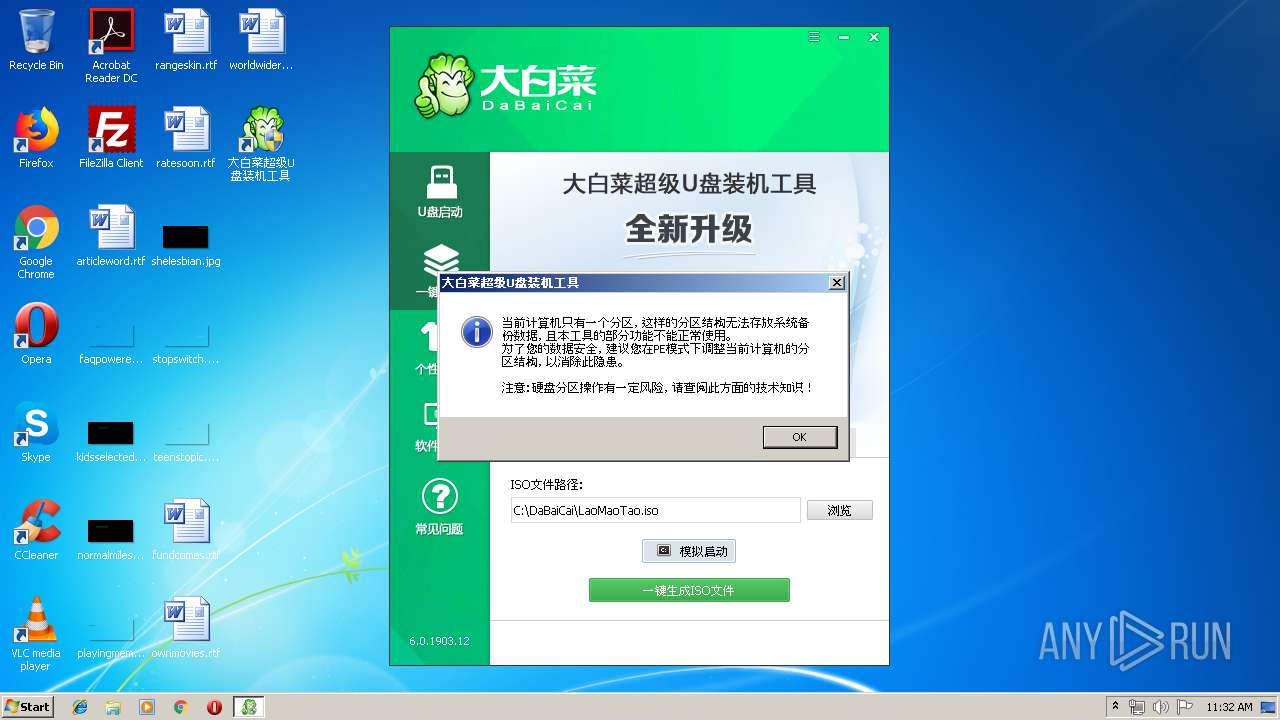
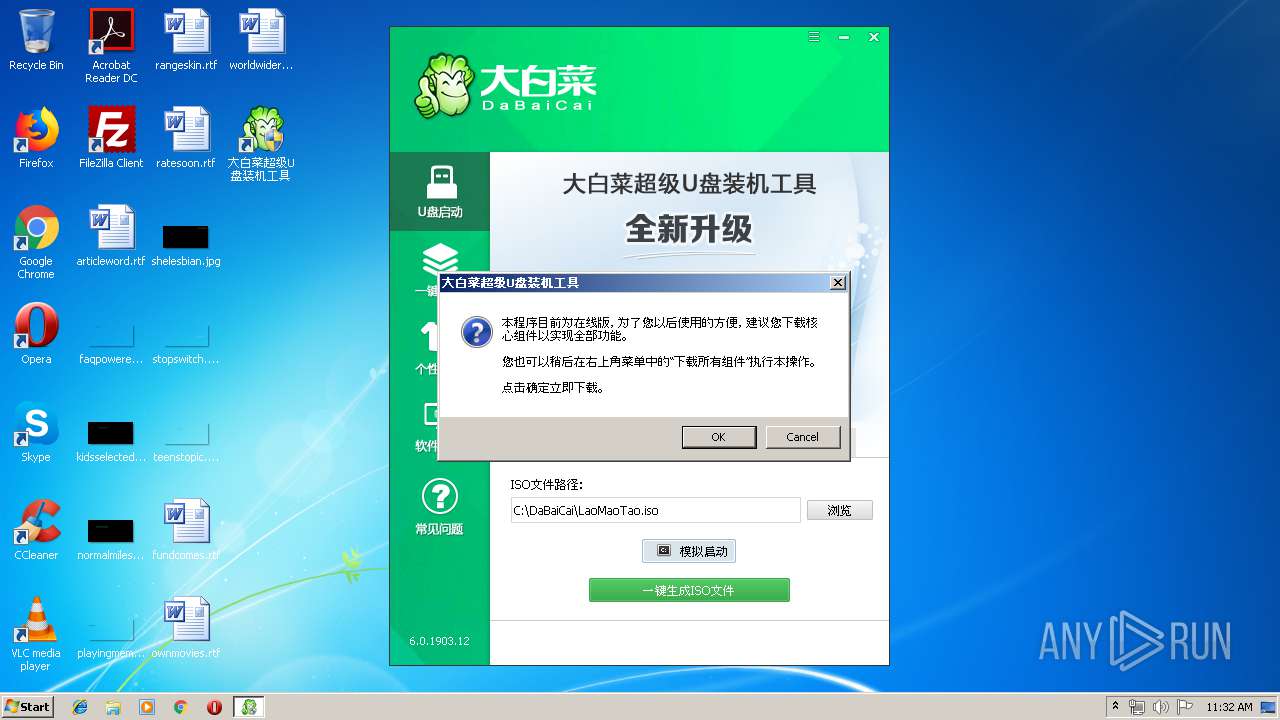
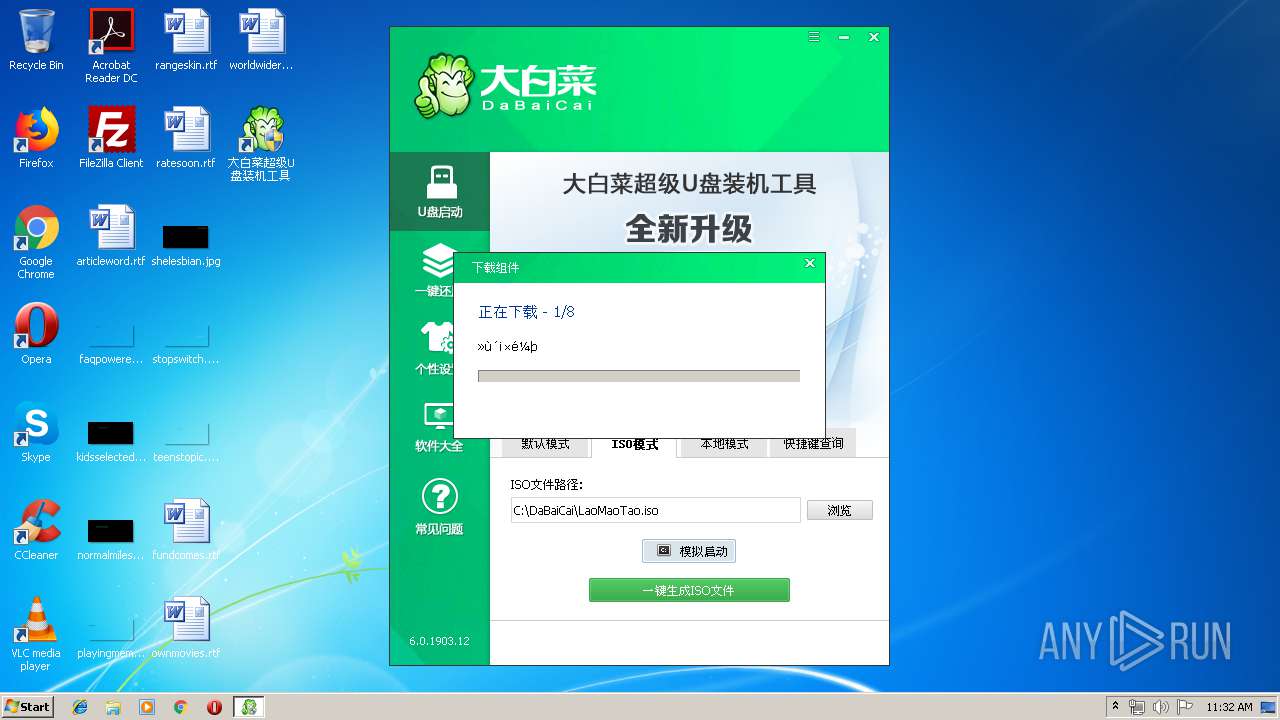
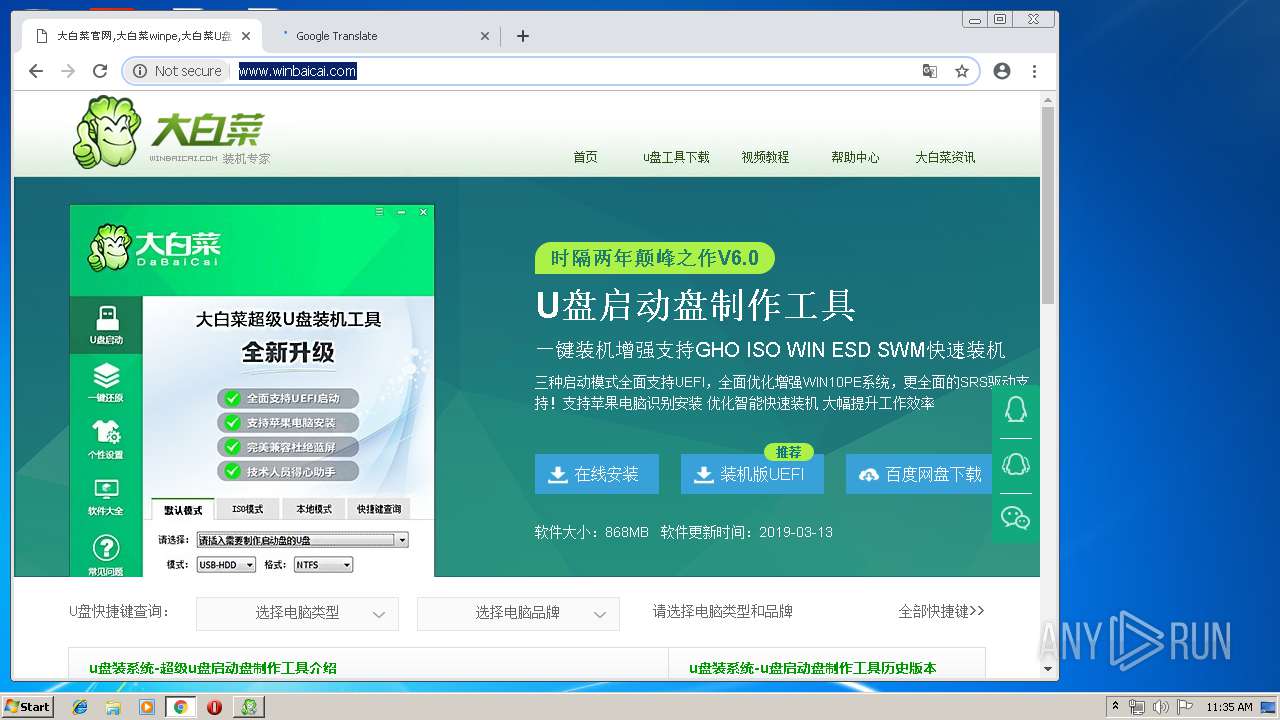
| File name: | daibaichi.exe |
| Full analysis: | https://app.any.run/tasks/c96e23ee-badd-4238-9716-57b9fe329c30 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | April 22, 2019, 10:31:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 96FB732713B28383C1F377D01E6FB84E |
| SHA1: | 1C0DA1BFD39C6D3A3AB9C4B8FA65BCC4DB235860 |
| SHA256: | 02332A3B01DF492D89759C9246058D8F118CA640F6FD32D674CB6B231423796B |
| SSDEEP: | 98304:HfQzWCaDi9Qjyd41W2HESikb7RjVejrJ:YKCh9Qjyd4Y2/HVirJ |
MALICIOUS
Loads dropped or rewritten executable
- dismhost.exe (PID: 2500)
- DaBaiCai.exe (PID: 2384)
- Dism.exe (PID: 3640)
- MiniThunderPlatform.exe (PID: 2880)
- Dism.exe (PID: 1448)
Application was dropped or rewritten from another process
- 7483.tmp (PID: 3176)
- Update.exe (PID: 3564)
- bcdedit.exe (PID: 2712)
- bcdedit.exe (PID: 2884)
- Update.exe (PID: 1708)
- dismhost.exe (PID: 2500)
- ThunderFW.exe (PID: 3680)
- MiniThunderPlatform.exe (PID: 2880)
- MiniTPFw.exe (PID: 2676)
- Update.exe (PID: 2984)
SUSPICIOUS
Executable content was dropped or overwritten
- daibaichi.exe (PID: 3612)
- DaBaiCai.exe (PID: 2384)
- Dism.exe (PID: 1448)
- MiniThunderPlatform.exe (PID: 2880)
Starts application with an unusual extension
- daibaichi.exe (PID: 3612)
Creates files in the program directory
- daibaichi.exe (PID: 3612)
- MiniThunderPlatform.exe (PID: 2880)
Starts itself from another location
- daibaichi.exe (PID: 3612)
Low-level read access rights to disk partition
- bcdedit.exe (PID: 2712)
- MiniThunderPlatform.exe (PID: 2880)
- DaBaiCai.exe (PID: 2384)
- bcdedit.exe (PID: 2884)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3860)
Creates files in the Windows directory
- Dism.exe (PID: 3640)
INFO
Dropped object may contain Bitcoin addresses
- DaBaiCai.exe (PID: 2384)
Reads settings of System Certificates
- chrome.exe (PID: 3860)
Application launched itself
- chrome.exe (PID: 3860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (61.1) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.8) |
| .exe | | | Win32 Executable (generic) (10.1) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:03:12 08:24:31+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 3518464 |
| InitializedDataSize: | 36864 |
| UninitializedDataSize: | 3637248 |
| EntryPoint: | 0x6d2620 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.1903.12 |
| ProductVersionNumber: | 6.0.1903.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Windows, Chinese (Simplified) |
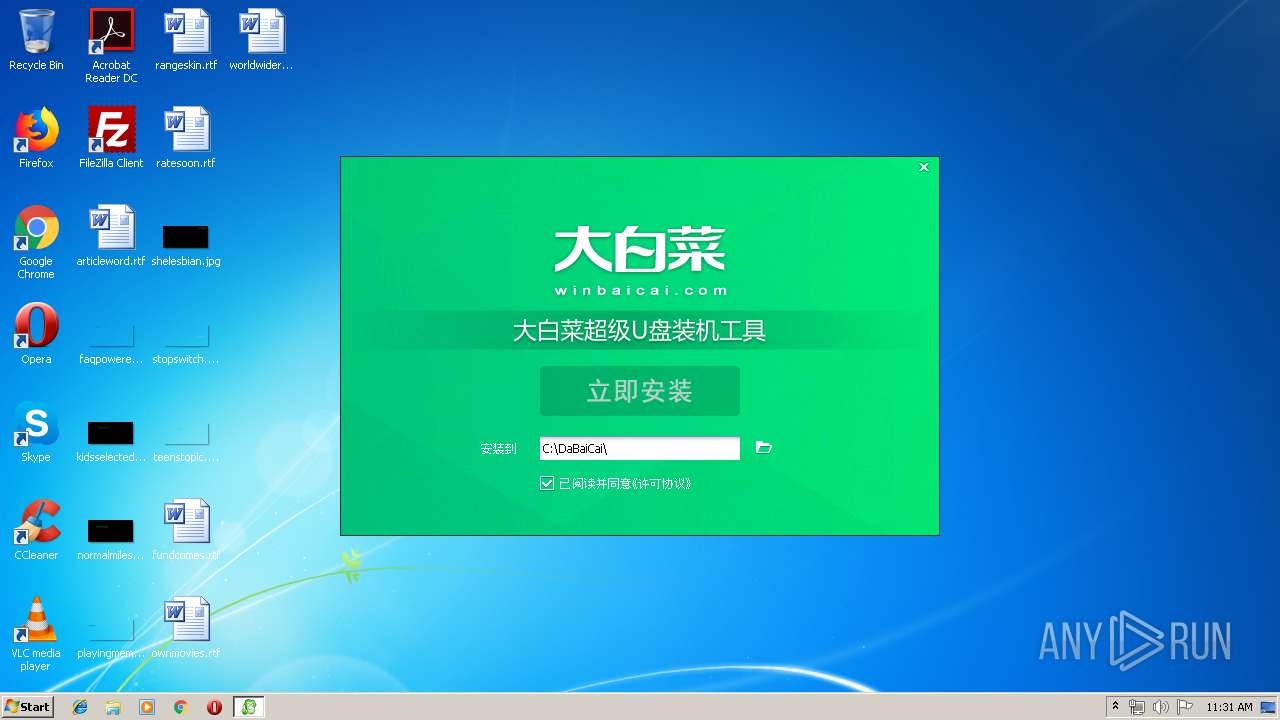
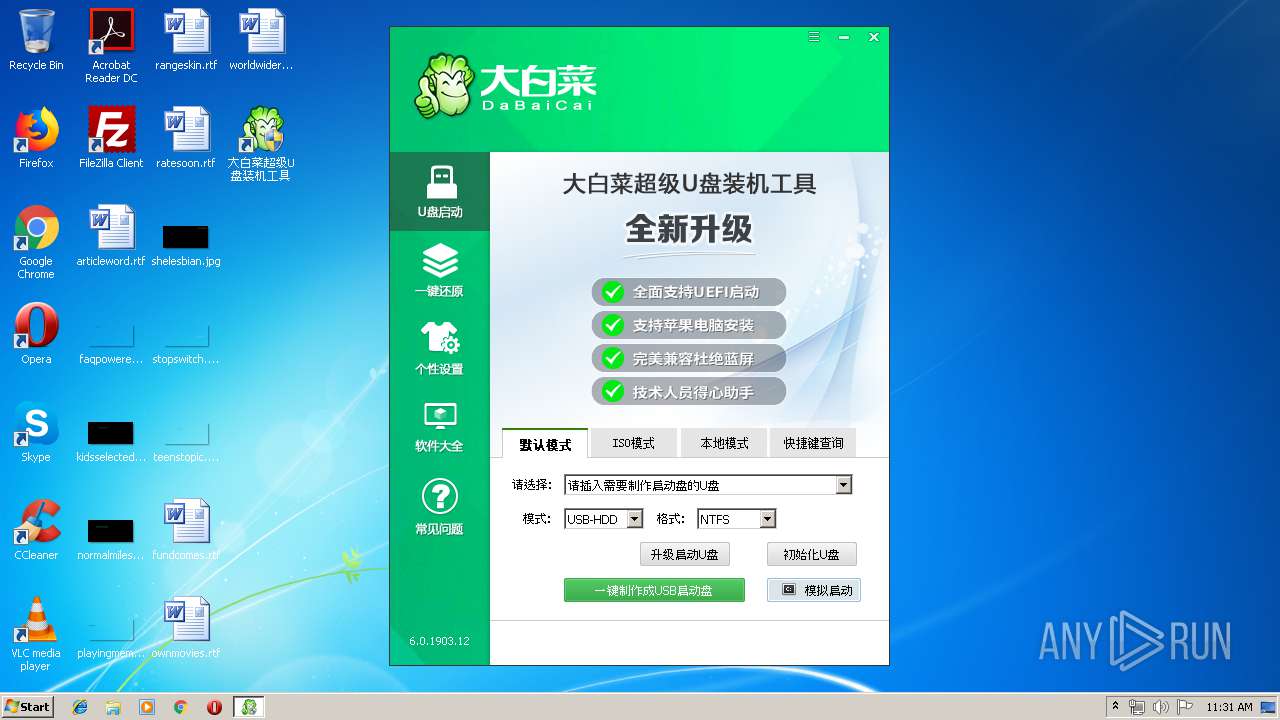
| CompanyName: | www.dabaicai.com |
| FileDescription: | 大白菜超级U盘装机工具 |
| FileVersion: | 6.0.1903.12 |
| LegalCopyright: | Copyright © 2010-2019 DaBaiCai.Com |
| LegalTrademarks: | www.dabaicai.com |
| ProductName: | 大白菜超级U盘装机工具 |
| ProductVersion: | 6.0.1903 |
| Comments: | 大白菜超级U盘装机工具 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 12-Mar-2019 07:24:31 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 12-Mar-2019 07:24:31 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00378000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00379000 | 0x0035B000 | 0x0035A400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99994 |
.rsrc | 0x006D4000 | 0x00009000 | 0x00008E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.41946 |
Imports
KERNEL32.DLL |
URLMON.DLL |
advapi32.dll |
comctl32.dll |
comdlg32.dll |
gdi32.dll |
gdiplus.dll |
msvcrt.dll |
ole32.dll |
oleacc.dll |
Total processes
89
Monitored processes
48
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,4281256617785832710,389174053161497089,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4960002280361980421 --mojo-platform-channel-handle=3816 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,4281256617785832710,389174053161497089,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15505196310789839665 --mojo-platform-channel-handle=3800 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 388 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,4281256617785832710,389174053161497089,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=13045995260656241316 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13045995260656241316 --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4208 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,4281256617785832710,389174053161497089,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=7962761279812953542 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7962761279812953542 --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4900 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=73.0.3683.75 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6e920f18,0x6e920f28,0x6e920f34 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,4281256617785832710,389174053161497089,131072 --enable-features=PasswordImport --service-pipe-token=9395181847974582637 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9395181847974582637 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 940 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,4281256617785832710,389174053161497089,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=16647409464037366905 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16647409464037366905 --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1884 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,4281256617785832710,389174053161497089,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=16289076510909838232 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16289076510909838232 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4272 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1184 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=960,4281256617785832710,389174053161497089,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=5536654071445602430 --mojo-platform-channel-handle=4292 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,4281256617785832710,389174053161497089,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=14405783785232835548 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14405783785232835548 --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4248 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
1 518
Read events
1 292
Write events
220
Delete events
6
Modification events
| (PID) Process: | (3612) daibaichi.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3612) daibaichi.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2384) DaBaiCai.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DaBaiCai_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2384) DaBaiCai.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DaBaiCai_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2384) DaBaiCai.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DaBaiCai_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2384) DaBaiCai.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DaBaiCai_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2384) DaBaiCai.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DaBaiCai_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2384) DaBaiCai.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DaBaiCai_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2384) DaBaiCai.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DaBaiCai_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2384) DaBaiCai.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\DaBaiCai_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
96
Suspicious files
180
Text files
256
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3612 | daibaichi.exe | C:\Users\admin\AppData\Local\Temp\7483.tmp | — | |
MD5:— | SHA256:— | |||
| 3612 | daibaichi.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\大白菜超级U盘装机工具.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3612 | daibaichi.exe | C:\Users\Public\Desktop\大白菜超级U盘装机工具.lnk | lnk | |
MD5:— | SHA256:— | |||
| 3612 | daibaichi.exe | C:\DaBaiCai\Data\Bin\Update.exe | executable | |
MD5:— | SHA256:— | |||
| 2384 | DaBaiCai.exe | C:\DaBaiCai\Data\Hash | text | |
MD5:— | SHA256:— | |||
| 3612 | daibaichi.exe | C:\DaBaiCai\DaBaiCai.exe | executable | |
MD5:— | SHA256:— | |||
| 2384 | DaBaiCai.exe | C:\DaBaiCai\Data\Bin\7za.dll | executable | |
MD5:93AA6A76E2F245C85C76FB4C993BC9CB | SHA256:0C19B611525E2B4FB5F04581B61F4119821A10EABDF73151F22BE18DB2C805B8 | |||
| 2384 | DaBaiCai.exe | C:\DaBaiCai\Data\Bin\bcdedit.exe | executable | |
MD5:C4D5B7B0CC017C7F5B906252A3F42C11 | SHA256:1D5A0320882BE0882BAD0D9A01B265533E359739E5552FBD94D2C49AA62940B3 | |||
| 2384 | DaBaiCai.exe | C:\DaBaiCai\Data\Bin\download\MiniThunderPlatform.exe | executable | |
MD5:DC62945C4E112BC3C3B043C8668A33DF | SHA256:C9B84B242479762DFCA7B707376FDE73CE99AA7BEFA74B9D4F18B4EC1967BD29 | |||
| 2384 | DaBaiCai.exe | C:\DaBaiCai\Data\Bin\download\download_engine.dll | executable | |
MD5:0D732EEA70FD5208A4454A8B0668C9BB | SHA256:440D13B2BD0988F6F6F0C4C7842ACC20A8ABF5B050D4024711AABAB29AA88E93 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
290
TCP/UDP connections
300
DNS requests
98
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2880 | MiniThunderPlatform.exe | GET | — | 103.205.6.84:88 | http://down.winbaicai.com:88/v1/Bin.7z | CN | — | — | suspicious |
2880 | MiniThunderPlatform.exe | GET | — | 103.205.6.84:88 | http://down.winbaicai.com:88/v1/Bin.7z | CN | — | — | suspicious |
2880 | MiniThunderPlatform.exe | GET | — | 103.205.6.84:88 | http://down.winbaicai.com:88/v1/Bin.7z | CN | — | — | suspicious |
2880 | MiniThunderPlatform.exe | GET | — | 103.205.6.84:88 | http://down.winbaicai.com:88/v1/Bin.7z | CN | — | — | suspicious |
2880 | MiniThunderPlatform.exe | GET | — | 103.205.6.84:88 | http://down.winbaicai.com:88/v1/Bin.7z | CN | — | — | suspicious |
2880 | MiniThunderPlatform.exe | GET | — | 103.205.6.84:88 | http://down.winbaicai.com:88/v1/Bin.7z | CN | — | — | suspicious |
2384 | DaBaiCai.exe | POST | — | 47.106.175.21:80 | http://tongji.laomaotao.net/api/dbc/v1/setData | CN | — | — | unknown |
2880 | MiniThunderPlatform.exe | POST | 200 | 119.188.108.14:80 | http://119.188.108.14:80/ | CN | fli | 268 b | unknown |
2880 | MiniThunderPlatform.exe | POST | 200 | 123.129.242.227:80 | http://123.129.242.227:80/ | CN | binary | 1.15 Kb | malicious |
2880 | MiniThunderPlatform.exe | POST | 200 | 123.129.242.221:80 | http://123.129.242.221:80/ | CN | binary | 1.76 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2384 | DaBaiCai.exe | 103.205.6.84:88 | down.winbaicai.com | — | CN | suspicious |
2984 | Update.exe | 103.205.6.84:88 | down.winbaicai.com | — | CN | suspicious |
1708 | Update.exe | 103.205.6.84:88 | down.winbaicai.com | — | CN | suspicious |
2880 | MiniThunderPlatform.exe | 123.129.242.221:80 | hub5c.hz.sandai.net | CHINA UNICOM China169 Backbone | CN | malicious |
2880 | MiniThunderPlatform.exe | 112.80.23.156:80 | pmap.hz.sandai.net | CHINA UNICOM China169 Backbone | CN | malicious |
2880 | MiniThunderPlatform.exe | 103.205.6.84:88 | down.winbaicai.com | — | CN | suspicious |
— | — | 211.91.242.38:8000 | hub5pn.hz.sandai.net | — | CN | unknown |
2880 | MiniThunderPlatform.exe | 123.129.242.154:80 | hubstat.hz.sandai.net | CHINA UNICOM China169 Backbone | CN | malicious |
2880 | MiniThunderPlatform.exe | 123.129.242.227:80 | hub5c.hz.sandai.net | CHINA UNICOM China169 Backbone | CN | malicious |
2880 | MiniThunderPlatform.exe | 119.188.108.14:80 | hub5pr.hz.sandai.net | CHINA UNICOM China169 Backbone | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
down.winbaicai.com |
| suspicious |
tj.colymas.com |
| malicious |
tongji.laomaotao.net |
| unknown |
hub5pnc.hz.sandai.net |
| malicious |
hub5pn.hz.sandai.net |
| unknown |
hub5u.hz.sandai.net |
| unknown |
relay.phub.hz.sandai.net |
| whitelisted |
hub5c.hz.sandai.net |
| malicious |
pmap.hz.sandai.net |
| malicious |
hub5idx.shub.hz.sandai.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2880 | MiniThunderPlatform.exe | Misc activity | ADWARE [PTsecurity] Win32.Downloader (Sogou/Chindo) |
2880 | MiniThunderPlatform.exe | Misc activity | ADWARE [PTsecurity] Win32.Downloader (Sogou/Chindo) |
2880 | MiniThunderPlatform.exe | Misc activity | ADWARE [PTsecurity] Win32.Downloader (Sogou/Chindo) |
2880 | MiniThunderPlatform.exe | Misc activity | ADWARE [PTsecurity] Win32.Downloader (Sogou/Chindo) |
2880 | MiniThunderPlatform.exe | Misc activity | ADWARE [PTsecurity] Win32.Downloader (Sogou/Chindo) |
2880 | MiniThunderPlatform.exe | Misc activity | ADWARE [PTsecurity] Win32.Downloader (Sogou/Chindo) |
2880 | MiniThunderPlatform.exe | Generic Protocol Command Decode | SURICATA STREAM CLOSEWAIT FIN out of window |
2880 | MiniThunderPlatform.exe | Generic Protocol Command Decode | SURICATA STREAM CLOSEWAIT FIN out of window |
2880 | MiniThunderPlatform.exe | Generic Protocol Command Decode | SURICATA STREAM CLOSEWAIT FIN out of window |
2880 | MiniThunderPlatform.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
Dism.exe | PID=3640 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=3640 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=3640 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=3640 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=3640 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=3640 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
Dism.exe | PID=3640 Getting Provider OSServices - CDISMProviderStore::GetProvider |
Dism.exe | PID=3640 The requested provider was not found in the Provider Store. - CDISMProviderStore::Internal_GetProvider(hr:0x80004005) |
Dism.exe | PID=3640 Failed to get an OSServices provider. Must be running in local store. Falling back to checking alongside the log provider for wdscore.dll. - CDISMLogger::FindWdsCore(hr:0x80004005) |
Dism.exe | PID=3640 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |