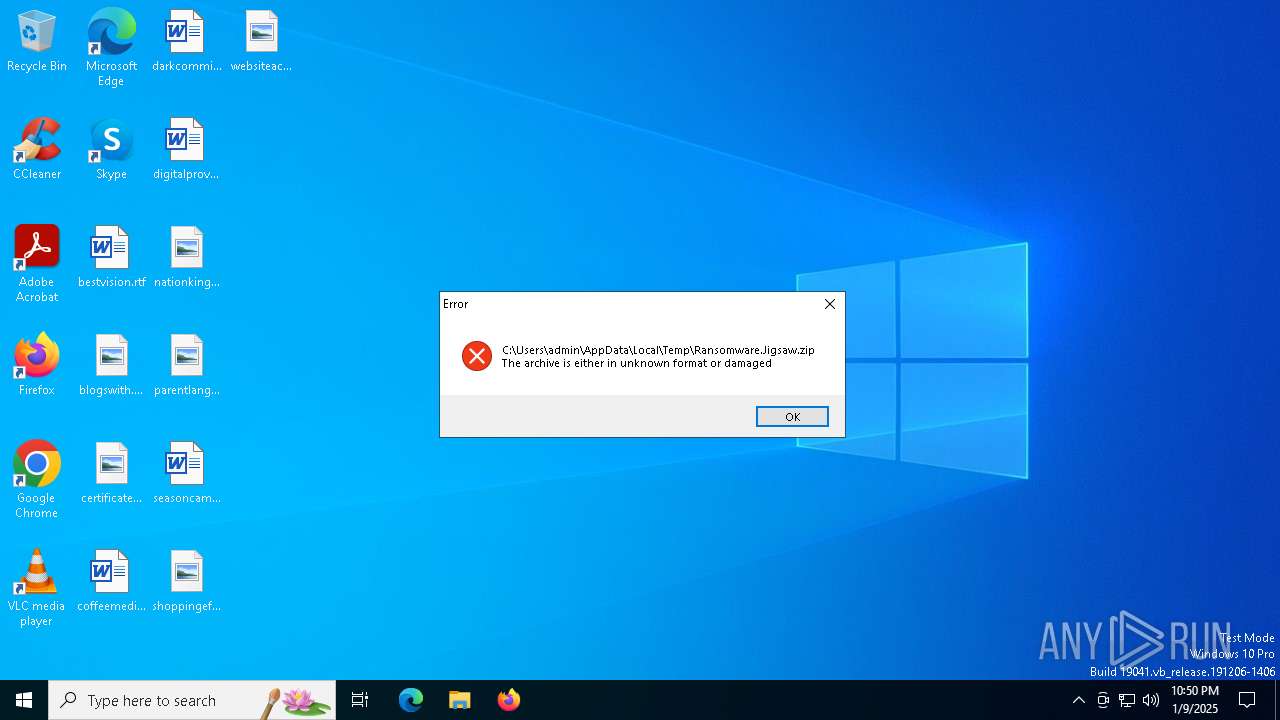
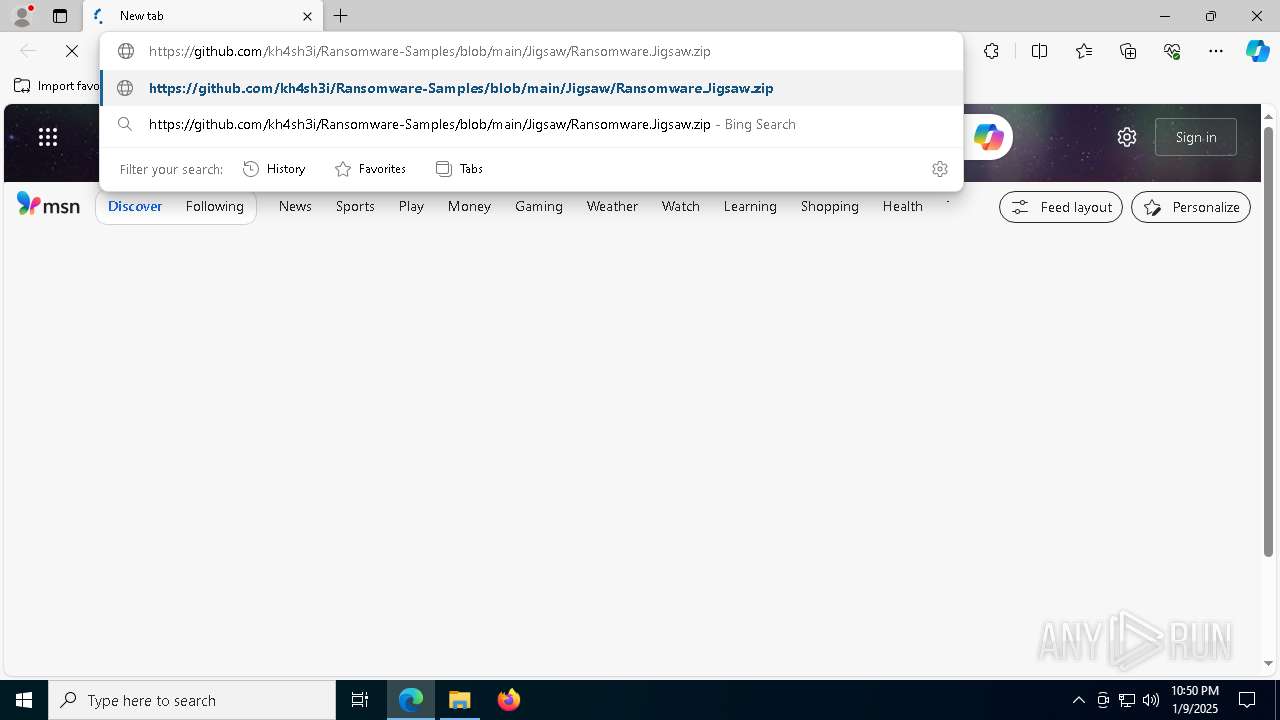
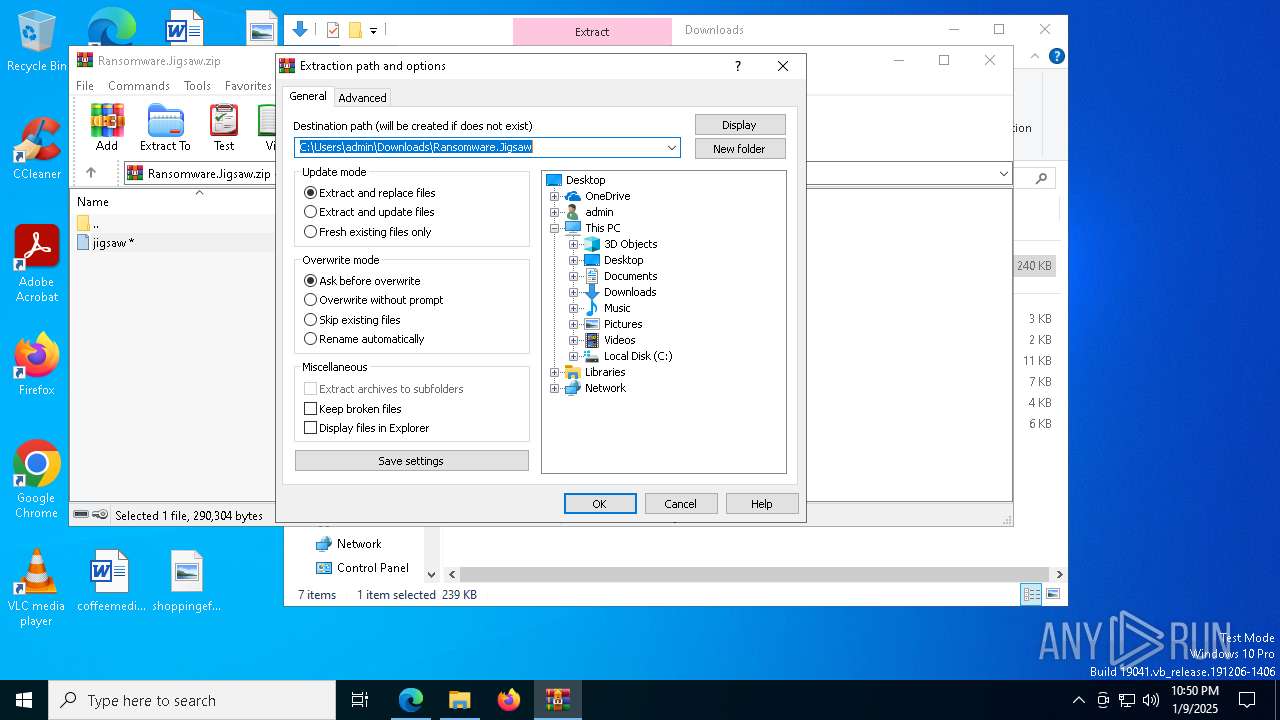
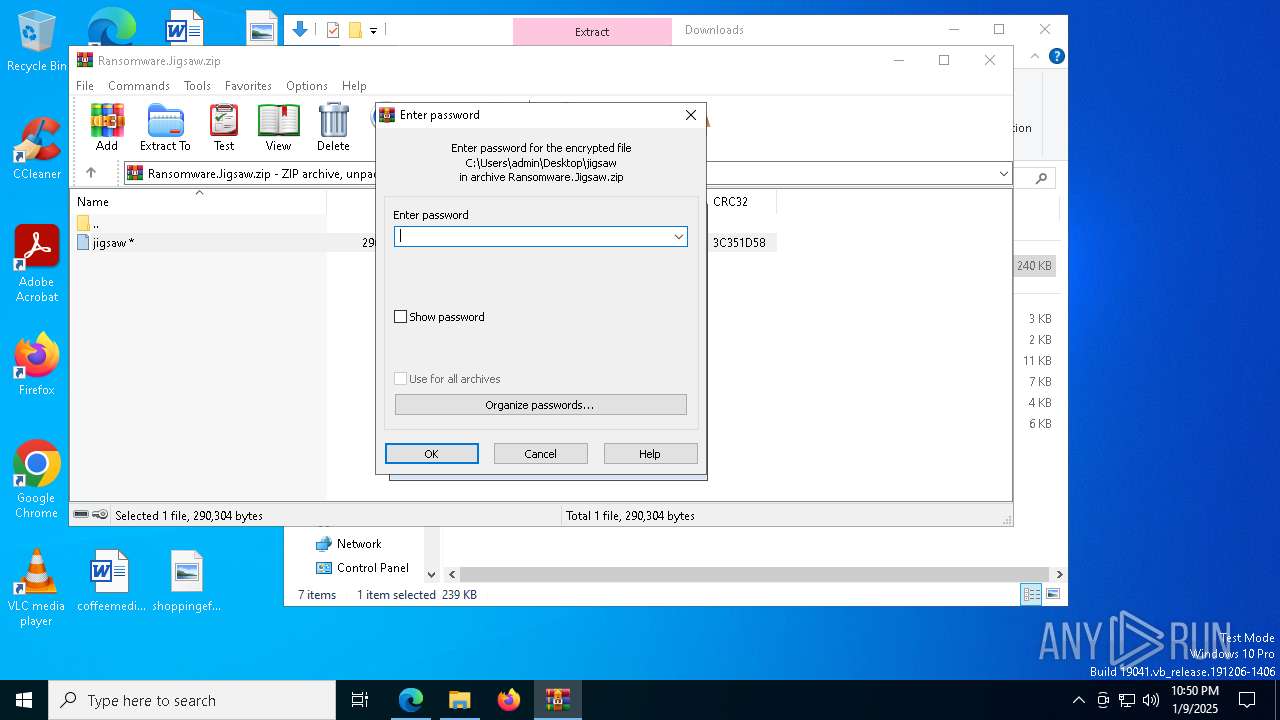
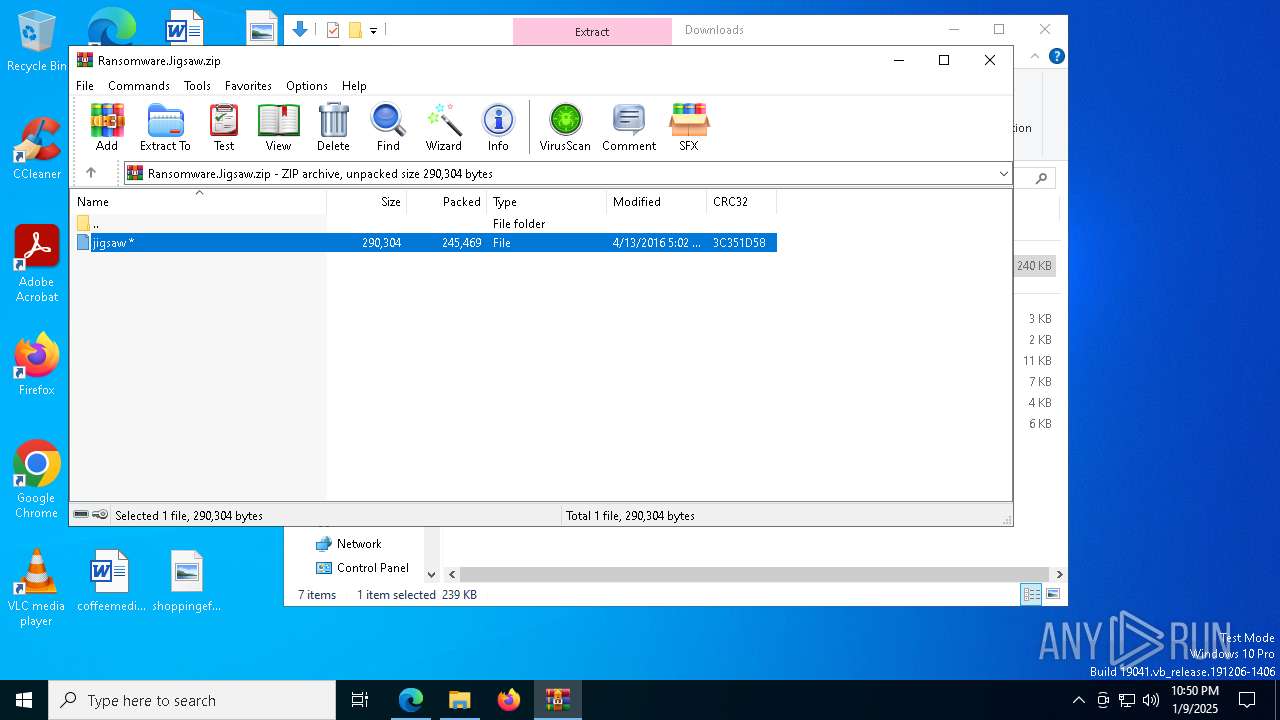
| download: | /kh4sh3i/Ransomware-Samples/blob/main/Jigsaw/Ransomware.Jigsaw.zip |
| Full analysis: | https://app.any.run/tasks/3cd66644-9ad6-4bf3-b379-aef2b5893ddf |
| Verdict: | Malicious activity |
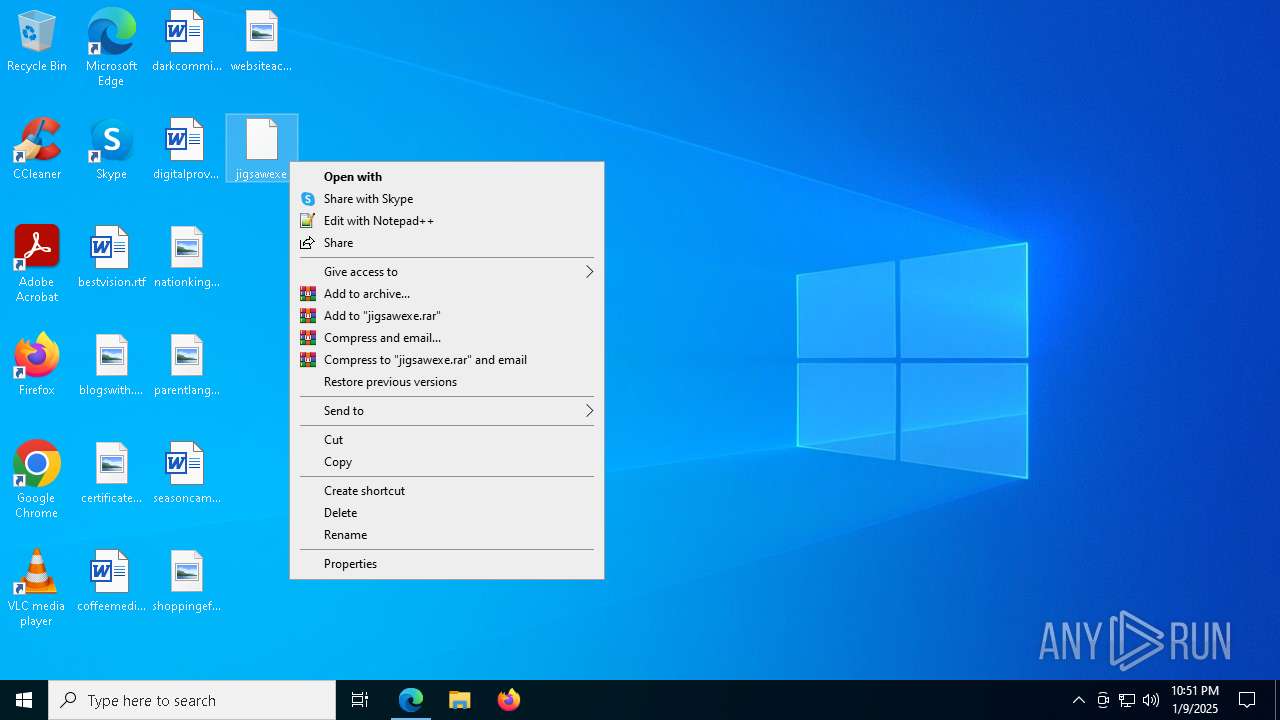
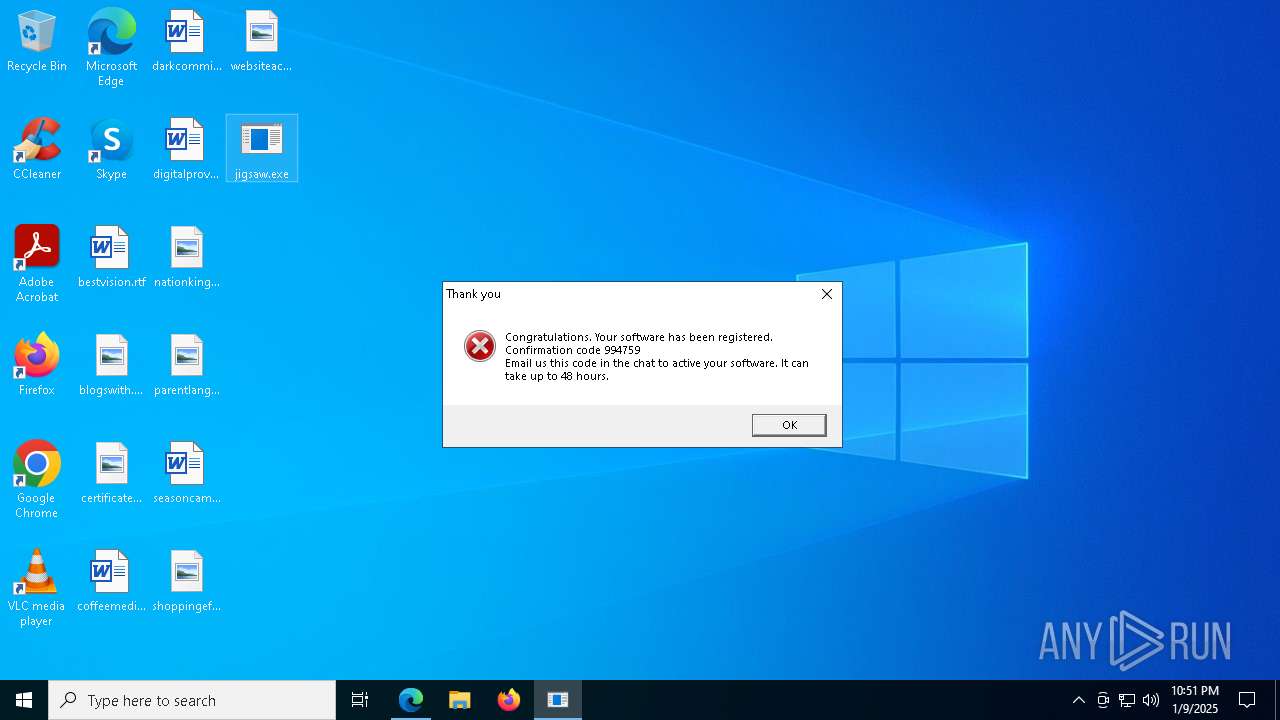
| Threats: | The Jigsaw ransomware, initially detected in 2016, encrypts files on compromised systems and requires a ransom payment in Bitcoin. If the ransom is not paid, the malware starts deleting files, increasing the pressure on victims to comply. Its source code is publicly accessible, allowing various threat actors to customize and repurpose the malware for different objectives. |
| Analysis date: | January 09, 2025, 22:49:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, Unicode text, UTF-8 text, with very long lines (1616) |
| MD5: | A85E0B39896DEC96E6D7B2DB77D90901 |
| SHA1: | 282ADAD630DE6542E47F3569BE57F3B6B79E128D |
| SHA256: | 0225FB0A196BCC06FABFC50698AC8E7D63FCF5EF25E5938E99CF14AA492437C2 |
| SSDEEP: | 6144:c7snApOL/saqkPV9Fe2LtcIDSsmwT95vZJT3CqbMrhryf65NRPaCieMjAkvCJv1i:YsnApOL/saqkPV9Fe2LtcIDSsmwT95v5 |
MALICIOUS
JIGSAW has been detected
- jigsaw.exe (PID: 7280)
SUSPICIOUS
Executable content was dropped or overwritten
- jigsaw.exe (PID: 7280)
Reads security settings of Internet Explorer
- jigsaw.exe (PID: 7280)
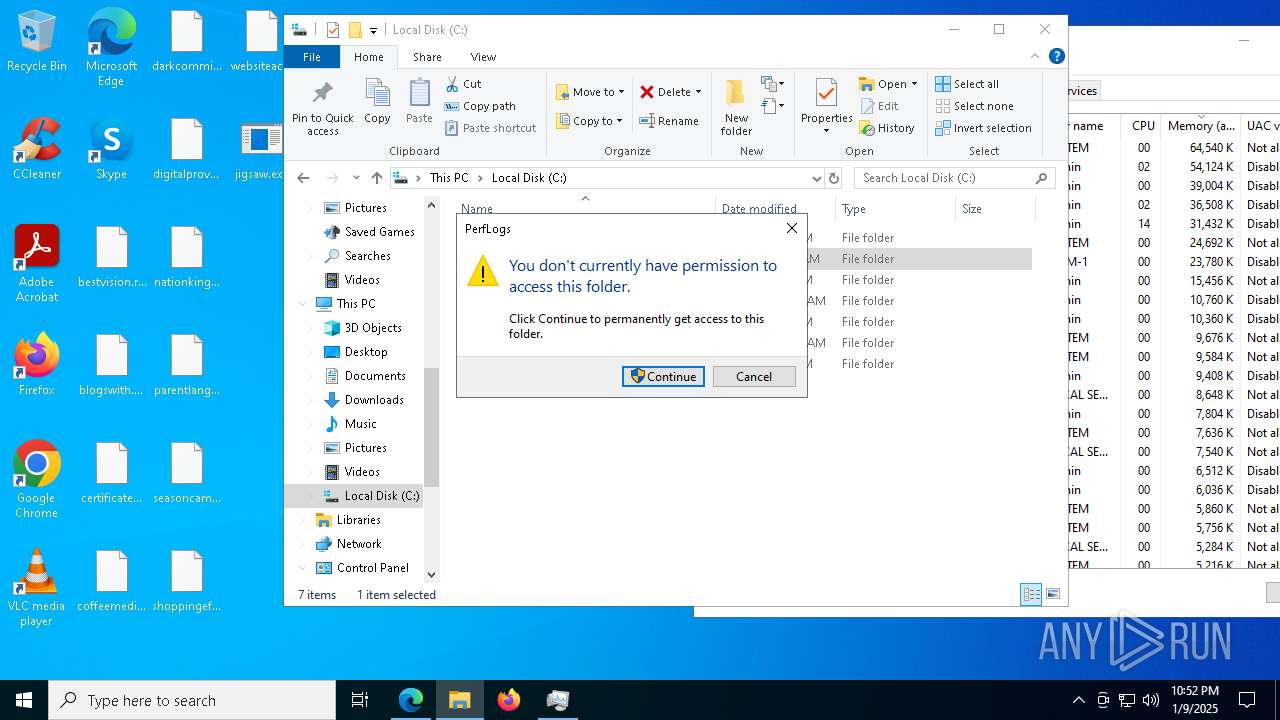
Starts itself from another location
- jigsaw.exe (PID: 7280)
INFO
Application launched itself
- msedge.exe (PID: 6252)
Manual execution by a user
- msedge.exe (PID: 6252)
- WinRAR.exe (PID: 7916)
- jigsaw.exe (PID: 7280)
- Taskmgr.exe (PID: 6680)
- Taskmgr.exe (PID: 6472)
Checks supported languages
- identity_helper.exe (PID: 7468)
- jigsaw.exe (PID: 7280)
- drpbx.exe (PID: 7136)
The process uses the downloaded file
- WinRAR.exe (PID: 7916)
- jigsaw.exe (PID: 7280)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7916)
Creates files or folders in the user directory
- jigsaw.exe (PID: 7280)
Confuser has been detected (YARA)
- drpbx.exe (PID: 7136)
Reads the machine GUID from the registry
- drpbx.exe (PID: 7136)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| Title: | Ransomware-Samples/Jigsaw/Ransomware.Jigsaw.zip at main · kh4sh3i/Ransomware-Samples · GitHub |
|---|---|
| RoutePattern: | /:user_id/:repository/blob/*name(/*path) |
| RouteController: | blob |
| RouteAction: | show |
| CurrentCatalogServiceHash: | f3abb0cc802f3d7b95fc8762b94bdcb13bf39634c40c357301c4aa1d67a256fb |
| RequestId: | 9D86:1D885C:15681D7:15ED7BD:67805292 |
| HtmlSafeNonce: | c77d76042969315457a8e27efd2385c06fc6b66aa1a43a1e53c02b0aefed319c |
| VisitorPayload: | eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI5RDg2OjFEODg1QzoxNTY4MUQ3OjE1RUQ3QkQ6Njc4MDUyOTIiLCJ2aXNpdG9yX2lkIjoiMjQwNTAzODc2NjYxMzAxOTA2IiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0= |
| VisitorHmac: | a30d4e1a01f5f8c6b902aec3a117d2606698935115bfc19c322e7e3dc35fb84f |
| HovercardSubjectTag: | repository:394609962 |
| GithubKeyboardShortcuts: | repository,source-code,file-tree,copilot |
| GoogleSiteVerification: | Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I |
| OctolyticsUrl: | https://collector.github.com/github/collect |
| AnalyticsLocation: | /<user-name>/<repo-name>/blob/show |
| UserLogin: | - |
| Viewport: | width=device-width |
| Description: | Small collection of Ransomware organized by family. - Ransomware-Samples/Jigsaw/Ransomware.Jigsaw.zip at main · kh4sh3i/Ransomware-Samples |
| AppleItunesApp: | app-id=1477376905, app-argument=https://github.com/kh4sh3i/Ransomware-Samples/blob/main/Jigsaw/Ransomware.Jigsaw.zip |
| TwitterImage: | https://opengraph.githubassets.com/30db34218db1a3ae83a3d4fe90127356301f7a5bfabffb6396a1ec6bce011433/kh4sh3i/Ransomware-Samples |
| TwitterSite: | @github |
| TwitterCard: | summary_large_image |
| TwitterTitle: | Ransomware-Samples/Jigsaw/Ransomware.Jigsaw.zip at main · kh4sh3i/Ransomware-Samples |
| TwitterDescription: | Small collection of Ransomware organized by family. - kh4sh3i/Ransomware-Samples |
| Hostname: | github.com |
| ExpectedHostname: | github.com |
| HTTPEquivXPjaxVersion: | 094293d1ac0b6948cbf7eff56e5c13d1744382e3a49fdb288152724062fffa71 |
| HTTPEquivXPjaxCspVersion: | ace39c3b6632770952207593607e6e0be0db363435a8b877b1f96abe6430f345 |
| HTTPEquivXPjaxCssVersion: | 83077cf911605d17127453d01c62034b8070f991798fc7ededcb0f1f056f9796 |
| HTTPEquivXPjaxJsVersion: | 5758a5334c3d33a61b2bd2d9a43aea1333399156ab4cadbeaf7ff85fee74b240 |
| TurboCacheControl: | no-cache |
| GoImport: | github.com/kh4sh3i/Ransomware-Samples git https://github.com/kh4sh3i/Ransomware-Samples.git |
| OctolyticsDimensionUser_id: | 64693844 |
| OctolyticsDimensionUser_login: | kh4sh3i |
| OctolyticsDimensionRepository_id: | 394609962 |
| OctolyticsDimensionRepository_nwo: | kh4sh3i/Ransomware-Samples |
| OctolyticsDimensionRepository_public: | |
| OctolyticsDimensionRepository_is_fork: | - |
| OctolyticsDimensionRepository_network_root_id: | 394609962 |
| OctolyticsDimensionRepository_network_root_nwo: | kh4sh3i/Ransomware-Samples |
| TurboBodyClasses: | logged-out env-production page-responsive |
| BrowserStatsUrl: | https://api.github.com/_private/browser/stats |
| BrowserErrorsUrl: | https://api.github.com/_private/browser/errors |
| ThemeColor: | #1e2327 |
| ColorScheme: | light dark |
Total processes
192
Monitored processes
59
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2416 --field-trial-handle=2244,i,16101050831476214064,6845224711536301427,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 880 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5836 --field-trial-handle=2244,i,16101050831476214064,6845224711536301427,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1704 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6160 --field-trial-handle=2244,i,16101050831476214064,6845224711536301427,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2136 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6944 --field-trial-handle=2244,i,16101050831476214064,6845224711536301427,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2148 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=4316 --field-trial-handle=2244,i,16101050831476214064,6845224711536301427,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2292 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5564 --field-trial-handle=2244,i,16101050831476214064,6845224711536301427,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2292 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --no-appcompat-clear --mojo-platform-channel-handle=5868 --field-trial-handle=2244,i,16101050831476214064,6845224711536301427,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2312 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3888 --field-trial-handle=2244,i,16101050831476214064,6845224711536301427,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2336 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=8456 --field-trial-handle=2244,i,16101050831476214064,6845224711536301427,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2800 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3696 --field-trial-handle=2244,i,16101050831476214064,6845224711536301427,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
18 789
Read events
18 719
Write events
56
Delete events
14
Modification events
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F0000000000000000000000000000000000000000000CC02070000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F0000000000000000000000000000000000000000000BA0205000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (6308) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F0000000000000000000000000000000000000000000020306000000000000000000180000006400000000000000000000000000000003000000 | |||
| (PID) Process: | (6252) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6252) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6252) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
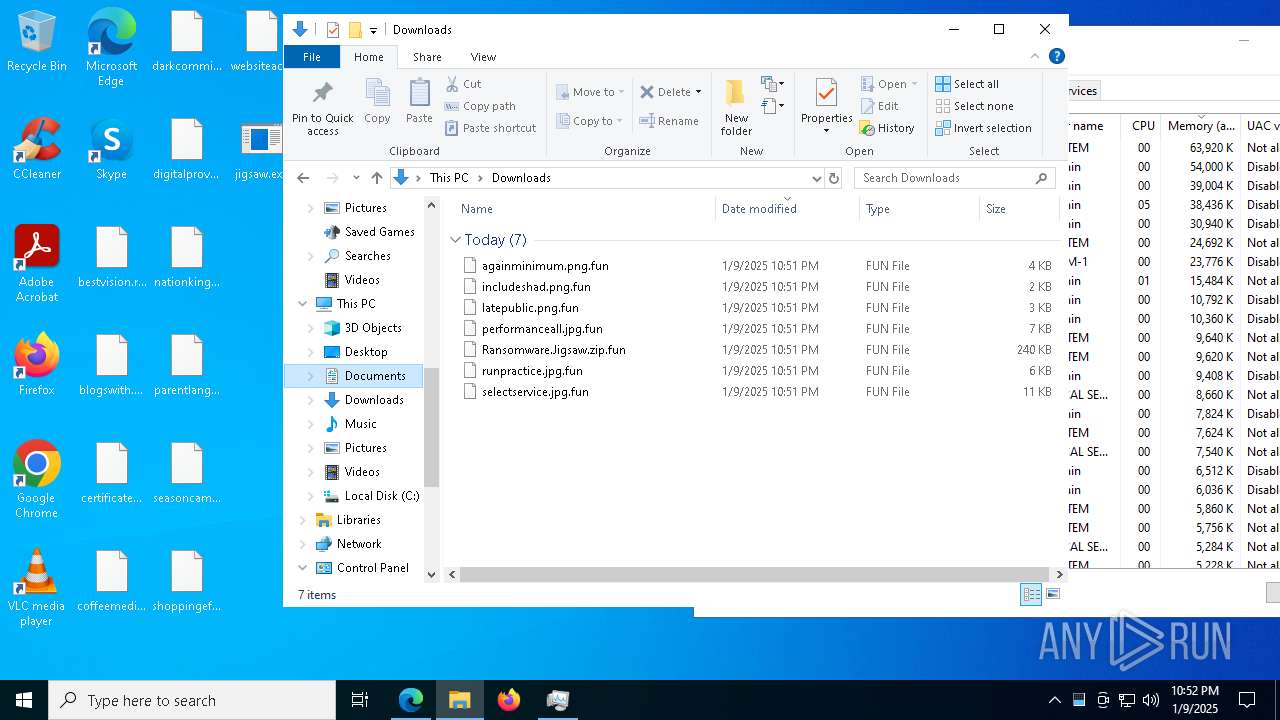
Executable files
33
Suspicious files
897
Text files
101
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF13ba4b.TMP | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF13ba5a.TMP | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF13ba5a.TMP | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF13ba6a.TMP | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF13ba6a.TMP | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6252 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
123
DNS requests
140
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7628 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1736931800&P2=404&P3=2&P4=GYqxR%2fUyCNN0gLwlmTZGrvNUFvak7kRbWd%2b4CLwtQkpvjnT7UOtqxRb4s%2fn0PDLu%2fkOSjls9WkDUCb9a629SSg%3d%3d | unknown | — | — | whitelisted |
7628 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fb6dd03b-99d7-4cc8-a878-91c8e655c2d3?P1=1736931800&P2=404&P3=2&P4=GYqxR%2fUyCNN0gLwlmTZGrvNUFvak7kRbWd%2b4CLwtQkpvjnT7UOtqxRb4s%2fn0PDLu%2fkOSjls9WkDUCb9a629SSg%3d%3d | unknown | — | — | whitelisted |
7628 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0529a13c-ea24-474d-87d7-66f668b071b4?P1=1736931800&P2=404&P3=2&P4=gLFFA4PhD%2fuPx07lE3uRp824317u3C2PWzIcRa5iLL6al5Vok%2fp7lPJLWZR65jpAlSOAqda25Dxc5Fq%2bJzZXoA%3d%3d | unknown | — | — | whitelisted |
7628 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0529a13c-ea24-474d-87d7-66f668b071b4?P1=1736931800&P2=404&P3=2&P4=gLFFA4PhD%2fuPx07lE3uRp824317u3C2PWzIcRa5iLL6al5Vok%2fp7lPJLWZR65jpAlSOAqda25Dxc5Fq%2bJzZXoA%3d%3d | unknown | — | — | whitelisted |
7628 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/0529a13c-ea24-474d-87d7-66f668b071b4?P1=1736931800&P2=404&P3=2&P4=gLFFA4PhD%2fuPx07lE3uRp824317u3C2PWzIcRa5iLL6al5Vok%2fp7lPJLWZR65jpAlSOAqda25Dxc5Fq%2bJzZXoA%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 69.192.161.44:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 69.192.161.44:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5000 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
640 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
640 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
640 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
640 | msedge.exe | Misc activity | SUSPICIOUS [ANY.RUN] Tracking Service (.popin .cc) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |