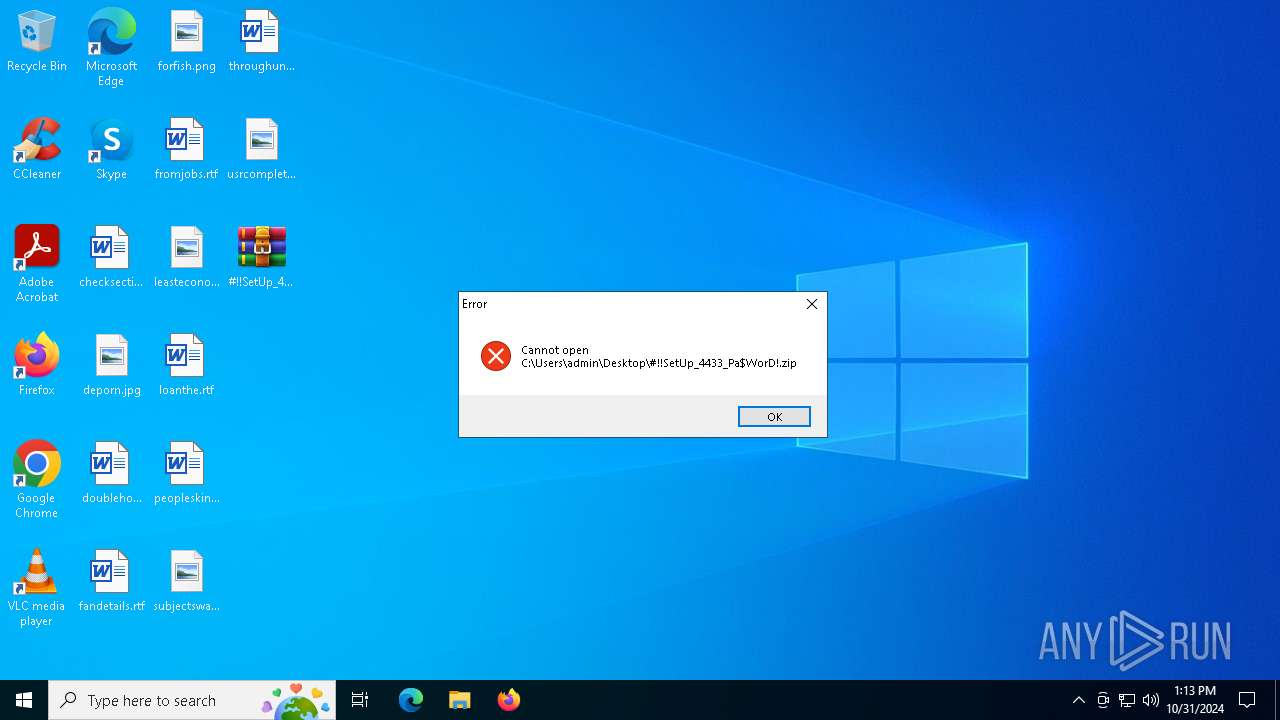
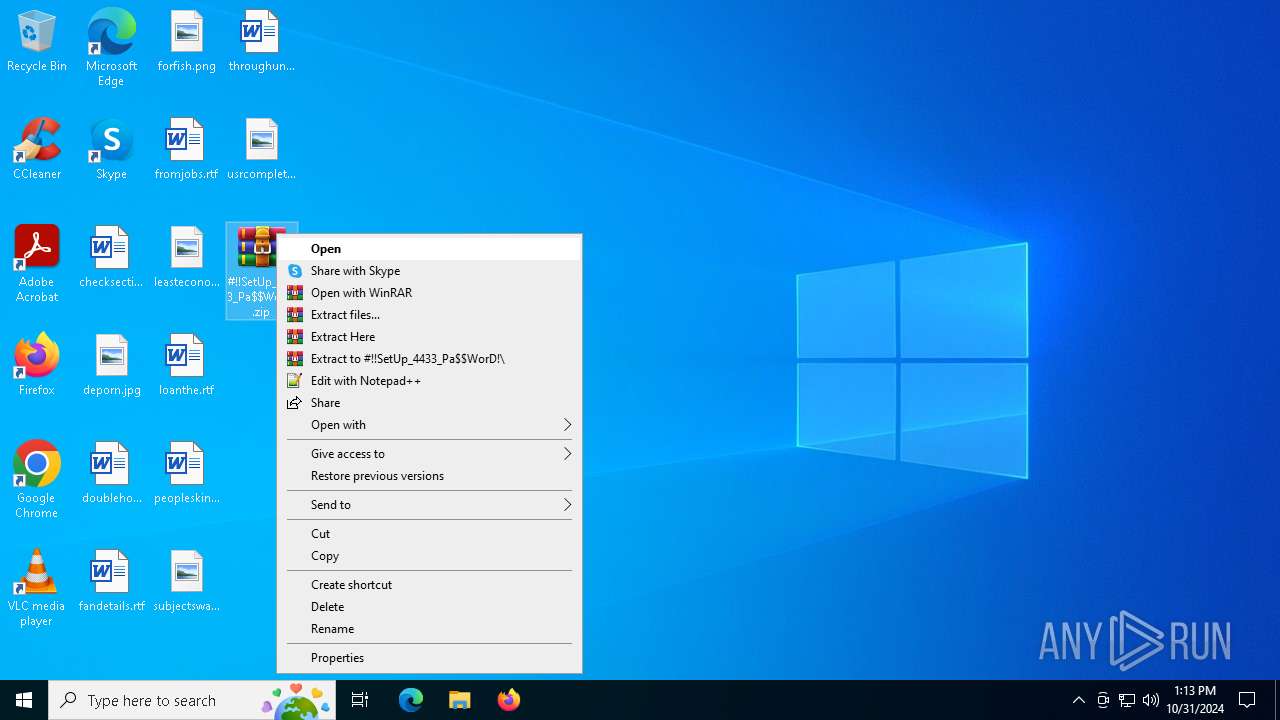
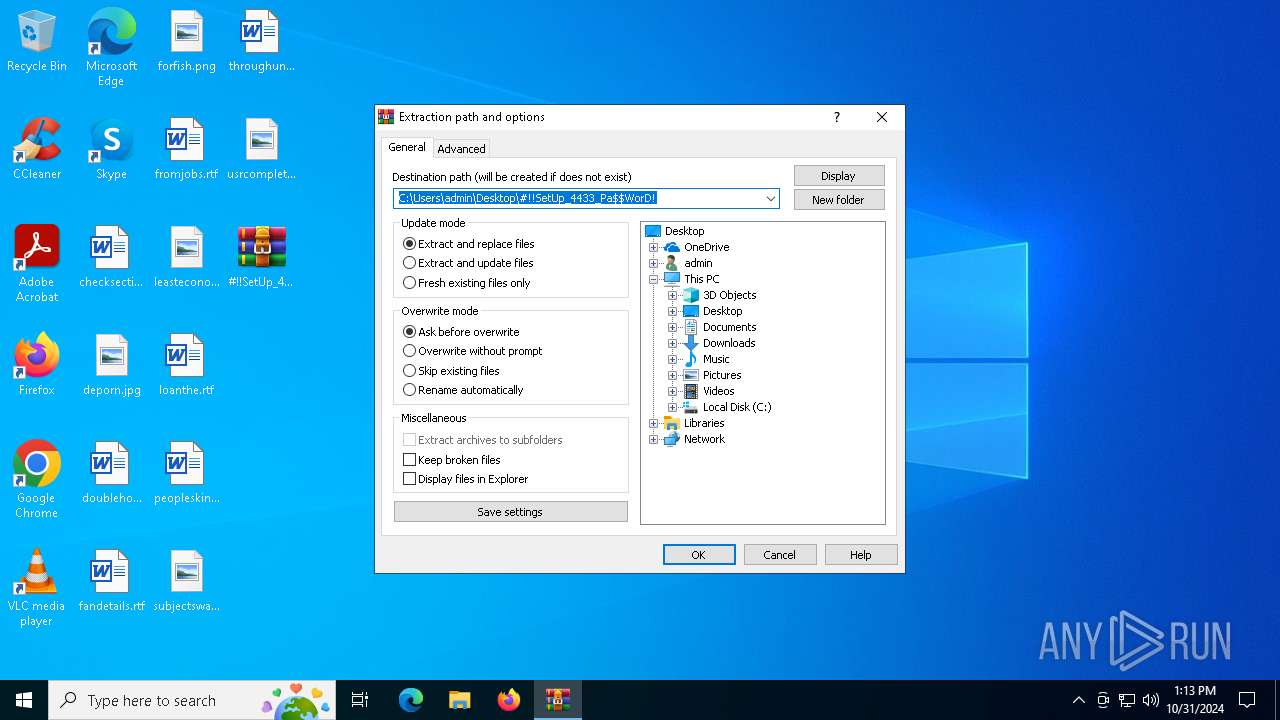
| File name: | #!!SetUp_4433_Pa$WorD!.zip |
| Full analysis: | https://app.any.run/tasks/b7362edf-d1a2-493d-9379-6df3f7f793d8 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | October 31, 2024, 13:13:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | BD59FC3D48FB364167544C5DC6619E78 |
| SHA1: | 4140B630A245BC844C8B393F703546E3F076117C |
| SHA256: | 01BE1D48F82E7DBF0D55C387134980748F2A871B004AB39D63D7DB775E0C1577 |
| SSDEEP: | 98304:Gt/a4YZDhTADh7bbMYIleaaAG6Zdt+NoUZJ0NRoYm+jTDct1Y7emeFiuasHUc5pd:CHcJtGfdj2NbF7/m1ecDz |
MALICIOUS
LUMMA has been detected (YARA)
- OpenWith.exe (PID: 6420)
Stealers network behavior
- svchost.exe (PID: 2172)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2172)
Bypass execution policy to execute commands
- powershell.exe (PID: 6960)
Changes powershell execution policy (Bypass)
- OpenWith.exe (PID: 6420)
AMADEY has been detected (YARA)
- explorer.exe (PID: 6704)
Connects to the CnC server
- explorer.exe (PID: 6704)
AMADEY has been detected (SURICATA)
- explorer.exe (PID: 6704)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1732)
- WinRAR.exe (PID: 6344)
- Set-up.exe (PID: 1784)
Executable content was dropped or overwritten
- Set-up.exe (PID: 1784)
- OpenWith.exe (PID: 6420)
- AutoIt3.exe (PID: 6612)
The process drops C-runtime libraries
- Set-up.exe (PID: 1784)
Starts a Microsoft application from unusual location
- Set-up.exe (PID: 1784)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2172)
- explorer.exe (PID: 6704)
Node.exe was dropped
- OpenWith.exe (PID: 6420)
Starts application with an unusual extension
- Set-up.exe (PID: 1784)
The process executes Powershell scripts
- OpenWith.exe (PID: 6420)
Starts POWERSHELL.EXE for commands execution
- OpenWith.exe (PID: 6420)
Connects to unusual port
- MicrosoftEdgeUpdateCore.exe (PID: 608)
Found regular expressions for crypto-addresses (YARA)
- MicrosoftEdgeUpdateCore.exe (PID: 608)
There is functionality for enable RDP (YARA)
- explorer.exe (PID: 6704)
INFO
Manual execution by a user
- WinRAR.exe (PID: 1732)
- Set-up.exe (PID: 1784)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1732)
The process uses the downloaded file
- WinRAR.exe (PID: 1732)
Application based on Golang
- MicrosoftEdgeUpdateCore.exe (PID: 608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(6704) explorer.exe
C2moviecentral-petparade.com
Strings (129)Kaspersky Lab
ProductName
------
POST
ESET
random
bi:
0000043f
S-%lu-
moviecentral-petparade.com
Doctor Web
GET
Bitdefender
moviecentral-petparade2.com
-unicode-
#
ar:
/Plugins/
cred.dll
VideoID
/quiet
wb
/g9jvjfd73/index.php
e3
&&
Powershell.exe
"
00000422
\
cmd /C RMDIR /s/q
00000423
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
a6c6395115
un:
cred.dll|clip.dll|
e2
moviecentral-petparade3.com
Programs
msi
av:
r=
/8bkjdSdfjCe/index.php
DefaultSettings.YResolution
AVG
dm:
rb
Panda Security
" && timeout 1 && del
Main
zip
5.03
SOFTWARE\Microsoft\Windows NT\CurrentVersion
%-lu
Norton
e1
Comodo
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
2016
CurrentBuild
Sophos
<d>
ComputerName
pc:
GetNativeSystemInfo
abcdefghijklmnopqrstuvwxyz0123456789-_
d1
lv:
AVAST Software
:::
Rem
exe
|
vs:
--
https://
WinDefender
st=s
&unit=
Startup
=
kernel32.dll
ProgramData\
rundll32.exe
id:
sd:
" && ren
Keyboard Layout\Preload
00000419
/k
.jpg
+++
-executionpolicy remotesigned -File "
"taskkill /f /im "
cmd
?scr=1
360TotalSecurity
0123456789
dll
shell32.dll
Content-Type: multipart/form-data; boundary=----
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Content-Disposition: form-data; name="data"; filename="
-%lu
------
\0000
ps1
Avira
clip.dll
2019
&& Exit"
rundll32
SYSTEM\ControlSet001\Services\BasicDisplay\Video
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
\App
http://
%USERPROFILE%
shutdown -s -t 0
"
Content-Type: application/octet-stream
Content-Type: application/x-www-form-urlencoded
/g9jvjfd74/index.php
Gxtuum.exe
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
og:
<c>
DefaultSettings.XResolution
os:
2025
2022
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:30 14:17:06 |
| ZipCRC: | 0x5bca7345 |
| ZipCompressedSize: | 1069200 |
| ZipUncompressedSize: | 1126214 |
| ZipFileName: | aktfh |
Total processes
148
Monitored processes
19
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 608 | C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.185.17\MicrosoftEdgeUpdateCore.exe | C:\Program Files (x86)\Microsoft\EdgeUpdate\1.3.185.17\MicrosoftEdgeUpdateCore.exe | AutoIt3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.185.17 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\#!!SetUp_4433_Pa$WorD!.zip" "?\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1784 | "C:\Users\admin\Desktop\#!!SetUp_4433_Pa$WorD!\Set-up.exe" | C:\Users\admin\Desktop\#!!SetUp_4433_Pa$WorD!\Set-up.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Live Messenger Exit code: 1 Version: 8.5.1235.0517 Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2928 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | comp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | more.com | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4436 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | nc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5580 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 515
Read events
14 479
Write events
23
Delete events
13
Modification events
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F00000000000000000000000000000000000000000003202090000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F0000000000000000000000000000000000000000000640204000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F0000000000000000000000000000000000000000000D80204000000000000000000180000006400000000000000000000000000000003000000 | |||
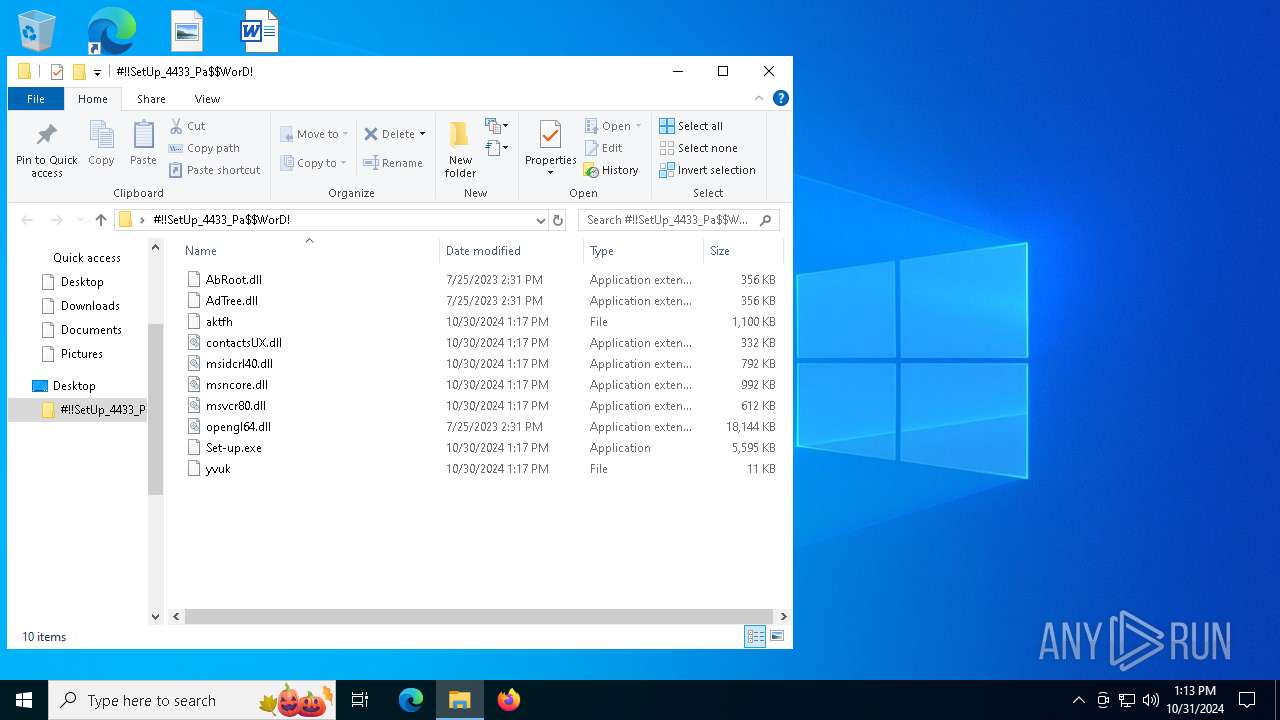
Executable files
16
Suspicious files
12
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7152 | more.com | C:\Users\admin\AppData\Local\Temp\fvqffhykhgeor | — | |
MD5:— | SHA256:— | |||
| 1732 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_4433_Pa$WorD!\msncore.dll | executable | |
MD5:DEAA38A71C85D2F9D4BA71343D1603DA | SHA256:1DC120F34B294E964EEE949C4D1EBD9C271715D46B38AE082FEC2F1D505E8D65 | |||
| 1732 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_4433_Pa$WorD!\aktfh | binary | |
MD5:721AC5A0FC4C15AFA7FCFADC3F56EA88 | SHA256:6CF445F695E484C35B252D630B0BA6A13DADEEBD58E9000033753FAF0BBB1CCA | |||
| 1732 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_4433_Pa$WorD!\msidcrl40.dll | executable | |
MD5:99AAF486011BB3251113CC4A3BEB4BA7 | SHA256:F2CDD90CECE5D69F2FFBE8C6349F08646DBB942993C8EE4CF44084F220F99ED3 | |||
| 1732 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_4433_Pa$WorD!\contactsUX.dll | executable | |
MD5:54EE6A204238313DC6ACA21C7E036C17 | SHA256:0ABF68B8409046A1555D48AC506FD26FDA4B29D8D61E07BC412A4E21DE2782FD | |||
| 1784 | Set-up.exe | C:\Users\admin\AppData\Roaming\euu\msncore.dll | executable | |
MD5:DEAA38A71C85D2F9D4BA71343D1603DA | SHA256:1DC120F34B294E964EEE949C4D1EBD9C271715D46B38AE082FEC2F1D505E8D65 | |||
| 1732 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_4433_Pa$WorD!\yvuk | binary | |
MD5:65BFB05C9DE474C1958E0B4AA0E71CEC | SHA256:DA0C735F265C9C1A5AC5471C62C9FC5BC1130A05A88FAAE049157531F22963AD | |||
| 1784 | Set-up.exe | C:\Users\admin\AppData\Roaming\euu\msidcrl40.dll | executable | |
MD5:99AAF486011BB3251113CC4A3BEB4BA7 | SHA256:F2CDD90CECE5D69F2FFBE8C6349F08646DBB942993C8EE4CF44084F220F99ED3 | |||
| 1784 | Set-up.exe | C:\Users\admin\AppData\Roaming\euu\contactsUX.dll | executable | |
MD5:54EE6A204238313DC6ACA21C7E036C17 | SHA256:0ABF68B8409046A1555D48AC506FD26FDA4B29D8D61E07BC412A4E21DE2782FD | |||
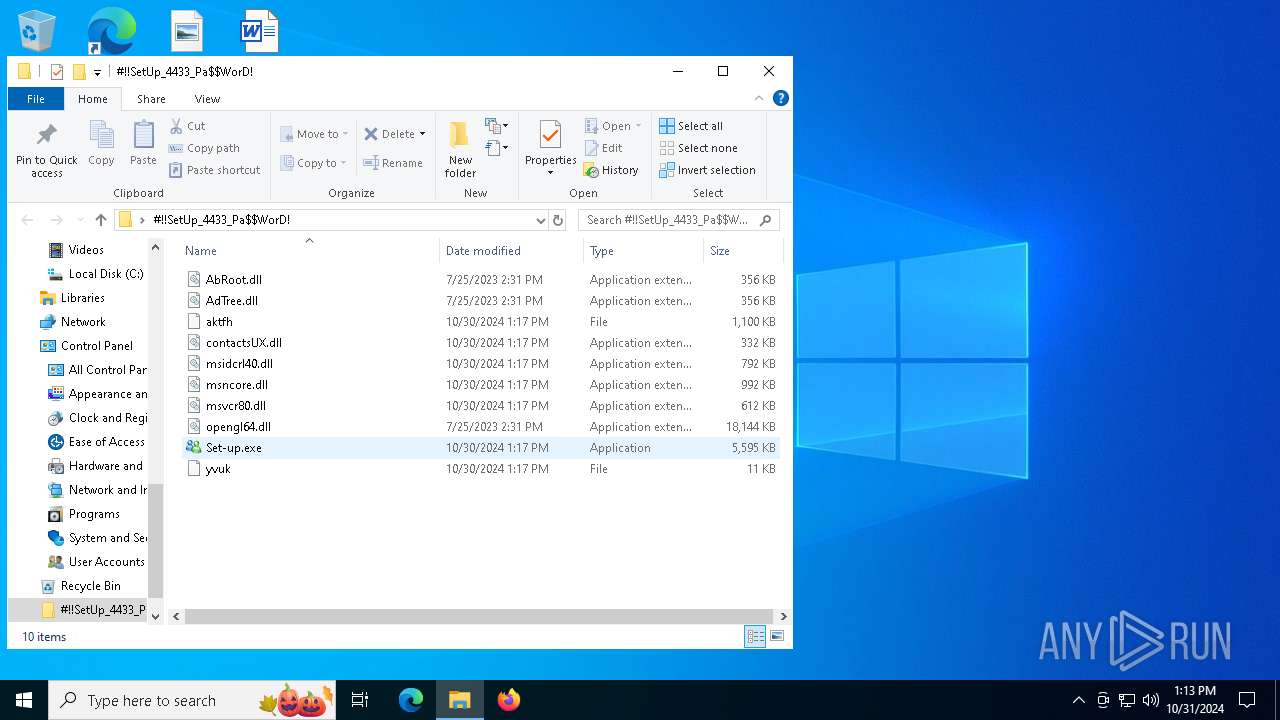
| 1732 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_4433_Pa$WorD!\Set-up.exe | executable | |
MD5:537915708FE4E81E18E99D5104B353ED | SHA256:6DC7275F2143D1DE0CA66C487B0F2EBFF3D4C6A79684F03B9619BF23143ECF74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
59
DNS requests
33
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3600 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6420 | OpenWith.exe | GET | 200 | 172.217.18.99:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
6420 | OpenWith.exe | GET | 200 | 172.217.18.99:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6704 | explorer.exe | POST | 200 | 104.21.23.211:80 | http://moviecentral-petparade.com/g9jvjfd73/index.php | unknown | — | — | malicious |
6704 | explorer.exe | POST | 200 | 104.21.23.211:80 | http://moviecentral-petparade.com/g9jvjfd73/index.php | unknown | — | — | malicious |
6704 | explorer.exe | POST | 200 | 104.21.23.211:80 | http://moviecentral-petparade.com/g9jvjfd73/index.php | unknown | — | — | malicious |
6704 | explorer.exe | POST | 200 | 104.21.23.211:80 | http://moviecentral-petparade.com/g9jvjfd73/index.php | unknown | — | — | malicious |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1588 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 104.126.37.178:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1552 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (creative-habitat .shop) |
2172 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
6420 | OpenWith.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (creative-habitat .shop) |
6704 | explorer.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
6704 | explorer.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
7 ETPRO signatures available at the full report