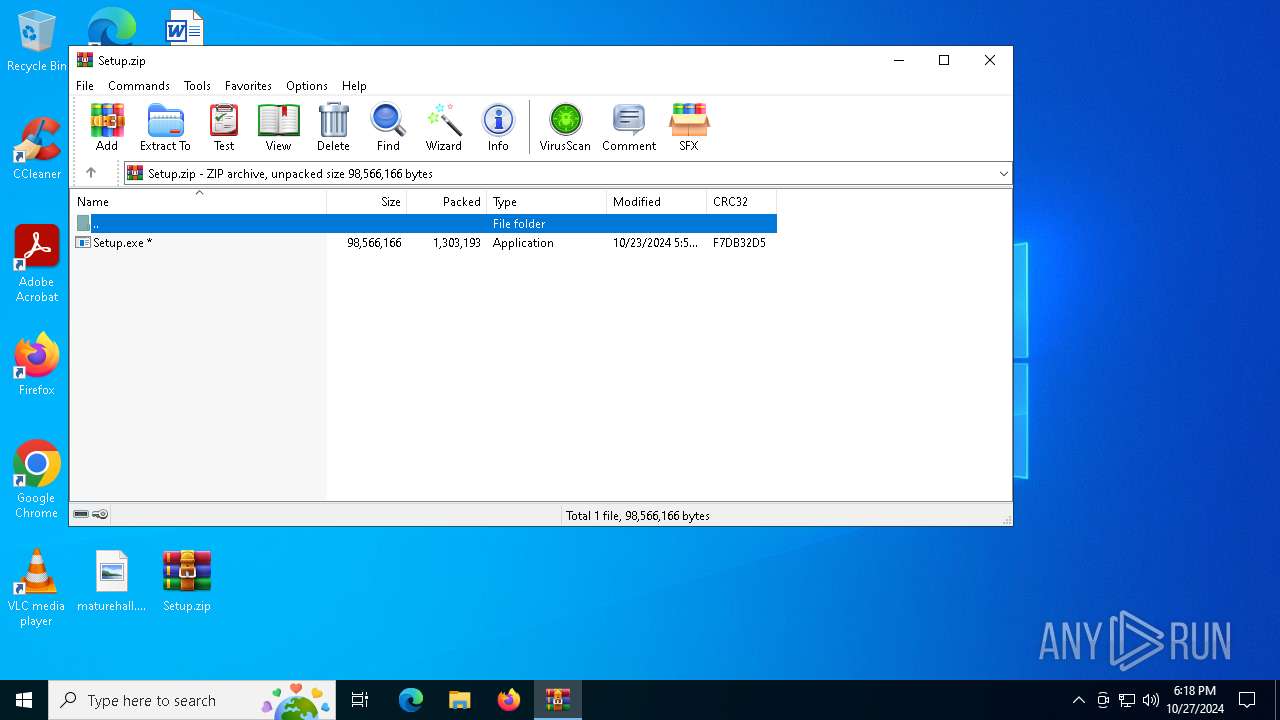
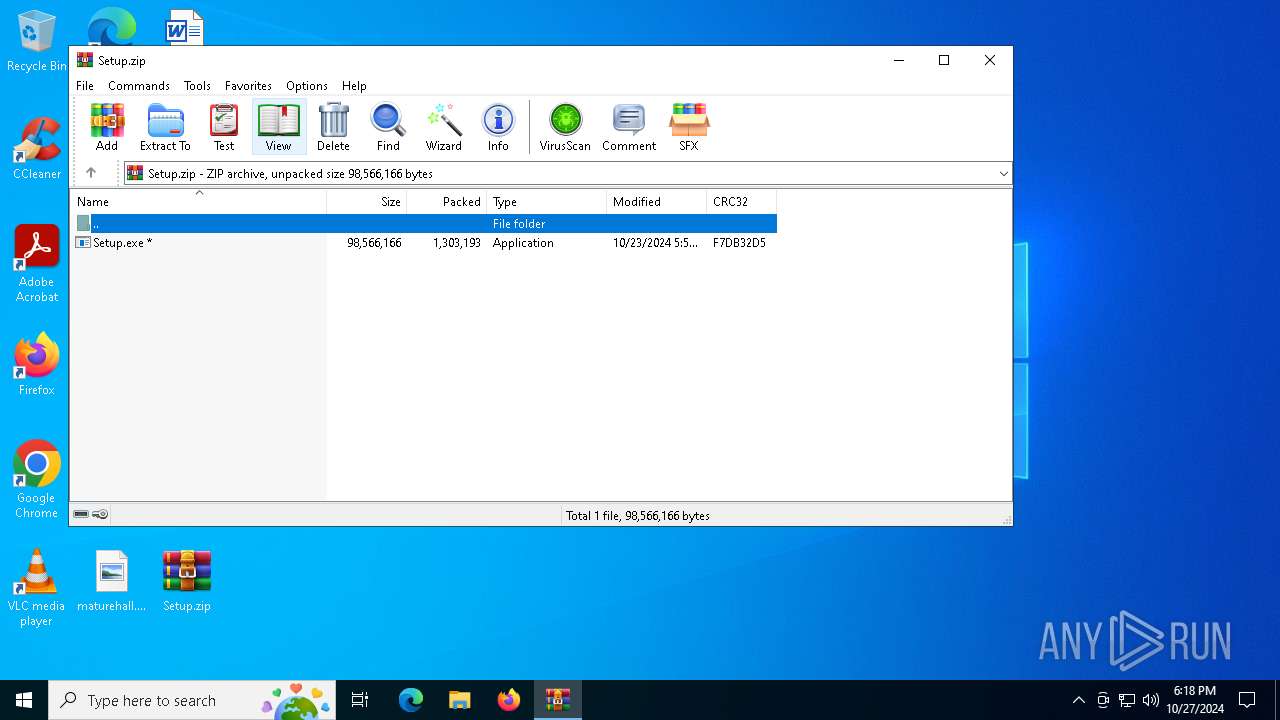
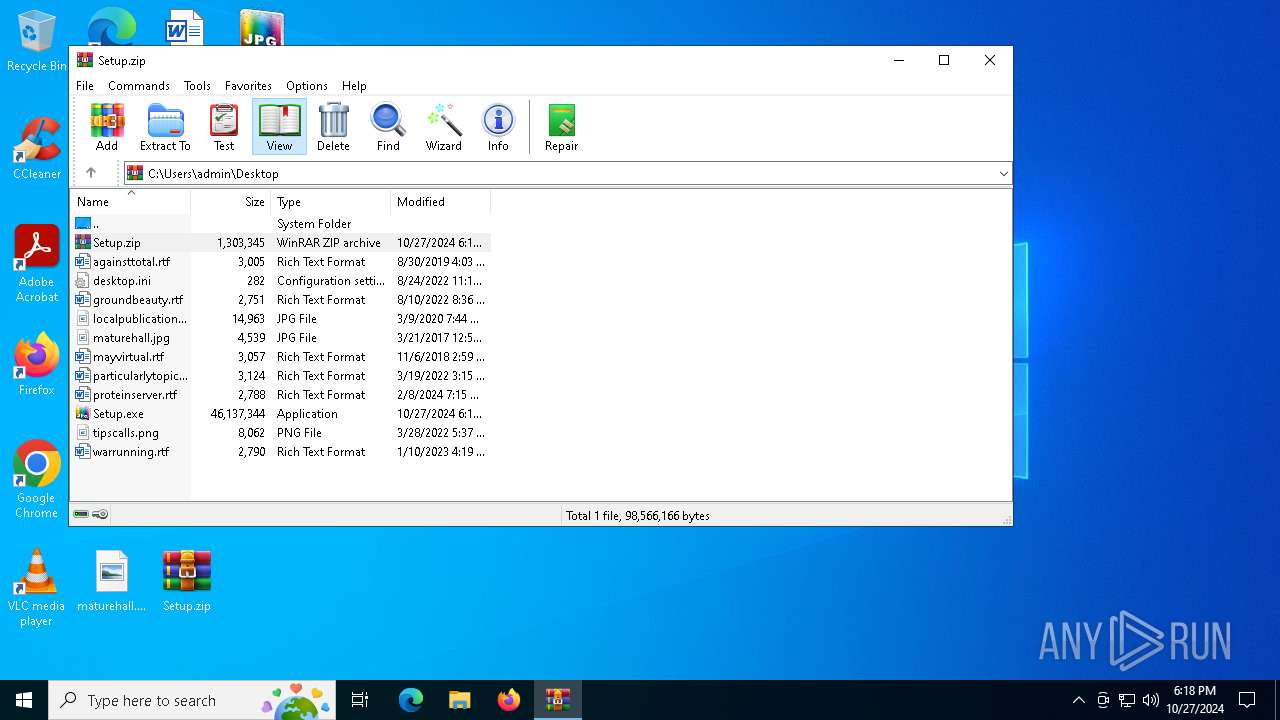
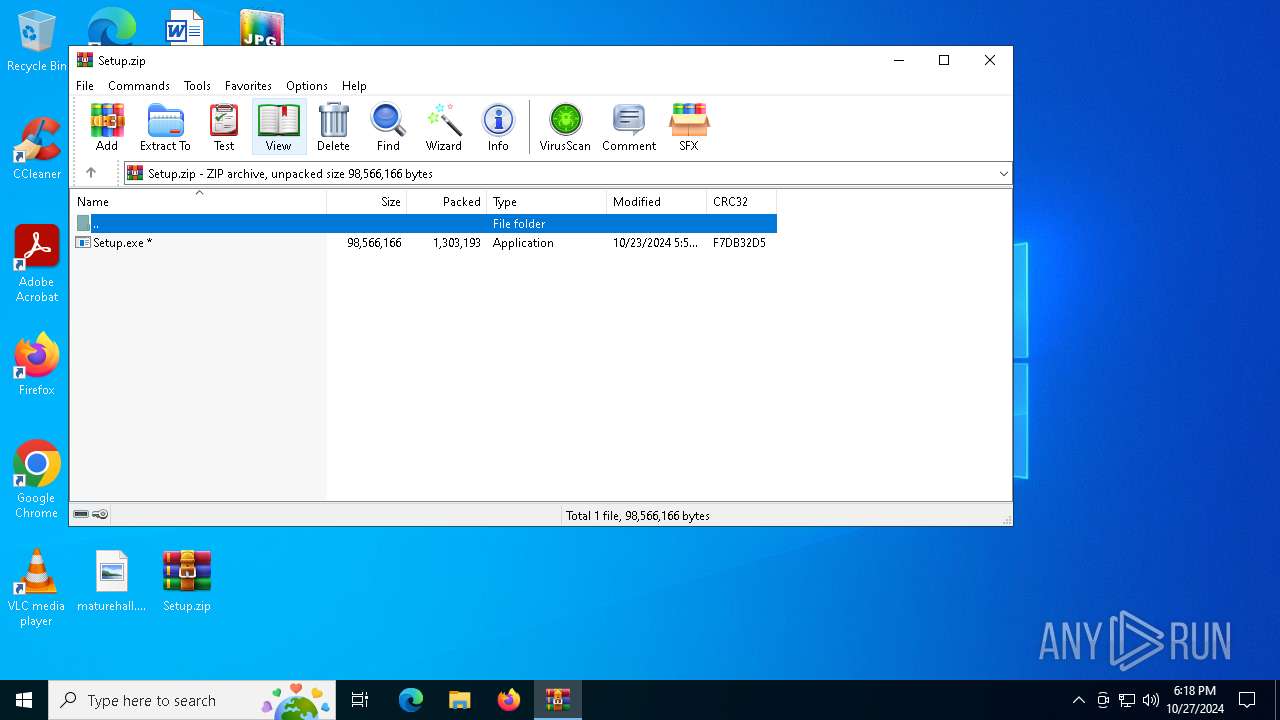
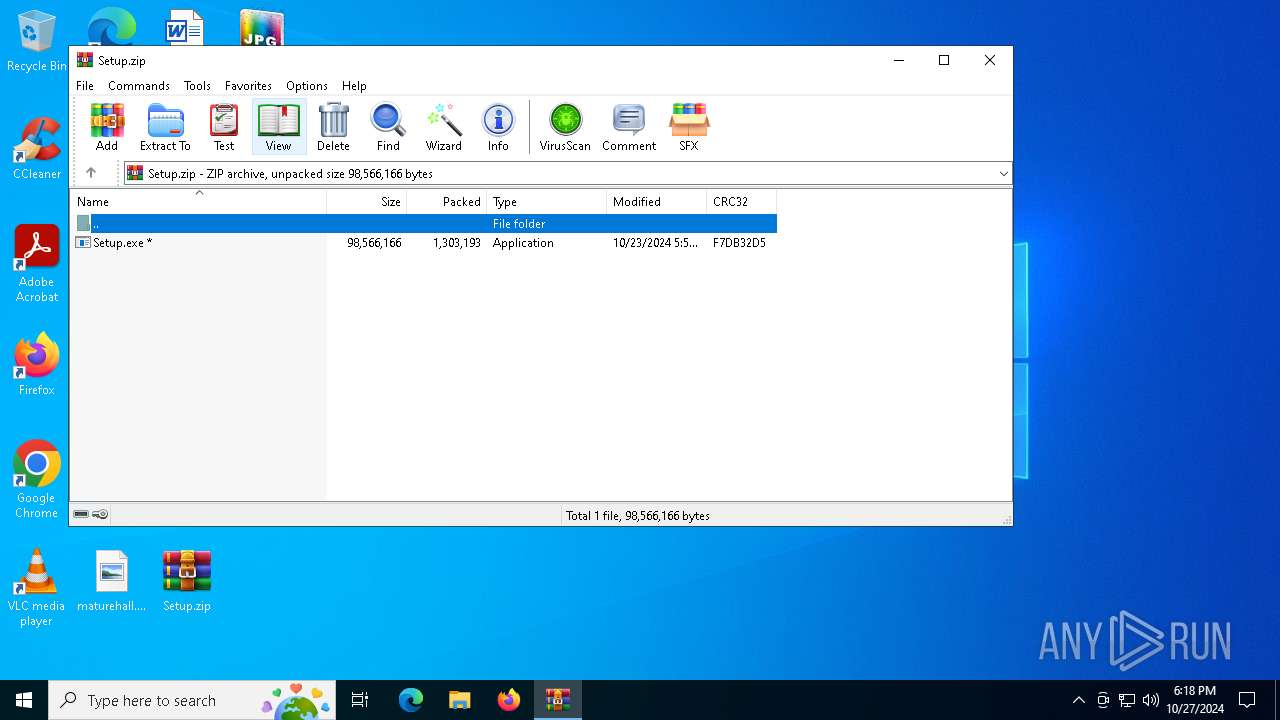
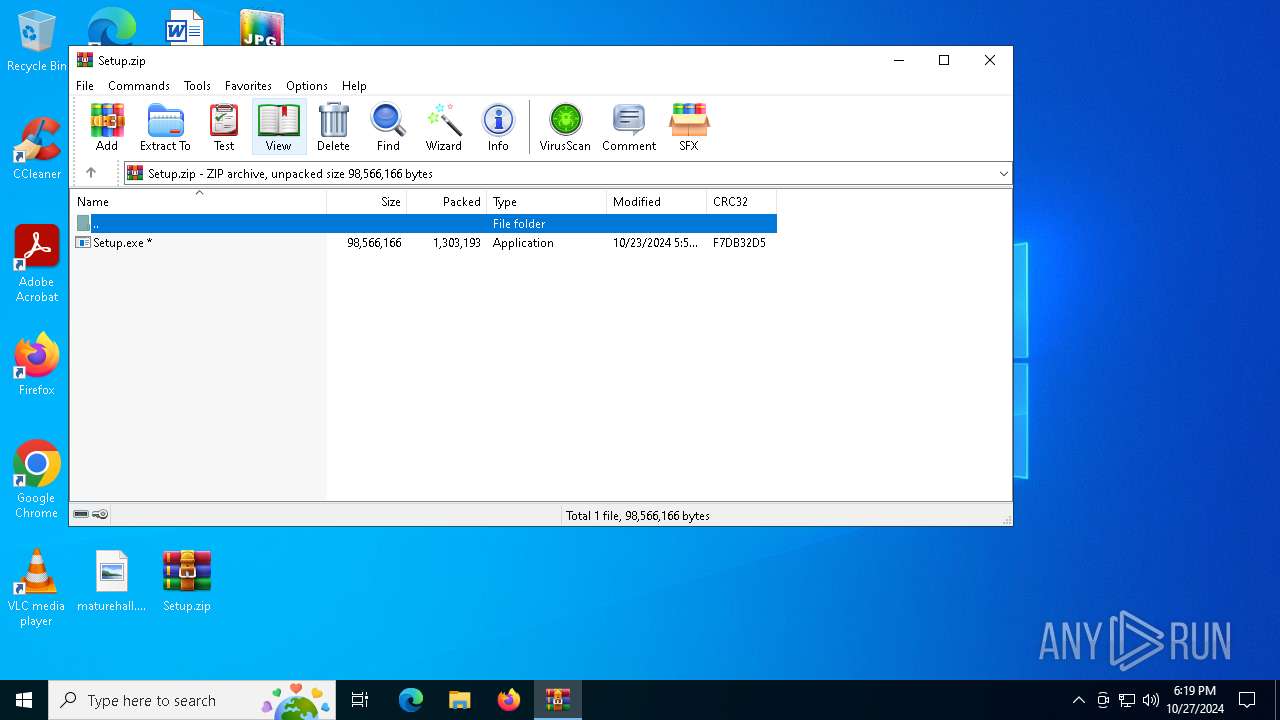
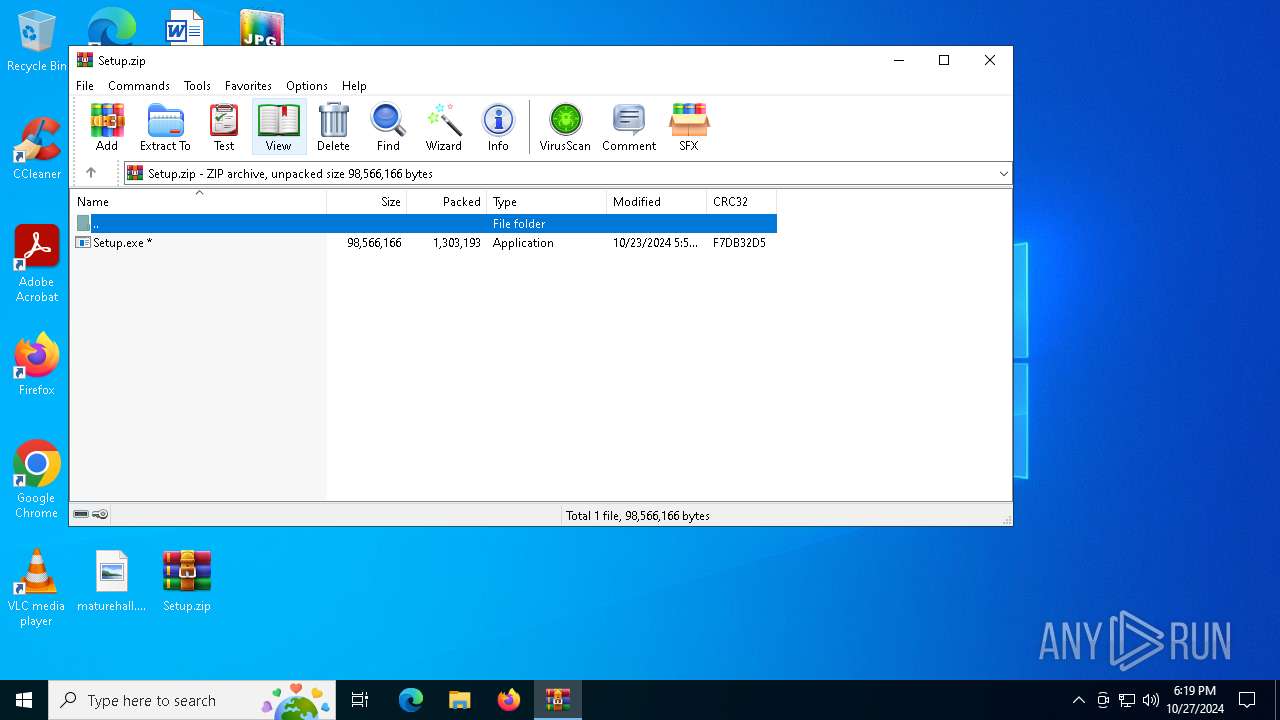
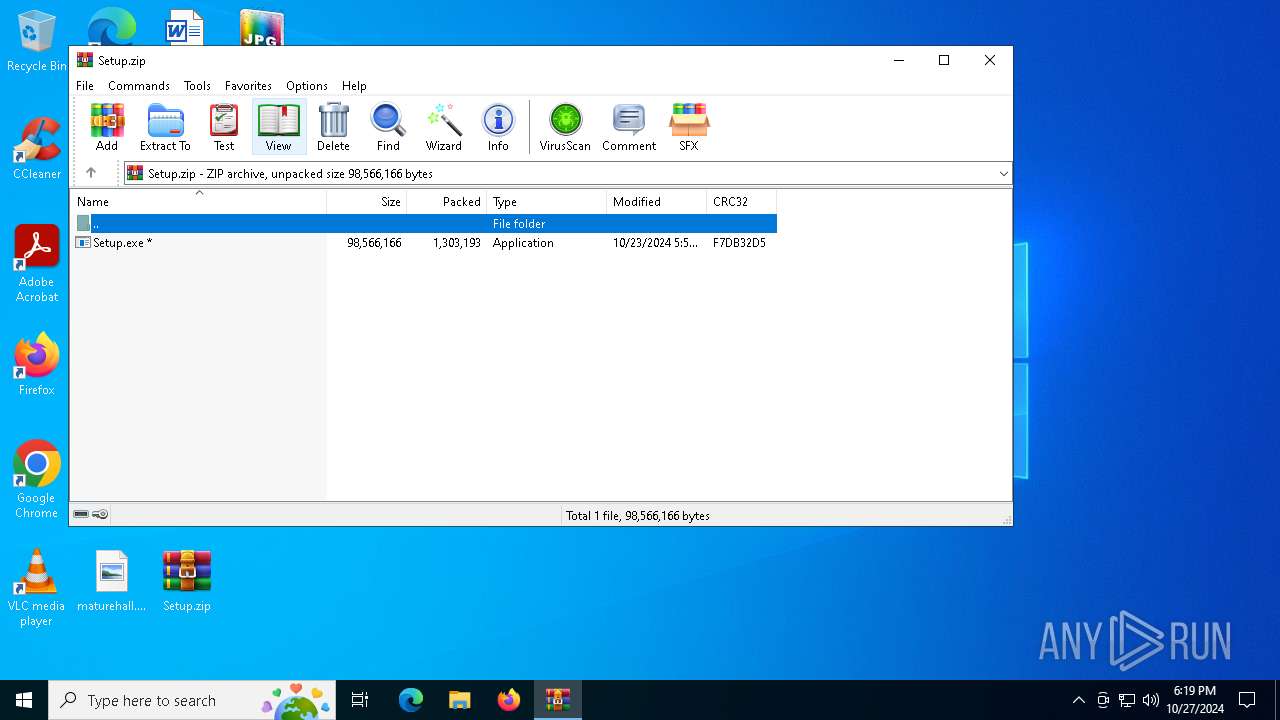
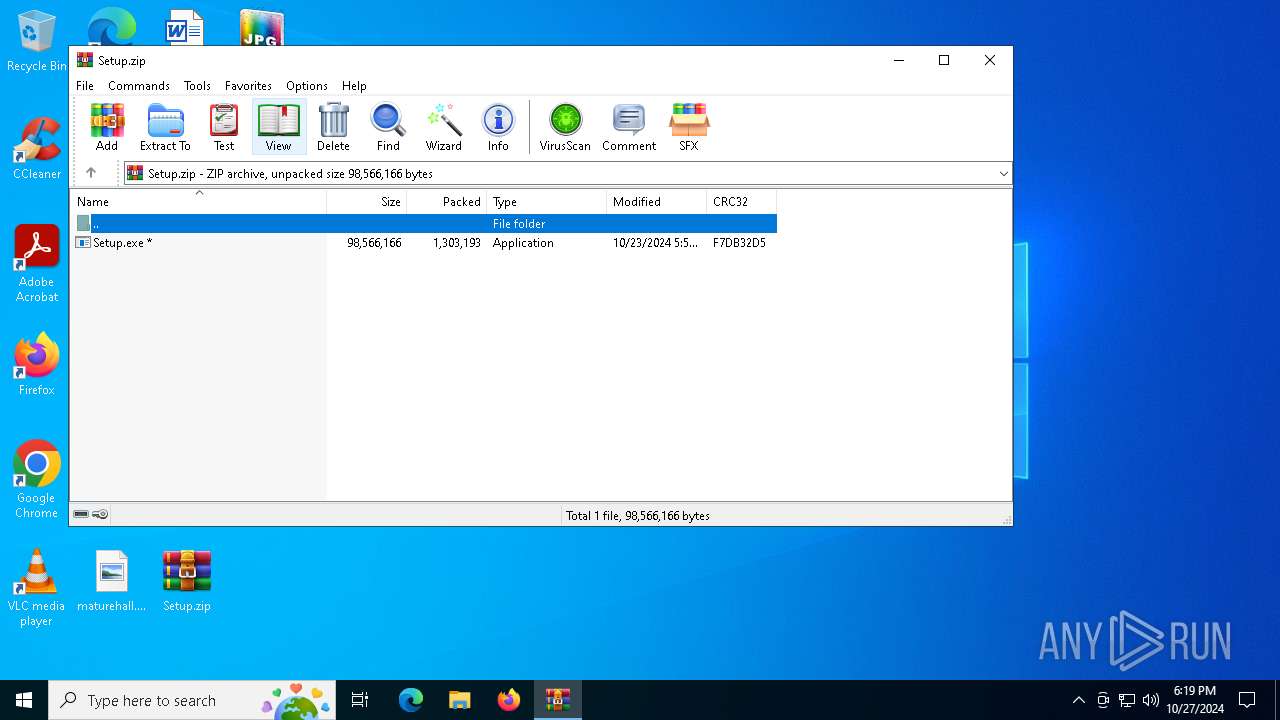
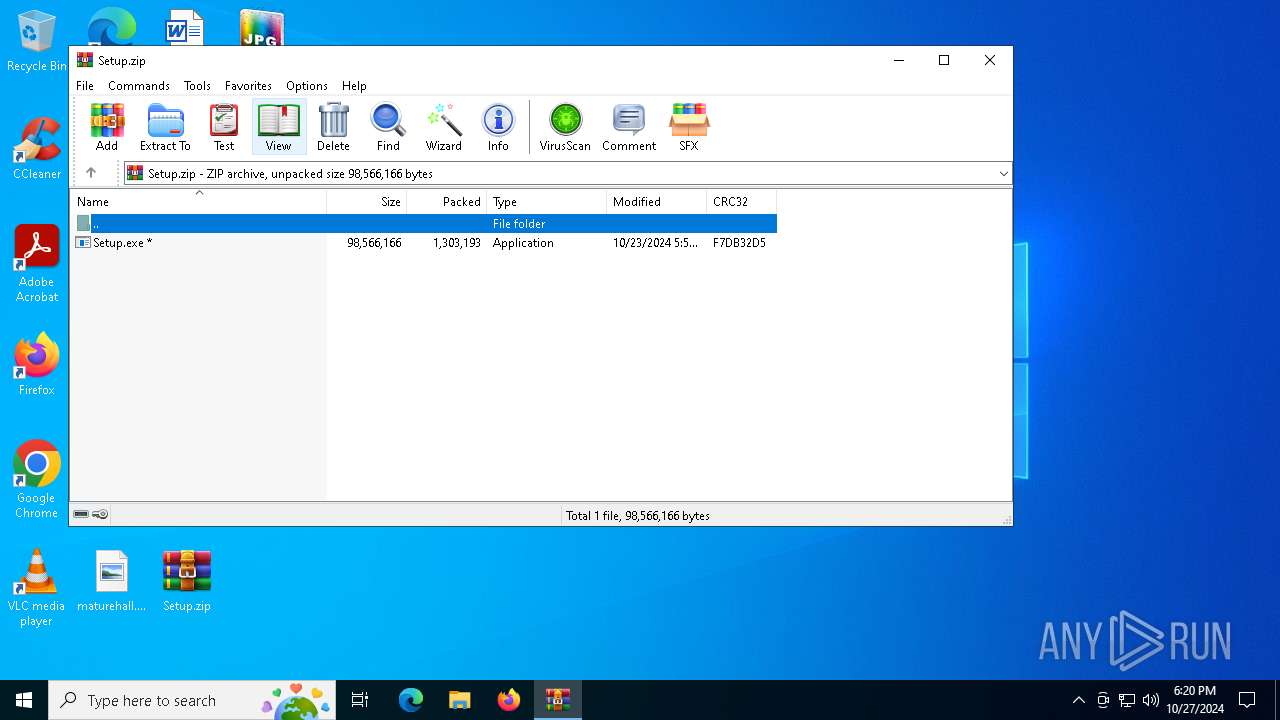
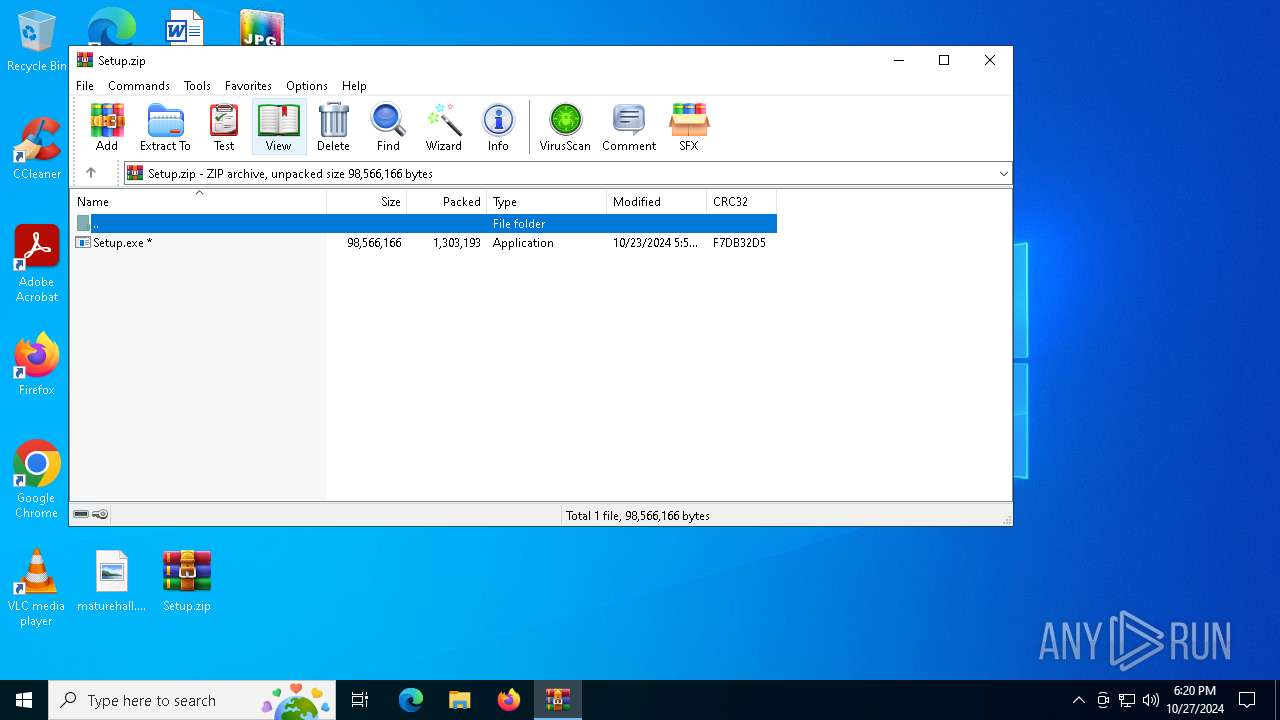
| File name: | Setup.zip |
| Full analysis: | https://app.any.run/tasks/70b8fd6f-6d00-48aa-b024-877b4263e9ee |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | October 27, 2024, 18:17:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 215B7C72D3C32AEF7D1A78077D1EE8CD |
| SHA1: | 2AC0D1871A5A0E8A2E28CFE6F175796D43D39776 |
| SHA256: | 014DFEB9502308DA26B56EFFC38B2A2BB74E1CAB9FE413AEE8E15ABB62B4CB4B |
| SSDEEP: | 49152:BF4rUJMREcEMiS3JDDHTmPJaI5/lGPIpSXXlK2/u+roA/D5YmceDIwrppZ7fS2v+:bKhR6MiC1PmhR/UXXI2/cwRrfZ7fSUWt |
MALICIOUS
AutoIt loader has been detected (YARA)
- Recommends.pif (PID: 6428)
LUMMA has been detected (SURICATA)
- Recommends.pif (PID: 6428)
- svchost.exe (PID: 2172)
Stealers network behavior
- svchost.exe (PID: 2172)
Connects to the CnC server
- svchost.exe (PID: 2172)
SUSPICIOUS
Reads security settings of Internet Explorer
- Setup.exe (PID: 1700)
Starts CMD.EXE for commands execution
- Setup.exe (PID: 1700)
- cmd.exe (PID: 2280)
Executing commands from a ".bat" file
- Setup.exe (PID: 1700)
Get information on the list of running processes
- cmd.exe (PID: 2280)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2280)
Application launched itself
- cmd.exe (PID: 2280)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 2280)
Starts application with an unusual extension
- cmd.exe (PID: 2280)
The executable file from the user directory is run by the CMD process
- Recommends.pif (PID: 6428)
Executable content was dropped or overwritten
- cmd.exe (PID: 2280)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2172)
- Recommends.pif (PID: 6428)
INFO
Checks supported languages
- Setup.exe (PID: 1700)
- Recommends.pif (PID: 6428)
Manual execution by a user
- Setup.exe (PID: 1700)
The process uses the downloaded file
- Setup.exe (PID: 1700)
Process checks computer location settings
- Setup.exe (PID: 1700)
Create files in a temporary directory
- Setup.exe (PID: 1700)
Reads the computer name
- Setup.exe (PID: 1700)
- Recommends.pif (PID: 6428)
Creates a new folder
- cmd.exe (PID: 6404)
Reads mouse settings
- Recommends.pif (PID: 6428)
Reads the machine GUID from the registry
- Recommends.pif (PID: 6428)
Reads the software policy settings
- Recommends.pif (PID: 6428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
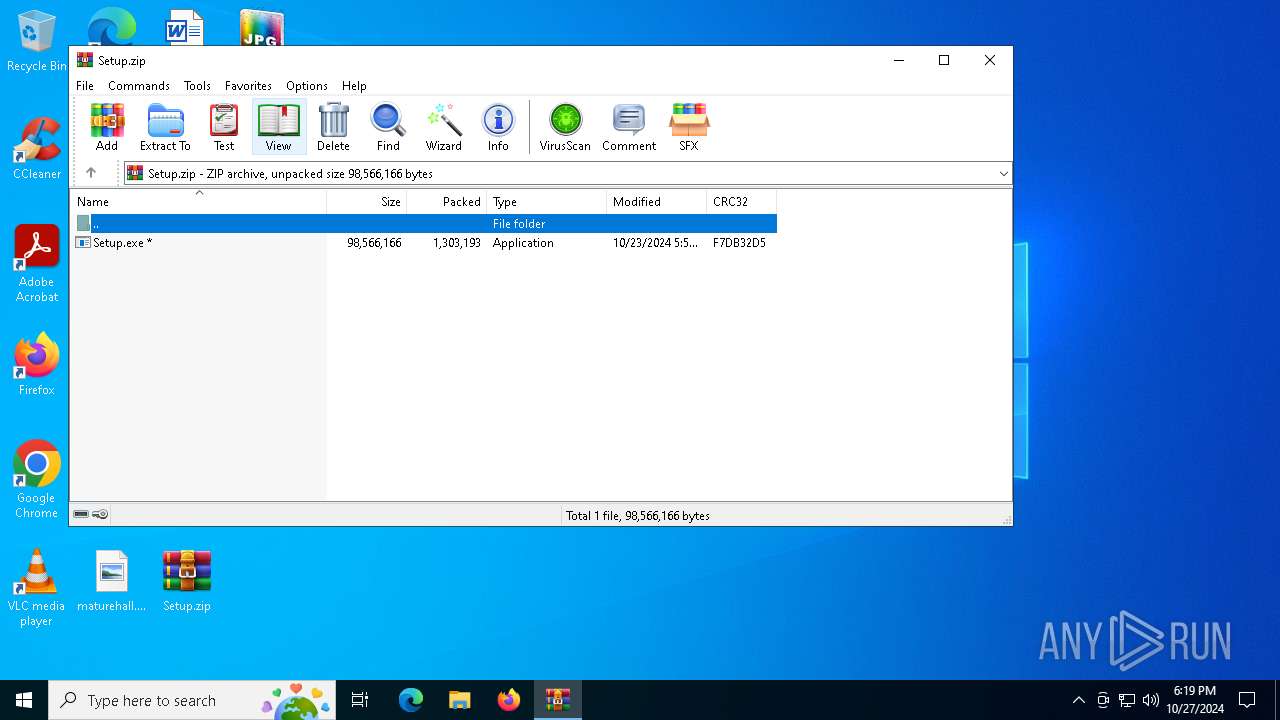
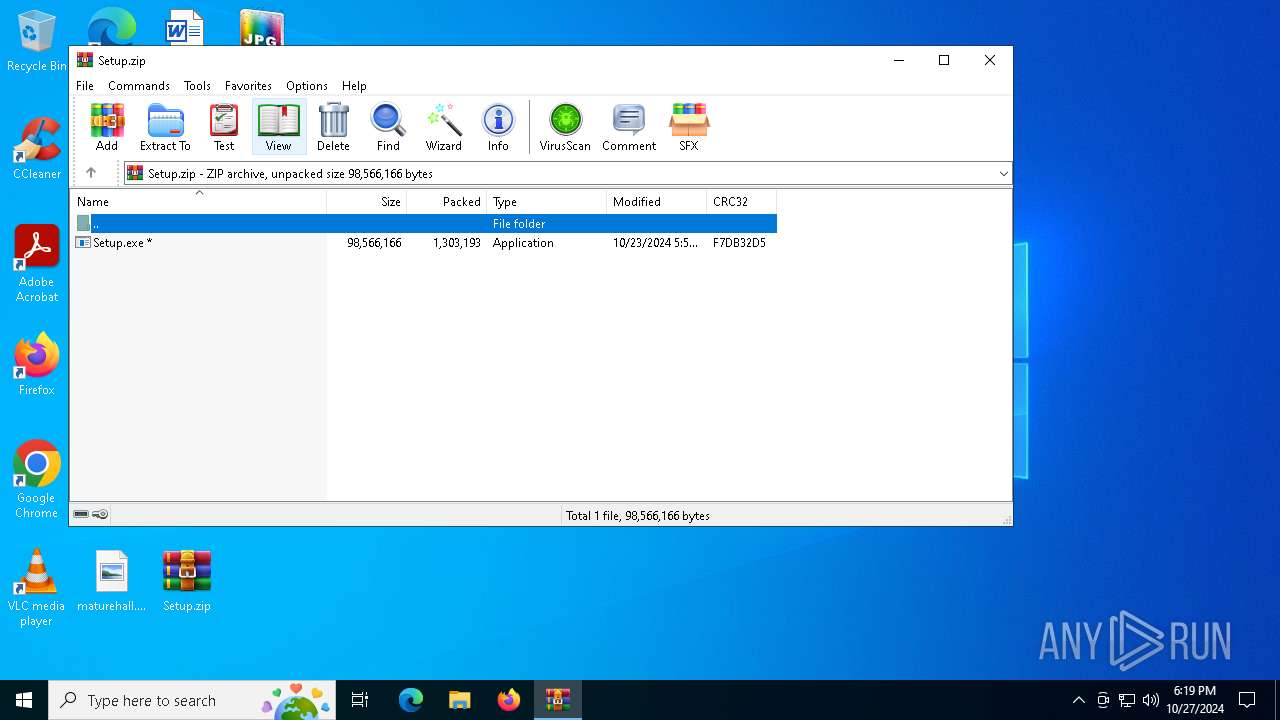
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:23 13:50:54 |
| ZipCRC: | 0xf7db32d5 |
| ZipCompressedSize: | 1303193 |
| ZipUncompressedSize: | 98566166 |
| ZipFileName: | Setup.exe |
Total processes
135
Monitored processes
14
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1700 | "C:\Users\admin\Desktop\Setup.exe" | C:\Users\admin\Desktop\Setup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1732 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Setup.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1952 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2280 | "C:\Windows\System32\cmd.exe" /c copy Map Map.bat & Map.bat | C:\Windows\SysWOW64\cmd.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4808 | findstr /V "supportcriminalarrivesemester" Replacement | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5644 | tasklist | C:\Windows\SysWOW64\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6000 | findstr /I "wrsa opssvc" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6404 | cmd /c md 261913 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 336
Read events
7 154
Write events
182
Delete events
0
Modification events
| (PID) Process: | (1732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (1732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
| (PID) Process: | (1732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | crc |
Value: 70 | |||
| (PID) Process: | (1732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Setup.zip | |||
| (PID) Process: | (1732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1732) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
10
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1700 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Highways | binary | |
MD5:C99BA88D2BE0781FA4B348A2E2F80642 | SHA256:51F9EFB8BDE05929DEAB3E6A46963BBEAEAB6D30653672946A9393559C8D2785 | |||
| 1700 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Peripherals | binary | |
MD5:604F1EE86C4D117D15AA86724AB68898 | SHA256:028832932063729F41EE6D533BE4AC6195E3DFE3C45104A08E1F4CDB4713CE06 | |||
| 1700 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Main | binary | |
MD5:7B25A06A892B856F6AE0667FF9870F08 | SHA256:A1E01FA4EA14D0261B192E7656D7534DB98CE561AFF6D14AFEA11ED27D444691 | |||
| 1700 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Touched | binary | |
MD5:07FE481307E21ADD30E1E749C6E081C7 | SHA256:2D7F598F9FD75985BD3EEFE7B315C7E06C8ACDE2A2FFEE9293A7F504FD800C39 | |||
| 6408 | cmd.exe | C:\Users\admin\AppData\Local\Temp\261913\J | binary | |
MD5:5F44447470F6D7A8EC0984E965F7D4AC | SHA256:6E5C369C3A6A1E4118E1CFEC616641DBF88A076DA00B4E2D62AAEE9FD8C3A908 | |||
| 1700 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Illustrations | binary | |
MD5:63831ED66E4EDE9181D24555E9DD1154 | SHA256:8D7C5187B6CEA37B5B81744F33C8A0A6396CEAB53E95669B281488D01636F28D | |||
| 2280 | cmd.exe | C:\Users\admin\AppData\Local\Temp\261913\Recommends.pif | executable | |
MD5:7C0949ADFFAC1D28CC48C595F37418F5 | SHA256:A20D86D97B0A5FAA71A90F9CB112CD6E13F087928E2D90D0729428E1938D9C55 | |||
| 1700 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Replacement | binary | |
MD5:C64ACCD95F739D788AFB67781FDAA029 | SHA256:51657A1CCC329F27E4CC1F1C8B51A62158AE1B1D83B301BB7ACC99EACDB29BD9 | |||
| 1700 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Dsc | binary | |
MD5:4D6FFF58A74564463493843F50E6B06C | SHA256:EE8D9565C3E316D843DB02520962CA1F1B88C0E07965D4A87ACF5B25722ED307 | |||
| 1700 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Map | text | |
MD5:CC67C6C323392DA95C55350B9BDAB845 | SHA256:CFC9F4434192C72208AA85CB8DEC73FD741BE7627E728E29C898B9EC052CCE71 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
31
DNS requests
19
Threats
36
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.67.133.187:443 | https://steamcommunity.com/profiles/76561199724331900 | unknown | html | 33.6 Kb | whitelisted |
— | — | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 188.114.97.9:443 | https://lossycristi.cyou/api | unknown | text | 17 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4292 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
816 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
cOGJPRGcAwTrnHZrKrIGUQaR.cOGJPRGcAwTrnHZrKrIGUQaR |
| unknown |
completedyu.cyou |
| malicious |
ostracizez.sbs |
| malicious |
strikebripm.sbs |
| malicious |
elaboretib.sbs |
| malicious |
definitib.sbs |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer CnC Host Checkin |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (ostracizez .sbs) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain (ostracizez .sbs) |
6428 | Recommends.pif | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (ostracizez .sbs in TLS SNI) |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer CnC Host Checkin |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (strikebripm .sbs) |
6428 | Recommends.pif | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (strikebripm .sbs in TLS SNI) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | STEALER [ANY.RUN] Suspected Lumma domain by CrossDomain (elaboretib .sbs) |
1 ETPRO signatures available at the full report