| File name: | key - Copy.exe |
| Full analysis: | https://app.any.run/tasks/ae0a581e-b86f-4513-a0e5-45f754d05549 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | November 18, 2023, 01:29:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 5C49C82CC68FC0D2497544F35188918E |
| SHA1: | 41FE99FD6E777660C5DD80B62B58D6677396C7A3 |
| SHA256: | 00ECBF0A7B18F828B59EFFC81BCAD06756C0B25E9D7F03831EFDF5A3CE382E6B |
| SSDEEP: | 49152:GBuaxMaawcI2r98/G3hs2ZS9AFaB6PEbdOxux6GhUmCItK51zXKaLMUW5E9TqrRm:GBZMecI2r98/G24Sp6PIO66G/W51zaez |
MALICIOUS
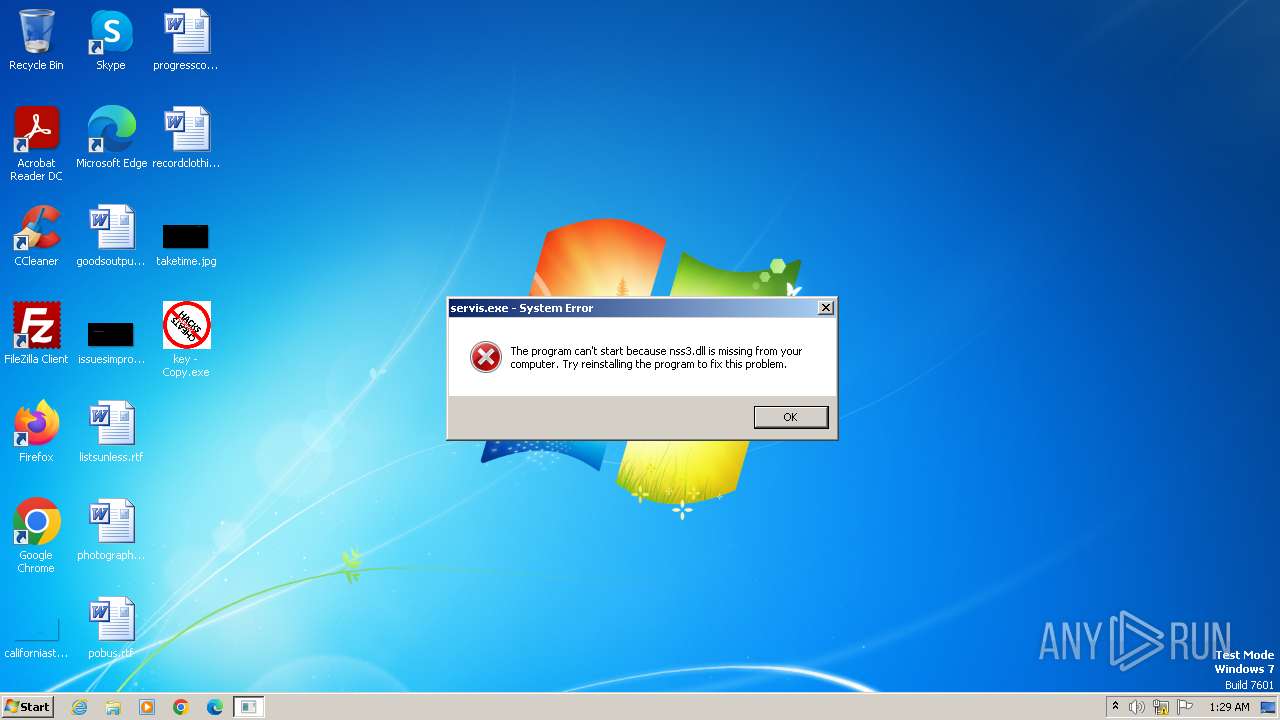
Drops the executable file immediately after the start
- key - Copy.exe (PID: 3128)
- key - Copy.exe (PID: 3540)
Changes appearance of the Explorer extensions
- AH.exe (PID: 3372)
Application was injected by another process
- explorer.exe (PID: 1388)
Runs injected code in another process
- key - Copy.exe (PID: 3540)
Actions looks like stealing of personal data
- vbc.exe (PID: 2116)
- vbc.exe (PID: 3740)
Uses NirSoft utilities to collect credentials
- vbc.exe (PID: 2116)
Steals credentials
- vbc.exe (PID: 2116)
Connects to the CnC server
- explorer.exe (PID: 3736)
REBHIP has been detected (SURICATA)
- explorer.exe (PID: 3736)
HAWKEYE has been detected (YARA)
- AH.exe (PID: 3372)
Steals credentials from Web Browsers
- vbc.exe (PID: 3740)
Accesses information about the status of the installed antivirus(Win32_AntivirusProduct) via WMI (SCRIPT)
- cscript.exe (PID: 664)
SUSPICIOUS
Application launched itself
- key - Copy.exe (PID: 3128)
- servis.exe (PID: 2068)
Reads the Internet Settings
- key - Copy.exe (PID: 3128)
- AH.exe (PID: 3372)
Loads DLL from Mozilla Firefox
- servis.exe (PID: 3788)
- vbc.exe (PID: 3740)
The process executes VB scripts
- AH.exe (PID: 3372)
- explorer.exe (PID: 3736)
Accesses Microsoft Outlook profiles
- vbc.exe (PID: 2116)
Connects to SMTP port
- AH.exe (PID: 3372)
Connects to unusual port
- explorer.exe (PID: 3736)
Reads settings of System Certificates
- AH.exe (PID: 3372)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 664)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 664)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 664)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 664)
INFO
Checks supported languages
- key - Copy.exe (PID: 3128)
- AH.exe (PID: 3372)
- key - Copy.exe (PID: 3540)
- servis.exe (PID: 2068)
- servis.exe (PID: 3788)
- vbc.exe (PID: 2116)
- wmpnscfg.exe (PID: 908)
- vbc.exe (PID: 3740)
Reads the machine GUID from the registry
- key - Copy.exe (PID: 3128)
- AH.exe (PID: 3372)
- vbc.exe (PID: 3740)
- wmpnscfg.exe (PID: 908)
Creates files or folders in the user directory
- key - Copy.exe (PID: 3128)
- AH.exe (PID: 3372)
- key - Copy.exe (PID: 3540)
- explorer.exe (PID: 3736)
Reads the computer name
- key - Copy.exe (PID: 3540)
- key - Copy.exe (PID: 3128)
- AH.exe (PID: 3372)
- servis.exe (PID: 3788)
- vbc.exe (PID: 2116)
- vbc.exe (PID: 3740)
- wmpnscfg.exe (PID: 908)
Reads Environment values
- AH.exe (PID: 3372)
Create files in a temporary directory
- key - Copy.exe (PID: 3540)
- explorer.exe (PID: 3736)
- vbc.exe (PID: 2116)
- vbc.exe (PID: 3740)
- cscript.exe (PID: 664)
Reads the Internet Settings
- explorer.exe (PID: 3736)
Manual execution by a user
- wmpnscfg.exe (PID: 908)
Reads security settings of Internet Explorer
- cscript.exe (PID: 664)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Hawkeye
(PID) Process(3372) AH.exe
encryptedemailstringmrkmarina@gmail.com
encryptedpassstringuqsnsajpzwlmwfjo
encryptedsmtpstringsmtp.gmail.com
portstring587
timerstring3600000
fakemgrstringThe application failed to initialize properly (0xc0000135)
encryptedftphostftp.host.com
encryptedftpuserusername
encryptedftppasspassword
encryptedphplinkhttp://www.DeceptiveEngineering.com/path/logs.php
useemailyesemail
useftpnoftp
usephpnophp
delaytime0
cleariedontclearie
clearffdontclearff
binderbindfiles
downloaderdownloadfiles
websitevisitorwebsitevisitor
websiteblockerwebsiteblocker
AdminRightsDisableAdminRights
notifyDisablenotify
DisableSSLDisableSSL
fakerrorDisablefakerror
startupDisablestartup
screenyDisablescreeny
clipDisableclip
TaskManagerDisableTaskManager
loggerDisablelogger
stealersstealers
meltDisablemelt
regDisablereg
cmdDisablecmd
misconfigDisablemsconfig
spreadersDisablespreaders
steamDisablesteam
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:11:14 02:15:31+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 1092608 |
| InitializedDataSize: | 202240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x10cbde |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 14.44.0.0 |
| ProductVersionNumber: | 14.44.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | jaje |
| FileVersion: | 14.44.00.00 |
| InternalName: | password.exe |
| LegalCopyright: | Copyright © 2014 |
| OriginalFileName: | password.exe |
| ProductName: | Properties |
| ProductVersion: | 14.44.00.00 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
46
Monitored processes
11
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Windows\system32\cscript.exe" "C:\Users\admin\AppData\Local\Temp\teste.vbs" | C:\Windows\System32\cscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 908 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1388 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2068 | "C:\Users\admin\AppData\Roaming\windows\servis.exe" | C:\Users\admin\AppData\Roaming\windows\servis.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: jaje Exit code: 0 Version: 14.44.00.00 Modules
| |||||||||||||||
| 2116 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holdermail.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | AH.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 Modules
| |||||||||||||||
| 3128 | "C:\Users\admin\Desktop\key - Copy.exe" | C:\Users\admin\Desktop\key - Copy.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: jaje Exit code: 0 Version: 14.44.00.00 Modules
| |||||||||||||||
| 3372 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\AH.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\AH.exe | key - Copy.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: turtle Exit code: 0 Version: 12.64.0.0 Modules
Hawkeye(PID) Process(3372) AH.exe encryptedemailstringmrkmarina@gmail.com encryptedpassstringuqsnsajpzwlmwfjo encryptedsmtpstringsmtp.gmail.com portstring587 timerstring3600000 fakemgrstringThe application failed to initialize properly (0xc0000135) encryptedftphostftp.host.com encryptedftpuserusername encryptedftppasspassword encryptedphplinkhttp://www.DeceptiveEngineering.com/path/logs.php useemailyesemail useftpnoftp usephpnophp delaytime0 cleariedontclearie clearffdontclearff binderbindfiles downloaderdownloadfiles websitevisitorwebsitevisitor websiteblockerwebsiteblocker AdminRightsDisableAdminRights notifyDisablenotify DisableSSLDisableSSL fakerrorDisablefakerror startupDisablestartup screenyDisablescreeny clipDisableclip TaskManagerDisableTaskManager loggerDisablelogger stealersstealers meltDisablemelt regDisablereg cmdDisablecmd misconfigDisablemsconfig spreadersDisablespreaders steamDisablesteam | |||||||||||||||
| 3540 | "C:\Users\admin\Desktop\key - Copy.exe" | C:\Users\admin\Desktop\key - Copy.exe | — | key - Copy.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: jaje Exit code: 0 Version: 14.44.00.00 Modules
| |||||||||||||||
| 3736 | explorer.exe | C:\Windows\explorer.exe | key - Copy.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3740 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holderwb.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | AH.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5483 Modules
| |||||||||||||||
Total events
7 460
Read events
7 360
Write events
94
Delete events
6
Modification events
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000F6D6788197A75D498472ACE88906AC8D000000000200000000001066000000010000200000007F0C5AFCF1AE7F71286A81A9B86E67A7BE47980777E154AD953E683E2064784E000000000E8000000002000020000000C547D0854BEA52CCDED7859B79990A863903B335001ED826D40C3D8E323F237F30000000DF0FBC24E15CFF4FE438F74D8486DFB808CBF3EC9160BD0CF16731298F2800053F0DC9D2737FB85ABF81EDB882A089A94000000011BAC043EAAF96F8497DEE93A36C7829C97427DA018BC7750377DAC2CC3CE4D64139784732F789D57202D54D80C3AAC2B4B5EE990B65AEF23416199647916AD4 | |||
| (PID) Process: | (3128) key - Copy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3128) key - Copy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3128) key - Copy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3128) key - Copy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1388) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\StartPage\NewShortcuts |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3372) AH.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | write | Name: | Hidden |
Value: 1 | |||
| (PID) Process: | (3736) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3736) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3736) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
2
Suspicious files
1
Text files
80
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3740 | vbc.exe | C:\Users\admin\AppData\Local\Temp\bhvA55D.tmp | — | |
MD5:— | SHA256:— | |||
| 3128 | key - Copy.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\AH.exe | executable | |
MD5:D3BD49DE915946A48E47B09F8015E767 | SHA256:DD397F41E5368C99B318B1BC1E5574743236F9D3950CC282287875E818722BD4 | |||
| 3540 | key - Copy.exe | C:\Users\admin\AppData\Local\Temp\admin2.txt | binary | |
MD5:4082F421A75E8D02457F5FCC4A676E94 | SHA256:0B7D1CEDFF49D02B56AABB748A07BDB10394550AC4A2D9BBAAE074D92AA7F620 | |||
| 3736 | explorer.exe | C:\Users\admin\AppData\Local\Temp\admin7 | text | |
MD5:CFFE4460B86BCA5CBD96AE5641F13AB3 | SHA256:32E6C109C59AD1C603AC280E8EF69C5F9A7FAAE1E997D20A4831557859CEE45E | |||
| 3372 | AH.exe | C:\Users\admin\AppData\Roaming\pid.txt | text | |
MD5:37D0B499FB84A552C17FCBB1442D7895 | SHA256:36684976BE1F529E6E2A32C9EDAB4CF8E364B2B916AE2CECA8893DB20C59AF9E | |||
| 2116 | vbc.exe | C:\Users\admin\AppData\Local\Temp\holdermail.txt | text | |
MD5:7FB9A9AD0FD9B1E0108ED71FBB276048 | SHA256:7D63C301317E144B0133A72250AE2D8E09AF65A92E6A807EC58A71939FE530A9 | |||
| 3372 | AH.exe | C:\Users\admin\AppData\Roaming\pidloc.txt | text | |
MD5:429C3A33830986CBB9CA3DAA0003AADA | SHA256:077D2813786D19092C98BE789FB6E7F8964BCA576256589D4B765AFCC5FC7C50 | |||
| 3736 | explorer.exe | C:\Users\admin\AppData\Local\Temp\admin8 | text | |
MD5:CFFE4460B86BCA5CBD96AE5641F13AB3 | SHA256:32E6C109C59AD1C603AC280E8EF69C5F9A7FAAE1E997D20A4831557859CEE45E | |||
| 3540 | key - Copy.exe | C:\Users\admin\AppData\Roaming\windows\servis.exe | executable | |
MD5:5C49C82CC68FC0D2497544F35188918E | SHA256:00ECBF0A7B18F828B59EFFC81BCAD06756C0B25E9D7F03831EFDF5A3CE382E6B | |||
| 664 | cscript.exe | C:\Users\admin\AppData\Local\Temp\teste.txt | text | |
MD5:81051BCC2CF1BEDF378224B0A93E2877 | SHA256:7EB70257593DA06F682A3DDDA54A9D260D4FC514F645237F5CA74B08F8DA61A6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
14
DNS requests
5
Threats
25
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3372 | AH.exe | GET | 301 | 104.16.154.36:80 | http://whatismyipaddress.com/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3372 | AH.exe | 104.16.154.36:80 | whatismyipaddress.com | CLOUDFLARENET | — | shared |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3372 | AH.exe | 104.16.154.36:443 | whatismyipaddress.com | CLOUDFLARENET | — | shared |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3736 | explorer.exe | 178.222.127.26:357 | 061.toh.info | TELEKOM SRBIJA a.d. | RS | unknown |
3372 | AH.exe | 74.125.71.108:587 | smtp.gmail.com | GOOGLE | US | whitelisted |
3736 | explorer.exe | 206.123.140.95:357 | maskulan.ddns.net | M247 Ltd | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
whatismyipaddress.com |
| shared |
061.toh.info |
| unknown |
smtp.gmail.com |
| shared |
maskulan.ddns.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3372 | AH.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |
3372 | AH.exe | Device Retrieving External IP Address Detected | ET POLICY Known External IP Lookup Service Domain in SNI |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.toh .info Domain |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.toh .info Domain |
1080 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.ddns .net |
3736 | explorer.exe | A Network Trojan was detected | ET MALWARE Cybergate/Rebhip/Spyrat Backdoor Keepalive |
3736 | explorer.exe | A Network Trojan was detected | ET MALWARE Cybergate/Rebhip/Spyrat Backdoor Keepalive Response |
3736 | explorer.exe | A Network Trojan was detected | ET MALWARE Cybergate/Rebhip/Spyrat Backdoor Keepalive |
3736 | explorer.exe | A Network Trojan was detected | ET MALWARE Cybergate/Rebhip/Spyrat Backdoor Keepalive Response |
3736 | explorer.exe | A Network Trojan was detected | ET MALWARE Cybergate/Rebhip/Spyrat Backdoor Keepalive |
14 ETPRO signatures available at the full report