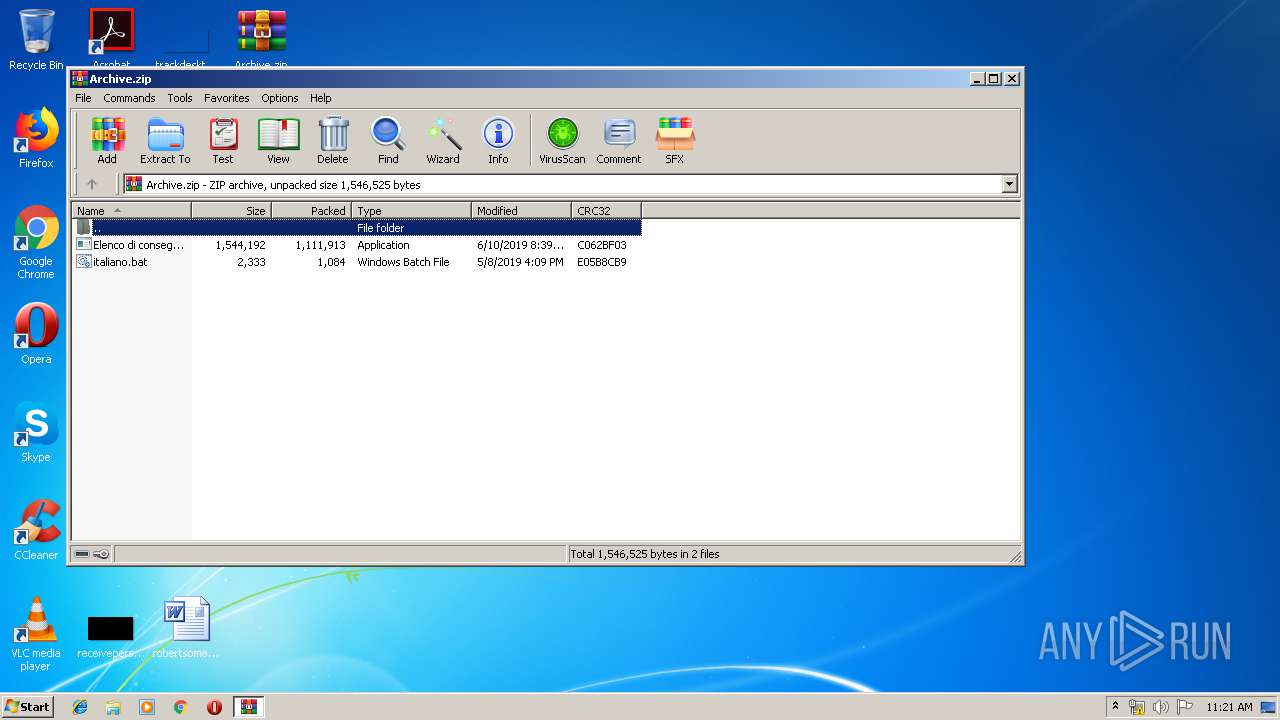
| File name: | Archive.zip |
| Full analysis: | https://app.any.run/tasks/9885c7fa-cdaf-4b90-9f22-94e6126b9a81 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | June 12, 2019, 10:20:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 200452397AF990878ED2E3B4E5482F4A |
| SHA1: | 9FA6EAEE5FB1A43C86EE30F335A546116CE70B72 |
| SHA256: | 00ADBA61B838079ACE134DE62D66612D7B571130CE853078D9C5771A2AB25516 |
| SSDEEP: | 24576:7LzT4OP5A2LaIZw7lh7MTekUez1S2trqTPeN7oeQI/L:rTi2LVYh7Mykxzlr2UoeQID |
MALICIOUS
Application was dropped or rewritten from another process
- Elenco di consegna merci di giugno.exe (PID: 2152)
Actions looks like stealing of personal data
- vbc.exe (PID: 3736)
- vbc.exe (PID: 2608)
Detected Hawkeye Keylogger
- RegAsm.exe (PID: 1720)
Stealing of credential data
- vbc.exe (PID: 2608)
- vbc.exe (PID: 3736)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1240)
Executes scripts
- RegAsm.exe (PID: 1720)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 3736)
INFO
Manual execution by user
- cmd.exe (PID: 2732)
- Elenco di consegna merci di giugno.exe (PID: 2152)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:06:10 21:39:21 |
| ZipCRC: | 0xc062bf03 |
| ZipCompressedSize: | 1111913 |
| ZipUncompressedSize: | 1544192 |
| ZipFileName: | Elenco di consegna merci di giugno.exe |
Total processes
49
Monitored processes
11
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1240 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Archive.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1680 | "C:\Windows\regedit.exe" /s "C:\Users\admin\AppData\Local\Temp\decoded" | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1720 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | Elenco di consegna merci di giugno.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 1812 | "C:\Windows\regedit.exe" /s "C:\Users\admin\AppData\Local\Temp\decoded" | C:\Windows\regedit.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2152 | "C:\Users\admin\Desktop\Elenco di consegna merci di giugno.exe" | C:\Users\admin\Desktop\Elenco di consegna merci di giugno.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2608 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe" /stext "C:\Users\admin\AppData\Local\Temp\tmpB9F3.tmp" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 2732 | cmd /c ""C:\Users\admin\Desktop\italiano.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2924 | regedit.exe /s "C:\Users\admin\AppData\Local\Temp\decoded" | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3152 | certutil /decode "C:\Users\admin\AppData\Local\Temp\b64" "C:\Users\admin\AppData\Local\Temp\decoded" | C:\Windows\system32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3616 | tzutil /s "W. Europe Standard Time" | C:\Windows\system32\tzutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Time Zone Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
474
Read events
392
Write events
82
Delete events
0
Modification events
| (PID) Process: | (1240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1240) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Archive.zip | |||
| (PID) Process: | (1240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1240) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (1240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
1
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1240 | WinRAR.exe | C:\Users\admin\Desktop\Elenco di consegna merci di giugno.exe | executable | |
MD5:— | SHA256:— | |||
| 2732 | cmd.exe | C:\Users\admin\AppData\Local\Temp\b64 | text | |
MD5:— | SHA256:— | |||
| 3152 | certutil.exe | C:\Users\admin\AppData\Local\Temp\decoded | text | |
MD5:— | SHA256:— | |||
| 3736 | vbc.exe | C:\Users\admin\AppData\Local\Temp\tmp8CF6.tmp | text | |
MD5:— | SHA256:— | |||
| 1240 | WinRAR.exe | C:\Users\admin\Desktop\italiano.bat | text | |
MD5:— | SHA256:— | |||
| 2608 | vbc.exe | C:\Users\admin\AppData\Local\Temp\tmpB9F3.tmp | text | |
MD5:7FB9A9AD0FD9B1E0108ED71FBB276048 | SHA256:7D63C301317E144B0133A72250AE2D8E09AF65A92E6A807EC58A71939FE530A9 | |||
| 1720 | RegAsm.exe | C:\Users\admin\AppData\Local\Temp\25291068-43af-3e16-50f6-5889d9ce7904 | text | |
MD5:454353131947D1483FF5470107478978 | SHA256:2DF94DC1C58E952A1EBD1AE1185A291A8A573982CA90EC1BBB87B81126002668 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1720 | RegAsm.exe | GET | 200 | 66.171.248.178:80 | http://bot.whatismyipaddress.com/ | US | text | 13 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1720 | RegAsm.exe | 66.171.248.178:80 | bot.whatismyipaddress.com | Alchemy Communications, Inc. | US | malicious |
— | — | 79.124.76.85:30905 | ftp.tiffanyhomestudio.com | NetInfo.BG JSCo | BG | malicious |
1720 | RegAsm.exe | 79.124.76.85:21 | ftp.tiffanyhomestudio.com | NetInfo.BG JSCo | BG | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bot.whatismyipaddress.com |
| shared |
ftp.tiffanyhomestudio.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1720 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Spy.HawkEye IP Check |
1720 | RegAsm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Spyware.HawkEyeKeyLogger Exfiltration over FTP |
1720 | RegAsm.exe | A Network Trojan was detected | ET TROJAN HawkEye Keylogger FTP |
2 ETPRO signatures available at the full report