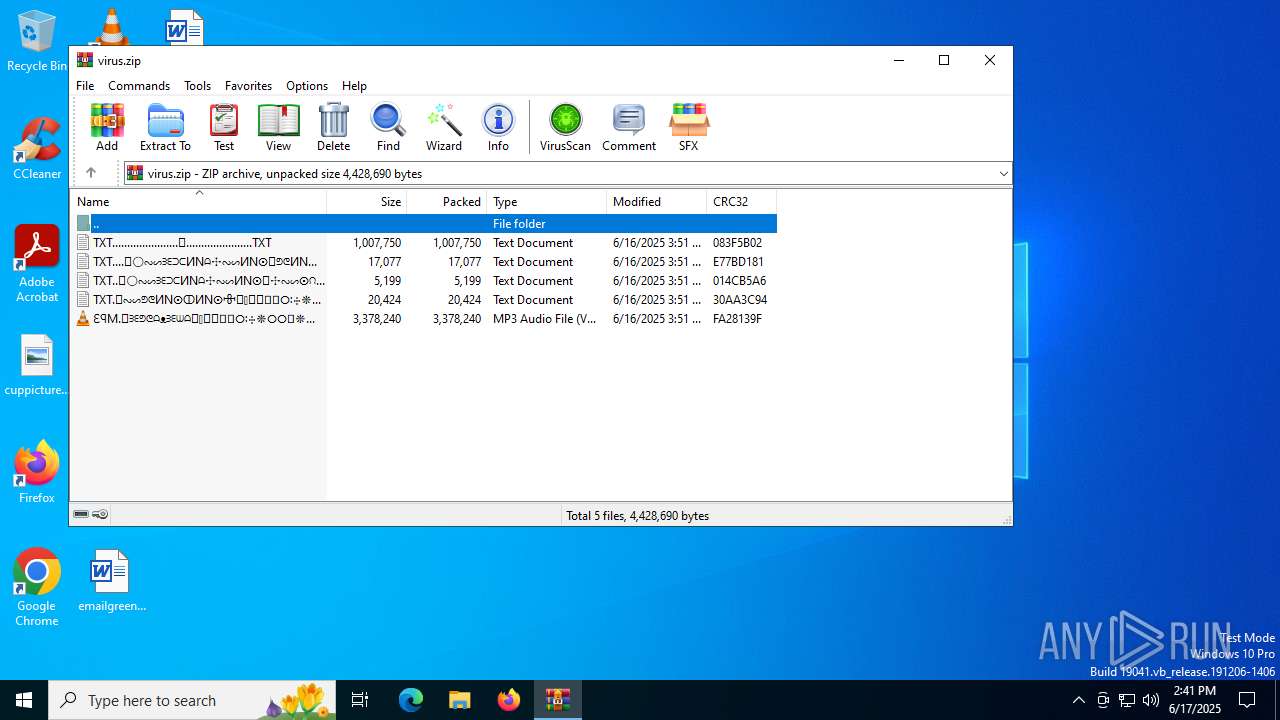
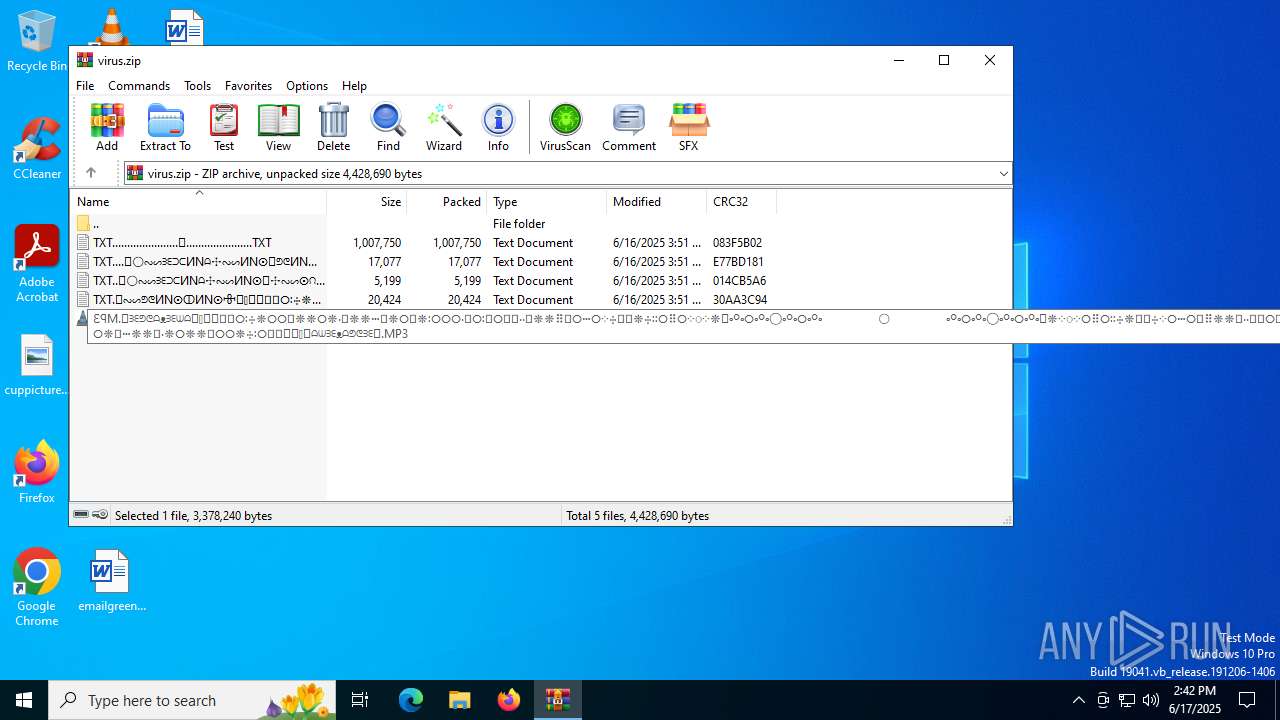
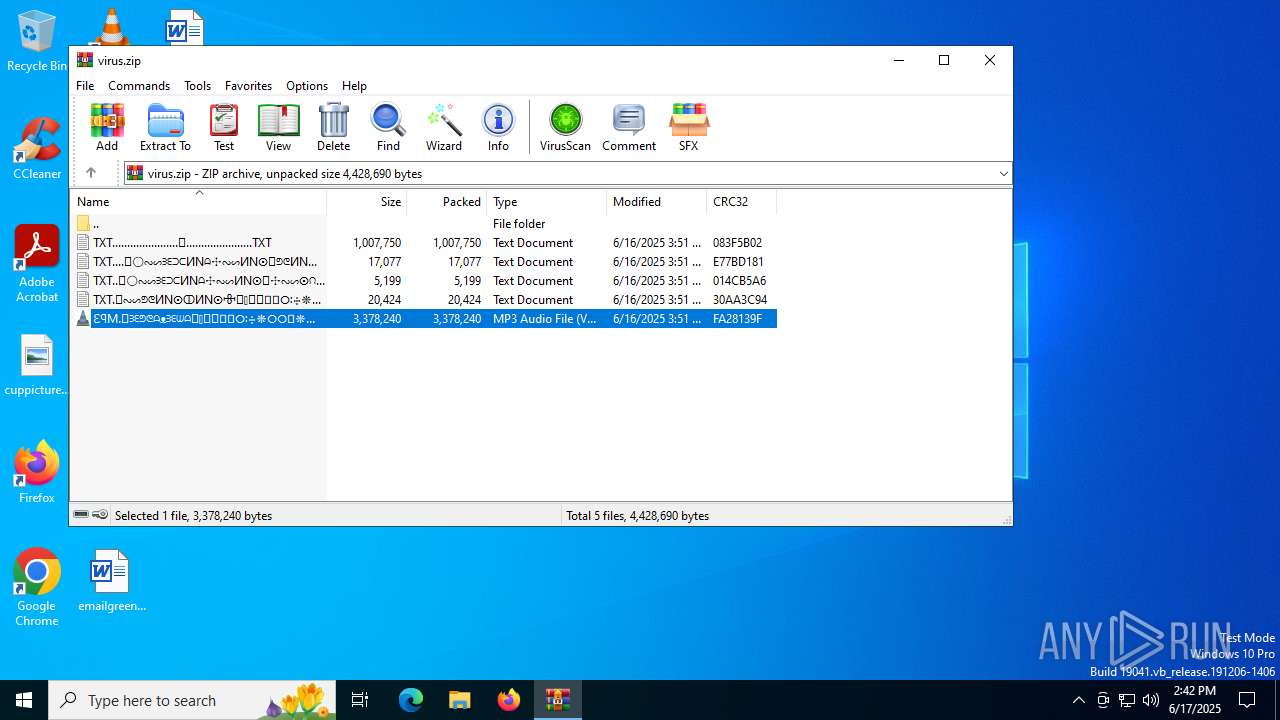
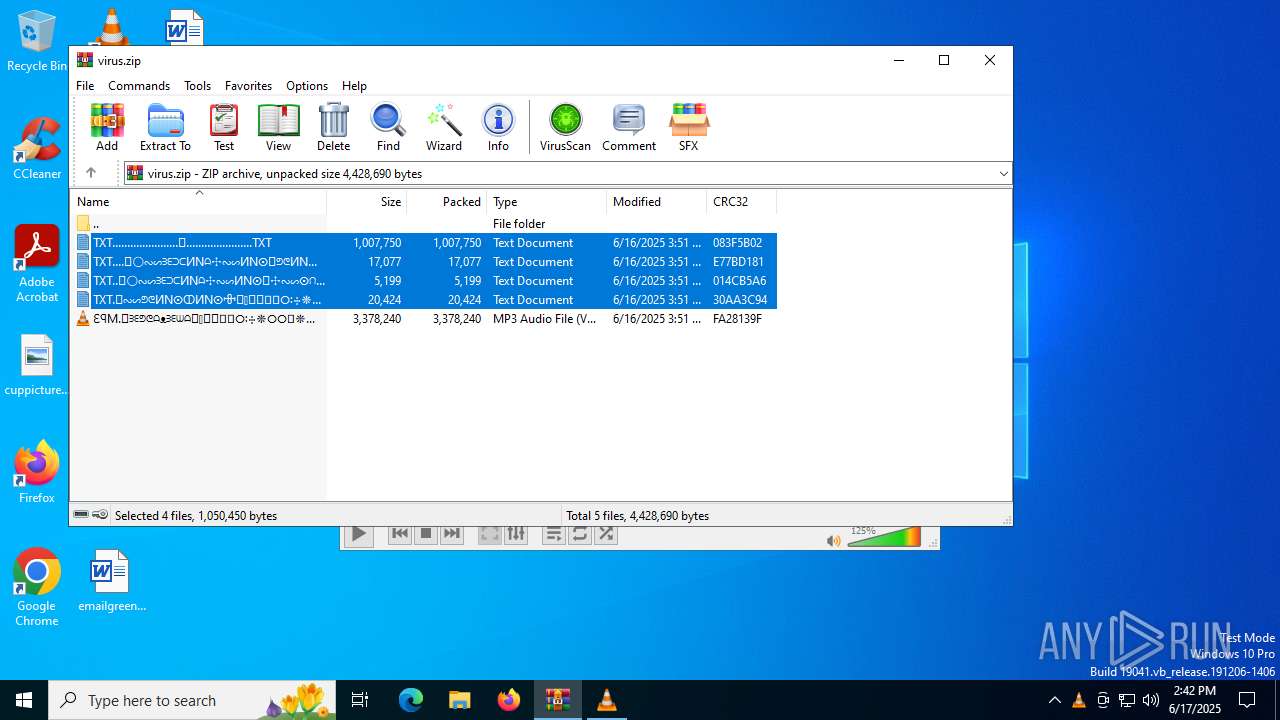
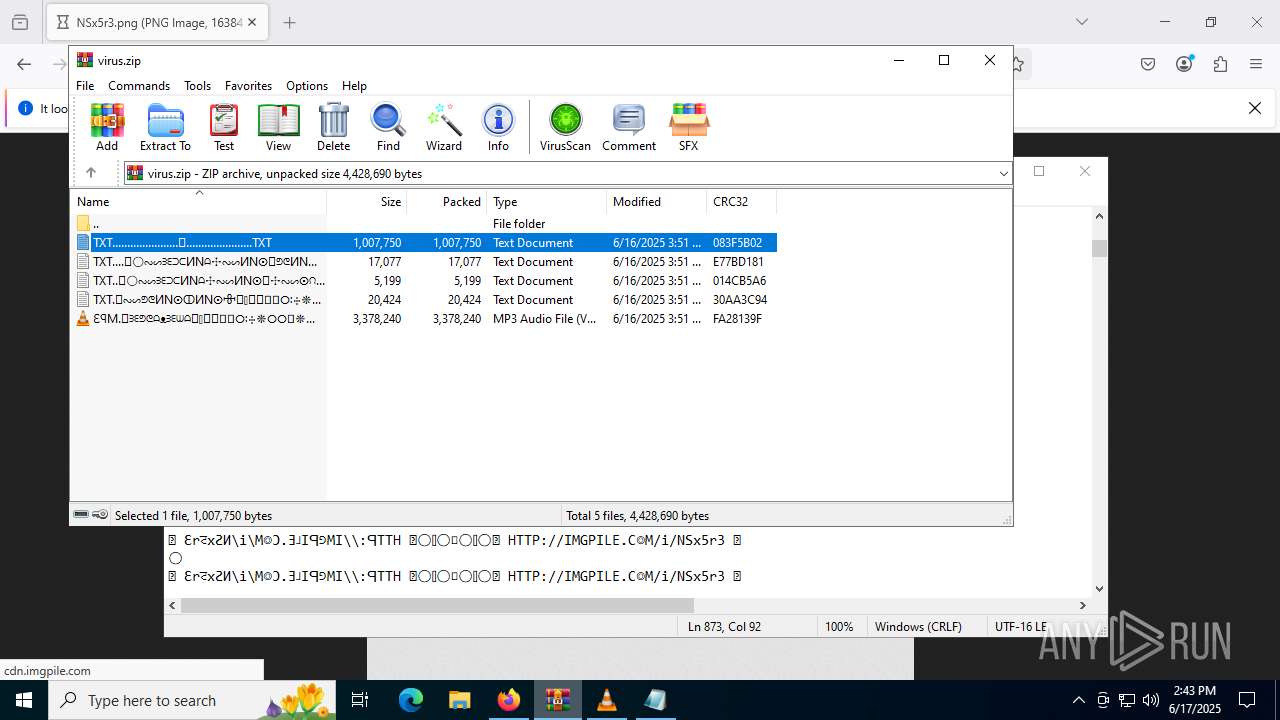
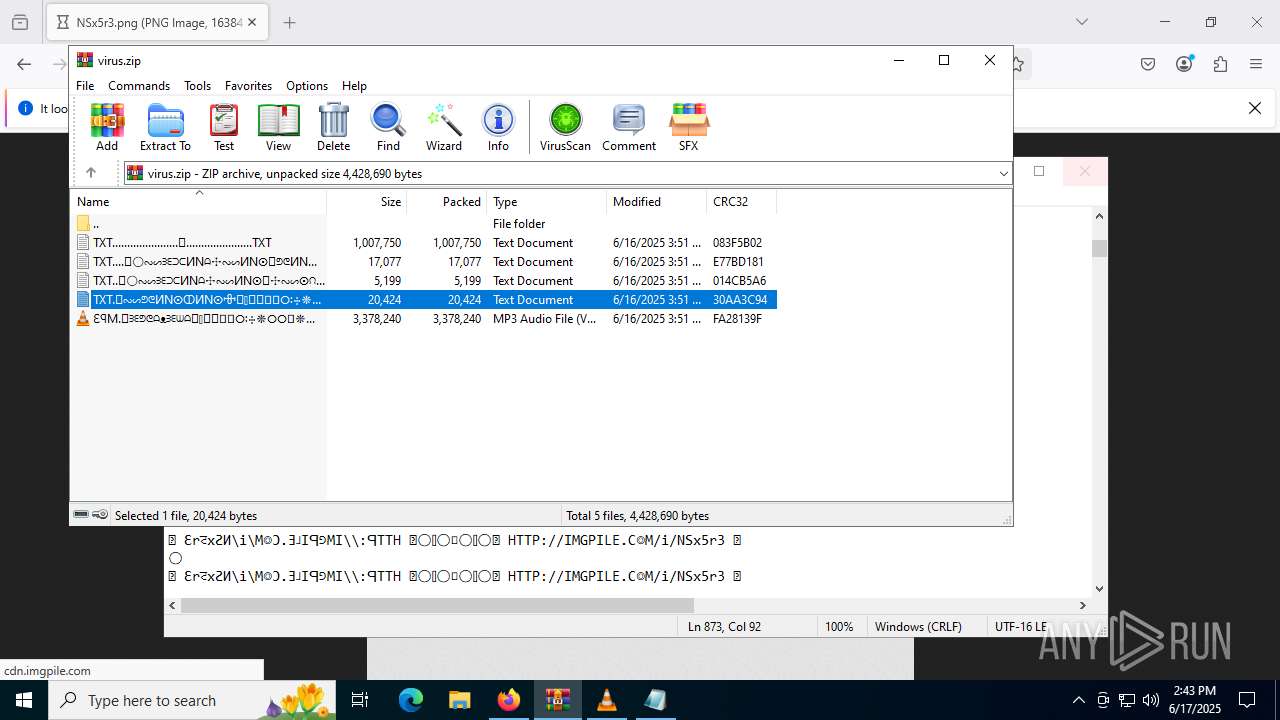
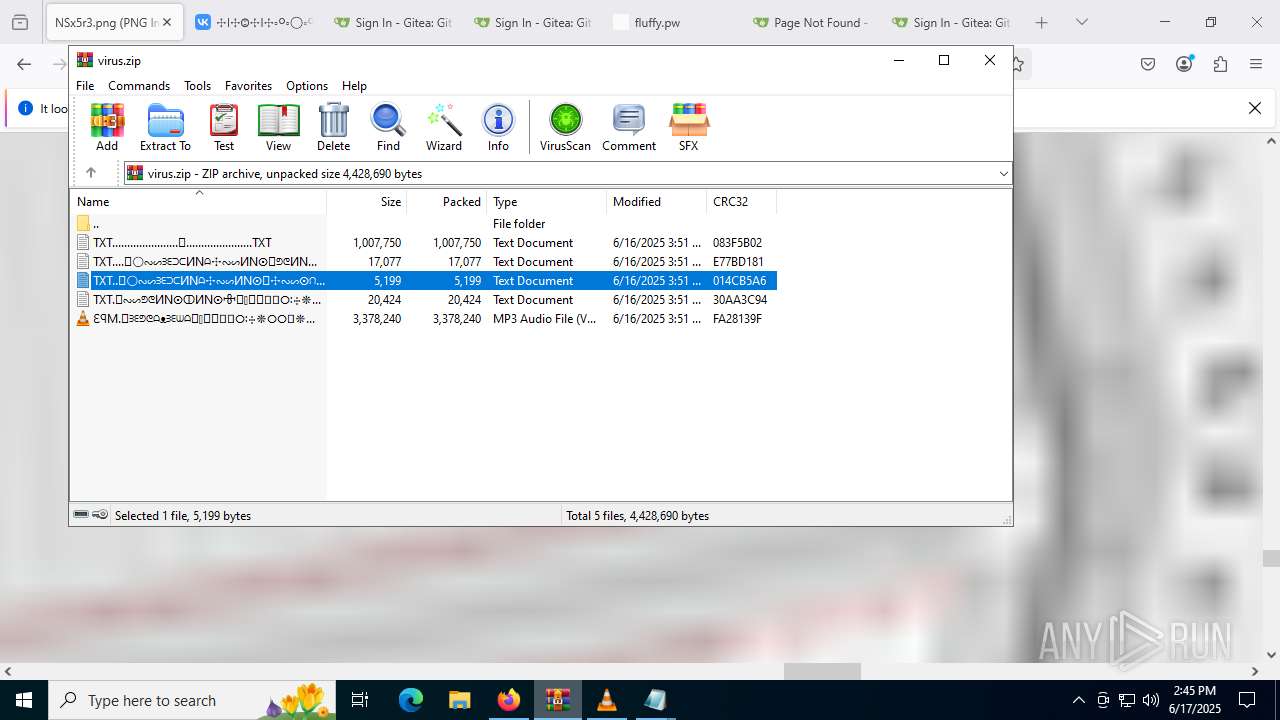
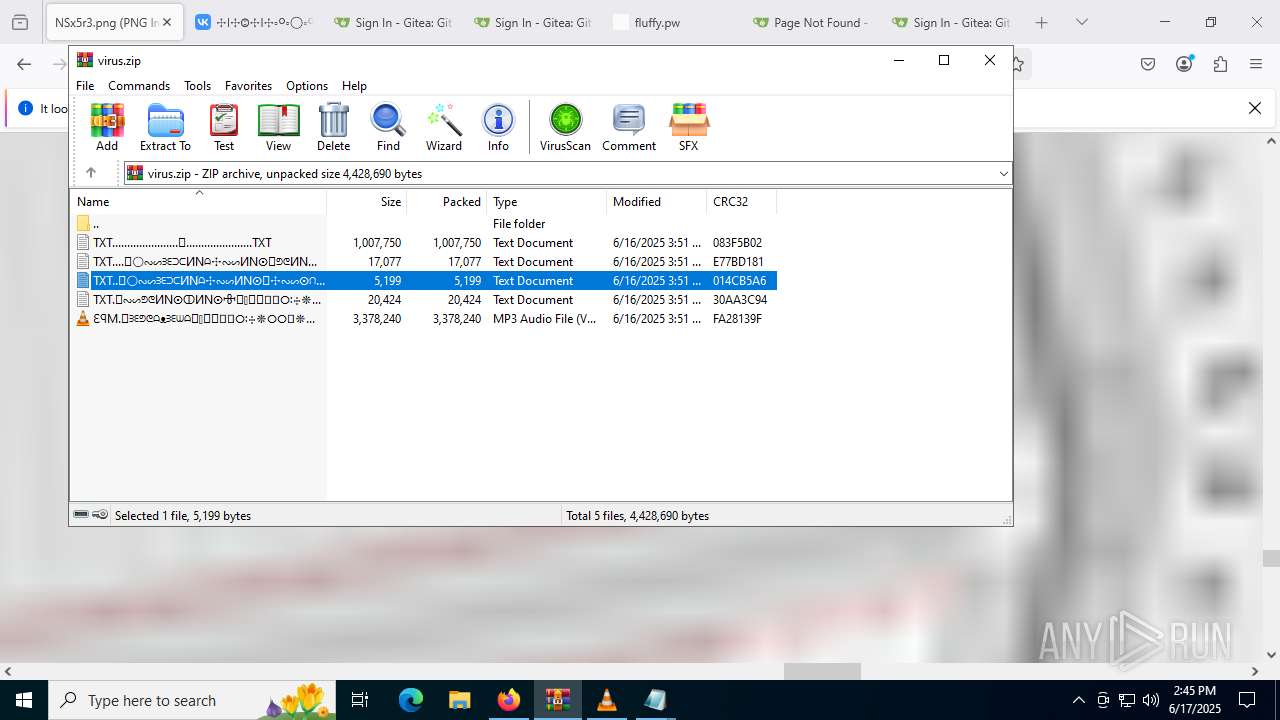
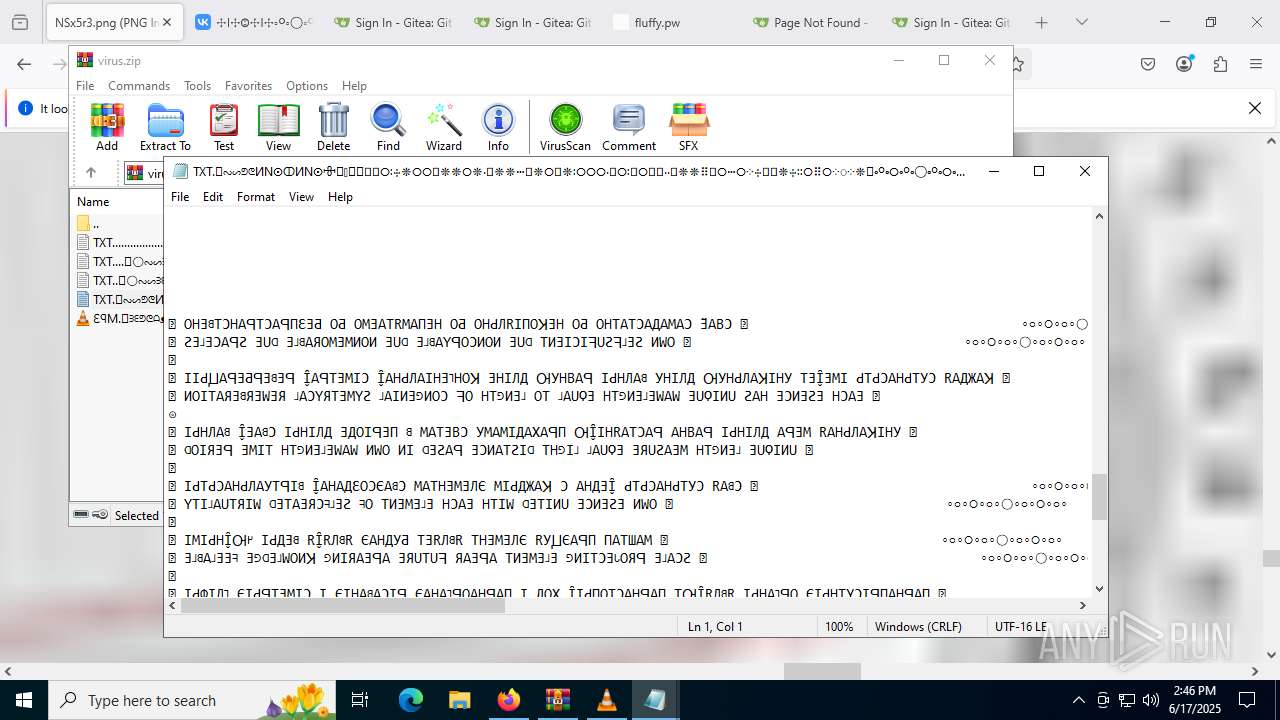
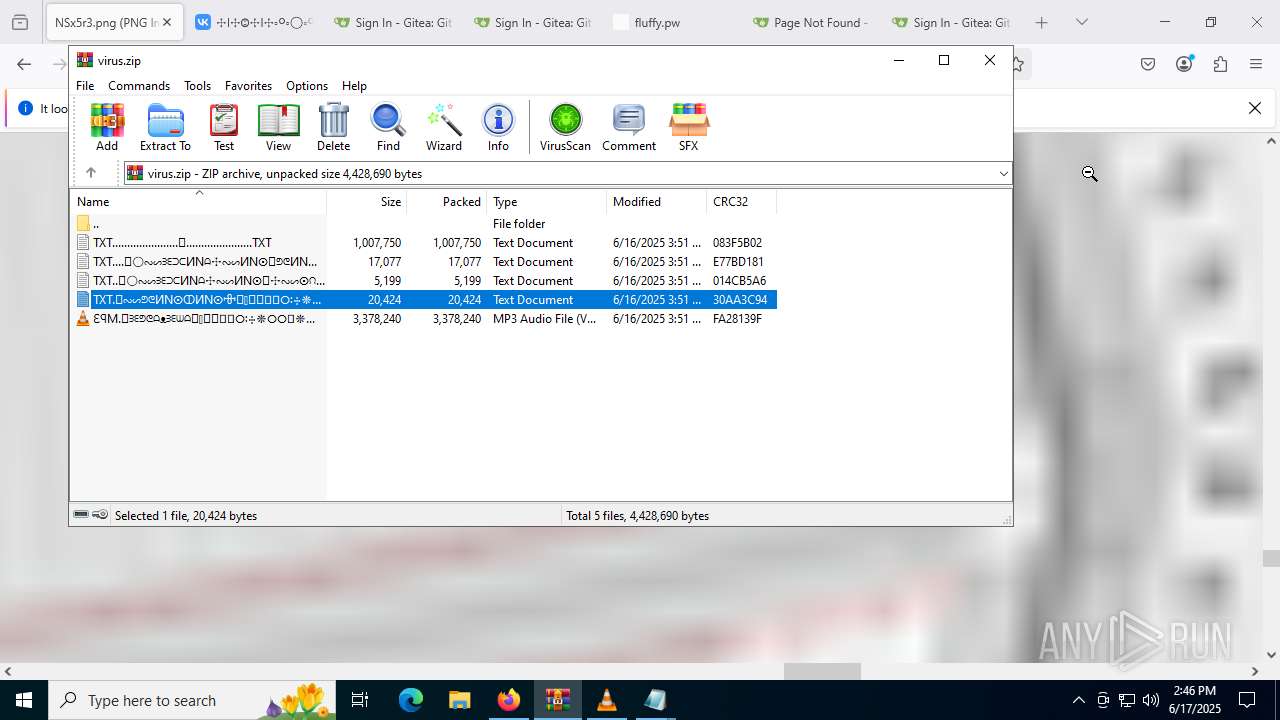
| File name: | virus.zip |
| Full analysis: | https://app.any.run/tasks/59d0bfb5-2b39-46c4-8a80-a2b3dbb77b55 |
| Verdict: | Malicious activity |
| Analysis date: | June 17, 2025, 14:41:45 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 1CC3DE5D0CF0AF0EC8EC159AD0FEDD2D |
| SHA1: | 79E41BF5BCED415804D5FFA853DBC8D232537B59 |
| SHA256: | 8E39B32C4FD875B9401ED04927F58861D83EF16F15068C7007693AAC0FD9BCEC |
| SSDEEP: | 98304:l8a1JsAVEYp4syoqVh/bKuG/+BGgPo8cVaQfR1vEQUChxwZt6yqJ3BsXrz:7g |
MALICIOUS
No malicious indicators.SUSPICIOUS
There is functionality for taking screenshot (YARA)
- vlc.exe (PID: 2368)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4676)
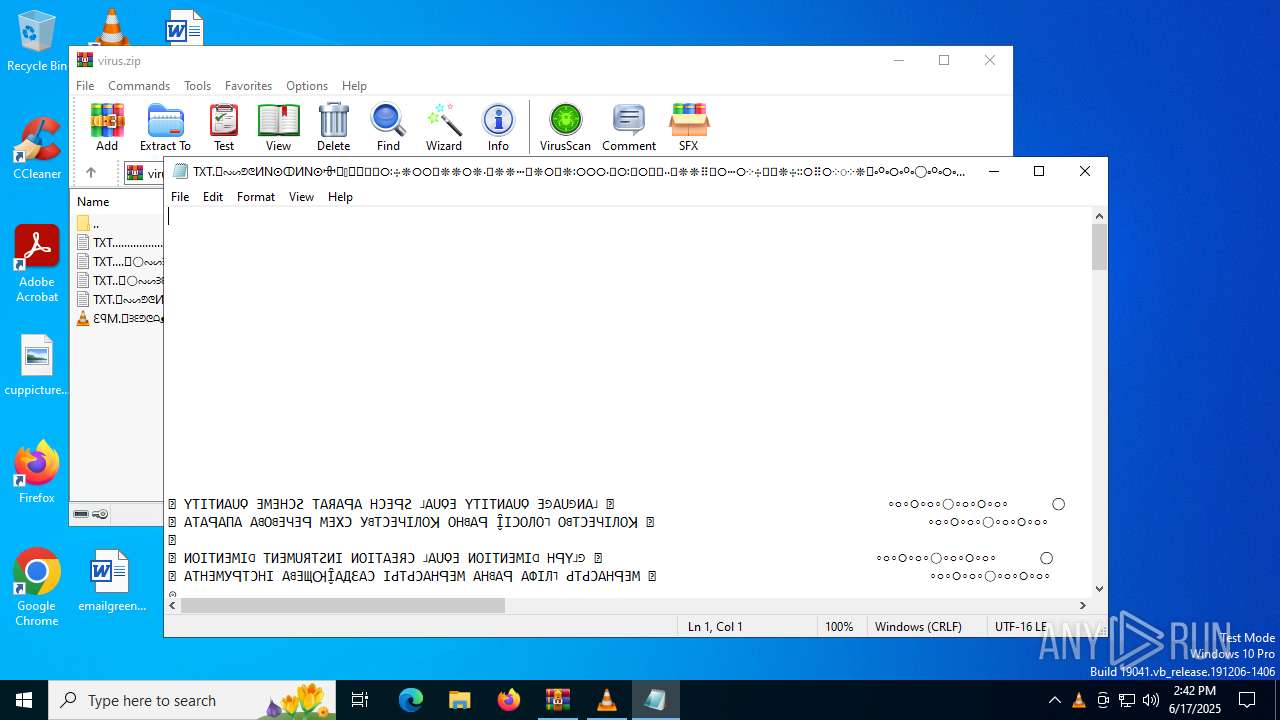
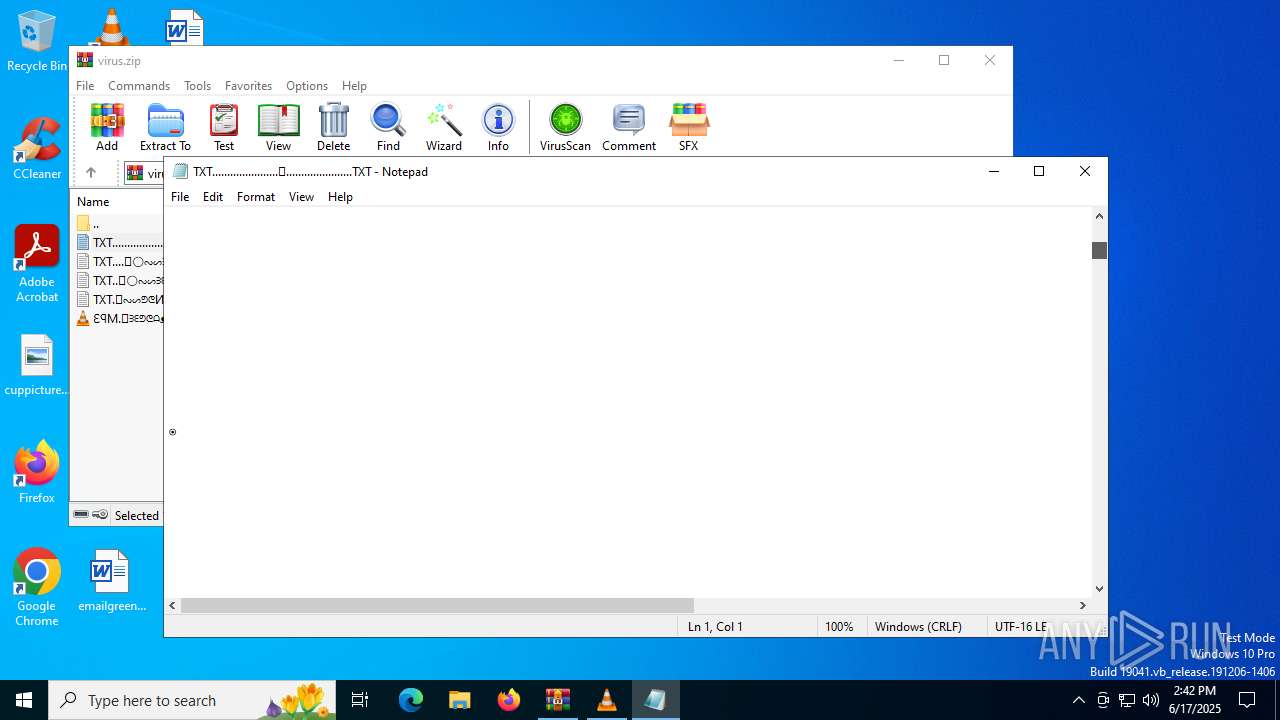
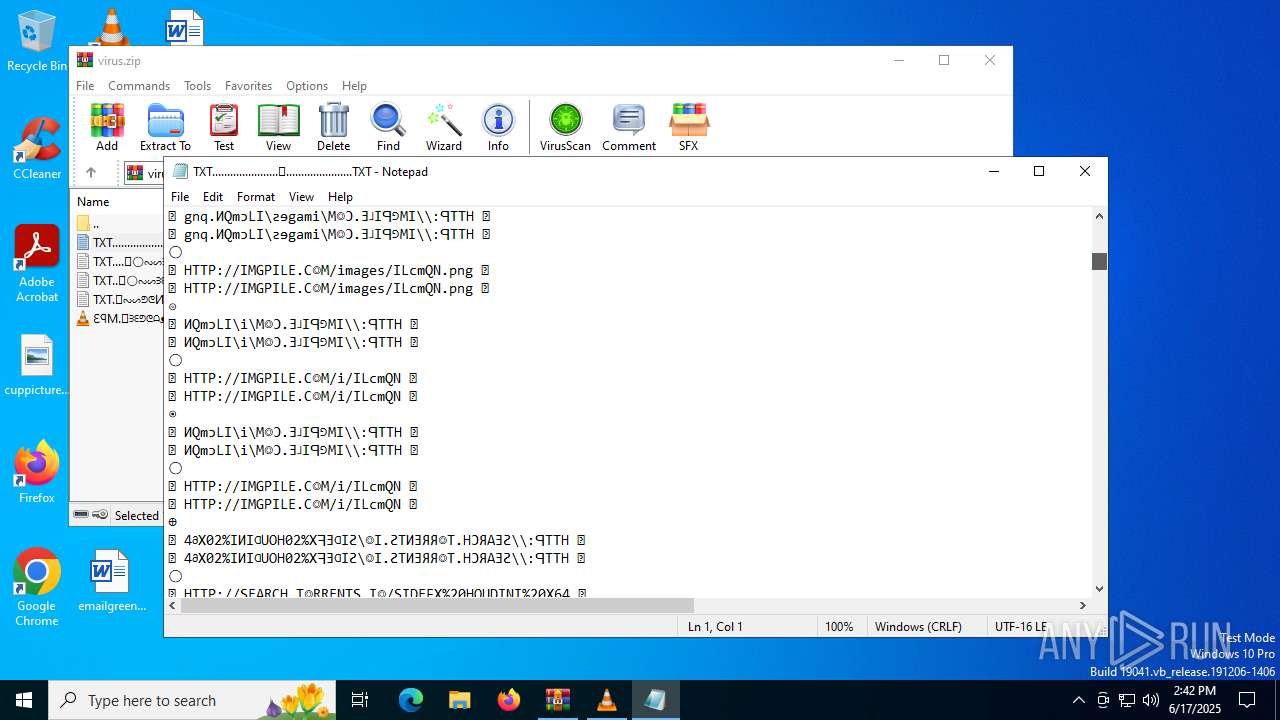
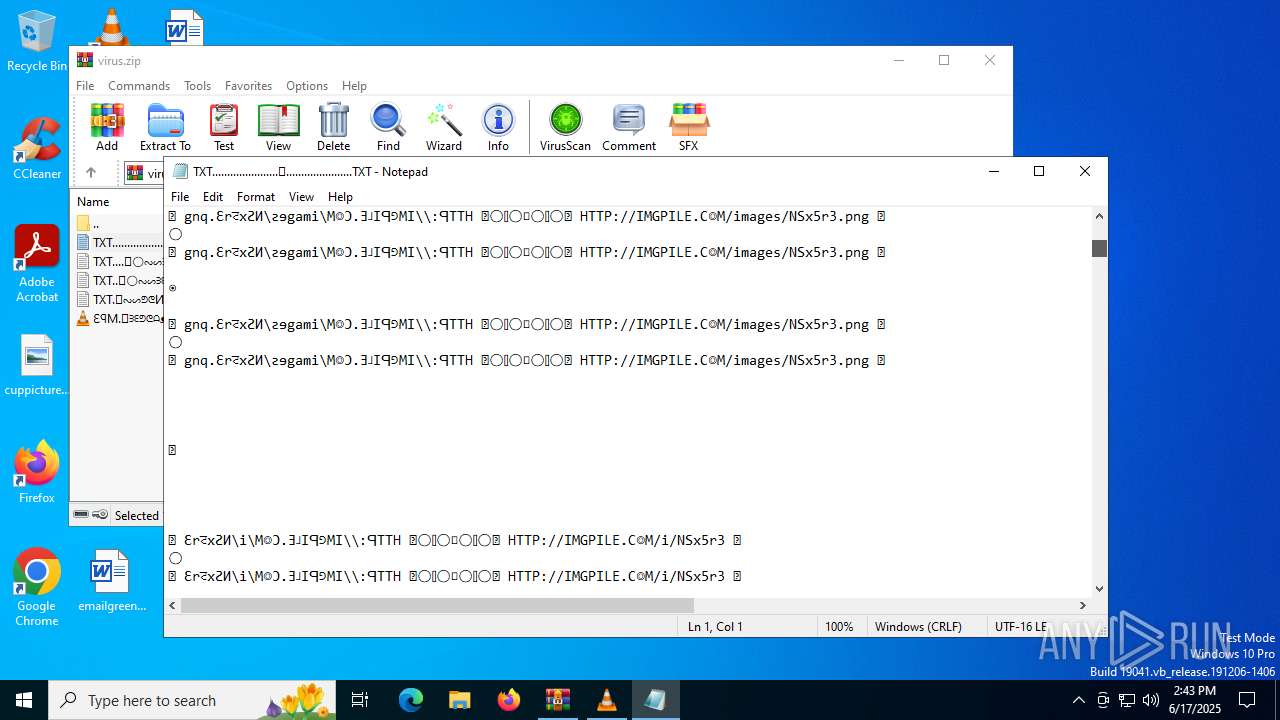
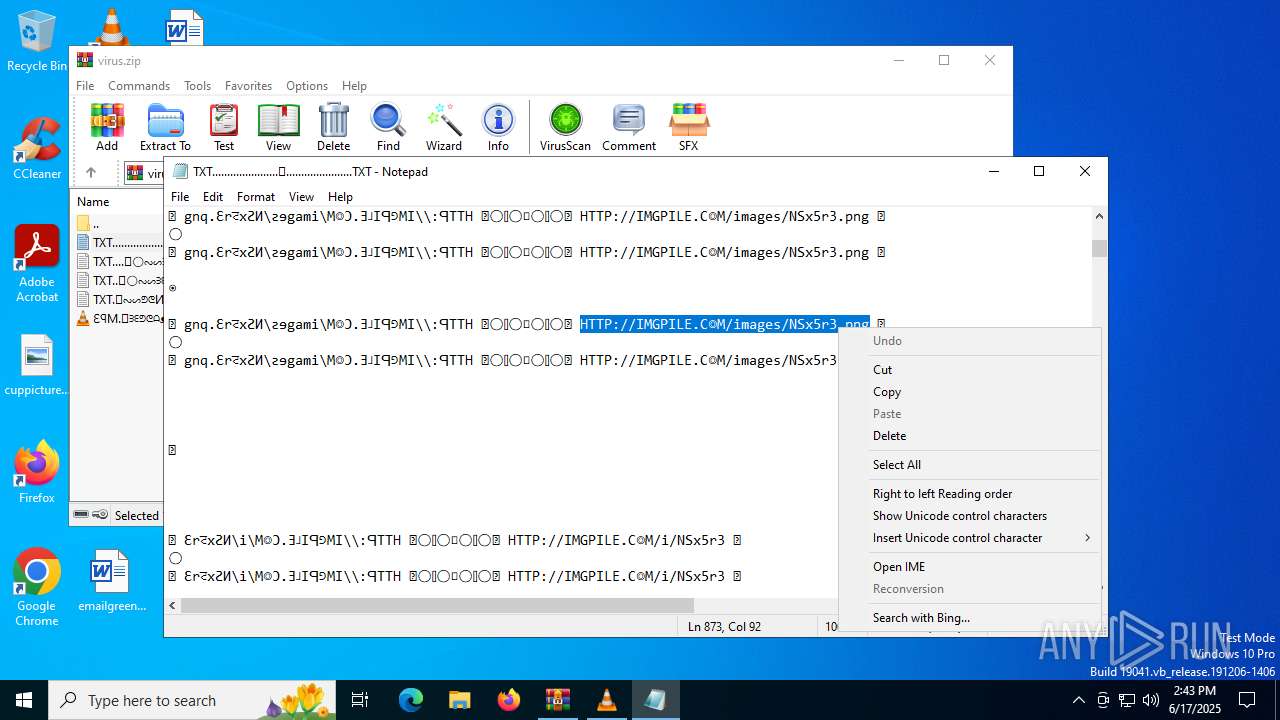
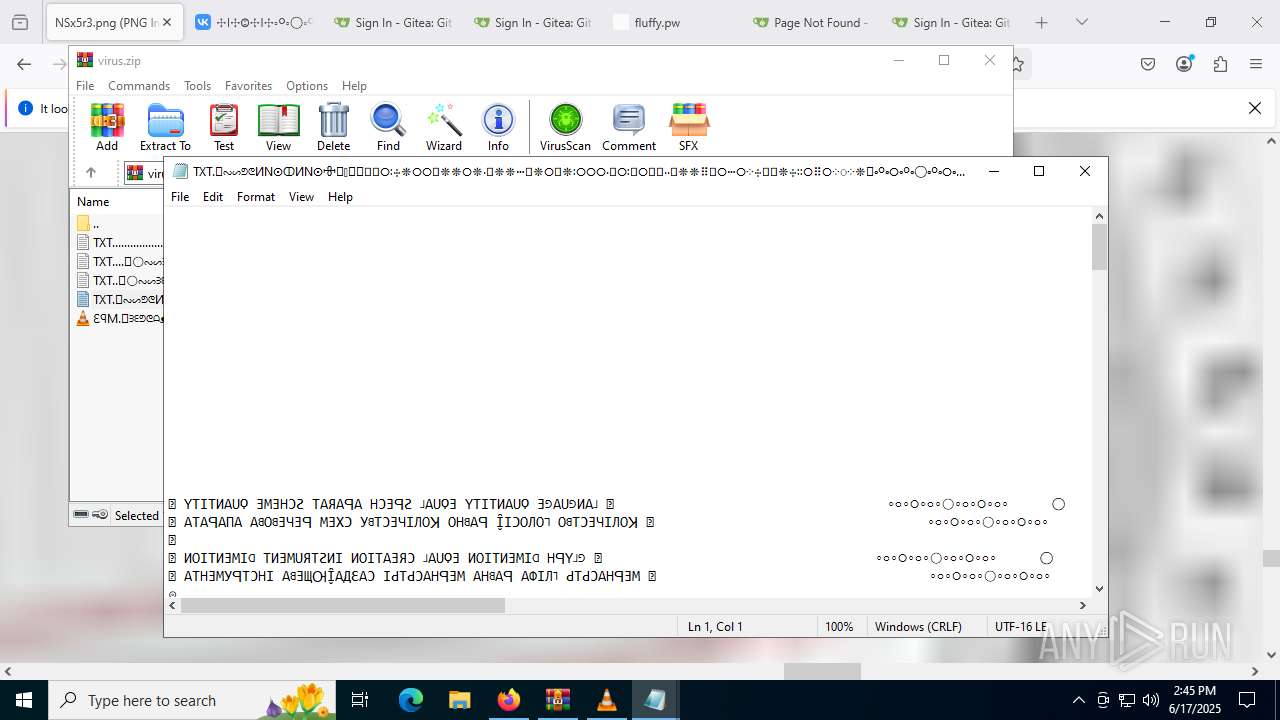
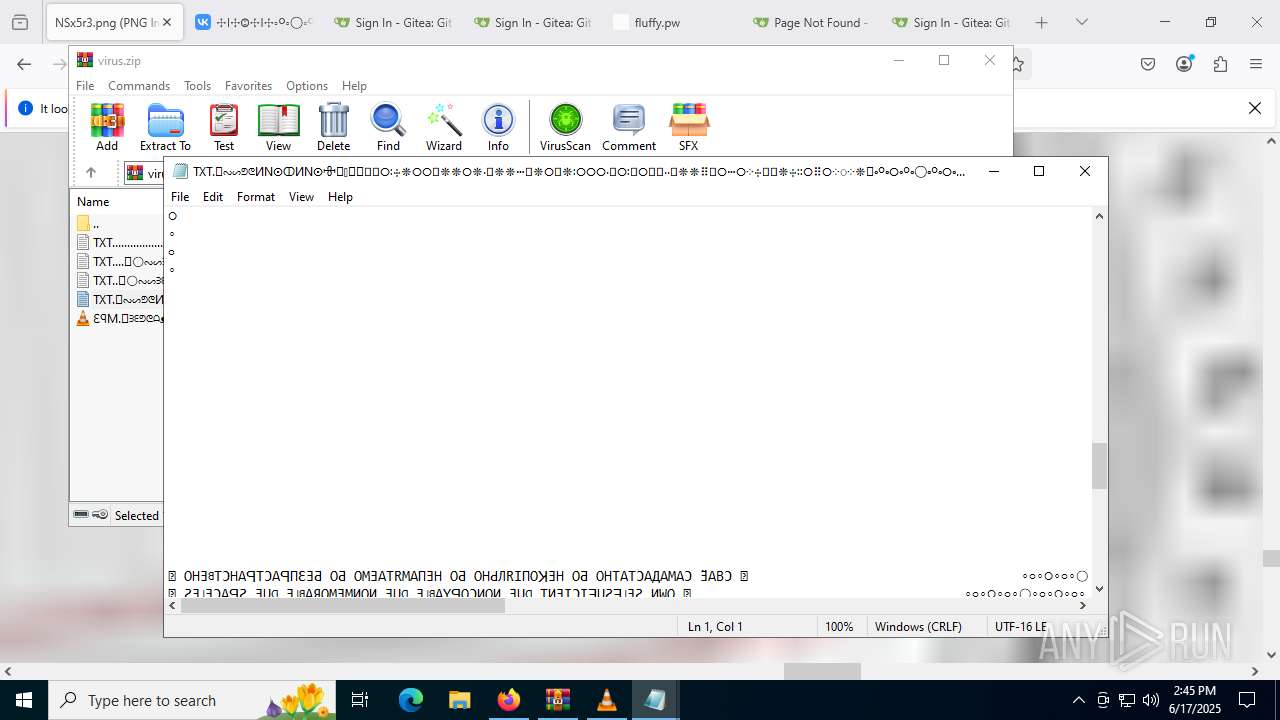
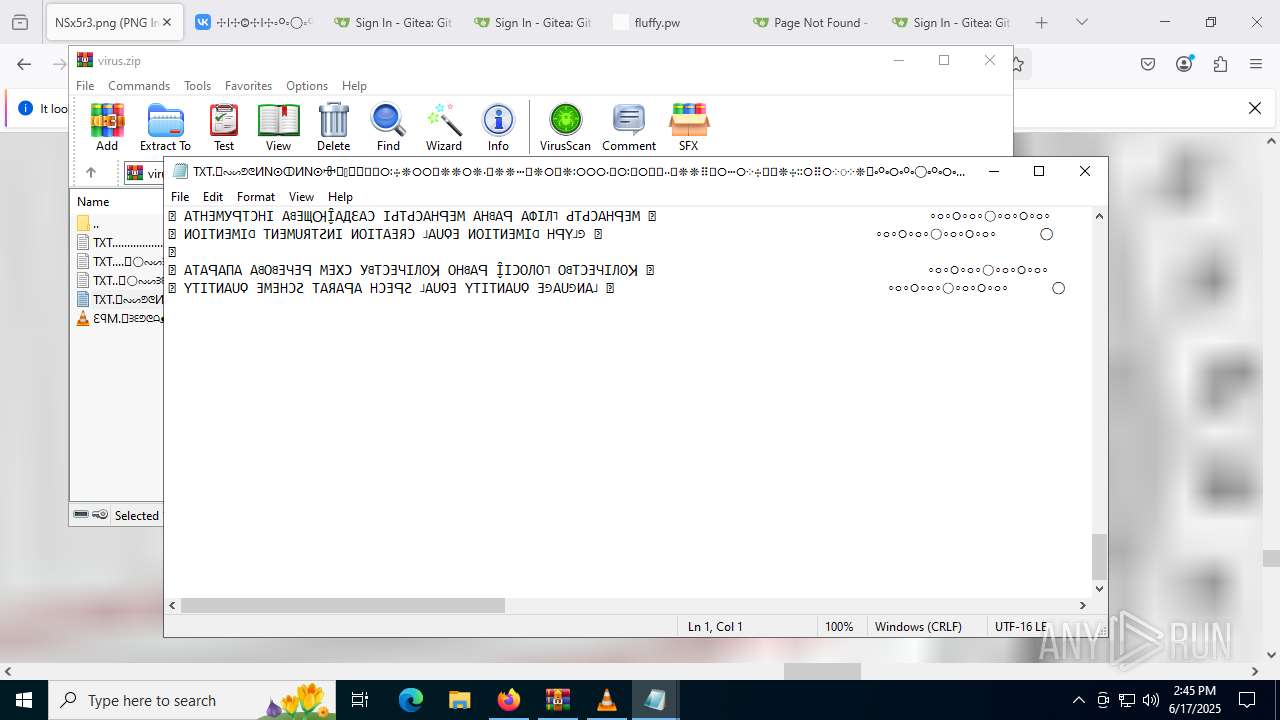
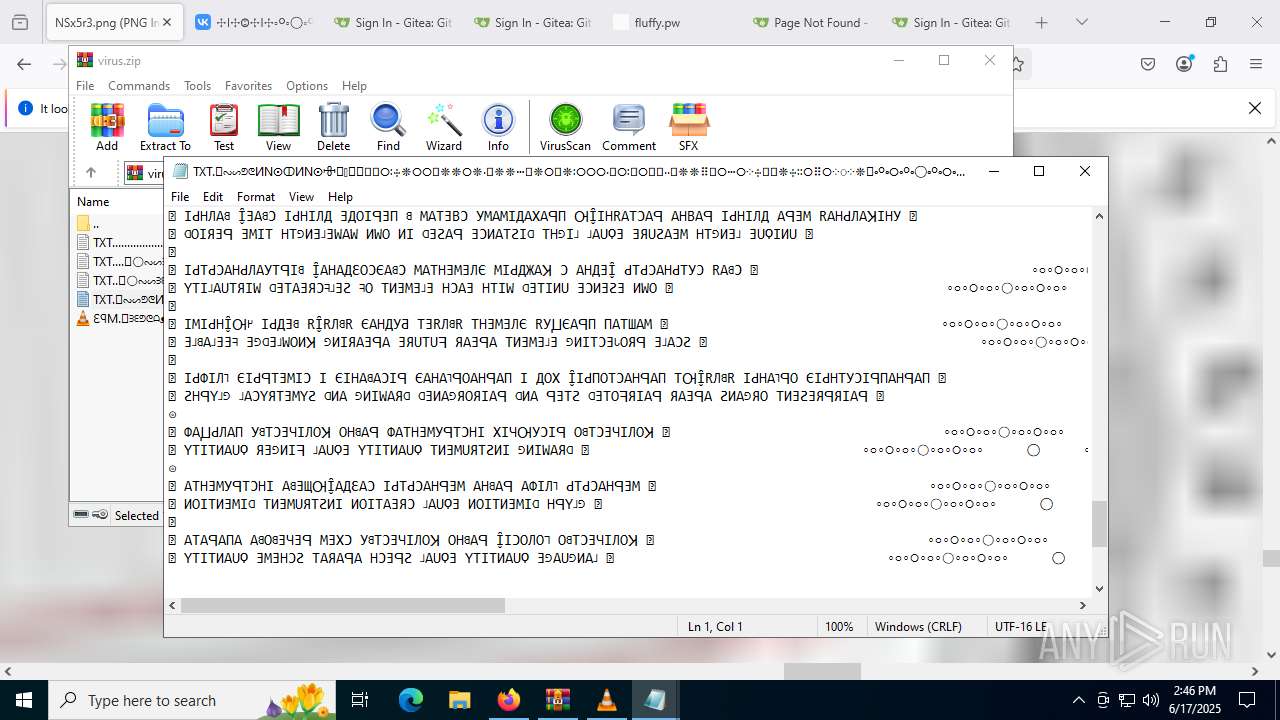
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 4676)
INFO
Checks supported languages
- vlc.exe (PID: 2368)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 4676)
- firefox.exe (PID: 1028)
Reads the computer name
- vlc.exe (PID: 2368)
Reads security settings of Internet Explorer
- notepad.exe (PID: 640)
- notepad.exe (PID: 6304)
- notepad.exe (PID: 7284)
- notepad.exe (PID: 7796)
The process uses Lua
- vlc.exe (PID: 2368)
Manual execution by a user
- firefox.exe (PID: 5184)
Application launched itself
- firefox.exe (PID: 5184)
- firefox.exe (PID: 1028)
Checks proxy server information
- slui.exe (PID: 6892)
Reads the software policy settings
- slui.exe (PID: 6892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2025:06:16 15:51:36 |
| ZipCRC: | 0x083f5b02 |
| ZipCompressedSize: | 1007750 |
| ZipUncompressedSize: | 1007750 |
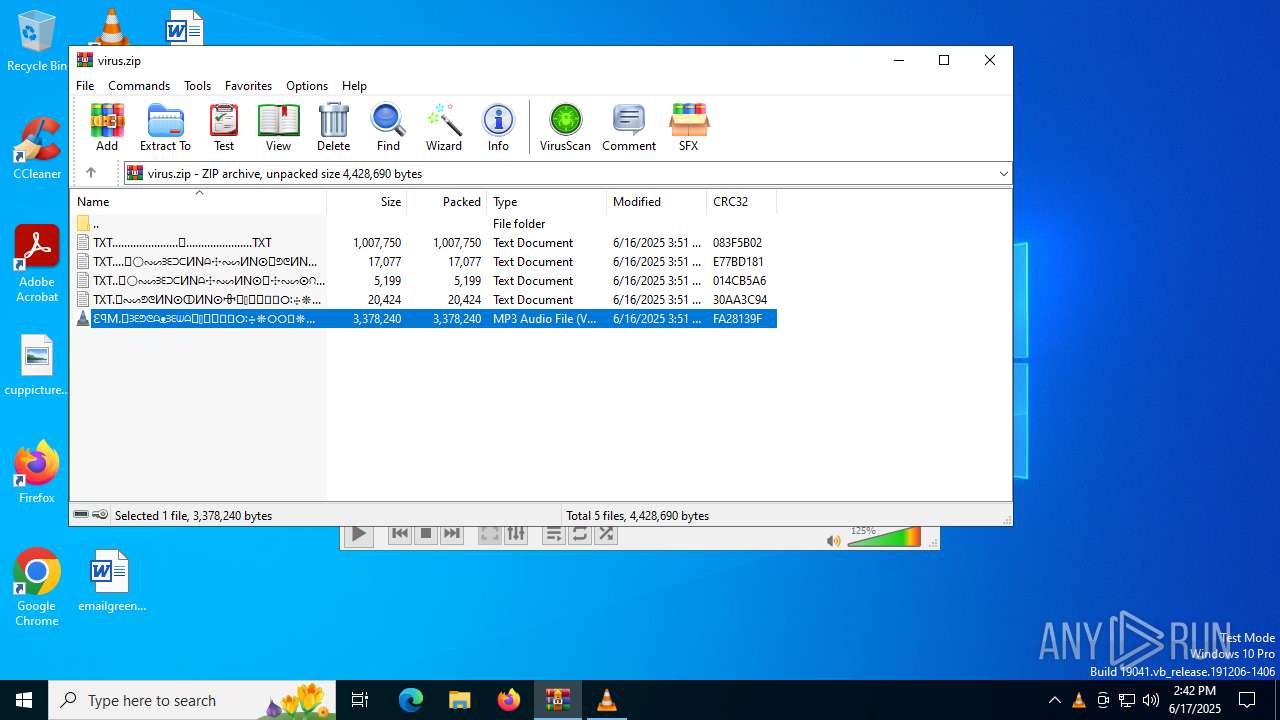
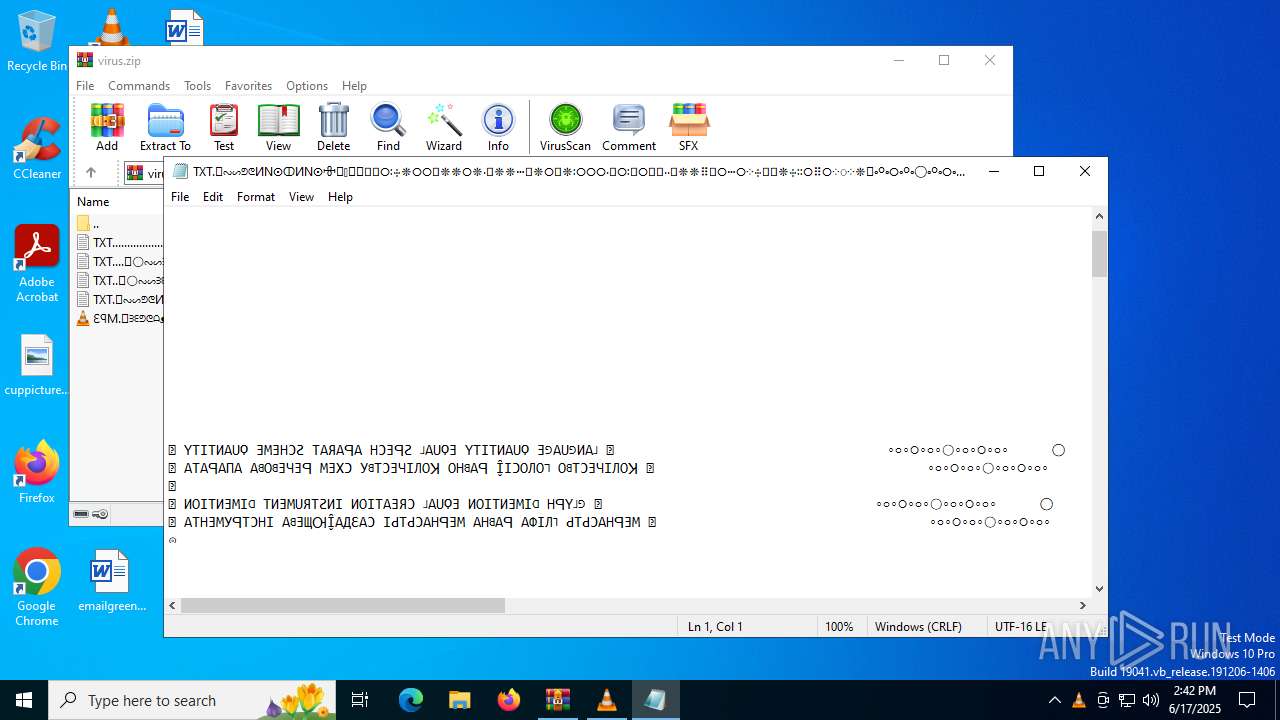
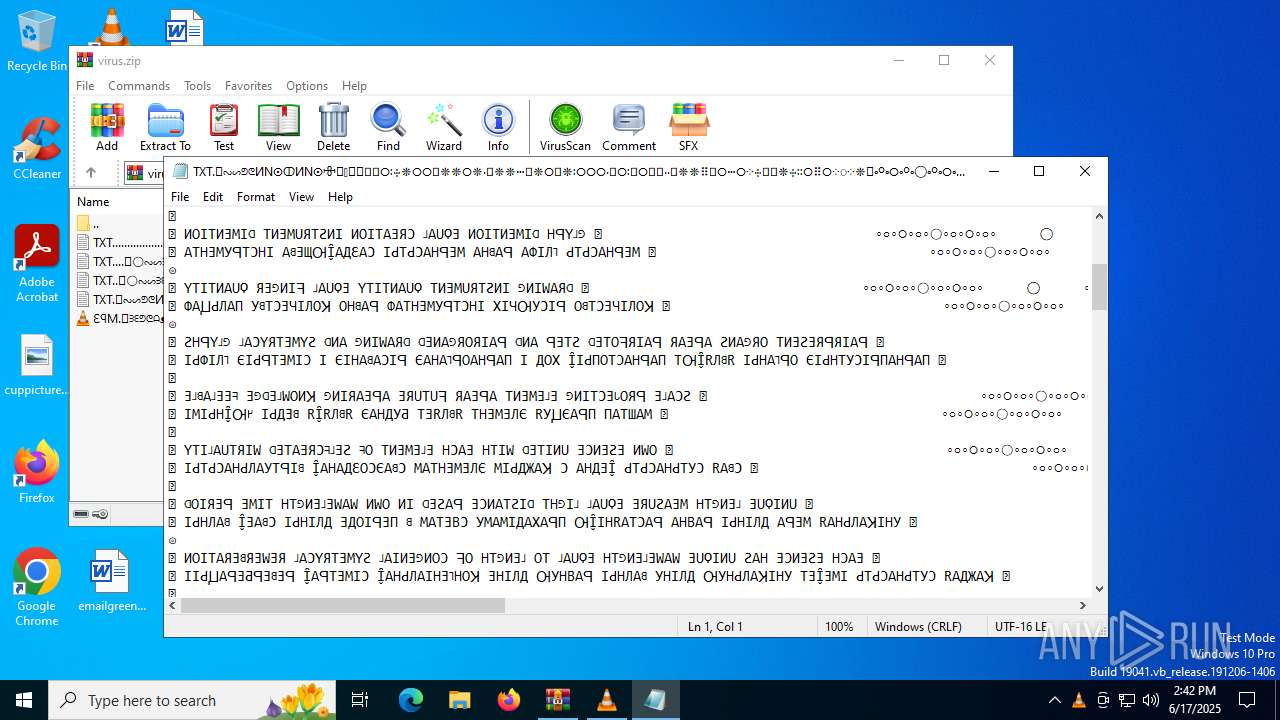
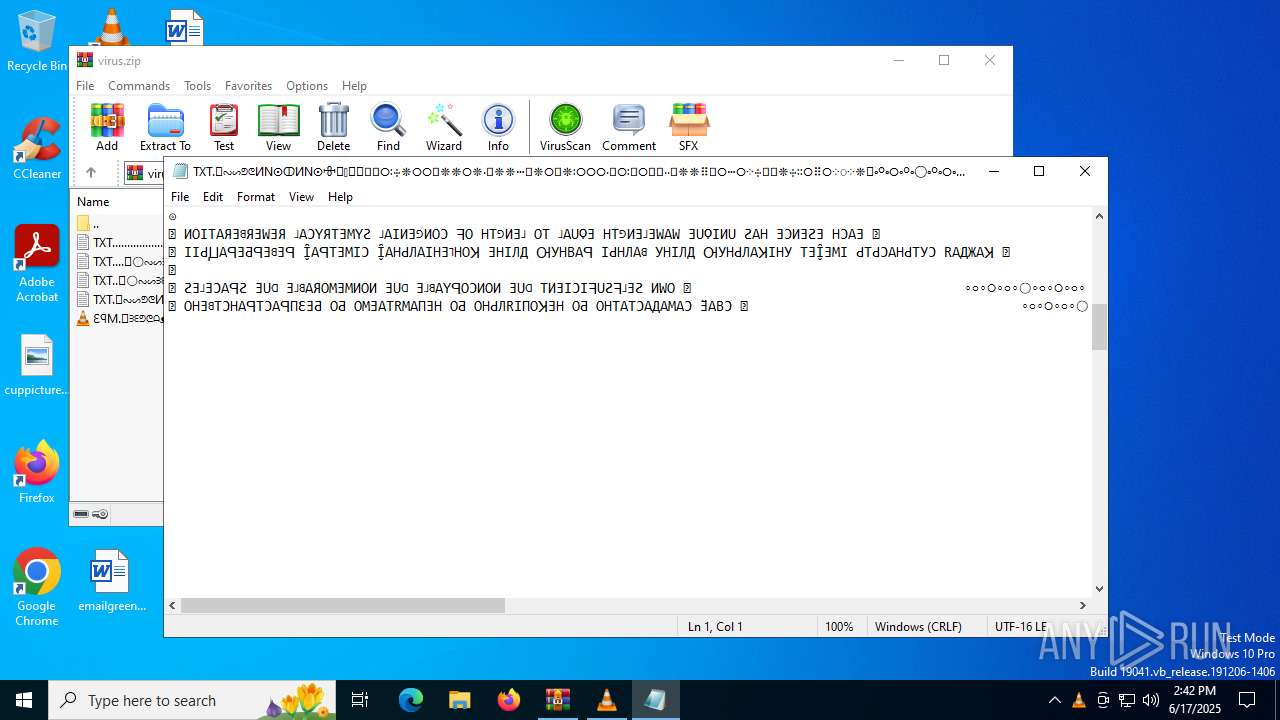
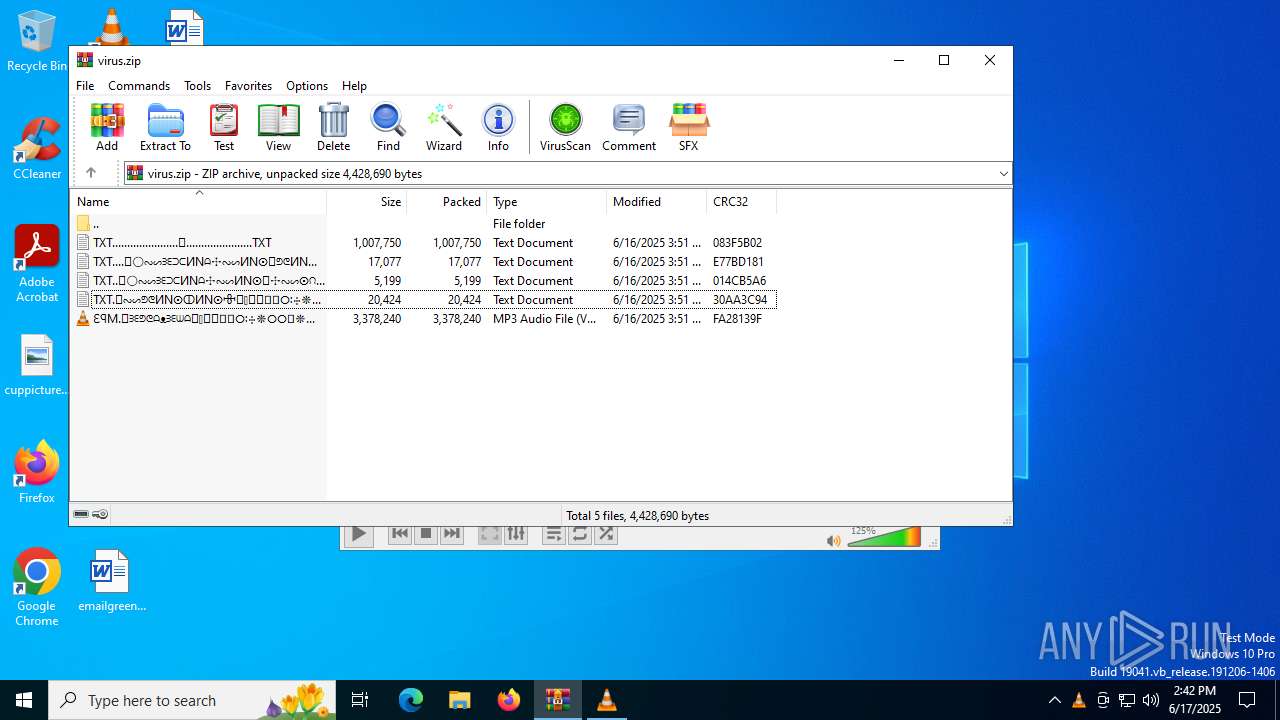
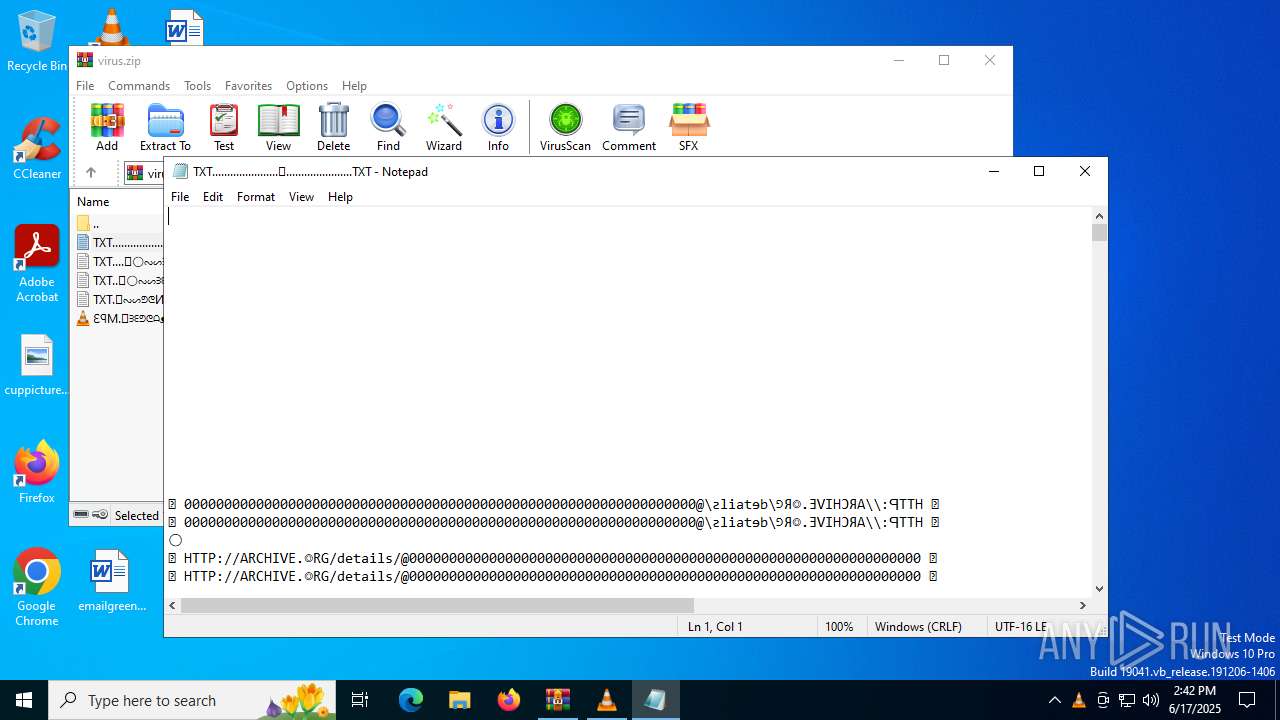
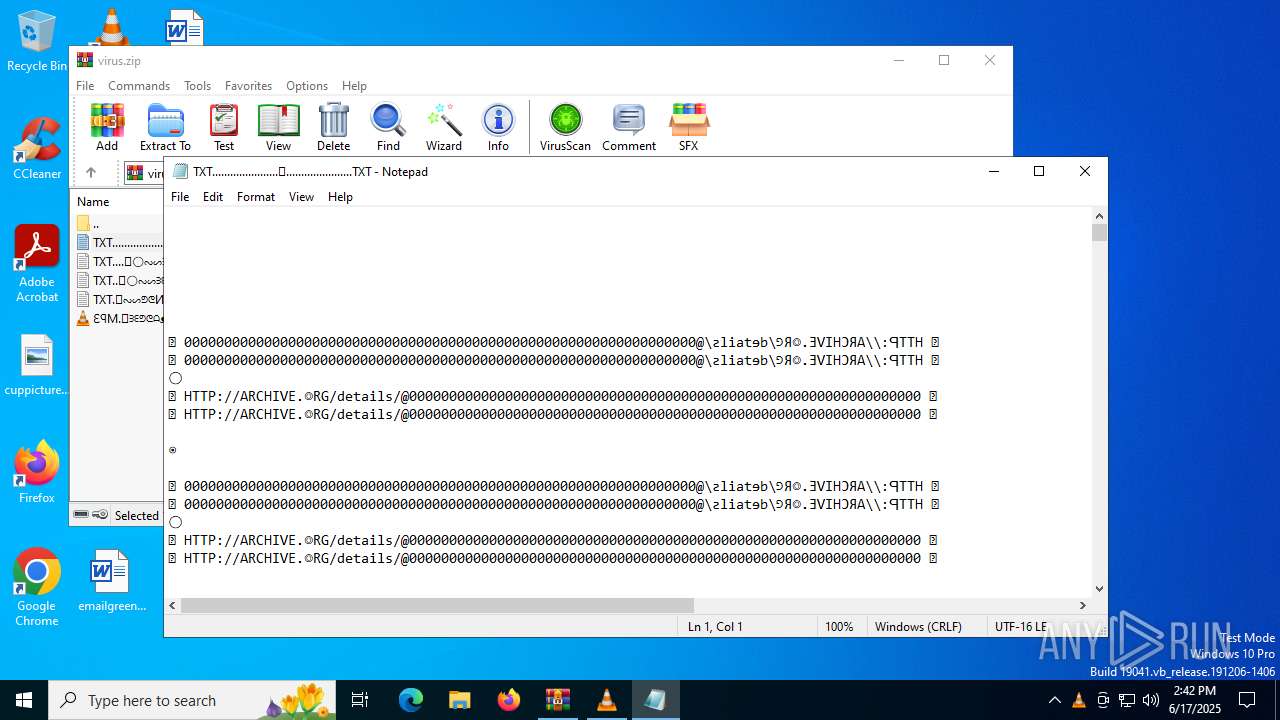
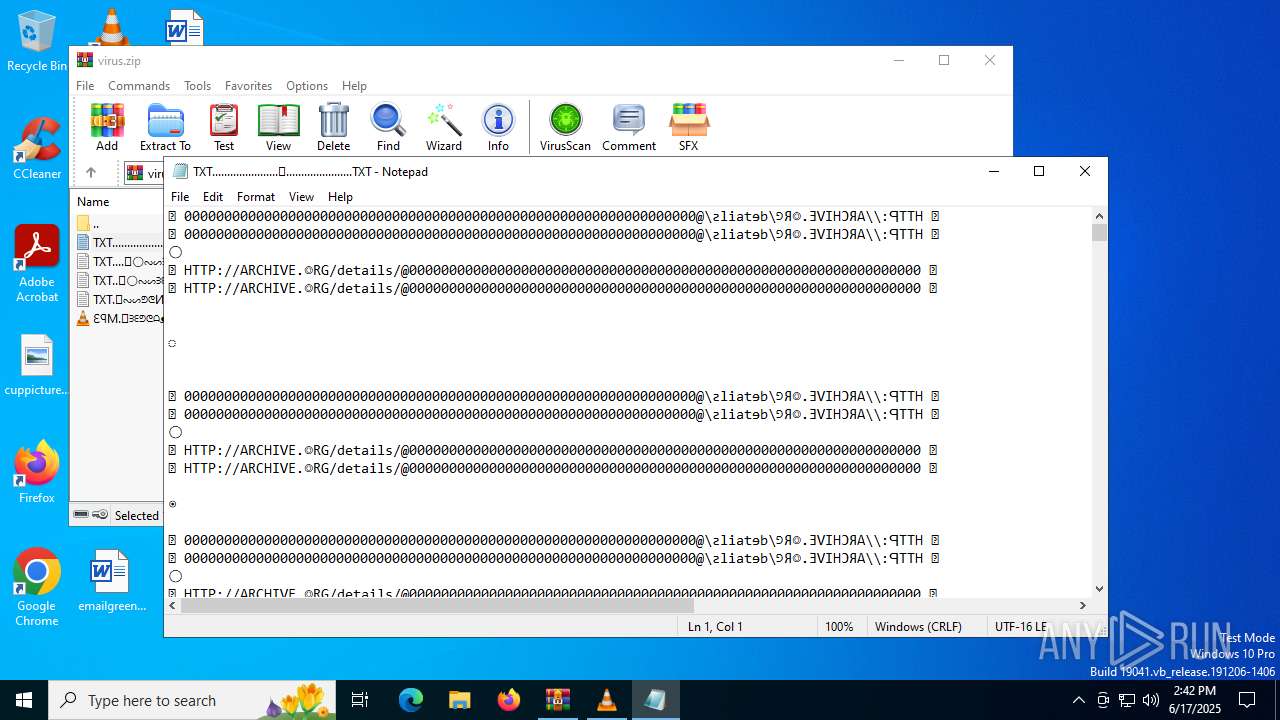
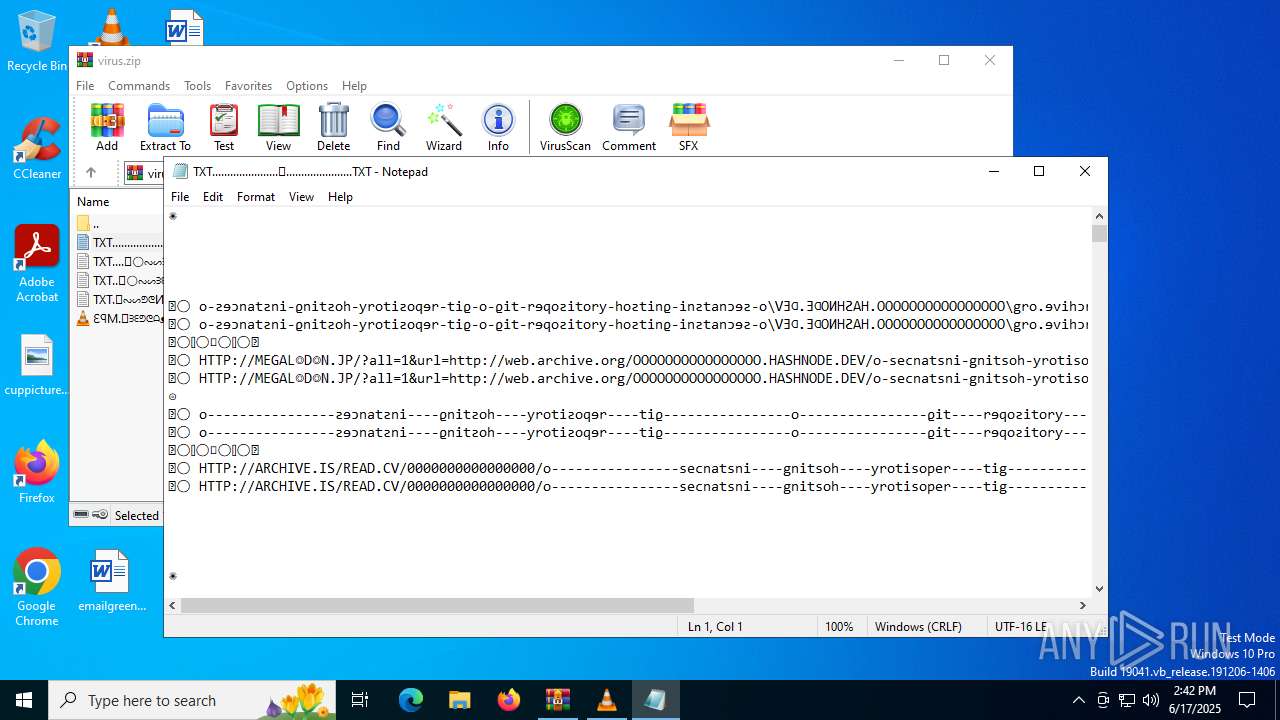
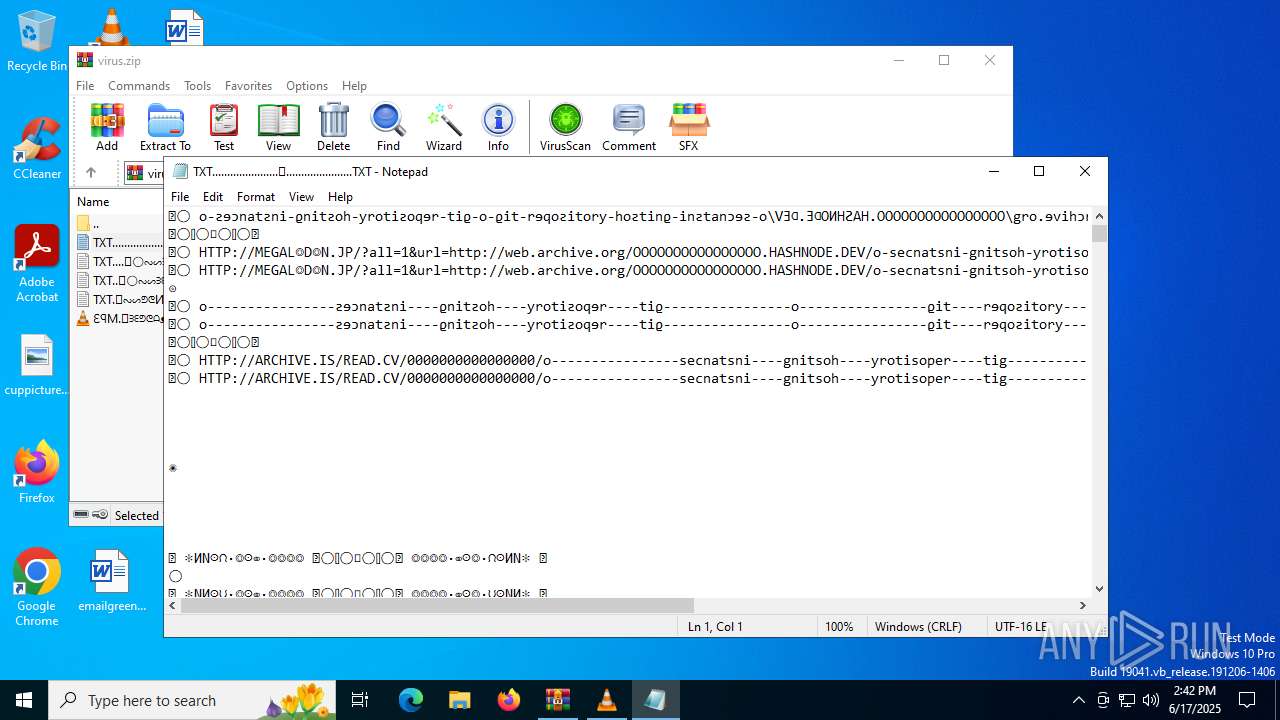
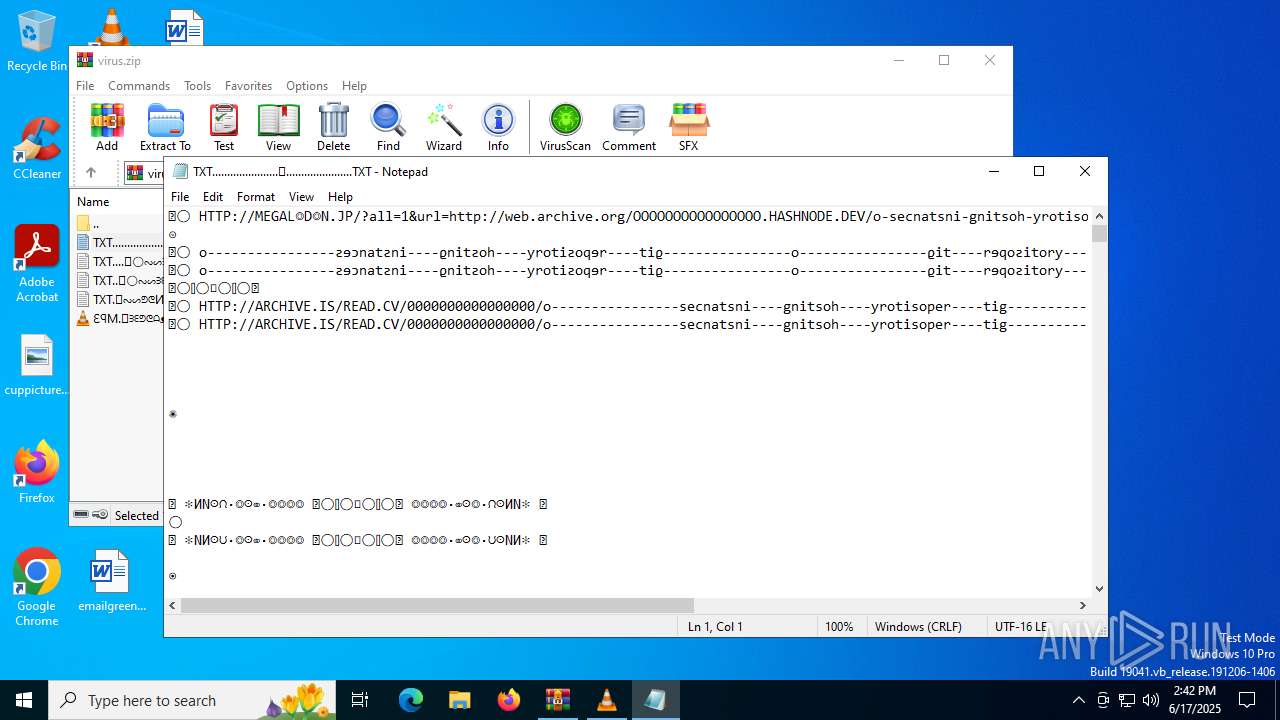
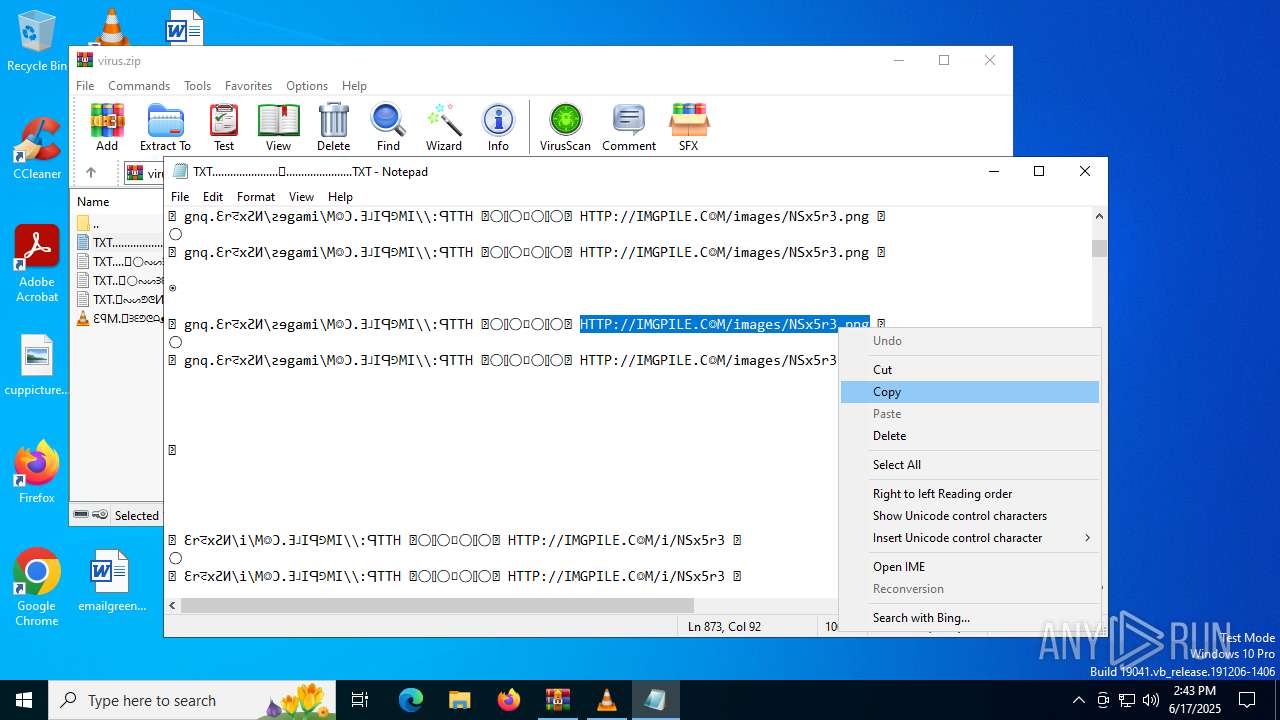
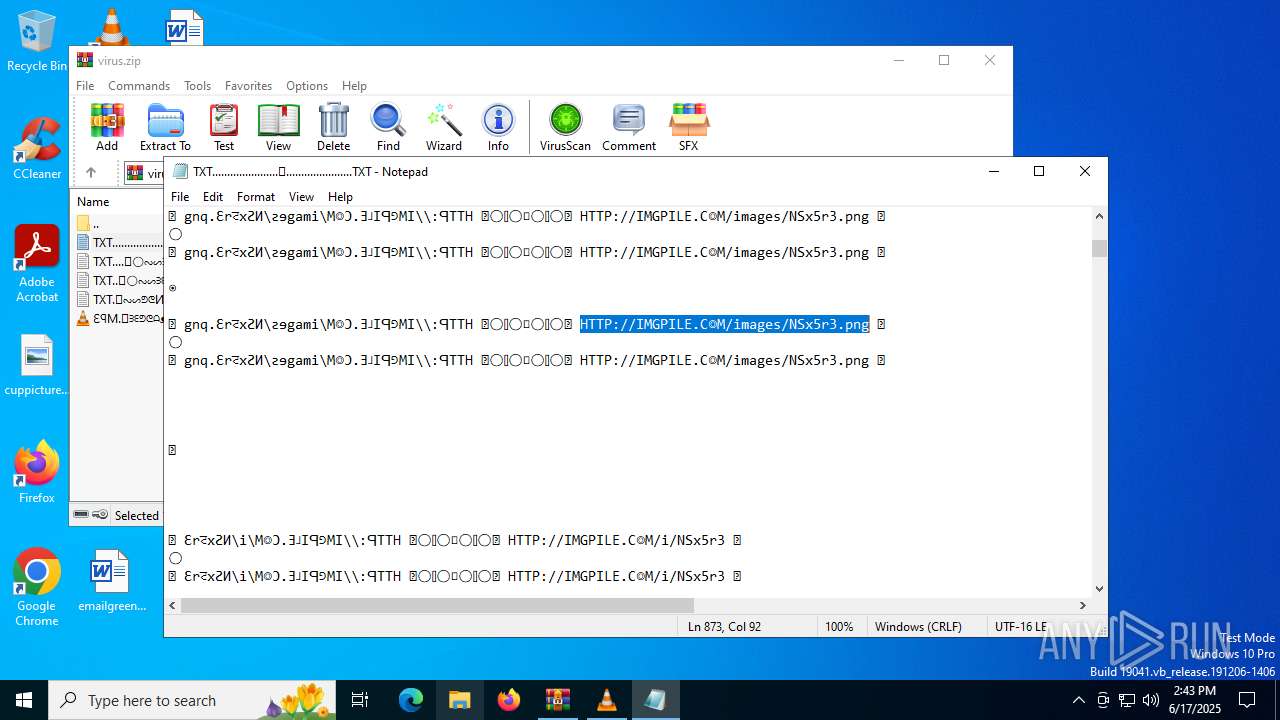
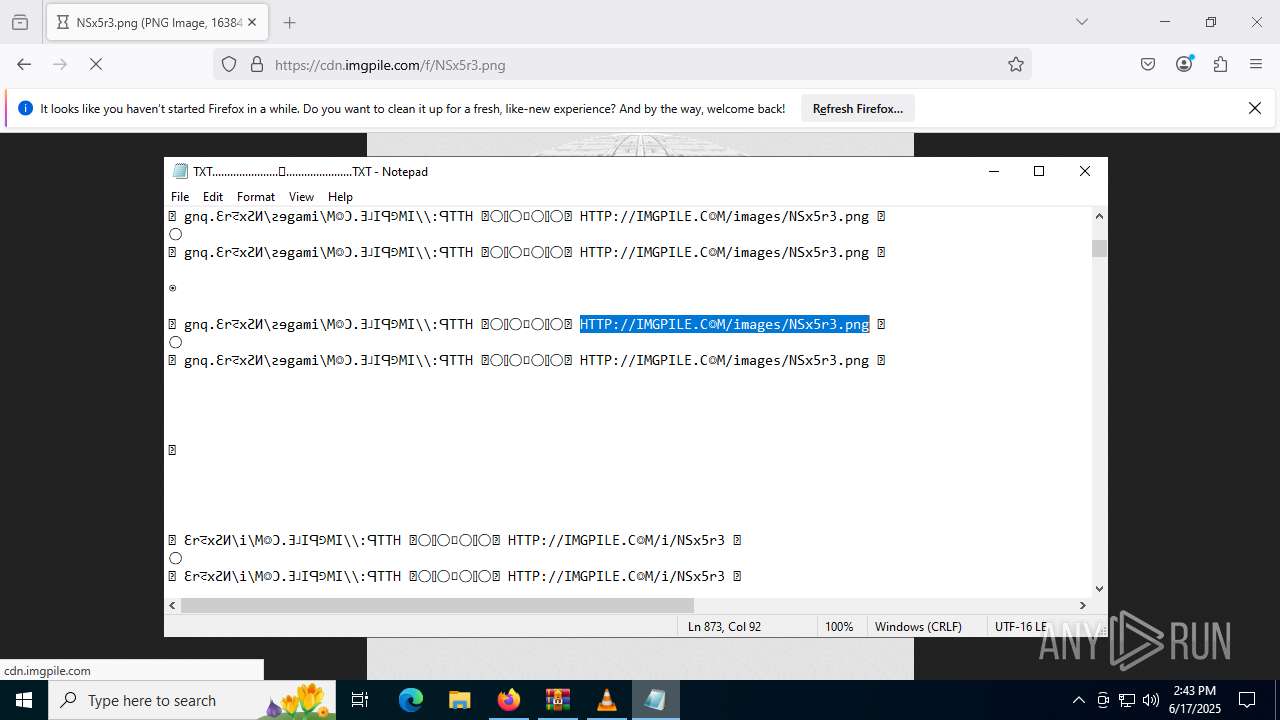
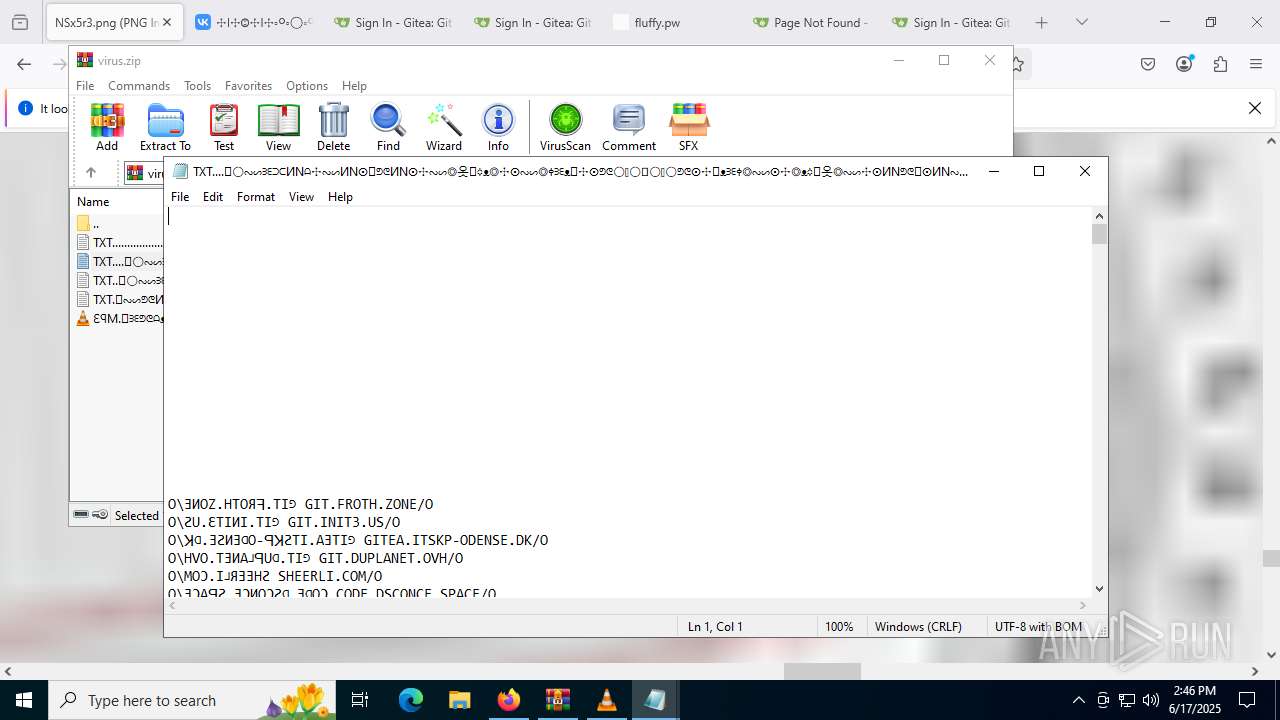
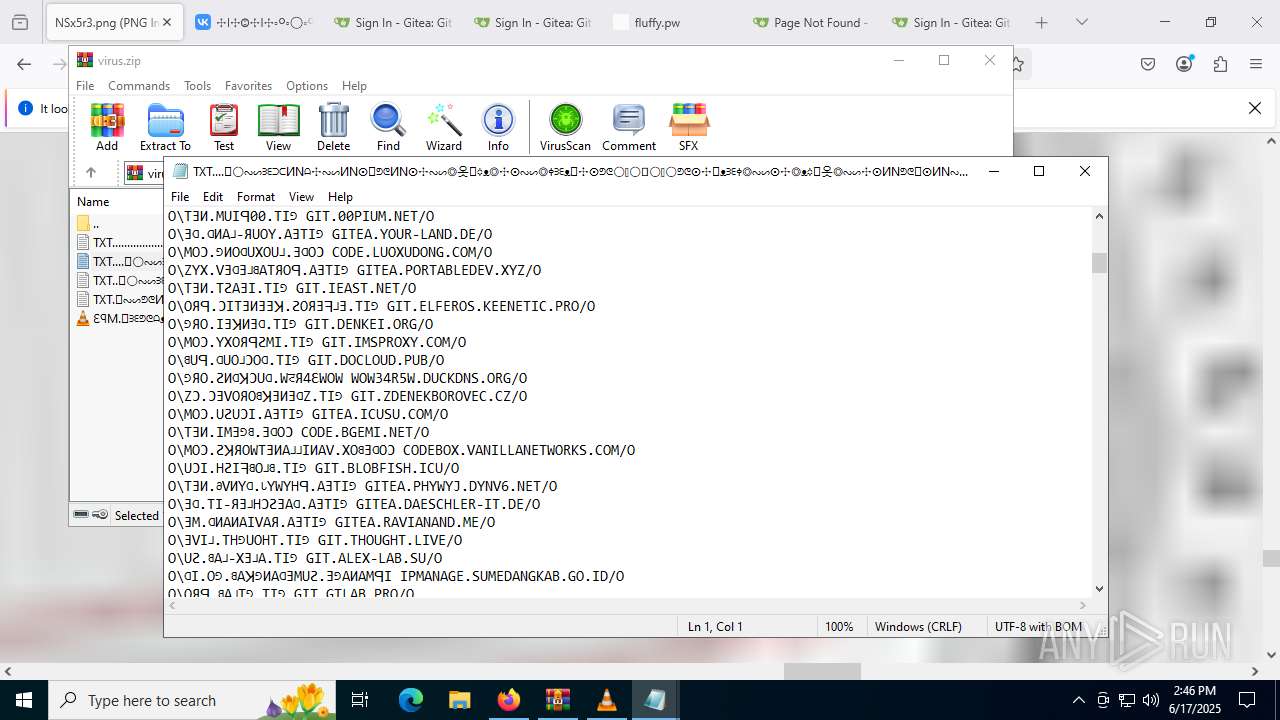
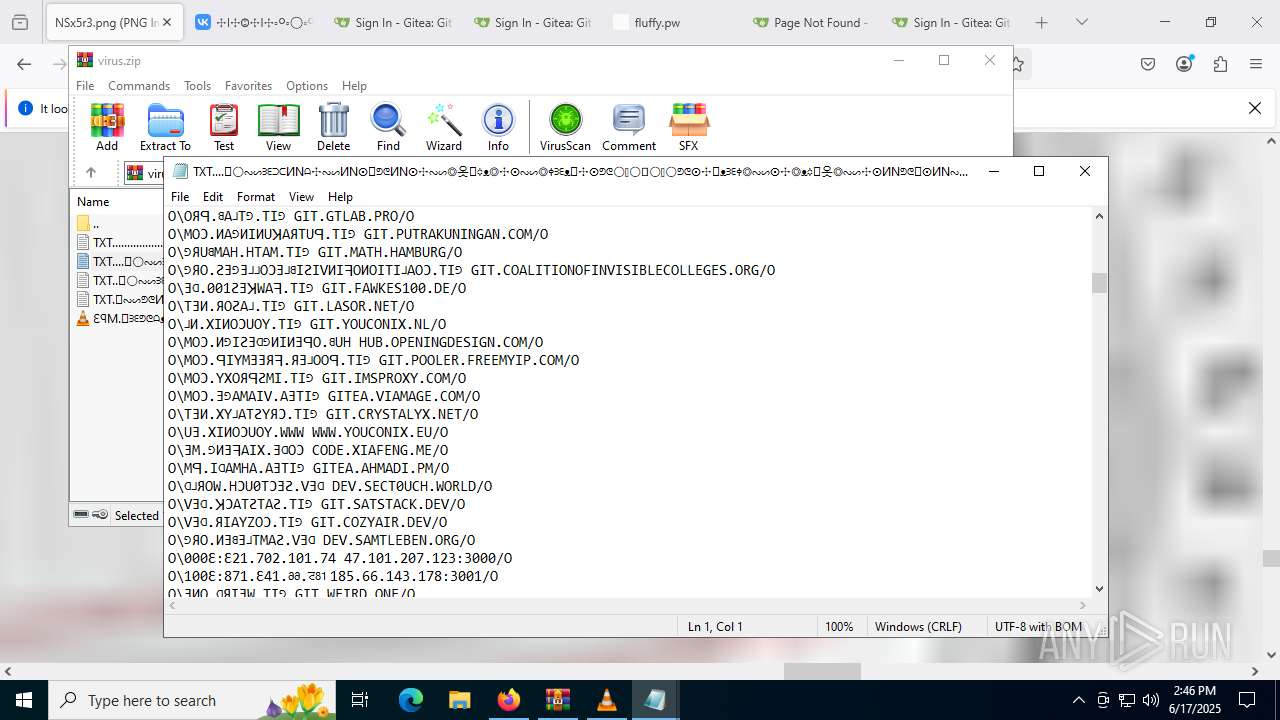
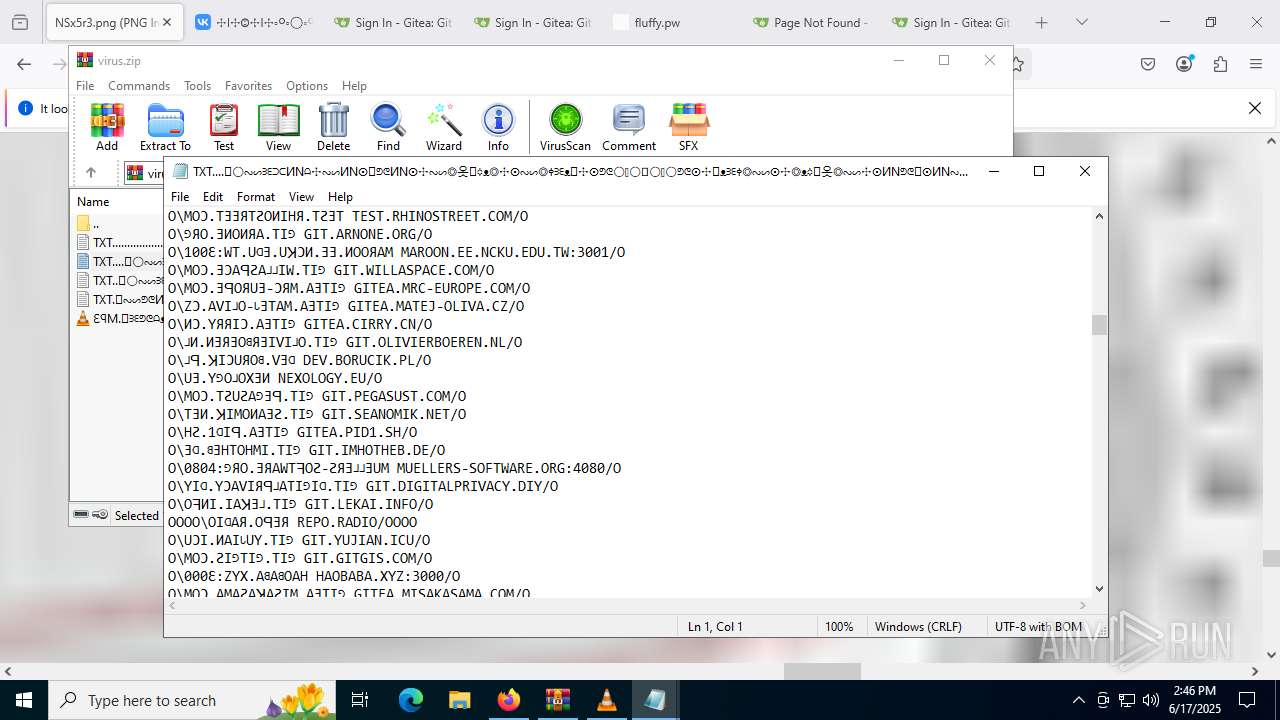
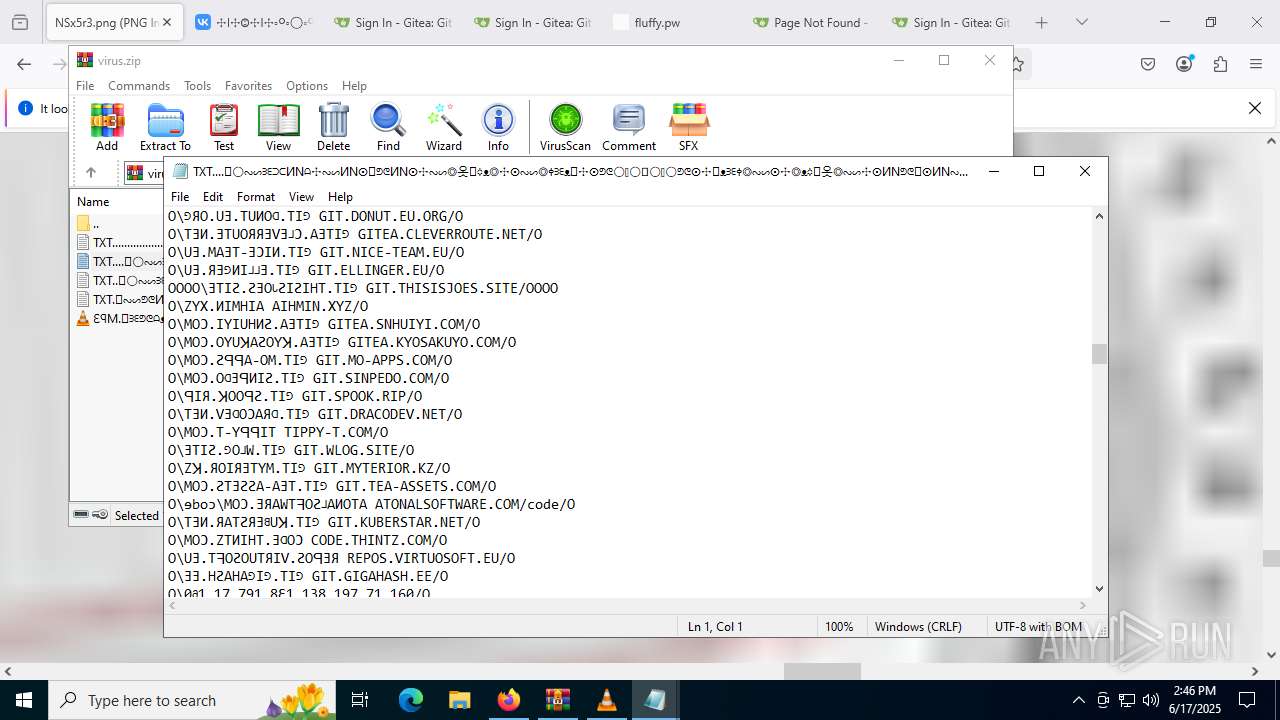
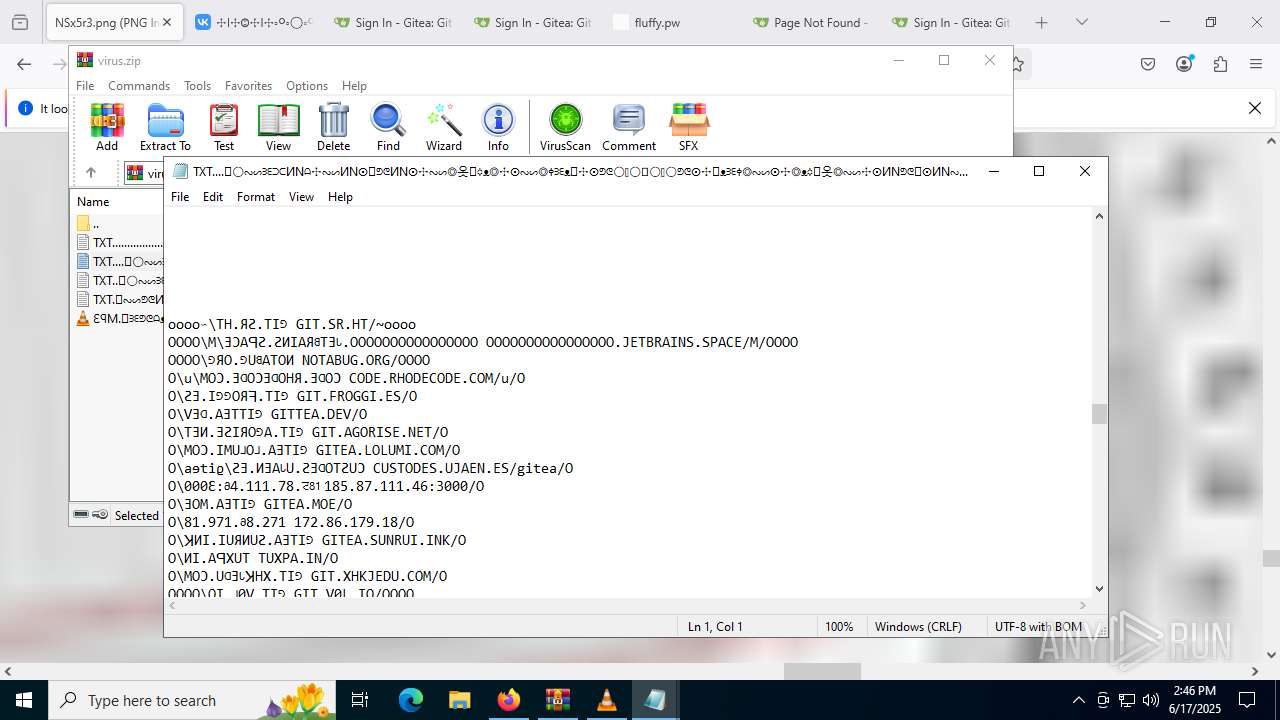
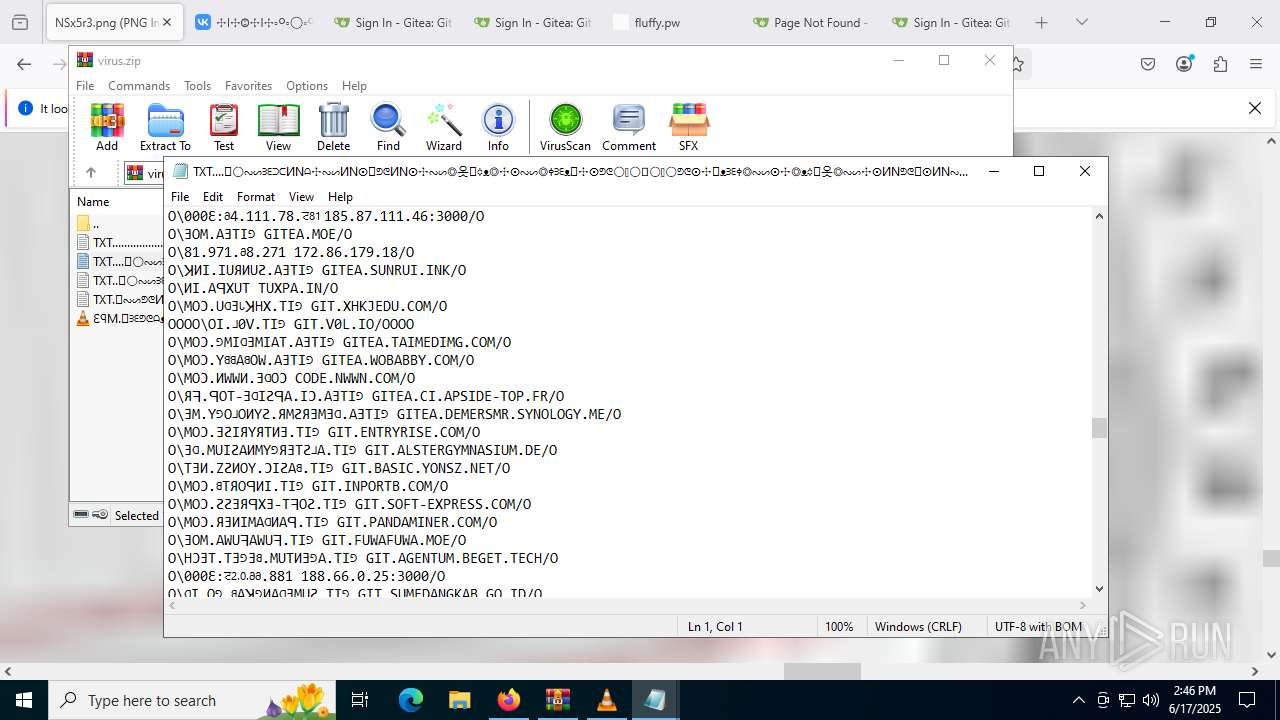
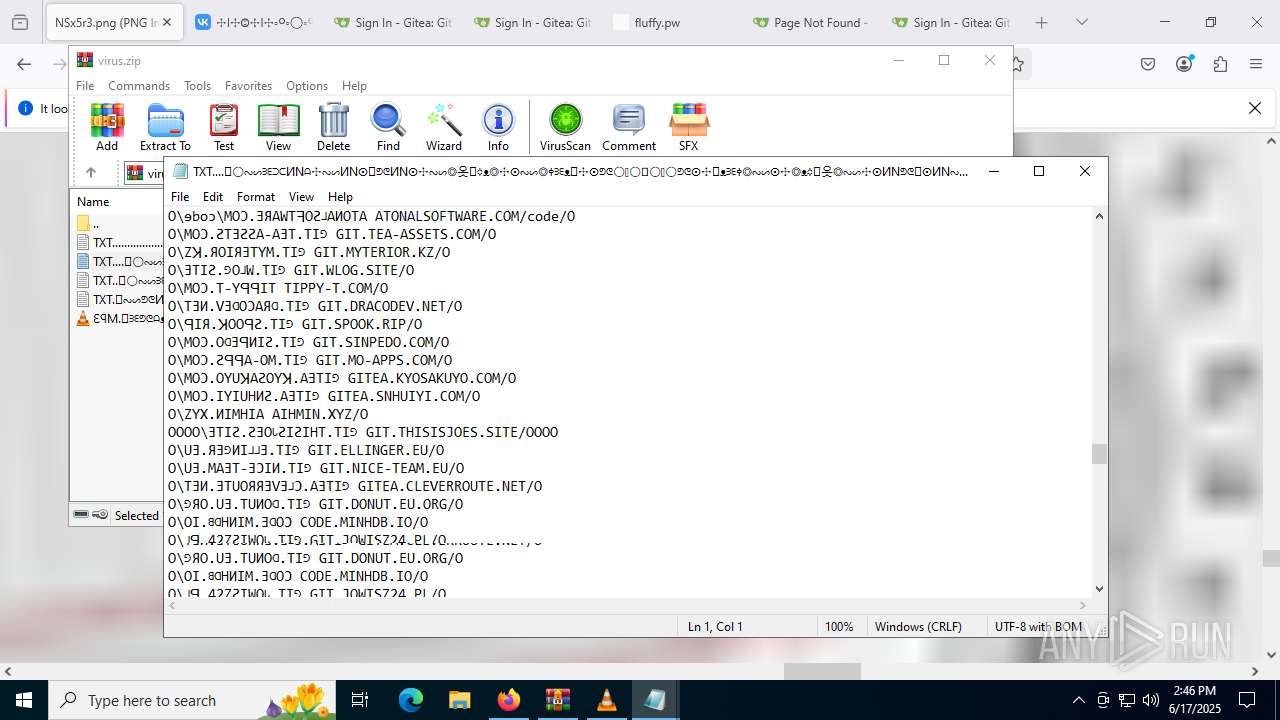
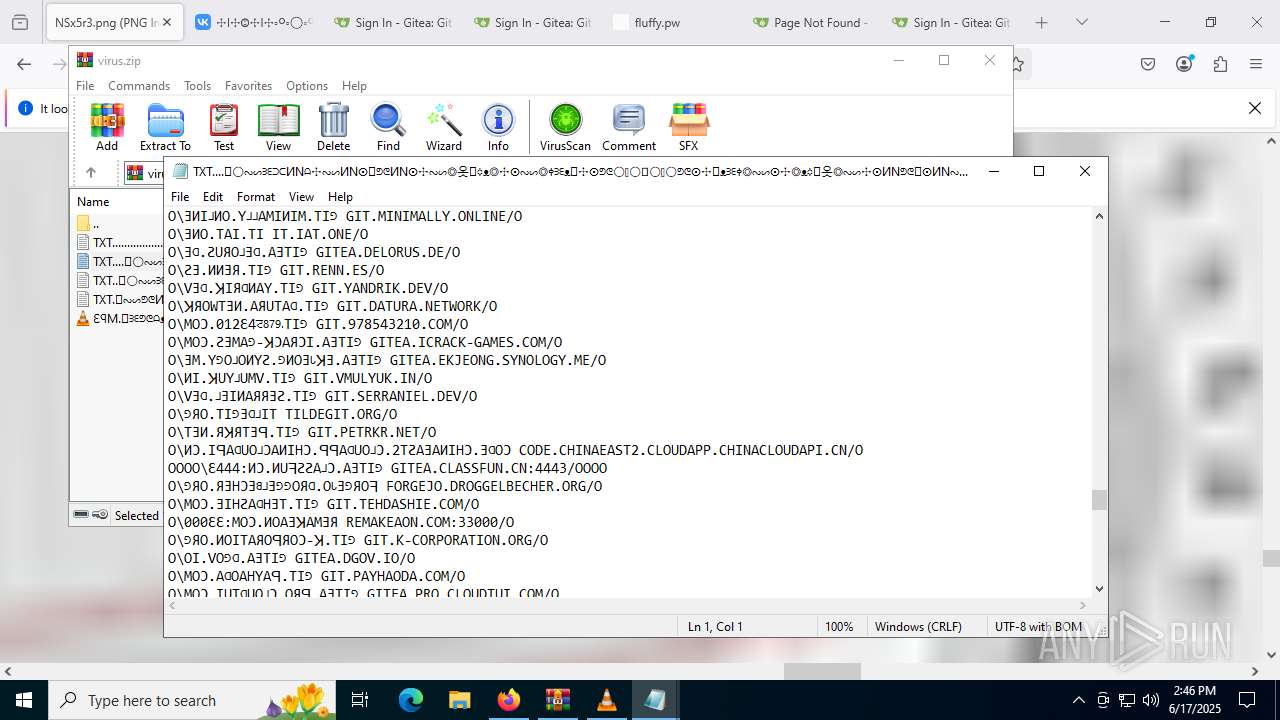
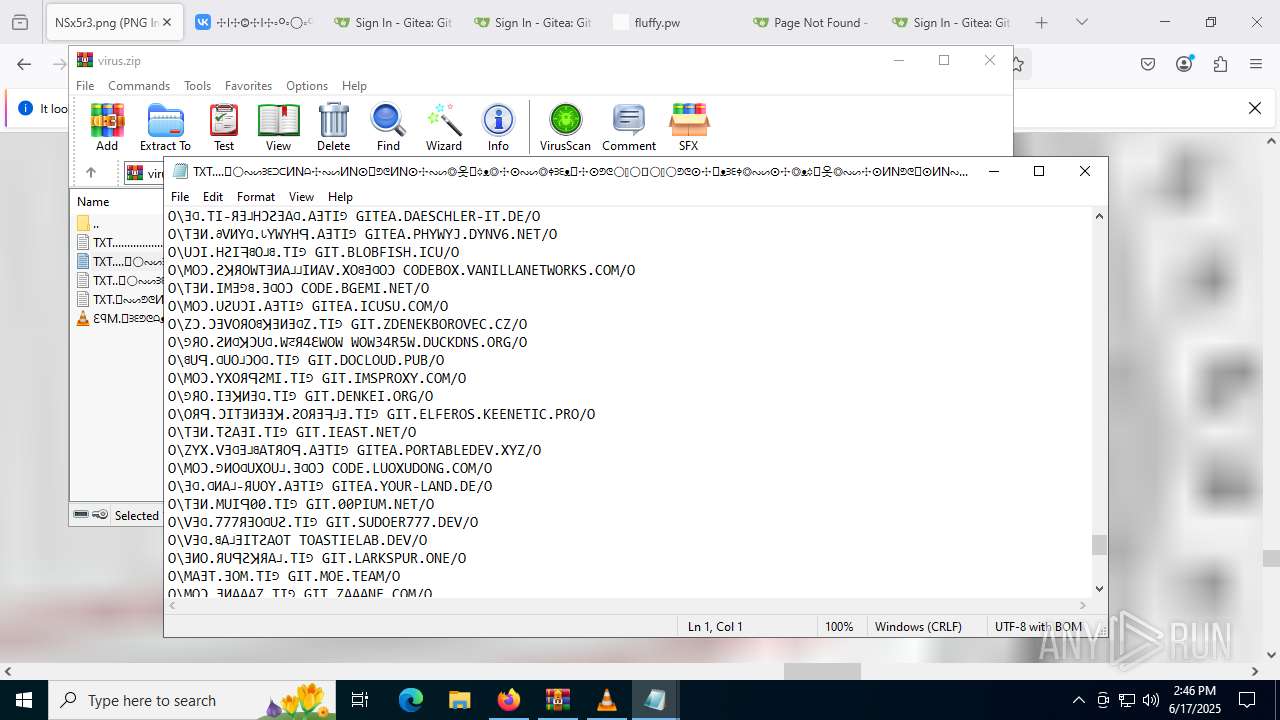
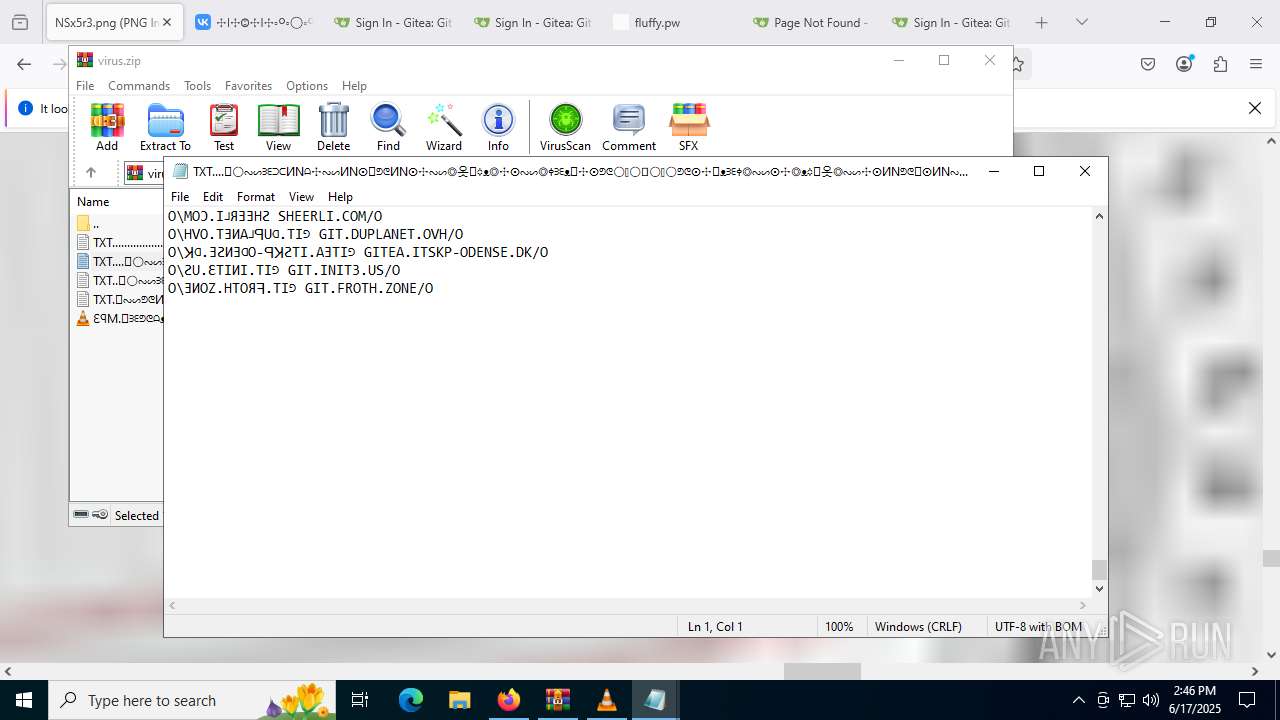
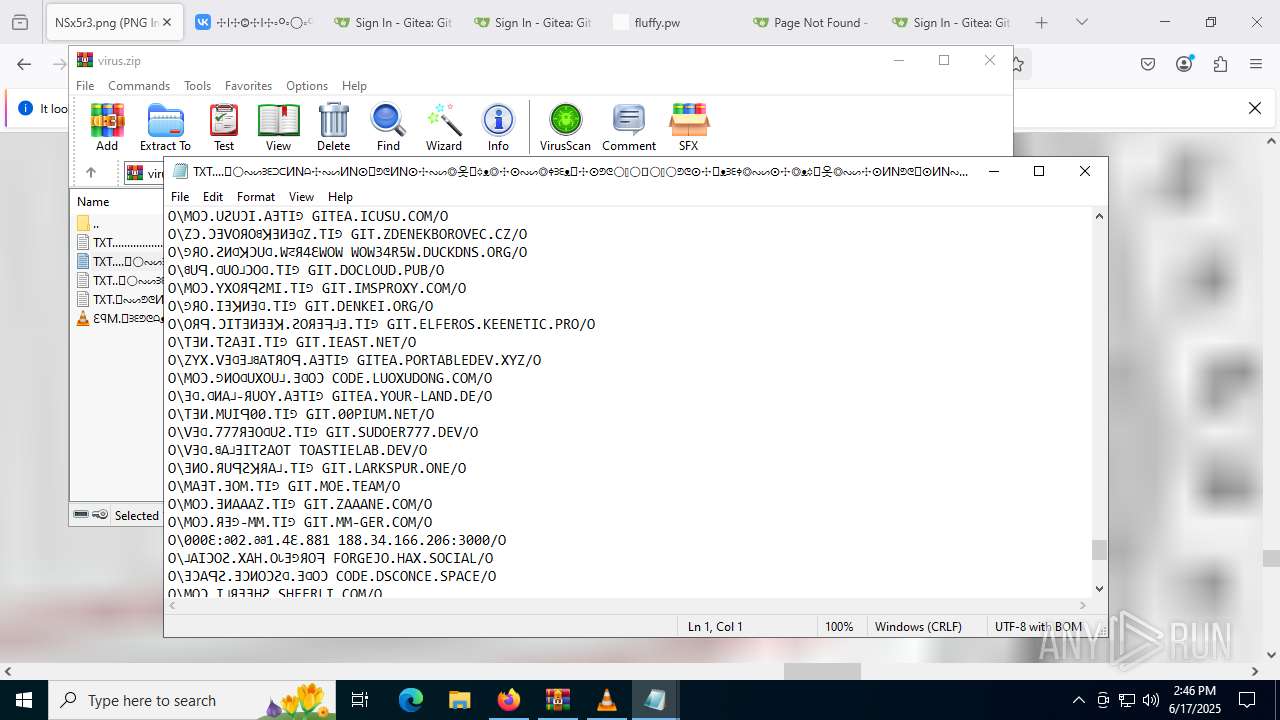
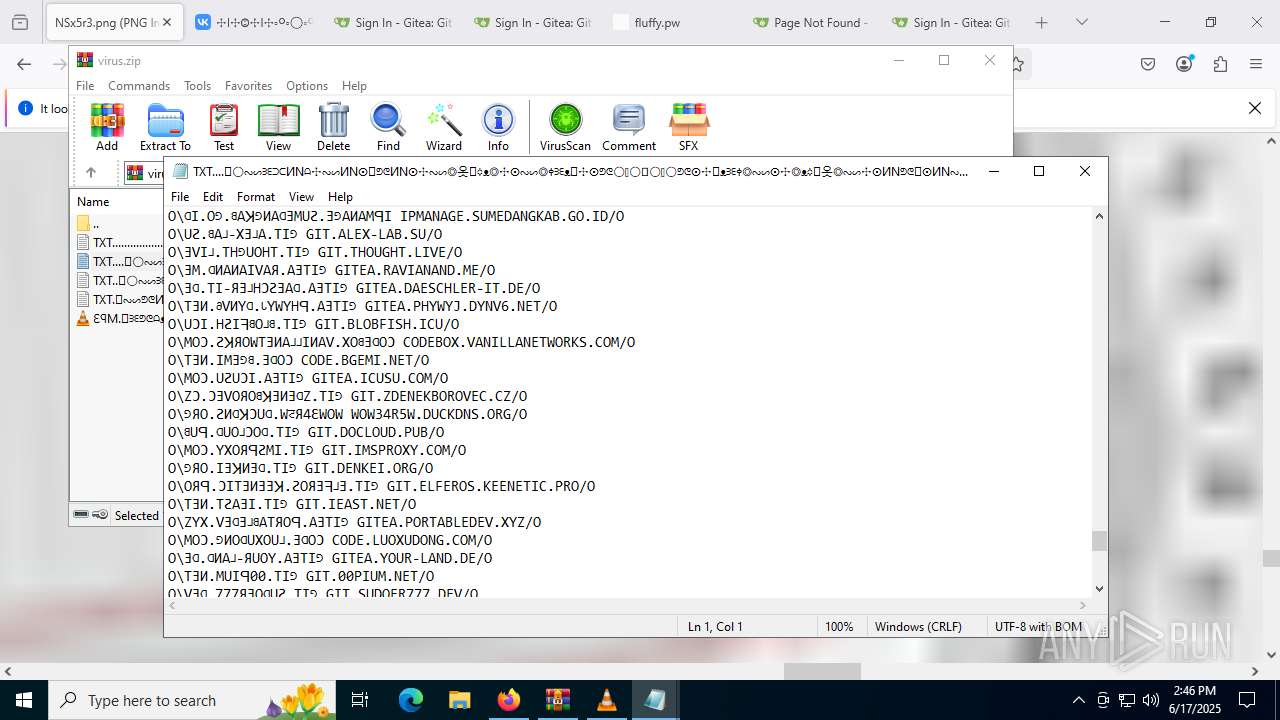
| ZipFileName: | TXT......................𖣠......................TXT |
Total processes
175
Monitored processes
38
Malicious processes
1
Suspicious processes
0
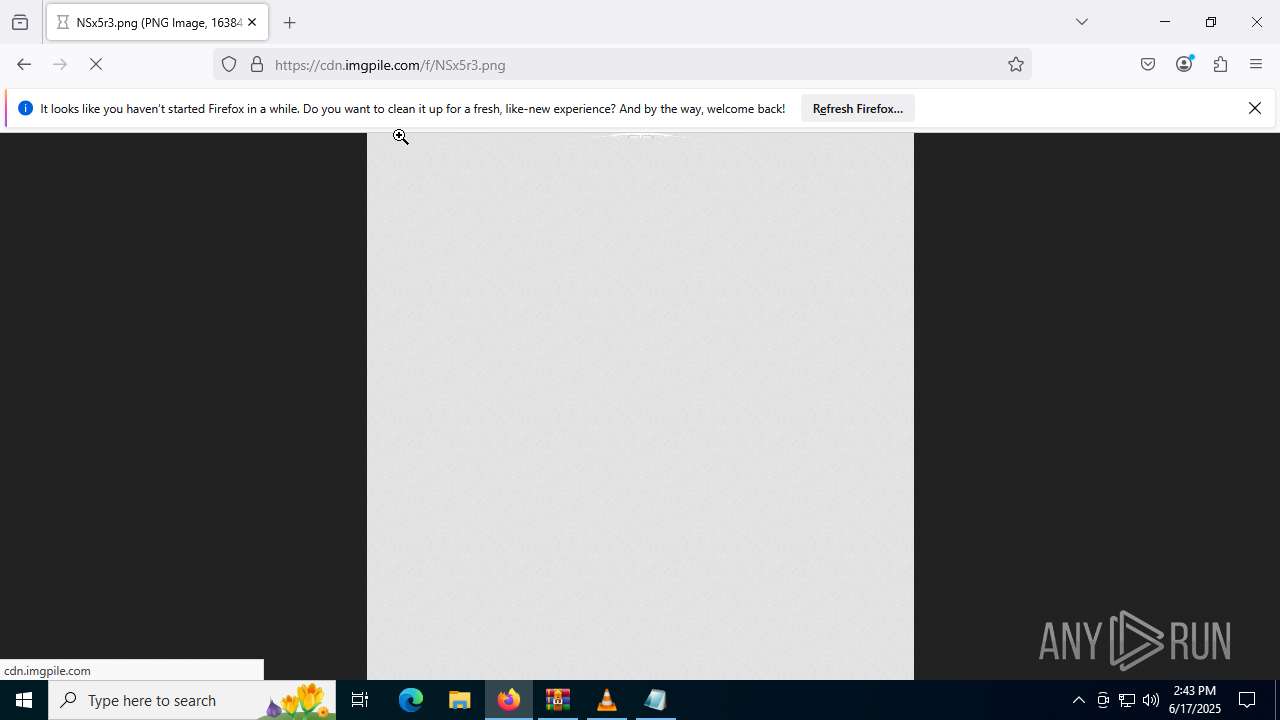
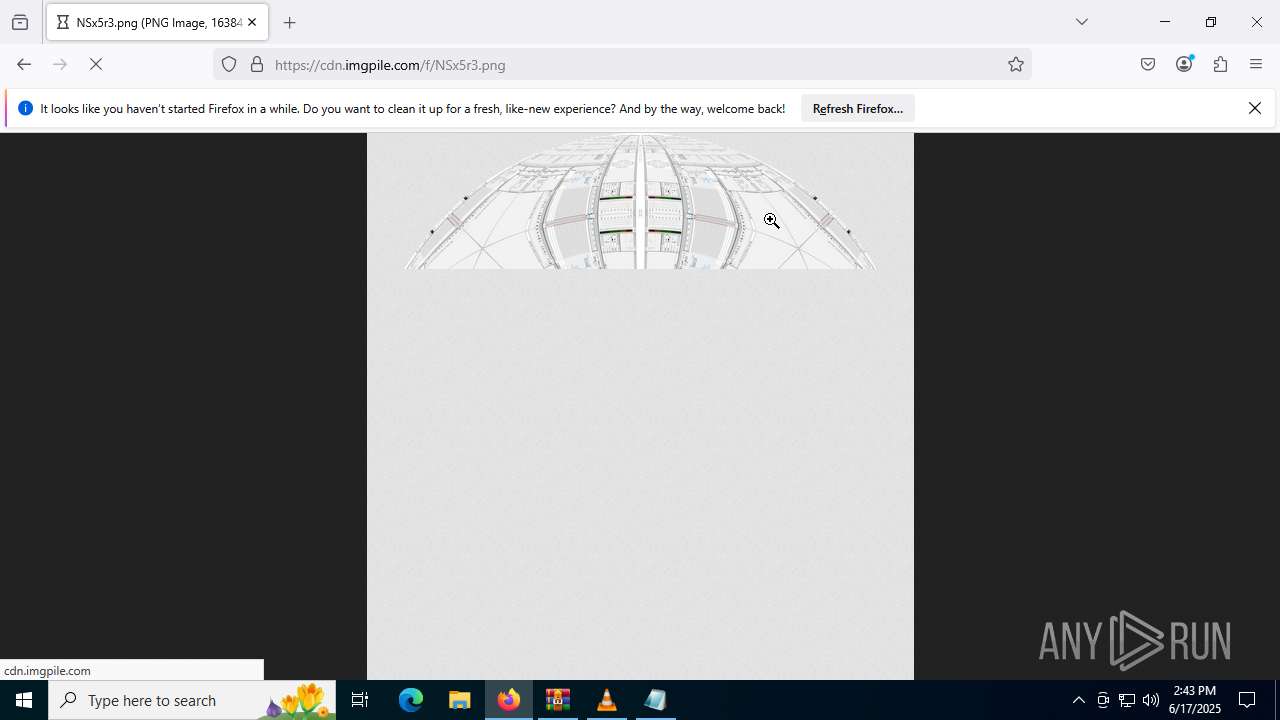
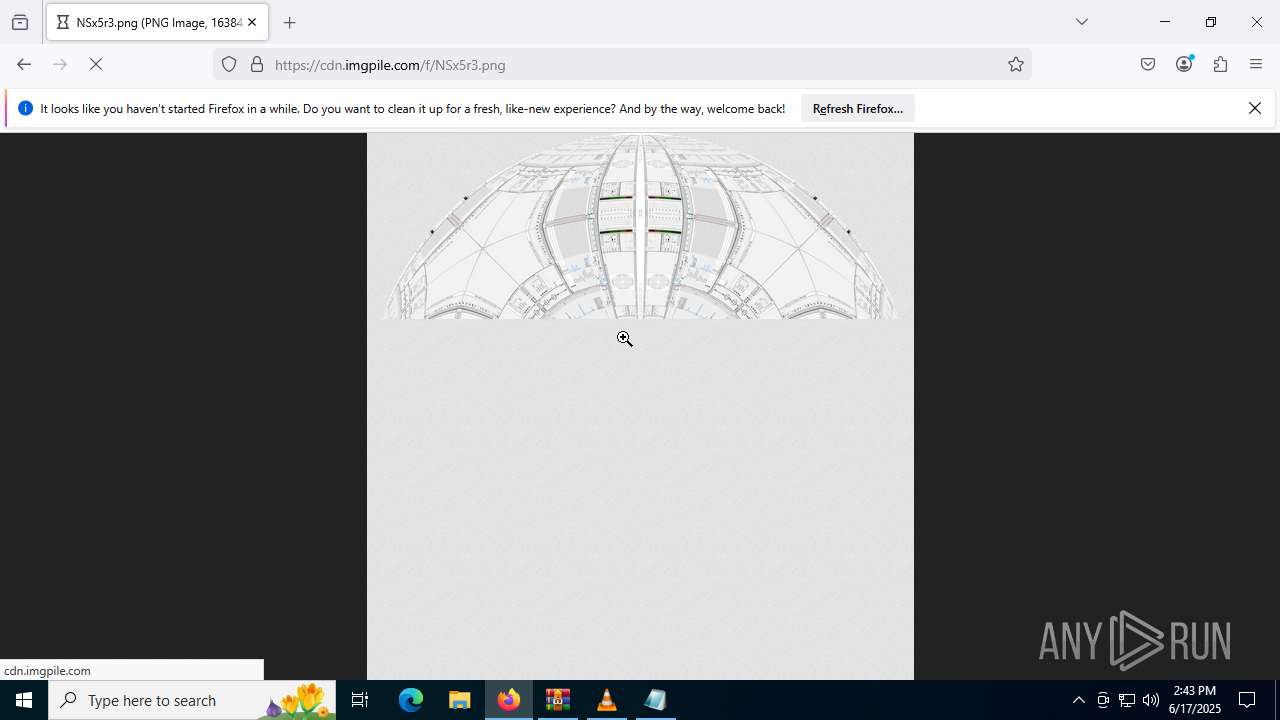
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 640 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa4676.15539\TXTNNN~1.TXT | C:\Windows\System32\notepad.exe | — | WinRAR.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1028 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 | ||||
| 1488 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 5292 -prefsLen 39068 -prefMapHandle 5328 -prefMapSize 272997 -jsInitHandle 5332 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 5340 -initialChannelId {7515c78d-002d-4381-8298-bde61a1a66de} -parentPid 1028 -crashReporter "\\.\pipe\gecko-crash-server-pipe.1028" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 9 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 | ||||
| 1564 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -prefsHandle 1976 -prefsLen 36520 -prefMapHandle 1980 -prefMapSize 272997 -ipcHandle 2040 -initialChannelId {e1e19580-ccab-48ca-8f63-fa696b0a6e34} -parentPid 1028 -crashReporter "\\.\pipe\gecko-crash-server-pipe.1028" -appDir "C:\Program Files\Mozilla Firefox\browser" - 1 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 | ||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | |
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 2272 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 4320 -prefsLen 39438 -prefMapHandle 6784 -prefMapSize 272997 -jsInitHandle 6828 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 6412 -initialChannelId {a4b32cc0-b04c-4a95-85f3-d72ab9841cd8} -parentPid 1028 -crashReporter "\\.\pipe\gecko-crash-server-pipe.1028" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 23 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 | ||||
| 2368 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\AppData\Local\Temp\Rar$DIa4676.13133\MEE78~1.MP3" | C:\Program Files\VideoLAN\VLC\vlc.exe | WinRAR.exe | |
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Version: 3.0.11 | ||||
| 3584 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -prefsHandle 2212 -prefsLen 36520 -prefMapHandle 2216 -prefMapSize 272997 -ipcHandle 2224 -initialChannelId {d73bb9cb-0963-4af0-a8f0-8ddd94dfe286} -parentPid 1028 -crashReporter "\\.\pipe\gecko-crash-server-pipe.1028" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 2 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 | ||||
| 3864 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 4820 -prefsLen 39149 -prefMapHandle 4816 -prefMapSize 272997 -jsInitHandle 4928 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 5396 -initialChannelId {b2505077-d912-4664-9a0e-67489767ea8f} -parentPid 1028 -crashReporter "\\.\pipe\gecko-crash-server-pipe.1028" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 10 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 | ||||
| 3876 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 5608 -prefsLen 39438 -prefMapHandle 5788 -prefMapSize 272997 -jsInitHandle 4328 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 6376 -initialChannelId {2c0eb4ed-19a5-4601-afa3-d71b026fa2ac} -parentPid 1028 -crashReporter "\\.\pipe\gecko-crash-server-pipe.1028" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 17 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
177
Text files
55
Unknown types
151
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa4676.16930\TXT......................𖣠......................TXT | text | |
MD5:A362B970963B175F0537B08E3CB2F671 | SHA256:B2EB8BAC12BBE57D3EF95BEE7A5C115DBCB2E970231FEBB5578A5998BF4CDC21 | |||
| 2368 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.cF2368 | ini | |
MD5:5A1B856C97E5589DBECD4A55775FFF74 | SHA256:5FE1D2474BCF41679651013020FA80BC2A7C8D8D26FF6D536AA46B19E74DFBFA | |||
| 2368 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.lock | text | |
MD5:9325214658BFDE150F3BC5F09028B442 | SHA256:0EF7C217EEA5838AE4CD54423257704CE7FA194A72D2431E8EDDB21EE6220F29 | |||
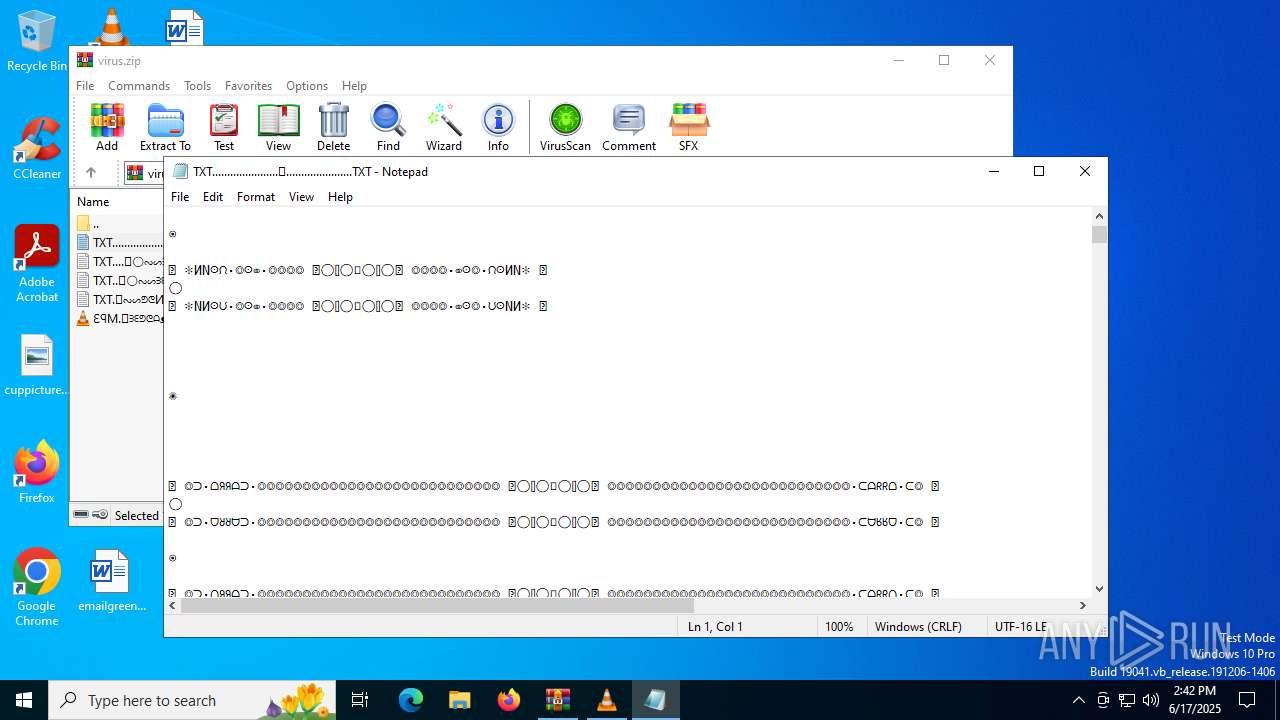
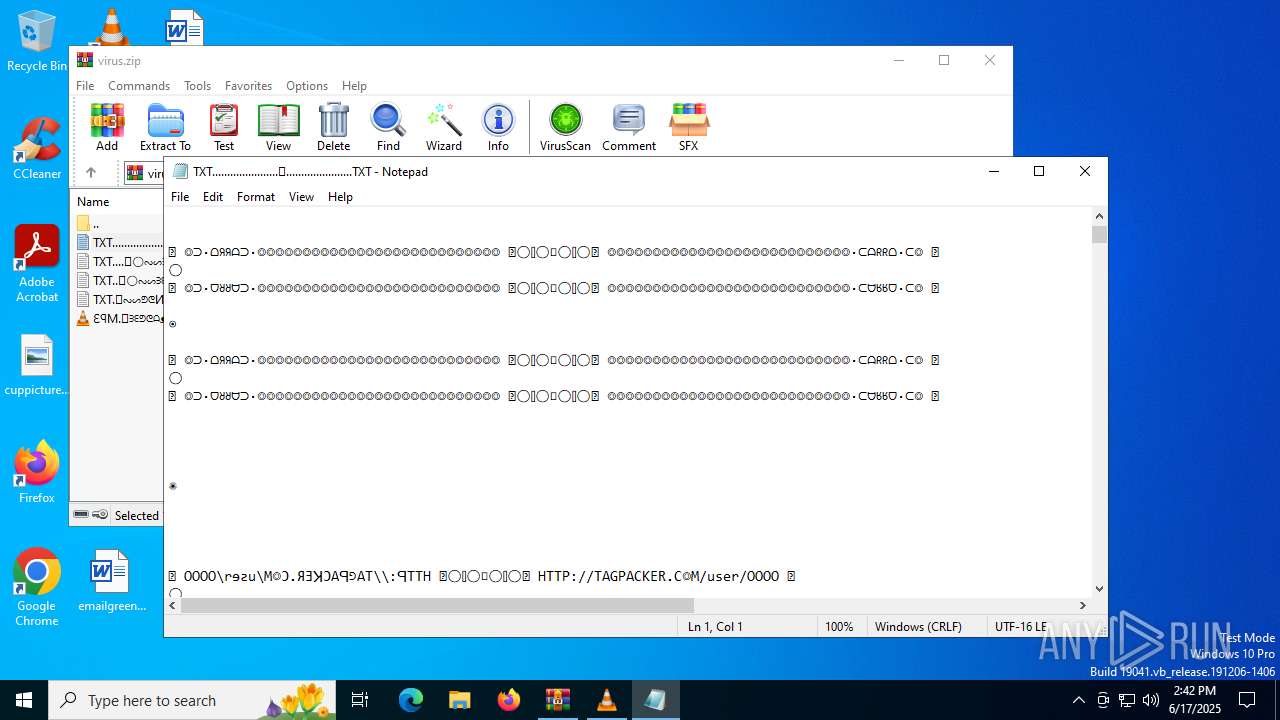
| 4676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa4676.13133\ԐꟼM.𖣠ᗱᗴᕤᕦᗩᴥᗱᗴᗯᗩ𖣠᳀𖣠𖢌𐧼𐧾ⵔ∶⸭❋ⵔⵔ𐧾❋❋ⵔ❋·𐧾❋❋ⵈ𐧾❋ⵔ𐧾❋∶ⵔⵔⵔ·𐧾ⵔ∶𐧾ⵔ𐧼··𐧾𐧾❋❋⠿𐧼ⵔⵈⵔ⁘⸭𐧾𐧾❋⸭∶∶ⵔ⠿ⵔ⁘◌⁘❋𖣠◦୦◦ⵔ◦୦◦◯◦୦◦ⵔ◦୦◦⠀⠀⠀⠀⠀⠀⠀⚪⠀⠀⠀⠀⠀⠀⠀◦୦◦ⵔ◦୦◦◯◦୦◦ⵔ◦୦◦𖣠❋⁘◌⁘ⵔ⠿ⵔ∶∶⸭❋𐧾𐧾⸭⁘ⵔⵈⵔ𐧼⠿❋❋𐧾𐧾··𐧼ⵔ𐧾∶ⵔ𐧾·ⵔⵔⵔ∶❋𐧾ⵔ❋𐧾ⵈ❋❋𐧾·❋ⵔ❋❋𐧾ⵔⵔ❋⸭∶ⵔ𐧾𐧼𖢌𖣠᳀𖣠ᗩᗯᗱᗴᴥᗩᕤᕦᗱᗴ𖣠.MP3 | mp3 | |
MD5:5FA0657D2454A823A49F4938EC9E98B1 | SHA256:516BED1A8DE8F9F1492F39D114182A9FFF392F972F4D19BB3670E4388AB0A033 | |||
| 1028 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1028 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | bs | |
MD5:553953B02D168D4FF16987625DAF2EDF | SHA256:F2417B6B62D65A518722E4293C65F5C10DE3715A5CF0717DDEFFE7545EF253F7 | |||
| 2368 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini | ini | |
MD5:5A1B856C97E5589DBECD4A55775FFF74 | SHA256:5FE1D2474BCF41679651013020FA80BC2A7C8D8D26FF6D536AA46B19E74DFBFA | |||
| 1028 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 1028 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1028 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
62
TCP/UDP connections
199
DNS requests
259
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2464 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1760 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1760 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1028 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1028 | firefox.exe | POST | — | 142.250.186.131:80 | http://o.pki.goog/s/wr3/3H4 | unknown | — | — | whitelisted |
1028 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://o.pki.goog/s/wr3/3H4 | unknown | — | — | whitelisted |
1028 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2464 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2464 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
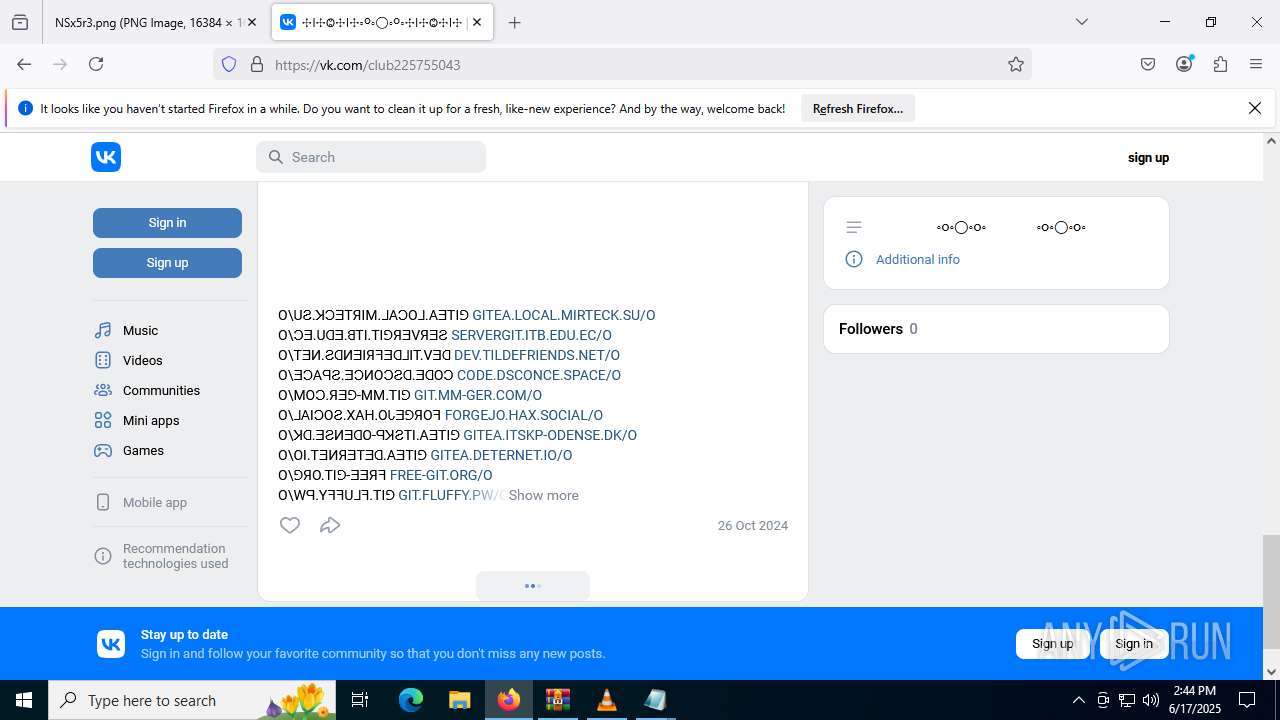
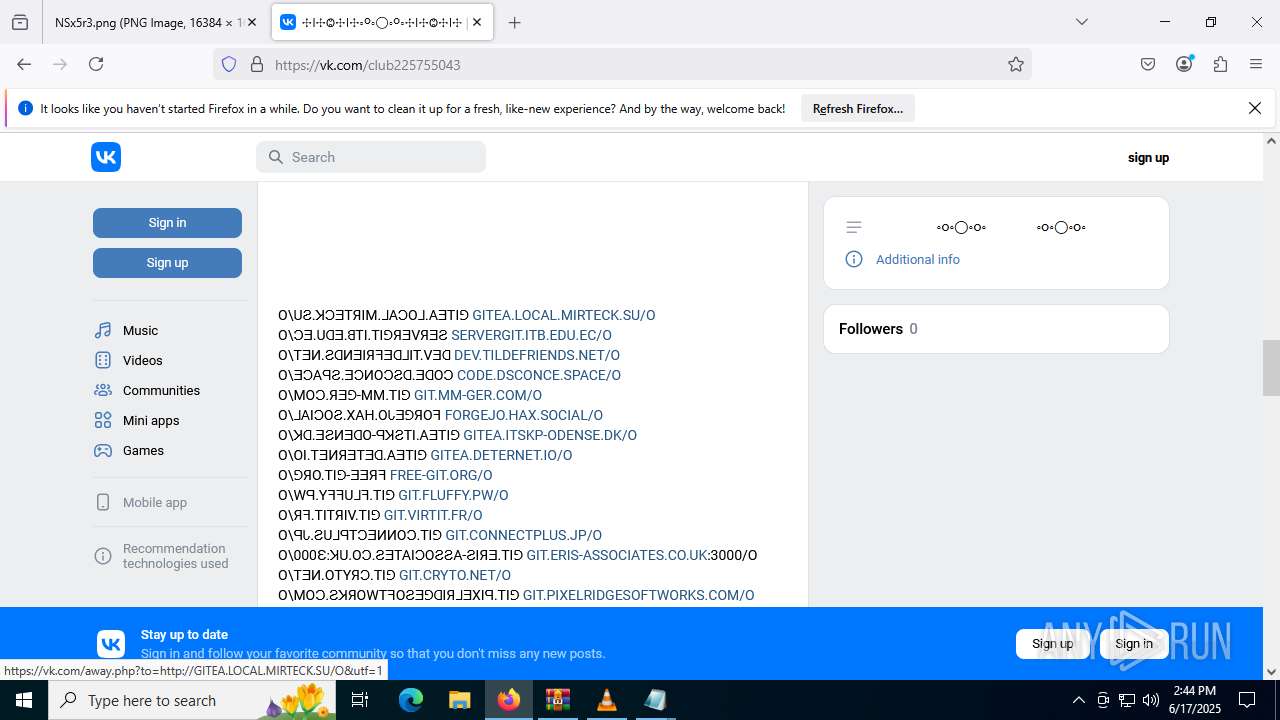
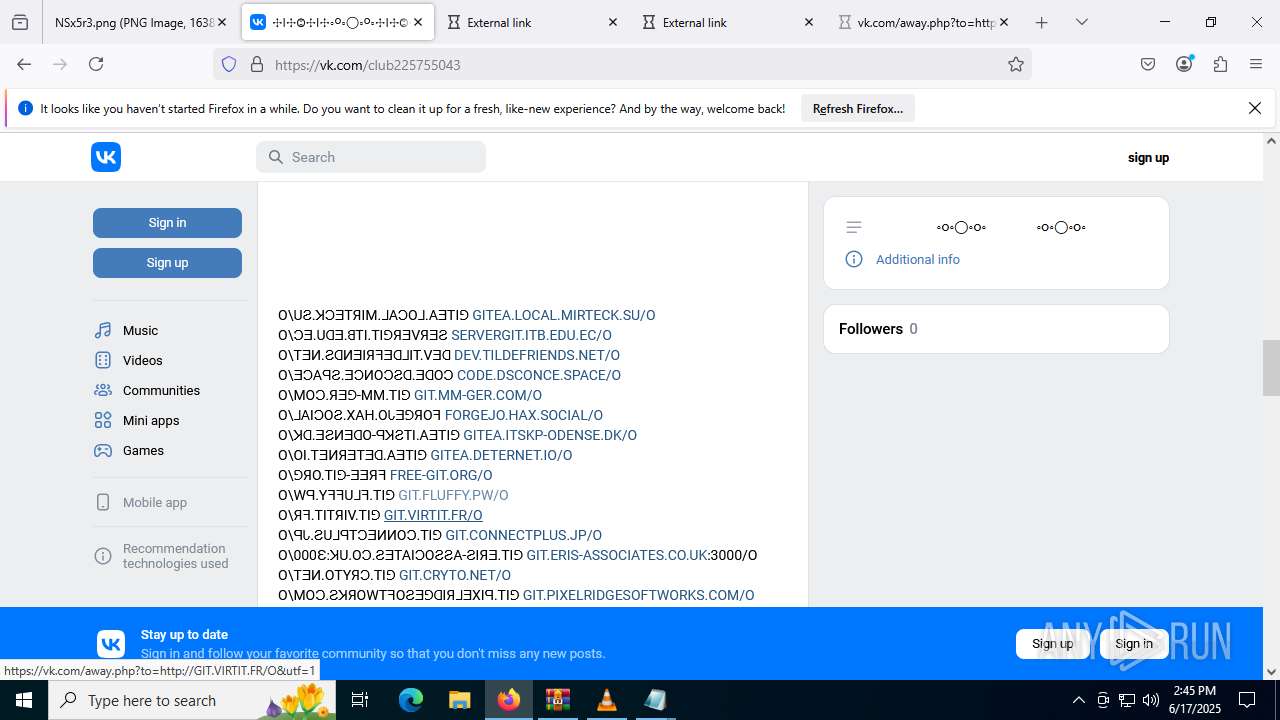
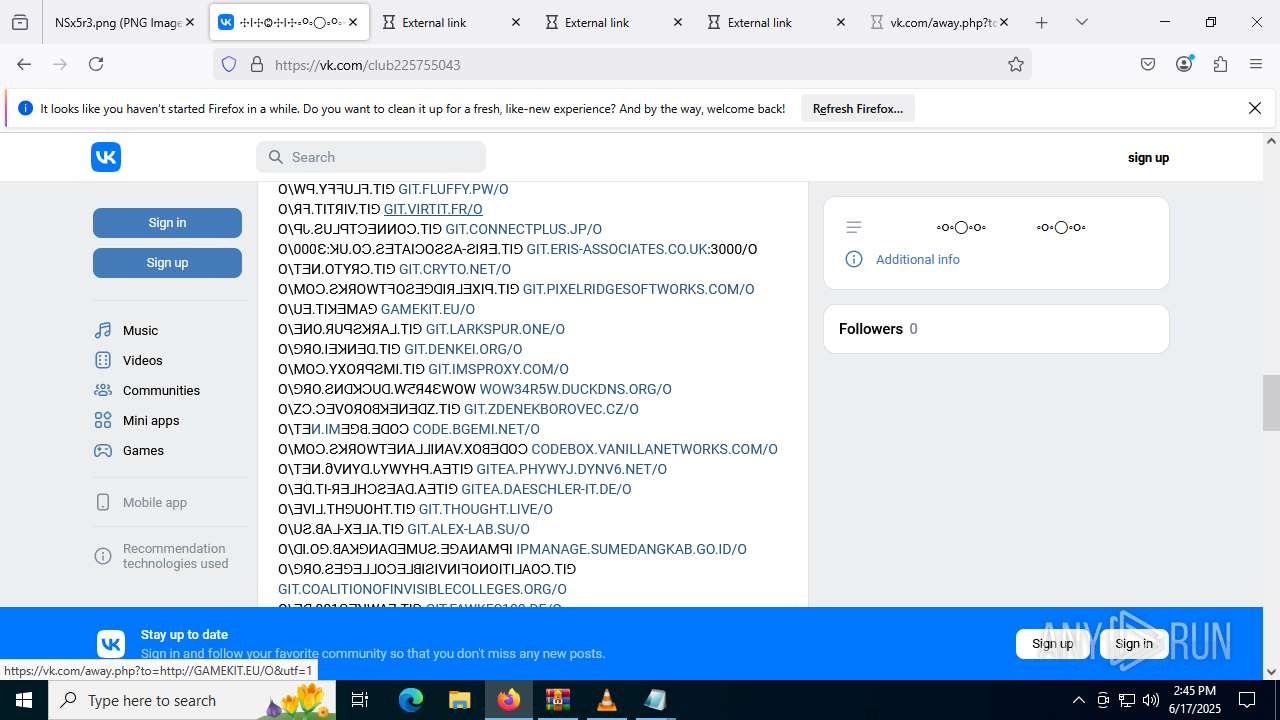
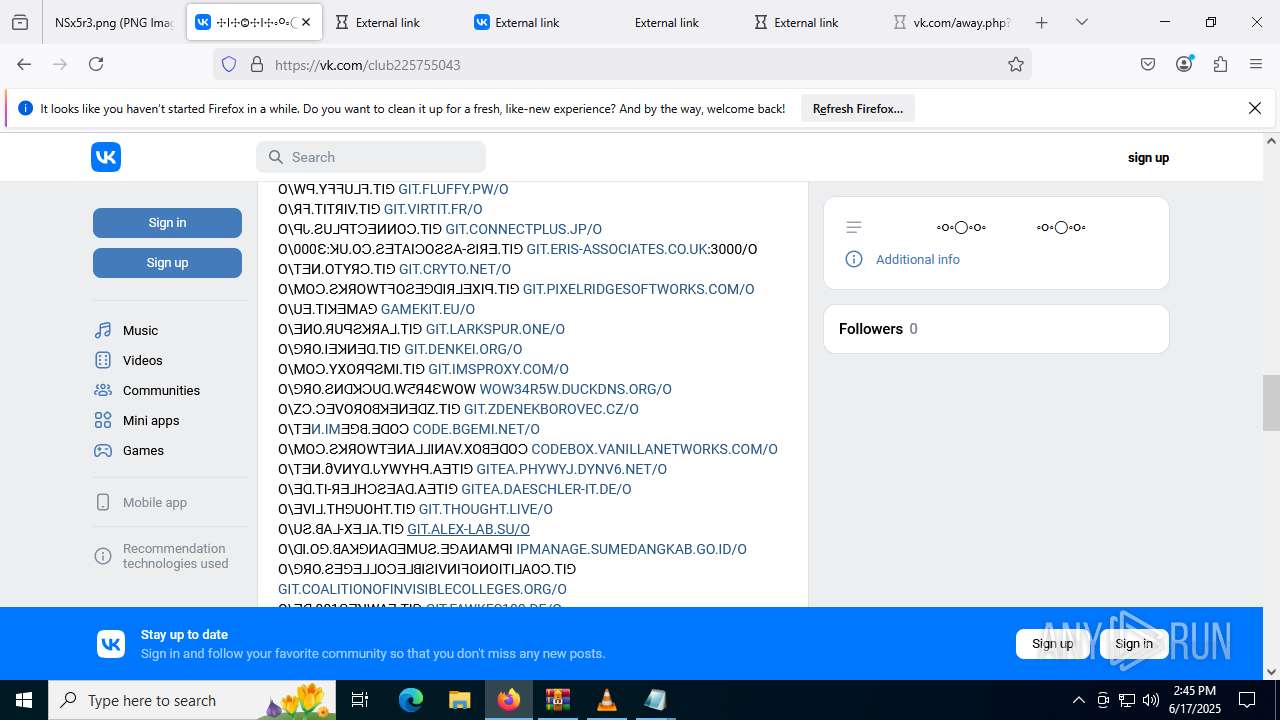
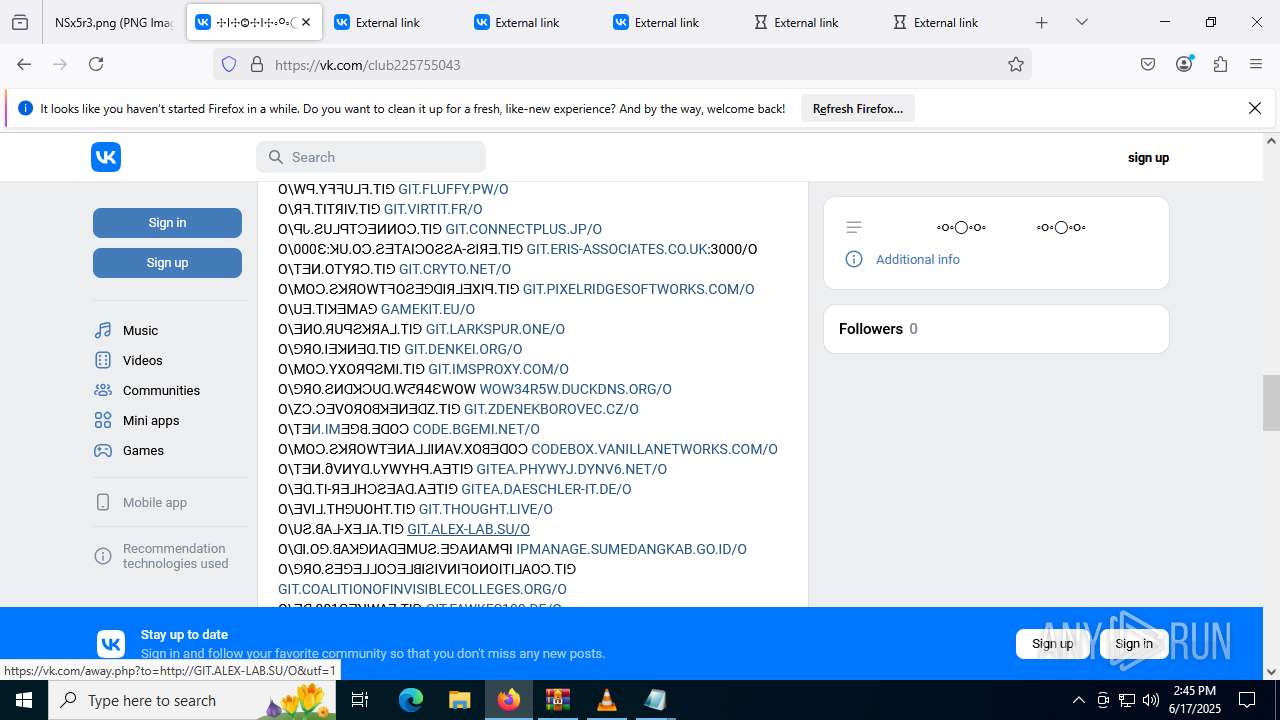
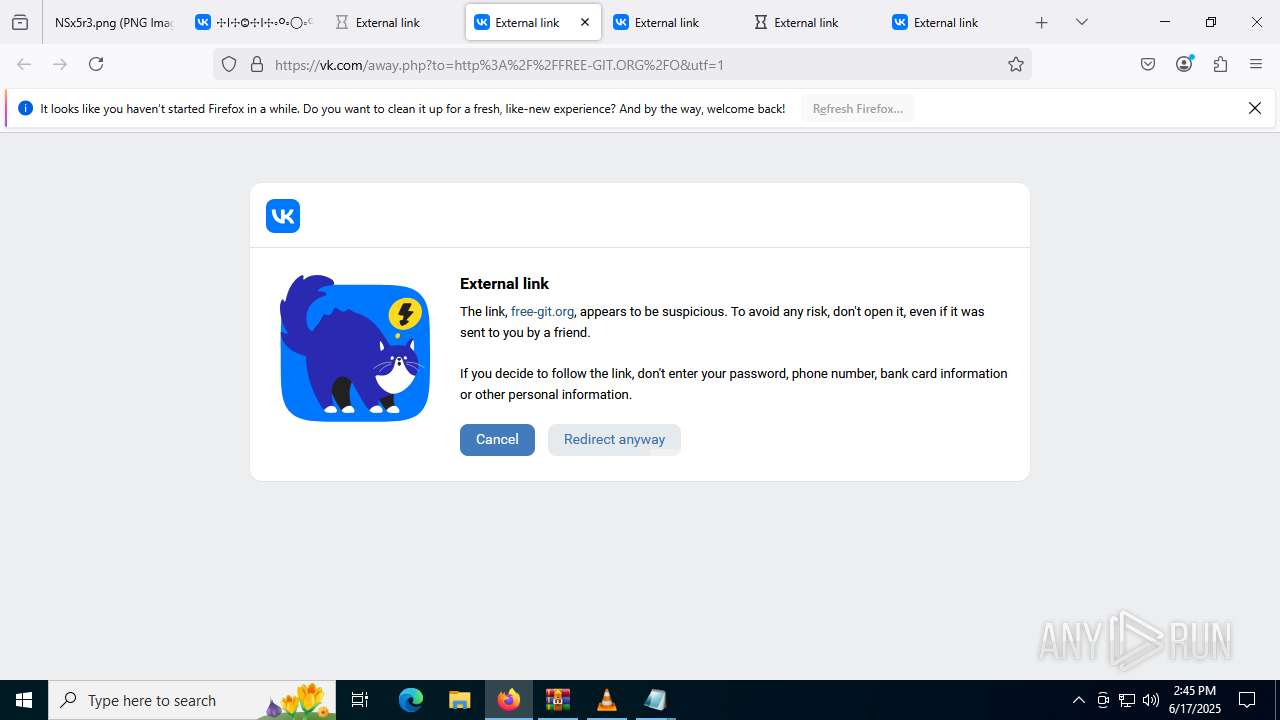
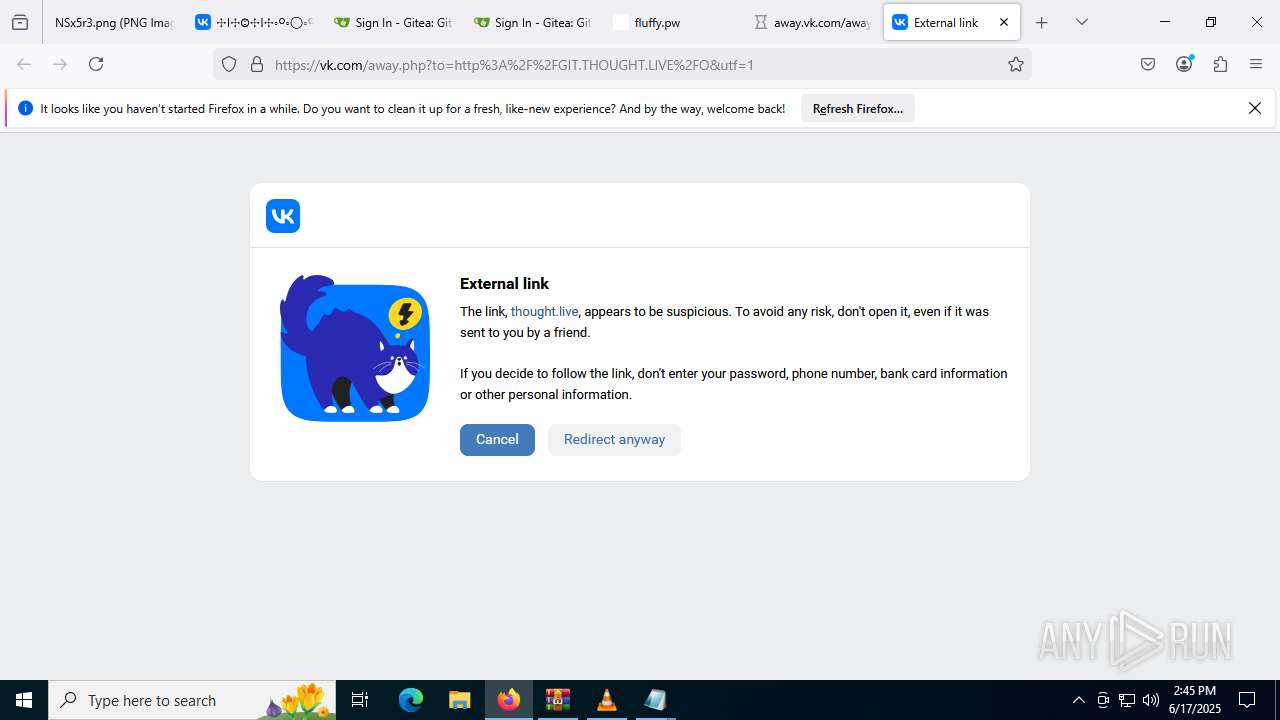
2200 | svchost.exe | Misc activity | ET INFO Observed DNS Query to vk .com API (api .vk .com) |
1028 | firefox.exe | Misc activity | ET INFO Observed vk .com API Domain (api .vk .com in TLS SNI) |
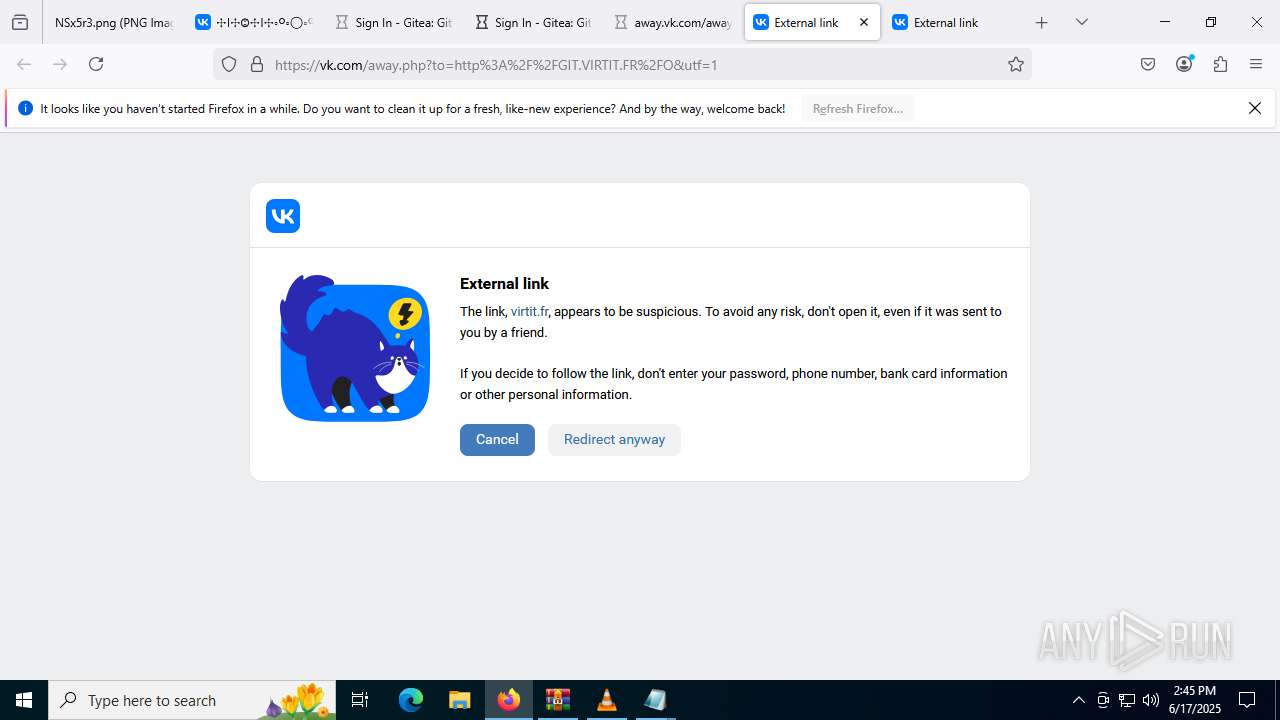
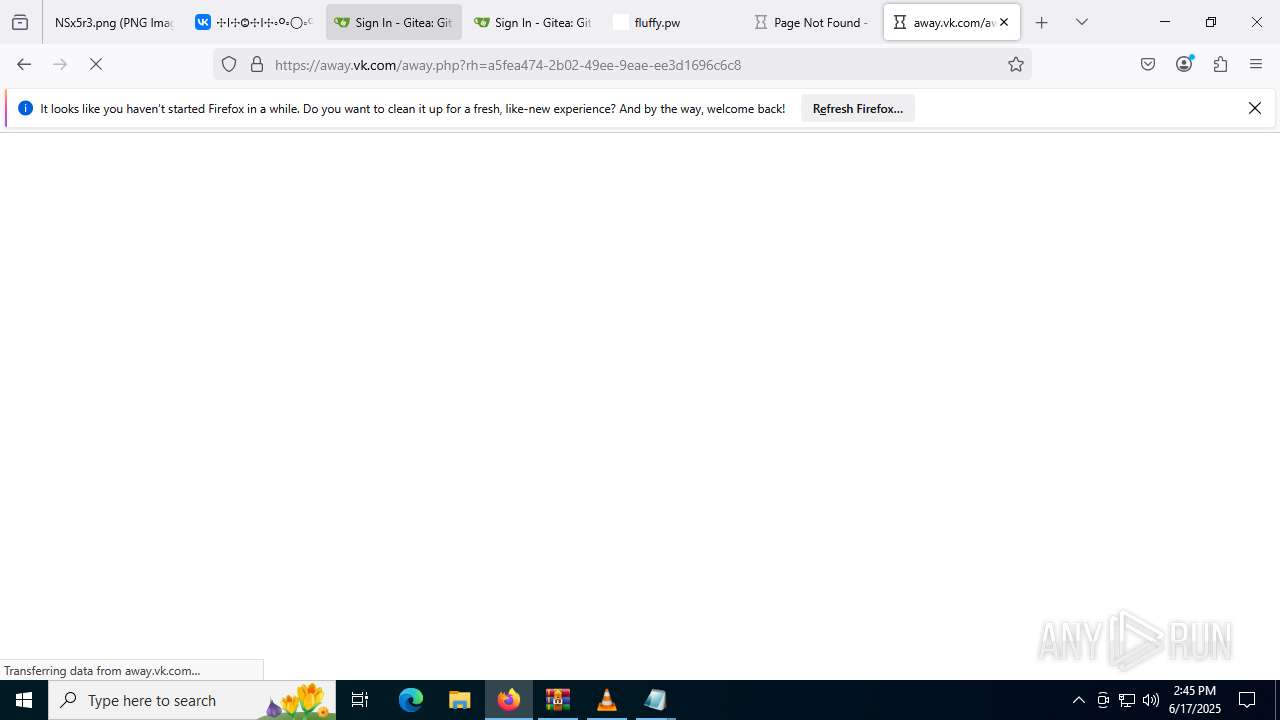
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] VK Redirect (away .vk .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] VK Redirect (away .vk .com) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] VK Redirect (away .vk .com) |
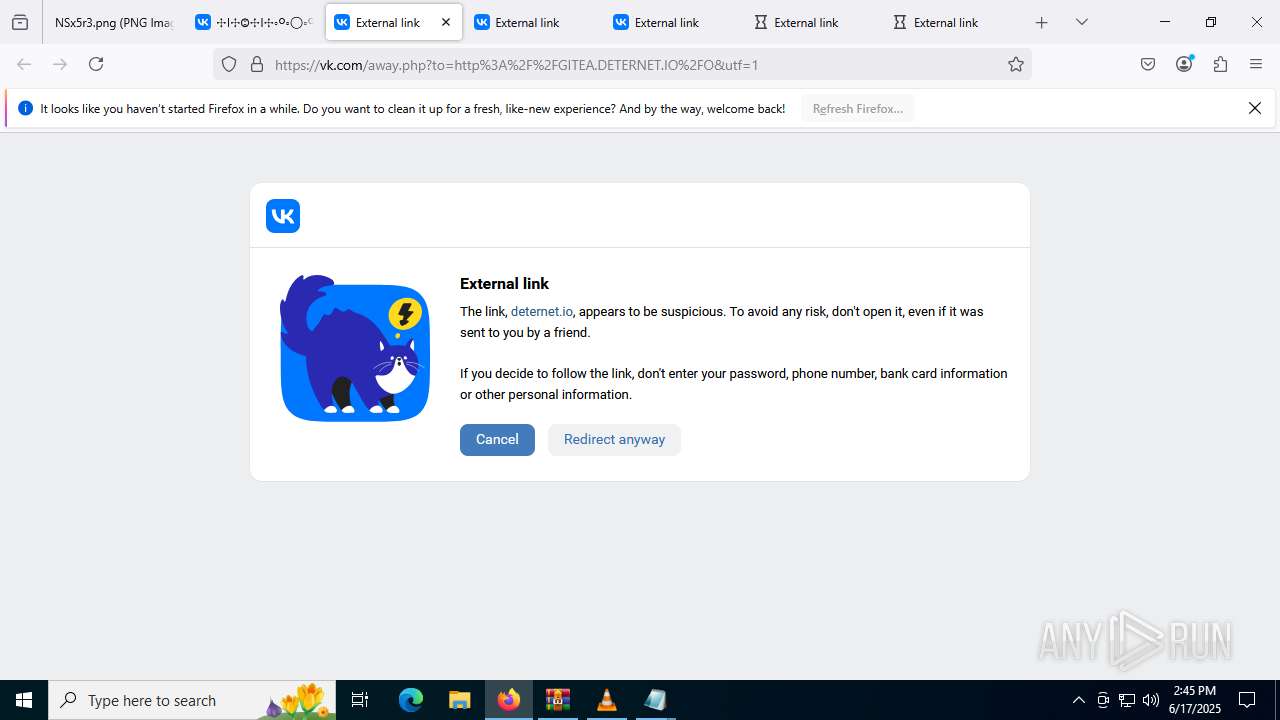
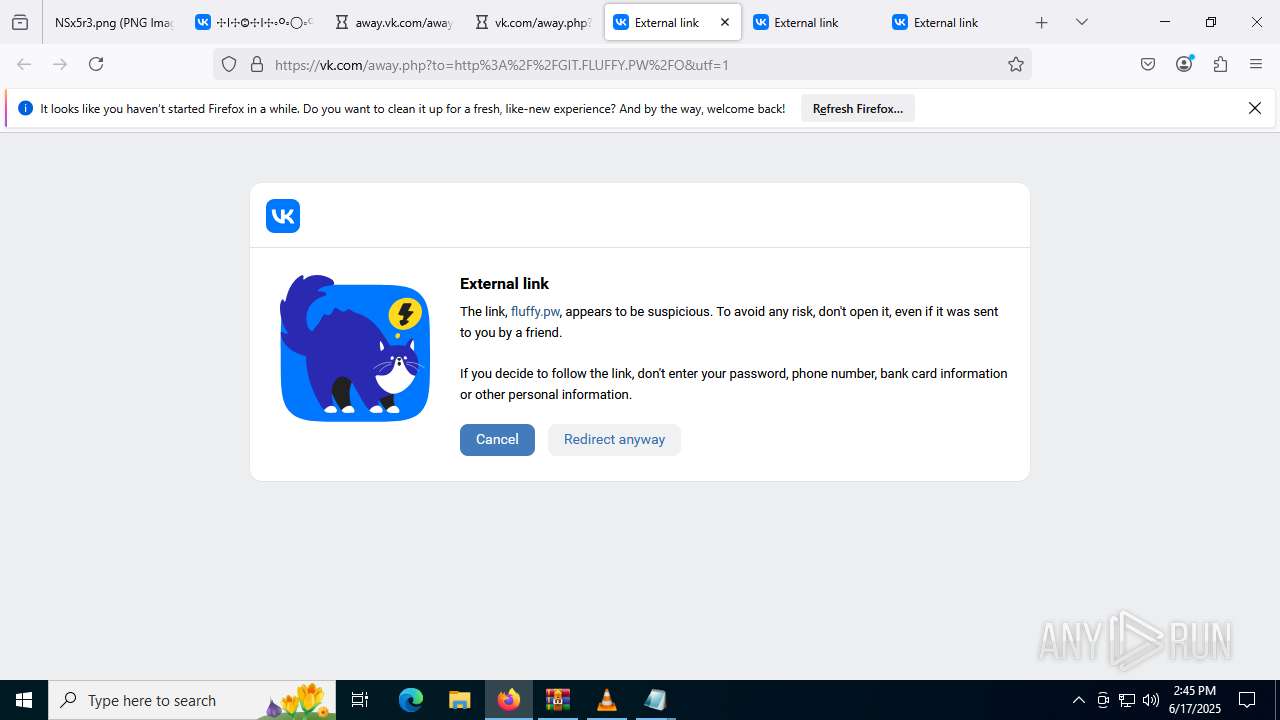
2200 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
2200 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
Process | Message |
|---|---|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=x86_64-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=x86_64-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x64/contrib/x86_64-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc debug: opening config file (C:\Users\admin\AppData\Roaming\vlc\vlcrc)
|