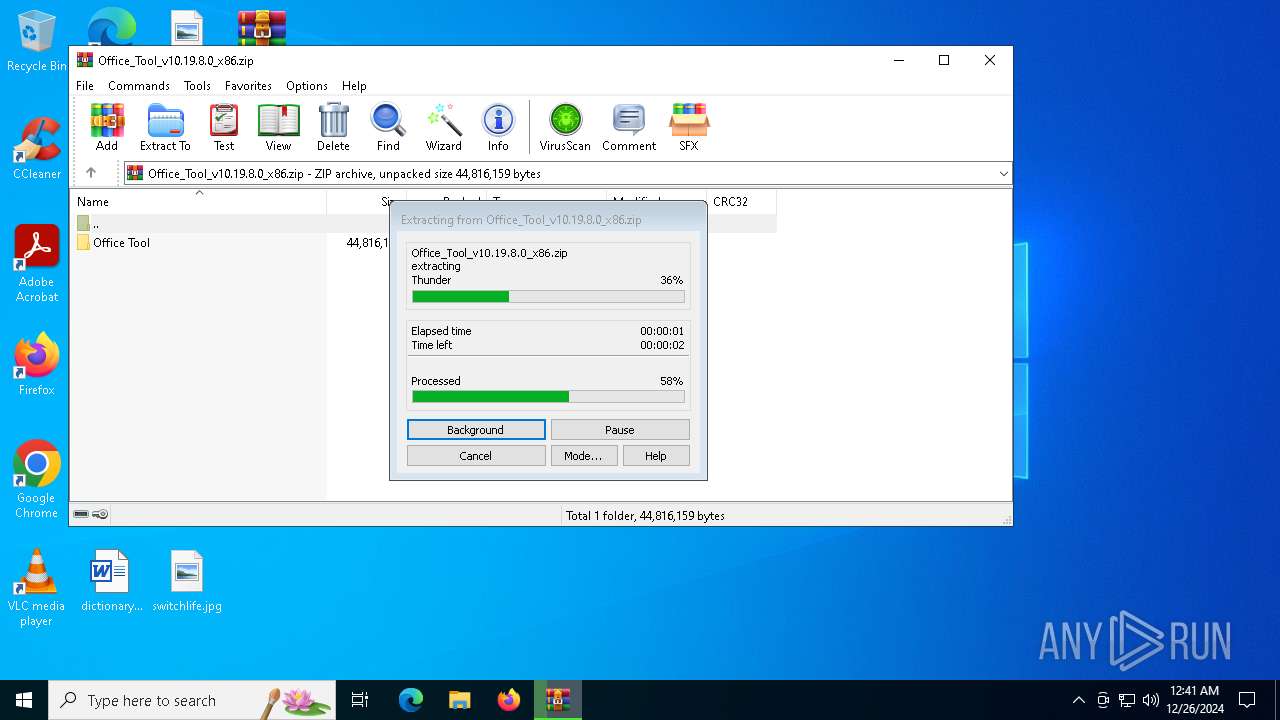
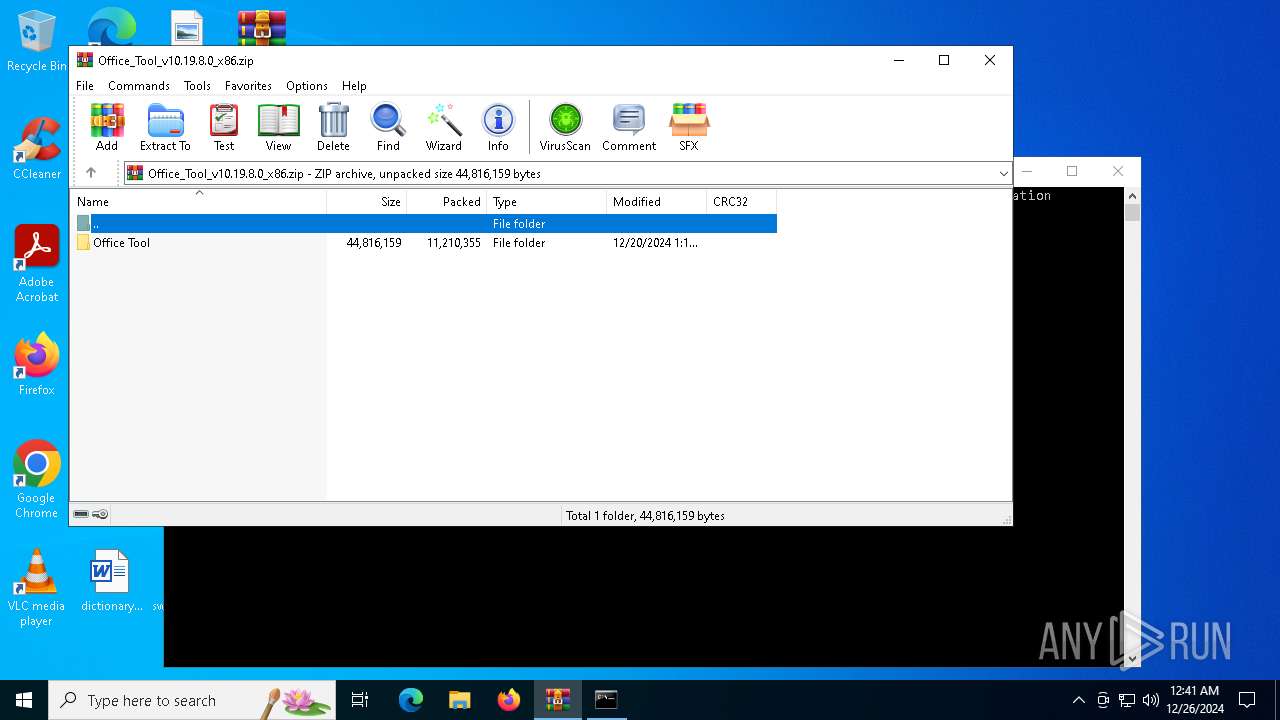
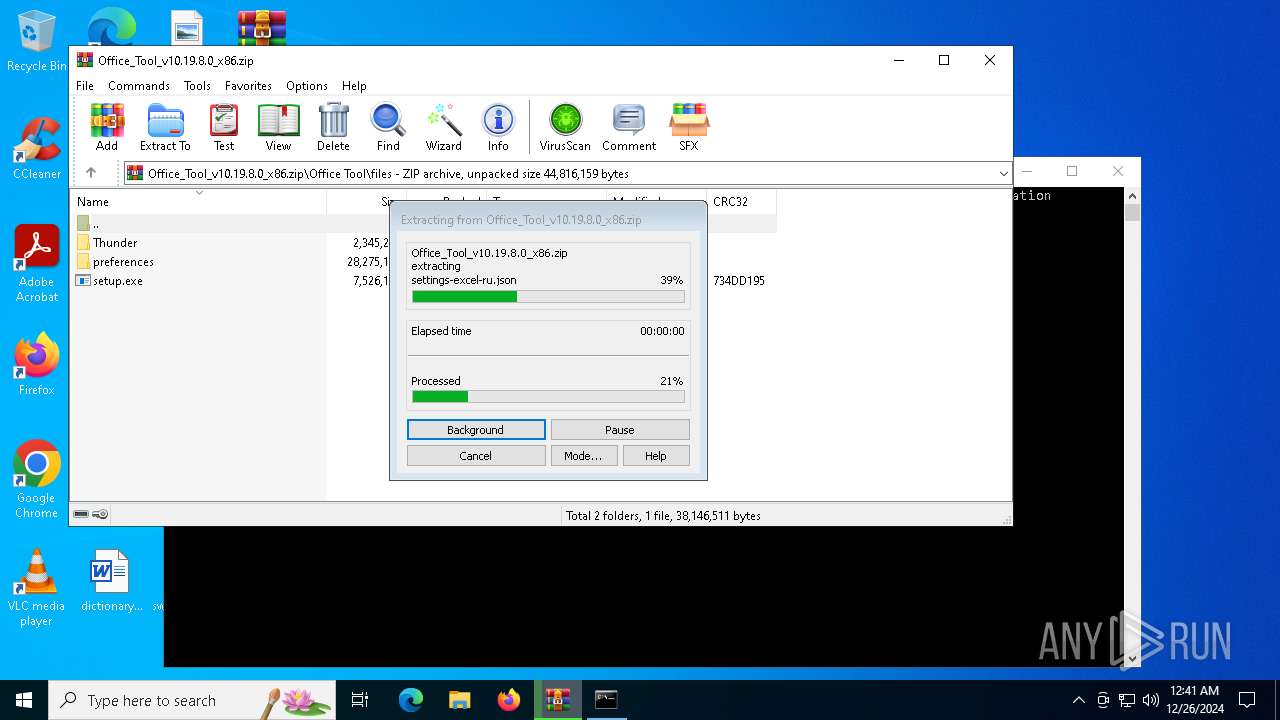
| File name: | Office_Tool_v10.19.8.0_x86.zip |
| Full analysis: | https://app.any.run/tasks/fd501b9f-1e43-4fd7-b90c-1c757f579320 |
| Verdict: | Malicious activity |
| Analysis date: | December 26, 2024, 00:40:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 1A080165968F8C6D5BEA7DBB98D5741E |
| SHA1: | AB1408A3ED0677435B7F6D6972165C0BE309946B |
| SHA256: | FFFC8524E1051816442A140EE5E451CAB9B1D5CF548CEE159CE3C8559DD34544 |
| SSDEEP: | 98304:nx7aPXkxd8cWQWsaynaRA+DTJ2hVe8rlDur4ypibqlHNOg09S0d1MbEPJoV6aUXD:tS8Z7bFw4qvaeFuy21UNfAO27Cm |
MALICIOUS
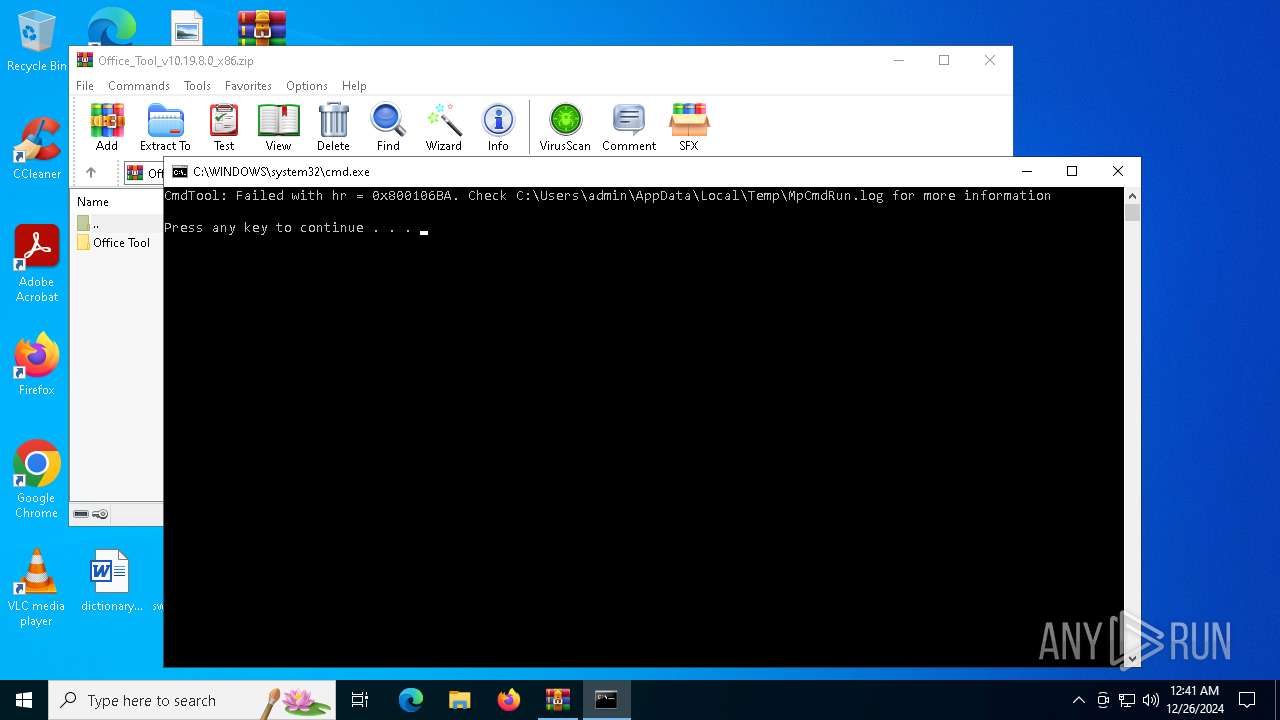
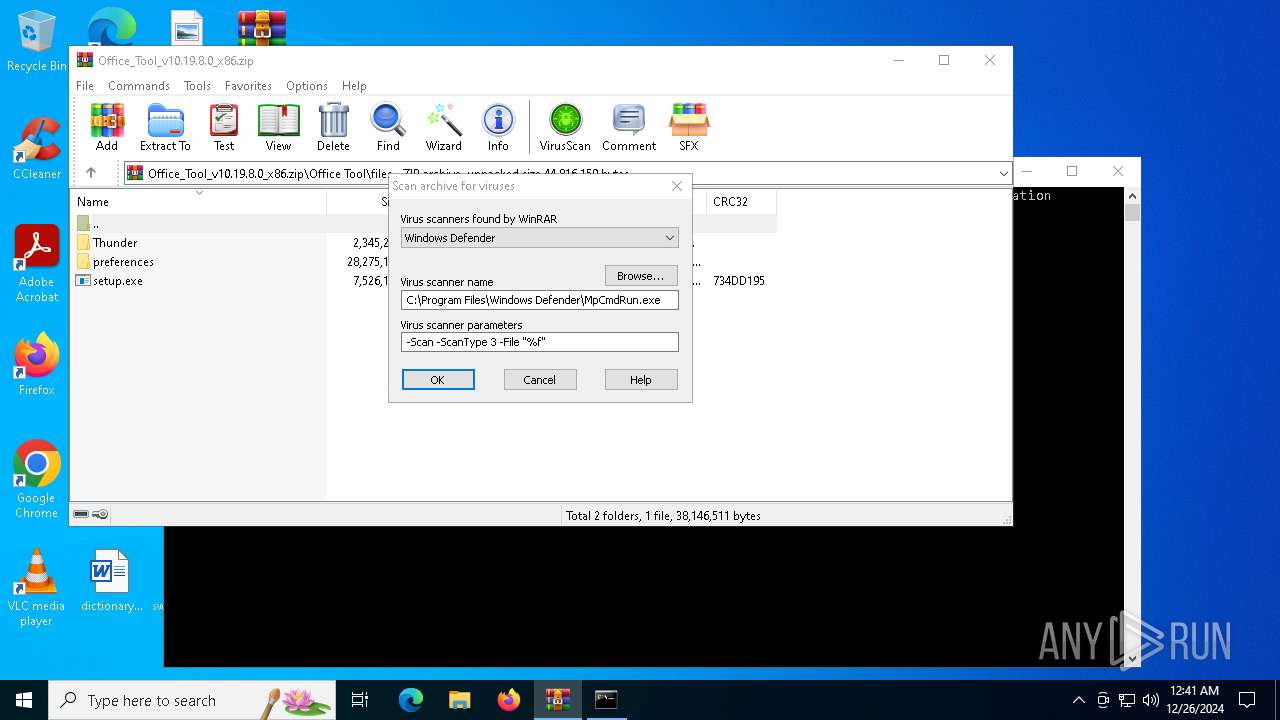
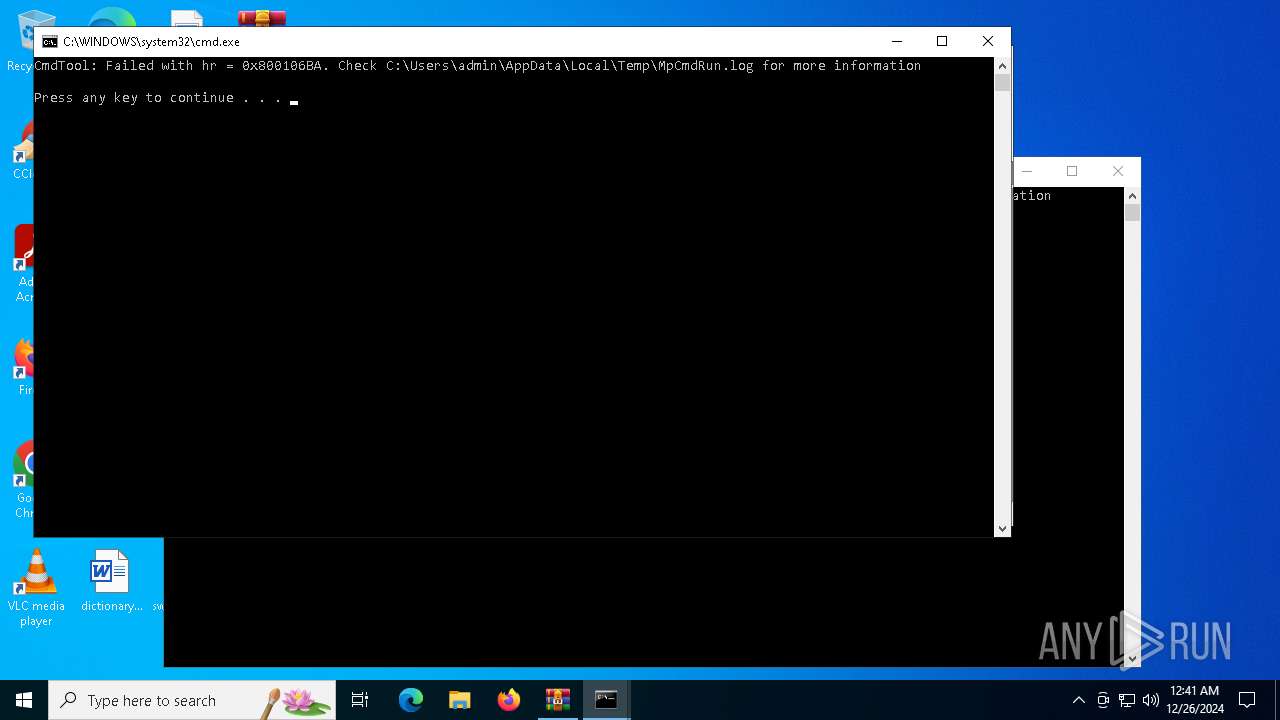
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 5920)
- MpCmdRun.exe (PID: 1596)
SUSPICIOUS
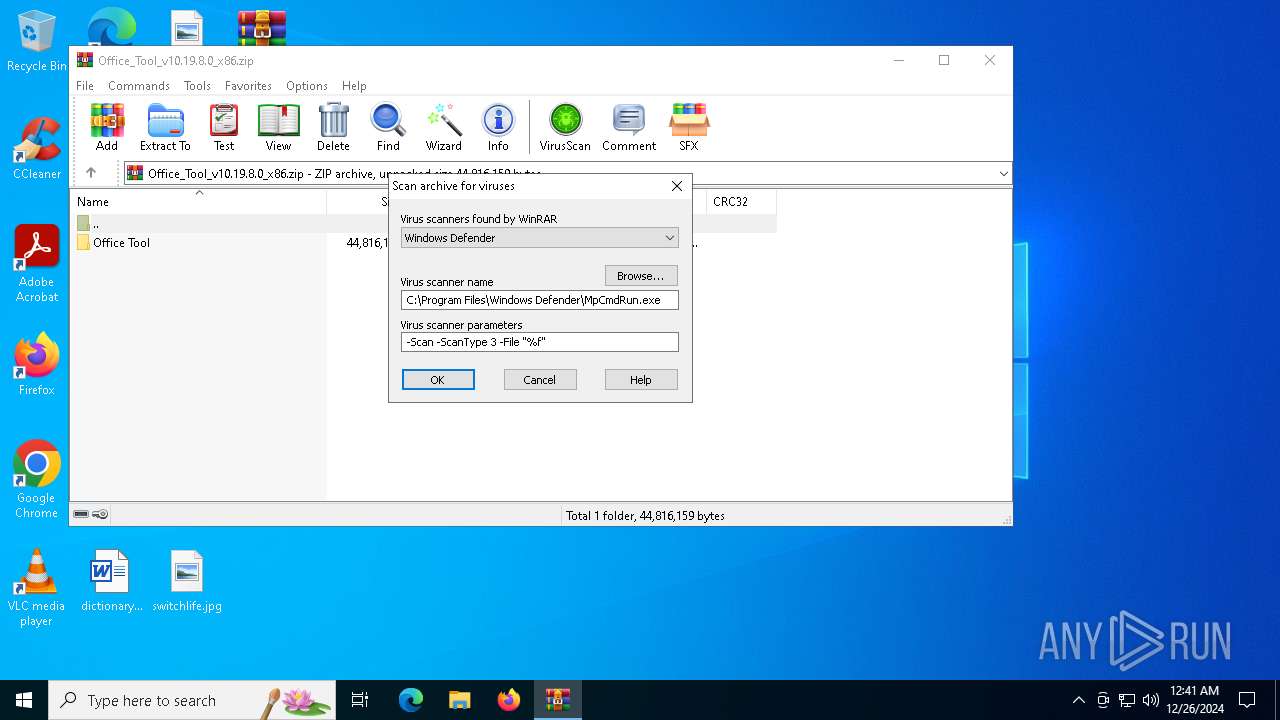
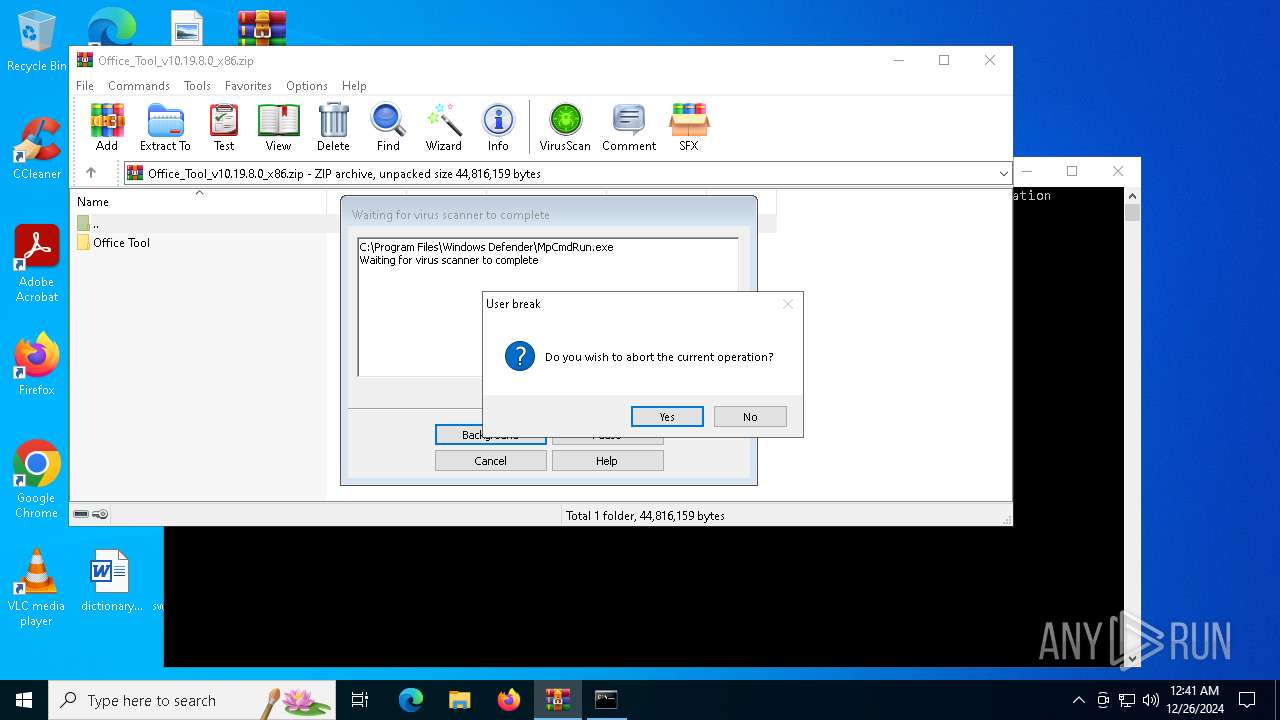
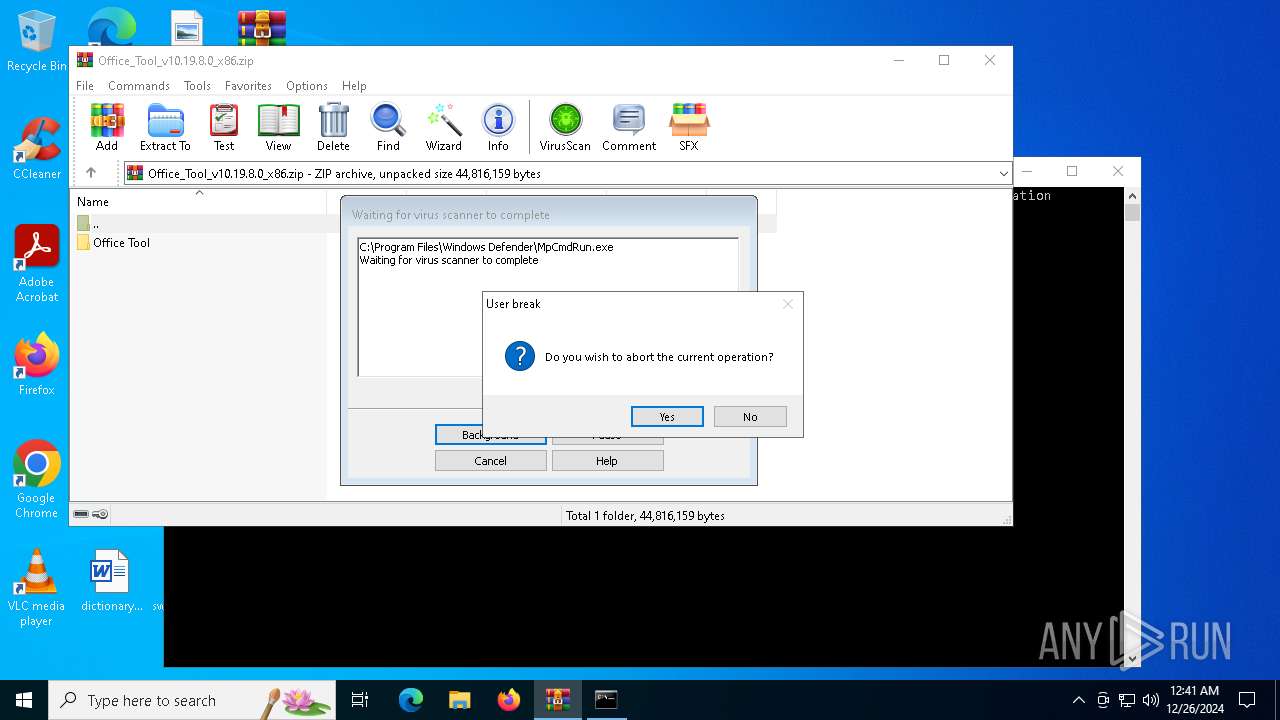
Executing commands from a ".bat" file
- WinRAR.exe (PID: 2324)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2324)
Process drops legitimate windows executable
- WinRAR.exe (PID: 2324)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2324)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 2324)
The sample compiled with chinese language support
- WinRAR.exe (PID: 2324)
Reads the computer name
- MpCmdRun.exe (PID: 5920)
- MpCmdRun.exe (PID: 1596)
Checks supported languages
- MpCmdRun.exe (PID: 5920)
- MpCmdRun.exe (PID: 1596)
Create files in a temporary directory
- MpCmdRun.exe (PID: 5920)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2324)
The process uses the downloaded file
- WinRAR.exe (PID: 2324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:20 21:12:50 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Office Tool/ |
Total processes
123
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 440 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Rar$Scan20957.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR2324.2254" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2224 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR2324.2254\Rar$Scan59480.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2324 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Office_Tool_v10.19.8.0_x86.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5920 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 802
Read events
1 791
Write events
11
Delete events
0
Modification events
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Office_Tool_v10.19.8.0_x86.zip | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
| (PID) Process: | (2324) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
Executable files
22
Suspicious files
240
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Office_Tool_v10.19.8.0_x86.zip\Office Tool\files\preferences\de-de\settings-ppt-de.json | binary | |
MD5:BEF06470E92E22EDC91A97C9454FD7B1 | SHA256:D91BE6A192241B4BAE94D9686D5031DFAA71E76E8B2C5025C8DC0CF075F19366 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Office_Tool_v10.19.8.0_x86.zip\Office Tool\files\preferences\en-us\settings-access-en.json | binary | |
MD5:9B3421B90762AB9CA88FD94B984DF334 | SHA256:697AE3F1C93F502D0B054D872837D9A8C6C3622FCA80C6A95ABBC3D27445E367 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Office_Tool_v10.19.8.0_x86.zip\Office Tool\files\preferences\de-de\settings-onent-de.json | binary | |
MD5:95A143A1B983DC509E16D575AC75CD38 | SHA256:41E3B906A846FDA1080FF2A945B01D4F02057A60A7C2F7D75EACD8E5DADE854C | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Office_Tool_v10.19.8.0_x86.zip\Office Tool\files\preferences\de-de\settings-pub-de.json | binary | |
MD5:94AAD9D532C21C23DE2FC8D9786536F6 | SHA256:8BAEFAD9352621F0ECD979083307FB3A4B6953C62CCA2111F47941C5C145F045 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Office_Tool_v10.19.8.0_x86.zip\Office Tool\files\preferences\de-de\settings-visio-de.json | binary | |
MD5:9A9AAC09AB29A8DB7723F2F8F1E67F74 | SHA256:1782F419435994169C862A6FC43420267D1E061D1B9A56EB248200E614A78254 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Office_Tool_v10.19.8.0_x86.zip\Office Tool\files\preferences\de-de\settings-outlk-de.json | binary | |
MD5:4BF4245AD197A930F4B0C03EBE0A3BDD | SHA256:0AFB82ABB950F0A3F9E0EED3BFEC7755751437110A22FF201E44490557A4609D | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Office_Tool_v10.19.8.0_x86.zip\Office Tool\files\preferences\de-de\settings-excel-de.json | binary | |
MD5:A5A2DDB5D679F8A91C89BAB337E3567F | SHA256:81F5FBD601534D6F9F19840732FCC7E973841F72036760DE5CD73CFD4E3DA9F9 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Office_Tool_v10.19.8.0_x86.zip\Office Tool\files\preferences\en-us\settings-excel-en.json | binary | |
MD5:53153B275FE2E3B98FED64E326EDEA49 | SHA256:4E279447B20FD37D8AABB7C25E992075279B02B952D0453C2BDBD90752209520 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Office_Tool_v10.19.8.0_x86.zip\Office Tool\files\preferences\en-us\settings-outlk-en.json | binary | |
MD5:C5E54A5738E7E6E58ED1B5B54E667BB2 | SHA256:9D8F42416E3BE31637FDECC4719F0B4C669F865C976122B798179148FCE2B910 | |||
| 2324 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR2324.48381\Office_Tool_v10.19.8.0_x86.zip\Office Tool\files\preferences\en-us\settings-visio-en.json | binary | |
MD5:0B71E07EC1F18A0862789E1299741604 | SHA256:7D039AA358EA1D2996C4249E2B87A344474C16E50D50AE7C2011AA3ECEE77D10 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6068 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6068 | svchost.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6068 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.212.110.152:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6068 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
6068 | svchost.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |