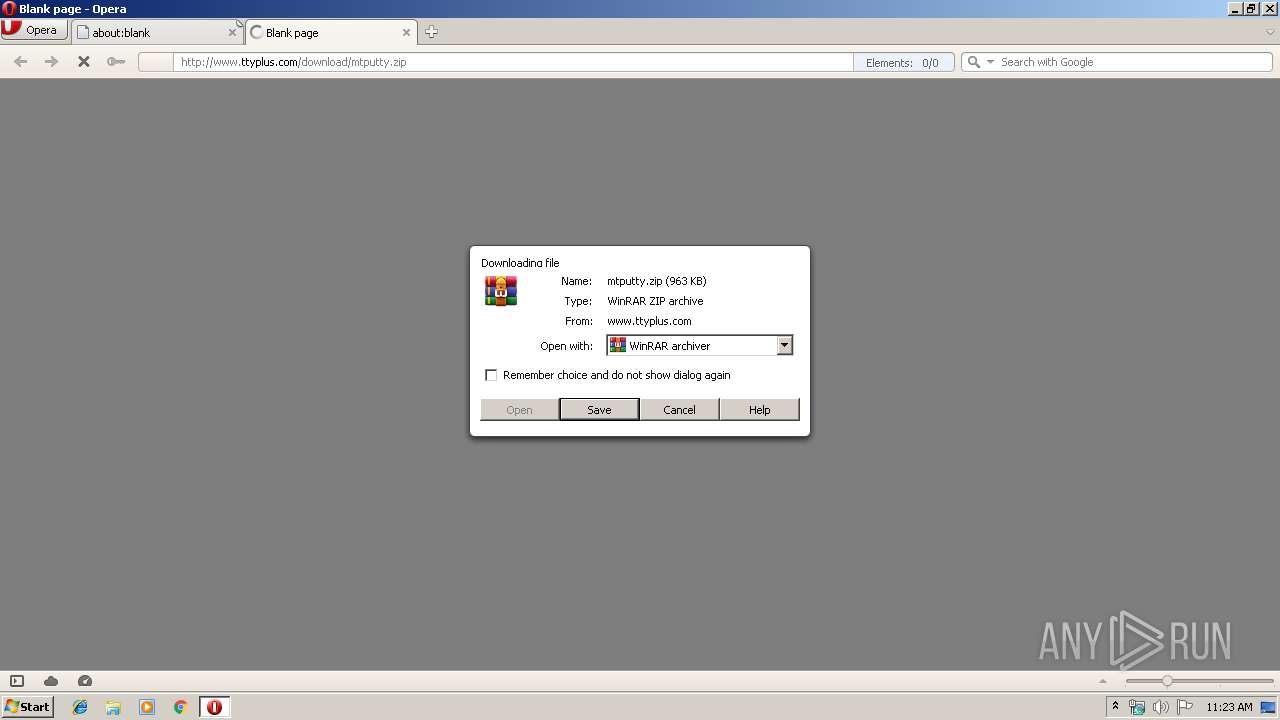
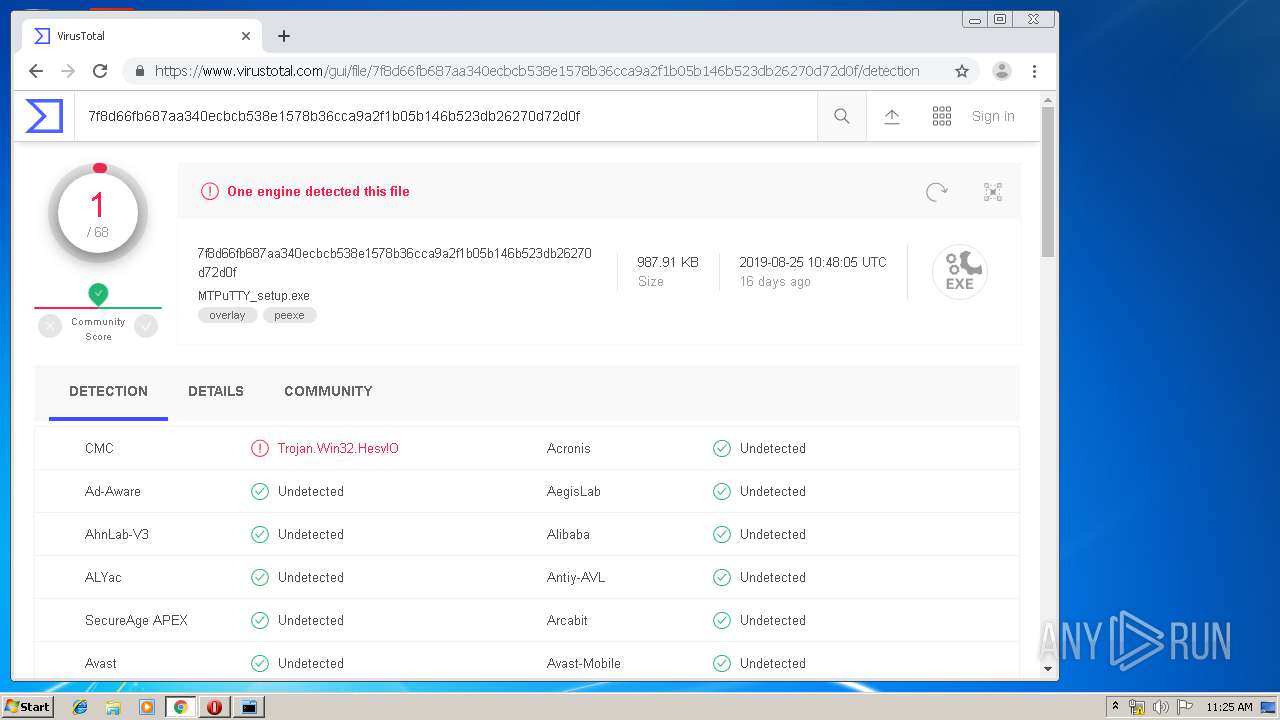
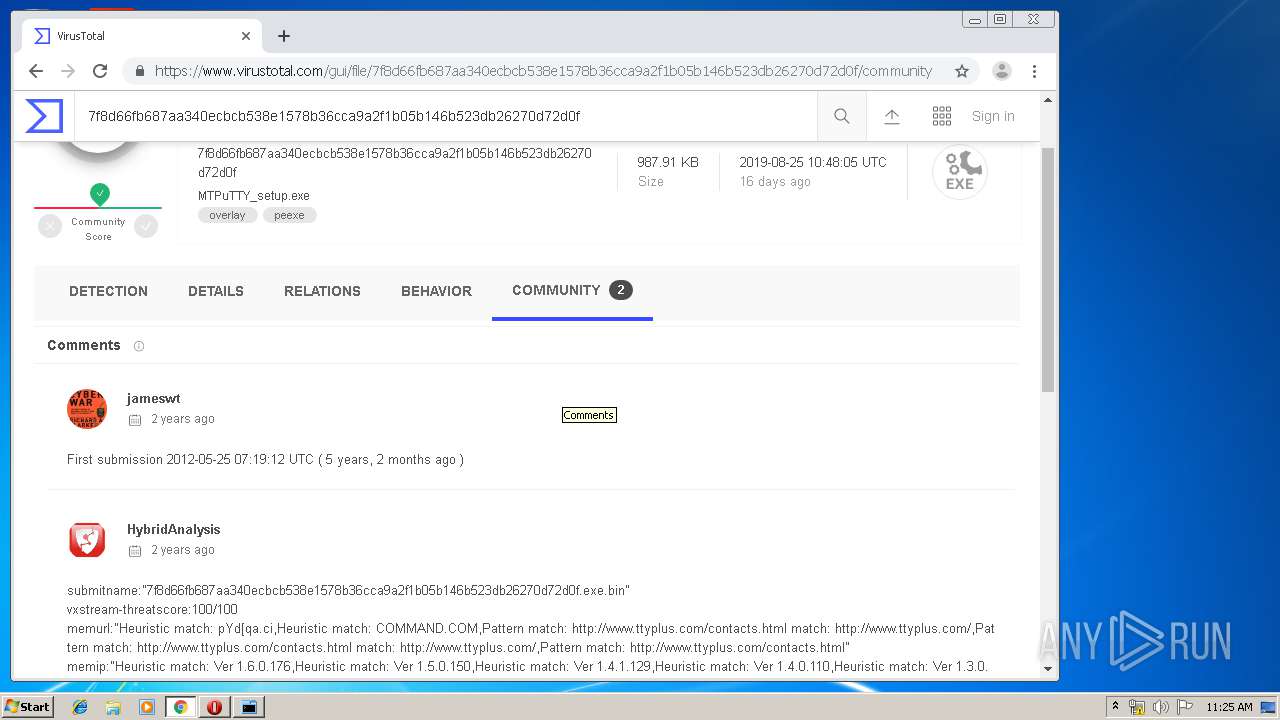
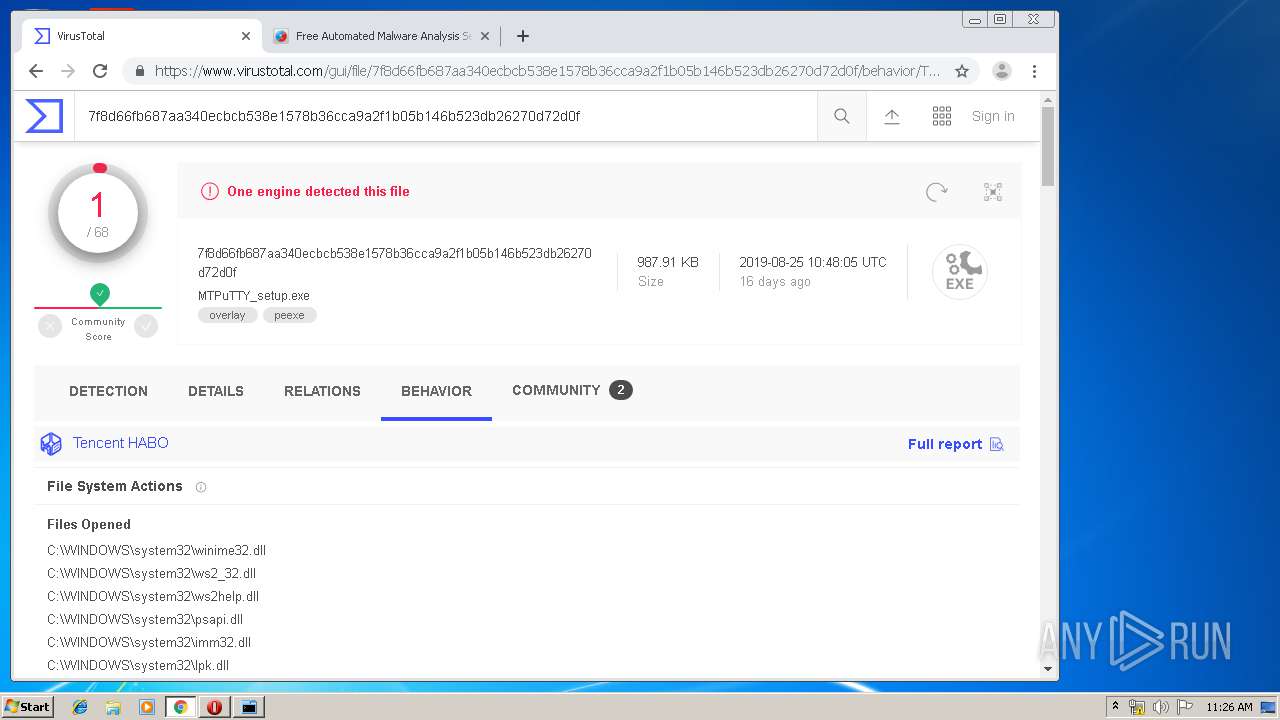
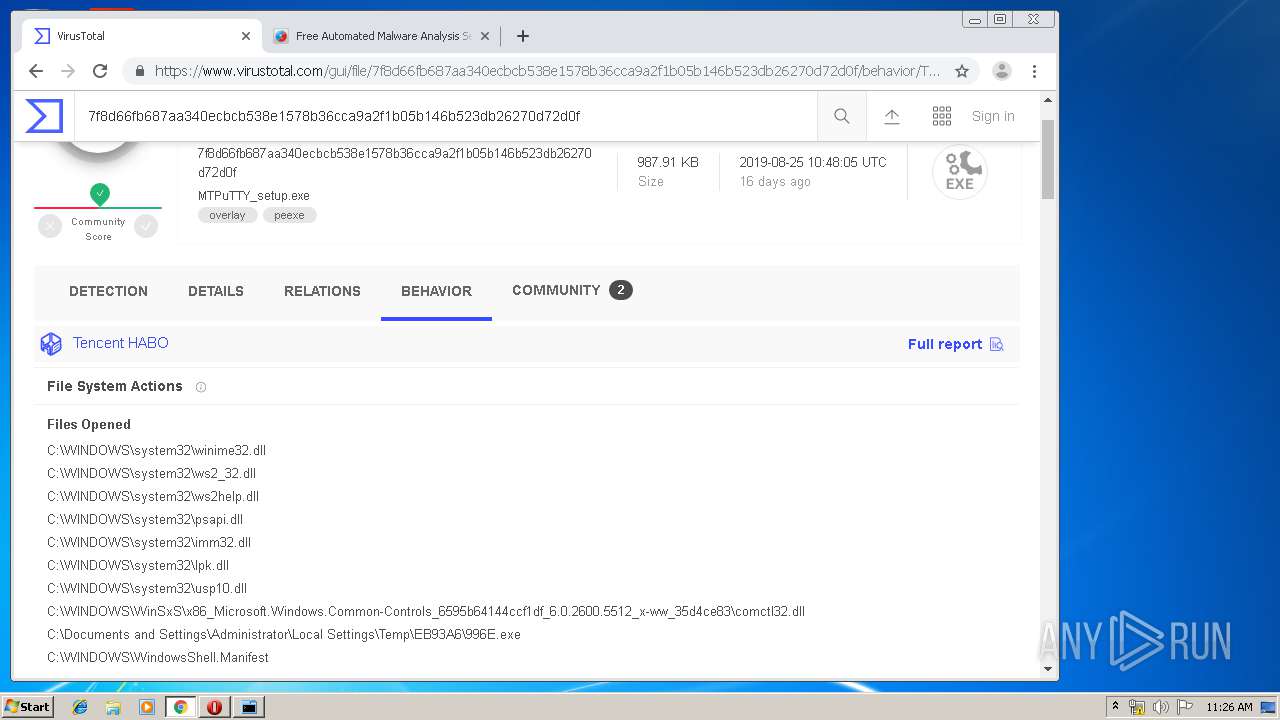
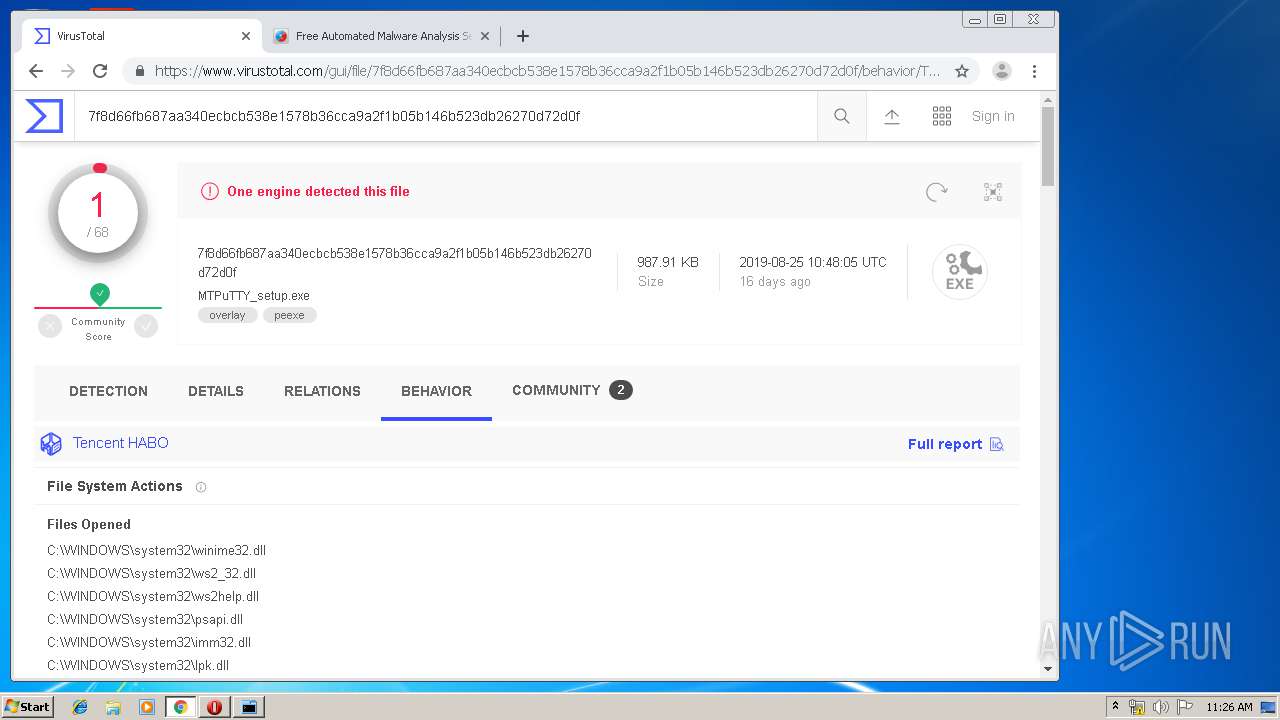
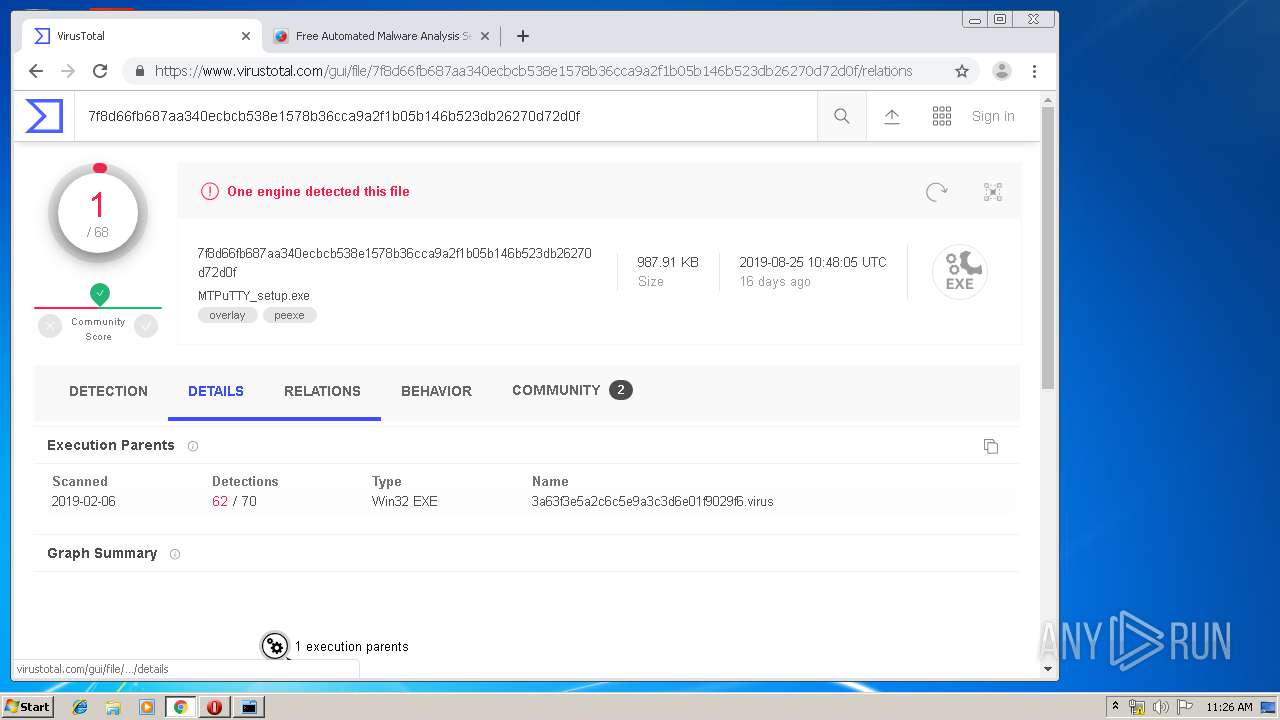
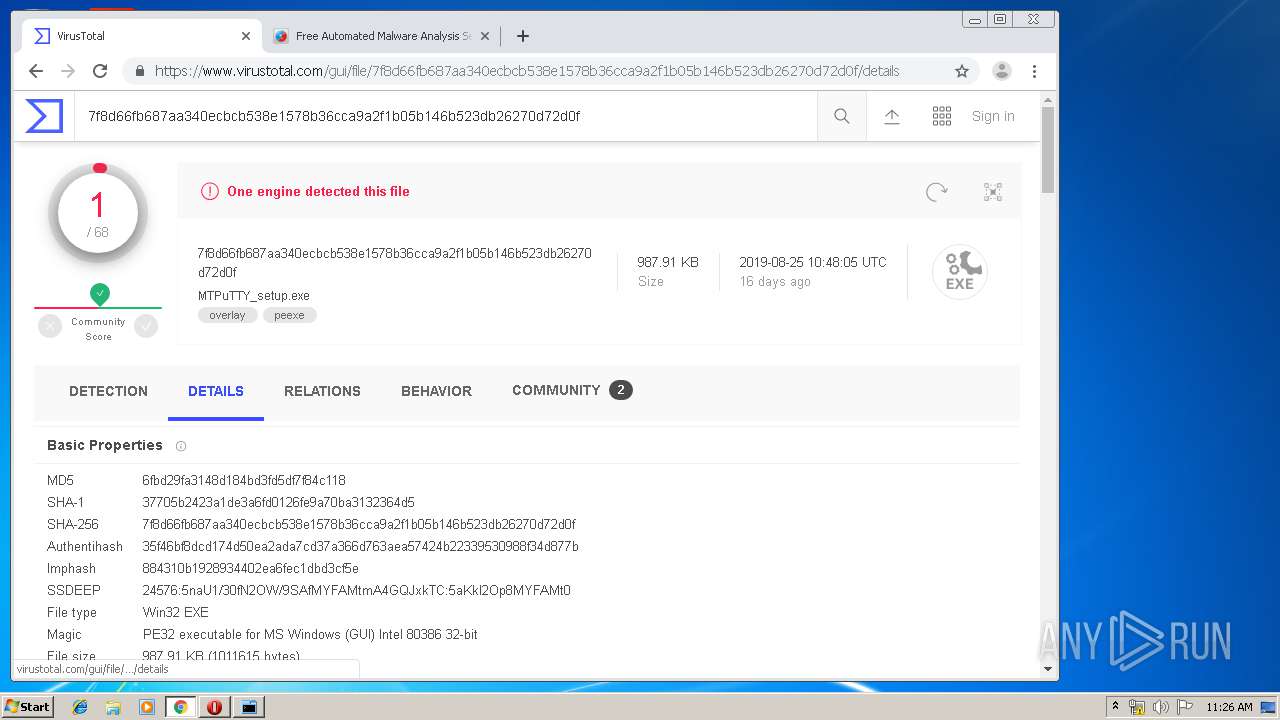
| URL: | http://www.ttyplus.com/download/mtputty.zip |
| Full analysis: | https://app.any.run/tasks/84df45f6-635d-405d-9e83-c424743193d6 |
| Verdict: | Malicious activity |
| Analysis date: | September 11, 2019, 10:23:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
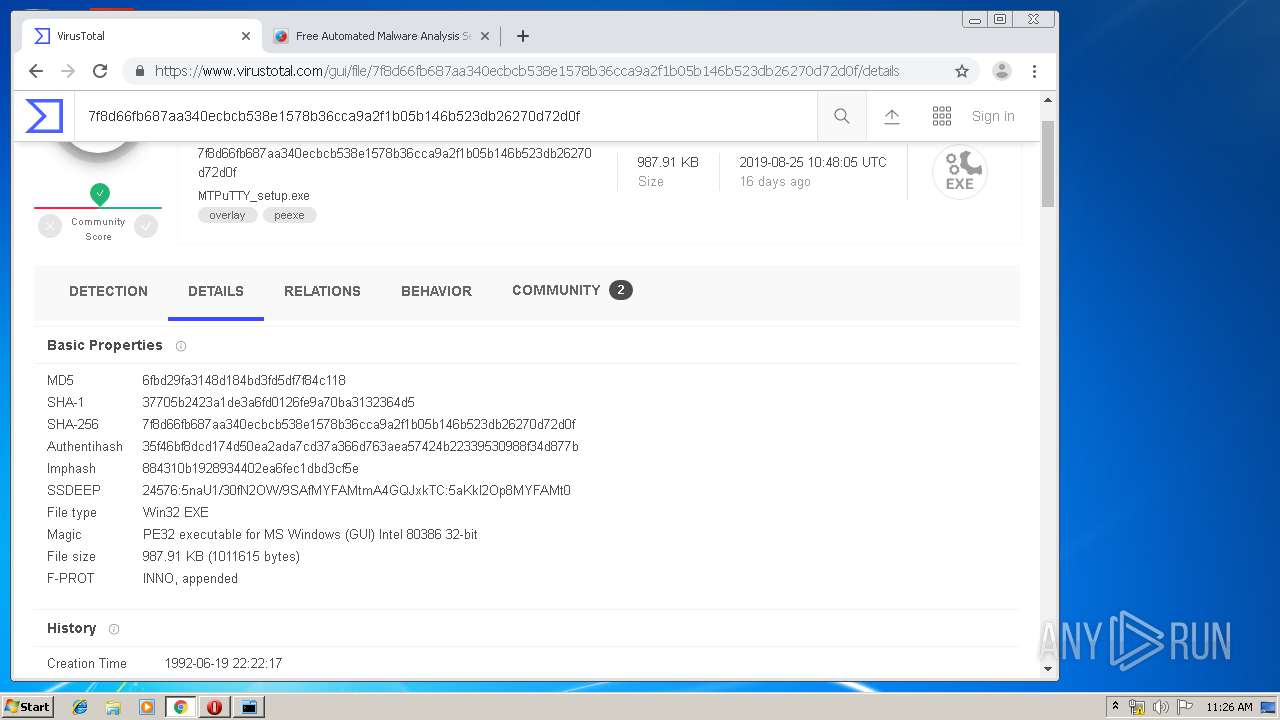
| MD5: | 02A5D9545865F7A397F61F8E71239127 |
| SHA1: | 4CDBEFDC49031E4A691E253C4B32A7E0DEEC6754 |
| SHA256: | FFF6856F8084C693615CE38D826B8036D5EF95FA8F2BCC3FE749D7A79A57178E |
| SSDEEP: | 3:N1KJS4sVJyWKLs6RcYV:Cc4Dlf |
MALICIOUS
Application was dropped or rewritten from another process
- MTPuTTY_setup.exe (PID: 2736)
- MTPuTTY_setup.exe (PID: 2628)
- mtputty.exe (PID: 2568)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2368)
- MTPuTTY_setup.exe (PID: 2736)
- MTPuTTY_setup.exe (PID: 2628)
- MTPuTTY_setup.tmp (PID: 3088)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2396)
Creates files in the user directory
- MTPuTTY_setup.tmp (PID: 3088)
INFO
Creates files in the user directory
- opera.exe (PID: 2784)
Manual execution by user
- chrome.exe (PID: 2396)
- WinRAR.exe (PID: 2368)
- MTPuTTY_setup.exe (PID: 2736)
- mtputty.exe (PID: 2568)
Creates a software uninstall entry
- MTPuTTY_setup.tmp (PID: 3088)
Reads Internet Cache Settings
- opera.exe (PID: 2784)
Application was dropped or rewritten from another process
- MTPuTTY_setup.tmp (PID: 3088)
- MTPuTTY_setup.tmp (PID: 3504)
Application launched itself
- chrome.exe (PID: 2396)
Reads the hosts file
- chrome.exe (PID: 2092)
- chrome.exe (PID: 2396)
Reads settings of System Certificates
- chrome.exe (PID: 2092)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2396)
Creates files in the program directory
- MTPuTTY_setup.tmp (PID: 3088)
Loads dropped or rewritten executable
- MTPuTTY_setup.tmp (PID: 3088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
82
Monitored processes
41
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,12184792248845886082,11172869793912757860,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14351380261529980655 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2916 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 316 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,12184792248845886082,11172869793912757860,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17769965930624741243 --mojo-platform-channel-handle=3716 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 796 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,12184792248845886082,11172869793912757860,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15885117129018701745 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1416 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,12184792248845886082,11172869793912757860,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5345951874015115957 --mojo-platform-channel-handle=4092 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1464 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,12184792248845886082,11172869793912757860,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12481128923309752970 --renderer-client-id=21 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4324 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,12184792248845886082,11172869793912757860,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15817044135916761125 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2228 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,12184792248845886082,11172869793912757860,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=13008614396519337054 --mojo-platform-channel-handle=3280 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,12184792248845886082,11172869793912757860,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=8514729005537728907 --mojo-platform-channel-handle=1600 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2152 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1028,12184792248845886082,11172869793912757860,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15832015322756064953 --mojo-platform-channel-handle=3620 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2156 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1028,12184792248845886082,11172869793912757860,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1586226332748664845 --renderer-client-id=33 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3192 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 679
Read events
2 313
Write events
357
Delete events
9
Modification events
| (PID) Process: | (2784) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe "http://www.ttyplus.com/download/mtputty.zip" | |||
| (PID) Process: | (2784) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2784) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2784) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0200000001000000000000000700000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2784) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (2784) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (2784) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (2784) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (2784) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
| (PID) Process: | (2784) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | FFlags |
Value: 1092616257 | |||
Executable files
7
Suspicious files
266
Text files
189
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2784 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr9177.tmp | — | |
MD5:— | SHA256:— | |||
| 2784 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr9187.tmp | — | |
MD5:— | SHA256:— | |||
| 2784 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr91E6.tmp | — | |
MD5:— | SHA256:— | |||
| 2784 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\65QPUX0SO85GQT7H1H7U.temp | — | |
MD5:— | SHA256:— | |||
| 2784 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00003.tmp | — | |
MD5:— | SHA256:— | |||
| 2784 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprE5F3.tmp | — | |
MD5:— | SHA256:— | |||
| 2784 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
| 2784 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2784 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 2784 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
41
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2784 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 528 b | whitelisted |
2092 | chrome.exe | GET | 302 | 172.217.22.78:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 515 b | whitelisted |
2784 | opera.exe | GET | 200 | 168.235.76.235:80 | http://www.ttyplus.com/download/mtputty.zip | US | compressed | 962 Kb | suspicious |
2784 | opera.exe | GET | 400 | 107.167.110.216:80 | http://sitecheck2.opera.com/?host=www.ttyplus.com&hdn=W/TD/0yTrGUuO60TeY/XnA== | US | html | 150 b | whitelisted |
2092 | chrome.exe | GET | 200 | 74.125.8.140:80 | http://r6---sn-5hnednlk.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.104.186.93&mm=28&mn=sn-5hnednlk&ms=nvh&mt=1568197413&mv=m&mvi=5&pl=24&shardbypass=yes | US | crx | 862 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2784 | opera.exe | 168.235.76.235:80 | www.ttyplus.com | RamNode LLC | US | suspicious |
2784 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2092 | chrome.exe | 172.217.18.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2784 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2092 | chrome.exe | 172.217.23.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
2092 | chrome.exe | 216.58.207.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
2092 | chrome.exe | 172.217.21.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2092 | chrome.exe | 172.217.16.195:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2784 | opera.exe | 107.167.110.216:80 | sitecheck2.opera.com | Opera Software Americas LLC | US | malicious |
2092 | chrome.exe | 172.217.21.225:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.ttyplus.com |
| suspicious |
sitecheck2.opera.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |