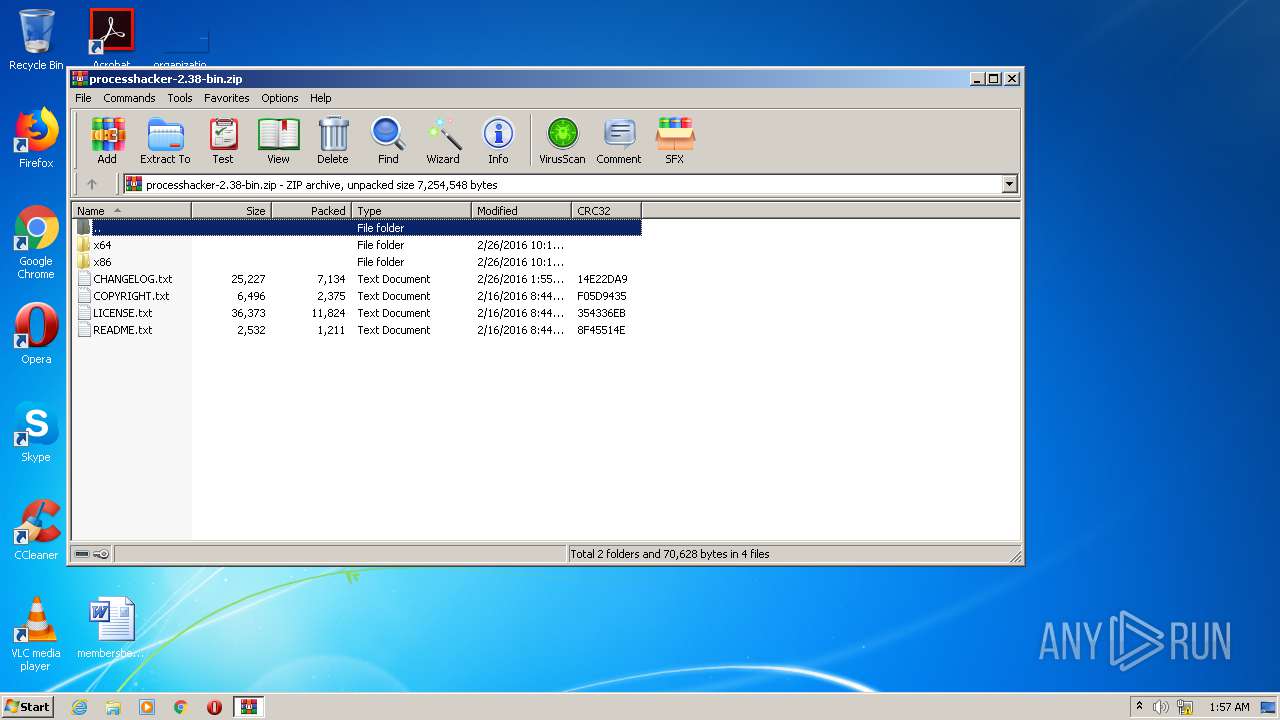
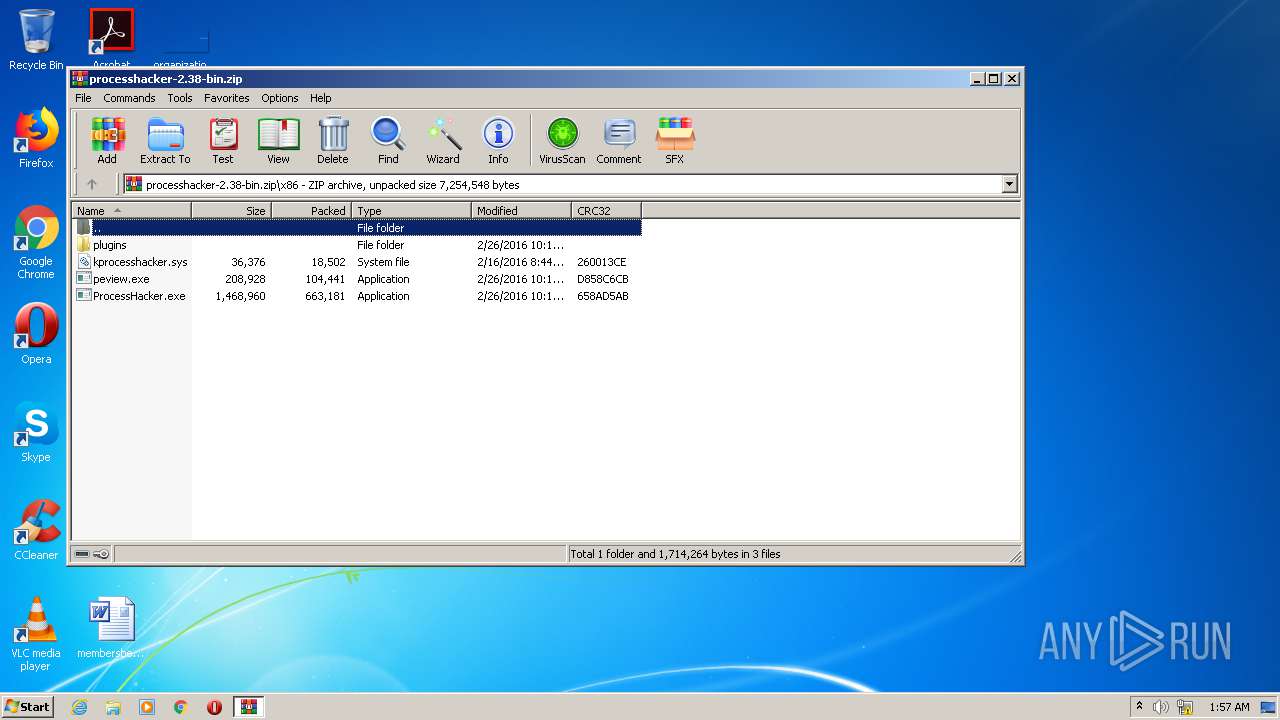
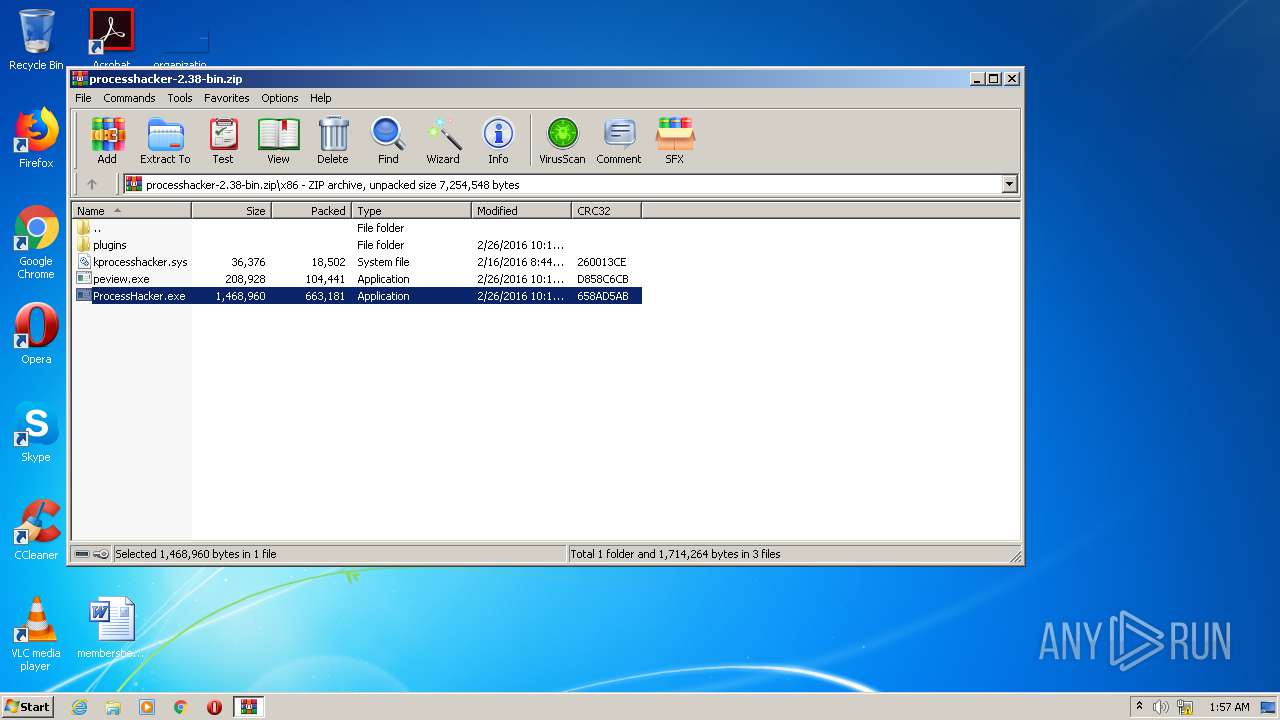
| File name: | processhacker-2.38-bin.zip |
| Full analysis: | https://app.any.run/tasks/077ccdb2-1e87-41db-88df-53f3a85c50df |
| Verdict: | Malicious activity |
| Analysis date: | January 07, 2021, 01:57:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8DD71039BB7FB960DDF187F11F089601 |
| SHA1: | F9AE9036E657393599D3282DDDDA4CCBB33AE11B |
| SHA256: | FFF36E5C17D0F6D1AB54A776FC7193AD908619FCC2EB221391A64E4EF43B93FE |
| SSDEEP: | 98304:ReQHM/E8ZmmKNHtvp2sDhkVt9CN4NIk++OqazMeobBU5:dMrgNF3hESzk++9az |
MALICIOUS
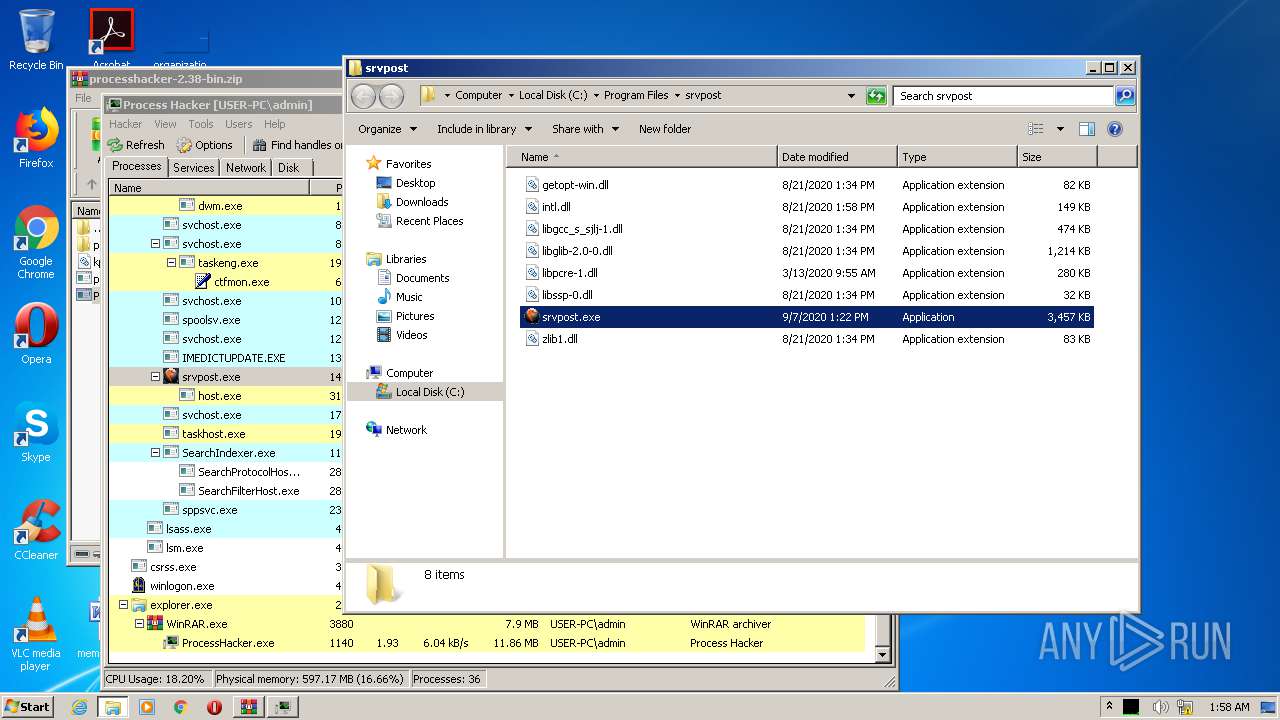
Application was dropped or rewritten from another process
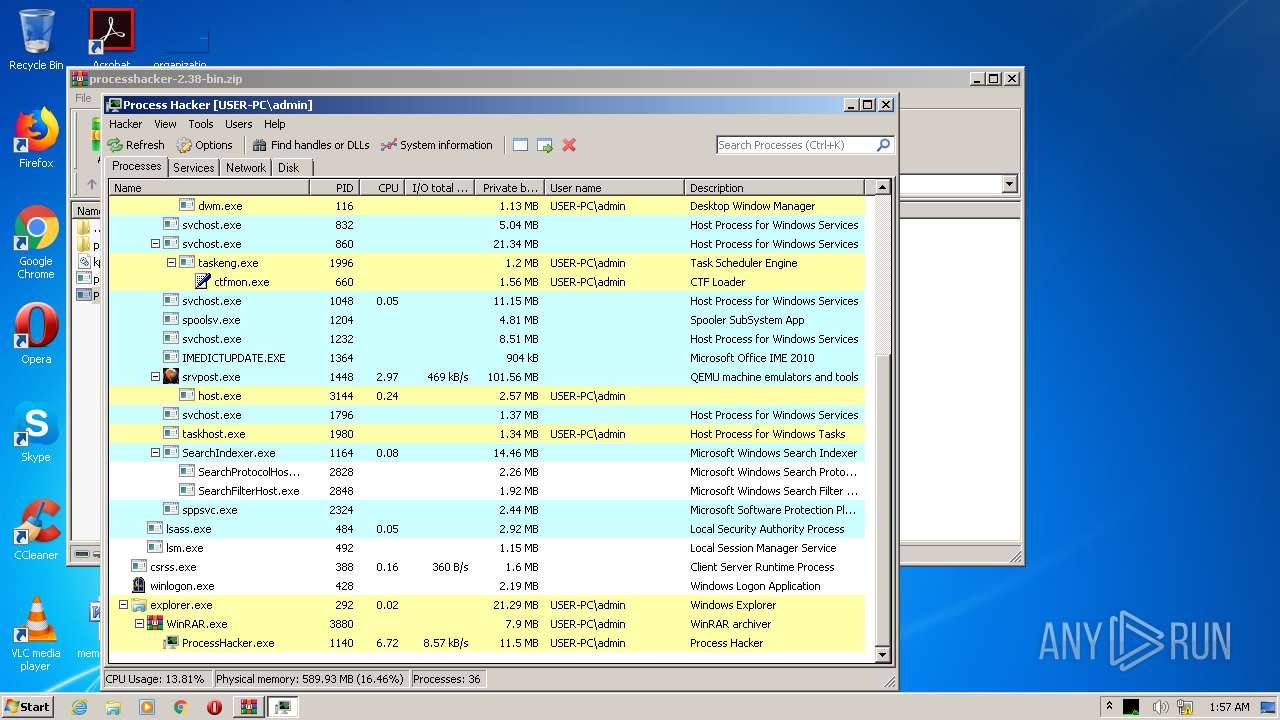
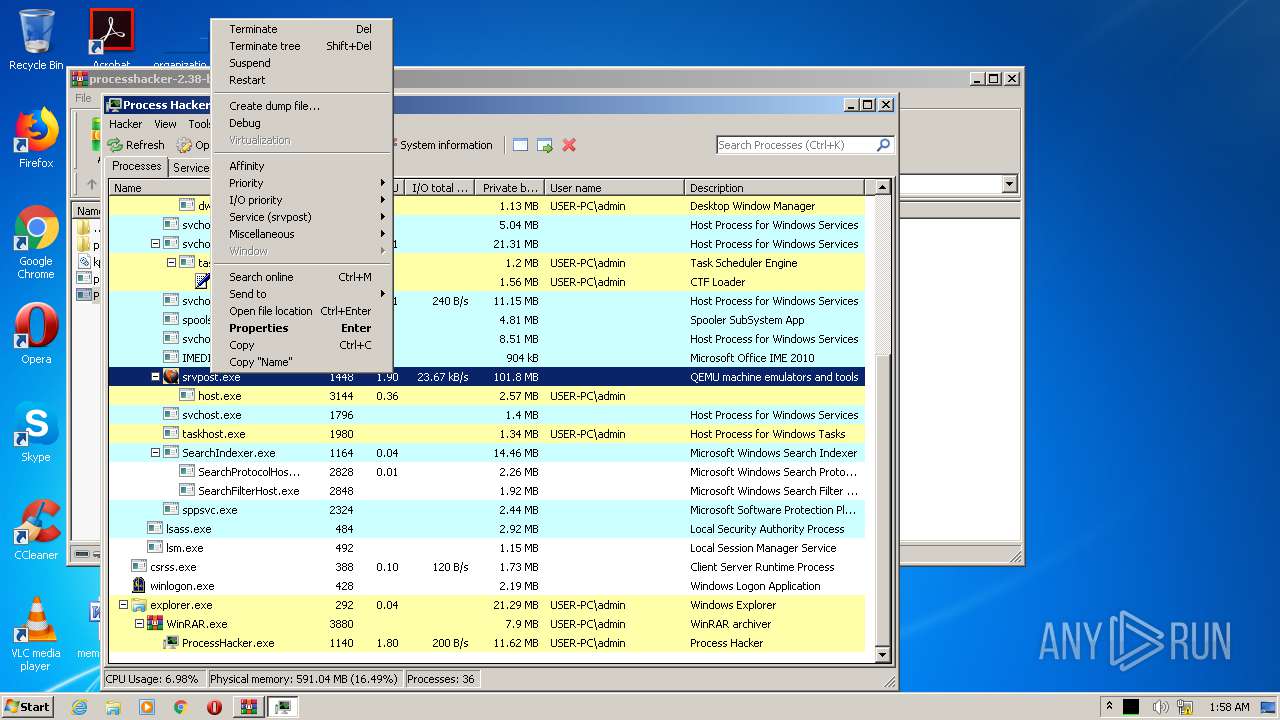
- ProcessHacker.exe (PID: 1140)
Loads dropped or rewritten executable
- ProcessHacker.exe (PID: 1140)
SUSPICIOUS
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3880)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3880)
INFO
Reads settings of System Certificates
- ProcessHacker.exe (PID: 1140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:02:26 12:55:19 |
| ZipCRC: | 0x14e22da9 |
| ZipCompressedSize: | 7134 |
| ZipUncompressedSize: | 25227 |
| ZipFileName: | CHANGELOG.txt |
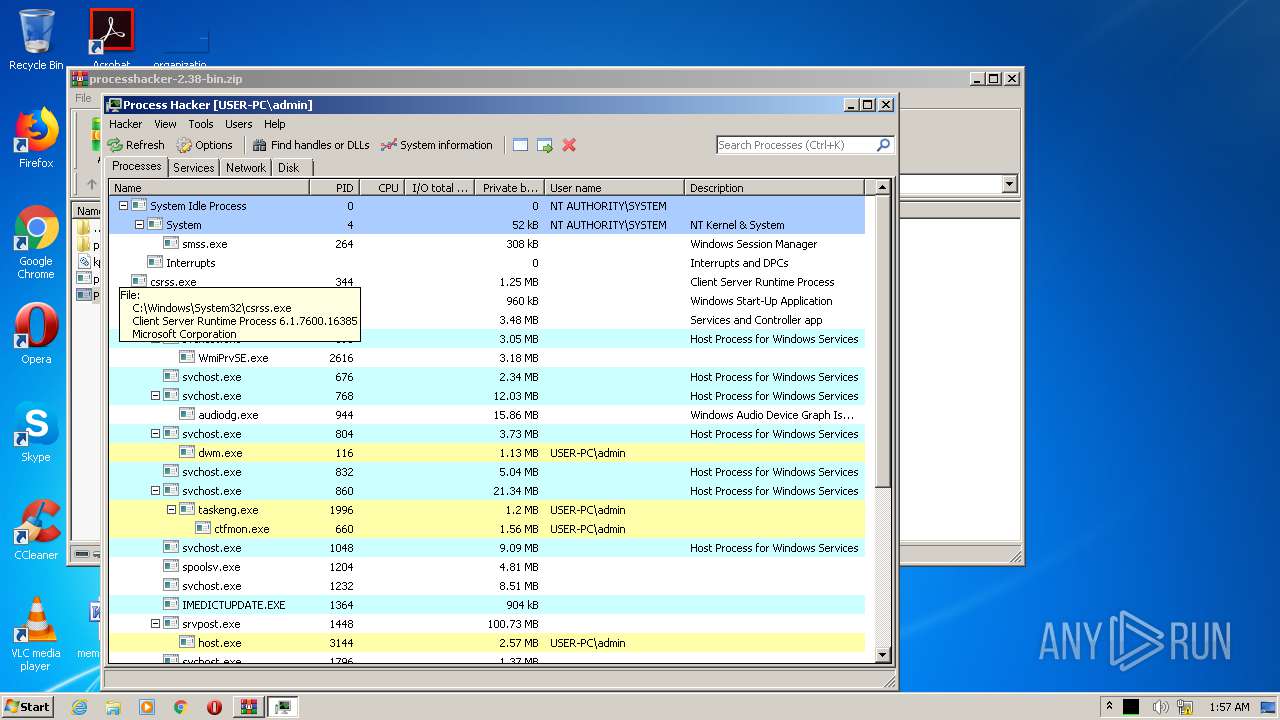
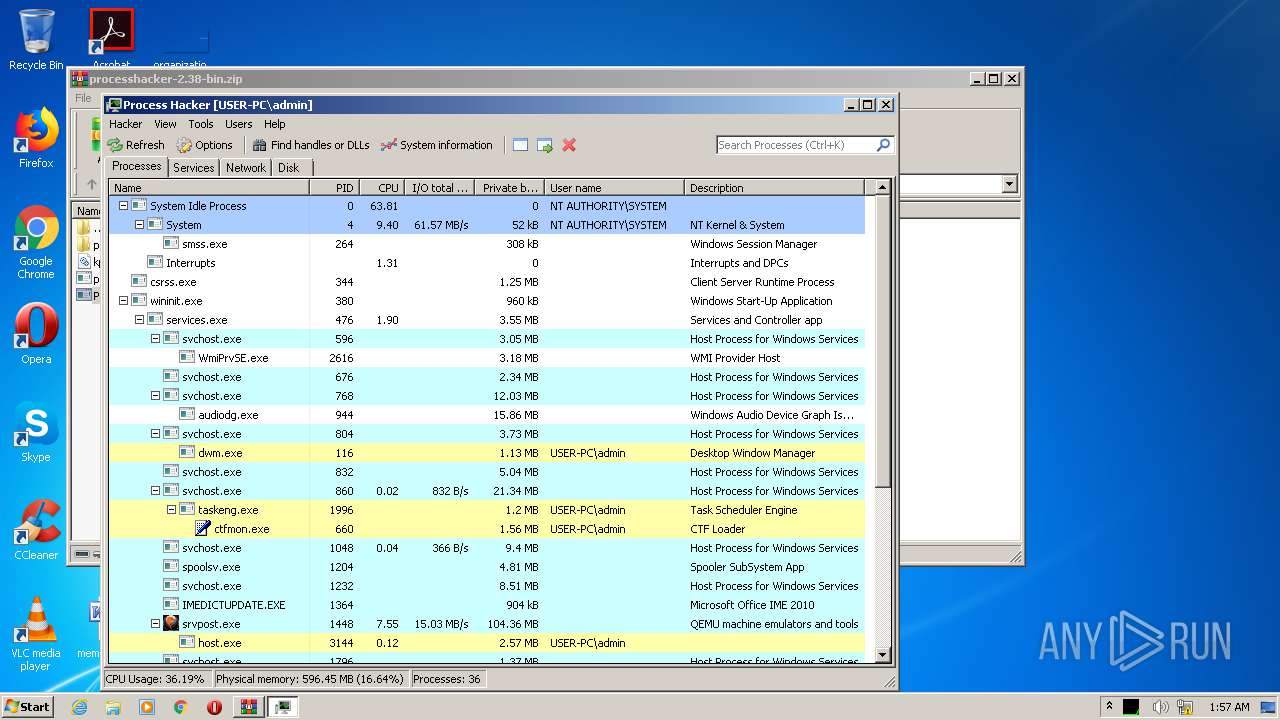
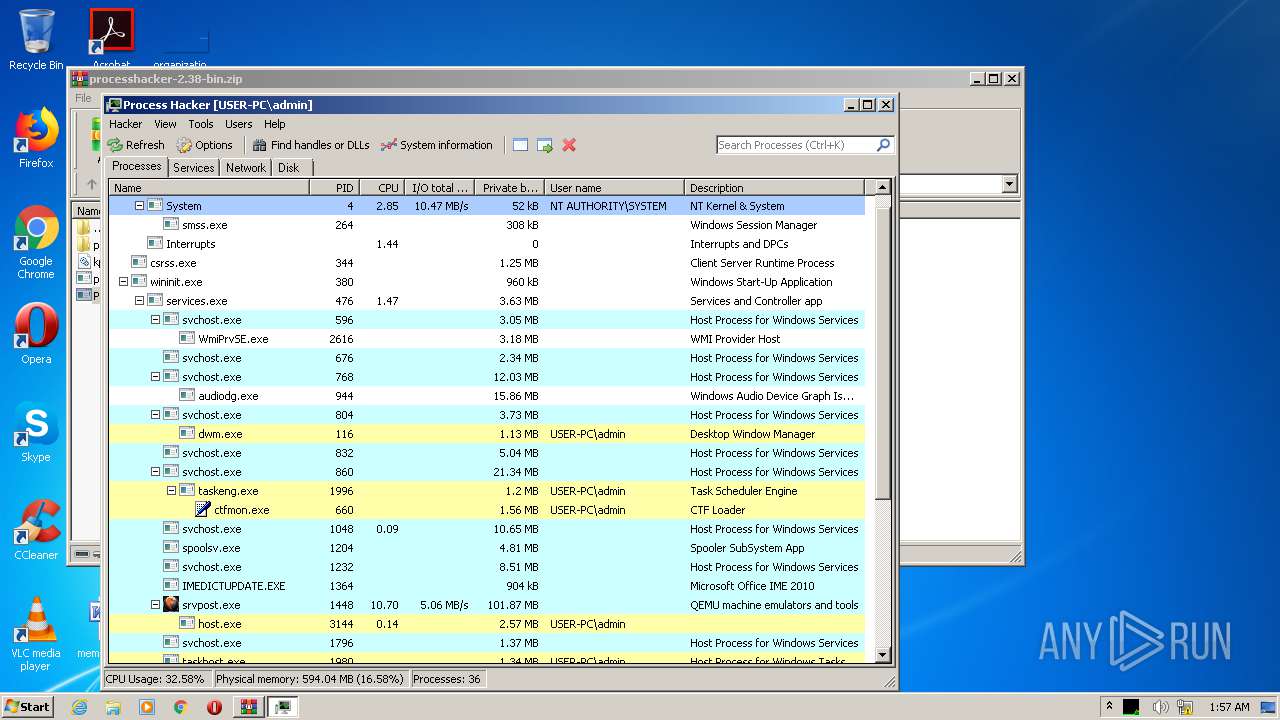
Total processes
38
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1140 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\x86\ProcessHacker.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\x86\ProcessHacker.exe | WinRAR.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: MEDIUM Description: Process Hacker Exit code: 0 Version: 2.38.0.343 Modules
| |||||||||||||||
| 3880 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\processhacker-2.38-bin.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
908
Read events
885
Write events
23
Delete events
0
Modification events
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\processhacker-2.38-bin.zip | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
30
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\x64\plugins\DotNetTools.dll | executable | |
MD5:C8D836446DDD95584C69CAEBA657D59B | SHA256:91EE1186D1950448C6D8403E4EF69D2C653D01DF3E4C2DEDB405BFEEF399A92A | |||
| 3880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\COPYRIGHT.txt | text | |
MD5:39B07060A5C6199730219E29C747C061 | SHA256:319CD301CF40BE03C00CD086560D4E810E0F6D0DBFDC2D28D6AF3522C027CF49 | |||
| 3880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\x64\kprocesshacker.sys | executable | |
MD5:BBBC9A6CC488CFB0F6C6934B193891EB | SHA256:C725919E6357126D512C638F993CF572112F323DA359645E4088F789EB4C7B8C | |||
| 3880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\x64\plugins\ExtendedServices.dll | executable | |
MD5:E53D4E0CBC9012BA3D9EE7C44D7A0BE3 | SHA256:E0FBFCC62268A03EE512FF43E0F974878EC52C915BCAB1AED0DF28F5D72FBECE | |||
| 3880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\x64\plugins\ExtendedNotifications.dll | executable | |
MD5:4743EB2C478096E257674F45D7FBDCDB | SHA256:1BDA47190276D04DF5BFD1CE6AA8D1F1C37E0CC93772E0ACE0400D2F3AABBCD2 | |||
| 3880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\x64\plugins\ExtendedTools.dll | executable | |
MD5:9DD086AC1A99ADD8E2E2E879BDD318CD | SHA256:0214CB8F2AFC2A2321ACA631BE85F18CFC3B29884D3E4599E4C38474373FAC28 | |||
| 3880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\x64\plugins\NetworkTools.dll | executable | |
MD5:30FE94DFFCDABB0EF660520DCA934E17 | SHA256:3C68ABC00E359B530BCA5831A879DA54DA4F70372E15737120234470E4EBF56E | |||
| 3880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\x64\plugins\Updater.dll | executable | |
MD5:C5DA132D699BCAF8E8BF9DD1CEFEFE85 | SHA256:D14DFDFAC79AE2F128E57DC9816556AC1929A707B8BB7B6D42E08B39FF217E1C | |||
| 3880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\x64\plugins\OnlineChecks.dll | executable | |
MD5:162870462B231CCC3AA32335D9725CB3 | SHA256:C08EA9D449EC004991A117D1AA83B6ED82C52A94E7BDFA2DF8DDDEDF9B2F2C7D | |||
| 3880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3880.108\LICENSE.txt | text | |
MD5:EB59E0A5D01D0A5B02DA0C9E7786969F | SHA256:C38E811F6F83428921D0CECD998A44B717149B577B4C1A63B66064F03C34E4E7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1140 | ProcessHacker.exe | 162.243.25.33:443 | wj32.org | Digital Ocean, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wj32.org |
| whitelisted |