| File name: | myfile.exe |
| Full analysis: | https://app.any.run/tasks/7b47b862-c456-4e06-939d-82af757153fc |
| Verdict: | Malicious activity |
| Analysis date: | January 08, 2024, 12:52:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | E57D1405893F48BACAD8ACFC6E0F677E |
| SHA1: | E799C03E455AA0F6E2A12A7017EEA97C24CBAF09 |
| SHA256: | FFEE1DD5823819F07E78A39B77EC50A6E2ACE983352134647155A52CA58FD44D |
| SSDEEP: | 12288:0A0SEiGBzz3nKAiQ7GcwqxYfMmXnAA/TYw3f:0AKiGBzz3njj7GcwiYkmXnAA7Ywv |
MALICIOUS
Runs injected code in another process
- itxos.exe (PID: 1404)
Scans artifacts that could help determine the target
- WinMail.exe (PID: 1392)
SUSPICIOUS
Reads Internet Explorer settings
- WinMail.exe (PID: 1392)
Reads the Internet Settings
- WinMail.exe (PID: 1392)
Reads Microsoft Outlook installation path
- WinMail.exe (PID: 1392)
Checks Windows Trust Settings
- WinMail.exe (PID: 1392)
Detected use of alternative data streams (AltDS)
- WinMail.exe (PID: 1392)
Reads security settings of Internet Explorer
- WinMail.exe (PID: 1392)
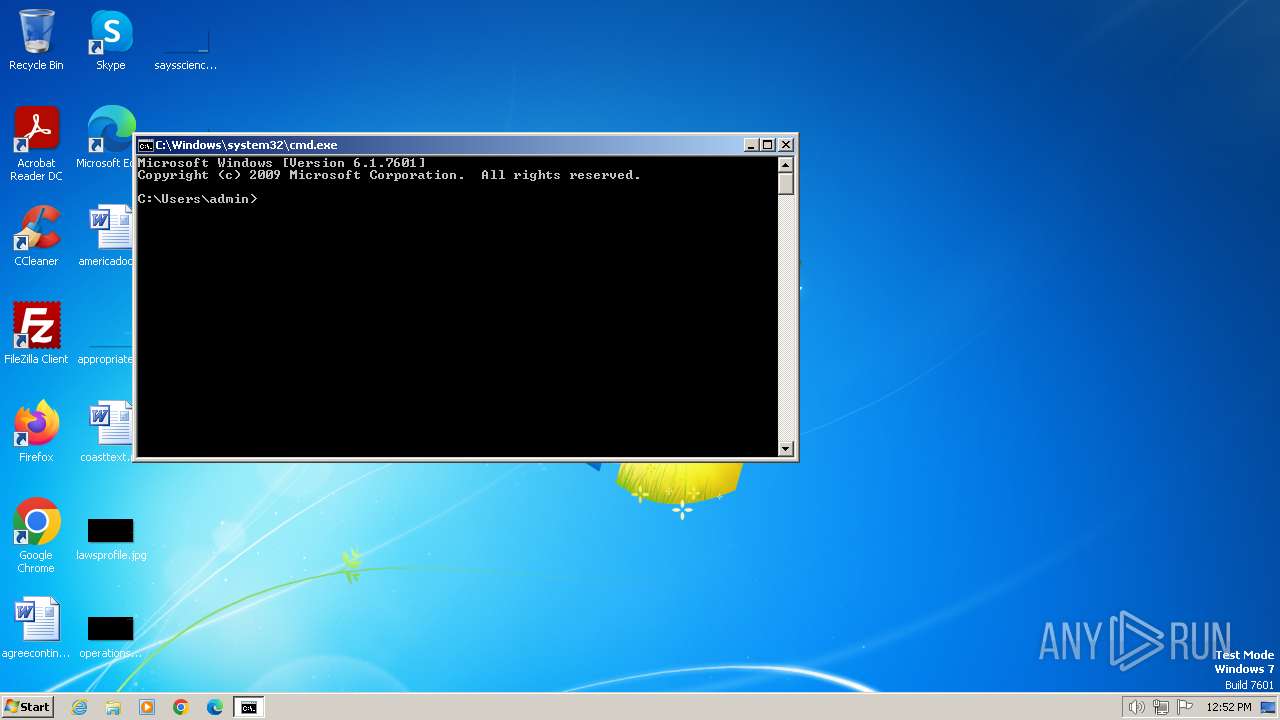
Executing commands from a ".bat" file
- myfile.exe (PID: 124)
Starts CMD.EXE for commands execution
- myfile.exe (PID: 124)
Reads settings of System Certificates
- WinMail.exe (PID: 1392)
INFO
Reads the machine GUID from the registry
- myfile.exe (PID: 124)
- WinMail.exe (PID: 1392)
Creates files or folders in the user directory
- myfile.exe (PID: 124)
- WinMail.exe (PID: 1392)
Drops the executable file immediately after the start
- myfile.exe (PID: 124)
- WinMail.exe (PID: 1392)
Checks supported languages
- myfile.exe (PID: 124)
- itxos.exe (PID: 1404)
- WinMail.exe (PID: 1392)
Reads the computer name
- myfile.exe (PID: 124)
- itxos.exe (PID: 1404)
- WinMail.exe (PID: 1392)
Application was injected by another process
- dwm.exe (PID: 612)
- taskeng.exe (PID: 300)
Checks proxy server information
- WinMail.exe (PID: 1392)
Drops a self-deleting batch file
- myfile.exe (PID: 124)
Create files in a temporary directory
- WinMail.exe (PID: 1392)
- myfile.exe (PID: 124)
Manual execution by a user
- cmd.exe (PID: 1844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (43.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (29.8) |
| .exe | | | Generic Win/DOS Executable (13.2) |
| .exe | | | DOS Executable Generic (13.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:01:23 19:05:57+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 4.22 |
| CodeSize: | 4608 |
| InitializedDataSize: | 301056 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11ae |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
39
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Users\admin\AppData\Local\Temp\myfile.exe" | C:\Users\admin\AppData\Local\Temp\myfile.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 300 | taskeng.exe {CE1452CD-5E82-4DCD-B0CC-498574D17563} | C:\Windows\System32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 612 | "C:\Windows\system32\Dwm.exe" | C:\Windows\System32\dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Windows Mail\WinMail.exe" -Embedding | C:\Program Files\Windows Mail\WinMail.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Mail Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1404 | "C:\Users\admin\AppData\Roaming\Fyuq\itxos.exe" | C:\Users\admin\AppData\Roaming\Fyuq\itxos.exe | — | myfile.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1844 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2000 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\tmp03cebda9.bat" | C:\Windows\System32\cmd.exe | — | myfile.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
4 758
Read events
4 718
Write events
34
Delete events
6
Modification events
| (PID) Process: | (300) taskeng.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Ofedz |
| Operation: | write | Name: | 9999882 |
Value: HgcQoQ== | |||
| (PID) Process: | (1392) WinMail.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Mail |
| Operation: | write | Name: | StoreMigratedV5 |
Value: 1 | |||
| (PID) Process: | (1392) WinMail.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Mail |
| Operation: | write | Name: | Settings Upgraded |
Value: 10 | |||
| (PID) Process: | (1392) WinMail.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\IAM |
| Operation: | write | Name: | Server ID |
Value: 2 | |||
| (PID) Process: | (1392) WinMail.exe | Key: | HKEY_CURRENT_USER\Identities |
| Operation: | write | Name: | Identity Ordinal |
Value: 2 | |||
| (PID) Process: | (1392) WinMail.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Mail |
| Operation: | write | Name: | LastBackup |
Value: E1070A0004000500090014000400CA01 | |||
| (PID) Process: | (1392) WinMail.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\IAM |
| Operation: | write | Name: | Default News Account |
Value: account{30CE7C98-AA27-4327-91CA-78FA20FFA850}.oeaccount | |||
| (PID) Process: | (1392) WinMail.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\WAB |
| Operation: | delete value | Name: | NamedProps |
Value: 0420060000000000C00000000000004604000000000000800E0000000100330032003800350034000000000001800E0000000100330032003800350035000000000002800E0000000100330032003800350036000000000003800E0000000100330032003800350037000000 | |||
| (PID) Process: | (1392) WinMail.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\WAB |
| Operation: | delete value | Name: | NamedPropCount |
Value: 1 | |||
| (PID) Process: | (1392) WinMail.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\WAB |
| Operation: | delete value | Name: | NamedProps |
Value: 0420060000000000C00000000000004604000000000000800E0000000100330032003800350034000000000001800E0000000100330032003800350035000000000002800E0000000100330032003800350036000000000003800E0000000100330032003800350037000000813284C18505D011B29000AA003CF6760B000000000004800E0000000100330032003700360039000000000005800E0000000100330032003700370030000000000006800E0000000100330032003700370031000000000007800E0000000100330032003700370032000000000008800E0000000100330032003700370033000000000009800E000000010033003200370037003400000000000A800E000000010033003200370037003500000000000B800E000000010033003200370037003600000000000C800E000000010033003200370037003700000000000D800E000000010033003200370037003800000000000E800E0000000100330032003700370039000000 | |||
Executable files
2
Suspicious files
19
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1392 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\edb.log | binary | |
MD5:09F9EC30C43F61C1B4E3CF574CEF1740 | SHA256:3A2C8485989DE3437B107D5459308E6984CC2D0F029B25CA74DFA0BC4B754054 | |||
| 1392 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\edb.chk | binary | |
MD5:8772FAEDBEB9D6AED5283C0825590CFC | SHA256:9558AAB47E4698D28B94D6352085475B390AD43BD9B5BBDFBE6FDCD69545DBF4 | |||
| 1392 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\Backup\temp\WindowsMail.MSMessageStore | binary | |
MD5:997543EC1CDE4A69BDB404E5154E41DB | SHA256:AB06476A058AB0AE50167F776C6ECE590996FA39BAC9F12F2875897EBBBBDCCF | |||
| 1392 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\edb00002.log | binary | |
MD5:2B7B267AA6181786848236D1D8307703 | SHA256:856BFB9C7CC6CE432645BBFED271389A3FC2FF44500D9DF08793B2016EFED2E1 | |||
| 1392 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\WindowsMail.pat | binary | |
MD5:CFEE54CD160002A4BCCB68A0ED7C7C79 | SHA256:30EAFE7A862EF50EAB4DB48343D6CC3C8737687DFC12B85C11ED47547687A5EA | |||
| 1392 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\WindowsMail.MSMessageStore | binary | |
MD5:B45D26E7688E37C569E7E5EAA0A96854 | SHA256:98D332C69FAB689D76A9923C57BF9998F2D665EE2A7789A7AA59AA516DD1FF00 | |||
| 124 | myfile.exe | C:\Users\admin\AppData\Roaming\Fyuq\itxos.exe | executable | |
MD5:144DA952F4A98FAD24CDD2F4826C0C3F | SHA256:0F60F397DDADFF62782A55B43526B6B52F1E960FCF69F58C04F25CB6EA2C7C2D | |||
| 1392 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\Backup\temp\edb00002.log | binary | |
MD5:2B7B267AA6181786848236D1D8307703 | SHA256:856BFB9C7CC6CE432645BBFED271389A3FC2FF44500D9DF08793B2016EFED2E1 | |||
| 1392 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\Local Folders\Inbox\51B51D64-00000001.eml | binary | |
MD5:CB071D274A42B95D7EDAB8855017D890 | SHA256:7712804AD1FFAF528261D2B2178770495B883B6390B4BFCF6DB8E730FD365396 | |||
| 1392 | WinMail.exe | C:\Users\admin\AppData\Local\Microsoft\Windows Mail\Local Folders\Sent Items\winmail.fol | binary | |
MD5:1D1A60631EFCF505795FB06471CB6A48 | SHA256:87EED194D869F1DEC6EBF639E985101ABAD37F6E5A347237A1B056B2DCBFC481 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
10
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
276 | taskhost.exe | 66.159.154.0:29411 | — | — | — | unknown |
276 | taskhost.exe | 83.20.6.42:22693 | — | — | — | unknown |
276 | taskhost.exe | 178.37.165.192:10076 | — | — | — | unknown |
276 | taskhost.exe | 82.211.186.140:29092 | — | — | — | unknown |
276 | taskhost.exe | 199.59.157.124:11145 | — | — | — | unknown |
276 | taskhost.exe | 95.237.204.30:25633 | — | — | — | unknown |