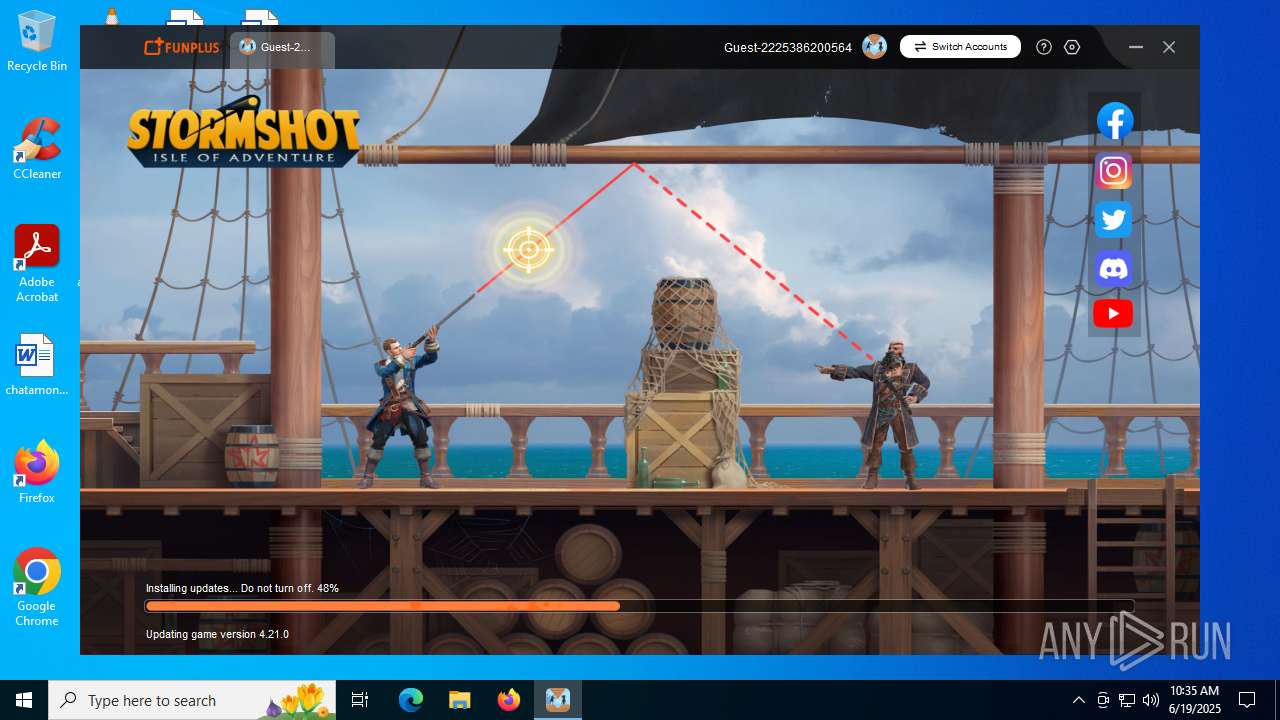
| File name: | Stormshot.PC.V1.0_25d5faae25.exe |
| Full analysis: | https://app.any.run/tasks/d01f41ac-997a-4001-abd9-95d17652f716 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2025, 10:33:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 7 sections |
| MD5: | 6AAE47CBAA4C56095A1EB0422C1D2ECB |
| SHA1: | 34E29D1801D270A2BD7AC02D4EA84C14C553D66F |
| SHA256: | FFD63FE2AEAA91F05BEF47B3583290CCDBA3F44912AB8B67044F3D58BF817EBF |
| SSDEEP: | 98304:5qXfKQQqTpl6ykKzUczpKnUOsGMG7F/1jzzXcVNbgtgz9GMGevZ7DTQ4H:DrzZtE |
MALICIOUS
Changes the autorun value in the registry
- PC-Launcher.exe (PID: 420)
SUSPICIOUS
Executable content was dropped or overwritten
- st_25d5faae25.exe (PID: 6344)
Drops 7-zip archiver for unpacking
- st_25d5faae25.exe (PID: 6344)
Process drops legitimate windows executable
- st_25d5faae25.exe (PID: 6344)
The process checks if it is being run in the virtual environment
- PC-Launcher.exe (PID: 420)
There is functionality for VM detection antiVM strings (YARA)
- PC-Launcher.exe (PID: 420)
There is functionality for taking screenshot (YARA)
- PC-Launcher.exe (PID: 420)
The process drops C-runtime libraries
- st_25d5faae25.exe (PID: 6344)
Creates a software uninstall entry
- st_25d5faae25.exe (PID: 6344)
INFO
Reads the machine GUID from the registry
- Stormshot.PC.V1.0_25d5faae25.exe (PID: 3564)
- PC-Launcher.exe (PID: 420)
Reads the computer name
- st_25d5faae25.exe (PID: 6344)
- Stormshot.PC.V1.0_25d5faae25.exe (PID: 3564)
- PC-Launcher.exe (PID: 420)
- 7za.exe (PID: 1944)
Checks supported languages
- Stormshot.PC.V1.0_25d5faae25.exe (PID: 3564)
- st_25d5faae25.exe (PID: 6344)
- PC-Launcher.exe (PID: 420)
- Launcher.exe (PID: 3676)
- 7za.exe (PID: 1944)
The sample compiled with chinese language support
- st_25d5faae25.exe (PID: 6344)
Create files in a temporary directory
- Stormshot.PC.V1.0_25d5faae25.exe (PID: 3564)
- PC-Launcher.exe (PID: 420)
The sample compiled with english language support
- st_25d5faae25.exe (PID: 6344)
Creates files in the program directory
- PC-Launcher.exe (PID: 420)
- 7za.exe (PID: 1944)
- st_25d5faae25.exe (PID: 6344)
Launching a file from a Registry key
- PC-Launcher.exe (PID: 420)
Creates files or folders in the user directory
- PC-Launcher.exe (PID: 420)
Reads CPU info
- PC-Launcher.exe (PID: 420)
- Stormshot.PC.V1.0_25d5faae25.exe (PID: 3564)
Checks proxy server information
- PC-Launcher.exe (PID: 420)
- slui.exe (PID: 3624)
Reads the software policy settings
- slui.exe (PID: 3624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:06:12 11:20:51+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.29 |
| CodeSize: | 1302016 |
| InitializedDataSize: | 1638912 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11272c |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
148
Monitored processes
8
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\Program Files (x86)\FunPlus\Stormshot\1.0.0.96\PC-Launcher.exe" --currentPath="C:\Program Files (x86)\FunPlus\Stormshot" --configVersion=1.0.0.96 --launchExe="C:\Program Files (x86)\FunPlus\Stormshot\Launcher.exe" | C:\Program Files (x86)\FunPlus\Stormshot\1.0.0.96\PC-Launcher.exe | Launcher.exe | ||||||||||||
User: admin Company: FunPlus, Inc. Integrity Level: HIGH Description: Stormshot Version: 1.0.0.96 Modules
| |||||||||||||||
| 1944 | "C:\Program Files (x86)\FunPlus\Stormshot\Plugin\7z.21.07\7za.exe" x -aoa -bsp2 -bse1 -bso0 "C:/Program Files (x86)/FunPlus/Stormshot/download/ngame/st_global_4.21.0_115eca27a3d0b5bea6603d6e2f59053e.7z" "-oC:/Program Files (x86)/FunPlus/Stormshot/nGame/4.21.0" | C:\Program Files (x86)\FunPlus\Stormshot\Plugin\7z.21.07\7za.exe | — | PC-Launcher.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7-Zip Standalone Console Version: 23.01 Modules
| |||||||||||||||
| 2228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7za.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3564 | "C:\Users\admin\AppData\Local\Temp\Stormshot.PC.V1.0_25d5faae25.exe" | C:\Users\admin\AppData\Local\Temp\Stormshot.PC.V1.0_25d5faae25.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3624 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3676 | "C:\Program Files (x86)\FunPlus\Stormshot\Launcher.exe" | C:\Program Files (x86)\FunPlus\Stormshot\Launcher.exe | — | st_25d5faae25.exe | |||||||||||
User: admin Company: FunPlus, Inc. Integrity Level: HIGH Description: Stormshot Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 3976 | "C:\Users\admin\AppData\Local\Temp\Stormshot.PC.V1.0_25d5faae25.exe" | C:\Users\admin\AppData\Local\Temp\Stormshot.PC.V1.0_25d5faae25.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 6344 | C:\Users\admin\AppData\Local\Temp\st_25d5faae25.exe | C:\Users\admin\AppData\Local\Temp\st_25d5faae25.exe | Stormshot.PC.V1.0_25d5faae25.exe | ||||||||||||
User: admin Company: FunPlus, Inc. Integrity Level: HIGH Description: Stormshot Exit code: 0 Version: 1, 0, 0, 96 Modules
| |||||||||||||||
Total events
2 993
Read events
2 983
Write events
10
Delete events
0
Modification events
| (PID) Process: | (6344) st_25d5faae25.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{304AB6C2-70F5-4A16-A5CA-2529CF4223E5}_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: "C:\Program Files (x86)\FunPlus\Stormshot\Launcher.exe" | |||
| (PID) Process: | (6344) st_25d5faae25.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{304AB6C2-70F5-4A16-A5CA-2529CF4223E5}_is1 |
| Operation: | write | Name: | DisplayName |
Value: Stormshot | |||
| (PID) Process: | (6344) st_25d5faae25.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{304AB6C2-70F5-4A16-A5CA-2529CF4223E5}_is1 |
| Operation: | write | Name: | DisplayVersion |
Value: 1.0.0.96 | |||
| (PID) Process: | (6344) st_25d5faae25.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{304AB6C2-70F5-4A16-A5CA-2529CF4223E5}_is1 |
| Operation: | write | Name: | Publisher |
Value: FunPlus, Inc. | |||
| (PID) Process: | (6344) st_25d5faae25.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{304AB6C2-70F5-4A16-A5CA-2529CF4223E5}_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\FunPlus\Stormshot\uninstall.exe" | |||
| (PID) Process: | (6344) st_25d5faae25.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{304AB6C2-70F5-4A16-A5CA-2529CF4223E5}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: "C:\Program Files (x86)\FunPlus\Stormshot" | |||
| (PID) Process: | (6344) st_25d5faae25.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{304AB6C2-70F5-4A16-A5CA-2529CF4223E5}_is1 |
| Operation: | write | Name: | EstimatedSize |
Value: 149718 | |||
| (PID) Process: | (420) PC-Launcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | st_global |
Value: C:\Program Files (x86)\FunPlus\Stormshot\Launcher.exe | |||
| (PID) Process: | (3676) Launcher.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\funplus.st |
| Operation: | write | Name: | URL Protocol |
Value: | |||
| (PID) Process: | (420) PC-Launcher.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\funplus.sdk |
| Operation: | write | Name: | orginuuid |
Value: p/zI1pFpOcMjSaXYw258DiyeY8zhuIIYrwvC/K+77ZVbZyCCwoyFsAKn2hErwfLv | |||
Executable files
88
Suspicious files
1 924
Text files
79
Unknown types
45
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3564 | Stormshot.PC.V1.0_25d5faae25.exe | C:\Users\admin\AppData\Local\Temp\st_tmp.dl | — | |
MD5:— | SHA256:— | |||
| 3564 | Stormshot.PC.V1.0_25d5faae25.exe | C:\Users\admin\AppData\Local\Temp\st_25d5faae25.exe | — | |
MD5:— | SHA256:— | |||
| 6344 | st_25d5faae25.exe | C:\Program Files (x86)\FunPlus\Stormshot\1.0.0.96\QtQml\RemoteObjects\qmldir | text | |
MD5:A1EDA6630C96C80E8FA7E8D870DF7516 | SHA256:46B7932B643C11FC40268BAEDC58004A70F1135C50CDE5D4BC2B7841864FBC12 | |||
| 6344 | st_25d5faae25.exe | C:\Program Files (x86)\FunPlus\Stormshot\1.0.0.96\QtQml\Models.2\qmldir | text | |
MD5:C6D831AD43AFA82977D838183DE61CD2 | SHA256:62F50F9B9AE3B9E6628DD2660B18D326C41794586E0D76B2E40F6FA4B182E0A7 | |||
| 6344 | st_25d5faae25.exe | C:\Program Files (x86)\FunPlus\Stormshot\1.0.0.96\fpx_config_pc | text | |
MD5:1AA7531D47B56ABD7855F18B316C5053 | SHA256:80DDBBC093AAEABA141BE65A4AF592A94EB77F8BBEB39652A5BA70851EE6BC9B | |||
| 6344 | st_25d5faae25.exe | C:\Program Files (x86)\FunPlus\Stormshot\config\icon.png | image | |
MD5:F484B35957374F16D904FC7D9ECD14CD | SHA256:7A9184EF47BDF12A42D98818AD40478F3D66D75414BFFDE87050442CD764660F | |||
| 6344 | st_25d5faae25.exe | C:\Program Files (x86)\FunPlus\Stormshot\Plugin\7z.21.07\Far\far7z.txt | text | |
MD5:E1FA666BC582130D4700A3FA7EA77A2B | SHA256:6F464CF2417FE86D88634A3BE72060B26B4CE695B9BF60E46B1D8FCE8835B2E5 | |||
| 6344 | st_25d5faae25.exe | C:\Program Files (x86)\FunPlus\Stormshot\config\version.ini | text | |
MD5:7A161DA22107D90A6A0DB79BDF9B8A95 | SHA256:54C5C1872A98C0D09056F0B03DAE9F794468A7267811996E263F9568F3E0B664 | |||
| 6344 | st_25d5faae25.exe | C:\Program Files (x86)\FunPlus\Stormshot\Plugin\7z.21.07\readme.txt | text | |
MD5:7435A38214A1CC5052E2C7862847AE1E | SHA256:2C508A6E488ACC2DDD4746521FF3587153FA8131B66E115D2BB5C9BF9D1617E9 | |||
| 6344 | st_25d5faae25.exe | C:\Program Files (x86)\FunPlus\Stormshot\Plugin\7z.21.07\Far\7-ZipRus.hlf | text | |
MD5:2007D21372287C4F47428A80627BE970 | SHA256:7445799449B41A7B1A57E4A4A971E3006AE21658A386E82BC612274A517B86D6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
44
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2596 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
432 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
432 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 92.123.17.129:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
472 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3564 | Stormshot.PC.V1.0_25d5faae25.exe | 54.188.242.131:443 | kg-logagent-st.kingsgroupgames.com | AMAZON-02 | US | unknown |
3564 | Stormshot.PC.V1.0_25d5faae25.exe | 2.16.168.123:443 | userplatform-download.akamaized.net | Akamai International B.V. | RU | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2596 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2596 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
kg-logagent-st.kingsgroupgames.com |
| unknown |
userplatform-download.akamaized.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
st_25d5faae25.exe | OnSize, nType=0 size=720,410
|
st_25d5faae25.exe | OnSize, nType=0 size=720,410
|
PC-Launcher.exe | QCursor: Cannot create bitmap cursor; invalid bitmap(s)
|
PC-Launcher.exe | QLayout: Attempting to add QLayout "" to MainWindow "", which already has a layout
|