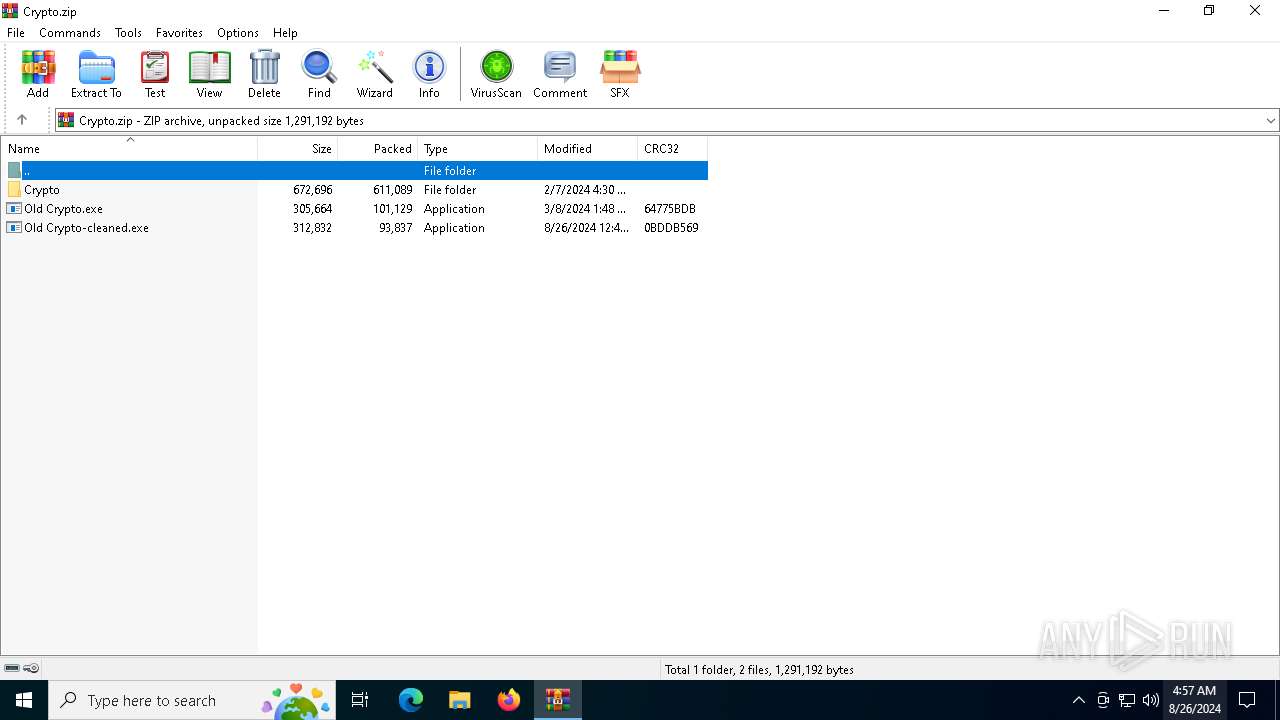
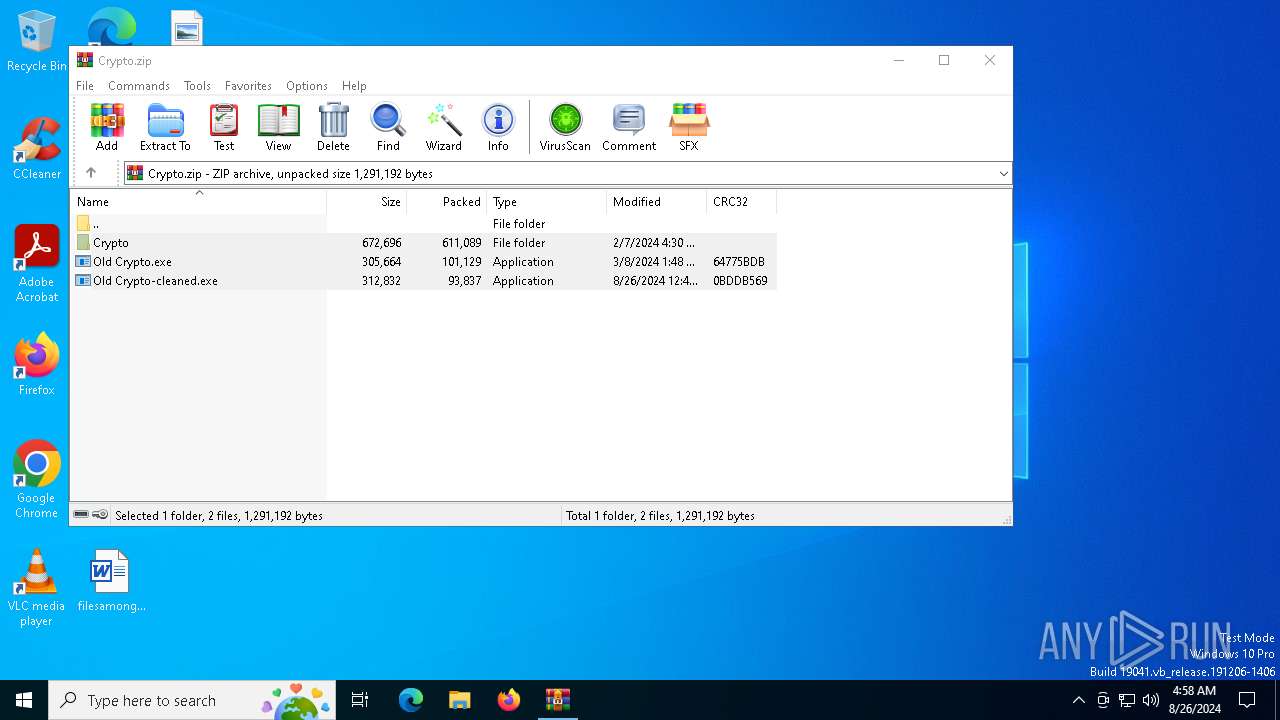
| File name: | Crypto.zip |
| Full analysis: | https://app.any.run/tasks/a5476782-dc9a-4de1-af7d-9d4ec7b565eb |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 04:57:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F0590242D0023D2826C280A4E738ECDA |
| SHA1: | 203DC03C0BE1027040737A1ADA4FCC0BFE529968 |
| SHA256: | FFBBF456F81412AFBBFC820E6C1895E7BCEDD759D87850B25440E01D9705F627 |
| SSDEEP: | 24576:AtQ53MDaIkVW16h/j+j/55jM9DM5f2xMBbbv55uJLyY0AOSH8+dOULaM8w6fuhFr:AtQ53caIkVWch/j+j/55jM9DM5f2xMB2 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6700)
Uses WMIC.EXE to obtain Windows Installer data
- Old Crypto-cleaned.exe (PID: 7012)
- Old Crypto.exe (PID: 6540)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7100)
- WMIC.exe (PID: 6544)
Checks for external IP
- svchost.exe (PID: 2256)
- Old Crypto-cleaned.exe (PID: 7012)
- Old Crypto.exe (PID: 6540)
INFO
Checks supported languages
- Old Crypto-cleaned.exe (PID: 7012)
- Old Crypto.exe (PID: 6540)
Reads the computer name
- Old Crypto-cleaned.exe (PID: 7012)
- Old Crypto.exe (PID: 6540)
Reads the machine GUID from the registry
- Old Crypto-cleaned.exe (PID: 7012)
- Old Crypto.exe (PID: 6540)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6700)
Manual execution by a user
- Old Crypto-cleaned.exe (PID: 7012)
- Old Crypto.exe (PID: 6540)
Disables trace logs
- Old Crypto-cleaned.exe (PID: 7012)
- Old Crypto.exe (PID: 6540)
Reads Environment values
- Old Crypto-cleaned.exe (PID: 7012)
- Old Crypto.exe (PID: 6540)
Checks proxy server information
- Old Crypto-cleaned.exe (PID: 7012)
- Old Crypto.exe (PID: 6540)
Reads the software policy settings
- Old Crypto-cleaned.exe (PID: 7012)
- Old Crypto.exe (PID: 6540)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7100)
- WMIC.exe (PID: 6544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:08 05:48:42 |
| ZipCRC: | 0x64775bdb |
| ZipCompressedSize: | 101129 |
| ZipUncompressedSize: | 305664 |
| ZipFileName: | Old Crypto.exe |
Total processes
133
Monitored processes
8
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6540 | "C:\Users\admin\Desktop\Old Crypto.exe" | C:\Users\admin\Desktop\Old Crypto.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6544 | "wmic.exe" csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | Old Crypto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6600 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6700 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Crypto.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7012 | "C:\Users\admin\Desktop\Old Crypto-cleaned.exe" | C:\Users\admin\Desktop\Old Crypto-cleaned.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 7100 | "wmic.exe" csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | Old Crypto-cleaned.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 815
Read events
7 768
Write events
47
Delete events
0
Modification events
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Crypto.zip | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
2
Suspicious files
1
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.9331\Crypto\assets\258f73b8.svg | image | |
MD5:61D9CAA8FB9638CE1E8C73BB9495A169 | SHA256:EC93A05FC1F25CF0D8D33D39B4F3864AA777405449DBF86A096002FBB2EA9633 | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.9331\Old Crypto.exe | executable | |
MD5:10742D08BEA1F728B4E3E094D4337119 | SHA256:481B30B6513779833D38A37739A7F71017254038FFD664D025E9C1A45FD3FA6B | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.9331\Crypto\assets\ac6a091c.svg | image | |
MD5:32C3E517D843663ECEB59AB38839C8B3 | SHA256:CB3641C4CC60D90139EF553D97137D0C657AA15E77BF6DC4EC49ADB94A5769A1 | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.9331\Crypto\assets\626abc69.svg | image | |
MD5:915280DC9790FA93B5D63250ABB1E4B0 | SHA256:F43BD942E519B9733450A9C538934474A5FE49F099A94293769D847E340FC930 | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.9331\Crypto\assets\9687118b.css | text | |
MD5:CAF6485ABD2FF89F9AEE5D7BADDFF278 | SHA256:A510F979FDC0EFBDEC7D854315A66B4E3DFB0F637DCF68E054E3B1A49ADC3CDB | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.9331\Crypto\assets\9feca606.png | image | |
MD5:4E4E7C36A70B1AA65B434DDCD4840B9D | SHA256:8D01D641DCB13588545C990271C2D0ED0BE5D4BE71153EA2D37B898190A8CE6B | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.9331\Crypto\assets\8261a1f0.svg | image | |
MD5:00FC724FC21846B2938FF04E4CE0612D | SHA256:22C1B0A23F90C2F02DF46BBA81D3AF66105DEA1FDC6E9A7558080CAC7204B448 | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.9331\Crypto\assets\bff4c7c0.svg | image | |
MD5:9C4BD31A54F7E53F714CFC617CB4D688 | SHA256:BFF4C7C0E3884A6AC68D2F0D48542B6D78F9465C28CBEB37974A00362437861F | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.9331\Crypto\assets\64906a61.svg | image | |
MD5:880CE4630A49F7EBC438D72E152CC875 | SHA256:ABF03325A8062258104C99EF4FEF711DE89BD49754B9D08A674C73F9CD48095D | |||
| 6700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6700.9331\Crypto\assets\65610dd3.svg | image | |
MD5:A186A9A3EF9528FCB5C3FE0542EC01C8 | SHA256:D803C62BF746950C521127B4457E21090BC2A22B1655B137A339A42844409CDB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
27
DNS requests
17
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7012 | Old Crypto-cleaned.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
5156 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6204 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6204 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6540 | Old Crypto.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5284 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3308 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5284 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7012 | Old Crypto-cleaned.exe | 216.58.206.67:443 | gstatic.com | GOOGLE | US | whitelisted |
7012 | Old Crypto-cleaned.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | unknown |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
gstatic.com |
| whitelisted |
ip-api.com |
| shared |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
7012 | Old Crypto-cleaned.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
7012 | Old Crypto-cleaned.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6540 | Old Crypto.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
6540 | Old Crypto.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |