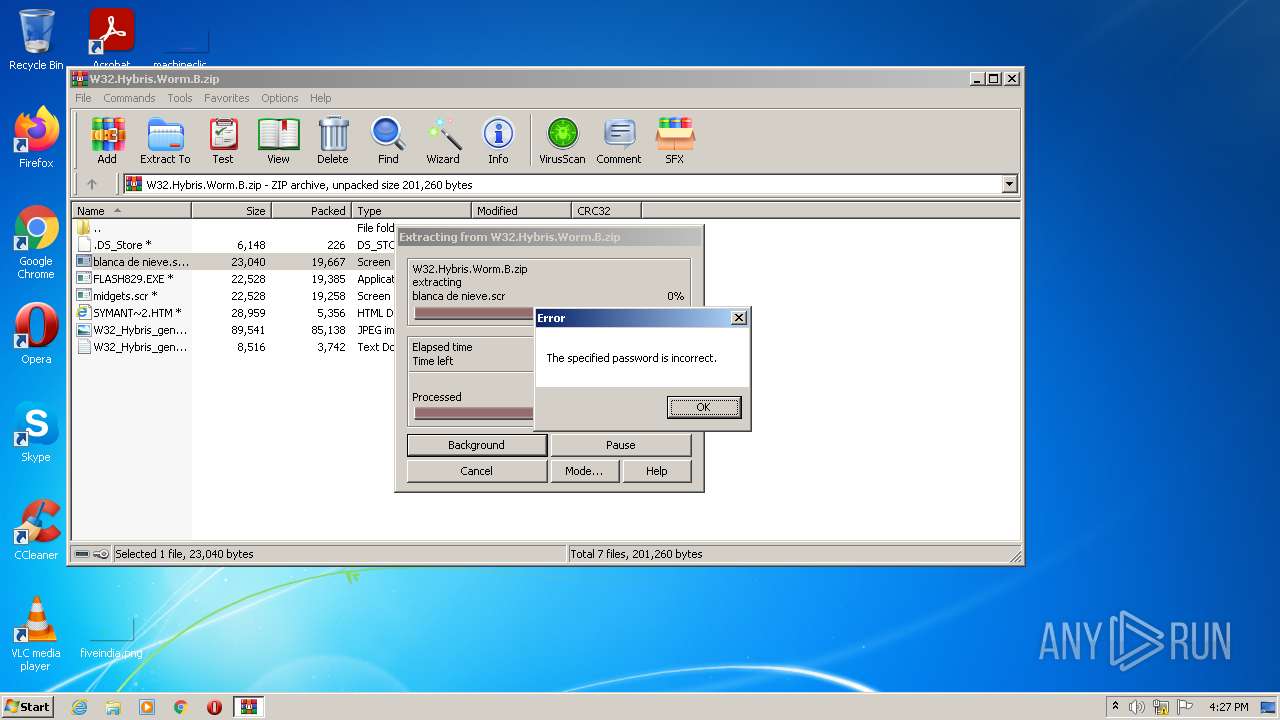
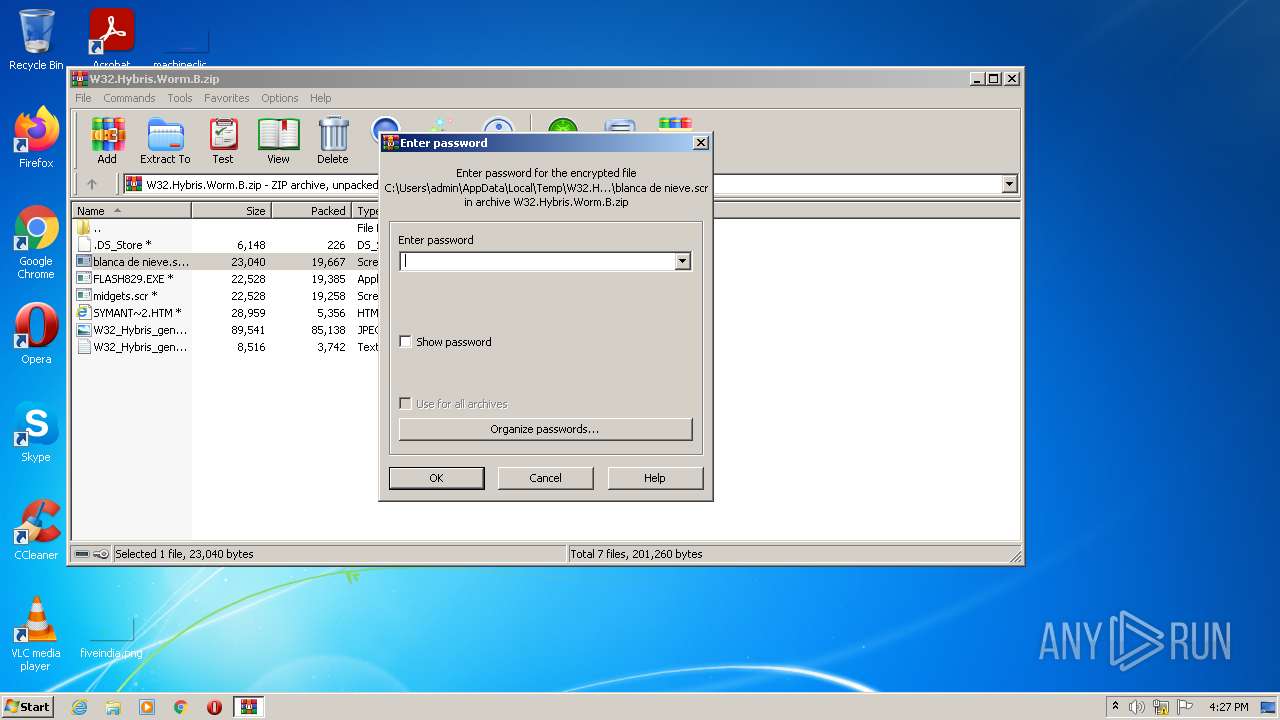
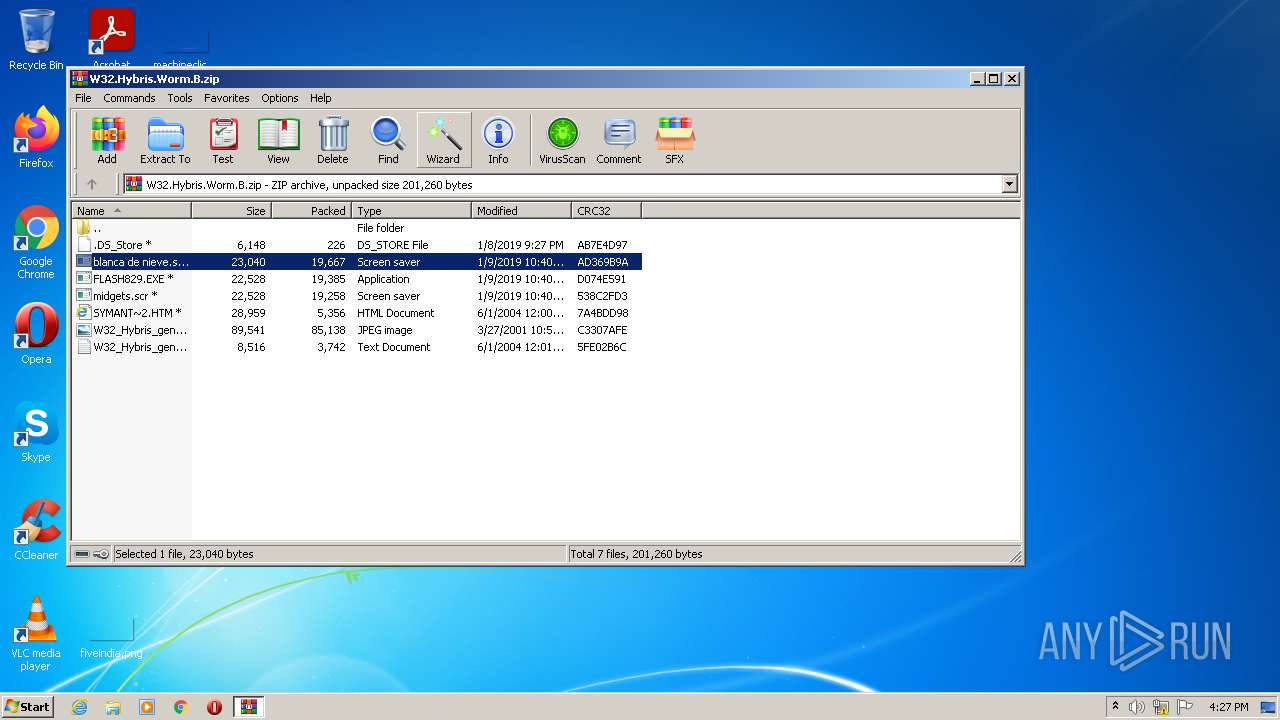
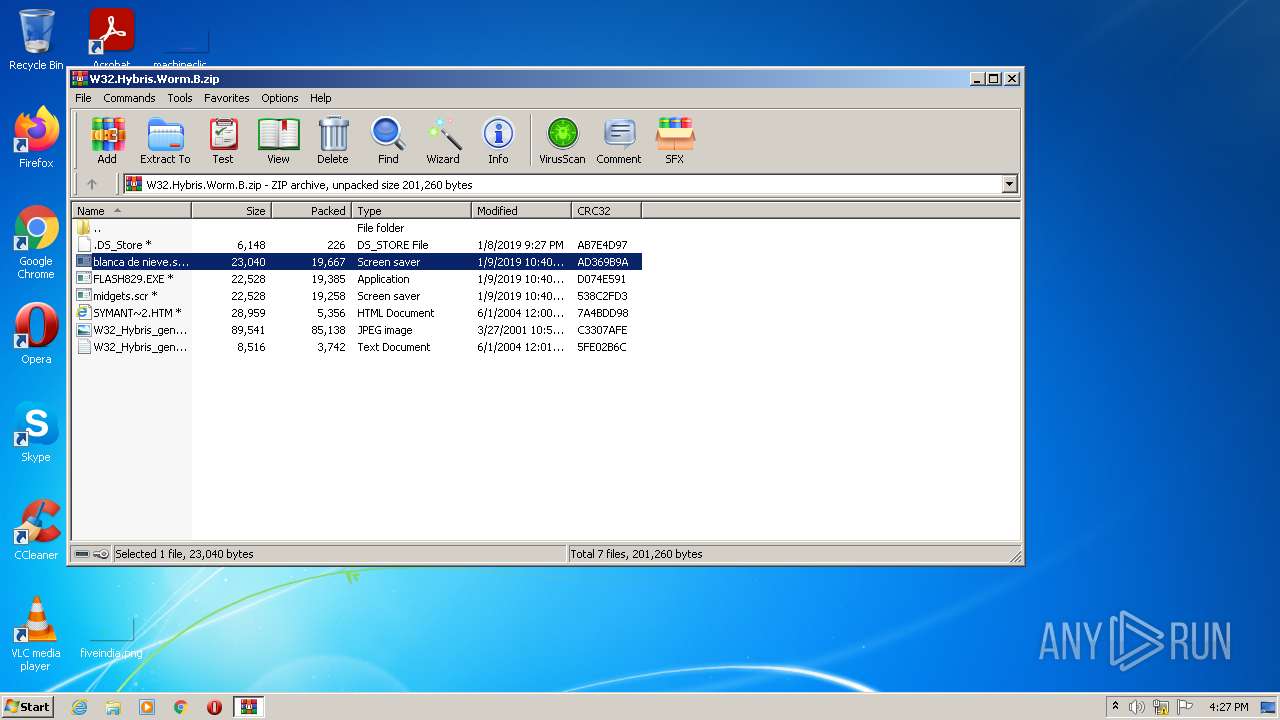
| download: | W32.Hybris.Worm.B.zip |
| Full analysis: | https://app.any.run/tasks/22475aff-7c3a-4877-9dee-d72d62d91fc0 |
| Verdict: | Malicious activity |
| Analysis date: | February 09, 2022, 16:26:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 34B5039109DB86C92C1FDB982E6A22B6 |
| SHA1: | EA1AC961E6BE79CC9432A6DBF6E343EF89F1EE0E |
| SHA256: | FF96BB9E84A7BD2D51139F52EF4FF7CD20175A5335F82BFEFF03EEE6B52AD8DF |
| SSDEEP: | 3072:wuxXs4zc6TN32zfZ8IhRVJpIaKaM/mp+HFyAMUHk6sMk:Hi4zXtsZ8wJLZ+YADk6Nk |
MALICIOUS
Drops executable file immediately after starts
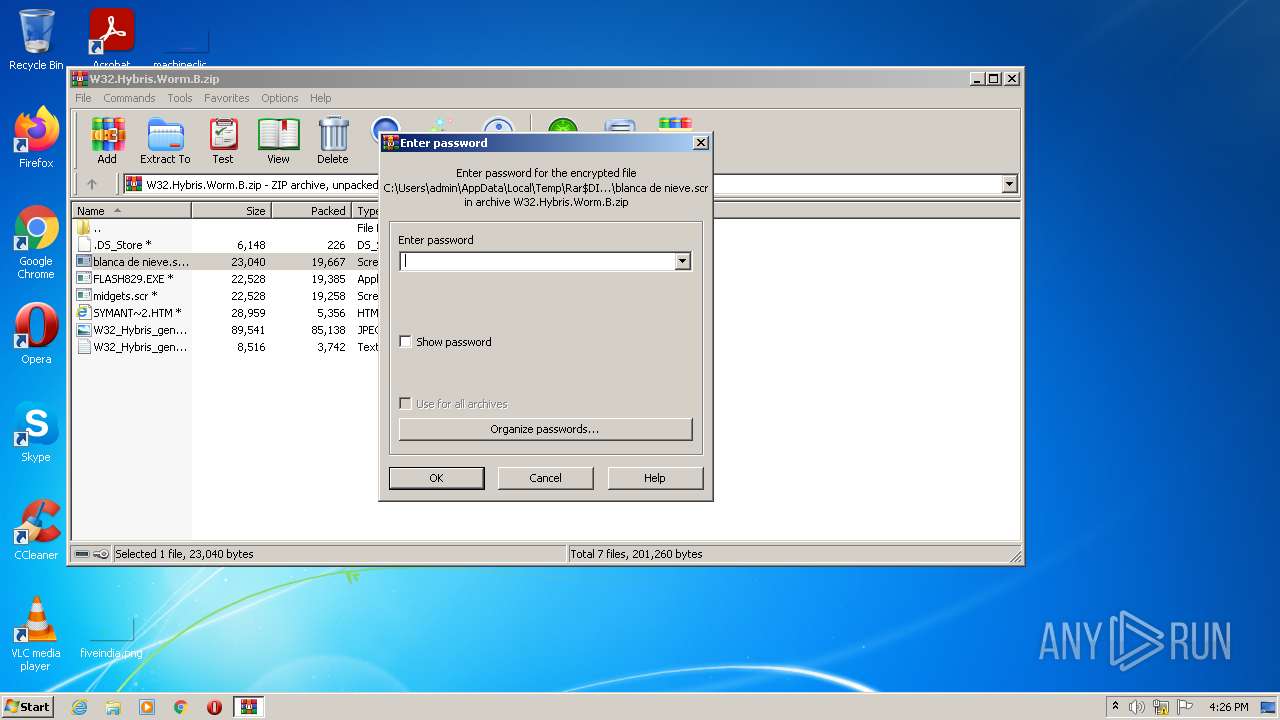
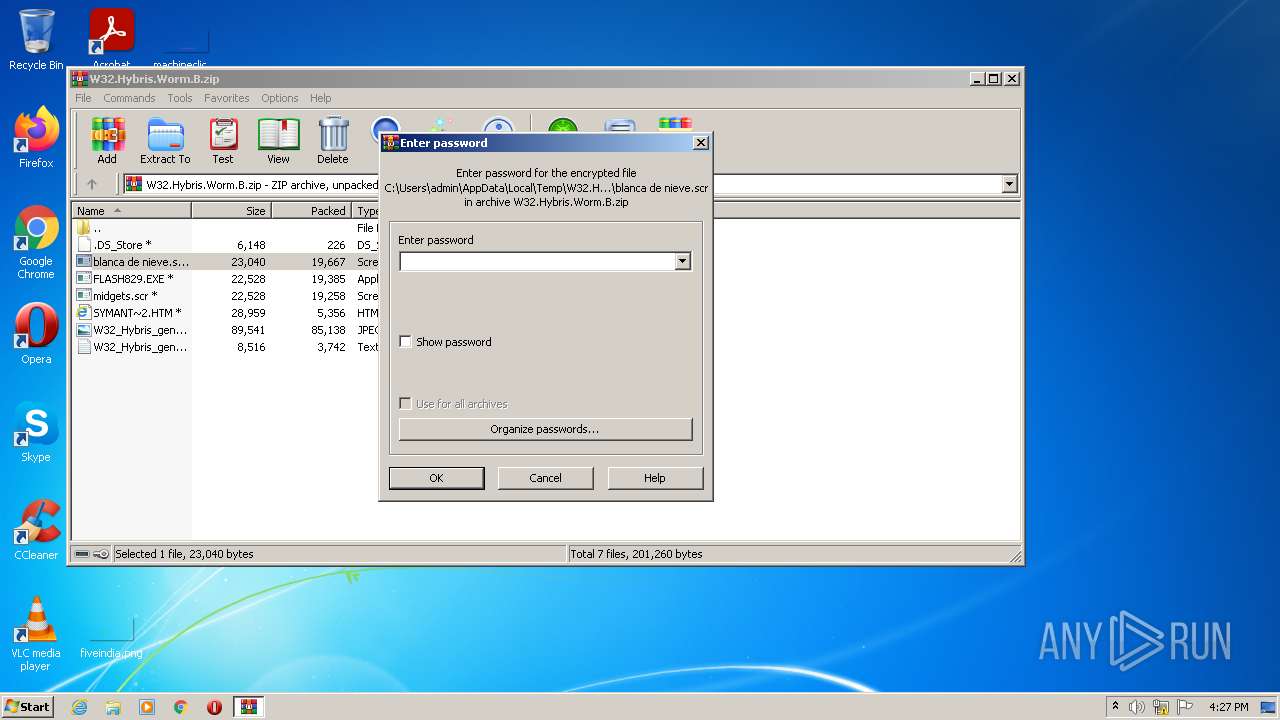
- blanca de nieve.scr (PID: 2812)
Application was dropped or rewritten from another process
- blanca de nieve.scr (PID: 2812)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3780)
Checks supported languages
- WinRAR.exe (PID: 3780)
- blanca de nieve.scr (PID: 2812)
Executable content was dropped or overwritten
- blanca de nieve.scr (PID: 2812)
- WinRAR.exe (PID: 3780)
Starts application with an unusual extension
- WinRAR.exe (PID: 3780)
Executed via COM
- DllHost.exe (PID: 2936)
Drops a file with too old compile date
- blanca de nieve.scr (PID: 2812)
- WinRAR.exe (PID: 3780)
Drops a file that was compiled in debug mode
- blanca de nieve.scr (PID: 2812)
INFO
Reads the computer name
- DllHost.exe (PID: 2936)
Checks supported languages
- DllHost.exe (PID: 2936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
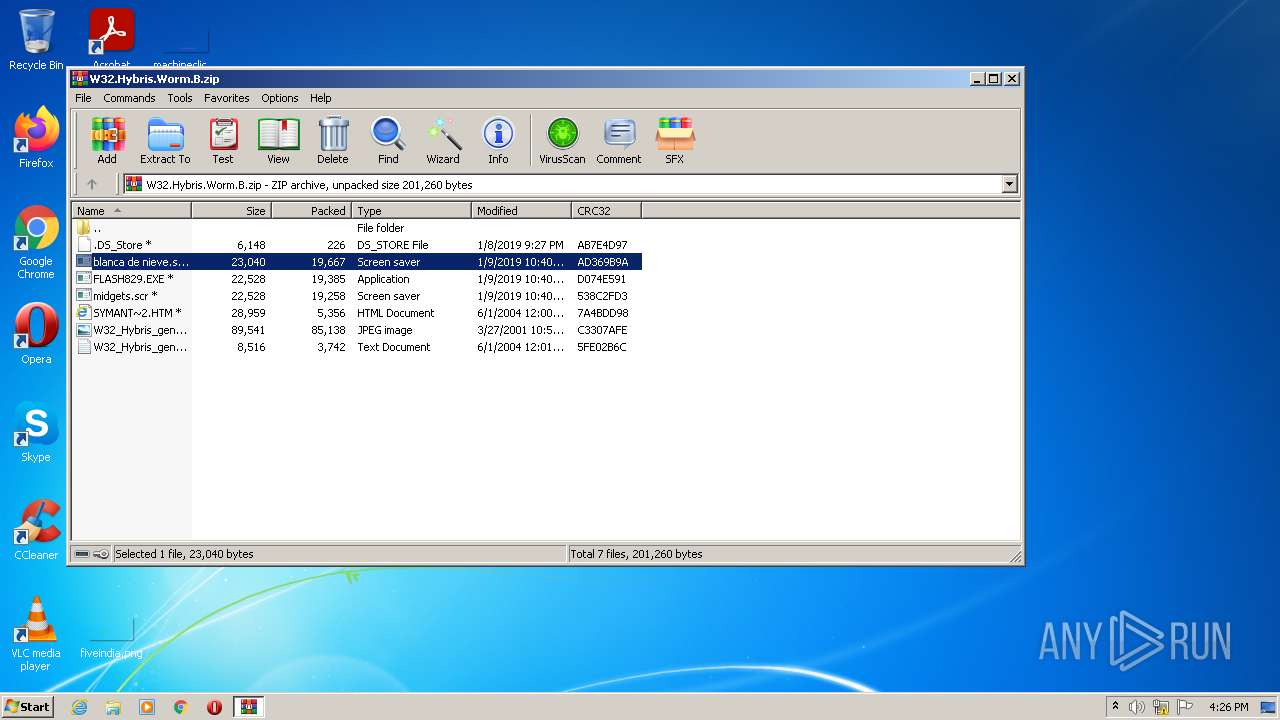
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | .DS_Store |
|---|---|
| ZipUncompressedSize: | 6148 |
| ZipCompressedSize: | 226 |
| ZipCRC: | 0xab7e4d97 |
| ZipModifyDate: | 2019:01:08 21:27:04 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 788 |
Total processes
36
Monitored processes
3
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2812 | "C:\Users\admin\AppData\Local\Temp\Rar$DIb3780.16818\blanca de nieve.scr" /S | C:\Users\admin\AppData\Local\Temp\Rar$DIb3780.16818\blanca de nieve.scr | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1977959898 Modules
| |||||||||||||||
| 2936 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3780 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\W32.Hybris.Worm.B.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 233
Read events
1 189
Write events
44
Delete events
0
Modification events
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\W32.Hybris.Worm.B.zip | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3780) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3780.16051\W32_Hybris_gen_MMVirus.jpg | image | |
MD5:1B8DAB654906824459269C88BB608F86 | SHA256:8F594D158E4143B3100F2AB9A673FF20E42364958C5251D2719E00A4EA1F989A | |||
| 3780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3780.16818\blanca de nieve.scr | executable | |
MD5:701DE4ADE46048FA65BDFB8EA73FB818 | SHA256:671B761CEFBD0FE347CAB620F0E43AFAAD0897136492A1C91112BBF45B46385A | |||
| 3780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\W32.Hybris.Worm.B\blanca de nieve.scr | executable | |
MD5:701DE4ADE46048FA65BDFB8EA73FB818 | SHA256:671B761CEFBD0FE347CAB620F0E43AFAAD0897136492A1C91112BBF45B46385A | |||
| 2812 | blanca de nieve.scr | C:\Users\admin\AppData\Local\VirtualStore\Windows\System32\ABGHHLCO | executable | |
MD5:DF13A51A5C591887D2EC6AE64CEED0FA | SHA256:DFD503AEBCAA056B2B0E669ACA52F6D26F4E6892F2DCFCCD902752C23A621653 | |||
| 2812 | blanca de nieve.scr | C:\Users\admin\AppData\Local\VirtualStore\Windows\WININIT.INI | text | |
MD5:F7613AFB326738E602A5029D3DEB320C | SHA256:E1EF7E122323687A7009DB9F38503CAB9CC54E0E8F7974BCA02B6AD35DB0505D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report