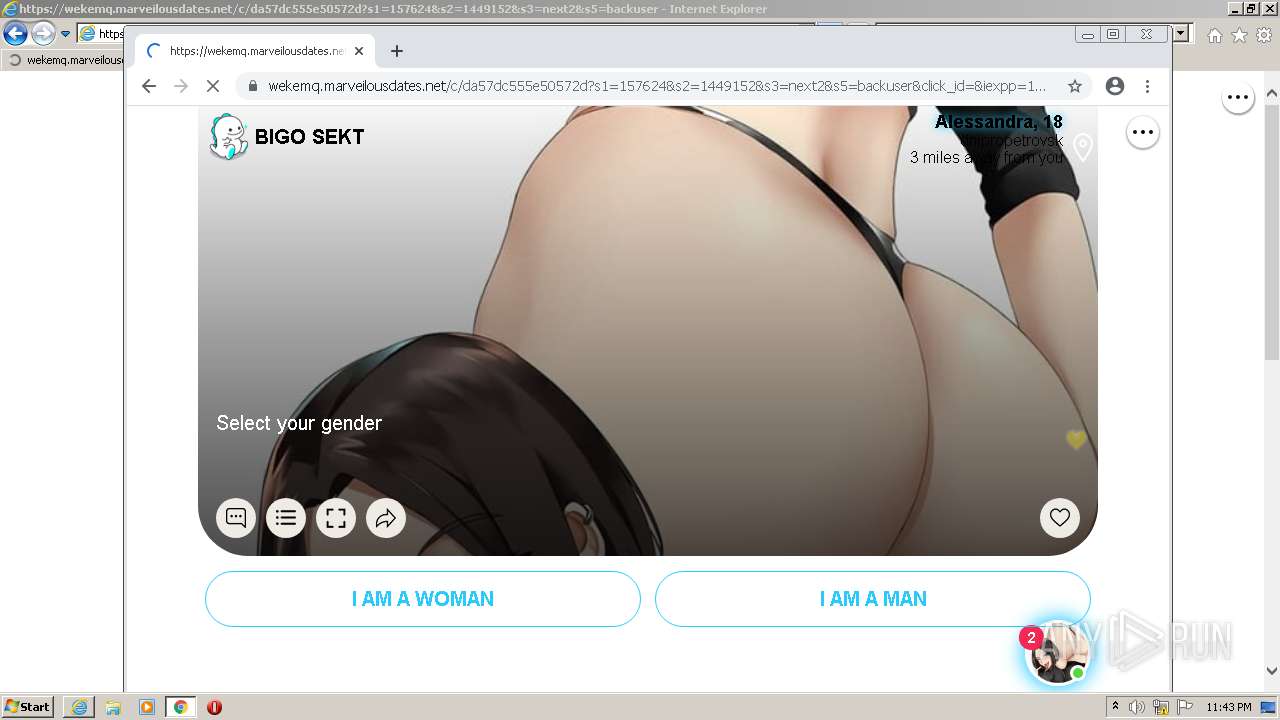
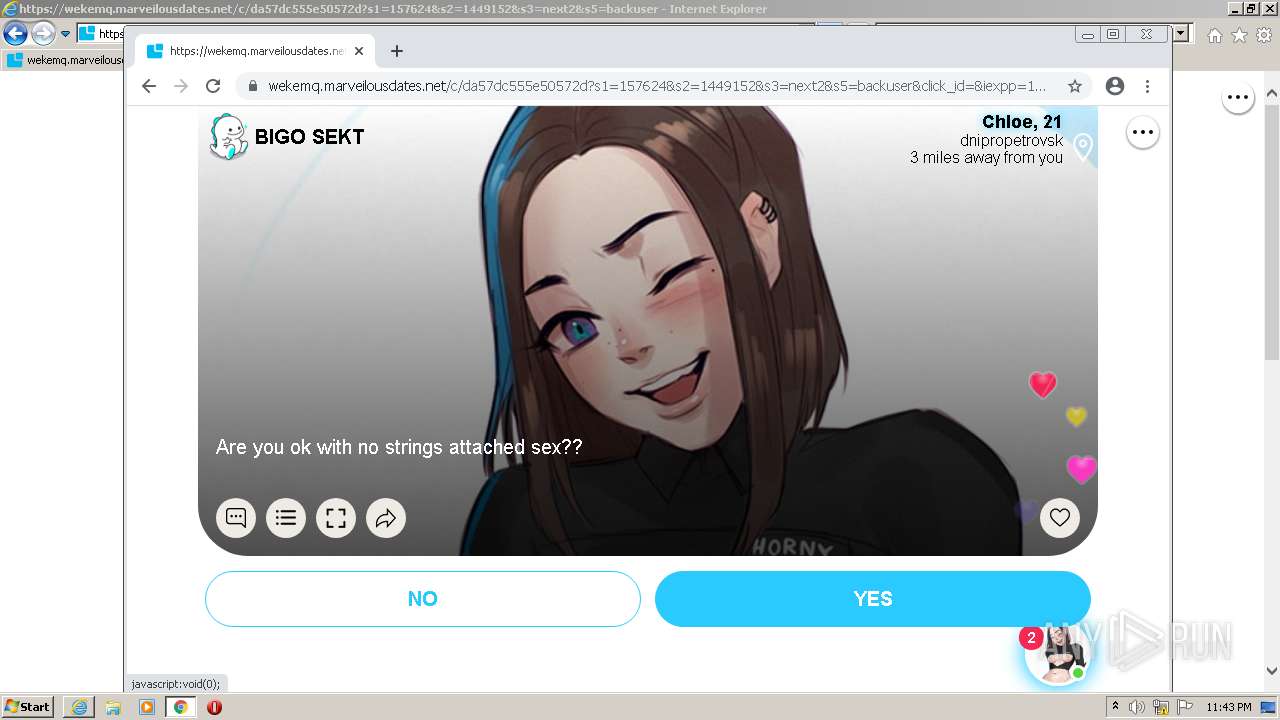
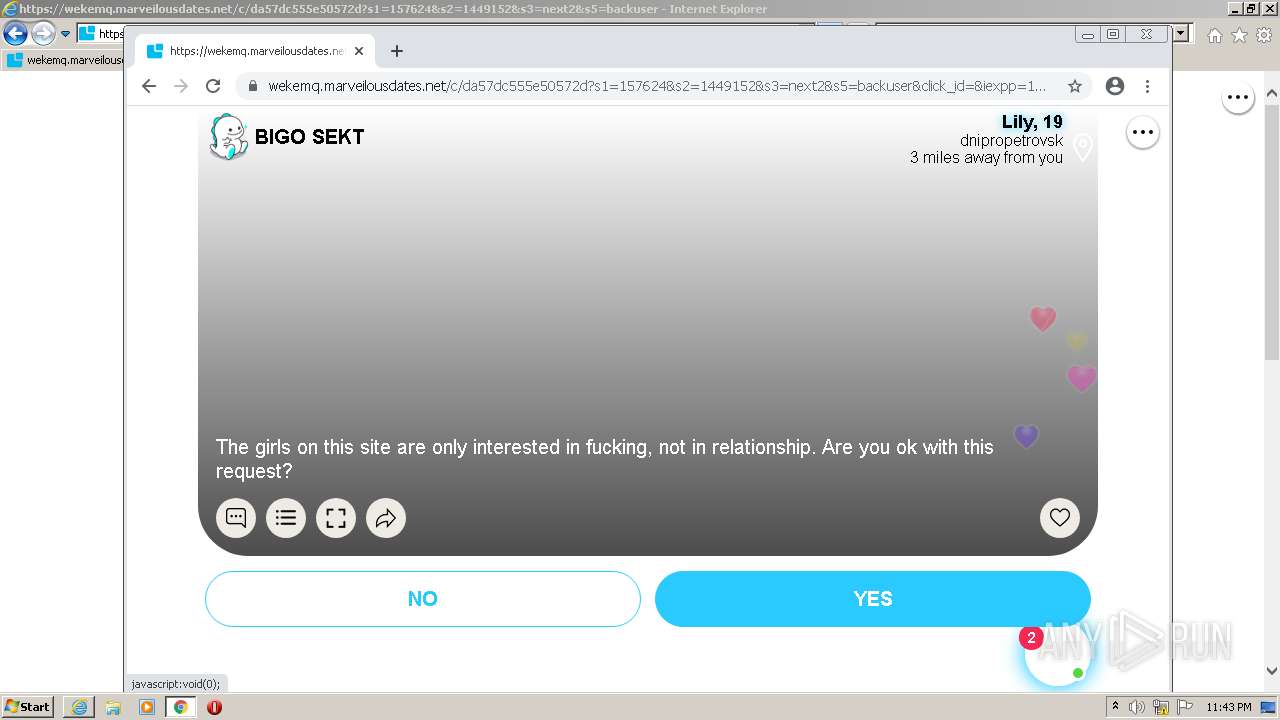
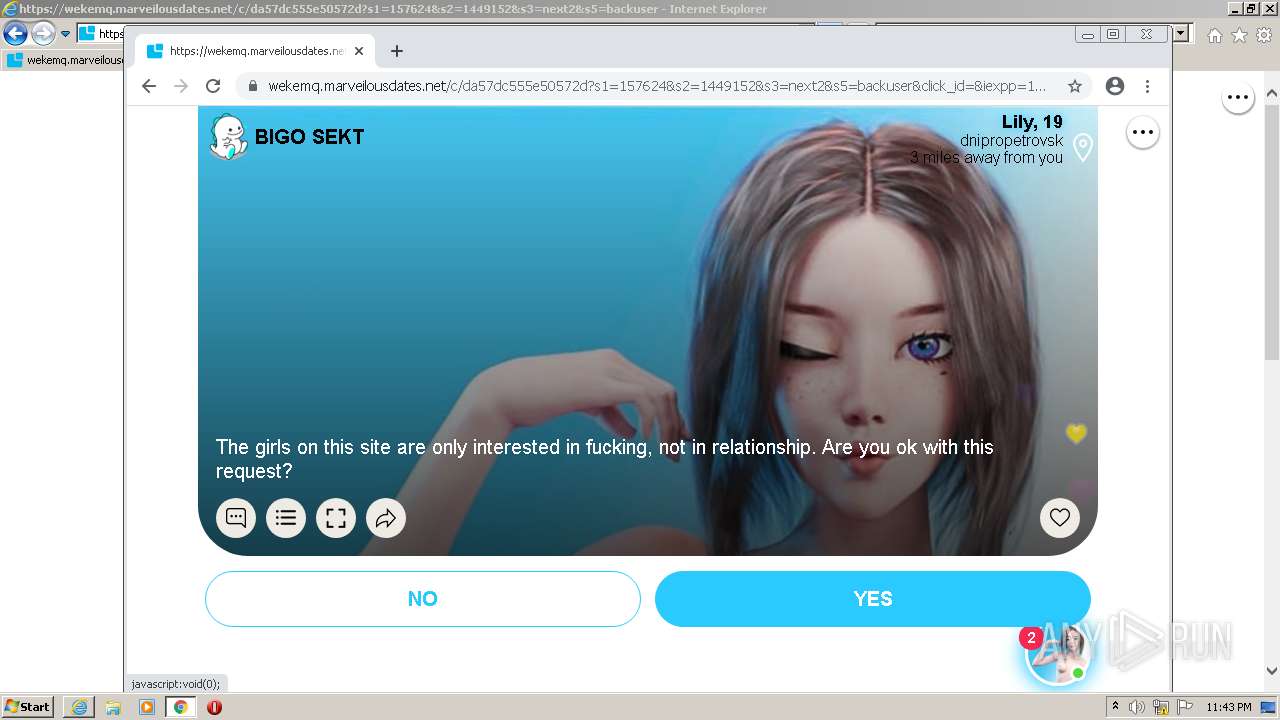
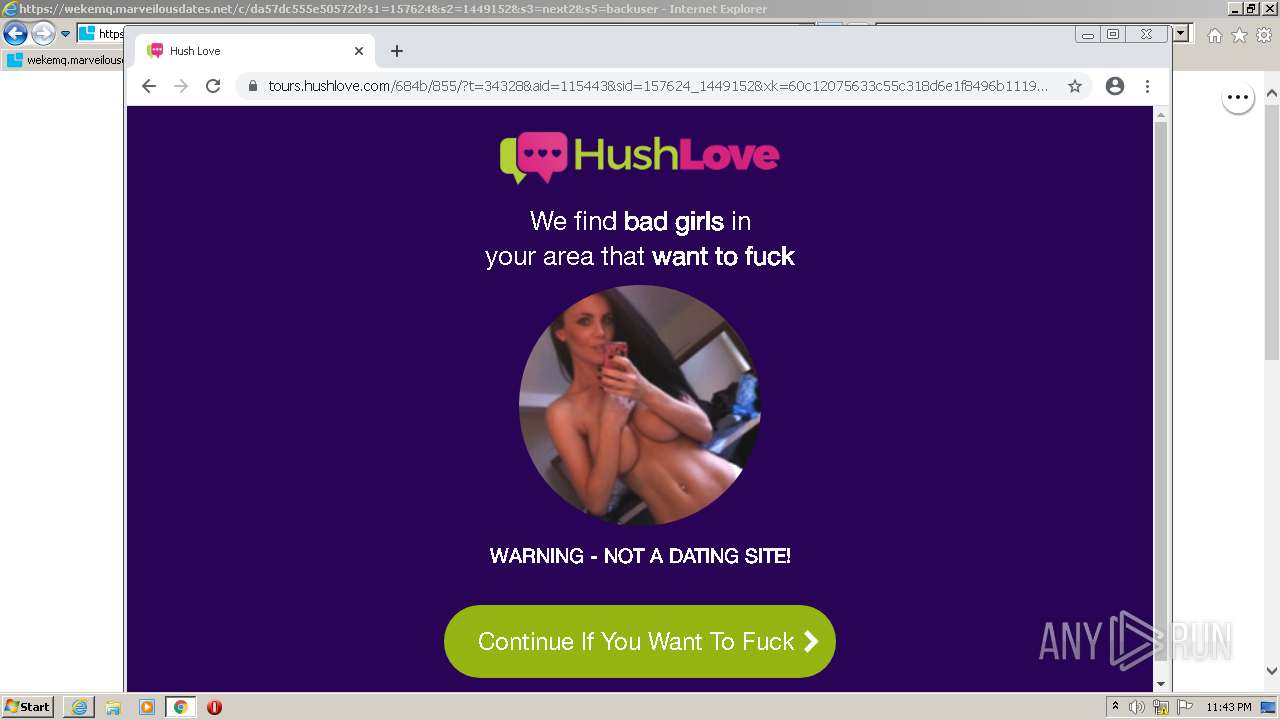
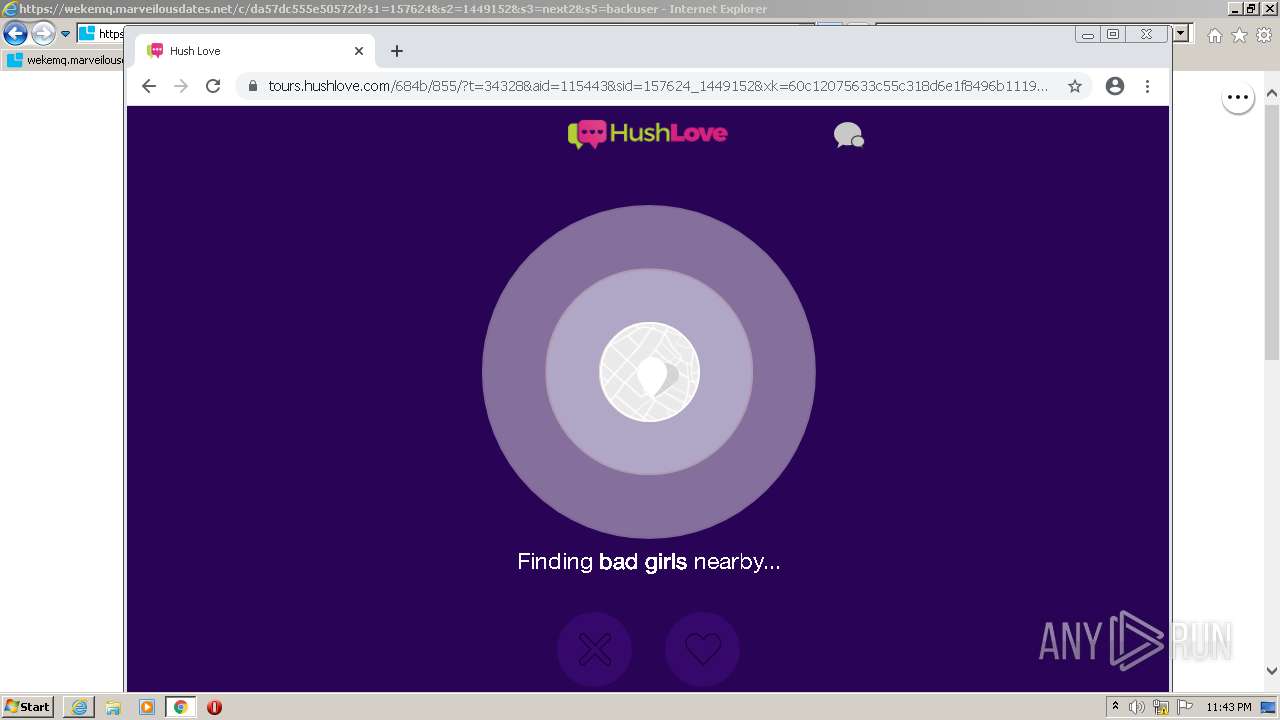
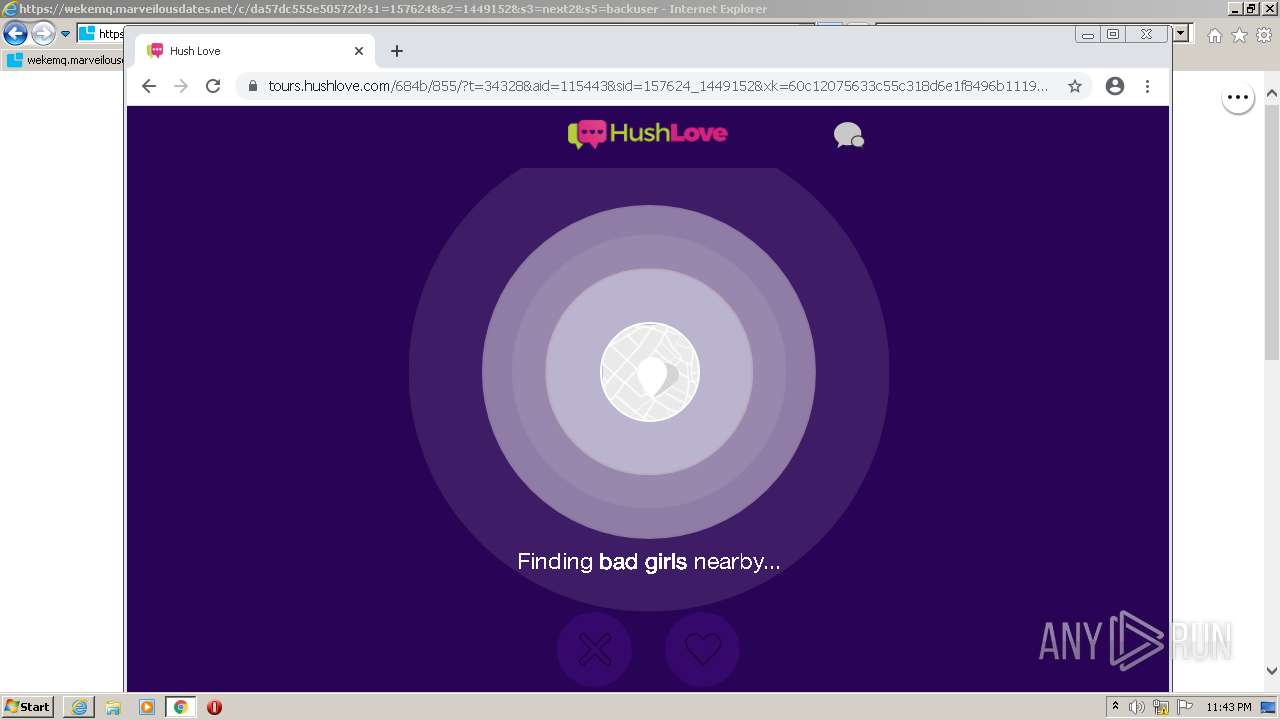
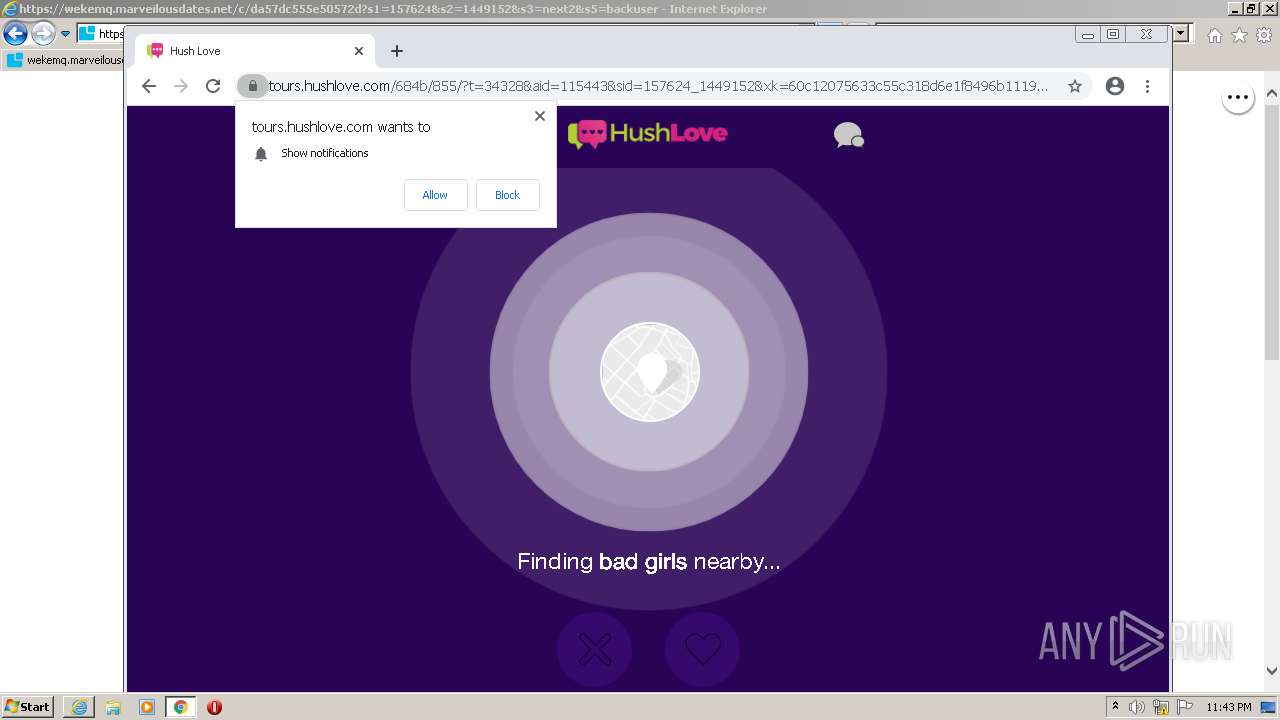
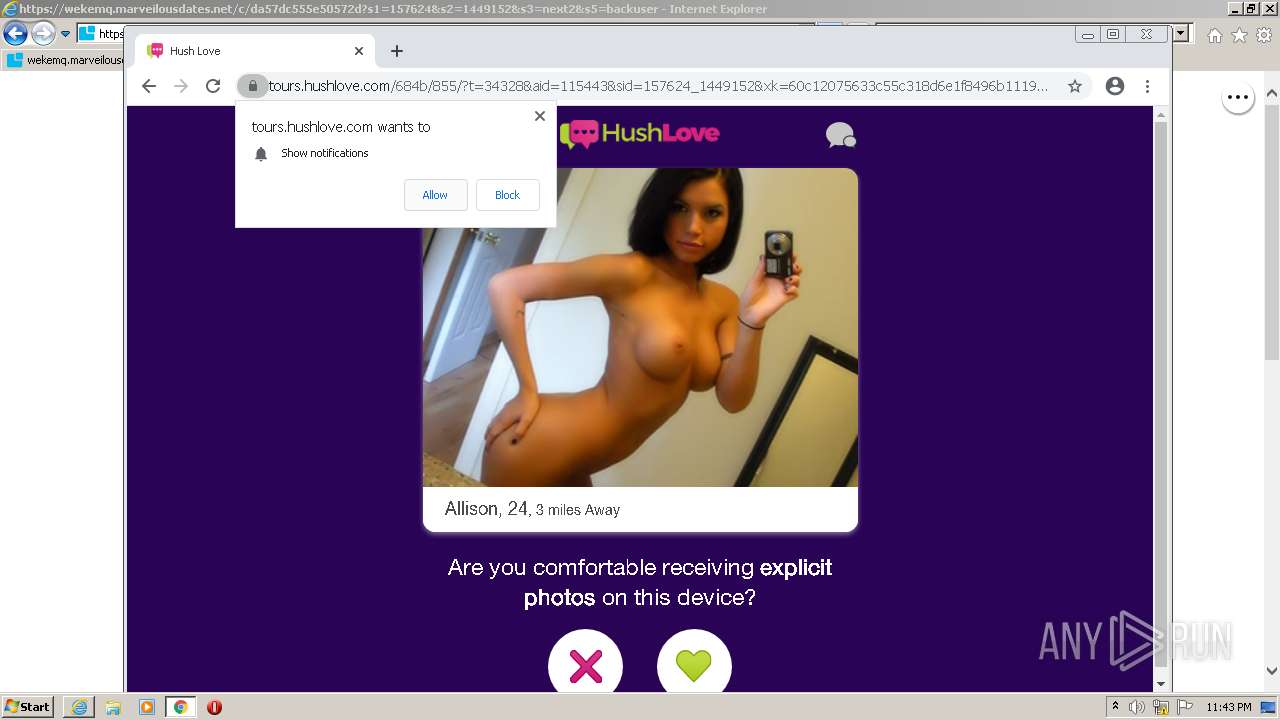
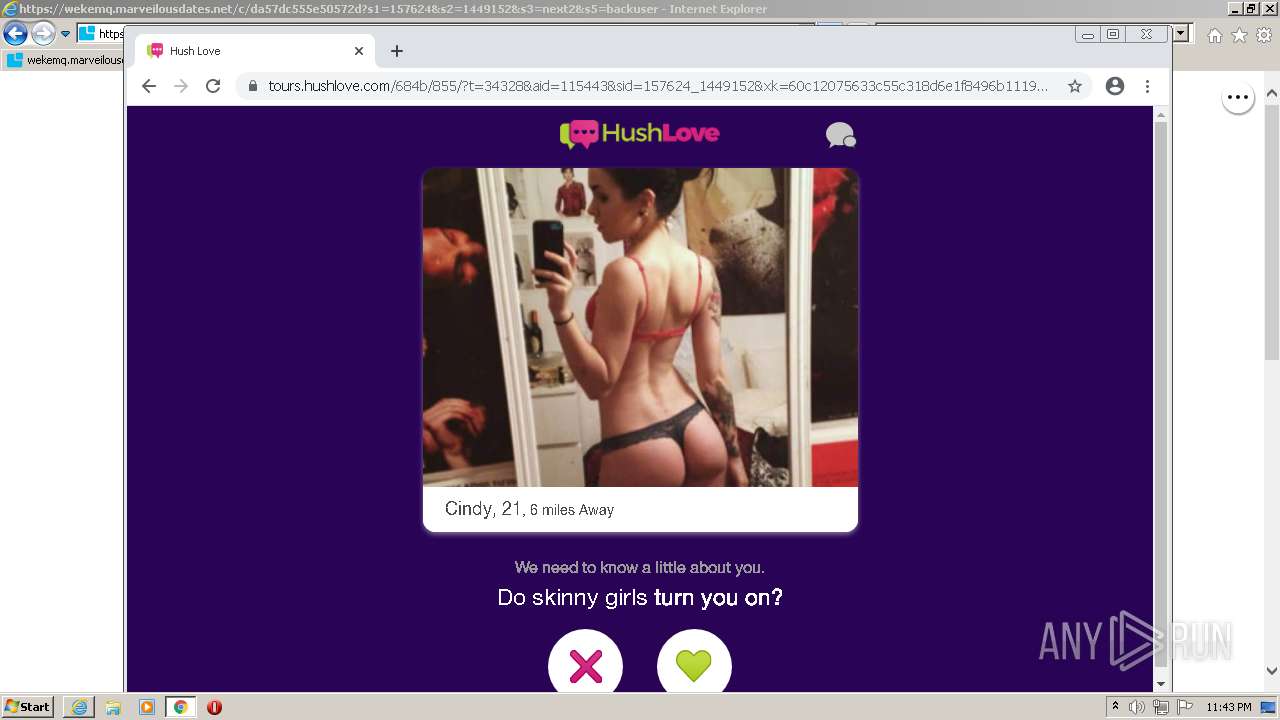
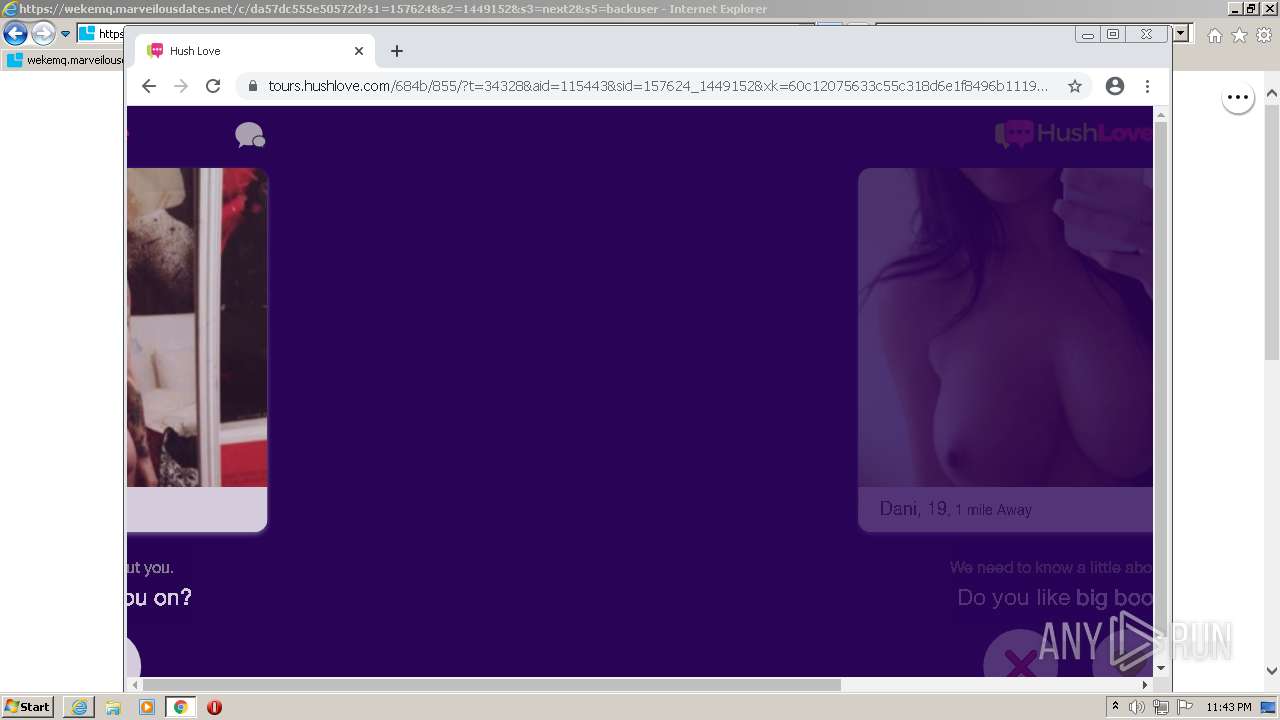
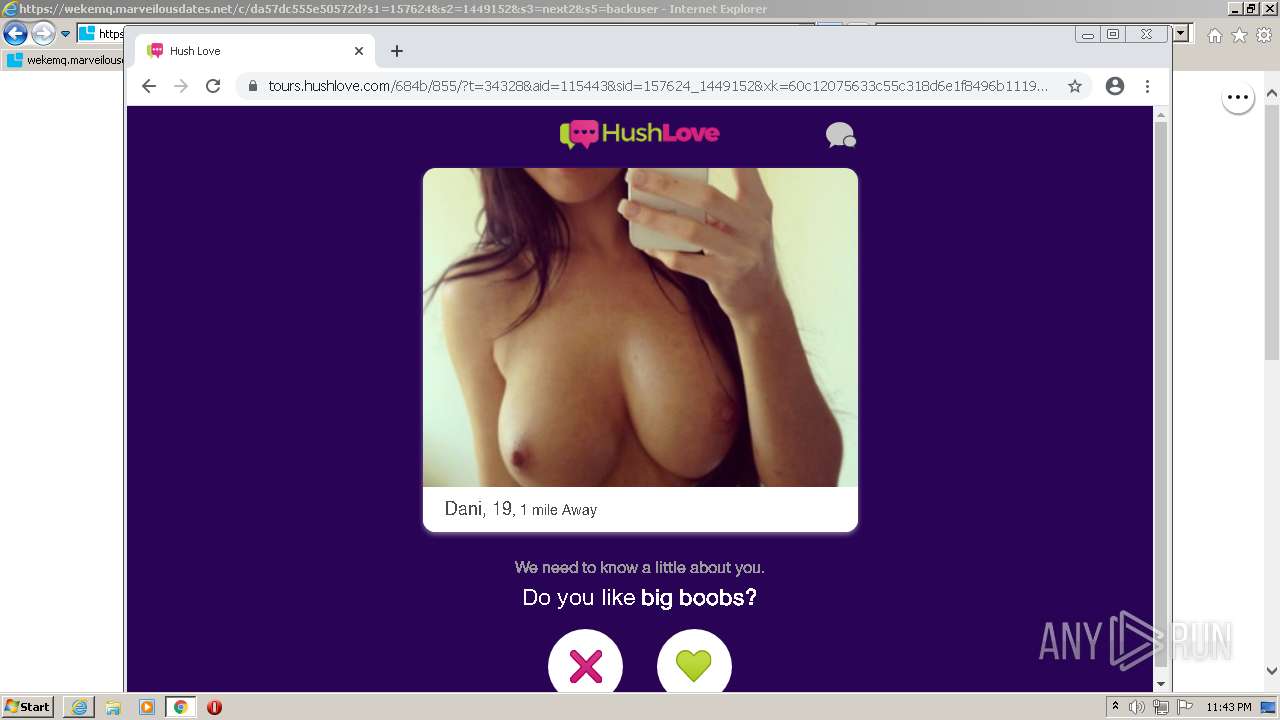
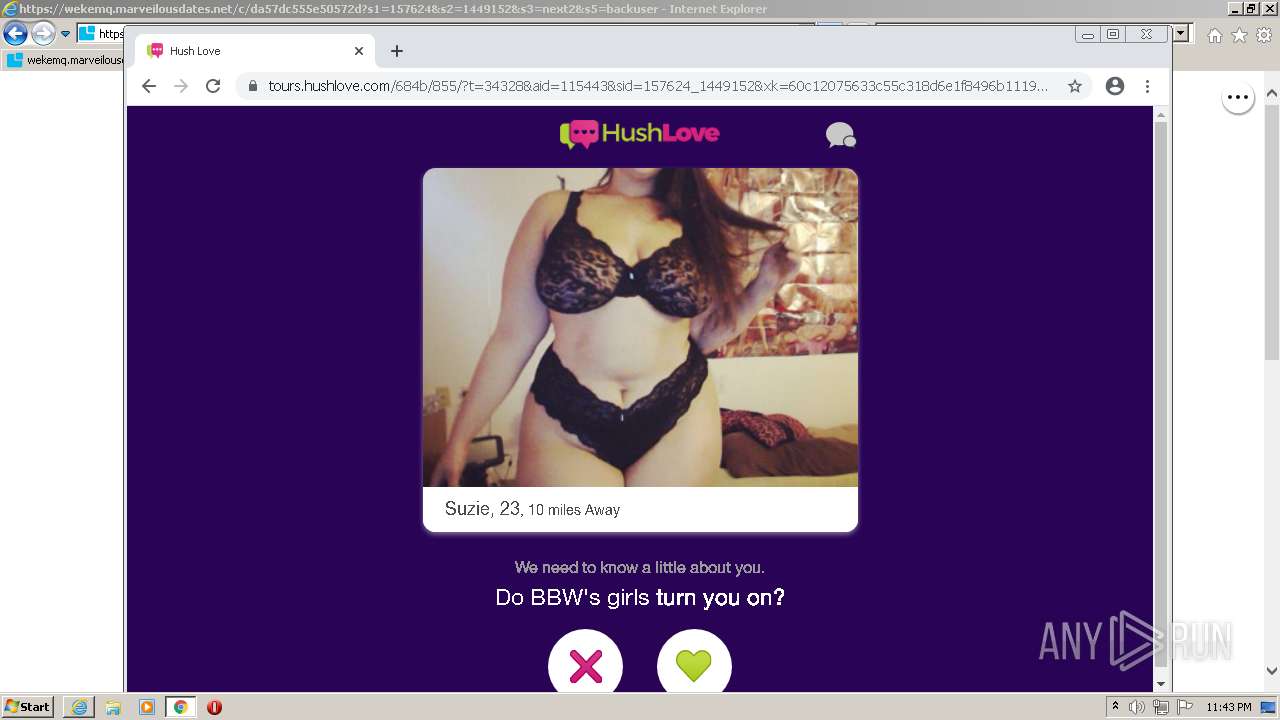
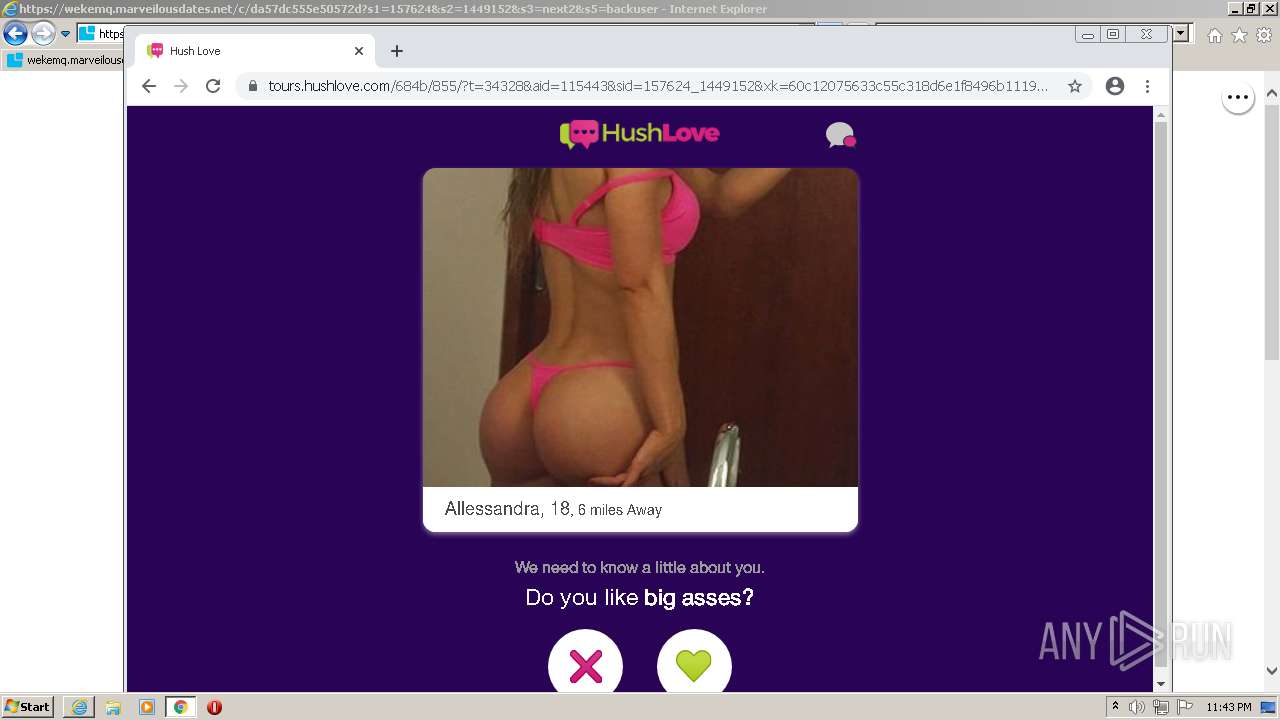
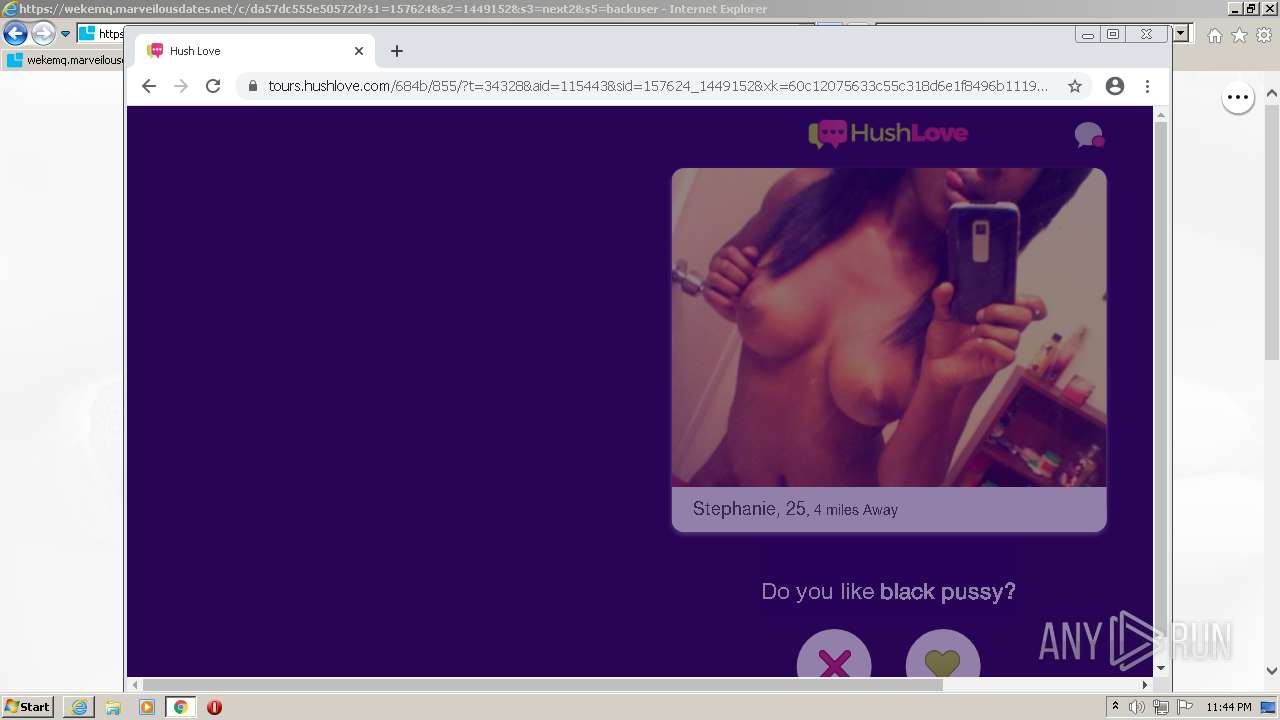
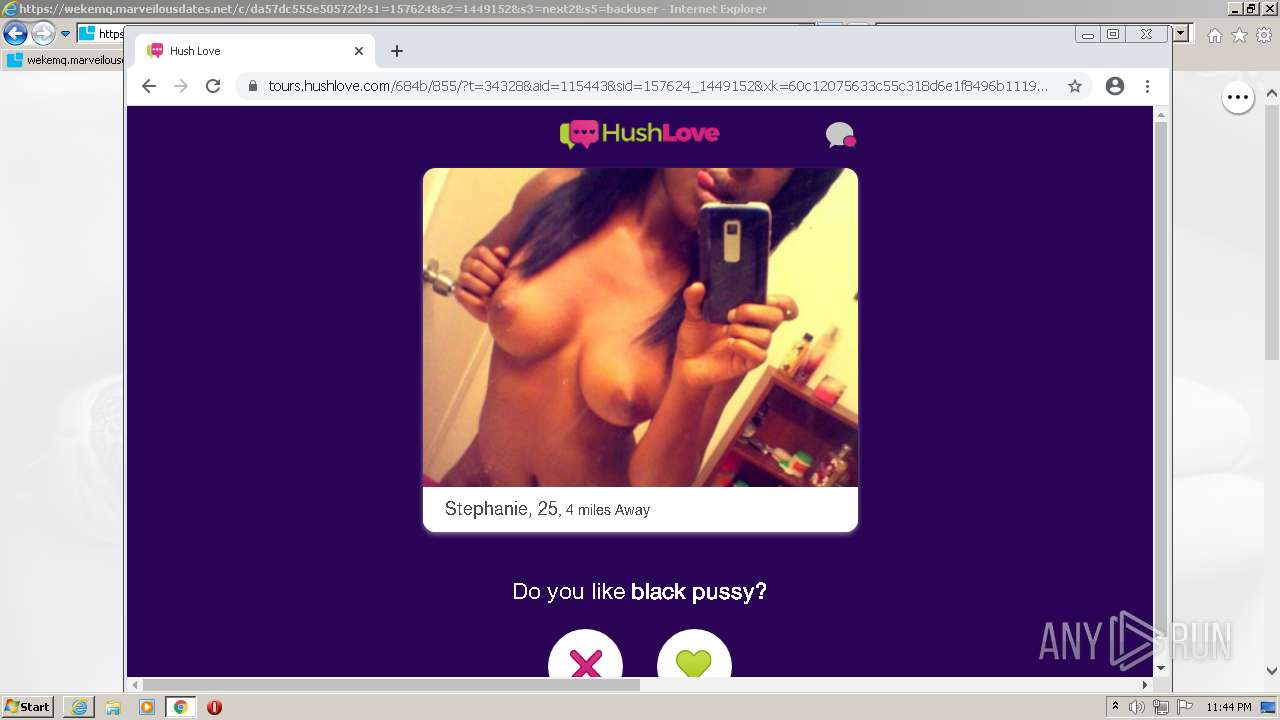
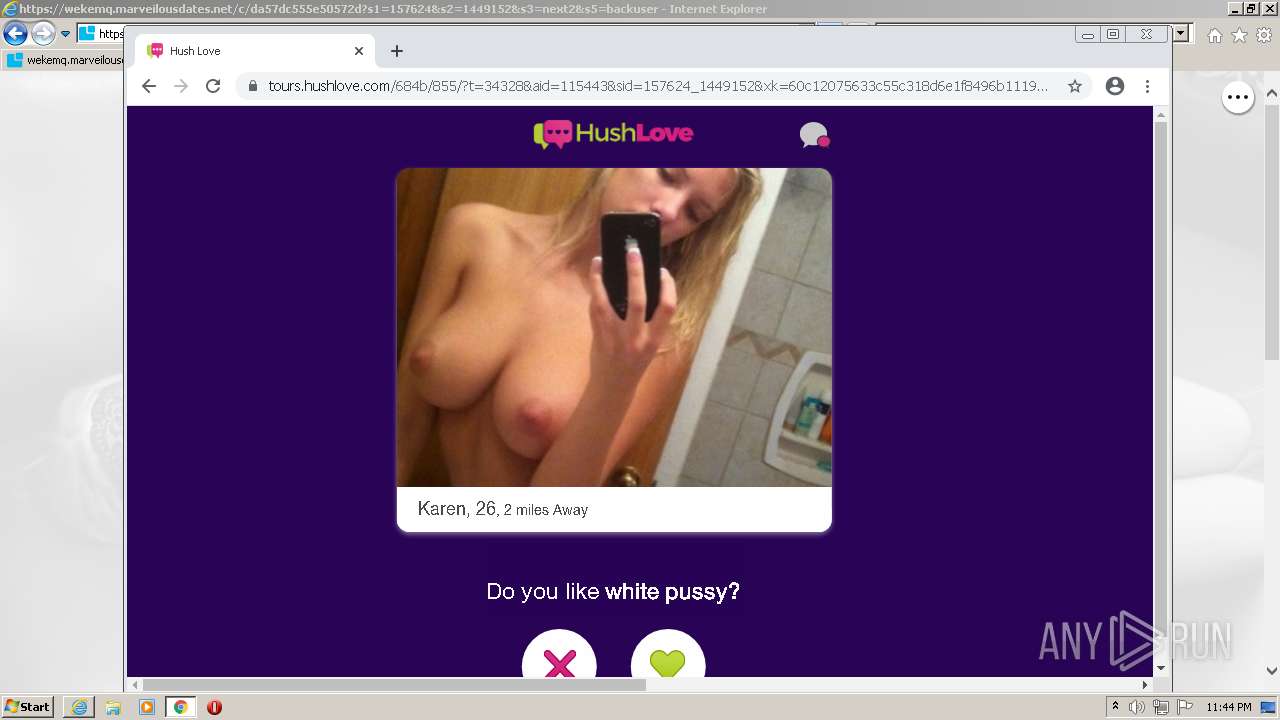
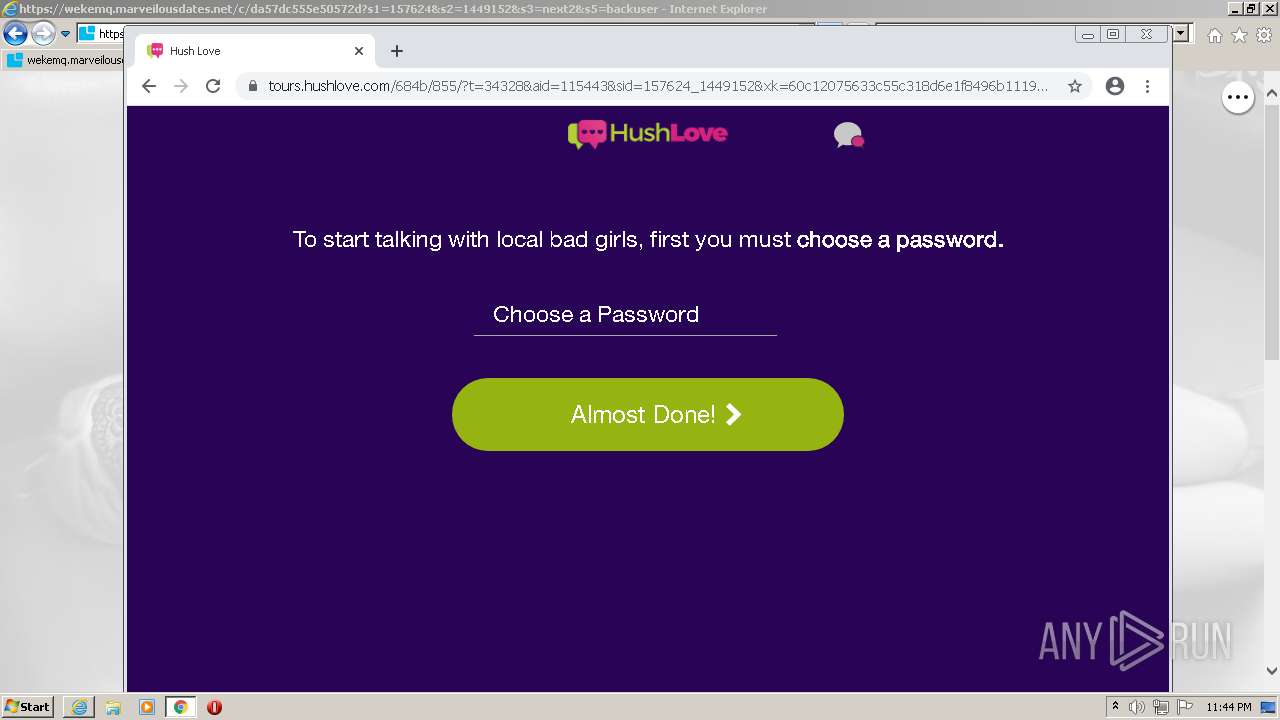
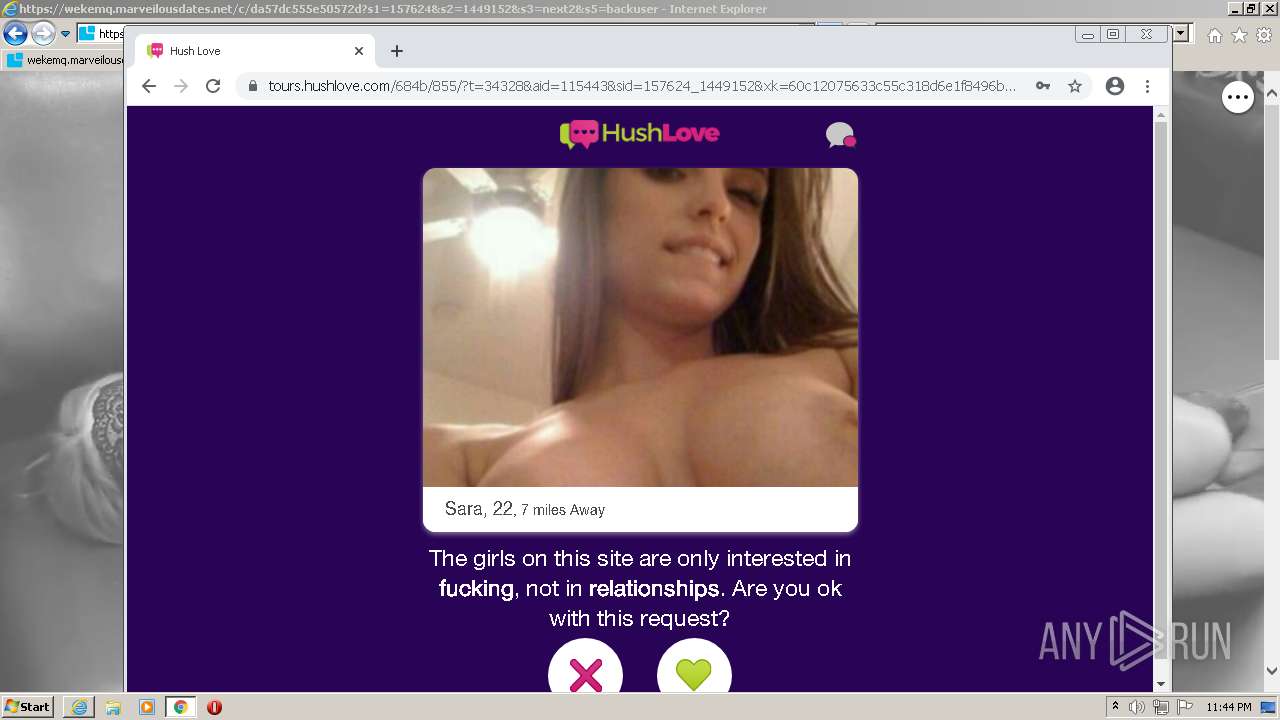
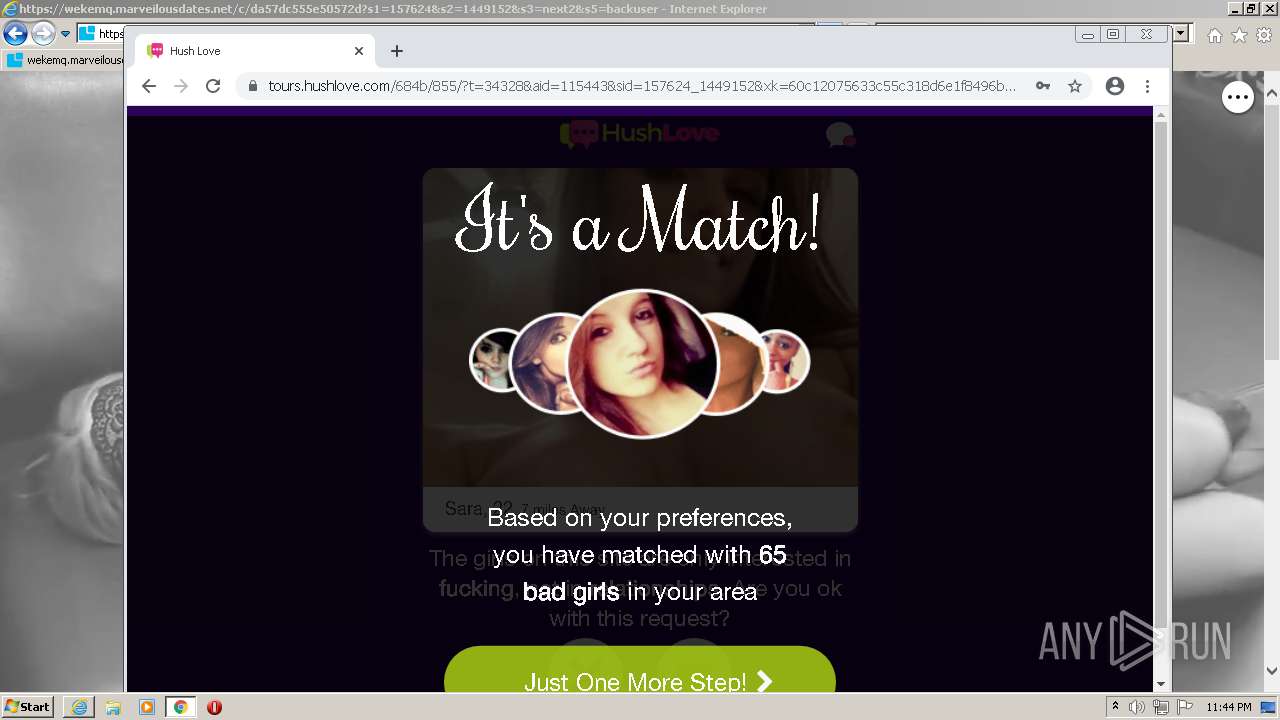
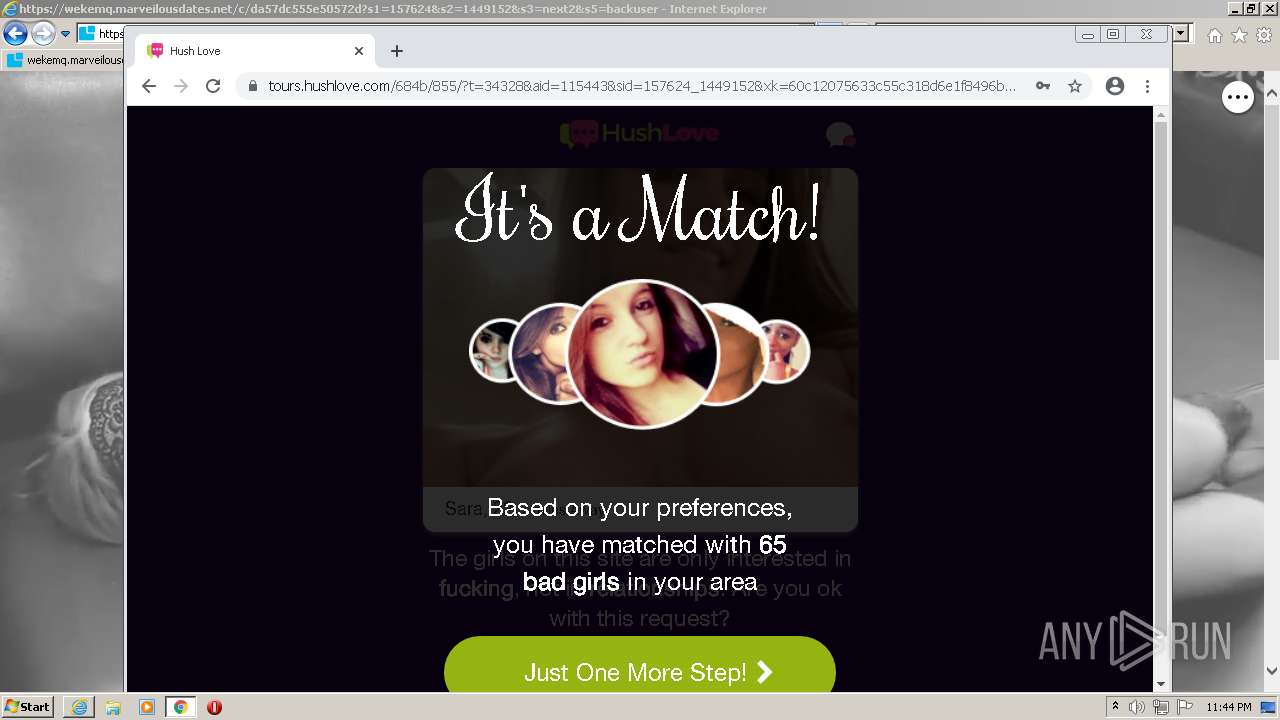
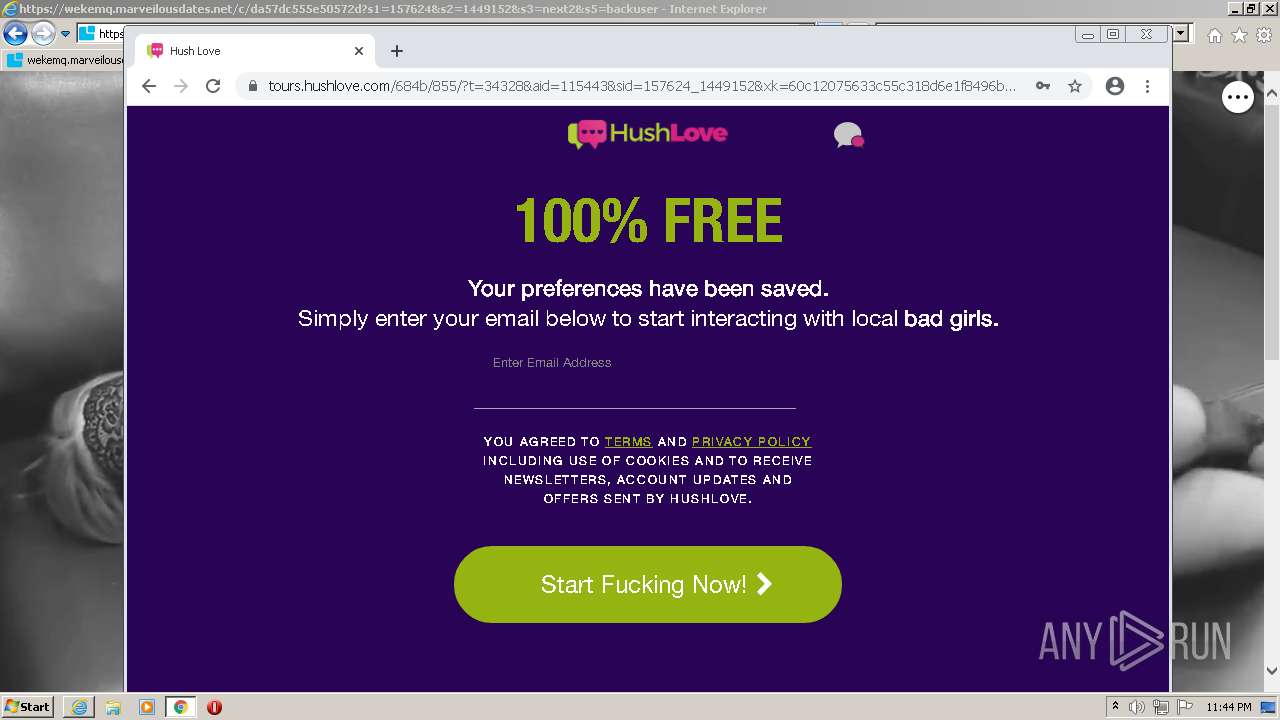
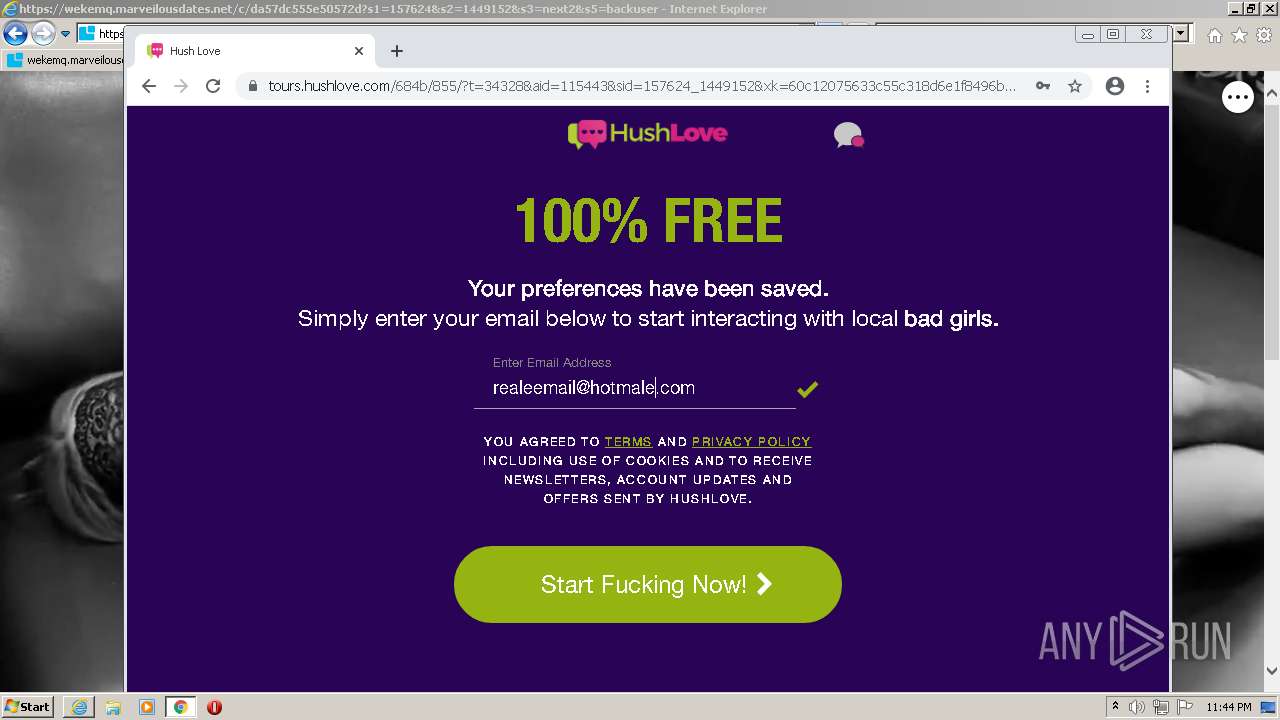
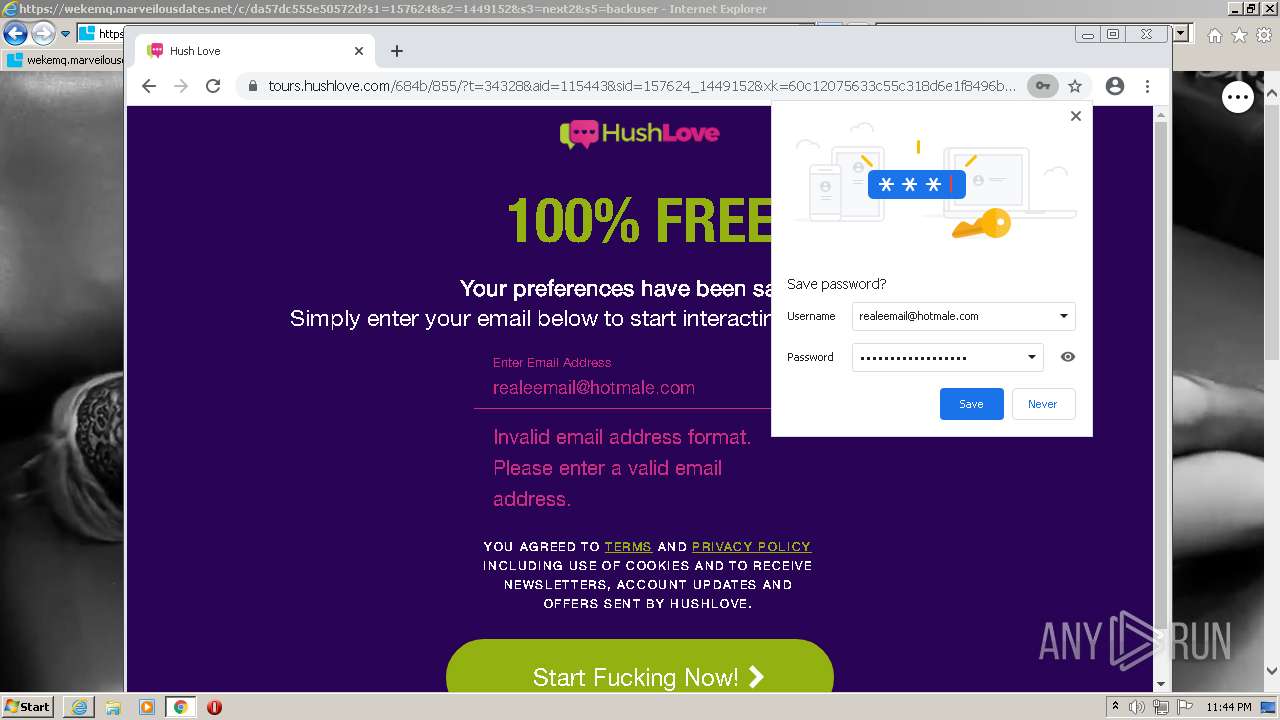
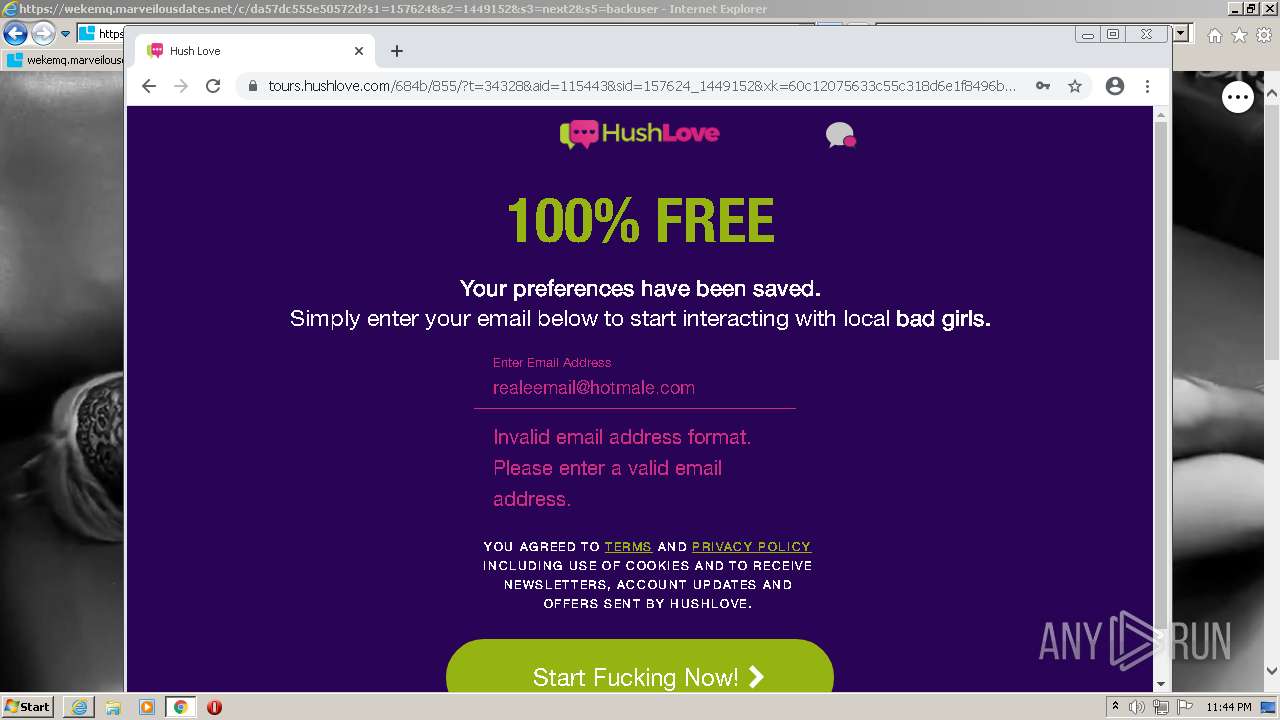
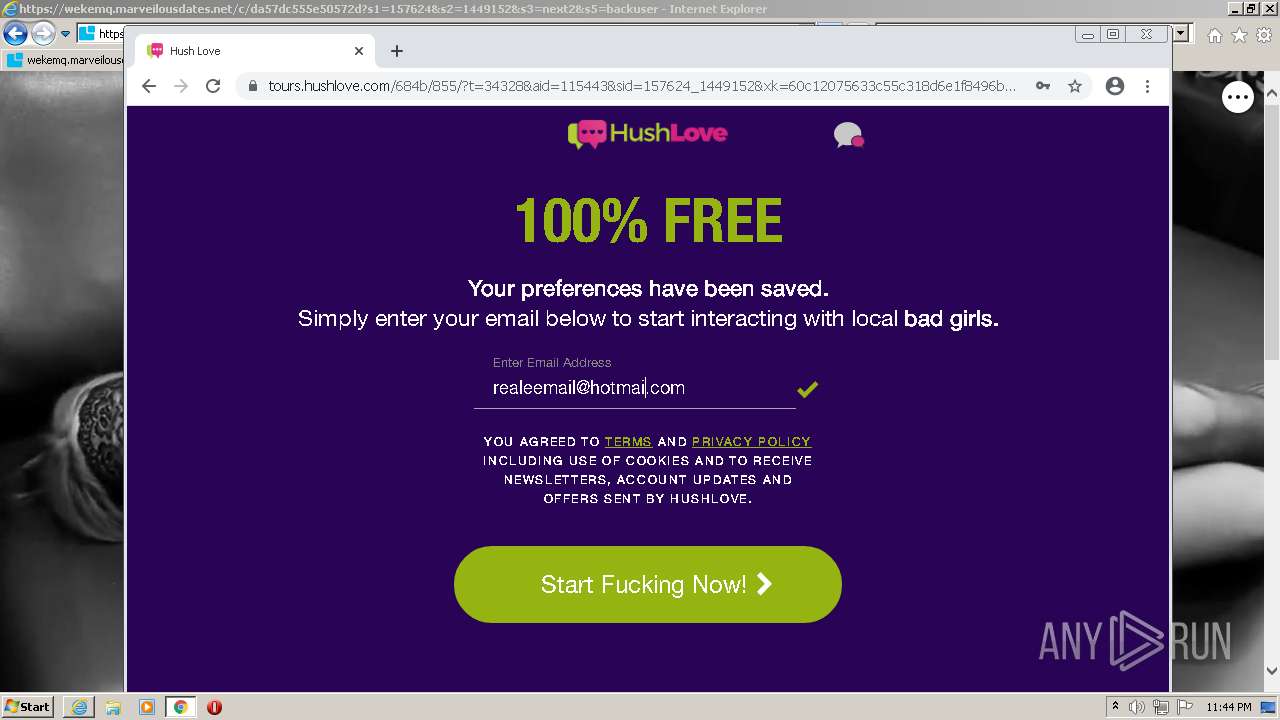
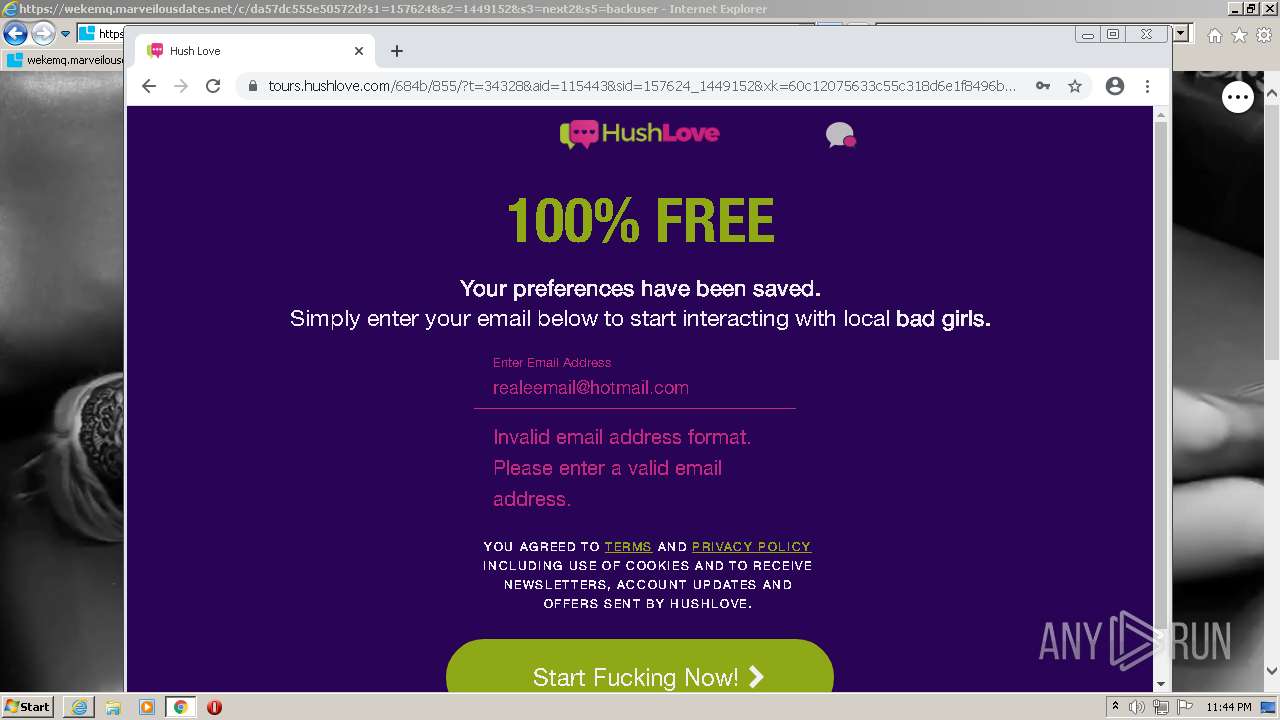
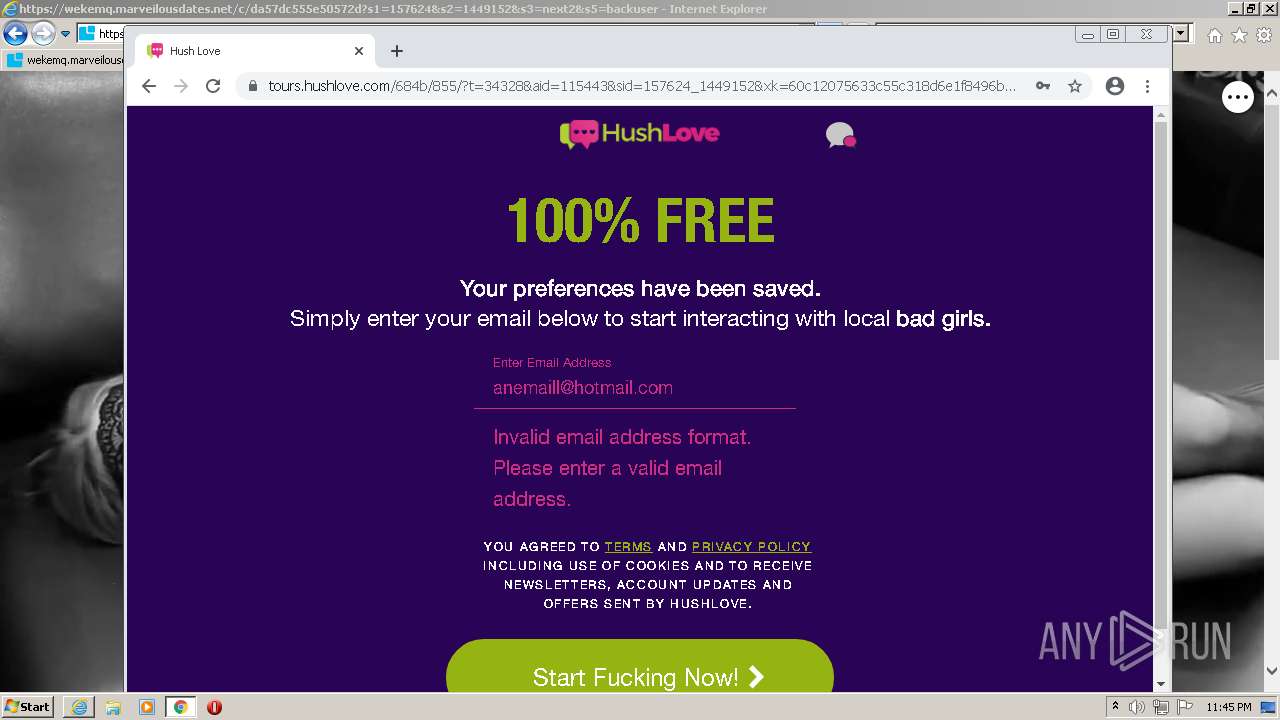
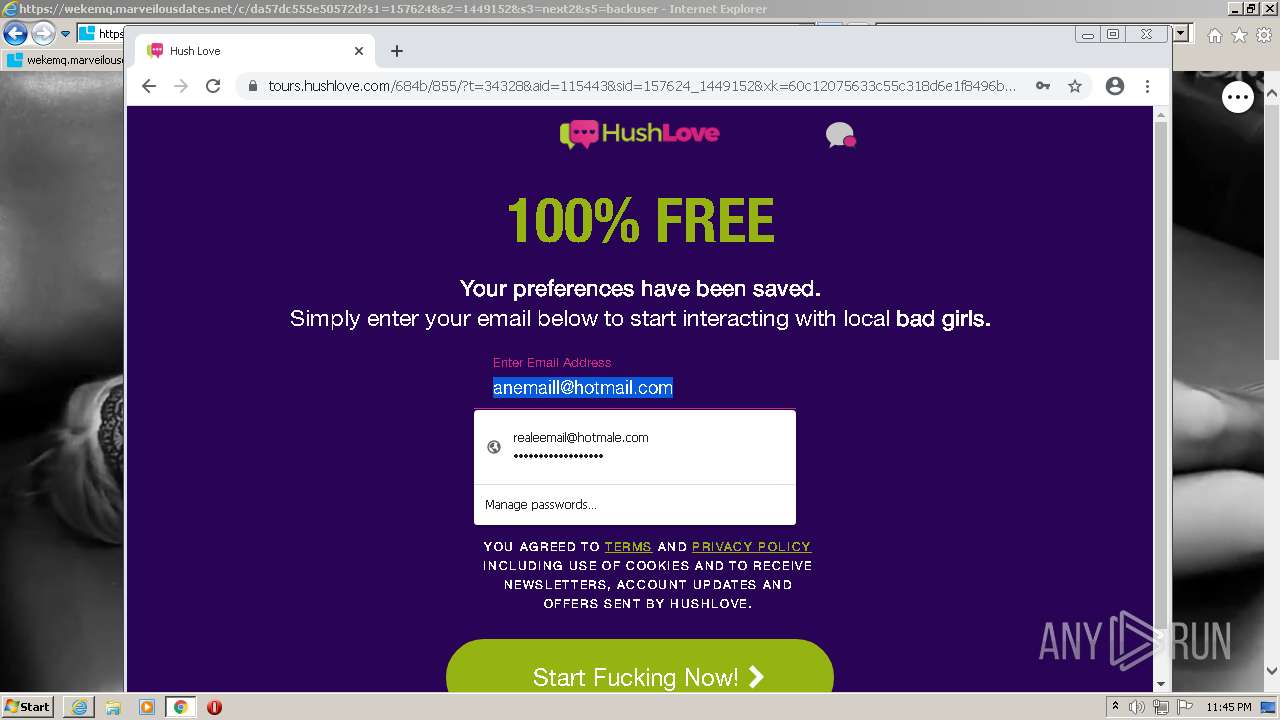
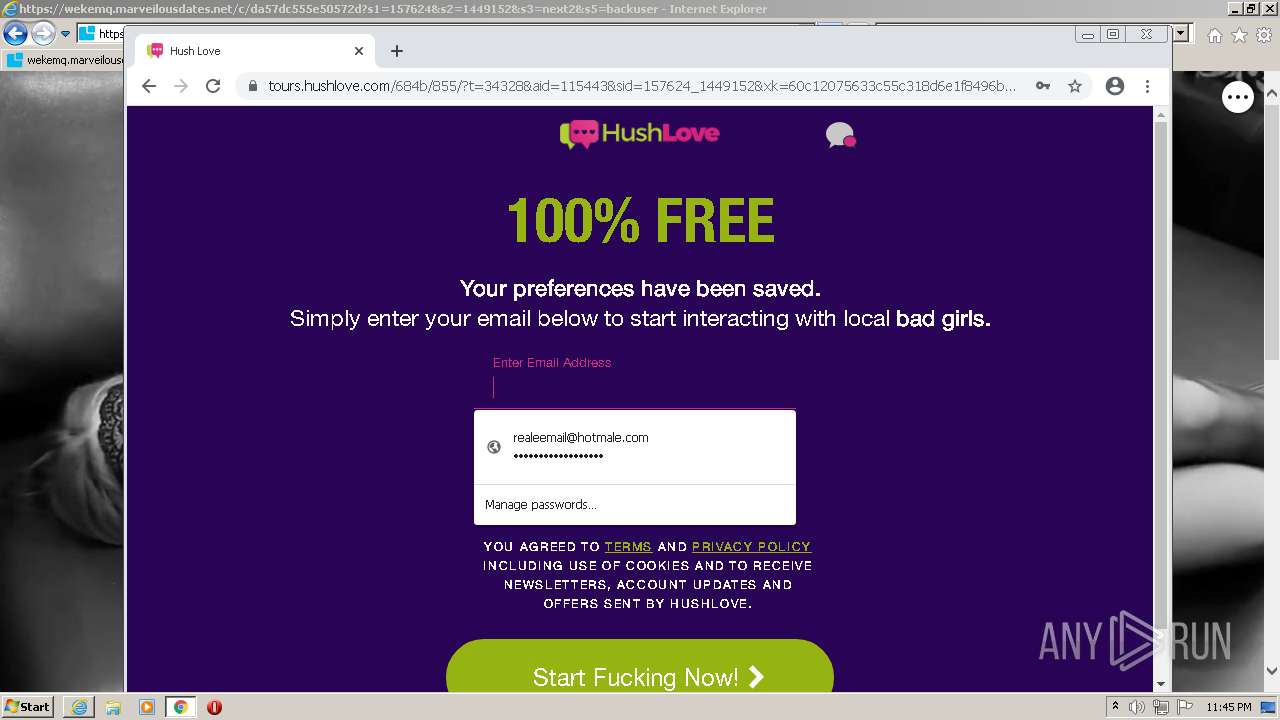
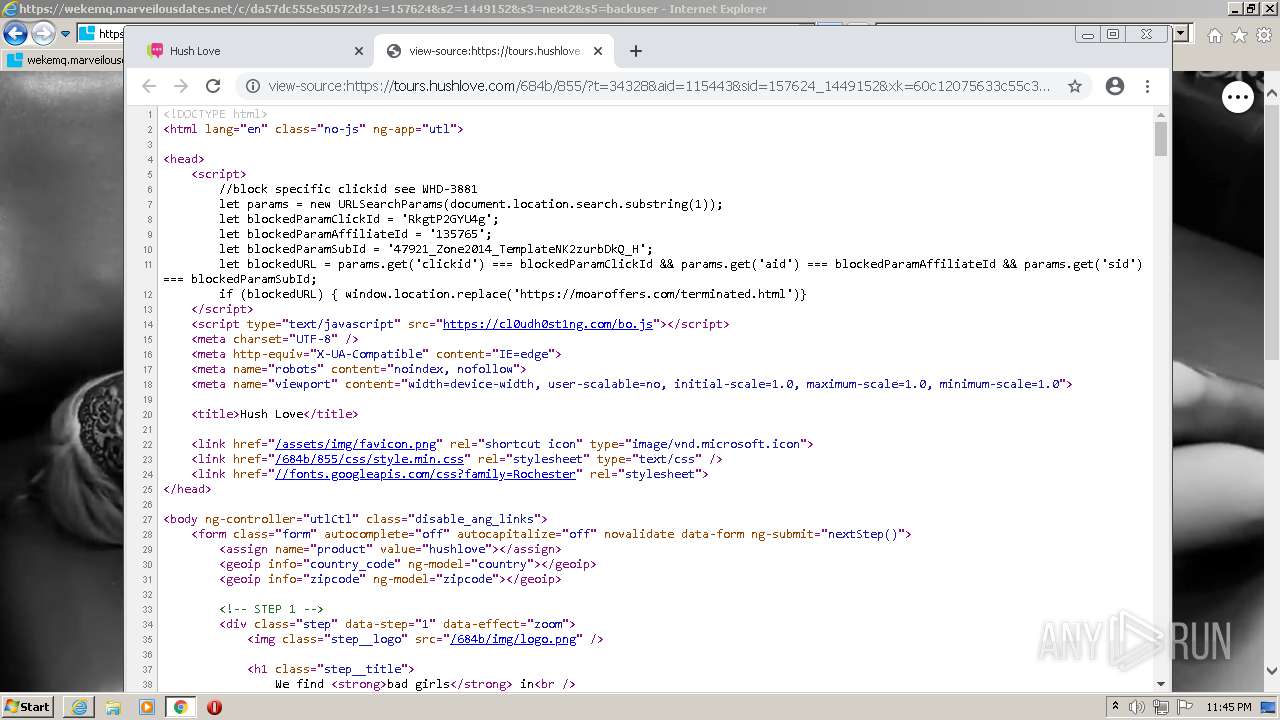
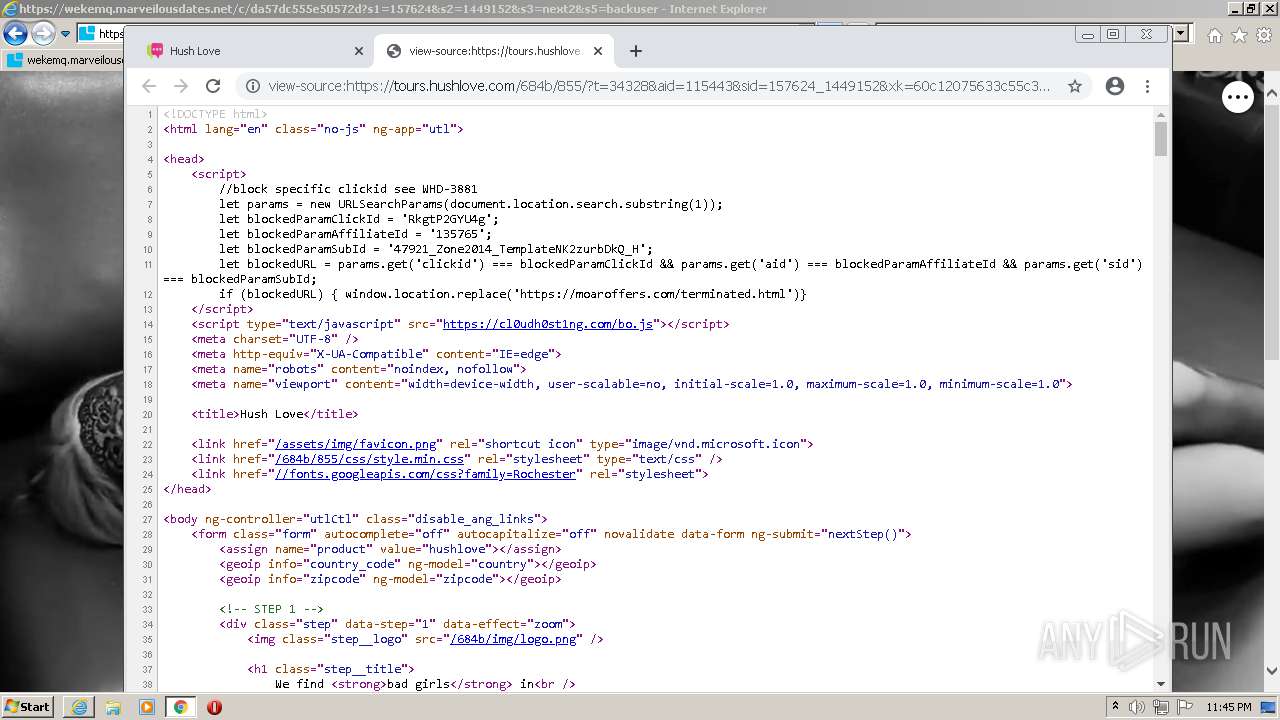
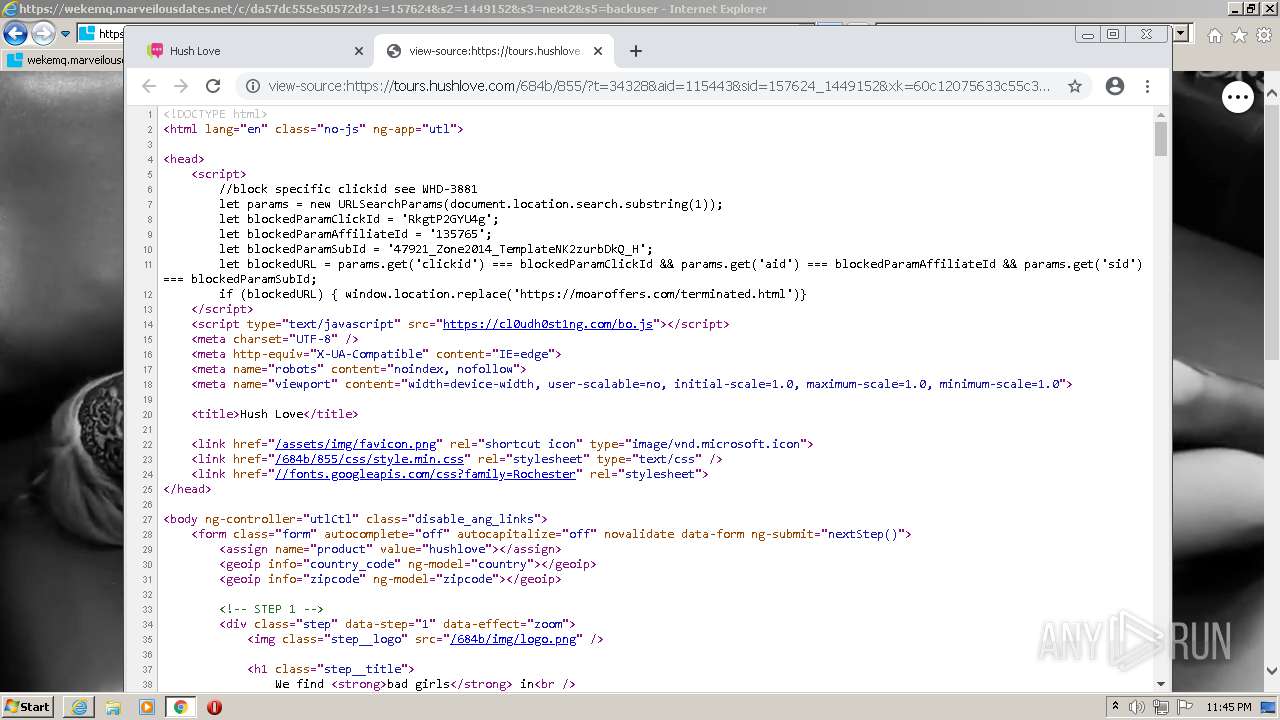
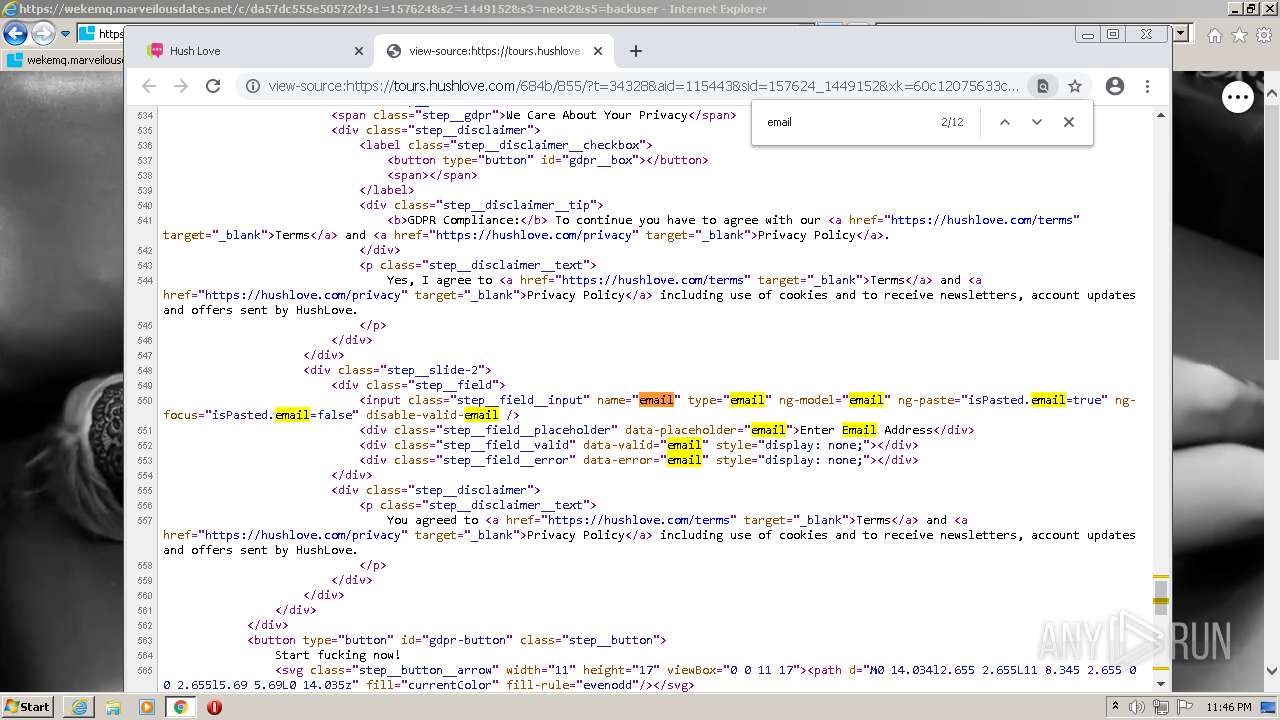
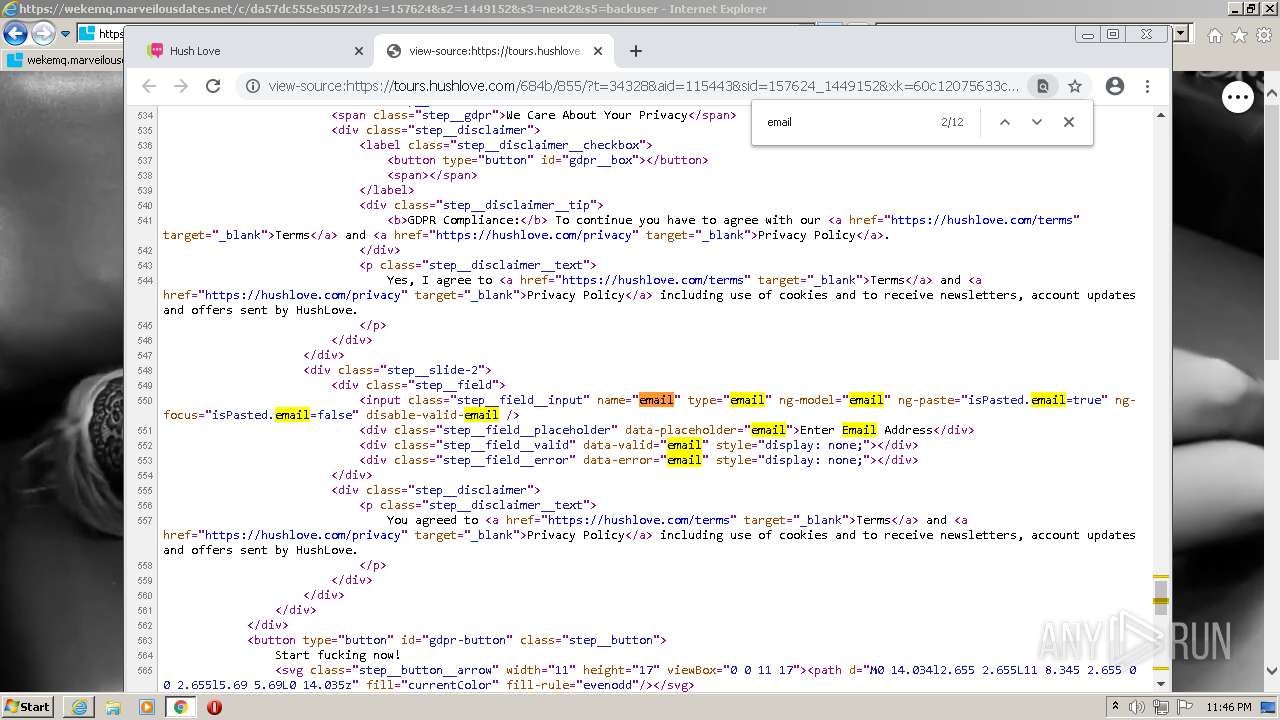
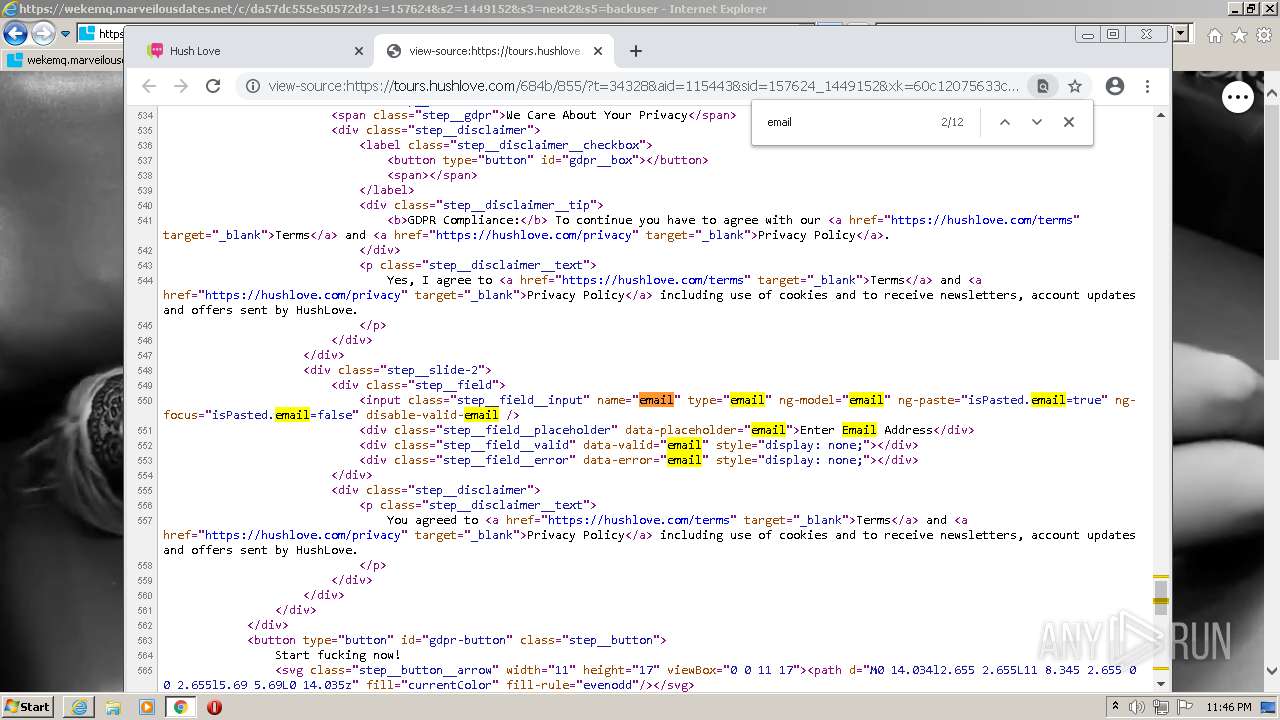
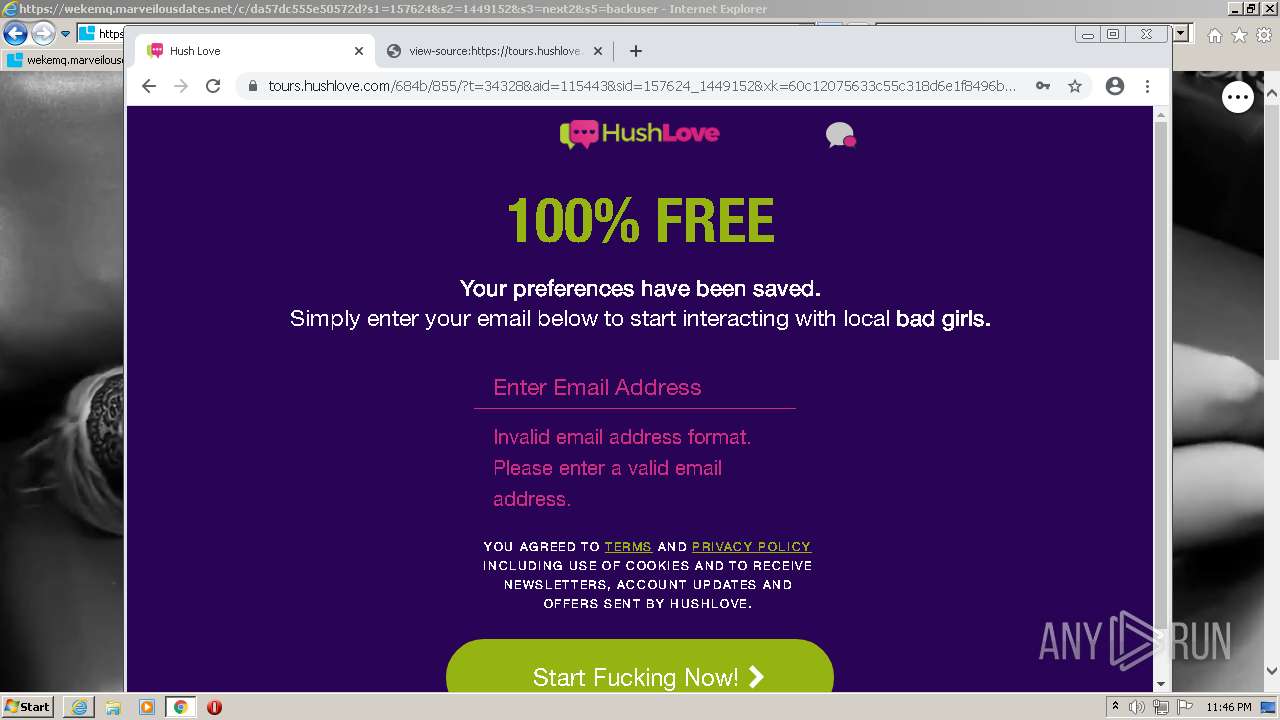
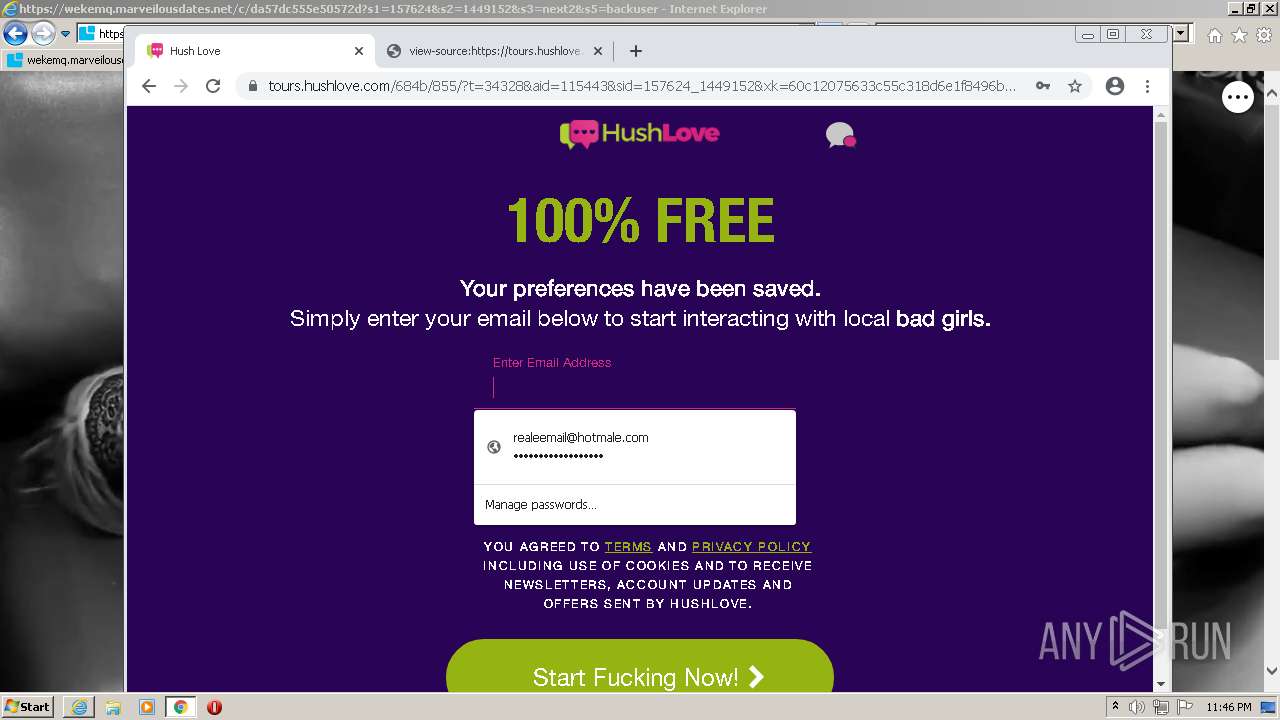
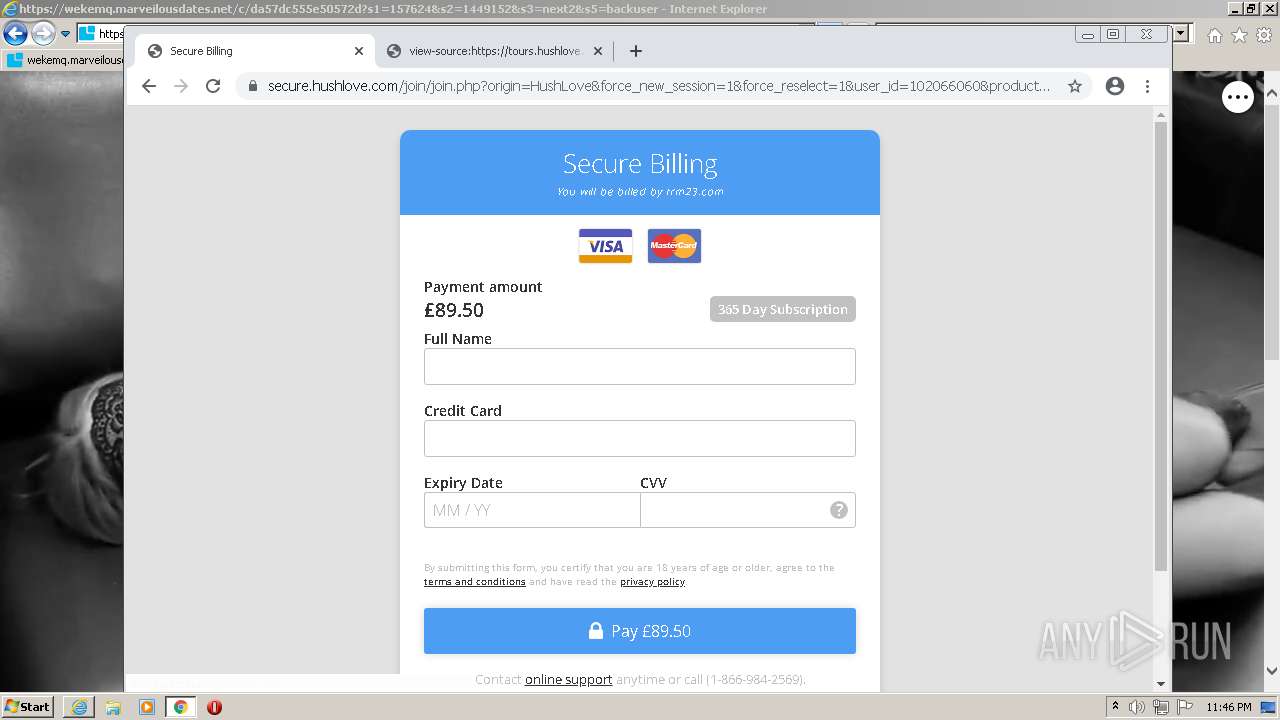
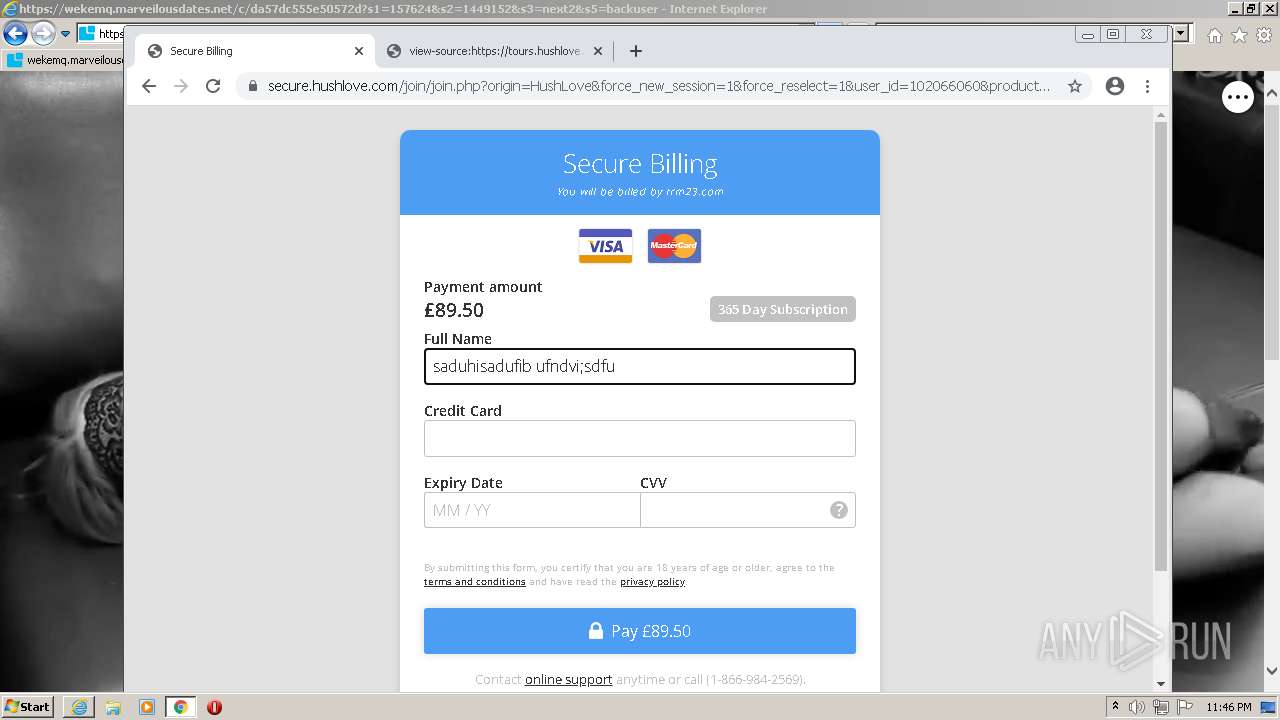
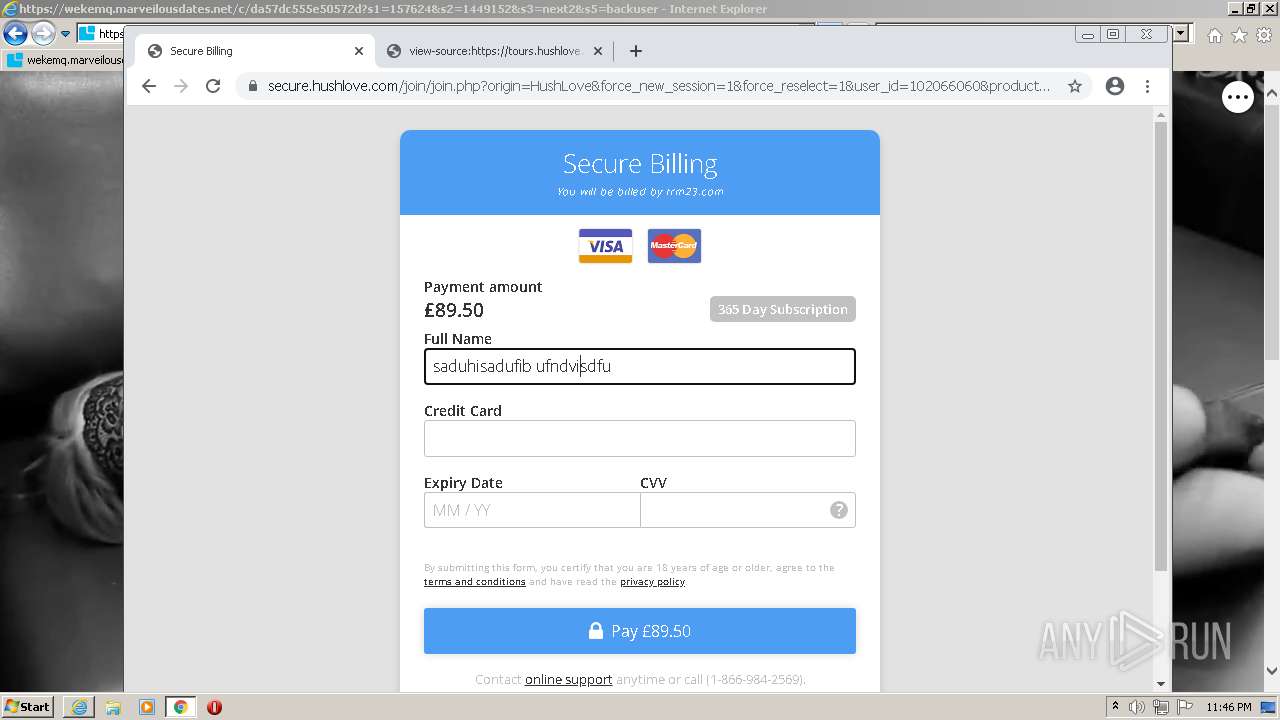
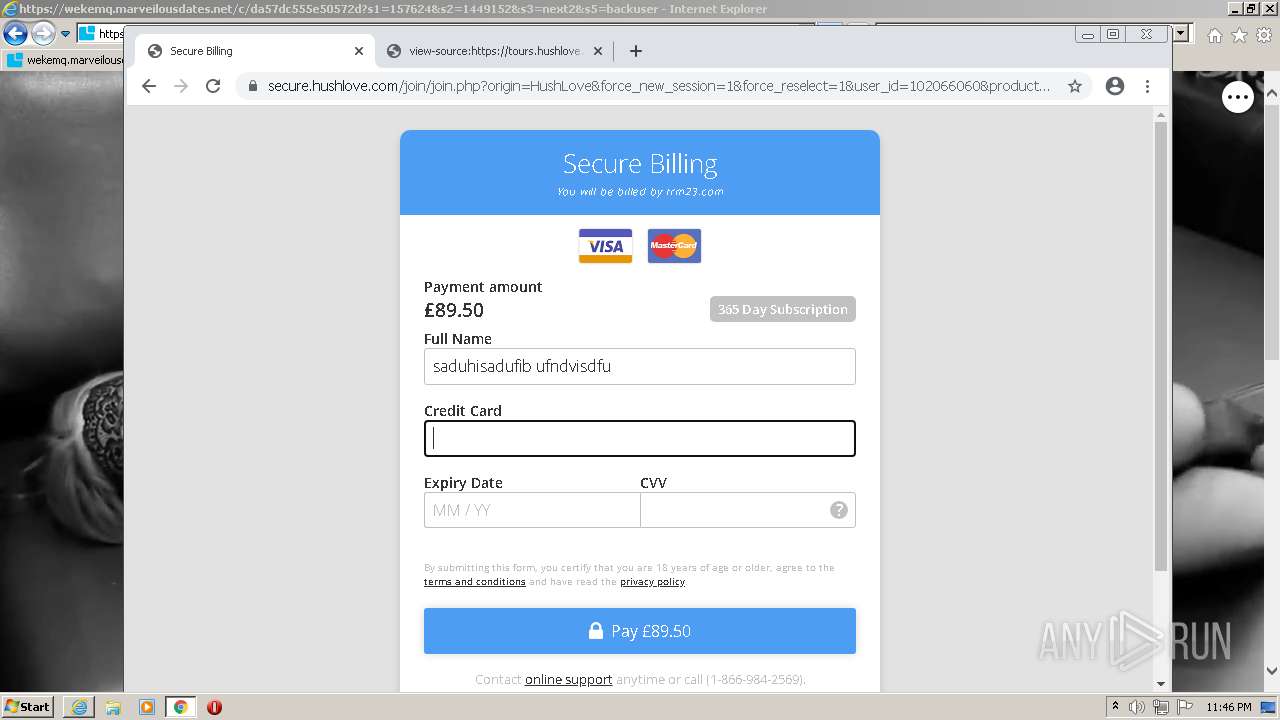
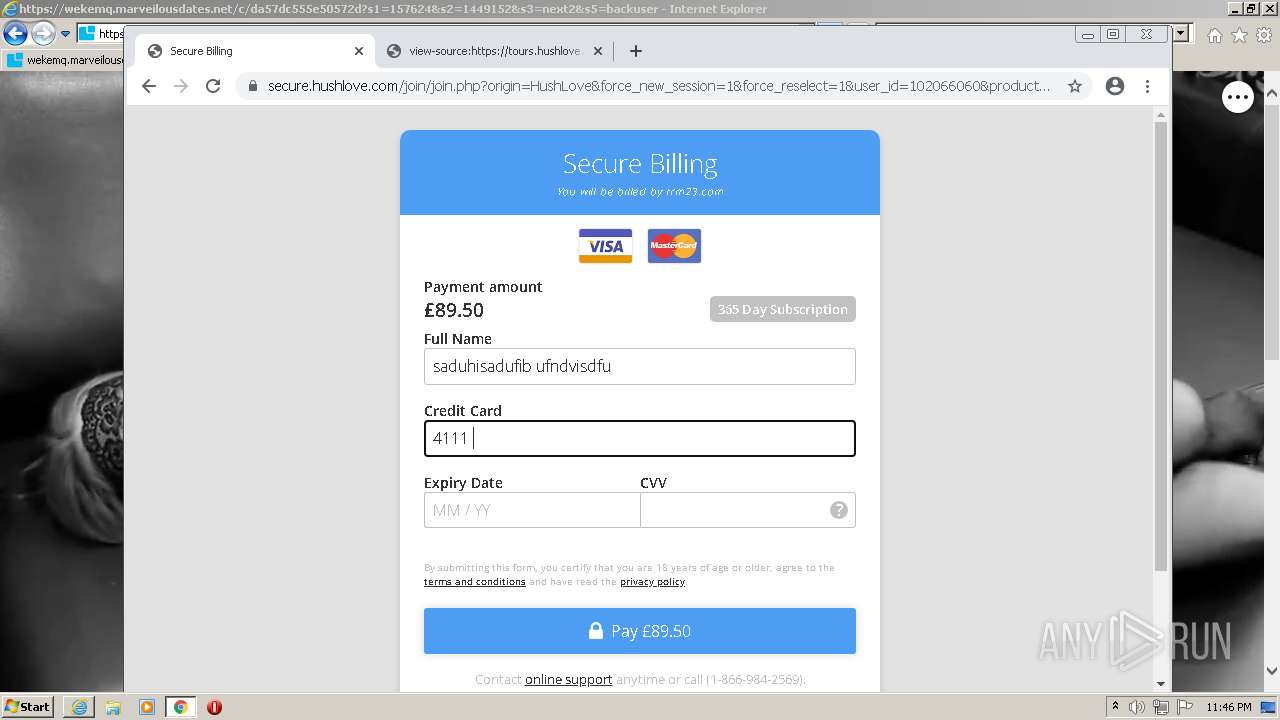
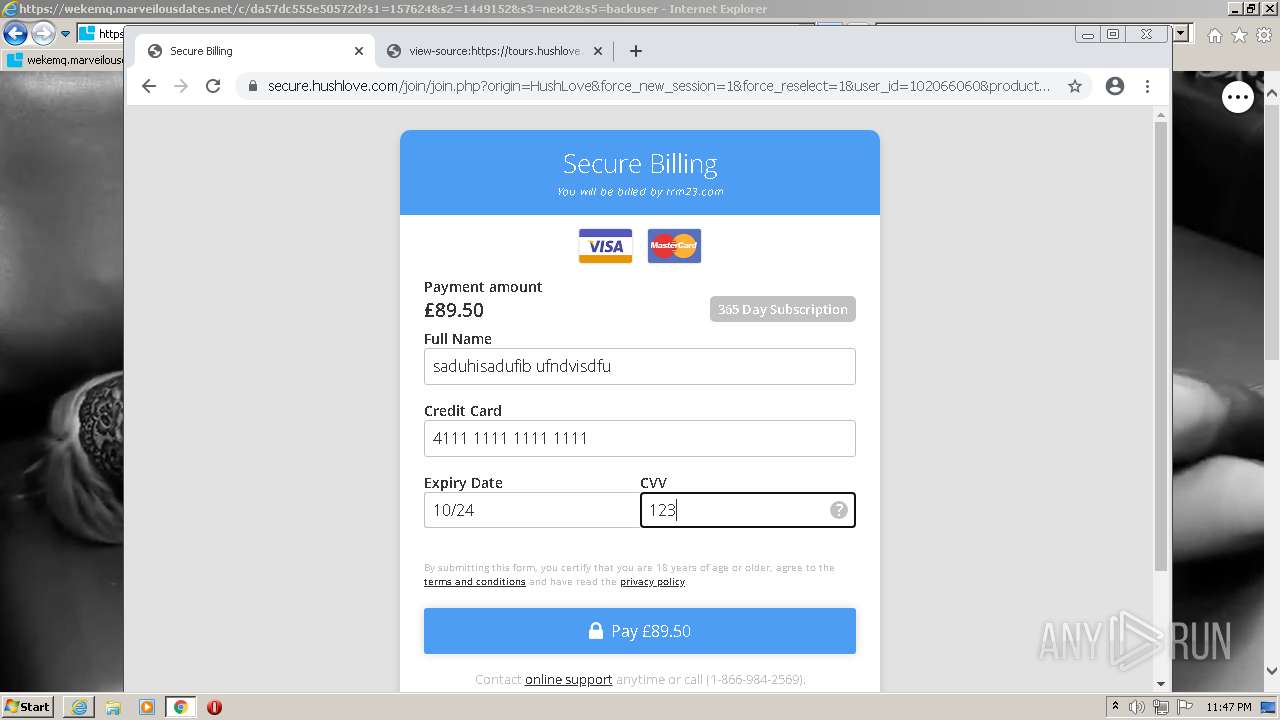
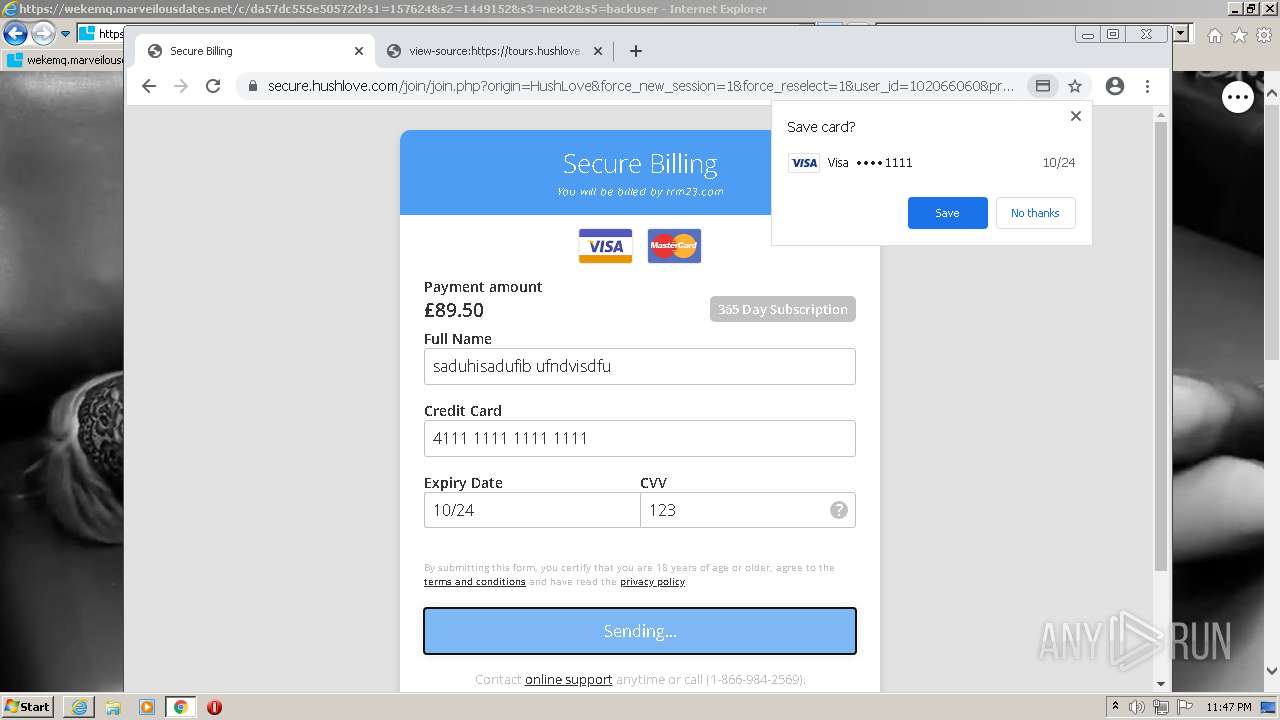
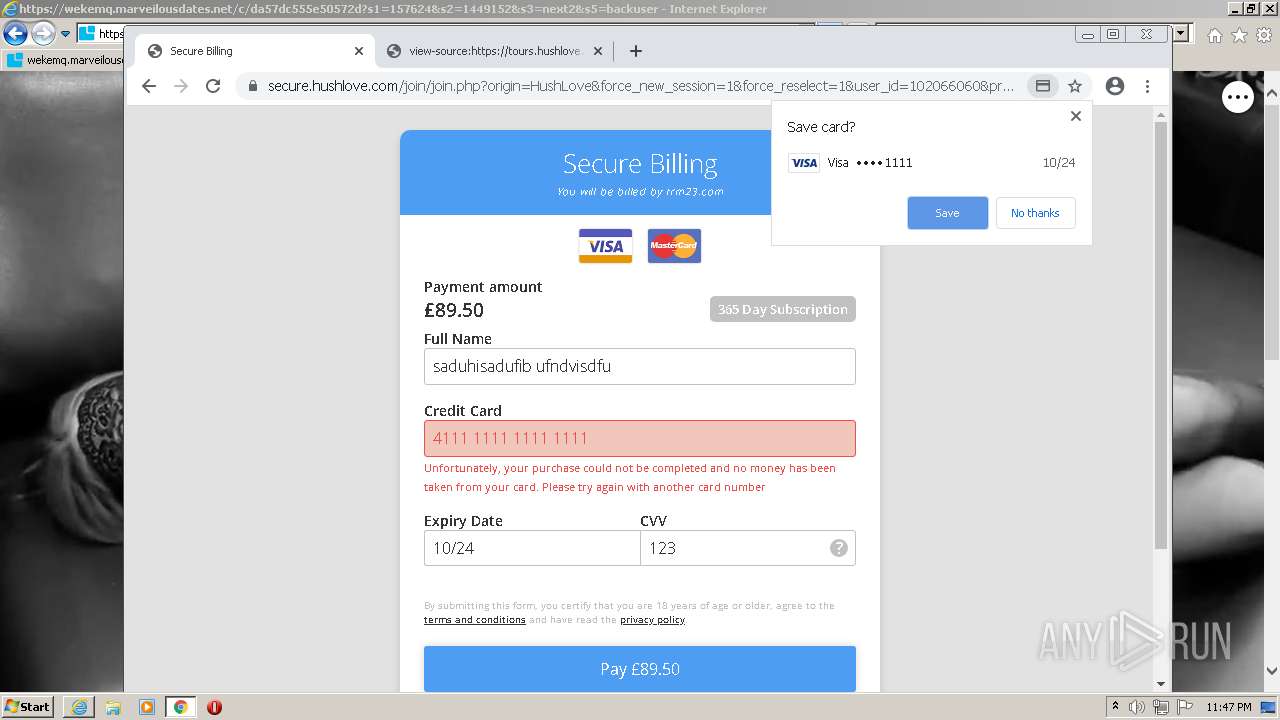
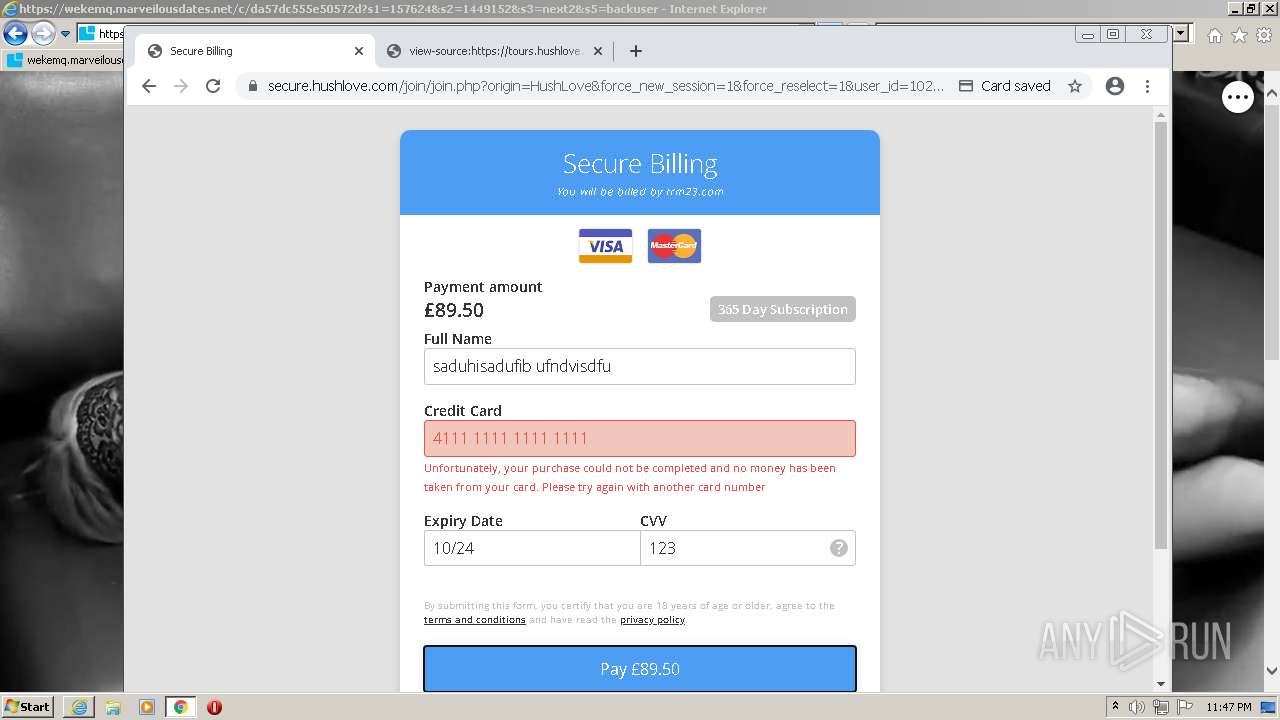
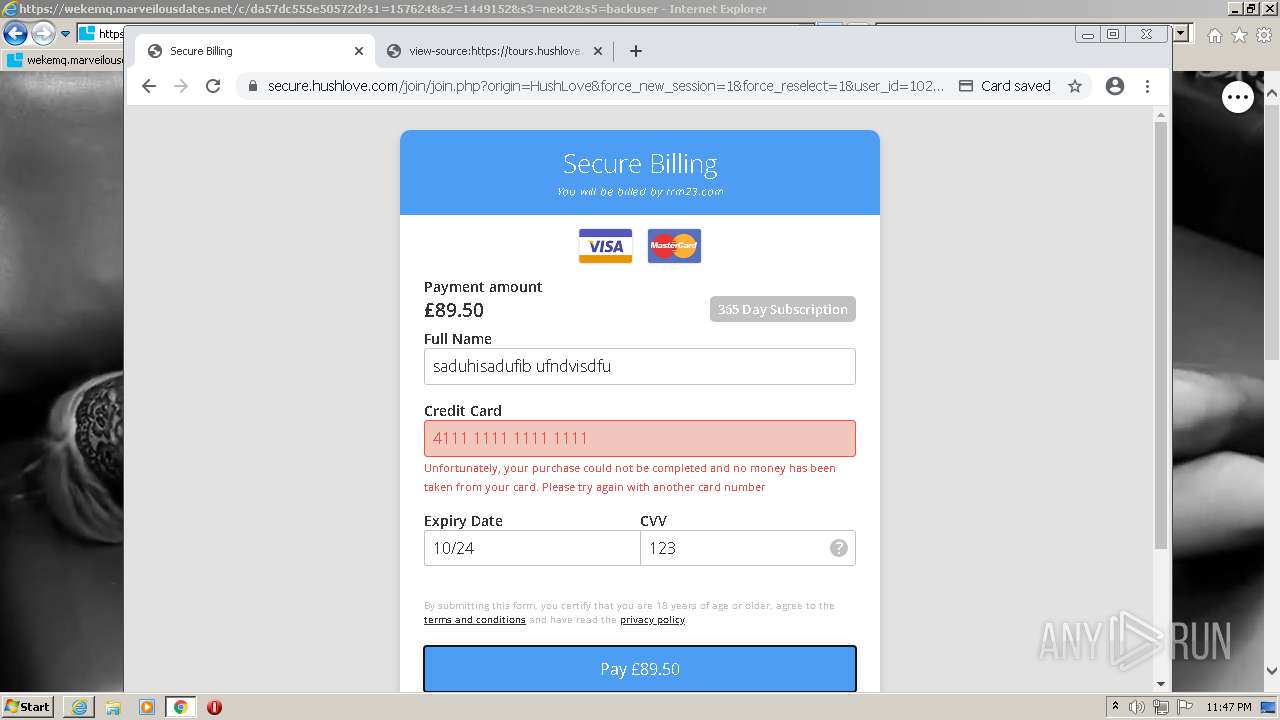
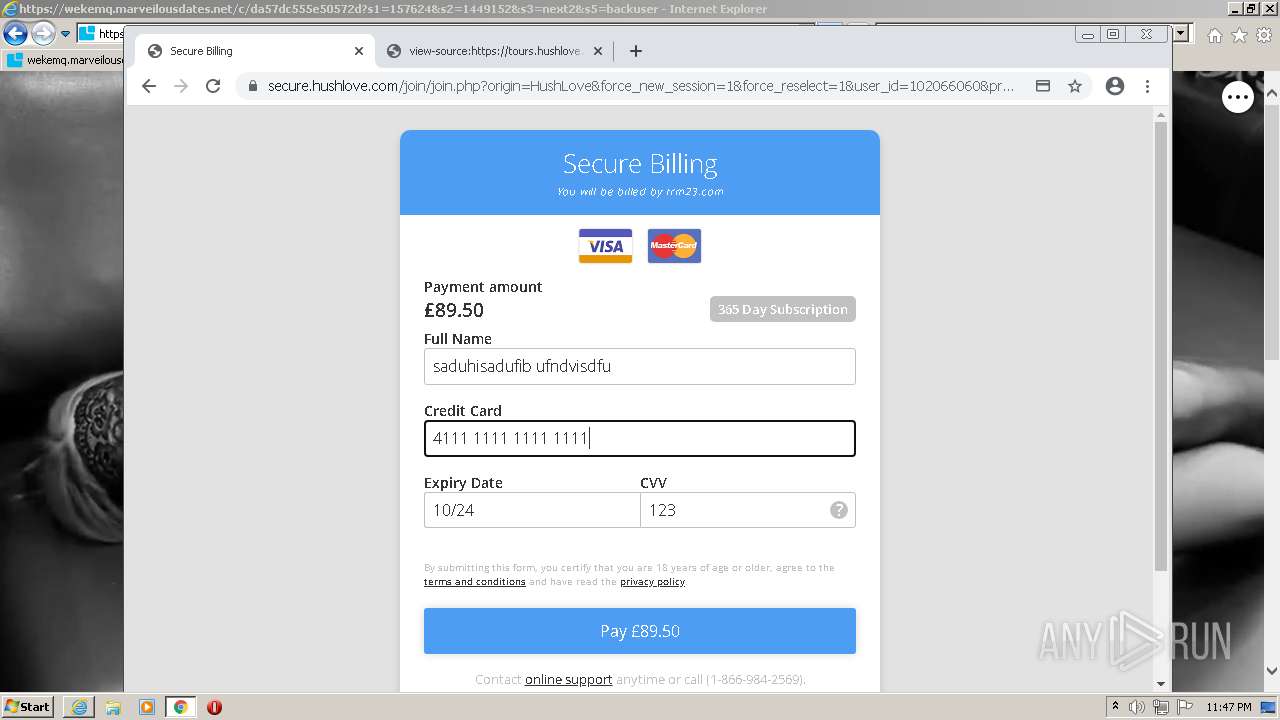
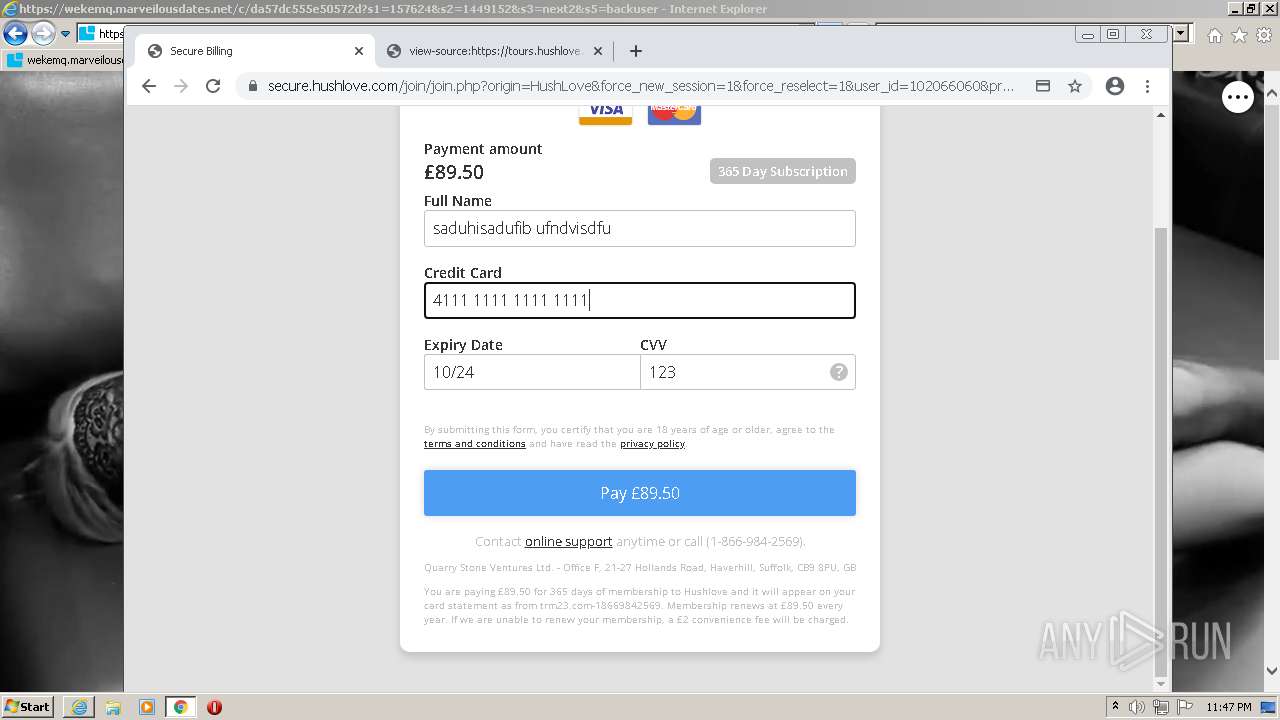
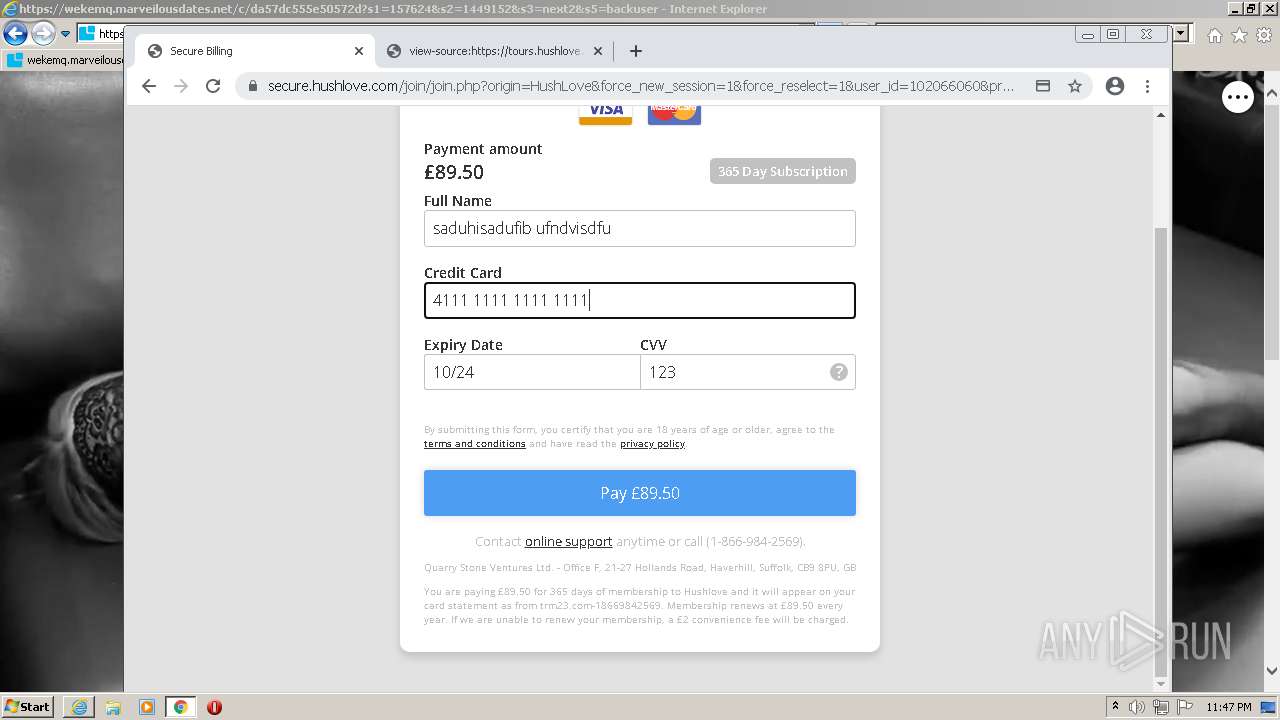
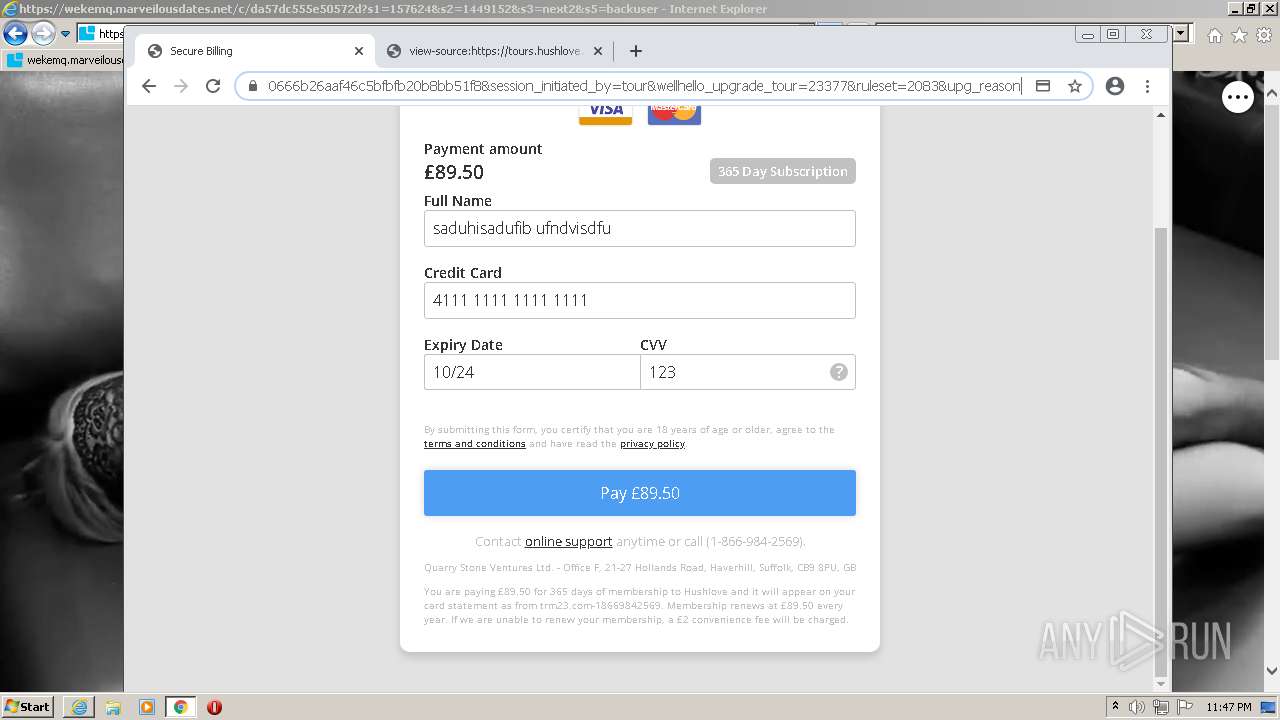
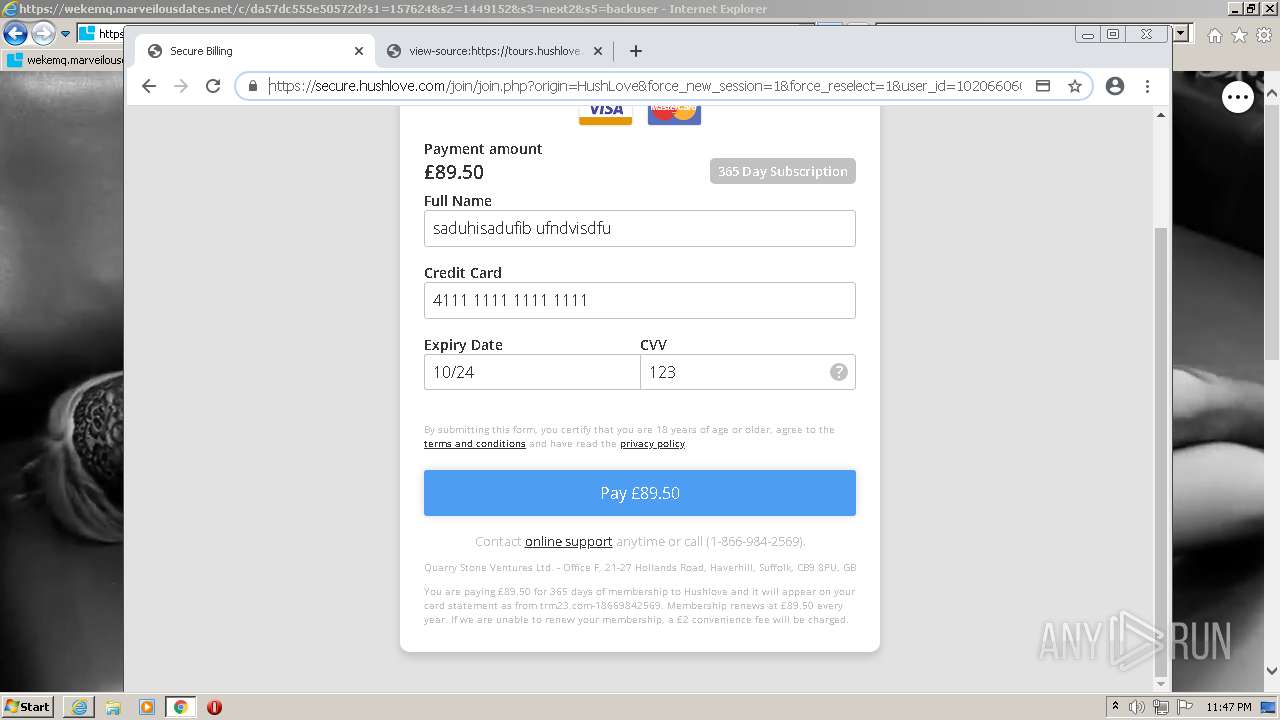
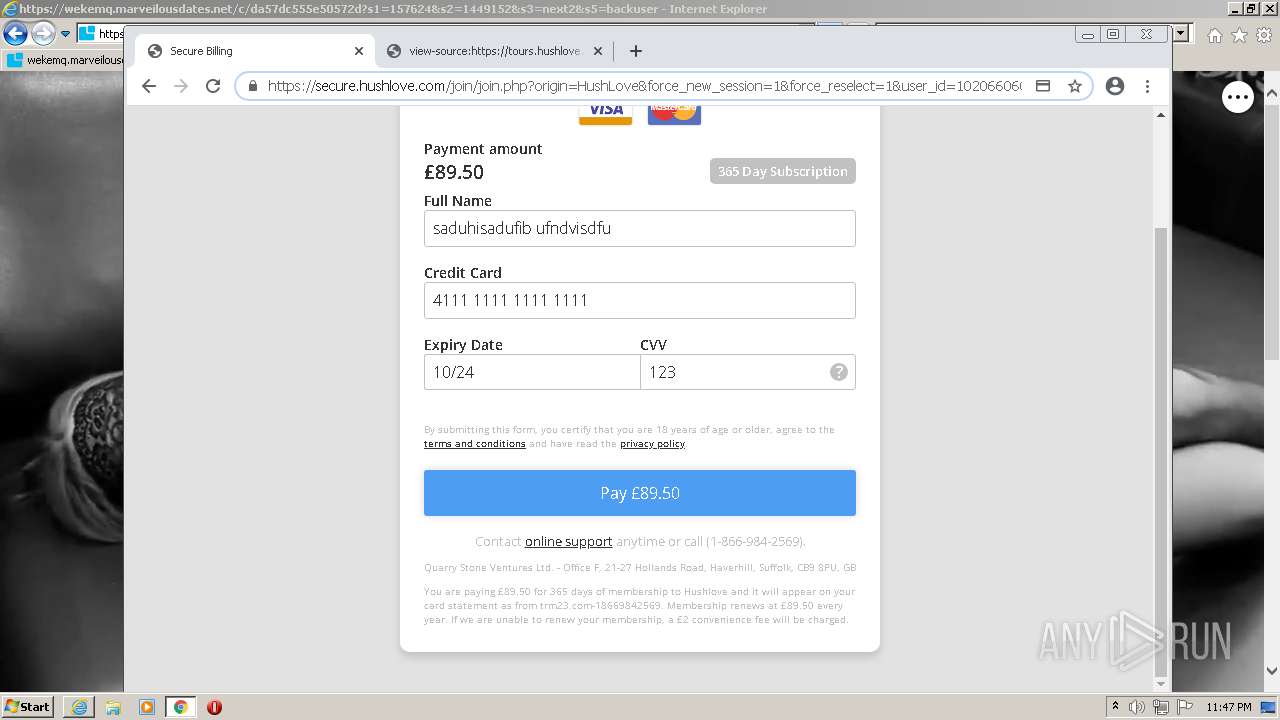
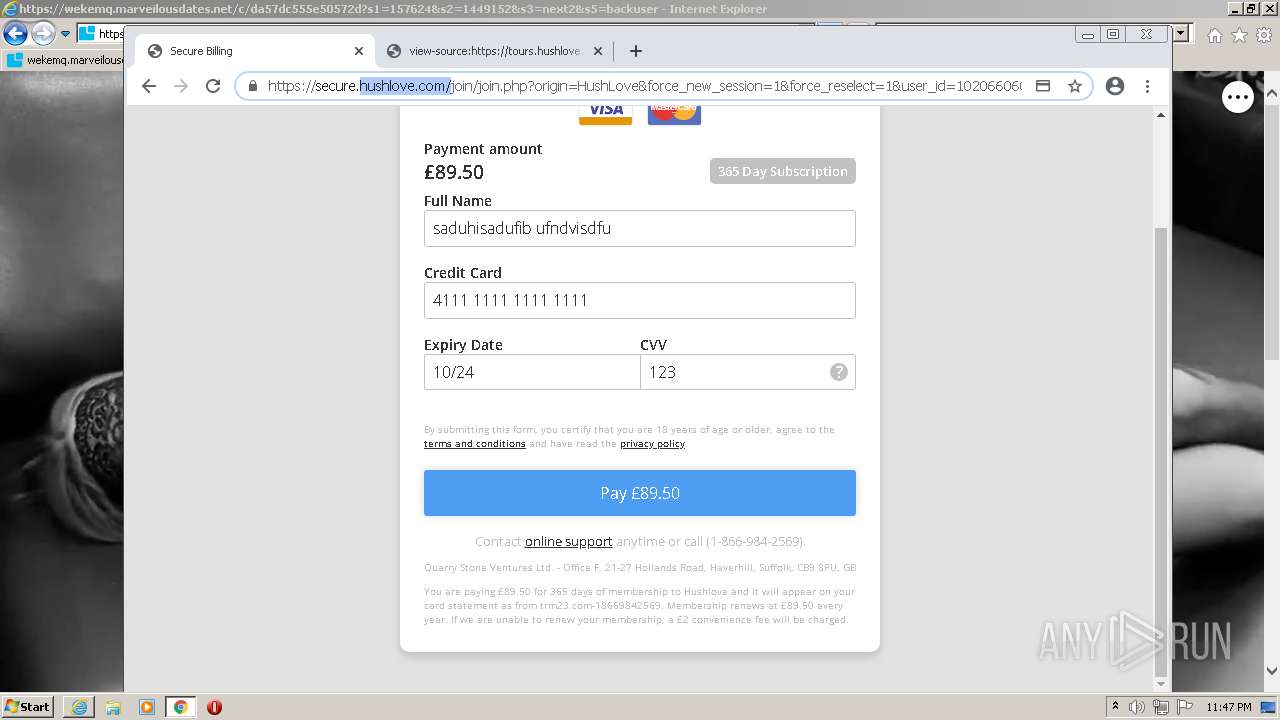
| URL: | https://wekemq.marveilousdates.net/c/da57dc555e50572d?s1=157624&s2=1449152&s3=next2&j1=1 |
| Full analysis: | https://app.any.run/tasks/d3030a2b-b308-45e1-b3d8-b8ecc673e43c |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 22:42:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4E6BA421A6C92A7C00DB8136E9CE5E55 |
| SHA1: | 5A4D65E71680B8B282F22DC689A4FFCF9276D104 |
| SHA256: | FF85E95D87530B4A85A3BFBC12C1376DE462C24800B99177C8A0895D2DBC77BA |
| SSDEEP: | 3:N8RBxnKQTRnLAs9VqAYhUHbMXyUQXDWQlU:2VdnjeUaHQTWQO |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 3924)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2984)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3656)
Drops a file with a compile date too recent
- chrome.exe (PID: 3924)
Executable content was dropped or overwritten
- chrome.exe (PID: 3924)
INFO
Checks supported languages
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 2984)
- chrome.exe (PID: 3288)
- chrome.exe (PID: 3656)
- chrome.exe (PID: 1856)
- chrome.exe (PID: 2028)
- chrome.exe (PID: 2032)
- chrome.exe (PID: 3604)
- chrome.exe (PID: 2828)
- chrome.exe (PID: 3224)
- chrome.exe (PID: 1628)
- chrome.exe (PID: 1688)
- chrome.exe (PID: 3384)
- chrome.exe (PID: 2008)
- chrome.exe (PID: 1232)
- chrome.exe (PID: 2872)
- chrome.exe (PID: 2400)
- chrome.exe (PID: 3952)
- chrome.exe (PID: 3120)
- chrome.exe (PID: 2040)
- chrome.exe (PID: 2672)
- chrome.exe (PID: 2368)
- chrome.exe (PID: 3924)
- chrome.exe (PID: 2828)
- chrome.exe (PID: 1208)
- chrome.exe (PID: 1664)
- chrome.exe (PID: 1248)
- chrome.exe (PID: 2376)
- chrome.exe (PID: 3508)
- chrome.exe (PID: 2428)
- chrome.exe (PID: 1812)
- chrome.exe (PID: 1412)
- chrome.exe (PID: 2776)
- chrome.exe (PID: 4032)
- chrome.exe (PID: 404)
- chrome.exe (PID: 3004)
- chrome.exe (PID: 3300)
- chrome.exe (PID: 1100)
- chrome.exe (PID: 3348)
- chrome.exe (PID: 2032)
- chrome.exe (PID: 928)
- chrome.exe (PID: 3748)
- chrome.exe (PID: 1568)
- chrome.exe (PID: 3468)
- chrome.exe (PID: 2552)
- chrome.exe (PID: 3224)
- chrome.exe (PID: 2412)
- chrome.exe (PID: 2276)
- chrome.exe (PID: 2020)
- chrome.exe (PID: 3872)
- chrome.exe (PID: 3312)
- chrome.exe (PID: 3760)
- chrome.exe (PID: 1532)
- chrome.exe (PID: 3044)
- chrome.exe (PID: 1988)
- chrome.exe (PID: 3844)
- chrome.exe (PID: 3680)
- chrome.exe (PID: 3864)
- chrome.exe (PID: 2596)
- chrome.exe (PID: 2692)
- chrome.exe (PID: 908)
- chrome.exe (PID: 3236)
- chrome.exe (PID: 4060)
- chrome.exe (PID: 3928)
- chrome.exe (PID: 2304)
- chrome.exe (PID: 1512)
- chrome.exe (PID: 340)
- chrome.exe (PID: 2332)
- chrome.exe (PID: 3972)
Reads the computer name
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 2984)
- chrome.exe (PID: 3656)
- chrome.exe (PID: 1856)
- chrome.exe (PID: 2028)
- chrome.exe (PID: 2008)
- chrome.exe (PID: 1688)
- chrome.exe (PID: 3952)
- chrome.exe (PID: 2672)
- chrome.exe (PID: 2828)
- chrome.exe (PID: 1812)
- chrome.exe (PID: 3348)
- chrome.exe (PID: 2032)
Changes internet zones settings
- iexplore.exe (PID: 2220)
Creates files in the user directory
- iexplore.exe (PID: 2984)
- iexplore.exe (PID: 2220)
Manual execution by user
- chrome.exe (PID: 3656)
Application launched itself
- iexplore.exe (PID: 2220)
- chrome.exe (PID: 3656)
Reads settings of System Certificates
- iexplore.exe (PID: 2984)
- iexplore.exe (PID: 2220)
- chrome.exe (PID: 2028)
Checks Windows Trust Settings
- iexplore.exe (PID: 2220)
- iexplore.exe (PID: 2984)
Reads internet explorer settings
- iexplore.exe (PID: 2984)
Reads the hosts file
- chrome.exe (PID: 3656)
- chrome.exe (PID: 2028)
Changes settings of System certificates
- iexplore.exe (PID: 2220)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2220)
Reads the date of Windows installation
- chrome.exe (PID: 2672)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
106
Monitored processes
69
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,4136502380782065010,5016144197317449606,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4396 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1032,4136502380782065010,5016144197317449606,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3548 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,4136502380782065010,5016144197317449606,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=5724 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1032,4136502380782065010,5016144197317449606,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3852 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1100 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,4136502380782065010,5016144197317449606,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=35 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2800 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,4136502380782065010,5016144197317449606,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3488 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,4136502380782065010,5016144197317449606,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3228 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1248 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1032,4136502380782065010,5016144197317449606,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3520 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1412 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,4136502380782065010,5016144197317449606,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1512 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,4136502380782065010,5016144197317449606,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=63 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5140 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
34 815
Read events
34 527
Write events
276
Delete events
12
Modification events
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960794 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 5580930 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960795 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2220) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
343
Text files
318
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2984 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9E69.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2984 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2984 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2984 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9E6A.tmp | cat | |
MD5:— | SHA256:— | |||
| 2984 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 2984 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9E6B.tmp | compressed | |
MD5:— | SHA256:— | |||
| 2984 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9E6C.tmp | cat | |
MD5:— | SHA256:— | |||
| 2984 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 2984 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\96589MIY.txt | text | |
MD5:— | SHA256:— | |||
| 2984 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\SSI706XE.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
181
DNS requests
102
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/YGkwa4MXjfWSuERyWQYP_A_4/aapLKTSZ439A-0g3nqJr3Q | US | — | — | whitelisted |
2984 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2984 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2984 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
2984 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDwQ9JNOs3IcArkp%2FBu7NbU | US | der | 472 b | whitelisted |
2984 | iexplore.exe | GET | 200 | 8.253.240.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e4425510b7c8ff5f | US | compressed | 60.0 Kb | whitelisted |
2984 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEG3aTvFLTYzNCmxS2fUJutw%3D | US | der | 471 b | whitelisted |
2984 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCdUrA%2FwvrytArhIvu6cF3d | US | der | 472 b | whitelisted |
2984 | iexplore.exe | GET | 200 | 8.253.240.121:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?379f6632df11727d | US | compressed | 60.0 Kb | whitelisted |
2220 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2984 | iexplore.exe | 52.19.101.114:443 | wekemq.marveilousdates.net | Amazon.com, Inc. | IE | malicious |
2984 | iexplore.exe | 8.253.240.121:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | unknown |
2984 | iexplore.exe | 96.16.145.230:80 | x1.c.lencr.org | Akamai Technologies, Inc. | US | suspicious |
2984 | iexplore.exe | 184.24.77.48:80 | r3.o.lencr.org | Time Warner Cable Internet LLC | US | unknown |
2984 | iexplore.exe | 23.50.131.20:443 | cdn-bimi.akamaized.net | TELECOM ITALIA SPARKLE S.p.A. | NL | suspicious |
2984 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2984 | iexplore.exe | 142.250.185.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2984 | iexplore.exe | 142.250.181.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2028 | chrome.exe | 142.250.186.110:443 | clients2.google.com | Google Inc. | US | whitelisted |
2028 | chrome.exe | 142.250.186.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wekemq.marveilousdates.net |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
cdn-bimi.akamaized.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2028 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2028 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2028 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2028 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2028 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2028 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |