| File name: | OInstall.exe |
| Full analysis: | https://app.any.run/tasks/4367b45c-b660-4a5b-b15c-a9af856ab732 |
| Verdict: | Malicious activity |
| Analysis date: | June 22, 2024, 13:58:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 84CADA0A42D62389069FEB51A78AF9DE |
| SHA1: | 7674CD3D537D9579E4DBDED8847A17B0FD9E2321 |
| SHA256: | FF827953337CEB936F95EEDA314B5F714B7D3EE40E54A2F9D8439C0E215BDA80 |
| SSDEEP: | 98304:j5Xg9czGAefkX2wrdBGxwCSoj/HdHYjt6jLQJeEGjoIeN7BUOHZe952UhVI+aI65:f76/x6 |
MALICIOUS
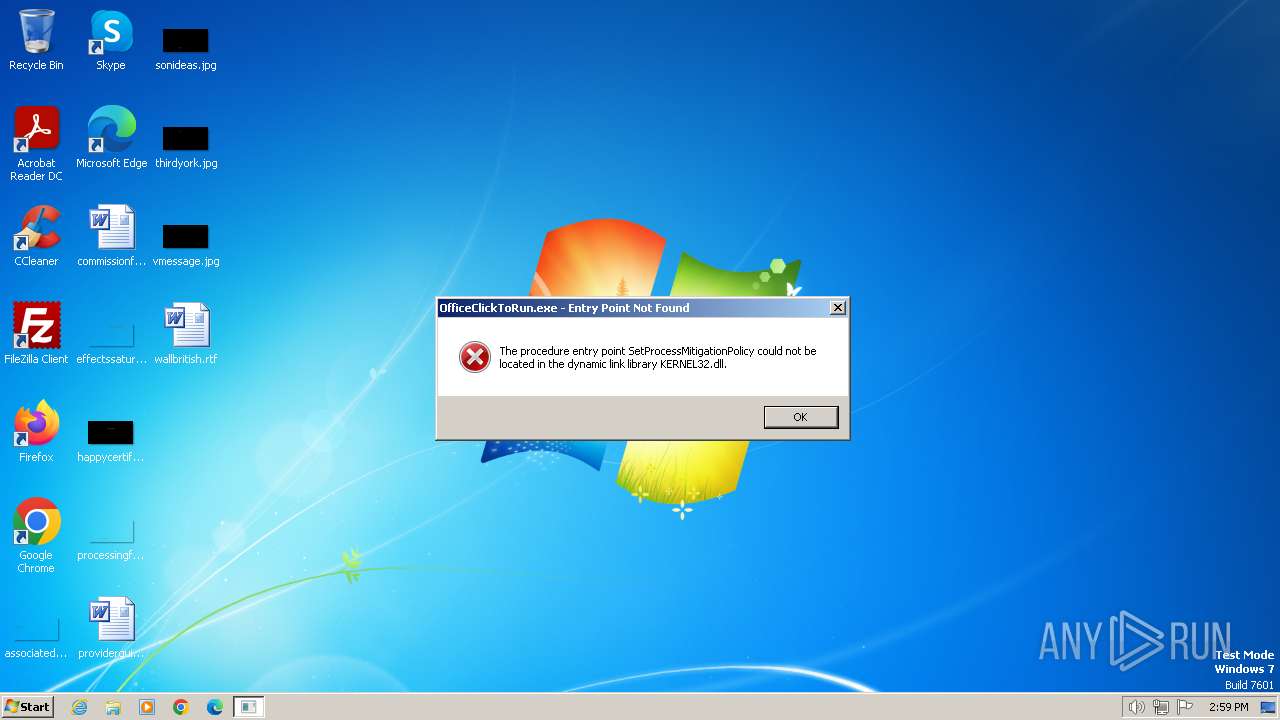
Drops the executable file immediately after the start
- OInstall.exe (PID: 3212)
- files.dat (PID: 2940)
SUSPICIOUS
Starts application with an unusual extension
- cmd.exe (PID: 2100)
Executable content was dropped or overwritten
- files.dat (PID: 2940)
- expand.exe (PID: 1608)
- OInstall.exe (PID: 3212)
Process drops legitimate windows executable
- files.dat (PID: 2940)
- expand.exe (PID: 1608)
Uses REG/REGEDIT.EXE to modify registry
- OInstall.exe (PID: 3212)
Starts CMD.EXE for commands execution
- OInstall.exe (PID: 3212)
Drops 7-zip archiver for unpacking
- OInstall.exe (PID: 3212)
The process drops C-runtime libraries
- files.dat (PID: 2940)
- expand.exe (PID: 1608)
Probably download files using WebClient
- OInstall.exe (PID: 3212)
Unpacks CAB file
- expand.exe (PID: 1608)
- expand.exe (PID: 4020)
Starts POWERSHELL.EXE for commands execution
- OInstall.exe (PID: 3212)
Reads the Internet Settings
- powershell.exe (PID: 2544)
- OInstall.exe (PID: 3212)
- powershell.exe (PID: 3552)
Reads security settings of Internet Explorer
- OInstall.exe (PID: 3212)
The executable file from the user directory is run by the CMD process
- files.dat (PID: 2940)
INFO
Reads the computer name
- OInstall.exe (PID: 3212)
- aria2_oinstall.exe (PID: 1044)
Create files in a temporary directory
- OInstall.exe (PID: 3212)
- files.dat (PID: 2940)
- aria2_oinstall.exe (PID: 1044)
Reads Environment values
- OInstall.exe (PID: 3212)
Checks supported languages
- OInstall.exe (PID: 3212)
- aria2_oinstall.exe (PID: 1044)
- files.dat (PID: 2940)
Disables trace logs
- powershell.exe (PID: 2544)
- powershell.exe (PID: 3552)
Creates files in the program directory
- expand.exe (PID: 1608)
- OInstall.exe (PID: 3212)
- expand.exe (PID: 4020)
Reads the machine GUID from the registry
- aria2_oinstall.exe (PID: 1044)
Drops the executable file immediately after the start
- expand.exe (PID: 1608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.3) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.1) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:01 06:15:12+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 1084416 |
| InitializedDataSize: | 15643648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.7.7.7 |
| ProductVersionNumber: | 7.7.7.7 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
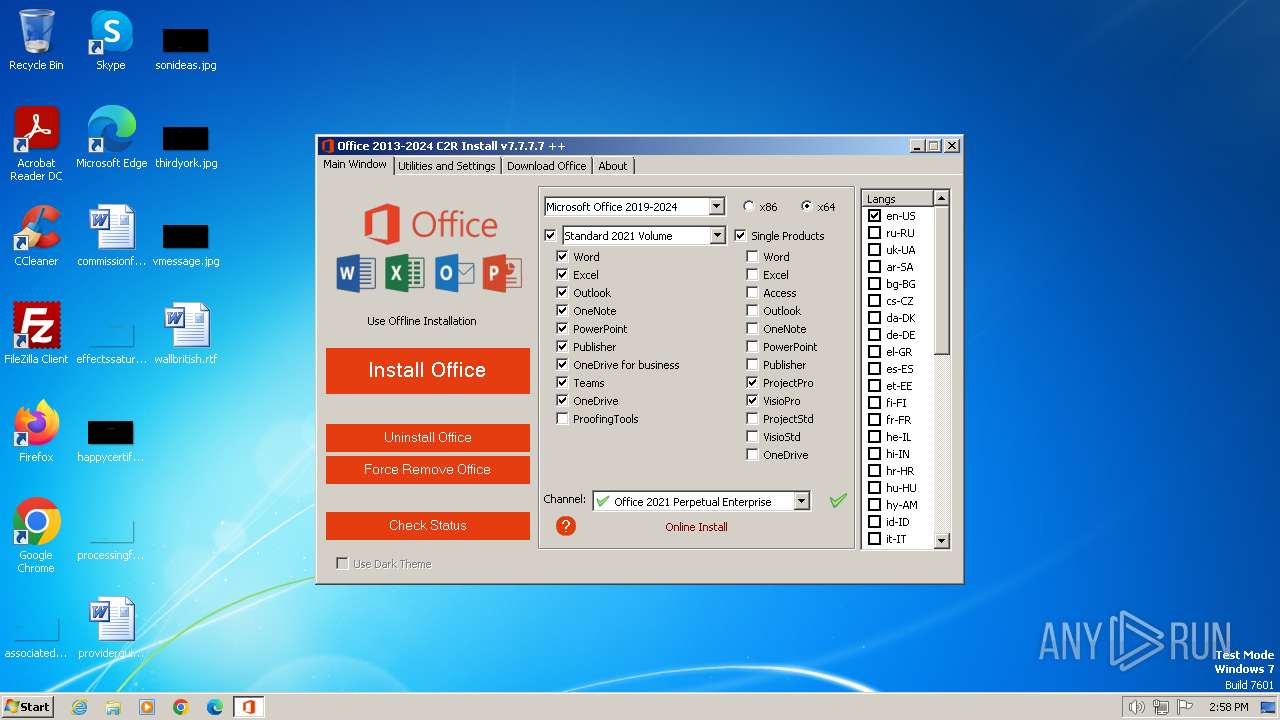
| ProductName: | Office 2013-2024 C2R Install |
| FileDescription: | Office 2013-2024 C2R Install |
Total processes
66
Monitored processes
16
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 936 | "C:\Windows\System32\reg.exe" add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform" /v KeyManagementServiceName /t REG_SZ /d kms.loli.best /f | C:\Windows\System32\reg.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1044 | "C:\Users\admin\AppData\Local\Temp\aria2_oinstall.exe" https://mrodevicemgr.officeapps.live.com/mrodevicemgrsvc/api/v2/C2RReleaseData -over.txt | C:\Users\admin\AppData\Local\Temp\aria2_oinstall.exe | OInstall.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1608 | "expand" i320.cab -F:* "C:\Program Files\Common Files\Microsoft Shared\ClickToRun" | C:\Windows\System32\expand.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: LZ Expansion Utility Exit code: 0 Version: 6.1.7601.24535 (win7sp1_ldr_escrow.191105-1059) Modules
| |||||||||||||||
| 1856 | "C:\Windows\System32\reg.exe" add HKLM\Software\Policies\Microsoft\Office\16.0\Common\OfficeUpdate /v UpdateBranch /d PerpetualVL2021 /f | C:\Windows\System32\reg.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2100 | "C:\Windows\System32\cmd.exe" /D /c files.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2108 | "C:\Windows\System32\reg.exe" add "HKLM\SOFTWARE\Microsoft\Windows Script Host\Settings" /v Enabled /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2492 | "C:\Windows\System32\cmd.exe" /D /c regedit.exe -s C:\Users\admin\AppData\Local\Temp\newui.reg | C:\Windows\System32\cmd.exe | — | OInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2500 | regedit.exe -s C:\Users\admin\AppData\Local\Temp\newui.reg | C:\Windows\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2544 | "powershell" -command "& { (New-Object Net.WebClient).DownloadFile('http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20721/i320.cab', 'C:\Users\admin\AppData\Local\Temp\over410637\i320.cab') }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OInstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2940 | files.dat -y -pkmsauto | C:\Users\admin\AppData\Local\Temp\files\files.dat | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 18.05 Modules
| |||||||||||||||
Total events
6 823
Read events
6 794
Write events
29
Delete events
0
Modification events
| (PID) Process: | (2108) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (3212) OInstall.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (936) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServiceName |
Value: kms.loli.best | |||
| (PID) Process: | (3092) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServicePort |
Value: 1688 | |||
| (PID) Process: | (2500) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\word |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.FluentSVRefresh |
Value: true | |||
| (PID) Process: | (2500) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\word |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.RibbonTouchOptimization |
Value: true | |||
| (PID) Process: | (2500) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\word |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.FluentSVRibbonOptionsMenu |
Value: true | |||
| (PID) Process: | (2500) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\excel |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.FluentSVRefresh |
Value: true | |||
| (PID) Process: | (2500) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\excel |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.RibbonTouchOptimization |
Value: true | |||
| (PID) Process: | (2500) regedit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ExperimentConfigs\ExternalFeatureOverrides\excel |
| Operation: | write | Name: | Microsoft.Office.UXPlatform.FluentSVRibbonOptionsMenu |
Value: true | |||
Executable files
218
Suspicious files
9
Text files
36
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2544 | powershell.exe | C:\Users\admin\AppData\Local\Temp\over410637\i320.cab | — | |
MD5:— | SHA256:— | |||
| 2940 | files.dat | C:\Users\admin\AppData\Local\Temp\files\Uninstall.xml | text | |
MD5:364F86F97324EA82FE0D142CD01CF6DD | SHA256:09D5B42140BAB13165BA97FBD0E77792304C3C93555BE02C3DCE21A7A69C66DD | |||
| 2544 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2940 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\cleanospp.exe | executable | |
MD5:98821A7A5737D656633D10A3AFB724BD | SHA256:04BA4487F95290E0B0557B44300C18F637FBAF0872EE96E3111013B8A1539F25 | |||
| 2940 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x86\msvcr100.dll | executable | |
MD5:BF38660A9125935658CFA3E53FDC7D65 | SHA256:60C06E0FA4449314DA3A0A87C1A9D9577DF99226F943637E06F61188E5862EFA | |||
| 2940 | files.dat | C:\Users\admin\AppData\Local\Temp\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 2544 | powershell.exe | C:\Users\admin\AppData\Local\Temp\5vr0gltg.nxt.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3212 | OInstall.exe | C:\Users\admin\AppData\Local\Temp\files\Configure.xml | text | |
MD5:46C7CEAD7726B1530BB4C096A648137E | SHA256:BF9CA6C946B42346C8E4B5B1EDCEAA9385069F680F53BEA30C9B16529C39EA8B | |||
| 1044 | aria2_oinstall.exe | C:\Users\admin\AppData\Local\Temp\ver.txt.aria2__temp | binary | |
MD5:6DCF1AC5F84442672C7E6DE4C180FFE1 | SHA256:246919A3DEDB59DDDD4EEC13AAE91BF7BB5F190E4BF0631B841A9307ABA9FAF4 | |||
| 1044 | aria2_oinstall.exe | C:\Users\admin\AppData\Local\Temp\ver.txt.aria2 | binary | |
MD5:6DCF1AC5F84442672C7E6DE4C180FFE1 | SHA256:246919A3DEDB59DDDD4EEC13AAE91BF7BB5F190E4BF0631B841A9307ABA9FAF4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
13
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
480 | lsass.exe | GET | 304 | 2.19.126.154:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?cfa3fea8103cb675 | unknown | — | — | unknown |
480 | lsass.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2544 | powershell.exe | GET | 200 | 178.79.242.16:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20721/i320.cab | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3552 | powershell.exe | GET | 200 | 178.79.242.16:80 | http://officecdn.microsoft.com/pr/5030841d-c919-4594-8d2d-84ae4f96e58e/Office/Data/16.0.14332.20721/i321033.cab | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1044 | aria2_oinstall.exe | 52.109.89.117:443 | mrodevicemgr.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
480 | lsass.exe | 2.19.126.154:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
480 | lsass.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1372 | svchost.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mrodevicemgr.officeapps.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |