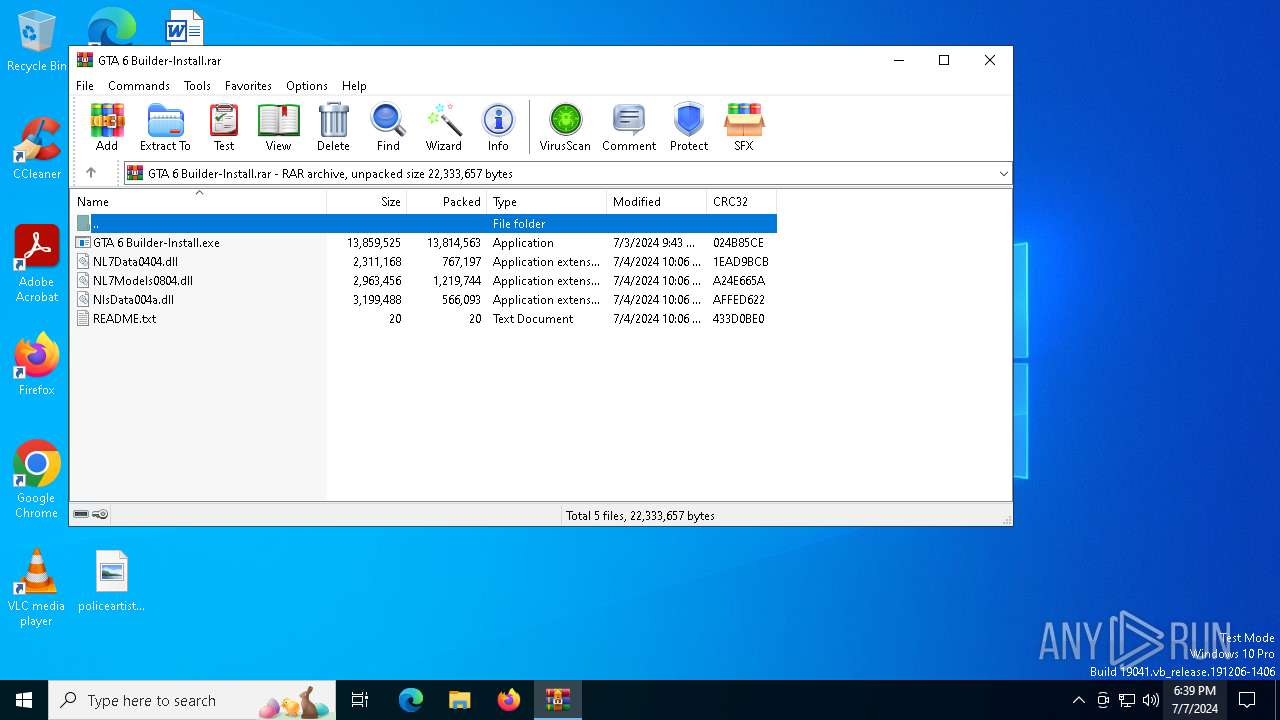
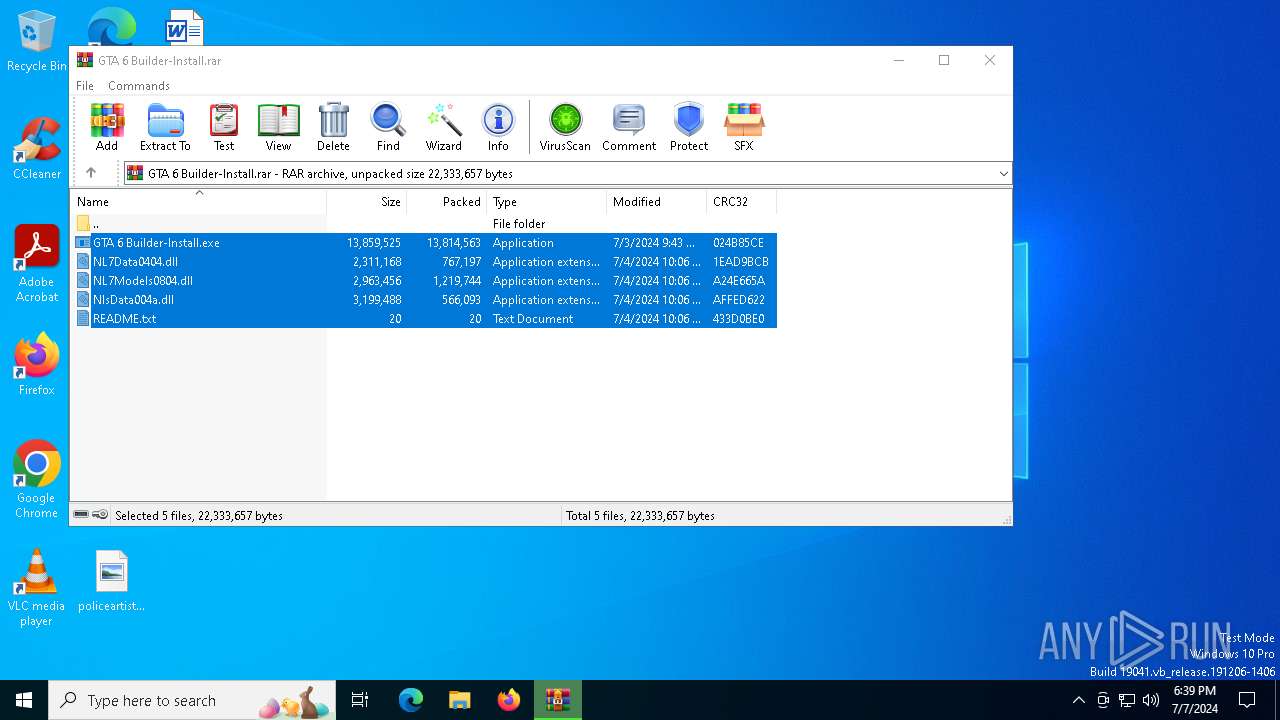
| File name: | GTA 6 Builder-Install.rar |
| Full analysis: | https://app.any.run/tasks/a7442f26-8820-4b41-afcf-9c69fdef15b5 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | July 07, 2024, 18:38:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 6A7189BB6B47EB3637AFF370BD6D04BE |
| SHA1: | 09A2132FA1C20A2B9298B801B4603CFEA84D7AC1 |
| SHA256: | FF635DB42400A8B73BFB2E2428ACE9F527393DD3429F6E8422A453CA2FE98720 |
| SSDEEP: | 98304:WsbA/uxT5Q9D66QMDsZ/qTjqqQSQhdcXFIJ0Rrn7ru0yldctdg5nysWHc8W+YAig:N7PePKakYwzQZxYV/uFxpjmLZp0 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2704)
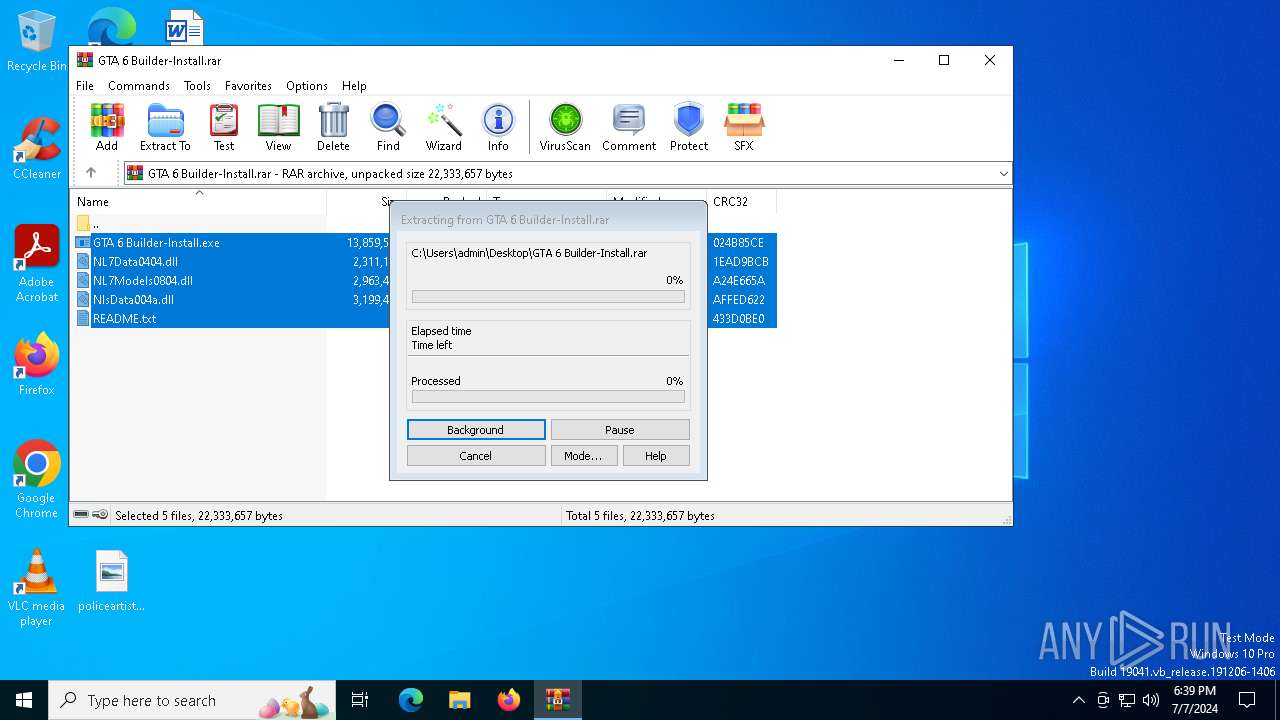
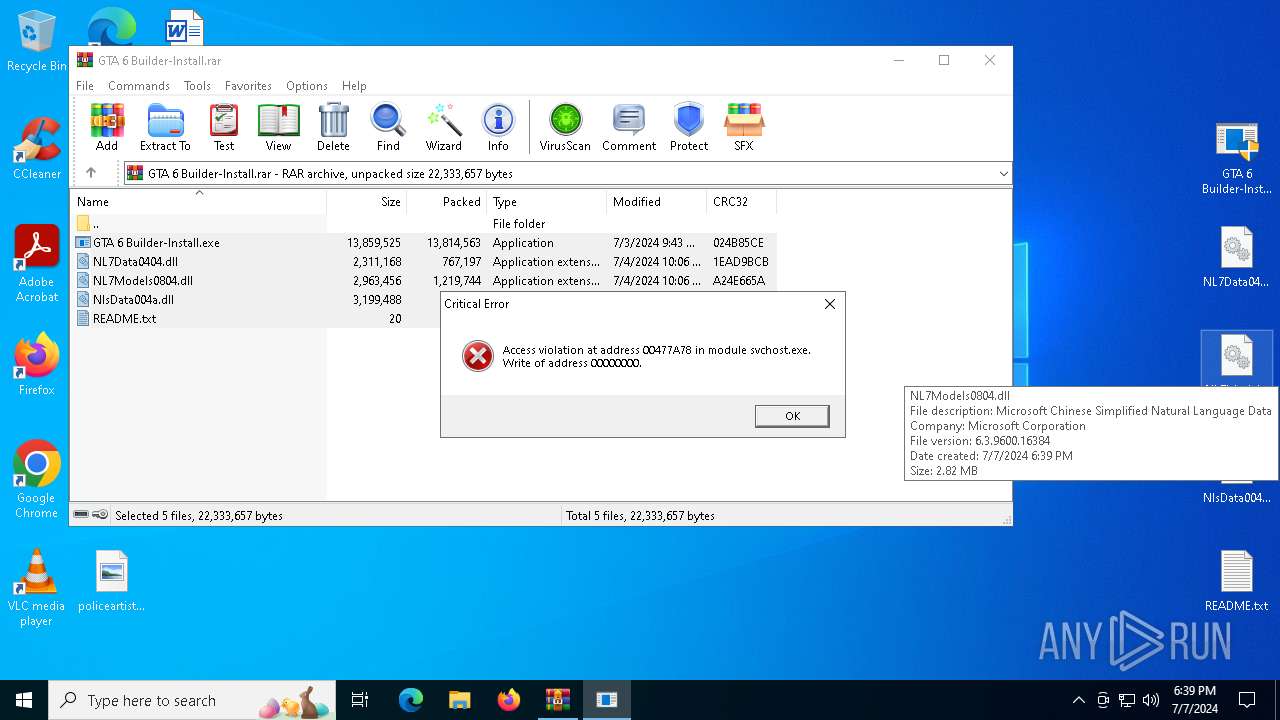
- GTA 6 Builder-Install.exe (PID: 5940)
- Runtime64.exe (PID: 2412)
- ComHostSvc.exe (PID: 1760)
Create files in the Startup directory
- Runtime64.exe (PID: 2412)
DcRAT is detected
- ComHostSvc.exe (PID: 1760)
Connects to the CnC server
- ComHostSvc.exe (PID: 1760)
DARKCRYSTAL has been detected (SURICATA)
- ComHostSvc.exe (PID: 1760)
DCRAT has been detected (YARA)
- ComHostSvc.exe (PID: 1760)
Steals credentials from Web Browsers
- ComHostSvc.exe (PID: 1760)
Actions looks like stealing of personal data
- ComHostSvc.exe (PID: 1760)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2704)
Reads the BIOS version
- GTA 6 Builder-Install.exe (PID: 5940)
Reads security settings of Internet Explorer
- GTA 6 Builder-Install.exe (PID: 5940)
- ComHostSvc.exe (PID: 1760)
Reads the date of Windows installation
- GTA 6 Builder-Install.exe (PID: 5940)
- ComHostSvc.exe (PID: 1760)
Executable content was dropped or overwritten
- GTA 6 Builder-Install.exe (PID: 5940)
- Runtime64.exe (PID: 2412)
- ComHostSvc.exe (PID: 1760)
The process creates files with name similar to system file names
- Runtime64.exe (PID: 2412)
Found regular expressions for crypto-addresses (YARA)
- Runtime64.exe (PID: 2412)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1924)
Starts CMD.EXE for commands execution
- ComHostSvc.exe (PID: 1760)
Starts application with an unusual extension
- cmd.exe (PID: 1924)
Loads DLL from Mozilla Firefox
- ComHostSvc.exe (PID: 1760)
Executing commands from a ".bat" file
- ComHostSvc.exe (PID: 1760)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2704)
Checks supported languages
- GTA 6 Builder-Install.exe (PID: 5940)
- ComHostSvc.exe (PID: 1760)
- Runtime64.exe (PID: 2412)
- chcp.com (PID: 3228)
Manual execution by a user
- GTA 6 Builder-Install.exe (PID: 5940)
- GTA 6 Builder-Install.exe (PID: 1956)
Create files in a temporary directory
- GTA 6 Builder-Install.exe (PID: 5940)
- ComHostSvc.exe (PID: 1760)
Process checks computer location settings
- GTA 6 Builder-Install.exe (PID: 5940)
- ComHostSvc.exe (PID: 1760)
Process checks whether UAC notifications are on
- GTA 6 Builder-Install.exe (PID: 5940)
Reads the computer name
- ComHostSvc.exe (PID: 1760)
- GTA 6 Builder-Install.exe (PID: 5940)
- Runtime64.exe (PID: 2412)
Reads Environment values
- ComHostSvc.exe (PID: 1760)
Disables trace logs
- ComHostSvc.exe (PID: 1760)
Creates files or folders in the user directory
- Runtime64.exe (PID: 2412)
Reads the machine GUID from the registry
- ComHostSvc.exe (PID: 1760)
Checks proxy server information
- ComHostSvc.exe (PID: 1760)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- ComHostSvc.exe (PID: 1760)
.NET Reactor protector has been detected
- ComHostSvc.exe (PID: 1760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DcRat
(PID) Process(1760) ComHostSvc.exe
C2 (1)http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php
Options
PluginConfigs
0{SYSTEMDRIVE}/Users/
1false
2false
3true
4true
5true
6true
7false
8true
9true
10true
11true
12true
13true
14true
Version5.0.1
C2 (1)http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php
Options
PluginConfigs
0{SYSTEMDRIVE}/Users/
1false
2false
3true
4true
5true
6true
7false
8true
9true
10true
11true
12true
13true
14true
Version5.0.1
Plugins (2)TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAKX/2QAAAAAAAAAAOAAIiALAQgAAEYBAAAGAAAAAAAA7mUBAAAgAAAAgAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAQAAAgAAm0ACAAMAQIUA...
TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDALI7+mQAAAAAAAAAAOAAIiALAQgAAAgBAAAGAAAAAAAAricBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAArNABAAMAQIUA...
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
145
Monitored processes
9
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | "C:\Users\admin\AppData\Local\Temp\ComHostSvc.exe" | C:\Users\admin\AppData\Local\Temp\ComHostSvc.exe | GTA 6 Builder-Install.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.2.7.1277 Modules
DcRat(PID) Process(1760) ComHostSvc.exe C2 (1)http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php Options PluginConfigs 0{SYSTEMDRIVE}/Users/ 1false 2false 3true 4true 5true 6true 7false 8true 9true 10true 11true 12true 13true 14true Version5.0.1 (PID) Process(1760) ComHostSvc.exe C2 (1)http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php Options PluginConfigs 0{SYSTEMDRIVE}/Users/ 1false 2false 3true 4true 5true 6true 7false 8true 9true 10true 11true 12true 13true 14true Version5.0.1 Plugins (2)TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDAAKX/2QAAAAAAAAAAOAAIiALAQgAAEYBAAAGAAAAAAAA7mUBAAAgAAAAgAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAADAAQAAAgAAm0ACAAMAQIUA... TVqQAAMAAAAEAAAA//8AALgAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAgAAAAA4fug4AtAnNIbgBTM0hVGhpcyBwcm9ncmFtIGNhbm5vdCBiZSBydW4gaW4gRE9TIG1vZGUuDQ0KJAAAAAAAAABQRQAATAEDALI7+mQAAAAAAAAAAOAAIiALAQgAAAgBAAAGAAAAAAAAricBAAAgAAAAQAEAAABAAAAgAAAAAgAABAAAAAAAAAAEAAAAAAAAAACAAQAAAgAArNABAAMAQIUA... | |||||||||||||||
| 1924 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\AppData\Local\Temp\iOYCRAfa0D.bat" | C:\Windows\System32\cmd.exe | — | ComHostSvc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1956 | "C:\Users\admin\Desktop\GTA 6 Builder-Install.exe" | C:\Users\admin\Desktop\GTA 6 Builder-Install.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2412 | "C:\Users\admin\AppData\Local\Temp\Runtime64.exe" | C:\Users\admin\AppData\Local\Temp\Runtime64.exe | GTA 6 Builder-Install.exe | ||||||||||||
User: admin Company: Microsoft Windows Integrity Level: HIGH Description: system32 Version: 15.6.13.6 Modules
| |||||||||||||||
| 2704 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\GTA 6 Builder-Install.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3228 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4264 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5940 | "C:\Users\admin\Desktop\GTA 6 Builder-Install.exe" | C:\Users\admin\Desktop\GTA 6 Builder-Install.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
13 448
Read events
13 396
Write events
52
Delete events
0
Modification events
| (PID) Process: | (2704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\GTA 6 Builder-Install.rar | |||
| (PID) Process: | (2704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5940) GTA 6 Builder-Install.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5940) GTA 6 Builder-Install.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
15
Suspicious files
20
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2704 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2704.35624\NlsData004a.dll | executable | |
MD5:BE007B645B9D1332E3346107727320D9 | SHA256:7B128BE8D77398CBC3BB789A34E21AFC984C2E87276907A01326F8FB4504E9DA | |||
| 5940 | GTA 6 Builder-Install.exe | C:\Users\admin\AppData\Local\Temp\Runtime64.exe | executable | |
MD5:DA23F44A96E6AA3A8B80F1CC40169DAE | SHA256:2D86AB0D97A265AA7B465439AC97C0C6B428A3BDC18000625F3FD66C07FF6F70 | |||
| 2704 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2704.35624\NL7Models0804.dll | executable | |
MD5:65525C7B89204D241120B7638934A0D2 | SHA256:18F7F52F14986133F9A9676D5AB959349377A53C0936CEA6EB9880E72F85BC54 | |||
| 5940 | GTA 6 Builder-Install.exe | C:\Users\admin\AppData\Local\Temp\ComHostSvc.exe | executable | |
MD5:31E5E3AC5A03D60D67188B6B0C3D152B | SHA256:DC73CE51066FDCD5F0C7C88FD6FDFB9A4A3722EBE3D2DEF1DC593FBC1AF9E467 | |||
| 2704 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2704.35624\README.txt | text | |
MD5:229BFB07694F123E2CB4986F47100A62 | SHA256:8DF26B1F550C80646F01D25B8AAFCABB1342BBB2BE1CD335CDB8D254BE8C4090 | |||
| 1760 | ComHostSvc.exe | C:\Users\admin\Desktop\GCTBJCRj.log | executable | |
MD5:2E116FC64103D0F0CF47890FD571561E | SHA256:25EEEA99DCA05BF7651264FA0C07E0E91D89E0DA401C387284E9BE9AFDF79625 | |||
| 1760 | ComHostSvc.exe | C:\Users\admin\Desktop\OgbrtvgQ.log | executable | |
MD5:E84DCD8370FAC91DE71DEF8DCF09BFEC | SHA256:DD7AC164E789CAD96D30930EFE9BBA99698473EDEA38252C2C0EA44043FB1DB5 | |||
| 2412 | Runtime64.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svhost.exe | executable | |
MD5:DA23F44A96E6AA3A8B80F1CC40169DAE | SHA256:2D86AB0D97A265AA7B465439AC97C0C6B428A3BDC18000625F3FD66C07FF6F70 | |||
| 1760 | ComHostSvc.exe | C:\Users\admin\Desktop\bFlxkUmr.log | executable | |
MD5:E9CE850DB4350471A62CC24ACB83E859 | SHA256:7C95D3B38114E7E4126CB63AADAF80085ED5461AB0868D2365DD6A18C946EA3A | |||
| 1760 | ComHostSvc.exe | C:\Users\admin\AppData\Local\Temp\gh78aReggp | sqlite | |
MD5:9F6D153D934BCC50E8BC57E7014B201A | SHA256:2A7FC7F64938AD07F7249EC0BED6F48BC5302EA84FE9E61E276436EA942BA230 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
84
TCP/UDP connections
69
DNS requests
19
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1968 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1968 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1760 | ComHostSvc.exe | POST | 200 | 172.67.185.34:80 | http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php | unknown | — | — | unknown |
1760 | ComHostSvc.exe | POST | 200 | 172.67.185.34:80 | http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php | unknown | — | — | unknown |
1760 | ComHostSvc.exe | POST | 200 | 172.67.185.34:80 | http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php | unknown | — | — | unknown |
1760 | ComHostSvc.exe | POST | 200 | 172.67.185.34:80 | http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php | unknown | — | — | unknown |
1760 | ComHostSvc.exe | POST | 200 | 172.67.185.34:80 | http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
1760 | ComHostSvc.exe | POST | 200 | 172.67.185.34:80 | http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php | unknown | — | — | unknown |
1760 | ComHostSvc.exe | POST | 200 | 172.67.185.34:80 | http://968620cm.nyashkoon.top/PythonLowProcesswpdownloads.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1968 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3828 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3808 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1968 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1968 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1968 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
1968 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
968620cm.nyashkoon.top |
| unknown |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
1760 | ComHostSvc.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
1760 | ComHostSvc.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
1760 | ComHostSvc.exe | A Network Trojan was detected | REMOTE [ANY.RUN] DarkCrystal Rat Check-in (POST) |
1760 | ComHostSvc.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible DarkCrystal Rat Encrypted Connection |
1760 | ComHostSvc.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
1760 | ComHostSvc.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
1760 | ComHostSvc.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible DarkCrystal Rat Encrypted Connection |