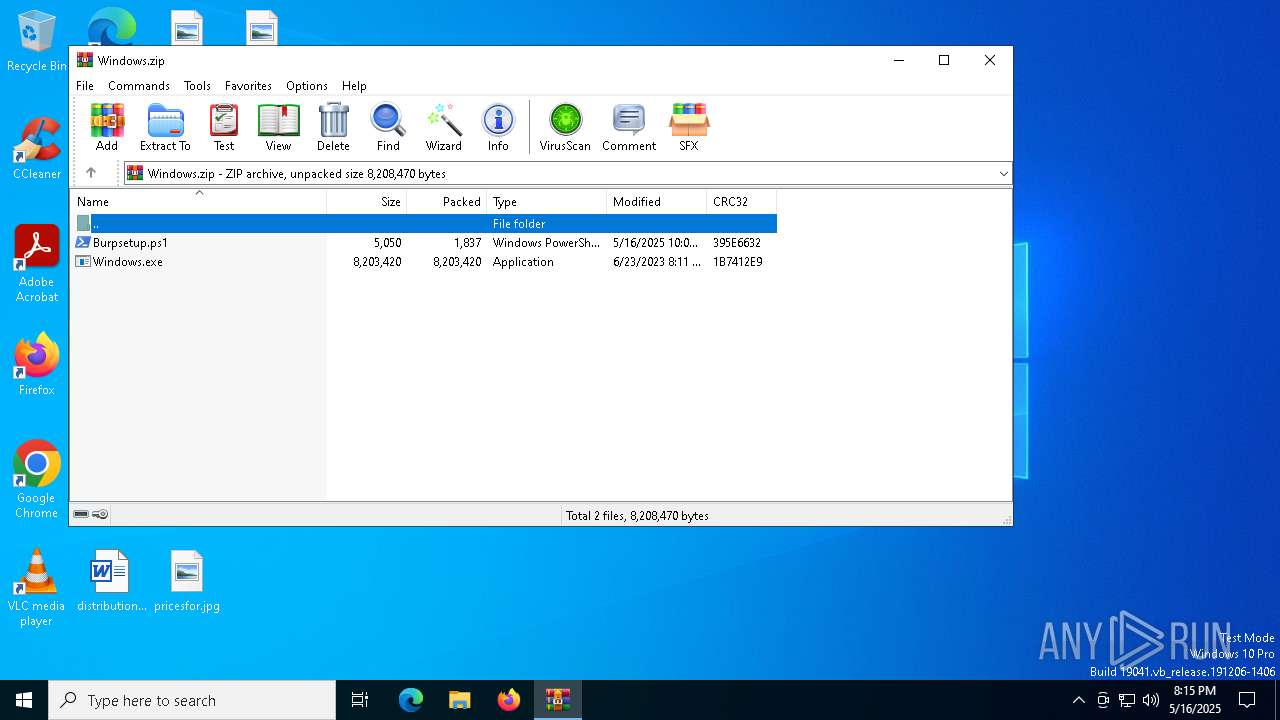
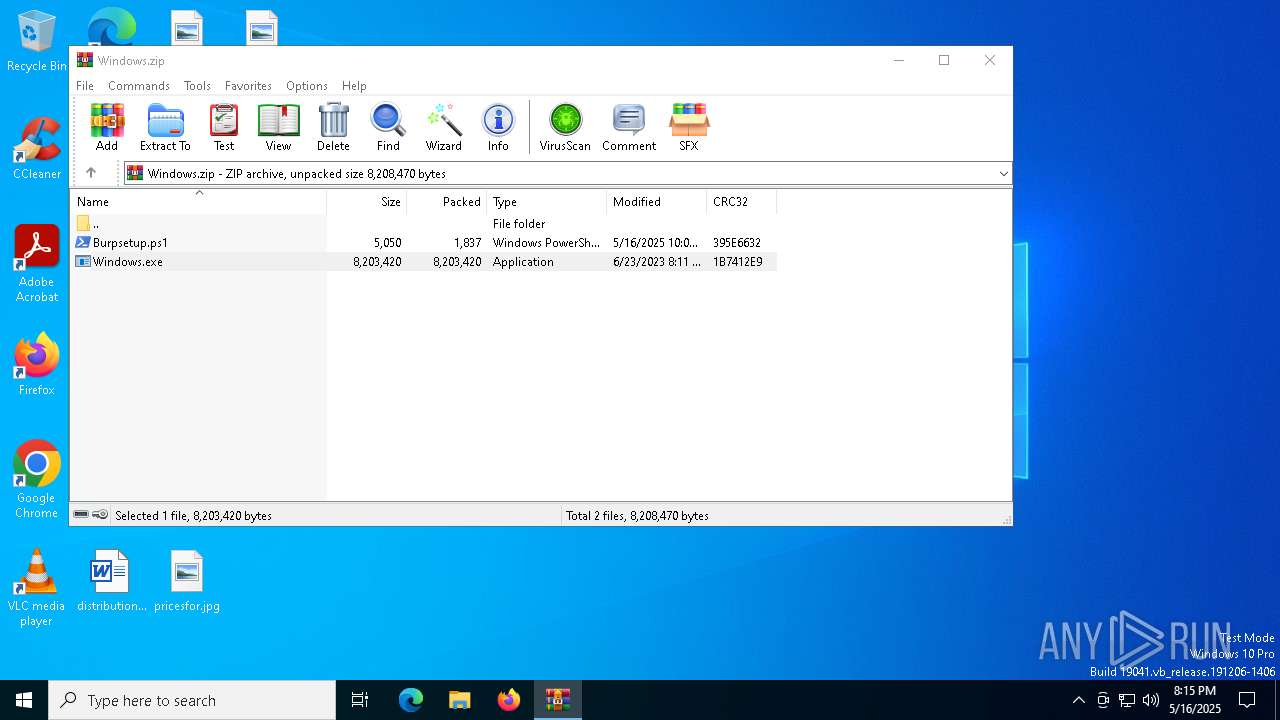
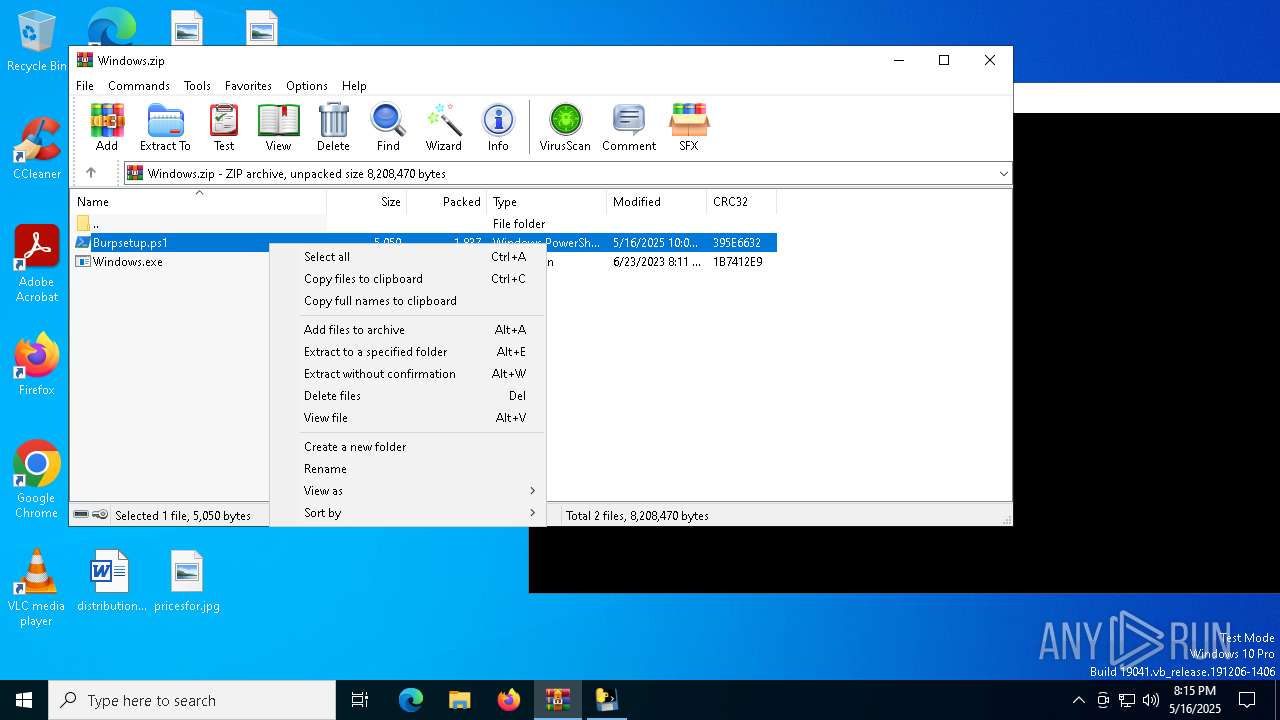
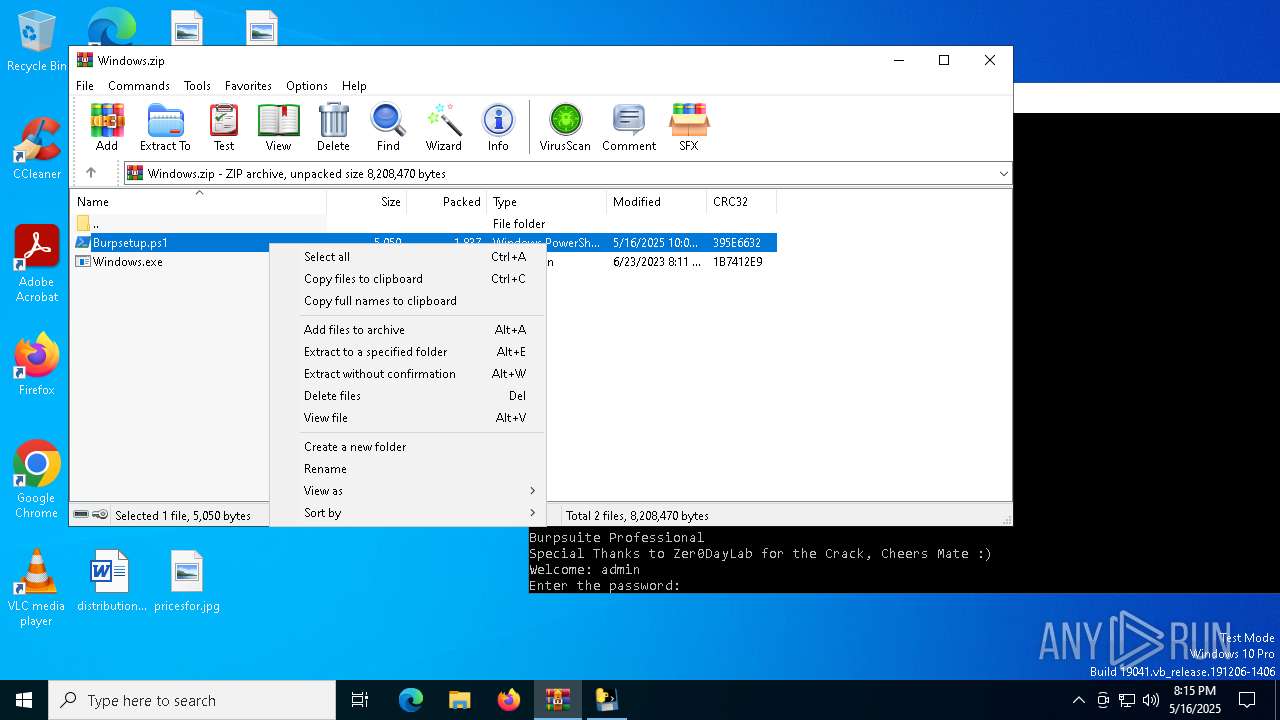
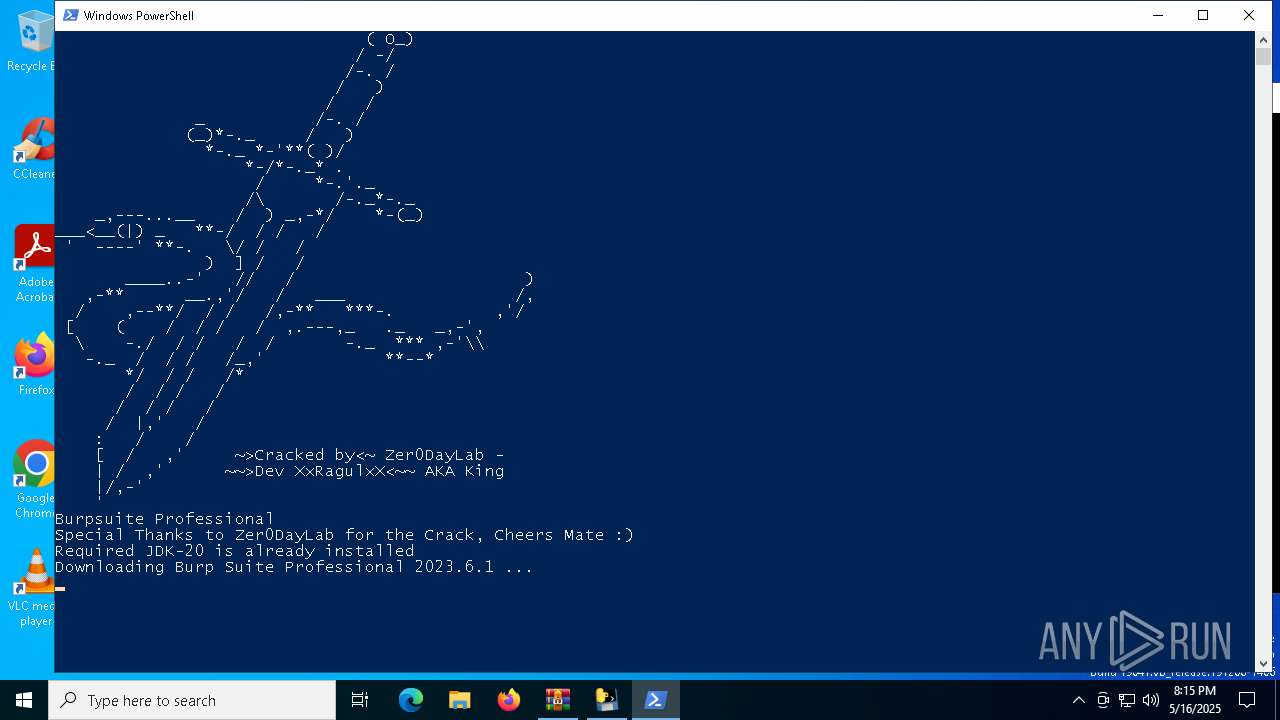
| File name: | Windows.zip |
| Full analysis: | https://app.any.run/tasks/a252375f-a7bd-4cbc-927e-16bff815cc48 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 20:15:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | E07163758A938E72745B598EC2DE18A3 |
| SHA1: | 612B4FCE65AC7B055971B521DBC35A10C5018B8F |
| SHA256: | FF4F9AECFD0885569125065B5FA7CD99E4B7A4F2C46043A659E95FC9A28B8DA2 |
| SSDEEP: | 98304:AXErSsuDacbtq9IRQJ+FgLHIcc1UmbOEk4Hr1XcRpls9LuZGsnaQTnTebLOAhujV:lBHzovr1D+p |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5868)
Changes powershell execution policy (Bypass)
- WinRAR.exe (PID: 5868)
Bypass execution policy to execute commands
- powershell.exe (PID: 7148)
SUSPICIOUS
Process drops legitimate windows executable
- Windows.exe (PID: 4880)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5868)
The process drops C-runtime libraries
- Windows.exe (PID: 4880)
Application launched itself
- Windows.exe (PID: 4880)
Process drops python dynamic module
- Windows.exe (PID: 4880)
The process executes Powershell scripts
- WinRAR.exe (PID: 5868)
Starts POWERSHELL.EXE for commands execution
- WinRAR.exe (PID: 5868)
Executable content was dropped or overwritten
- Windows.exe (PID: 4880)
Loads Python modules
- Windows.exe (PID: 5972)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5868)
The sample compiled with english language support
- Windows.exe (PID: 4880)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 5868)
Checks supported languages
- Windows.exe (PID: 4880)
- Windows.exe (PID: 5972)
Reads the computer name
- Windows.exe (PID: 4880)
Create files in a temporary directory
- Windows.exe (PID: 4880)
Disables trace logs
- powershell.exe (PID: 7148)
Checks proxy server information
- powershell.exe (PID: 7148)
Reads the software policy settings
- slui.exe (PID: 6476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:06:23 13:41:56 |
| ZipCRC: | 0x1b7412e9 |
| ZipCompressedSize: | 8203420 |
| ZipUncompressedSize: | 8203420 |
| ZipFileName: | Windows.exe |
Total processes
136
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1300 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1312 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Windows.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5868.33950\Windows.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5868.33950\Windows.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5868 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Windows.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5972 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5868.33950\Windows.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5868.33950\Windows.exe | — | Windows.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6476 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7148 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\AppData\Local\Temp\Rar$DIa5868.35227\Burpsetup.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 258
Read events
8 249
Write events
9
Delete events
0
Modification events
| (PID) Process: | (5868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Windows.zip | |||
| (PID) Process: | (5868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5868) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.ps1\OpenWithProgids |
| Operation: | write | Name: | Microsoft.PowerShellConsole.1 |
Value: | |||
Executable files
19
Suspicious files
4
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4880 | Windows.exe | C:\Users\admin\AppData\Local\Temp\_MEI48802\_hashlib.pyd | executable | |
MD5:4255C44DC64F11F32C961BF275AAB3A2 | SHA256:E557873D5AD59FD6BD29D0F801AD0651DBB8D9AC21545DEFE508089E92A15E29 | |||
| 5868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5868.33950\Burpsetup.ps1 | text | |
MD5:FD70BFFDA7CCF55C959B13AD4BF9B9C7 | SHA256:2778FCE8B9C54BE75658DE4968068DDC6150BCA08C44F795291F91AAE1E2DC46 | |||
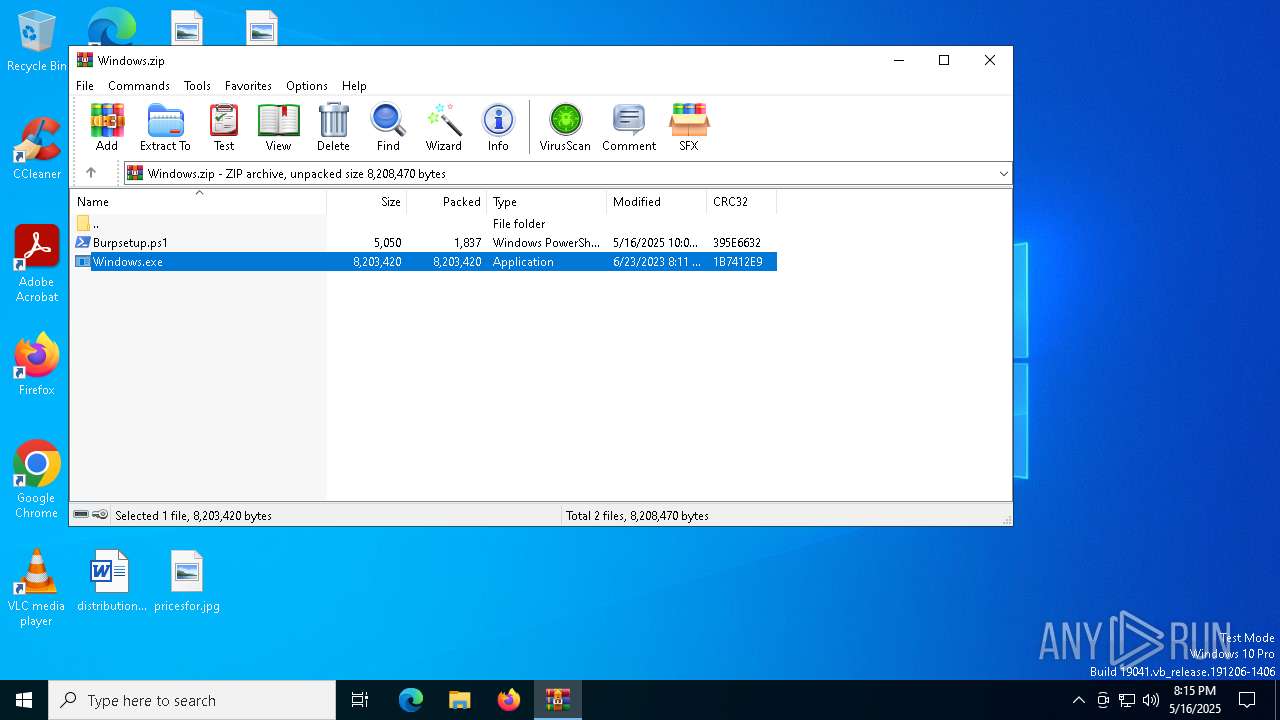
| 5868 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5868.33950\Windows.exe | executable | |
MD5:B8689FCF95C9BA980E9BC49E8CBBE34C | SHA256:93FA55CD1E46C9282D183AE68F0BA84973AFF1D9BD790F728A55F5C67753B752 | |||
| 4880 | Windows.exe | C:\Users\admin\AppData\Local\Temp\_MEI48802\zstandard\_cffi.cp311-win_amd64.pyd | executable | |
MD5:C07CA2CC7D6B81D35C160C09E44906CC | SHA256:3733FF51D56DEC9204DC36DA4BCA9D01FE4C68EC0954C81E3D1F105D9AE12C92 | |||
| 4880 | Windows.exe | C:\Users\admin\AppData\Local\Temp\_MEI48802\python3.dll | executable | |
MD5:B711598FC3ED0FE4CF2C7F3E0877979E | SHA256:520169AA6CF49D7EE724D1178DE1BE0E809E4BDCF671E06F3D422A0DD5FD294A | |||
| 4880 | Windows.exe | C:\Users\admin\AppData\Local\Temp\_MEI48802\_ssl.pyd | executable | |
MD5:208B0108172E59542260934A2E7CFA85 | SHA256:5160500474EC95D4F3AF7E467CC70CB37BEC1D12545F0299AAB6D69CEA106C69 | |||
| 4880 | Windows.exe | C:\Users\admin\AppData\Local\Temp\_MEI48802\charset_normalizer\md.cp311-win_amd64.pyd | executable | |
MD5:FA50D9F8BCE6BD13652F5090E7B82C4D | SHA256:FFF69928DEA1432E0C7CB1225AB96F94FD38D5D852DE9A6BB8BF30B7D2BEDCEB | |||
| 4880 | Windows.exe | C:\Users\admin\AppData\Local\Temp\_MEI48802\select.pyd | executable | |
MD5:C97A587E19227D03A85E90A04D7937F6 | SHA256:C4AA9A106381835CFB5F9BADFB9D77DF74338BC66E69183757A5A3774CCDACCF | |||
| 4880 | Windows.exe | C:\Users\admin\AppData\Local\Temp\_MEI48802\libcrypto-1_1.dll | executable | |
MD5:E94733523BCD9A1FB6AC47E10A267287 | SHA256:F20EB4EFD8647B5273FDAAFCEB8CCB2B8BA5329665878E01986CBFC1E6832C44 | |||
| 4880 | Windows.exe | C:\Users\admin\AppData\Local\Temp\_MEI48802\VCRUNTIME140.dll | executable | |
MD5:4585A96CC4EEF6AAFD5E27EA09147DC6 | SHA256:A8F950B4357EC12CFCCDDC9094CCA56A3D5244B95E09EA6E9A746489F2D58736 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1388 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1388 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1388 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
portswigger-cdn.net |
| unknown |