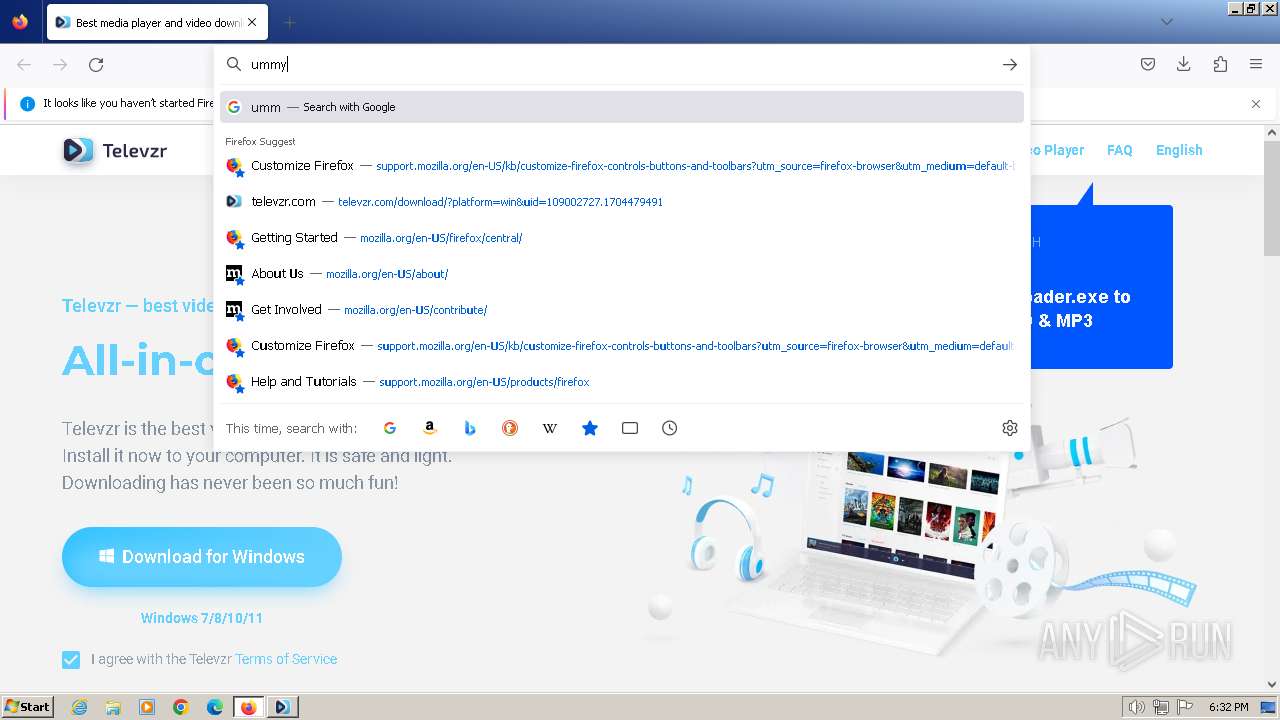
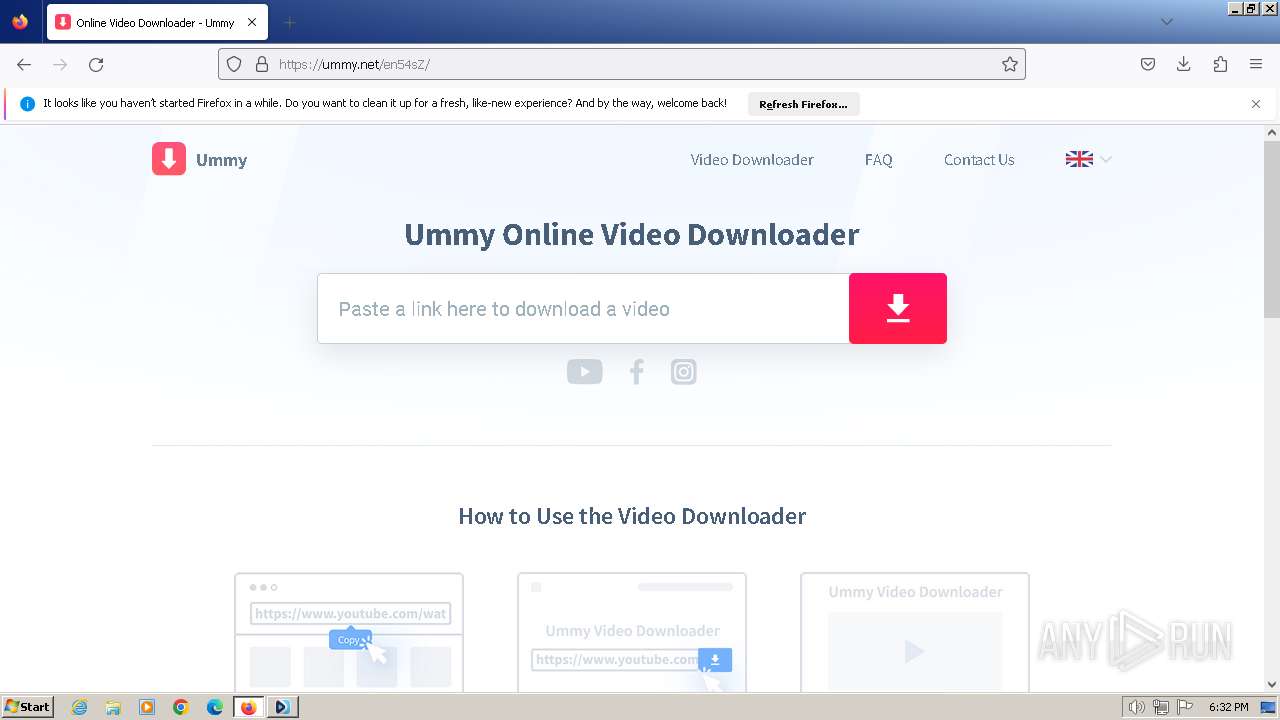
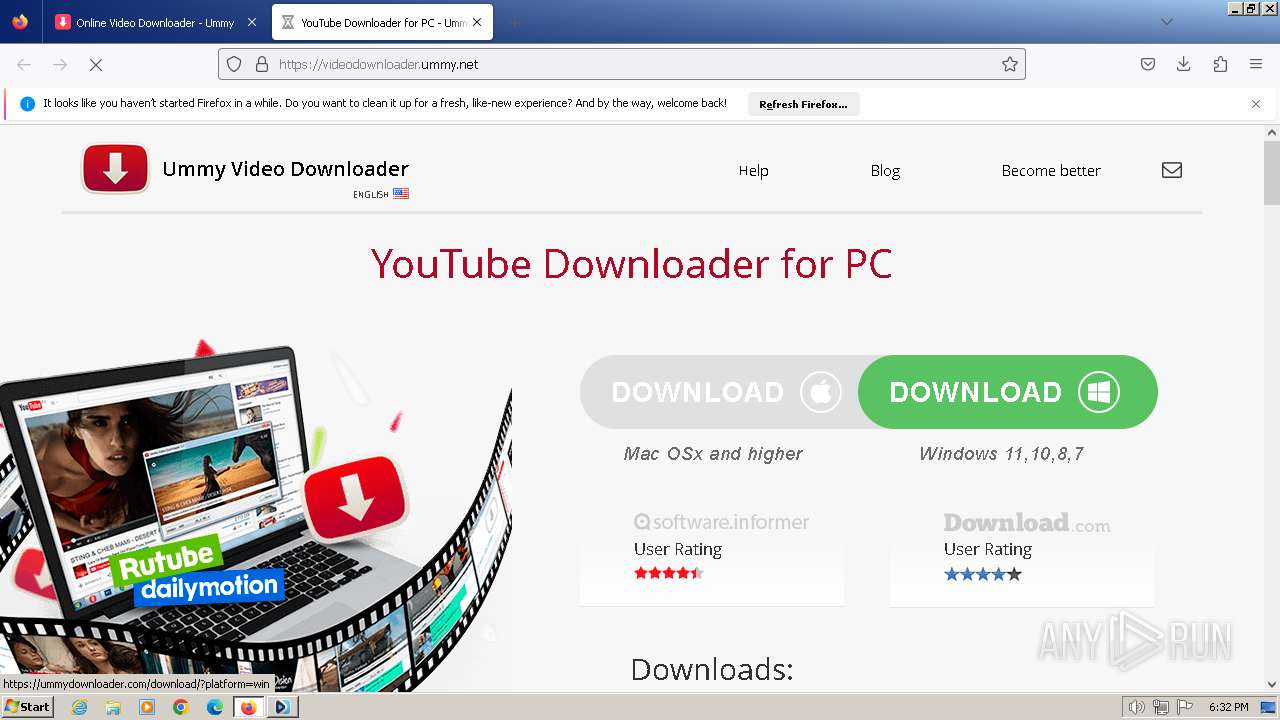
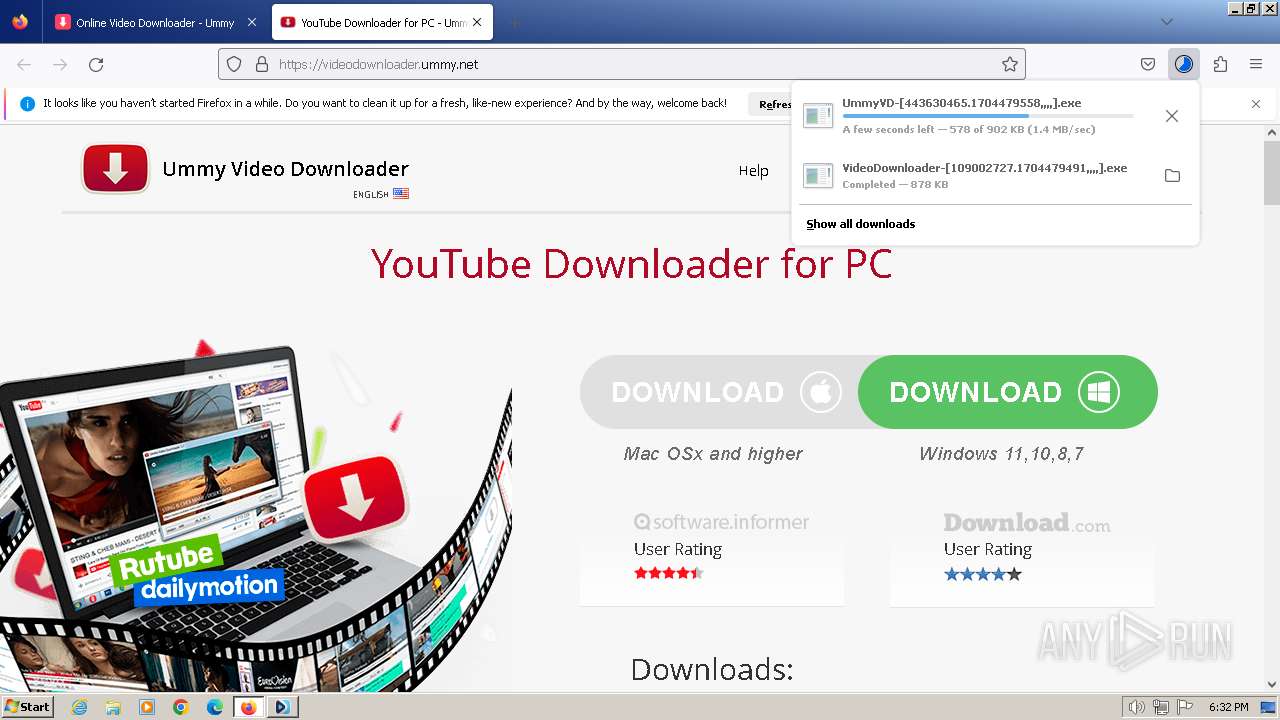
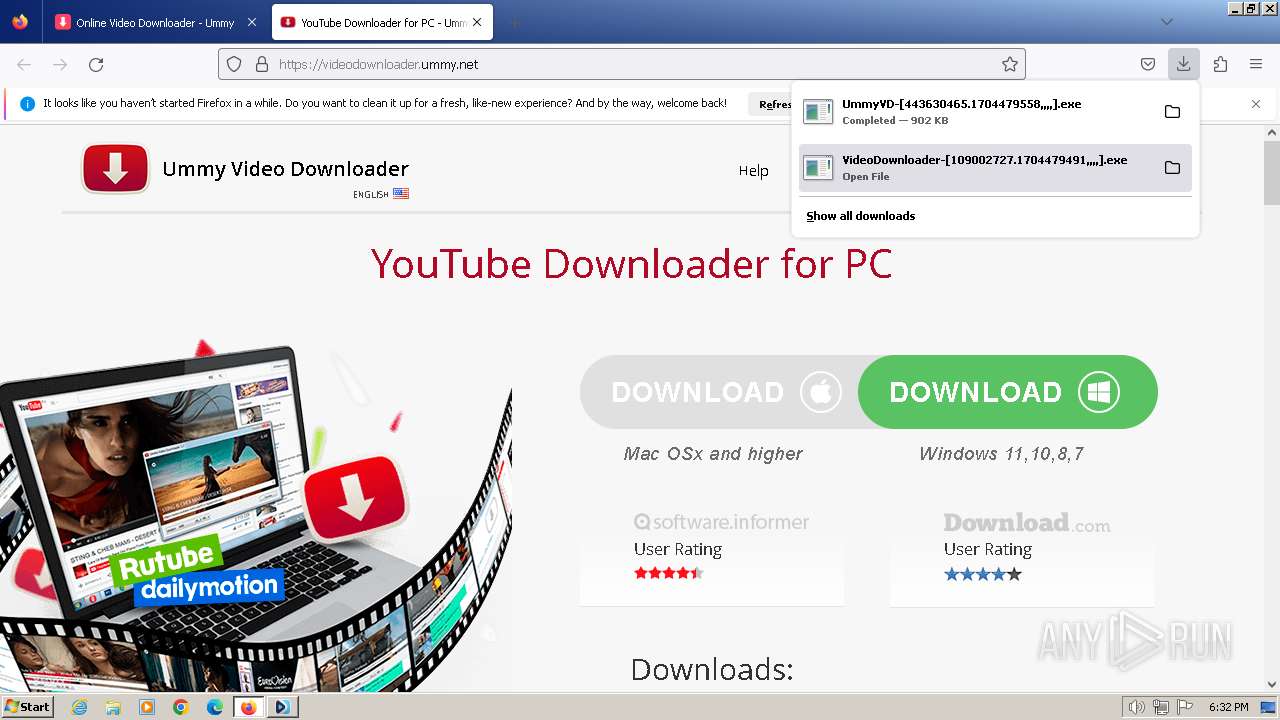
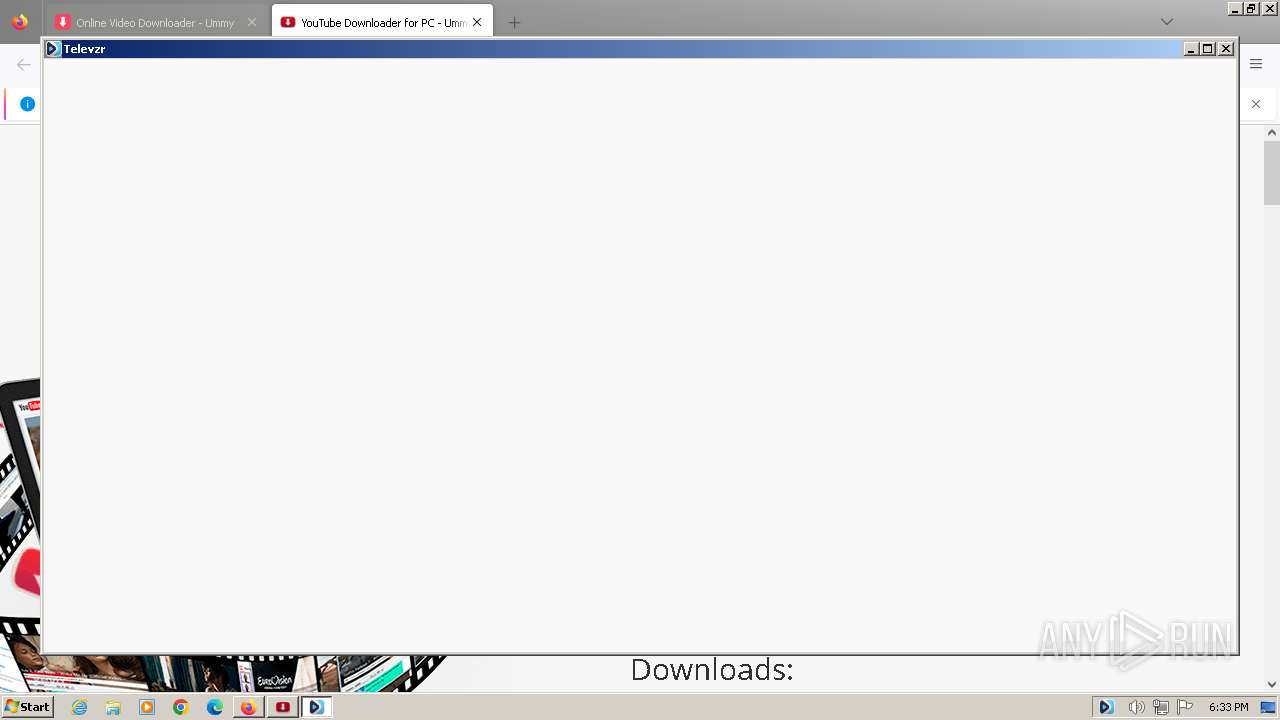
| URL: | https://televzr.com |
| Full analysis: | https://app.any.run/tasks/0f04ea01-42f9-4c13-9ab5-eed873165119 |
| Verdict: | Malicious activity |
| Analysis date: | January 05, 2024, 18:31:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8671D15BEBAC14CCCD90AC0A6F193BB4 |
| SHA1: | 7A0DFC2C52F2CA6C8A96147EBF157C00676A61DE |
| SHA256: | FF41BC05CB58D549B475E3C8E28C95A713B39A916BAD11EB27036DCD6C7DF470 |
| SSDEEP: | 3:N8IObGT:2Ip |
MALICIOUS
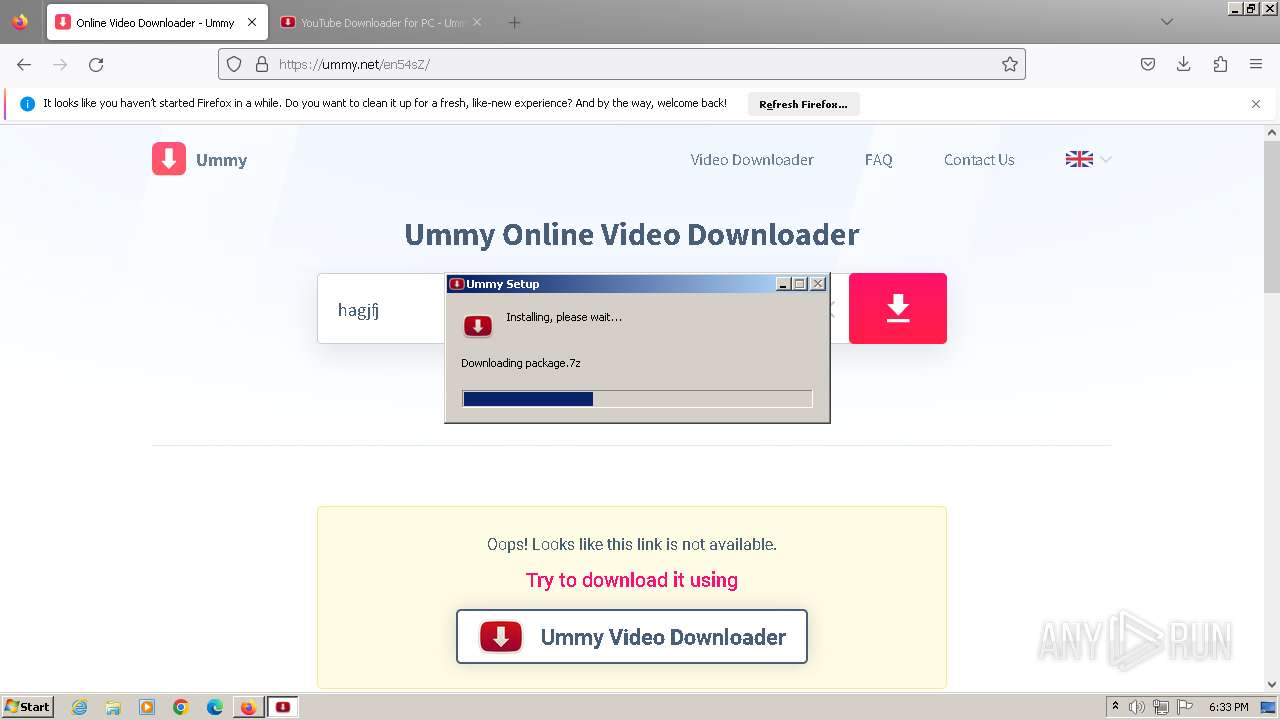
Creates a writable file in the system directory
- msiexec.exe (PID: 2884)
Actions looks like stealing of personal data
- Televzr.exe (PID: 1104)
- Ummy.exe (PID: 3652)
SUSPICIOUS
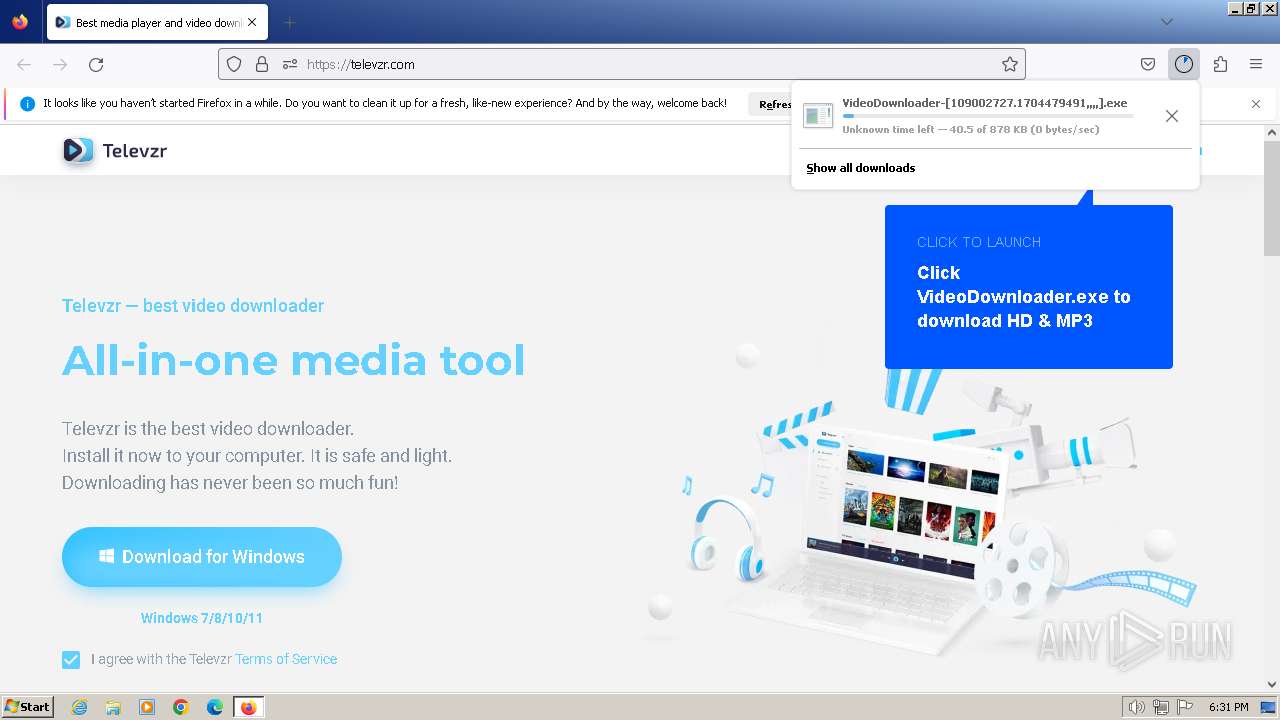
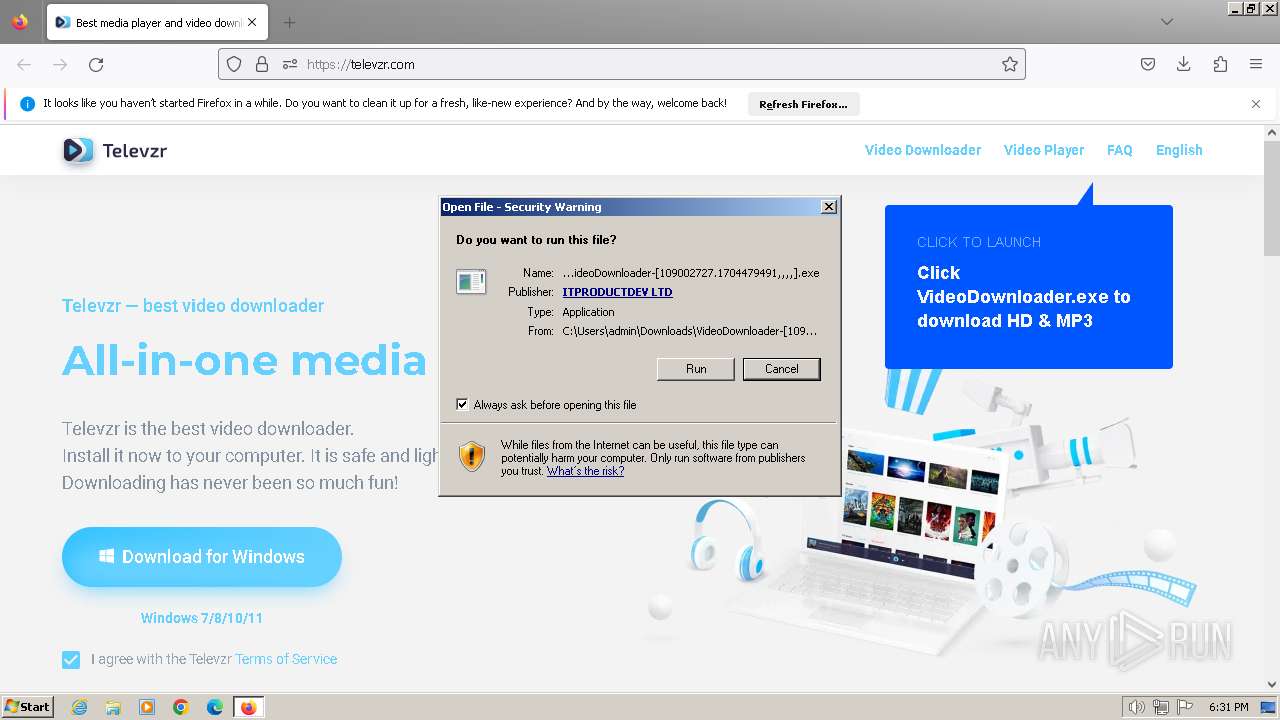
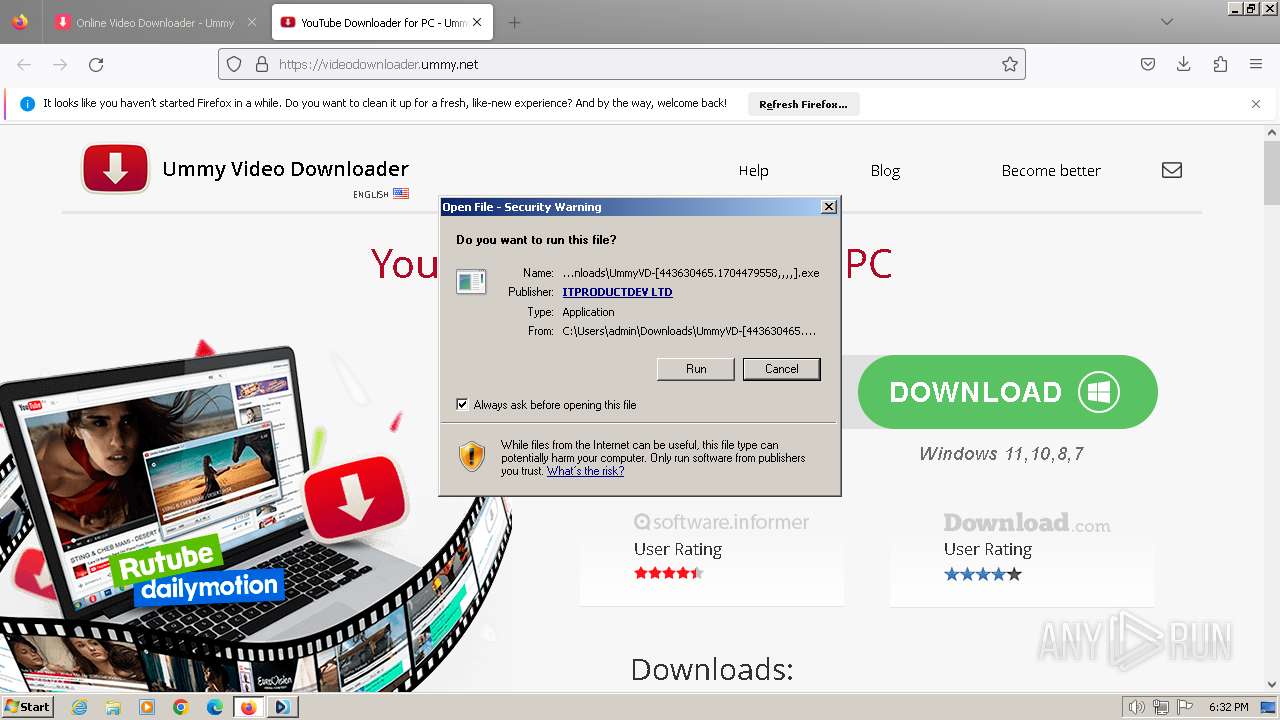
Starts application with an unusual extension
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- cmd.exe (PID: 3008)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- cmd.exe (PID: 3528)
Starts CMD.EXE for commands execution
- ns21FD.tmp (PID: 2460)
- ns2FD9.tmp (PID: 3252)
- ns218B.tmp (PID: 3652)
- ns3060.tmp (PID: 2260)
The process creates files with name similar to system file names
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
Get information on the list of running processes
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- ns2FD9.tmp (PID: 3252)
- cmd.exe (PID: 3308)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- ns3060.tmp (PID: 2260)
- cmd.exe (PID: 2796)
Reads the Internet Settings
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- Televzr.exe (PID: 3460)
- Ummy.exe (PID: 2108)
- Televzr.exe (PID: 3916)
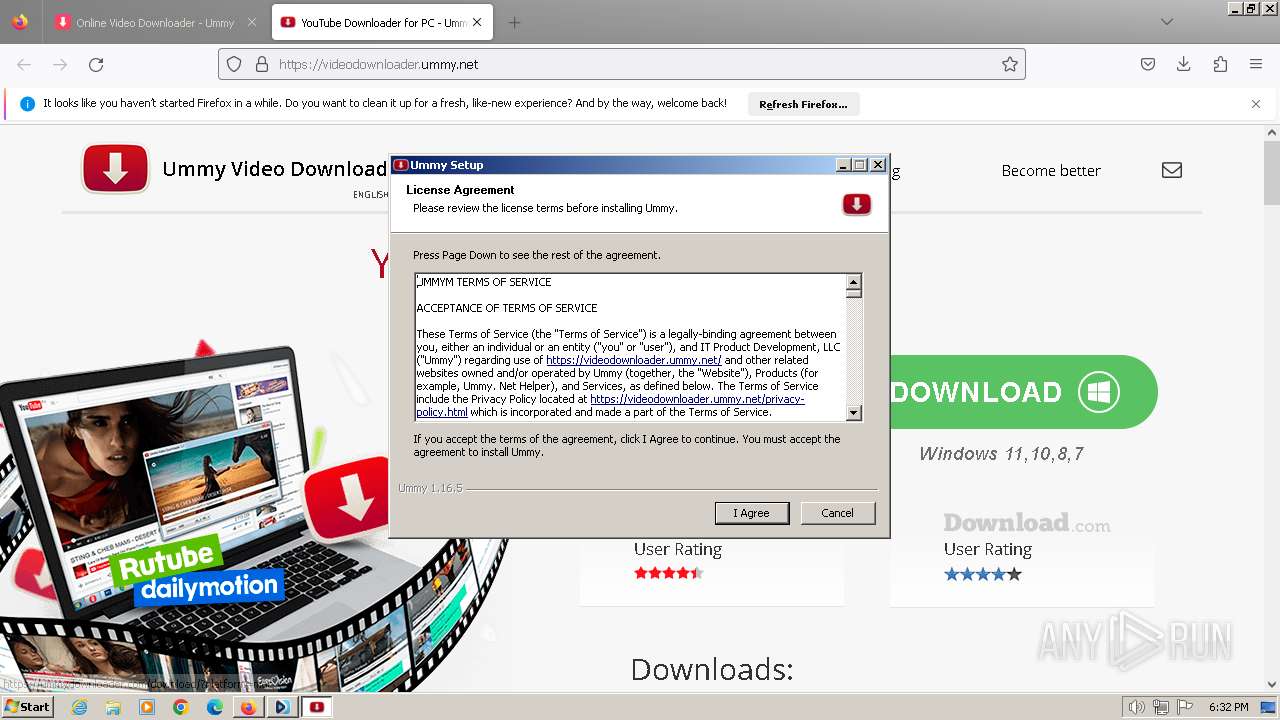
Checks Windows Trust Settings
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- Setup.exe (PID: 2876)
- msiexec.exe (PID: 2884)
- Setup.exe (PID: 2644)
Reads security settings of Internet Explorer
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- Setup.exe (PID: 2876)
- Setup.exe (PID: 2644)
Reads settings of System Certificates
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- Setup.exe (PID: 2876)
- Televzr.exe (PID: 3460)
- Setup.exe (PID: 2644)
- Ummy.exe (PID: 2108)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2884)
- msiexec.exe (PID: 2888)
Uses REG/REGEDIT.EXE to modify registry
- Televzr.exe (PID: 3460)
- Ummy.exe (PID: 2108)
INFO
The process uses the downloaded file
- firefox.exe (PID: 1072)
- cmd.exe (PID: 3008)
- cmd.exe (PID: 3528)
- Ummy.exe (PID: 2108)
Reads the computer name
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- vcredist_x86.exe (PID: 2436)
- Setup.exe (PID: 2876)
- msiexec.exe (PID: 2884)
- Televzr.exe (PID: 3460)
- Televzr.exe (PID: 3040)
- Televzr.exe (PID: 3388)
- Televzr.exe (PID: 332)
- Televzr.exe (PID: 2448)
- Televzr.exe (PID: 3916)
- wmpnscfg.exe (PID: 3896)
- Televzr.exe (PID: 992)
- Televzr.exe (PID: 3856)
- Televzr.exe (PID: 4028)
- vcredist_x86.exe (PID: 4064)
- Setup.exe (PID: 2644)
- msiexec.exe (PID: 2888)
- Ummy.exe (PID: 2108)
- Ummy.exe (PID: 3544)
- Ummy.exe (PID: 3628)
- Ummy.exe (PID: 3148)
Create files in a temporary directory
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- Setup.exe (PID: 2876)
- msiexec.exe (PID: 2884)
- Televzr.exe (PID: 3460)
- Setup.exe (PID: 2644)
- msiexec.exe (PID: 2888)
- Ummy.exe (PID: 2108)
Application launched itself
- firefox.exe (PID: 1072)
- firefox.exe (PID: 116)
- Televzr.exe (PID: 3460)
- Televzr.exe (PID: 1892)
- Televzr.exe (PID: 3916)
- Ummy.exe (PID: 2108)
Drops the executable file immediately after the start
- firefox.exe (PID: 1072)
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- vcredist_x86.exe (PID: 2436)
- msiexec.exe (PID: 2884)
- vcredist_x86.exe (PID: 4064)
Checks supported languages
- more.com (PID: 1628)
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- ns21FD.tmp (PID: 2460)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- ns218B.tmp (PID: 3652)
- ns2FD9.tmp (PID: 3252)
- more.com (PID: 3520)
- ns3060.tmp (PID: 2260)
- vcredist_x86.exe (PID: 2436)
- Setup.exe (PID: 2876)
- msiexec.exe (PID: 2884)
- Televzr.exe (PID: 3460)
- Televzr.exe (PID: 3388)
- Televzr.exe (PID: 1104)
- Televzr.exe (PID: 332)
- Televzr.exe (PID: 2644)
- Televzr.exe (PID: 2448)
- Televzr.exe (PID: 3916)
- Televzr.exe (PID: 992)
- wmpnscfg.exe (PID: 3896)
- Televzr.exe (PID: 4028)
- vcredist_x86.exe (PID: 4064)
- Televzr.exe (PID: 3856)
- Setup.exe (PID: 2644)
- msiexec.exe (PID: 2888)
- Ummy.exe (PID: 2108)
- Ummy.exe (PID: 3544)
- Ummy.exe (PID: 3628)
- Ummy.exe (PID: 2568)
- Televzr.exe (PID: 3040)
- Ummy.exe (PID: 3148)
- Ummy.exe (PID: 3652)
- Televzr.exe (PID: 1892)
Reads the machine GUID from the registry
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- Setup.exe (PID: 2876)
- msiexec.exe (PID: 2884)
- Televzr.exe (PID: 3460)
- vcredist_x86.exe (PID: 2436)
- vcredist_x86.exe (PID: 4064)
- msiexec.exe (PID: 2888)
- Setup.exe (PID: 2644)
- Ummy.exe (PID: 2108)
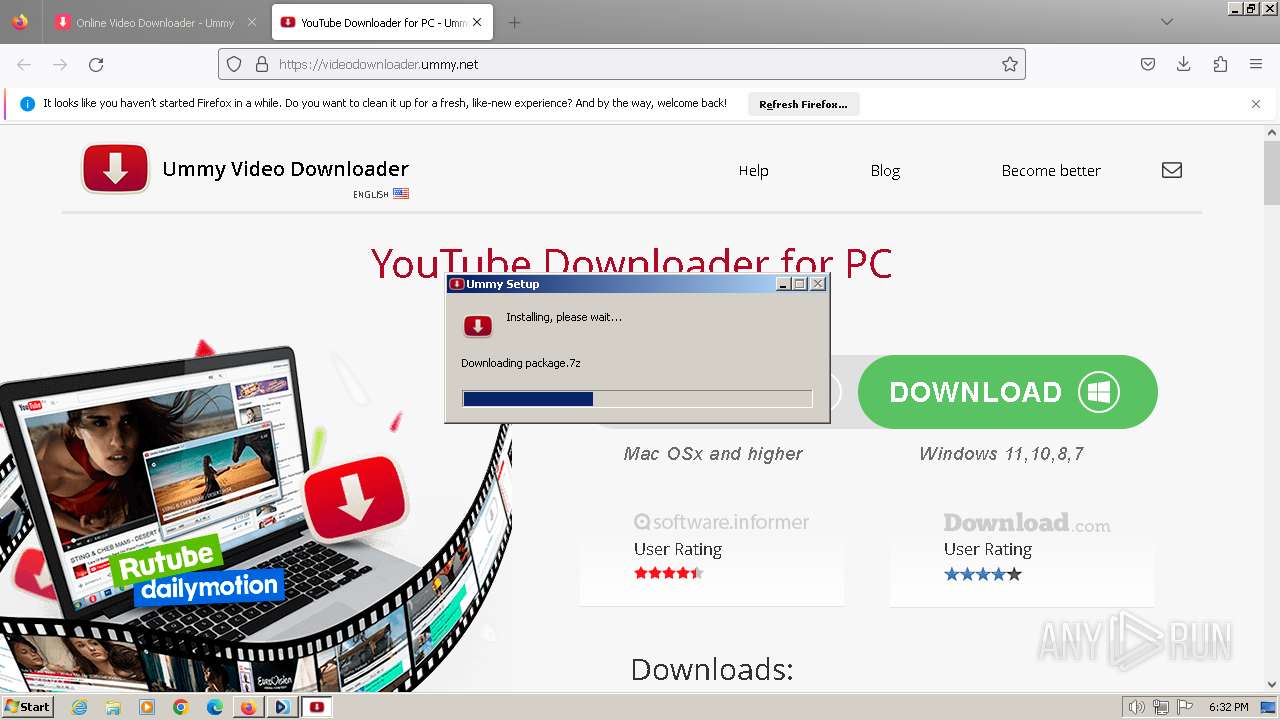
Drops 7-zip archiver for unpacking
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
Checks proxy server information
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
Malware-specific behavior (creating "System.dll" in Temp)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
Creates files or folders in the user directory
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- Televzr.exe (PID: 3460)
- Televzr.exe (PID: 3388)
- Televzr.exe (PID: 3916)
- Televzr.exe (PID: 1104)
- Ummy.exe (PID: 3628)
- Ummy.exe (PID: 3652)
- Ummy.exe (PID: 2108)
Reads Environment values
- vcredist_x86.exe (PID: 2436)
- Televzr.exe (PID: 3460)
- Televzr.exe (PID: 3916)
- vcredist_x86.exe (PID: 4064)
- Ummy.exe (PID: 2108)
Process drops legitimate windows executable
- vcredist_x86.exe (PID: 2436)
- msiexec.exe (PID: 2884)
- VideoDownloader-[109002727.1704479491,,,,].exe (PID: 3196)
- UmmyVD-[443630465.1704479558,,,,].exe (PID: 188)
- vcredist_x86.exe (PID: 4064)
Reads CPU info
- Setup.exe (PID: 2876)
- Setup.exe (PID: 2644)
Creates a software uninstall entry
- msiexec.exe (PID: 2884)
- msiexec.exe (PID: 2888)
Manual execution by a user
- Televzr.exe (PID: 3460)
- wmpnscfg.exe (PID: 3896)
- Ummy.exe (PID: 2108)
Reads product name
- Televzr.exe (PID: 3460)
- Televzr.exe (PID: 3916)
- Ummy.exe (PID: 2108)
Process checks computer location settings
- Televzr.exe (PID: 2644)
- Televzr.exe (PID: 3460)
- Televzr.exe (PID: 1104)
- Ummy.exe (PID: 2568)
- Ummy.exe (PID: 2108)
- Ummy.exe (PID: 3652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
211
Monitored processes
110
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://televzr.com" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 124 | C:\Windows\system32\reg.exe QUERY HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\\UserChoice /v ProgId | C:\Windows\System32\reg.exe | — | Televzr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 188 | "C:\Users\admin\Downloads\UmmyVD-[443630465.1704479558,,,,].exe" | C:\Users\admin\Downloads\UmmyVD-[443630465.1704479558,,,,].exe | firefox.exe | ||||||||||||
User: admin Company: ITPRODUCTDEV LTD Integrity Level: MEDIUM Description: Ummy Desktop Exit code: 0 Version: 1.16.5 Modules
| |||||||||||||||
| 240 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1072.6.320431118\131886723" -childID 5 -isForBrowser -prefsHandle 4148 -prefMapHandle 4144 -prefsLen 29209 -prefMapSize 244195 -jsInitHandle 916 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {49bf8f46-f9a6-4bdb-9607-8ef41fd69381} 1072 "\\.\pipe\gecko-crash-server-pipe.1072" 4232 19310b20 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 268 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1072.0.527385228\2077348706" -parentBuildID 20230710165010 -prefsHandle 1112 -prefMapHandle 1104 -prefsLen 28523 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {42944129-1829-458d-89b5-24877b0116f5} 1072 "\\.\pipe\gecko-crash-server-pipe.1072" 1196 d5a96c0 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 332 | "C:\Users\admin\AppData\Local\televzr\Televzr.exe" --type=gpu-process --field-trial-handle=1108,10399519207014745819,11261793735869269454,131072 --disable-features=CookiesWithoutSameSiteMustBeSecure,HardwareMediaKeyHandling,SameSiteByDefaultCookies,SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand --no-sandbox --user-data-dir="C:\Users\admin\AppData\Roaming\Televzr Desktop" --gpu-preferences=UAAAAAAAAADgAAAQAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHgAAAAAAAAAeAAAAAAAAAAoAAAABAAAACAAAAAAAAAAKAAAAAAAAAAwAAAAAAAAADgAAAAAAAAAEAAAAAAAAAAAAAAADQAAABAAAAAAAAAAAQAAAA0AAAAQAAAAAAAAAAQAAAANAAAAEAAAAAAAAAAHAAAADQAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1116 /prefetch:2 | C:\Users\admin\AppData\Local\televzr\Televzr.exe | — | Televzr.exe | |||||||||||
User: admin Company: ITPRODUCTDEV LTD Integrity Level: MEDIUM Description: Televzr Exit code: 0 Version: 1.16.7 Modules
| |||||||||||||||
| 560 | C:\Windows\system32\reg.exe ADD HKCU\Software\Classes\televzr\shell\open /ve /t REG_SZ /d "Open with Televzr" /f | C:\Windows\System32\reg.exe | — | Televzr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1072.10.2057494387\345565909" -childID 9 -isForBrowser -prefsHandle 3368 -prefMapHandle 3372 -prefsLen 31722 -prefMapSize 244195 -jsInitHandle 916 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {9aa812a5-3a76-419b-8673-059d98999c68} 1072 "\\.\pipe\gecko-crash-server-pipe.1072" 3380 1d34f560 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 748 | C:\Windows\system32\reg.exe ADD HKCU\Software\Classes\.avi\OpenWithProgids /v ummy /t REG_SZ /d "" /f | C:\Windows\System32\reg.exe | — | Ummy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | C:\Windows\system32\reg.exe QUERY HKCU\Software\Classes\ /ve | C:\Windows\System32\reg.exe | — | Ummy.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
70 840
Read events
70 076
Write events
690
Delete events
74
Modification events
| (PID) Process: | (116) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 2166C0A101000000 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 044CC1A101000000 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
| (PID) Process: | (1072) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|AppLastRunTime |
Value: D14E5F3C23B0D901 | |||
Executable files
138
Suspicious files
546
Text files
255
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:B7A3C61D0C144CC5E166B1E769CA8F8C | SHA256:7FADCB77FFACA6B9E9F15C6F1CD3AAD4C20DCD90FA92429A627A3A7110CA2644 | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:60E0DE9E05EC76C749D80F0D15A81B21 | SHA256:08252FA62CCCCD316474E20CC7317A6B5C932B2C972234318E8CCDA39EC2EF48 | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\protections.sqlite-journal | binary | |
MD5:AB72C94446FC9802450B0C67C2C20E63 | SHA256:EE6F20666E1F0726C85A42E60A553CD0C460762CEDD0A73A3B0029F5E10E908E | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cert9.db | binary | |
MD5:C2232CED566FB72063D8AFDE6B2299C6 | SHA256:6A060EE1C359ED0D0CB4F99947986611DD0ADB962AD425584612C56335982C76 | |||
| 1072 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage.sqlite-journal | binary | |
MD5:768B271B8B4D699413ABE75968E19F1E | SHA256:3145686B540C34F1A8FDC2BF9C102A32AB56175929E7480134E4706E2F9D1300 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
189
DNS requests
253
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1072 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
1072 | firefox.exe | POST | 200 | 18.238.246.206:80 | http://ocsp.r2m02.amazontrust.com/ | unknown | binary | 471 b | unknown |
1072 | firefox.exe | POST | 200 | 95.101.54.203:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
1072 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
1072 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
1072 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 471 b | unknown |
1072 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 471 b | unknown |
1072 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
1072 | firefox.exe | POST | 200 | 95.101.54.203:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
1072 | firefox.exe | POST | — | 95.101.54.203:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1072 | firefox.exe | 104.21.63.211:443 | televzr.com | — | — | unknown |
1072 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
1072 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
1072 | firefox.exe | 54.83.112.81:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
1072 | firefox.exe | 95.101.54.203:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
1072 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | unknown |
1072 | firefox.exe | 142.250.186.138:443 | fonts.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
televzr.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| shared |
proxyserverecs-1736642167.us-east-1.elb.amazonaws.com |
| shared |
r3.o.lencr.org |
| shared |
firefox.settings.services.mozilla.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Setup.exe | The operation completed successfully.
|
Setup.exe | The operation completed successfully.
|