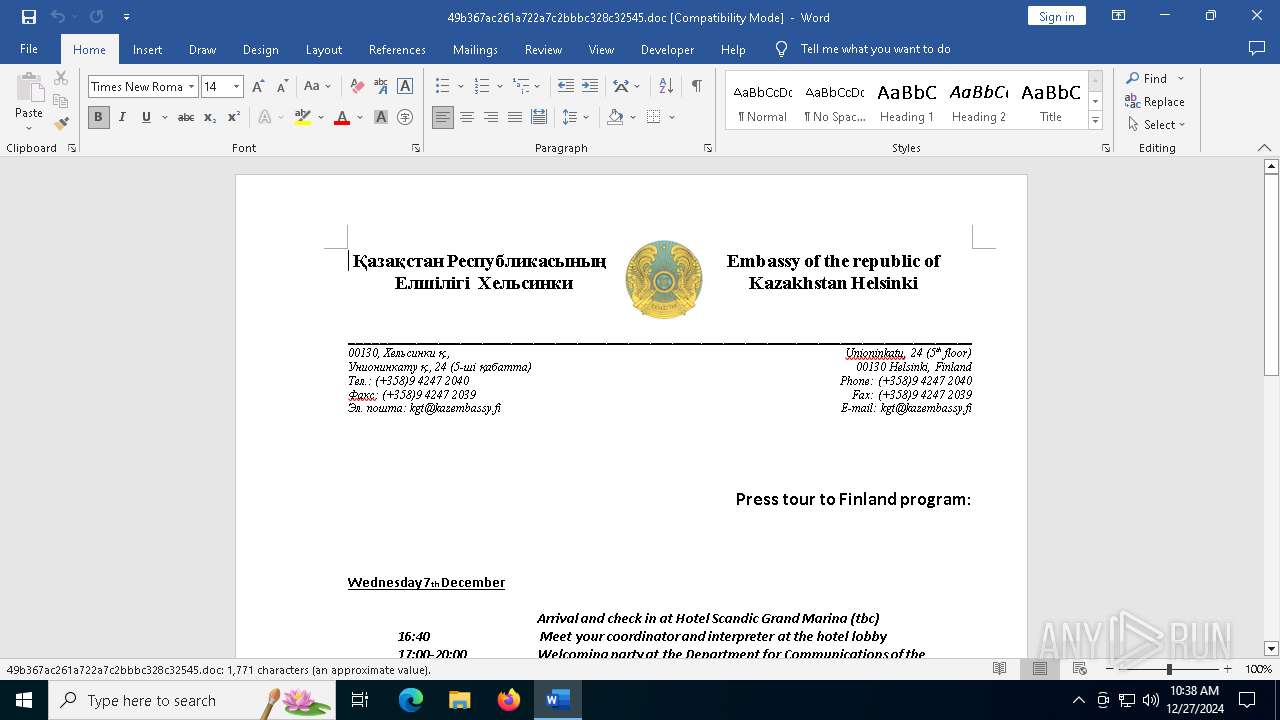
| File name: | 49b367ac261a722a7c2bbbc328c32545 |
| Full analysis: | https://app.any.run/tasks/b546e669-019e-43f3-86e2-62251b30397e |
| Verdict: | Malicious activity |
| Analysis date: | December 27, 2024, 10:38:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: user, Template: Normal.dotm, Last Saved By: John, Revision Number: 11, Name of Creating Application: Microsoft Office Word, Total Editing Time: 08:00, Create Time/Date: Fri Nov 25 19:04:00 2016, Last Saved Time/Date: Fri Nov 25 20:04:00 2016, Number of Pages: 1, Number of Words: 320, Number of Characters: 1828, Security: 0 |
| MD5: | 49B367AC261A722A7C2BBBC328C32545 |
| SHA1: | 5BD2E2B8DDC65931704C8C3EA57ADC2BB778F66A |
| SHA256: | FF2C8CADAA0FD8DA6138CCE6FCE37E001F53A5D9CECCD67945B15AE273F4D751 |
| SSDEEP: | 6144:1iuv7iu2oErXZ+e7m5OPoeKAUXso/UUsAJtfiZA:1N7iu2oaXYOrWjdfi6 |
MALICIOUS
Checks whether a specified folder exists (SCRIPT)
- WINWORD.EXE (PID: 640)
- wscript.exe (PID: 4512)
Unusual execution from MS Office
- WINWORD.EXE (PID: 640)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 4512)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- WINWORD.EXE (PID: 640)
- wscript.exe (PID: 4512)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 640)
The process executes JS scripts
- WINWORD.EXE (PID: 640)
Accesses command line arguments (SCRIPT)
- wscript.exe (PID: 4512)
Gets name of the script (SCRIPT)
- wscript.exe (PID: 4512)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 4512)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 4512)
INFO
Drops encrypted VBS script (Microsoft Script Encoder)
- WINWORD.EXE (PID: 640)
The process uses the downloaded file
- WINWORD.EXE (PID: 640)
Sends debugging messages
- WINWORD.EXE (PID: 640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | user |
| Keywords: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | John |
| Software: | Microsoft Office Word |
| CreateDate: | 2016:11:25 19:04:00 |
| ModifyDate: | 2016:11:25 20:04:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Olymp |
| CharCountWithSpaces: | 2144 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 11 |
| TotalEditTime: | 8 minutes |
| Words: | 320 |
| Characters: | 1828 |
| Pages: | 1 |
| Paragraphs: | 4 |
| Lines: | 15 |
Total processes
124
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\49b367ac261a722a7c2bbbc328c32545.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4264 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "B8340C59-5341-4BBE-958F-B8AA91036523" "ACA9544D-43D4-47B6-B9A6-7CA7CEDEFD08" "640" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 4512 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\maintools.js" EzZETcSXyKAdF_e5I2i1 | C:\Windows\System32\wscript.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
15 096
Read events
14 705
Write events
360
Delete events
31
Modification events
| (PID) Process: | (640) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (640) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\640 |
| Operation: | write | Name: | 0 |
Value: 0B0E10ABCC32E1E2F2F44E9B4BC81E30EF86A7230046DEBEAC93B789D6ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118005D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (640) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (640) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (640) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (640) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (640) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (640) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (640) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (640) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
4
Suspicious files
114
Text files
47
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\maintools.js | text | |
MD5:5EA3FD094B69E9E00894842F95FD5D85 | SHA256:3A065547ADB0AFC63E318C2FA1F682108664E602934490A898C3DE1B23975628 | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:BA90DE4EBF35F9716A843F305E19BE2A | SHA256:59FE1439564359B60AAD021332C4B25969A636926136E9E6B1F63A935C0D9849 | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\E0CDAE86.emf | emf | |
MD5:EB10732AA3F3BB122DC9452917A62FA1 | SHA256:750987BD6026CC8C515D0B6D65FFBE5BCBF7824EE56E82128D220EEF86390874 | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:219F7908DB2272A34375B15E3603AAD2 | SHA256:2FFA911BB7F8AB45E5E12E6B41A26BB46A46542FB12BADC90414A7D9242990F8 | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\8BD9A3FD-2977-457F-87A9-F09A464A9260 | xml | |
MD5:C0CADAE28702AB3BEF0D523CA05A266D | SHA256:7C6C062C45E56ADBB0E9A9BDE6643F2D7B02A2AE7133329E9ECF817A2D13671B | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:38AEF5BF87A95AEEB91CBA39C26A6A8E | SHA256:D7A725EC89B2360733C932D55E02A1A95C470A5FCD2D08057FAD7501993B435B | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\691140CF.emf | emf | |
MD5:FDBBE99A5DD164B403945E6A98434CC1 | SHA256:D416447FB0A6AA8F66CB9C943B7FFDA365CE56D2AD8AC12AC0154EF8A52D1CA0 | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:C5F1A4006433181DAD01A40FCE0BB997 | SHA256:38D1E20527A9396CF07241A625B001664F2DA3EF7344258E0F2793B89066AC7A | |||
| 640 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 640 | WINWORD.EXE | C:\Users\admin\Desktop\~$b367ac261a722a7c2bbbc328c32545.doc | binary | |
MD5:B11676CE8840529E9563D3F627DEA687 | SHA256:19DA3D185A5B5E6B24AFC28E4C63C667520104550BF291E67FA6E45ACE7E70C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
71
TCP/UDP connections
83
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1684 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1684 | svchost.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.109.32.97:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 178 Kb | whitelisted |
— | — | GET | 200 | 23.48.23.42:443 | https://omex.cdn.office.net/addinclassifier/officesharedentities | unknown | text | 314 Kb | whitelisted |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/word/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=winword.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7bE132CCAB-F2E2-4EF4-9B4B-C81E30EF86A7%7d&LabMachine=false | unknown | tss | 398 Kb | whitelisted |
— | — | GET | 200 | 52.109.16.3:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=0&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7BE132CCAB-F2E2-4EF4-9B4B-C81E30EF86A7%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%2Cofjhlwlmoc1pz531%22%7D | unknown | text | 542 b | whitelisted |
— | — | GET | 200 | 2.21.20.154:443 | https://binaries.templates.cdn.office.net/support/templates/en-us/tp0309043402.cab | unknown | compressed | 706 Kb | whitelisted |
— | — | GET | 200 | 2.21.20.154:443 | https://binaries.templates.cdn.office.net/support/templates/en-us/tp02851226.cab | unknown | compressed | 34.6 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.21.110.146:443 | www.bing.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1684 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
640 | WINWORD.EXE | 52.109.89.18:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1684 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1684 | svchost.exe | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
640 | WINWORD.EXE | 23.48.23.18:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|