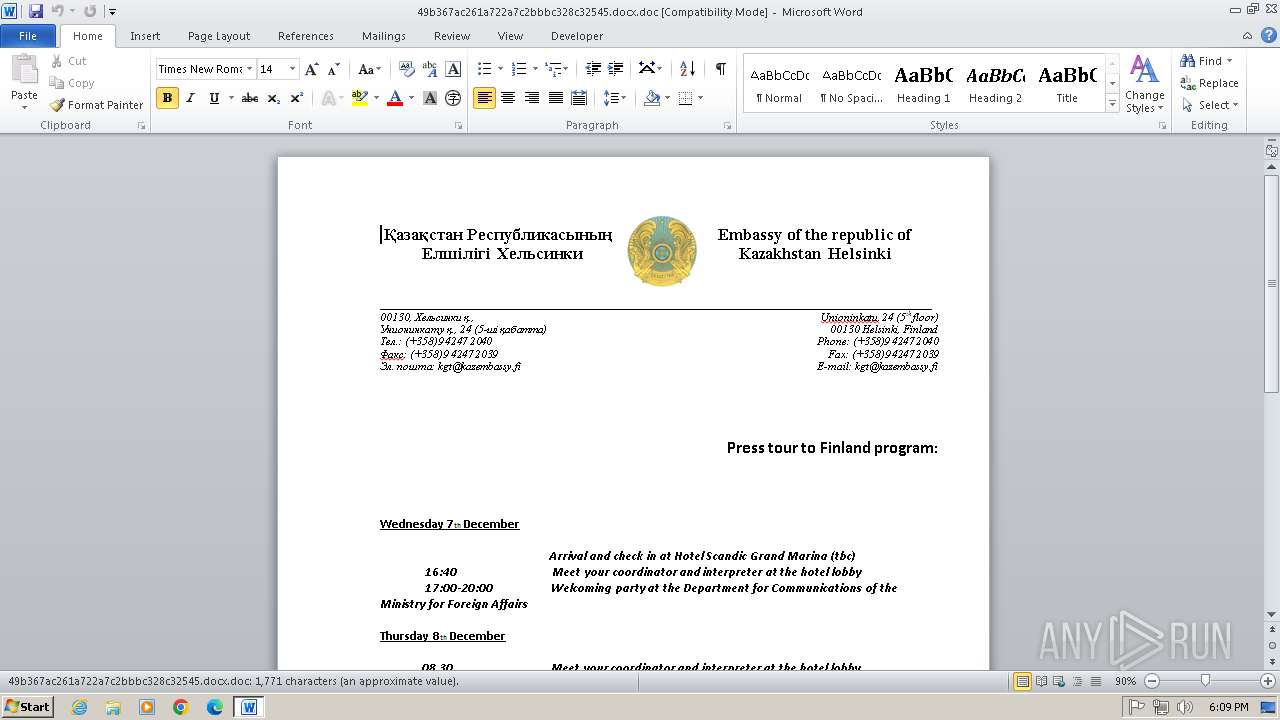
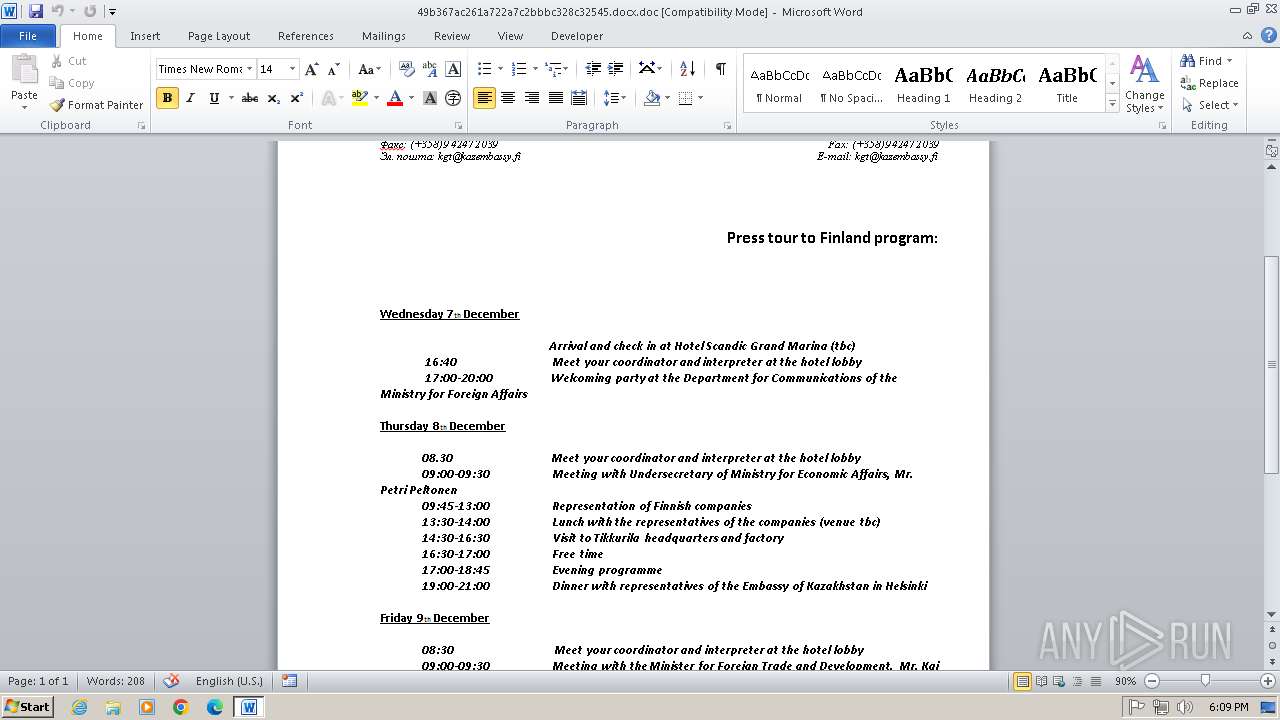
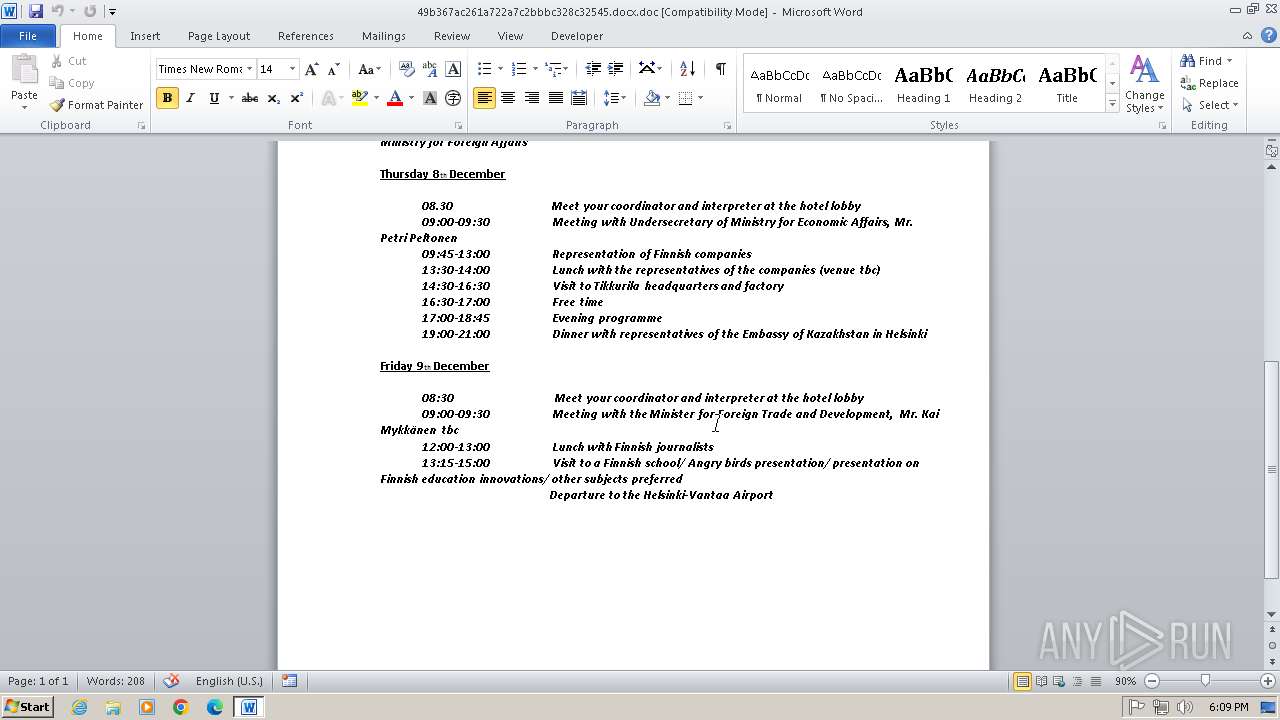
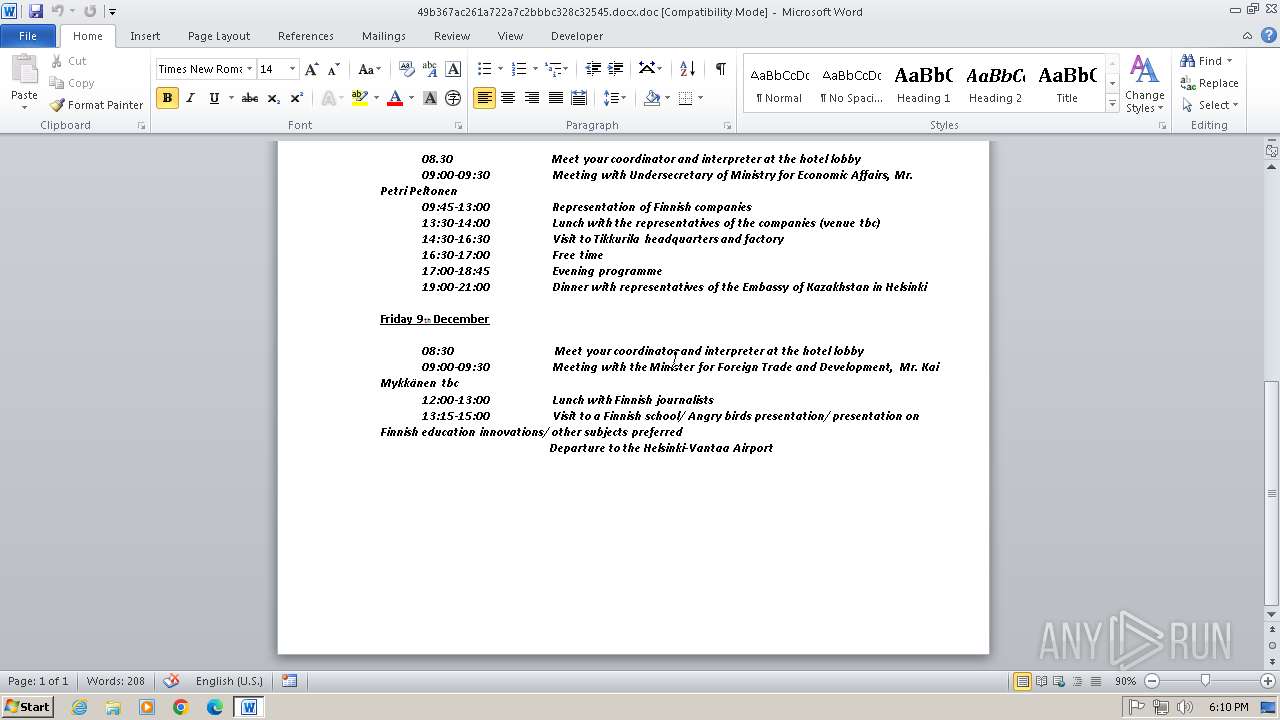
| File name: | 49b367ac261a722a7c2bbbc328c32545.docx |
| Full analysis: | https://app.any.run/tasks/9b24f4b7-0042-42c1-9a58-9d4c67f87948 |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2025, 17:09:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: user, Template: Normal.dotm, Last Saved By: John, Revision Number: 11, Name of Creating Application: Microsoft Office Word, Total Editing Time: 08:00, Create Time/Date: Fri Nov 25 19:04:00 2016, Last Saved Time/Date: Fri Nov 25 20:04:00 2016, Number of Pages: 1, Number of Words: 320, Number of Characters: 1828, Security: 0 |
| MD5: | 49B367AC261A722A7C2BBBC328C32545 |
| SHA1: | 5BD2E2B8DDC65931704C8C3EA57ADC2BB778F66A |
| SHA256: | FF2C8CADAA0FD8DA6138CCE6FCE37E001F53A5D9CECCD67945B15AE273F4D751 |
| SSDEEP: | 6144:1iuv7iu2oErXZ+e7m5OPoeKAUXso/UUsAJtfiZA:1N7iu2oaXYOrWjdfi6 |
MALICIOUS
GENERIC has been found (auto)
- WINWORD.EXE (PID: 2168)
Checks whether a specified folder exists (SCRIPT)
- WINWORD.EXE (PID: 2168)
- wscript.exe (PID: 2336)
Unusual execution from MS Office
- WINWORD.EXE (PID: 2168)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 2336)
SUSPICIOUS
The process executes JS scripts
- WINWORD.EXE (PID: 2168)
Creates FileSystem object to access computer's file system (SCRIPT)
- WINWORD.EXE (PID: 2168)
- wscript.exe (PID: 2336)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 2168)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 2336)
Accesses command line arguments (SCRIPT)
- wscript.exe (PID: 2336)
Gets name of the script (SCRIPT)
- wscript.exe (PID: 2336)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 2336)
There is functionality for taking screenshot (YARA)
- WINWORD.EXE (PID: 2168)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | user |
| Keywords: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | John |
| Software: | Microsoft Office Word |
| CreateDate: | 2016:11:25 19:04:00 |
| ModifyDate: | 2016:11:25 20:04:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Olymp |
| CharCountWithSpaces: | 2144 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 11 |
| TotalEditTime: | 8 minutes |
| Words: | 320 |
| Characters: | 1828 |
| Pages: | 1 |
| Paragraphs: | 4 |
| Lines: | 15 |
Total processes
35
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2168 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n C:\Users\admin\Desktop\49b367ac261a722a7c2bbbc328c32545.docx.doc | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2336 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\maintools.js" EzZETcSXyKAdF_e5I2i1 | C:\Windows\System32\wscript.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
8 085
Read events
7 185
Write events
586
Delete events
314
Modification events
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ~o? |
Value: 7E6F3F007808000002000000000000008E00000001000000500000003200000063003A005C00700072006F006700720061007E0031005C006D006900630072006F0073007E0031005C006F0066006600690063006500310034005C00670065006E006B006F002E0064006C006C0000006D006900630072006F0073006F0066007400200077006F00720064002000D0C6E0ACC0C9200094CD00AC200030AEA5B20000 | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | dl? |
Value: 646C3F0078080000010000000000000000000000 | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2168) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
Executable files
0
Suspicious files
6
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2054.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:0E006271C2D5BB8A4813CC5F01AD97E6 | SHA256:09A8574D1143CC5B568A1AE78390DE1A915E6B55E0CCE0FCDE73FE5281516498 | |||
| 2168 | WINWORD.EXE | C:\Users\admin\Desktop\~$b367ac261a722a7c2bbbc328c32545.docx.doc | binary | |
MD5:C225F79F8E42B5376978F90E9215C321 | SHA256:7CB7FB27876403F13F937D8D2AA475A24433B8FB077F9222CA0A5F97A867BDA9 | |||
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\49b367ac261a722a7c2bbbc328c32545.docx.doc.LNK | binary | |
MD5:4875E6A7870927F94B2AE28A1E62EF6A | SHA256:22443E8734CFE7078E978D31656E86C6F5F96FE19A148E53D0E5CA17D3F045E3 | |||
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\9DFBE04E.emf | binary | |
MD5:FDBBE99A5DD164B403945E6A98434CC1 | SHA256:D416447FB0A6AA8F66CB9C943B7FFDA365CE56D2AD8AC12AC0154EF8A52D1CA0 | |||
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\48C777F7.emf | binary | |
MD5:FDBBE99A5DD164B403945E6A98434CC1 | SHA256:D416447FB0A6AA8F66CB9C943B7FFDA365CE56D2AD8AC12AC0154EF8A52D1CA0 | |||
| 2336 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\maintools.js | text | |
MD5:5EA3FD094B69E9E00894842F95FD5D85 | SHA256:3A065547ADB0AFC63E318C2FA1F682108664E602934490A898C3DE1B23975628 | |||
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D14E1341.emf | binary | |
MD5:EB10732AA3F3BB122DC9452917A62FA1 | SHA256:750987BD6026CC8C515D0B6D65FFBE5BCBF7824EE56E82128D220EEF86390874 | |||
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\maintools.js | text | |
MD5:5EA3FD094B69E9E00894842F95FD5D85 | SHA256:3A065547ADB0AFC63E318C2FA1F682108664E602934490A898C3DE1B23975628 | |||
| 2168 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN0409.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
7
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2168 | WINWORD.EXE | POST | 302 | 95.100.186.9:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | unknown | — | — | whitelisted |
2168 | WINWORD.EXE | POST | 302 | 95.100.186.9:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | unknown | — | — | whitelisted |
2168 | WINWORD.EXE | POST | 302 | 95.100.186.9:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2168 | WINWORD.EXE | 95.100.186.9:80 | go.microsoft.com | AKAMAI-AS | FR | whitelisted |
2168 | WINWORD.EXE | 40.91.76.224:443 | activation.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |