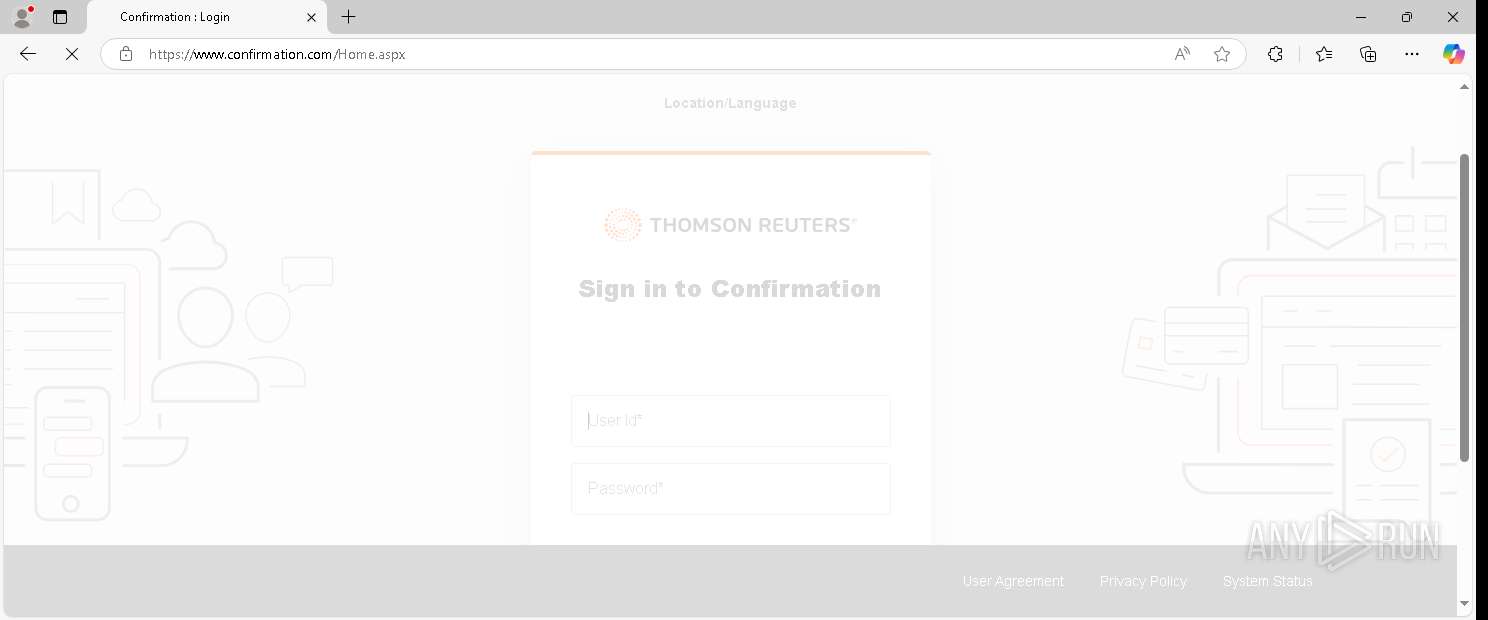
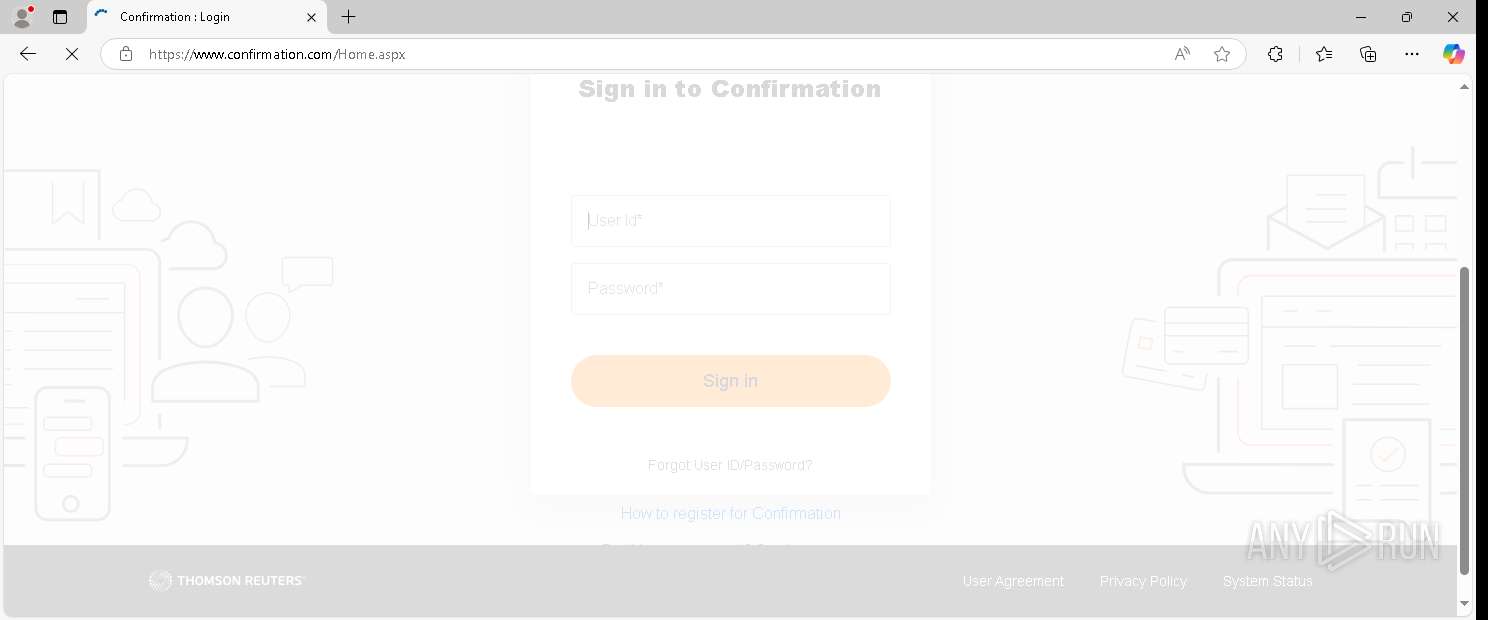
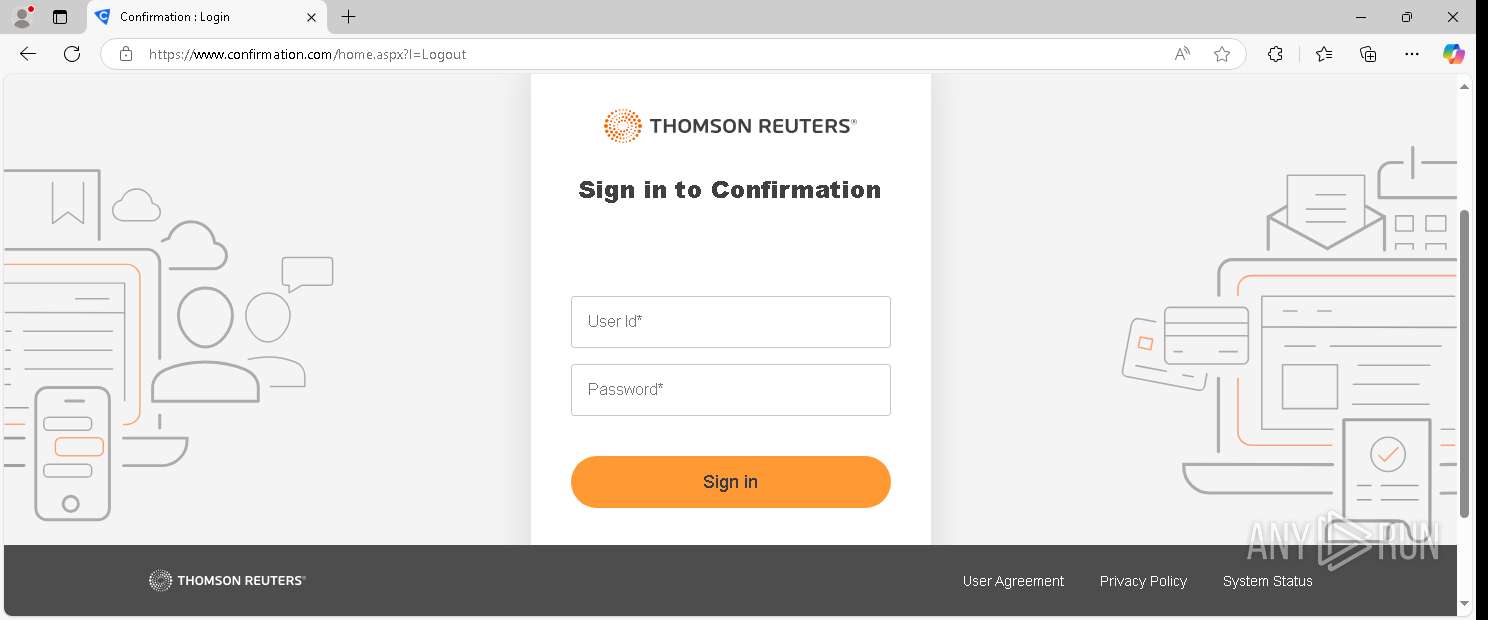
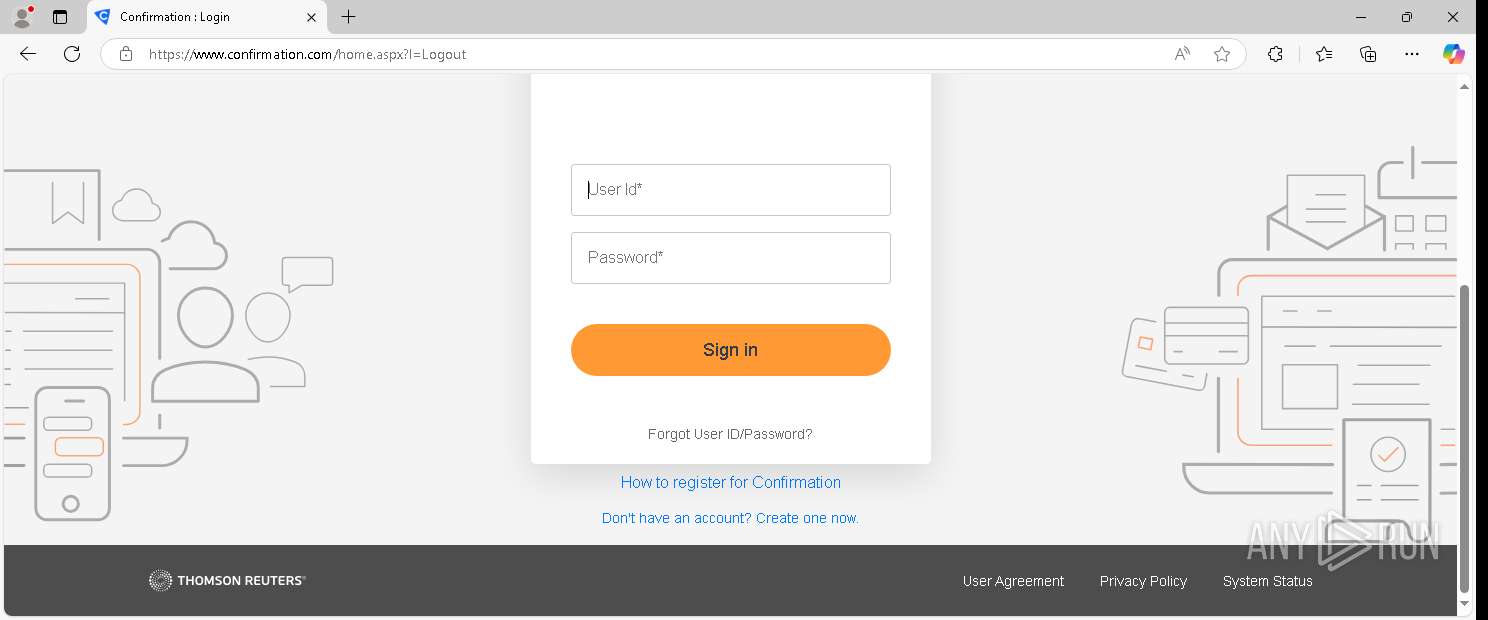
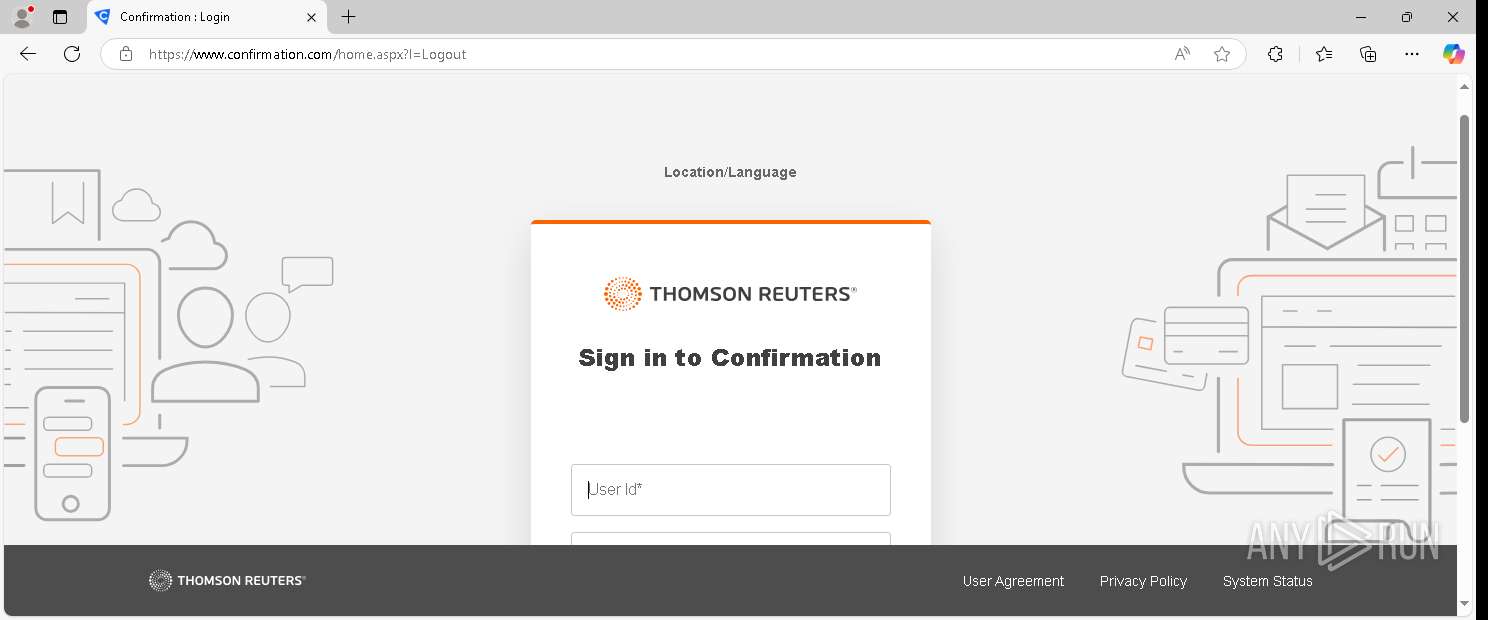
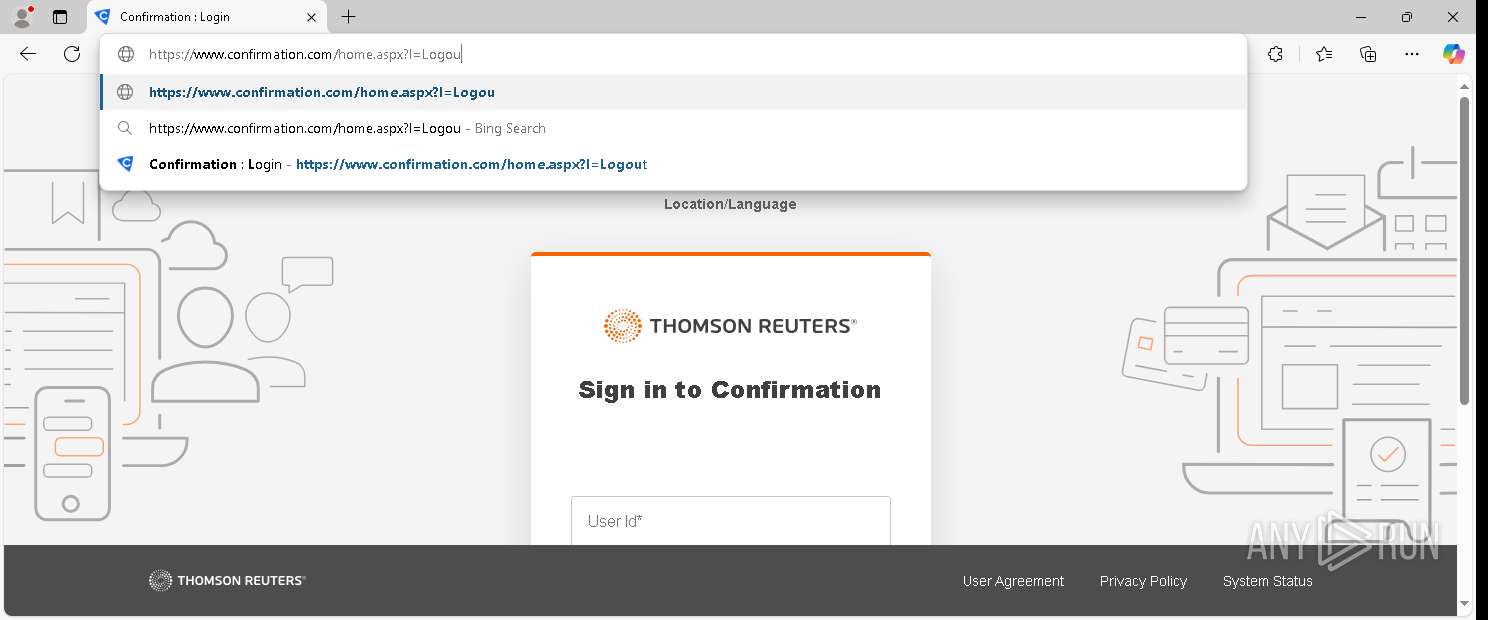
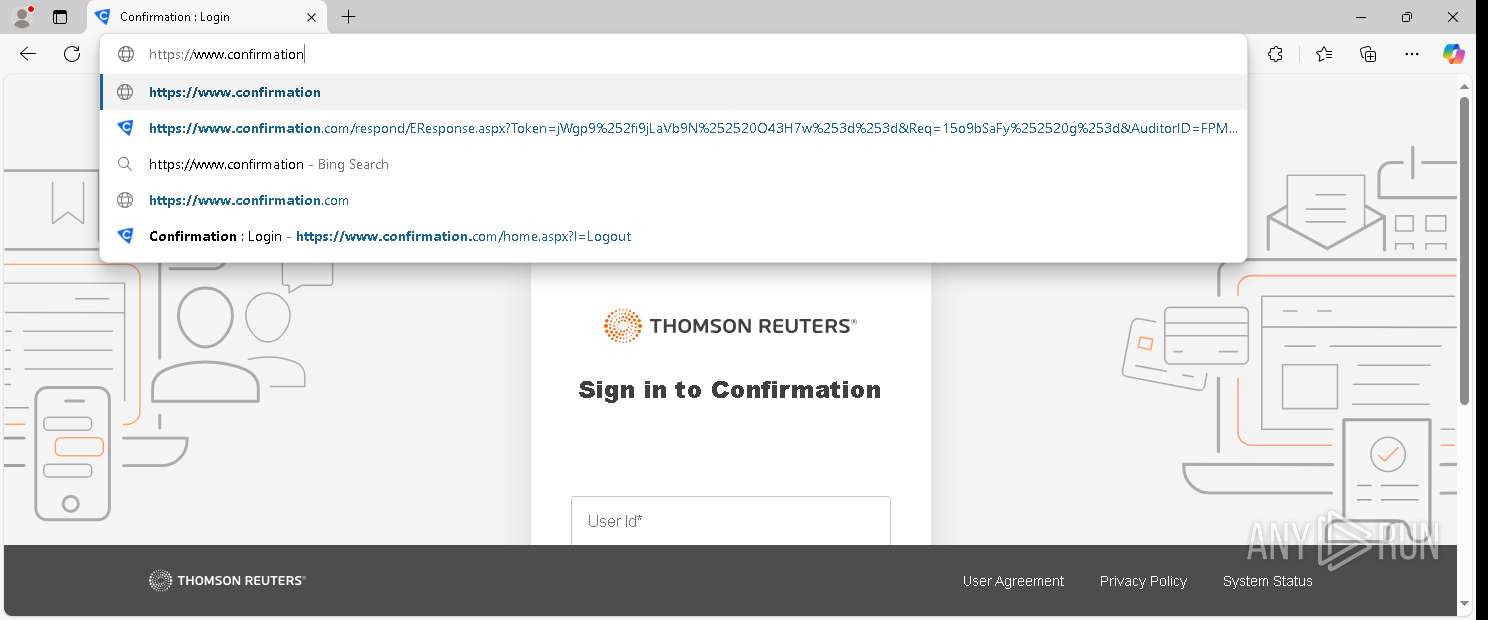
| URL: | https://www.confirmation.com/respond/EResponse.aspx?Token=jWgp9%252fi9jLaVb9N%252520O43H7w%253d%253d&Req=15o9bSaFy%252520g%253d&AuditorID=FPM1Sh7XUC8%253d |
| Full analysis: | https://app.any.run/tasks/2e8f50ea-f0b6-459a-b0e4-7c07849f858e |
| Verdict: | Malicious activity |
| Analysis date: | October 29, 2025, 15:45:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MD5: | 7305E2C1F2391030A3847CAD225A6BFE |
| SHA1: | 5C33D643C23AB950FC90FFF407C3D8893F3E7521 |
| SHA256: | FED9320D34C996EC1E53CDCBDEA4E3925298179C7BD5DB9381CA71FC1663BC5D |
| SSDEEP: | 3:N8DSL8LdIMyKTVH2xVuRCnA5RMjQ92x70H2EjxXbVeKXsOmwwmJG:2OLYI9KSuyAPMs89+2gLfsOmwQ |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
136
Monitored processes
0
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
143
TCP/UDP connections
68
DNS requests
47
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 104.102.63.189:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | — | — | — |
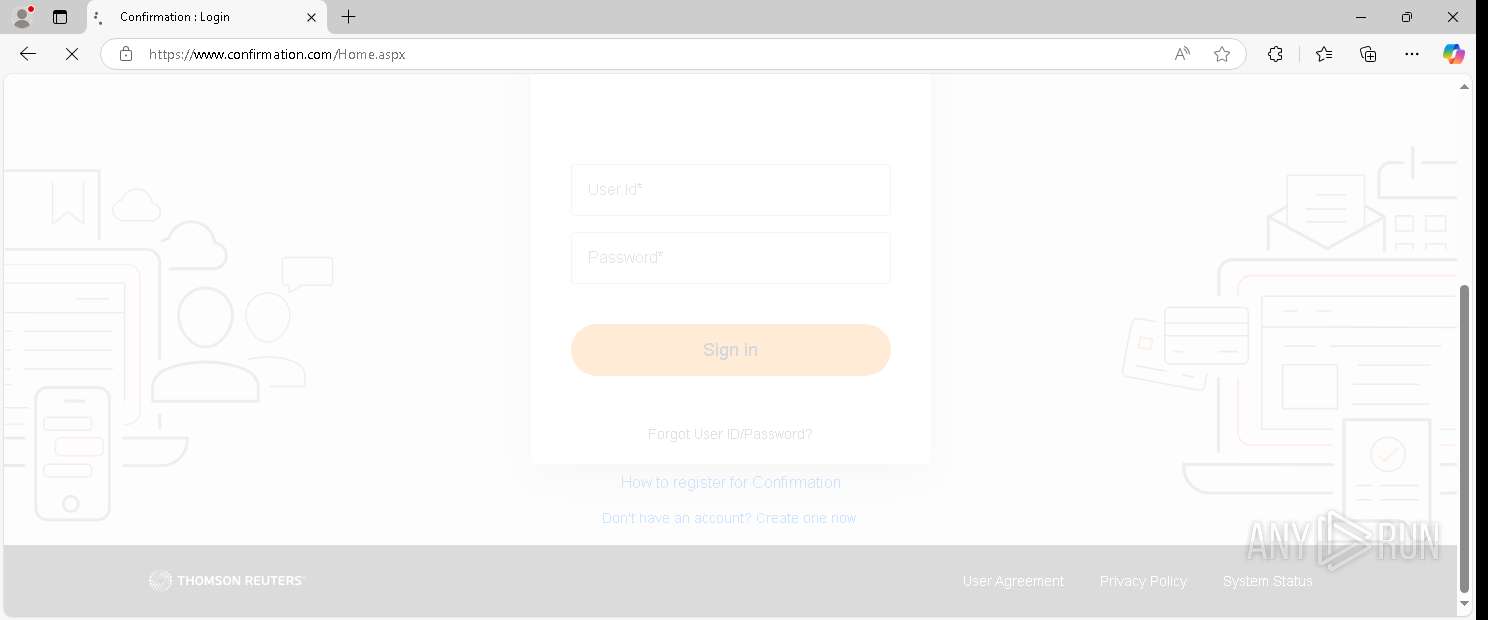
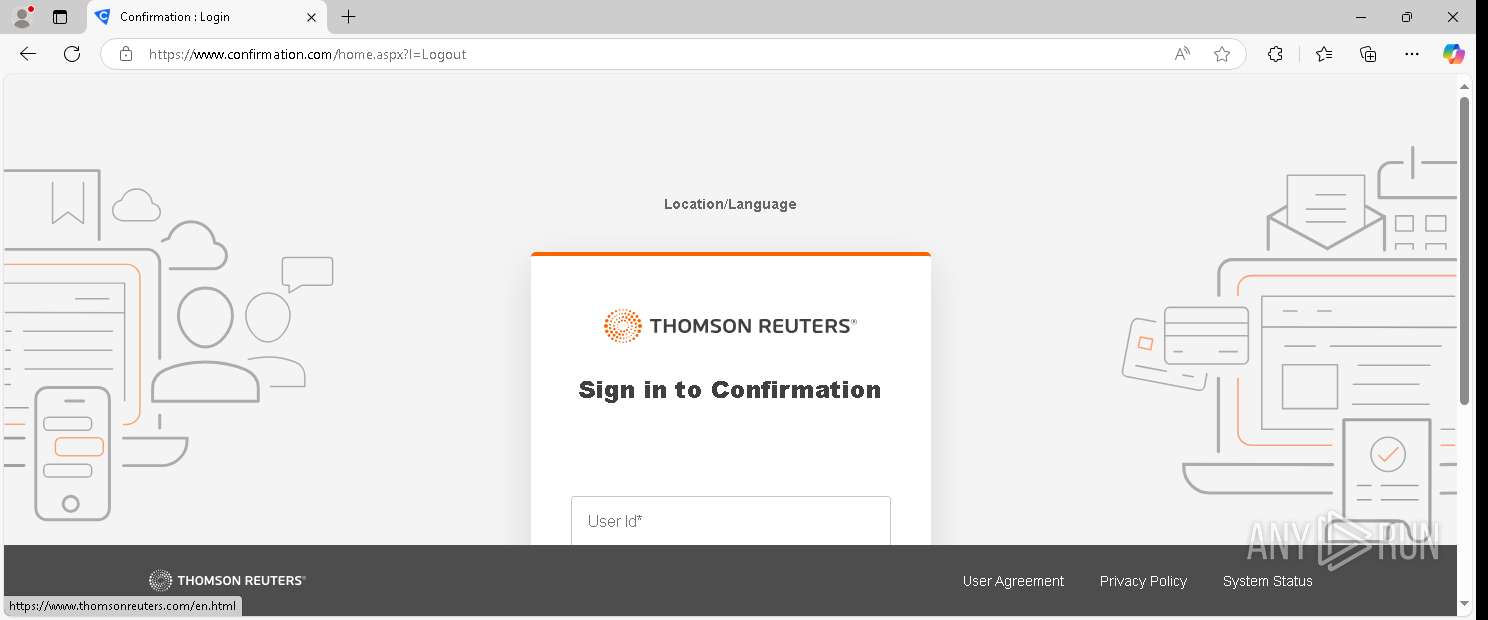
— | — | GET | 302 | 155.46.210.7:443 | https://www.confirmation.com/respond/EResponse.aspx?Token=jWgp9%252fi9jLaVb9N%252520O43H7w%253d%253d&Req=15o9bSaFy%252520g%253d&AuditorID=FPM1Sh7XUC8%253d | unknown | html | 145 b | — |
6888 | msedge.exe | GET | 403 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1753186353&P2=404&P3=2&P4=JctxgV%2fBzu58lG09sot5gGnCe%2fY1hwdAjsjhuzjzxTQ2YzQOHr%2fJXcKzV3SdbfHgQEdRSVQGHksTHkDx0nQLkQ%3d%3d | unknown | — | — | whitelisted |
— | — | POST | 200 | 150.171.28.11:443 | https://edge.microsoft.com/componentupdater/api/v1/update | unknown | text | 1.46 Kb | — |
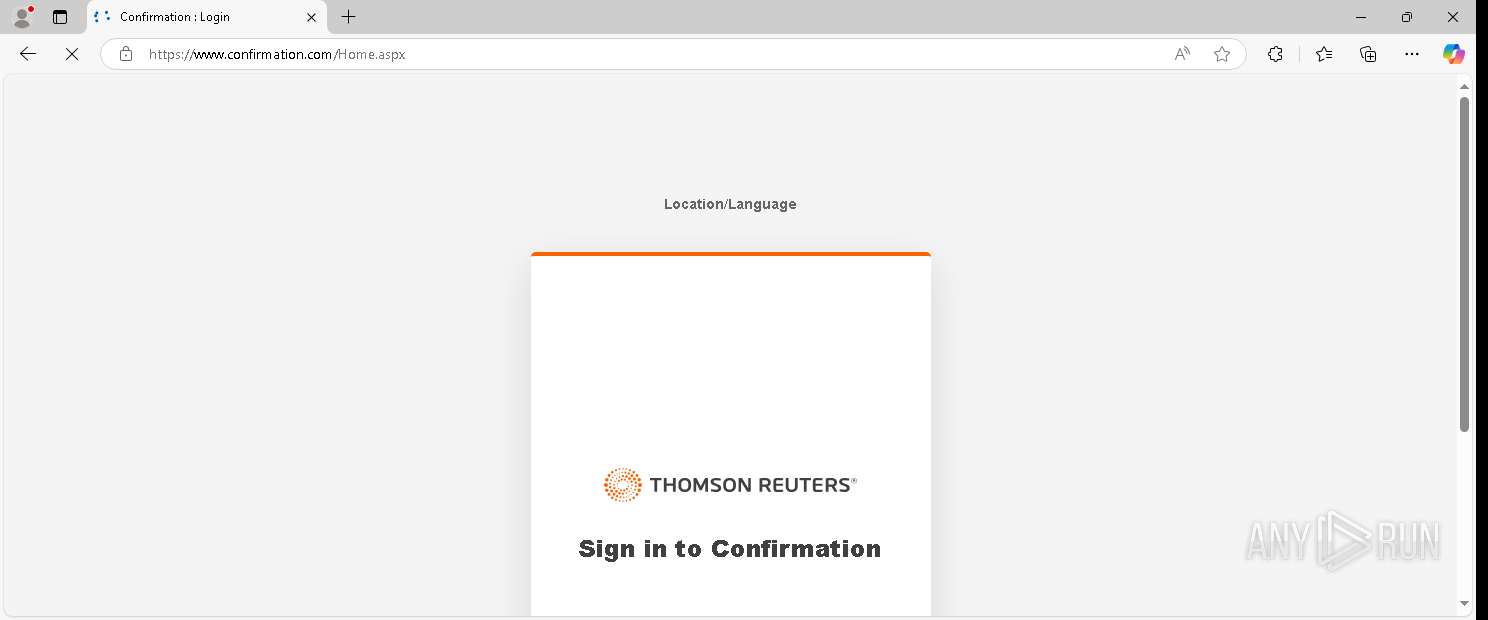
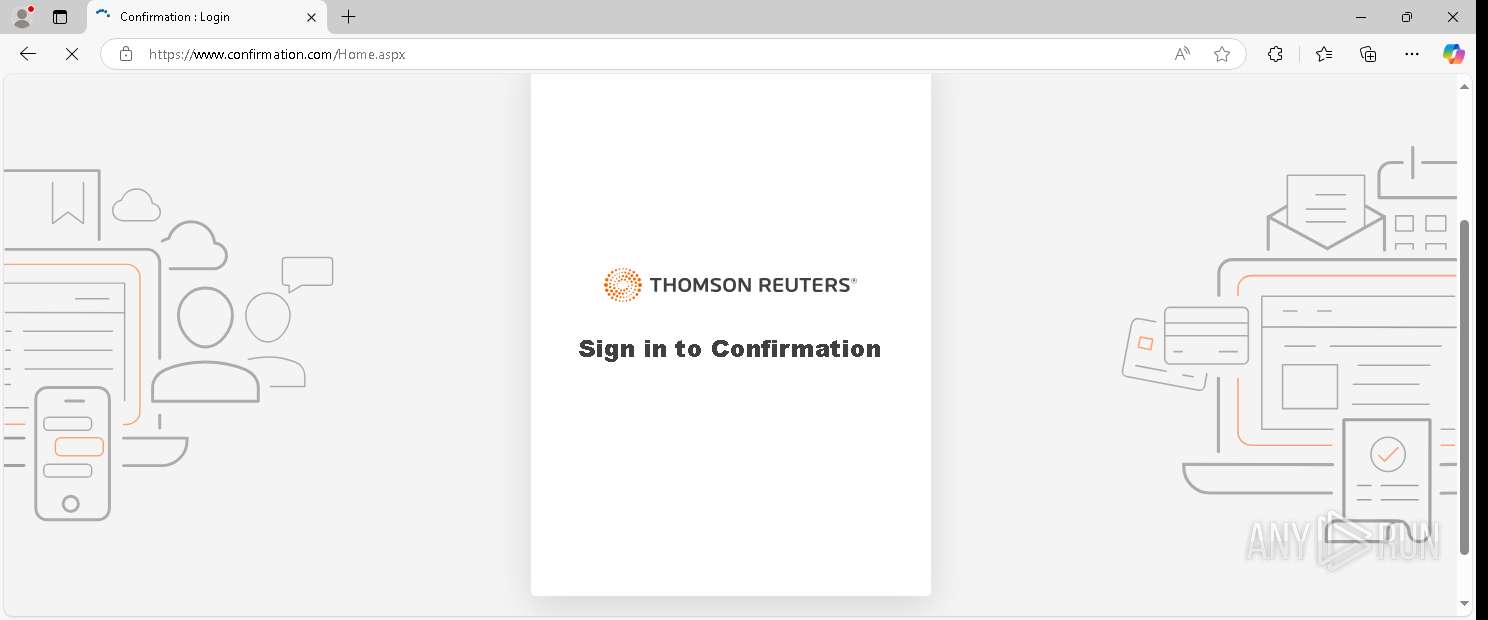
— | — | GET | 200 | 155.46.210.7:443 | https://www.confirmation.com/Home.aspx | unknown | — | — | — |
— | — | GET | 200 | 155.46.210.7:443 | https://www.confirmation.com/Marketing/content/fonts/font-styles.css | unknown | — | — | — |
— | — | GET | 200 | 155.46.210.7:443 | https://www.confirmation.com/Marketing/content/scripts/js.cookie.js | unknown | — | — | — |
— | — | GET | 200 | 2.16.204.156:443 | https://www.bing.com/bloomfilterfiles/ExpandedDomainsFilterGlobal.json | unknown | binary | 656 Kb | — |
6316 | RUXIMICS.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4252 | svchost.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4252 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6316 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6888 | msedge.exe | 199.232.214.172:80 | msedge.b.tlu.dl.delivery.mp.microsoft.com | FASTLY | US | whitelisted |
— | — | 224.0.0.251:5353 | — | — | — | whitelisted |
5008 | svchost.exe | 104.102.63.189:443 | fs.microsoft.com | AKAMAI-AS | US | whitelisted |
6888 | msedge.exe | 155.46.210.7:443 | www.confirmation.com | — | US | whitelisted |
6316 | RUXIMICS.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4252 | svchost.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6888 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
msedge.b.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
www.confirmation.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
app-data.gcs.trstatic.net |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
6888 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
6888 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Signs of phishing were detected in the page code |