| URL: | https://linkprotect.cudasvc.com/url?a=https%3a%2f%2fsecure.virtru.com%2fstart%2f%3fc%3dbarebones%26t%3dbarebones-1-0-2%26s%3dbrooke.loske%2540mykeymortgage.com%26p%3d0854fd0a-c1d4-4e74-9015-544f58774e99%23v%3d3.0.0%26d%3dhttps%253A%252F%252Fstorage.virtru.com%252Fapi%252Fpolicies%252F0854fd0a-c1d4-4e74-9015-544f58774e99%252Fdata%252Fmetadata%26dk%3dg28jd73B%252FofBoSGhbXFeN7%252BaID1%252Bkr9XvijEdmO6f0c%253D&c=E,1,N_aD1WYmIpn7Vk1qBU_Ec24BJ9zMyMOmXe7Em581QW4VTaPRdV4Qz5jqDSL5-5MNsnarqQwoKEsJium7wQV4HNeKXE0W7PyNyGYRAiMW&typo=1 |
| Full analysis: | https://app.any.run/tasks/8ffaa446-bc34-45a2-a076-948206b1a6b9 |
| Verdict: | Malicious activity |
| Analysis date: | August 13, 2019, 18:27:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | FB0D0DF008B7C426D4714713FDAF5774 |
| SHA1: | 895383B8D62AF532B824BFE22BCA7F6081EF7860 |
| SHA256: | FE9A253EDE8F1F962B6F2E5DA1F9BEFE53BBA671697A3345761CC72E1C4F7A51 |
| SSDEEP: | 12:2MtMyUQOq7HtRJOAyeLxeZ4oQA2jdkLxQXg1O3vXHakTqp3xjQeQ:2QJOqDtRAK8ZIhj6eyqfFTqpBjQeQ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- msdt.exe (PID: 2432)
Executed via COM
- sdiagnhost.exe (PID: 2296)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3336)
Creates files in the user directory
- iexplore.exe (PID: 3068)
- iexplore.exe (PID: 3336)
Reads Internet Cache Settings
- iexplore.exe (PID: 3068)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3336)
Changes settings of System certificates
- iexplore.exe (PID: 3336)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 3068)
Reads internet explorer settings
- iexplore.exe (PID: 3068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2296 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2432 | -modal 721252 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDF27BB.tmp -ep NetworkDiagnosticsWeb | C:\Windows\system32\msdt.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3068 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3336 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3336 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
573
Read events
461
Write events
107
Delete events
5
Modification events
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {020BDFE7-BDF8-11E9-9885-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3336) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307080002000D0012001B001F007400 | |||
Executable files
2
Suspicious files
15
Text files
120
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3336 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabA02C.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarA02D.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabA03E.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarA03F.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabAC65.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarAC66.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\94308059B57B3142E455B38A6EB92015 | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
57
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3068 | iexplore.exe | GET | — | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=brook&maxwidth=253&rowheight=20§ionHeight=400&FORM=IE8SSC&market=en-us | US | — | — | whitelisted |
3068 | iexplore.exe | GET | — | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=brooke&maxwidth=253&rowheight=20§ionHeight=400&FORM=IE8SSC&market=en-us | US | — | — | whitelisted |
3068 | iexplore.exe | GET | — | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=brooke+los&maxwidth=253&rowheight=20§ionHeight=400&FORM=IE8SSC&market=en-us | US | — | — | whitelisted |
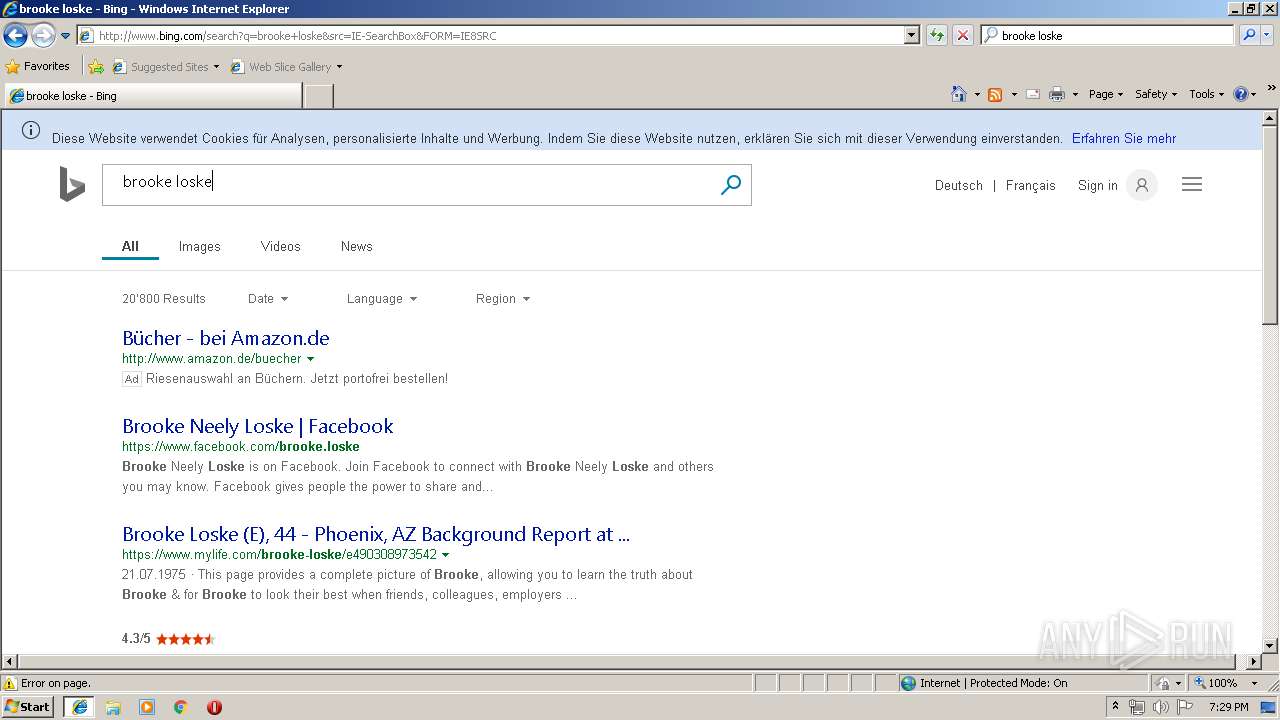
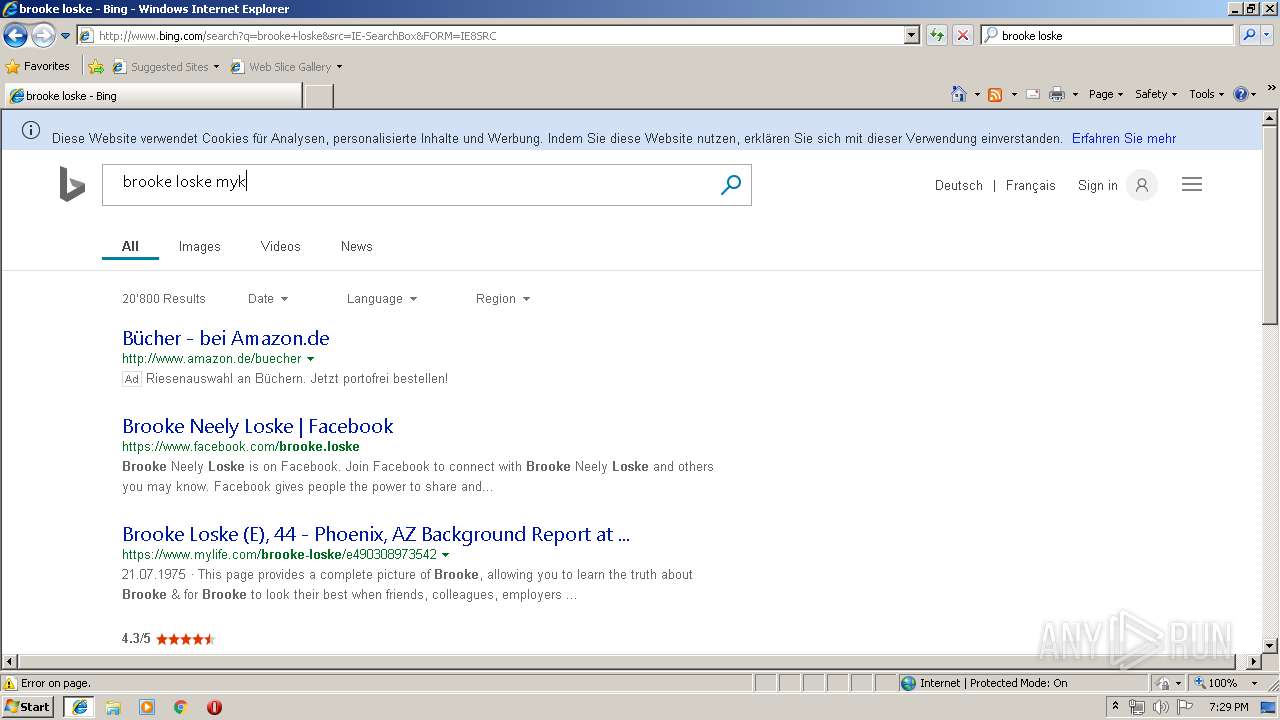
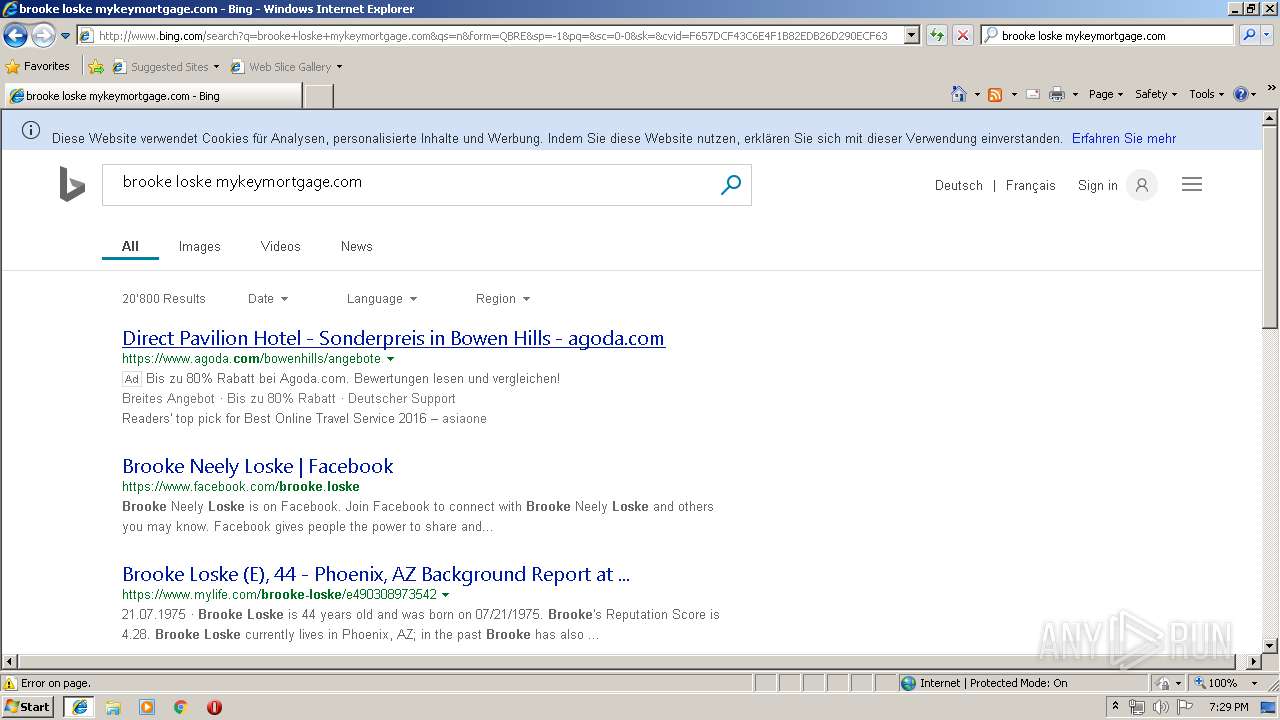
3068 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/search?q=brooke+loske&src=IE-SearchBox&FORM=IE8SRC | US | html | 43.1 Kb | whitelisted |
3068 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=b&maxwidth=253&rowheight=20§ionHeight=400&FORM=IE8SSC&market=en-us | US | xml | 248 b | whitelisted |
3068 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=br&maxwidth=253&rowheight=20§ionHeight=400&FORM=IE8SSC&market=en-us | US | xml | 240 b | whitelisted |
3068 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=broo&maxwidth=253&rowheight=20§ionHeight=400&FORM=IE8SSC&market=en-us | US | xml | 226 b | whitelisted |
3068 | iexplore.exe | GET | 200 | 13.107.5.80:80 | http://api.bing.com/qsml.aspx?query=brooke+lo&maxwidth=253&rowheight=20§ionHeight=400&FORM=IE8SSC&market=en-us | US | xml | 231 b | whitelisted |
3068 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/sa/simg/SharedSpriteDesktopRewards_022118.png | US | image | 5.73 Kb | whitelisted |
3068 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/rs/5b/2e/cj,nj/08abbb2f/e177b199.js | US | text | 2.86 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3336 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3068 | iexplore.exe | 13.35.254.82:80 | x.ss2.us | — | US | suspicious |
3068 | iexplore.exe | 18.194.14.44:443 | linkprotect.cudasvc.com | Amazon.com, Inc. | DE | unknown |
3068 | iexplore.exe | 205.185.216.10:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3068 | iexplore.exe | 3.13.89.219:443 | secure.virtru.com | — | US | unknown |
3068 | iexplore.exe | 13.107.5.80:80 | api.bing.com | Microsoft Corporation | US | whitelisted |
3068 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3068 | iexplore.exe | 65.54.187.128:443 | login.live.com | Microsoft Corporation | US | whitelisted |
3068 | iexplore.exe | 104.211.160.15:80 | 228ea03ed0f2a9792862f9ec2eccdffb.clo.footprintdns.com | Microsoft Corporation | IN | whitelisted |
3068 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
linkprotect.cudasvc.com |
| whitelisted |
x.ss2.us |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
secure.virtru.com |
| malicious |
api.bing.com |
| whitelisted |
tse1.mm.bing.net |
| whitelisted |
login.live.com |
| whitelisted |
edd7400d9259dc0b7eb422aa42f57bb0.clo.footprintdns.com |
| unknown |
228ea03ed0f2a9792862f9ec2eccdffb.clo.footprintdns.com |
| unknown |