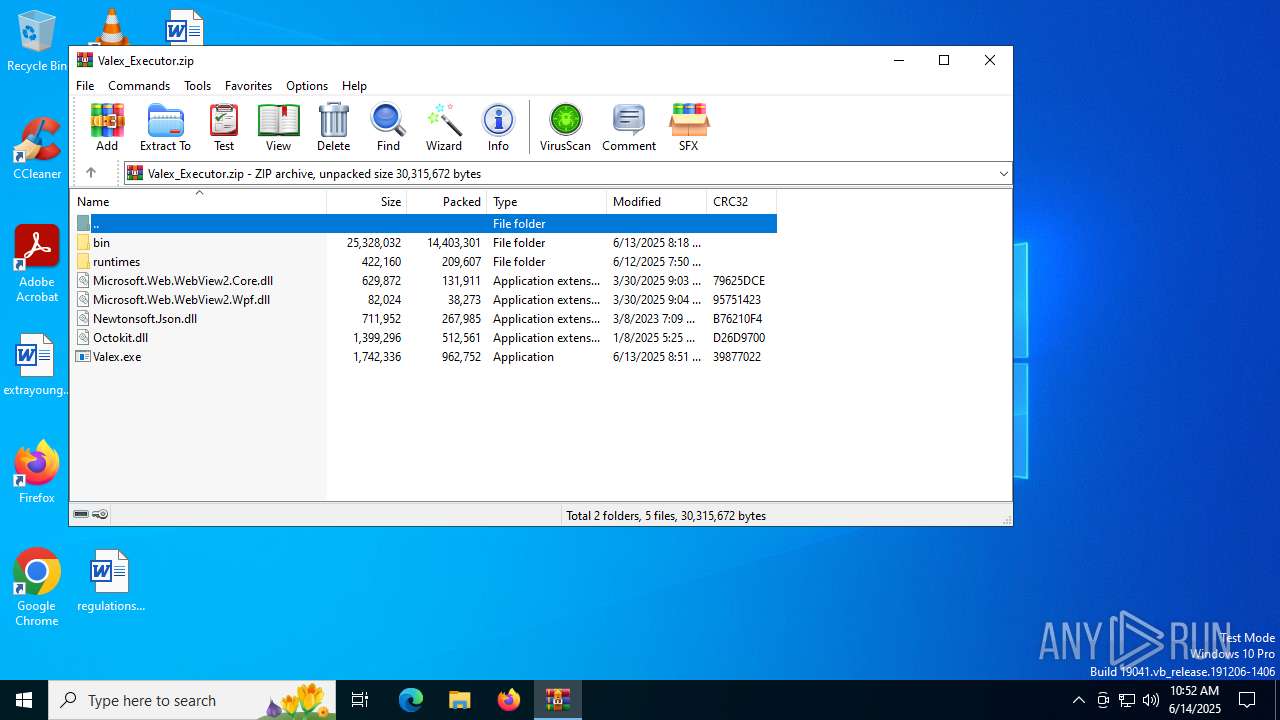
| File name: | Valex_Executor.zip |
| Full analysis: | https://app.any.run/tasks/784479fd-2e74-4b12-92cc-e852ed7c2133 |
| Verdict: | Malicious activity |
| Analysis date: | June 14, 2025, 10:51:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | BE07C03E4B7C97004B37B6813918112E |
| SHA1: | 12E58A1A22F512EFC32C76A706A398B155451267 |
| SHA256: | FE969C08599664C940F3131BA6B0D24D3A2D5C8CFE85F3D54CA1C3705A599139 |
| SSDEEP: | 196608:adpEgIX4Czr22IDZGCDvRNLxfPp8gwgrdkI+Ithy98FxM6N3:eElX1JIDZdDvf5h5RxkI+IthJFTN3 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 5644)
- WinRAR.exe (PID: 4172)
Executes application which crashes
- Valex.exe (PID: 5556)
- Valex.exe (PID: 3668)
- Valex.exe (PID: 1508)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5644)
- WinRAR.exe (PID: 4172)
Manual execution by a user
- WinRAR.exe (PID: 4172)
- Valex.exe (PID: 4864)
- Valex.exe (PID: 5556)
- Valex.exe (PID: 5008)
- Valex.exe (PID: 3668)
- Valex.exe (PID: 1508)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4172)
Checks supported languages
- Valex.exe (PID: 5556)
- Valex.exe (PID: 1508)
- Valex.exe (PID: 3668)
Reads the computer name
- Valex.exe (PID: 5556)
- Valex.exe (PID: 3668)
- Valex.exe (PID: 1508)
Disables trace logs
- Valex.exe (PID: 5556)
- Valex.exe (PID: 3668)
- Valex.exe (PID: 1508)
Checks proxy server information
- Valex.exe (PID: 5556)
- WerFault.exe (PID: 3608)
- Valex.exe (PID: 3668)
- WerFault.exe (PID: 2716)
- Valex.exe (PID: 1508)
- WerFault.exe (PID: 5900)
Reads the machine GUID from the registry
- Valex.exe (PID: 5556)
- Valex.exe (PID: 3668)
- Valex.exe (PID: 1508)
Reads the software policy settings
- Valex.exe (PID: 5556)
- WerFault.exe (PID: 3608)
- WerFault.exe (PID: 2716)
- Valex.exe (PID: 3668)
- Valex.exe (PID: 1508)
- WerFault.exe (PID: 5900)
Creates files or folders in the user directory
- WerFault.exe (PID: 3608)
- WerFault.exe (PID: 2716)
- WerFault.exe (PID: 5900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:30 05:04:10 |
| ZipCRC: | 0x95751423 |
| ZipCompressedSize: | 38273 |
| ZipUncompressedSize: | 82024 |
| ZipFileName: | Microsoft.Web.WebView2.Wpf.dll |
Total processes
148
Monitored processes
12
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
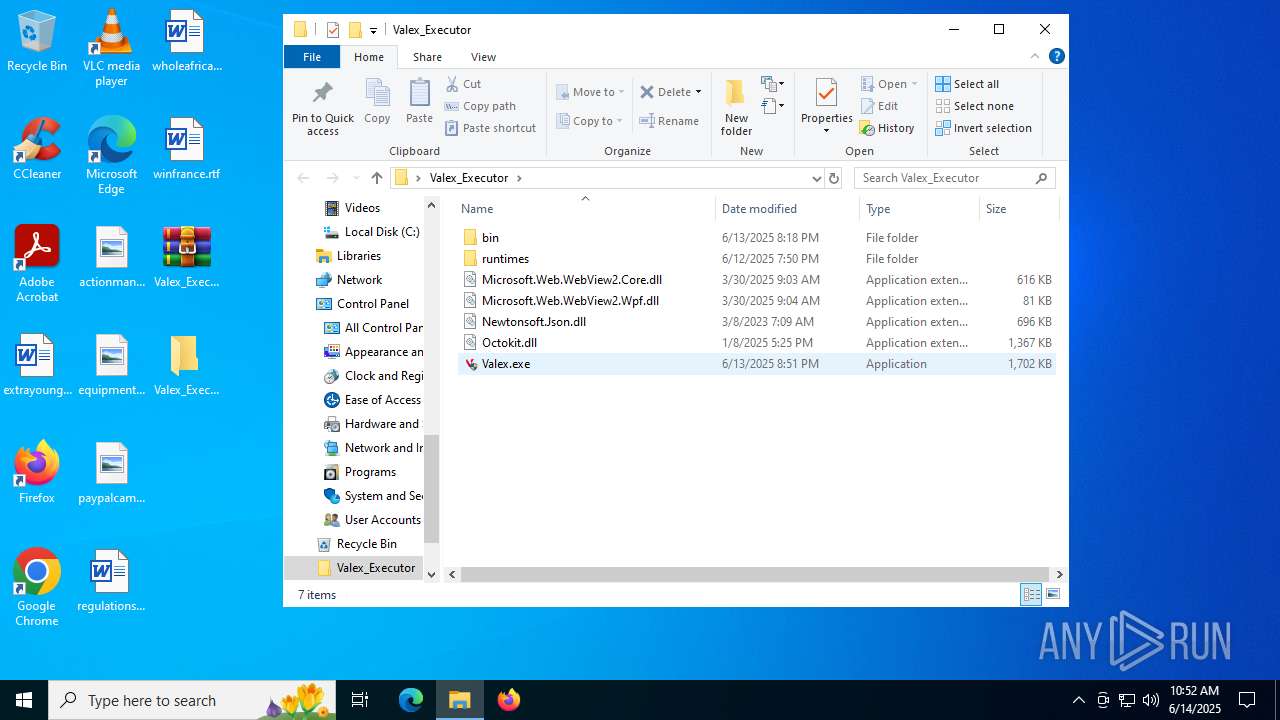
| 1508 | "C:\Users\admin\Desktop\Valex_Executor\Valex.exe" | C:\Users\admin\Desktop\Valex_Executor\Valex.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Nezur Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 3668 -s 2092 | C:\Windows\SysWOW64\WerFault.exe | Valex.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5556 -s 2088 | C:\Windows\SysWOW64\WerFault.exe | Valex.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3668 | "C:\Users\admin\Desktop\Valex_Executor\Valex.exe" | C:\Users\admin\Desktop\Valex_Executor\Valex.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Nezur Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4172 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Valex_Executor.zip" C:\Users\admin\Desktop\Valex_Executor\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4864 | "C:\Users\admin\Desktop\Valex_Executor\Valex.exe" | C:\Users\admin\Desktop\Valex_Executor\Valex.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Nezur Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5008 | "C:\Users\admin\Desktop\Valex_Executor\Valex.exe" | C:\Users\admin\Desktop\Valex_Executor\Valex.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Nezur Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5556 | "C:\Users\admin\Desktop\Valex_Executor\Valex.exe" | C:\Users\admin\Desktop\Valex_Executor\Valex.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Nezur Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5644 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Valex_Executor.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
30 929
Read events
30 870
Write events
50
Delete events
9
Modification events
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Valex_Executor.zip | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5644) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
10
Suspicious files
7
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4172 | WinRAR.exe | C:\Users\admin\Desktop\Valex_Executor\bin\libz3.dll | executable | |
MD5:B0097E1EA9D0E44EEE5B2D28681E57CA | SHA256:7DB664F4F0A1EB059D50327B338813CB5CFD2492F590846899E50DF533FA77FB | |||
| 4172 | WinRAR.exe | C:\Users\admin\Desktop\Valex_Executor\Octokit.dll | executable | |
MD5:2C2A65E9CF0776FA77600D5FE3B30783 | SHA256:6A48642D6AE464B43A6CB50292618AF6C73ADA8D726644E50D4FA44A1783F638 | |||
| 4172 | WinRAR.exe | C:\Users\admin\Desktop\Valex_Executor\Valex.exe | executable | |
MD5:452D917F90185A169A4B201B3905E6F5 | SHA256:77C0F2D523D0363E3FBE1A5DD5F5126A5192DF389A9E578FF30F1BBF81F52A31 | |||
| 4172 | WinRAR.exe | C:\Users\admin\Desktop\Valex_Executor\bin\Monaco\vs\basic-languages\lua\lua.js | binary | |
MD5:8706D861294E09A1F2F7E63D19E5FCB7 | SHA256:FC2D6FB52A524A56CD8AC53BFE4BAD733F246E76DC73CBEC4C61BE32D282AC42 | |||
| 4172 | WinRAR.exe | C:\Users\admin\Desktop\Valex_Executor\bin\Monaco\Monaco.html | html | |
MD5:6C54F348B6511858B8963C5F5BD836AC | SHA256:B5E998236CED3177E44A7A35B33892751D758275B5623CC050872BAB66A738C4 | |||
| 4172 | WinRAR.exe | C:\Users\admin\Desktop\Valex_Executor\bin\Monaco\vs\editor\editor.main.js | binary | |
MD5:9399A8EAA741D04B0AE6566A5EBB8106 | SHA256:93D28520C07FBCA09E20886087F28797BB7BD0E6CF77400153AAB5AE67E3CE18 | |||
| 4172 | WinRAR.exe | C:\Users\admin\Desktop\Valex_Executor\Newtonsoft.Json.dll | executable | |
MD5:195FFB7167DB3219B217C4FD439EEDD6 | SHA256:E1E27AF7B07EEEDF5CE71A9255F0422816A6FC5849A483C6714E1B472044FA9D | |||
| 4172 | WinRAR.exe | C:\Users\admin\Desktop\Valex_Executor\bin\Monaco\vs\editor\editor.main.nls.ko.js | text | |
MD5:9CCF83D22E9A9BFAFA2000F366AC47E6 | SHA256:100CA482C015571ED9AAD97C2DCC5E266B270A650CE892507443B5D4F32DF64F | |||
| 4172 | WinRAR.exe | C:\Users\admin\Desktop\Valex_Executor\bin\Monaco\vs\editor\editor.main.nls.zh-cn.js | text | |
MD5:F954AC1091C6D0B640ED5F0ABDCD8ADB | SHA256:AC881E6F56544ED9B8DD4FD8FD8A73F1DA864FB8D79D91C45F5A51F923BD5287 | |||
| 4172 | WinRAR.exe | C:\Users\admin\Desktop\Valex_Executor\bin\Monaco\vs\editor\editor.main.nls.ru.js | text | |
MD5:FD1AA66906D2B3C0C9B734B17F04D73B | SHA256:FA180F7B77EE252AEFE73BA5993FBE7C89F43482358D7FD32E8E2F50B3B21BED | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
48
DNS requests
15
Threats
4
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
436 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5556 | Valex.exe | 104.26.1.5:443 | keyauth.win | CLOUDFLARENET | US | malicious |
6024 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3608 | WerFault.exe | 20.189.173.22:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
keyauth.win |
| malicious |
watson.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
171.39.242.20.in-addr.arpa |
| unknown |
d.3.0.0.0.0.0.0.0.0.0.0.0.0.0.0.7.0.0.0.8.0.4.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5556 | Valex.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
2200 | svchost.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain in DNS Lookup (keyauth .win) |
3668 | Valex.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |
1508 | Valex.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |