analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
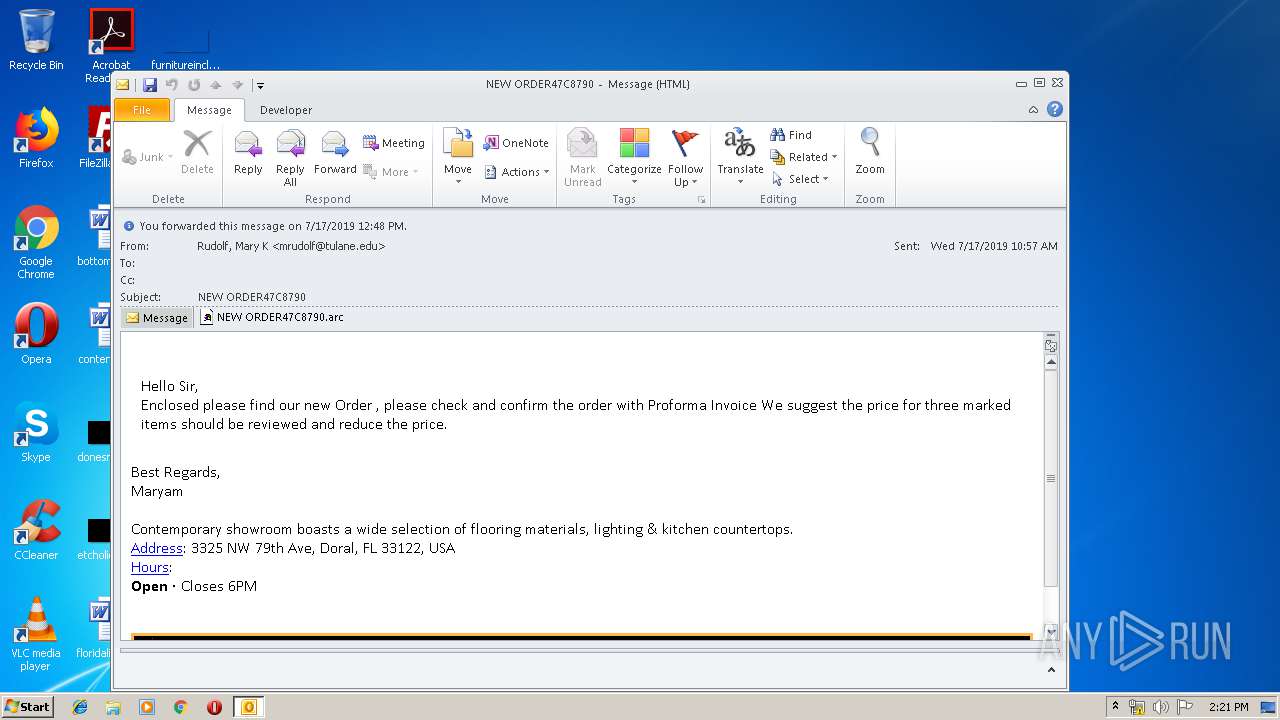
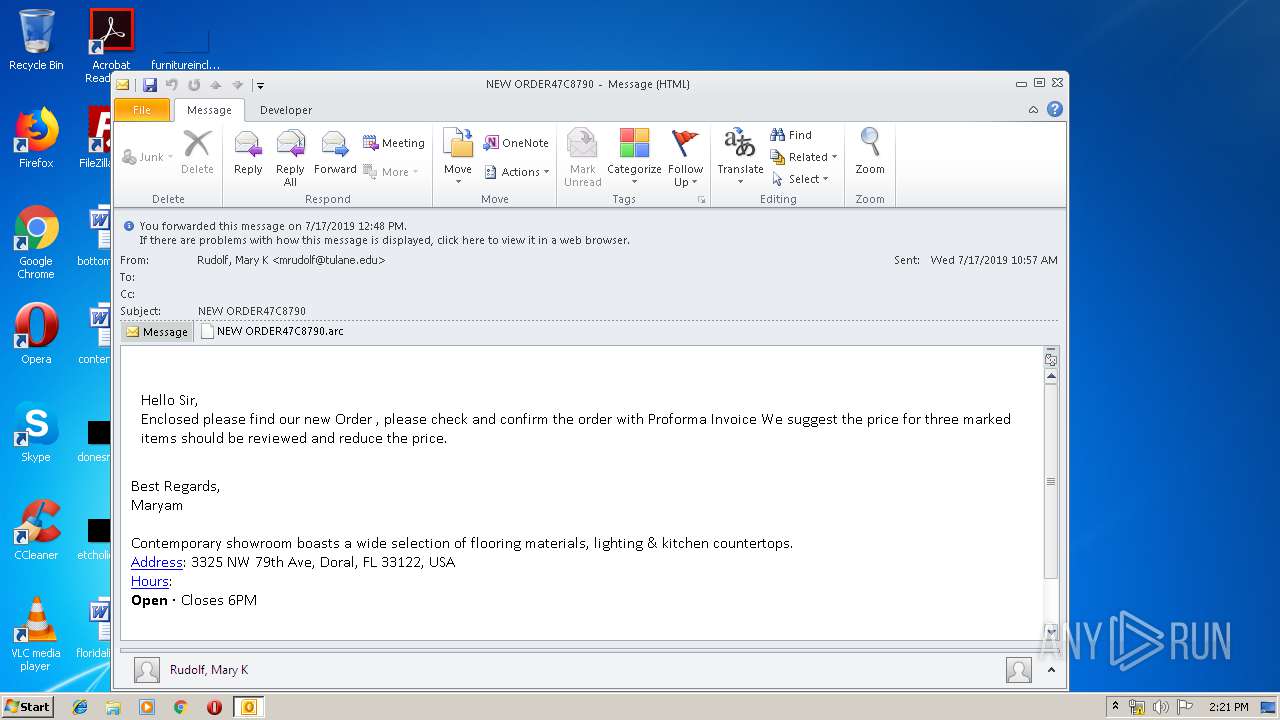
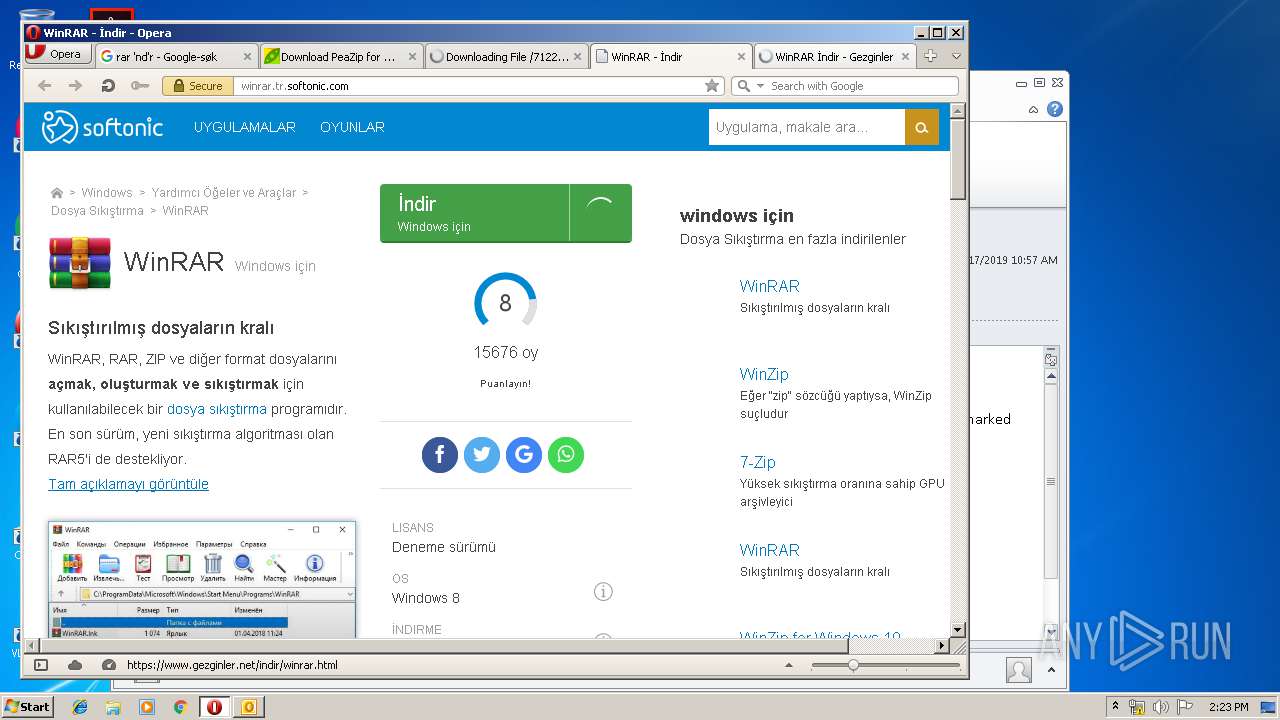
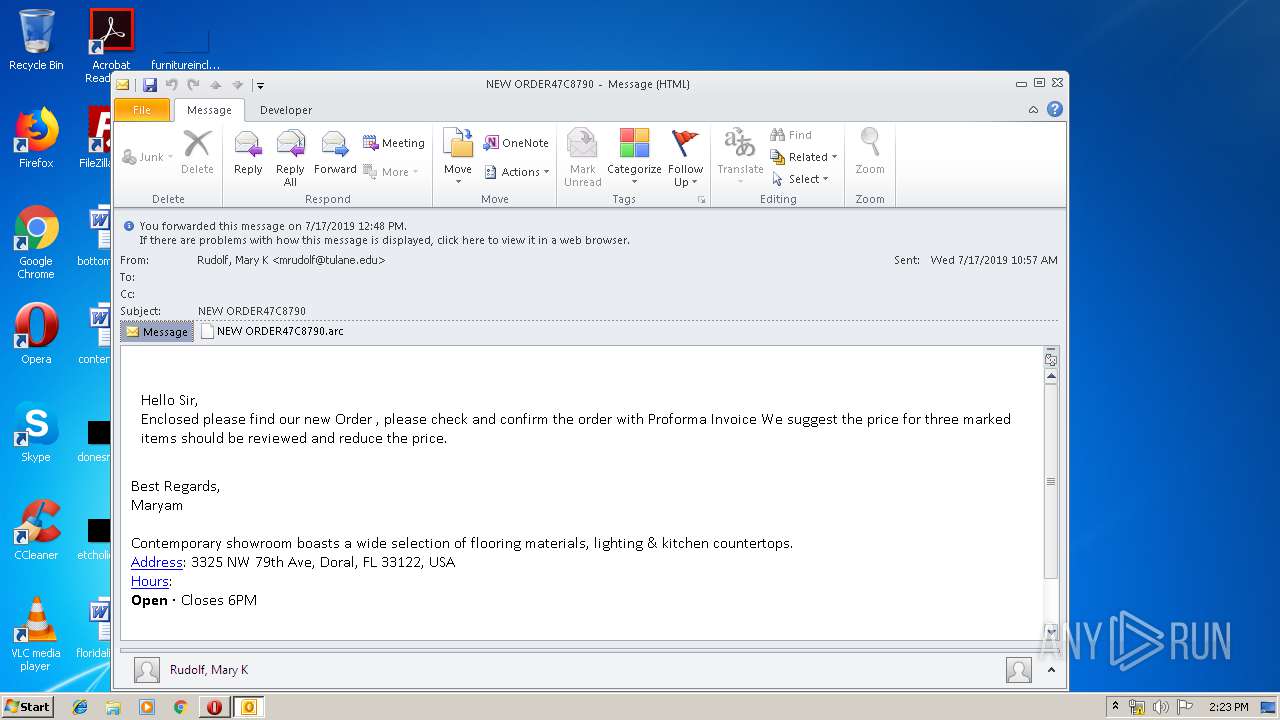
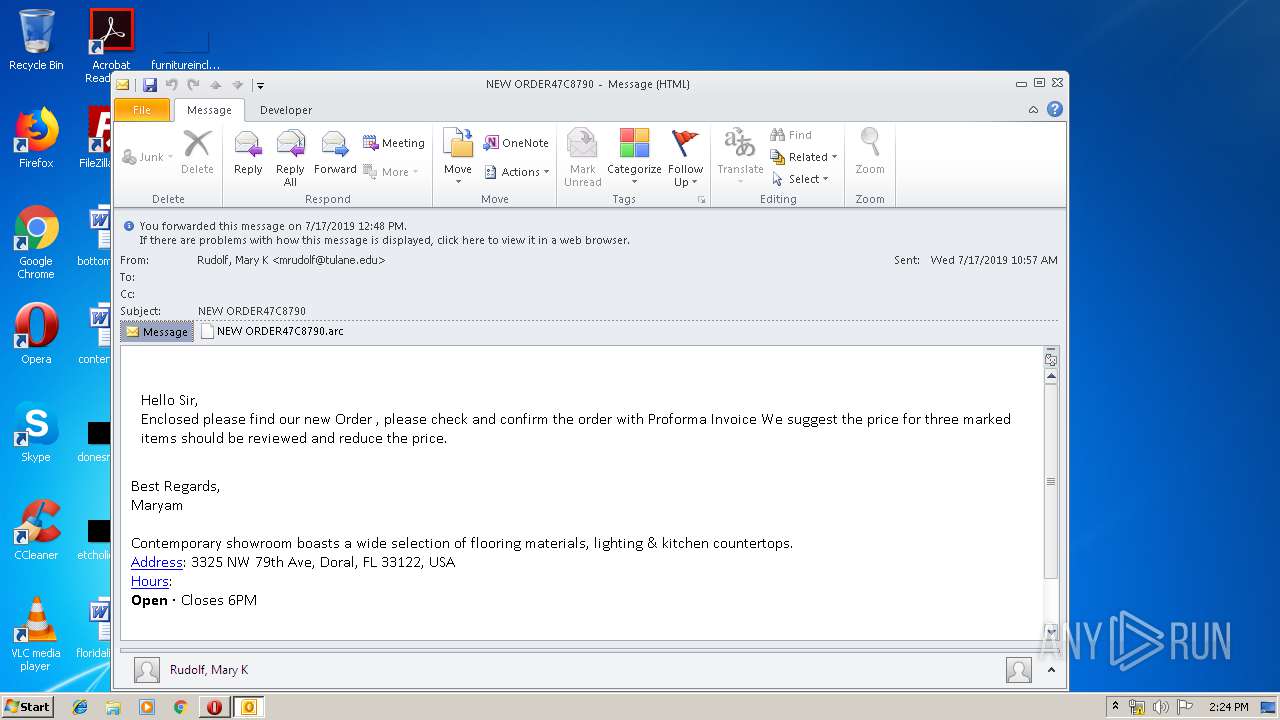
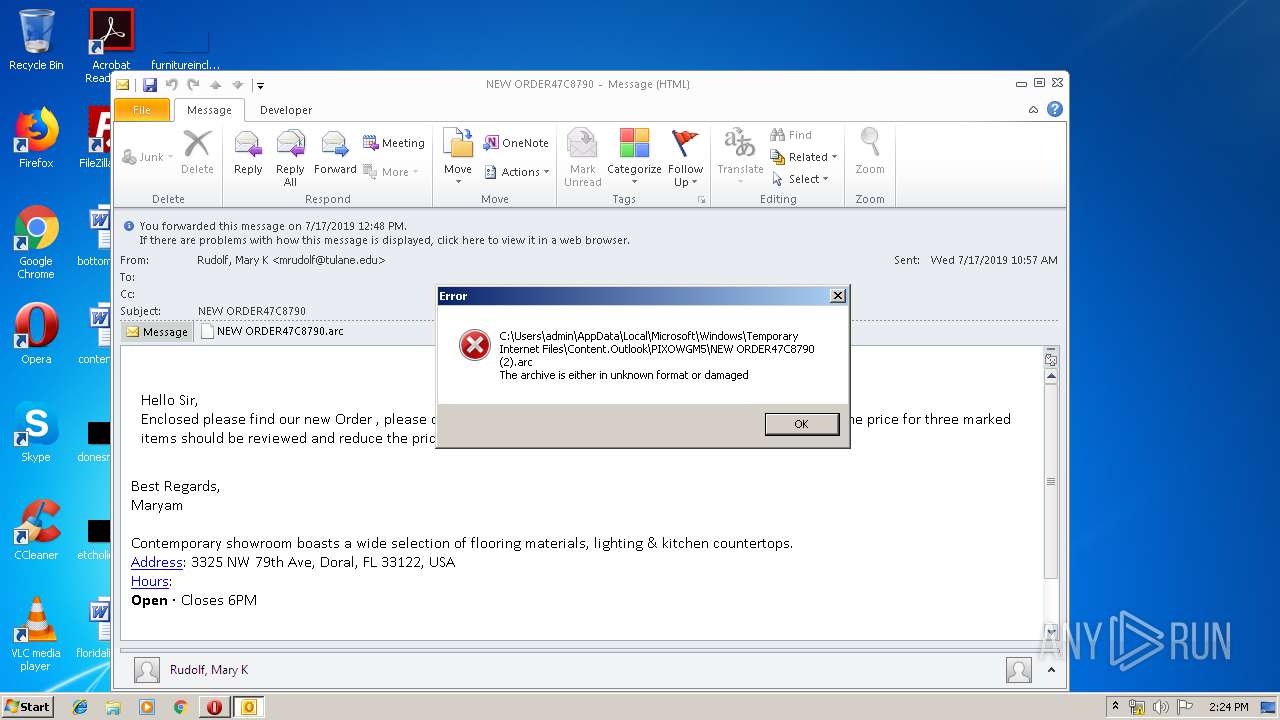
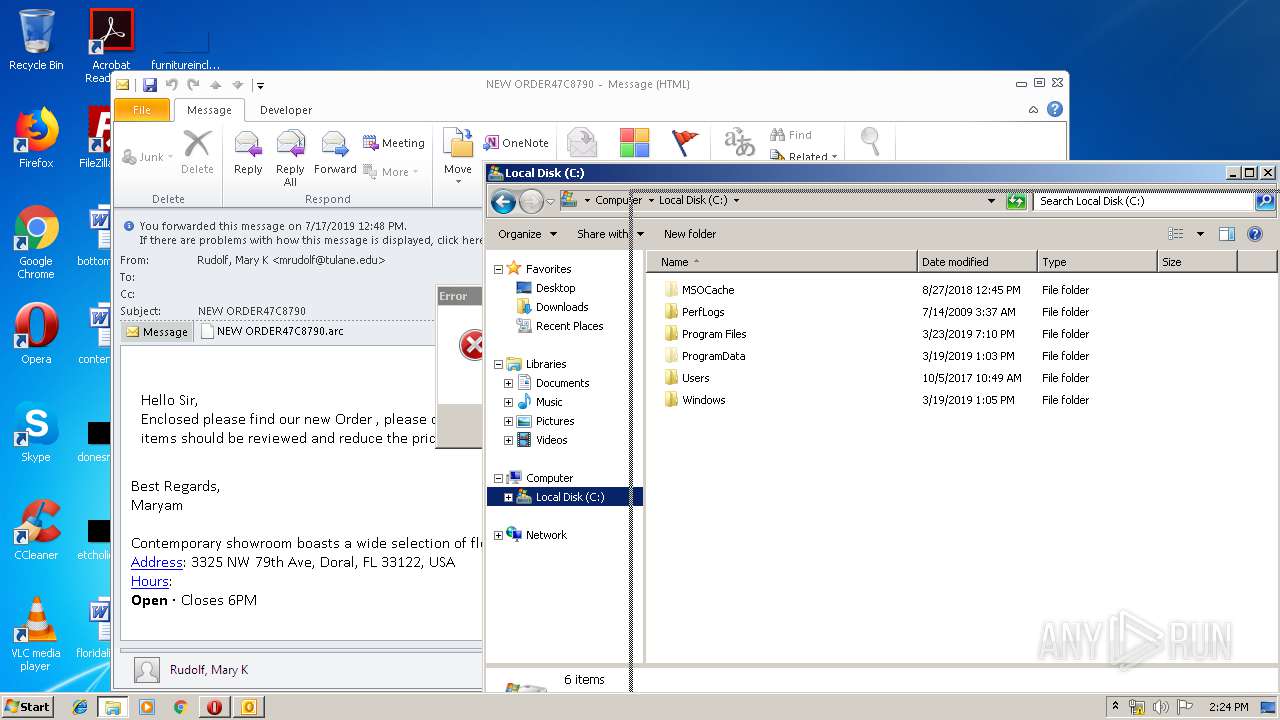
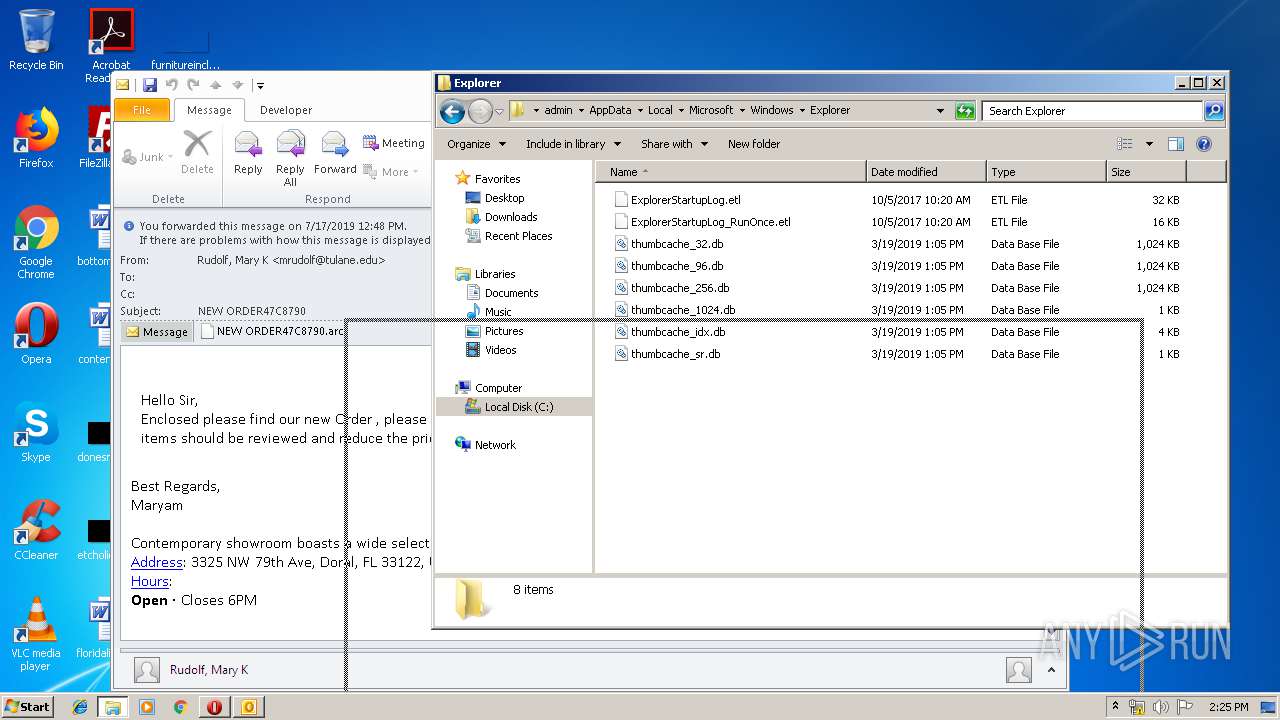
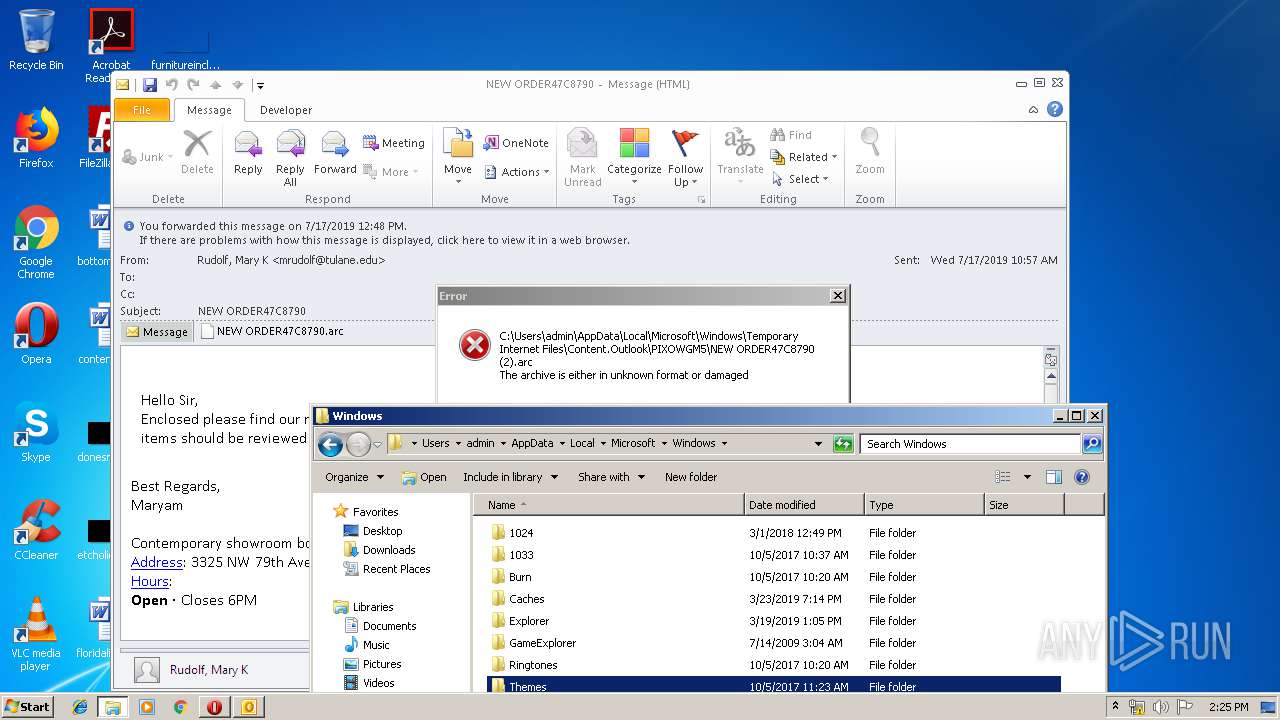
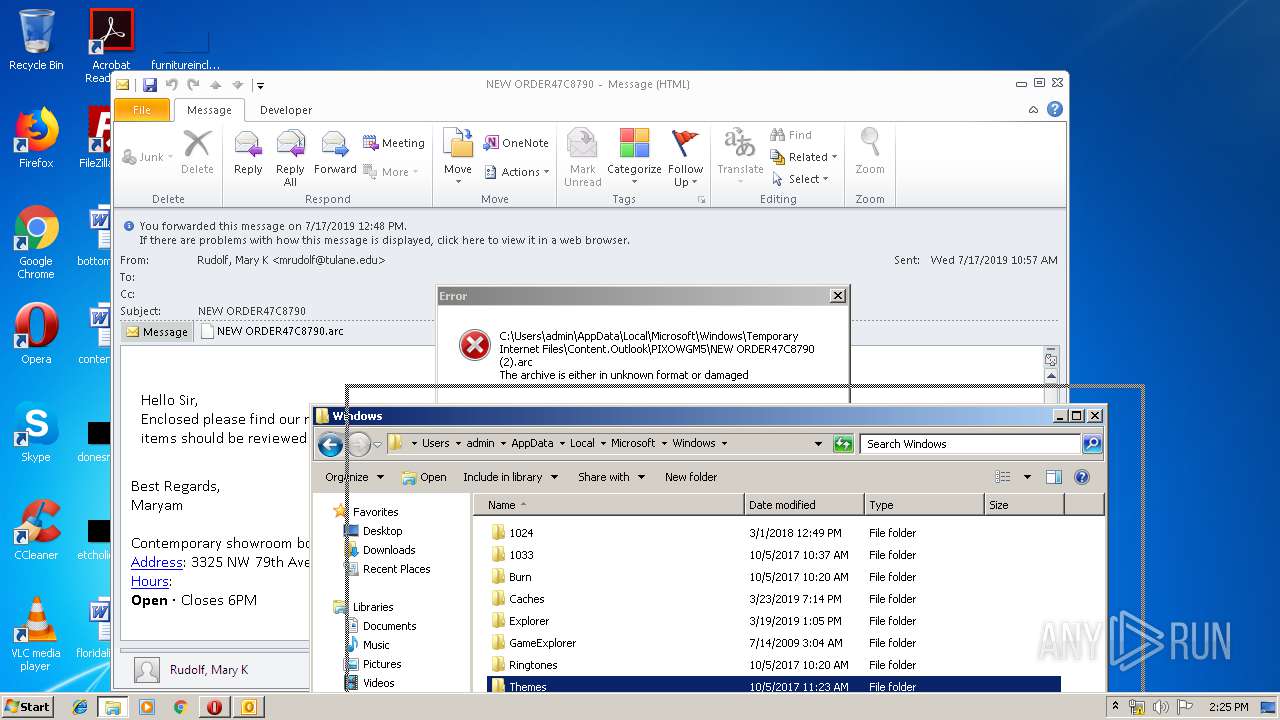
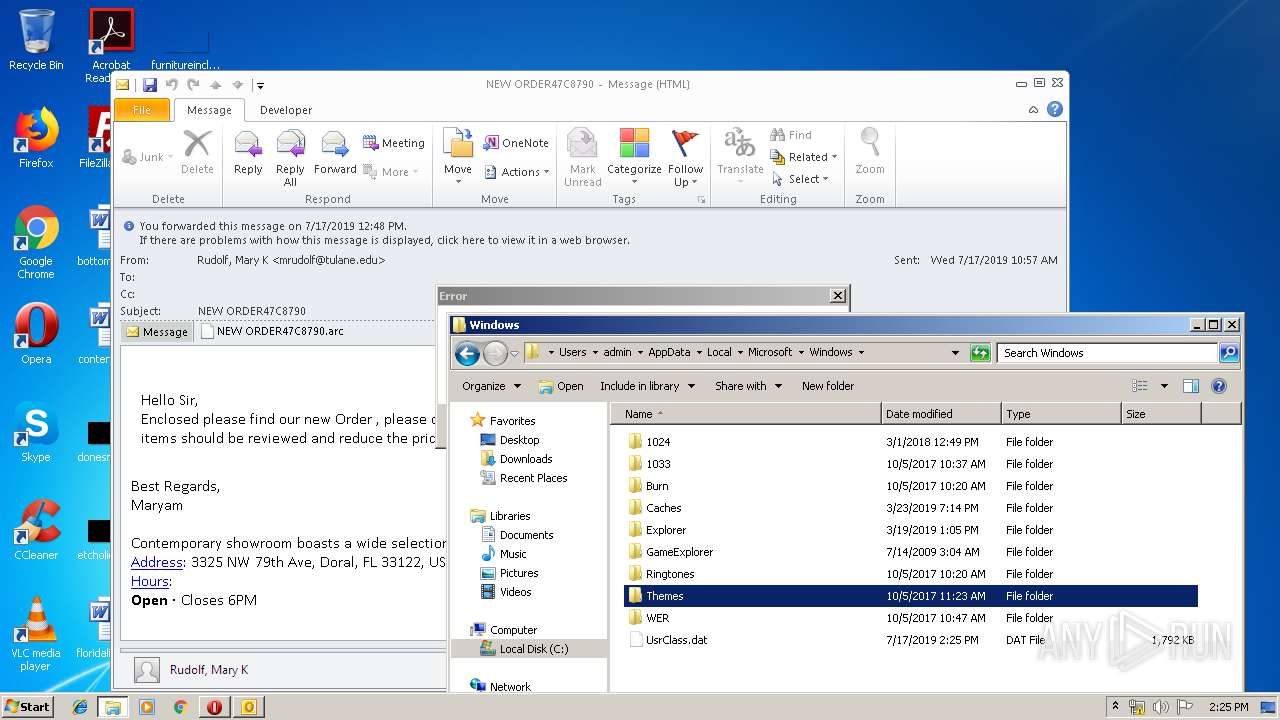
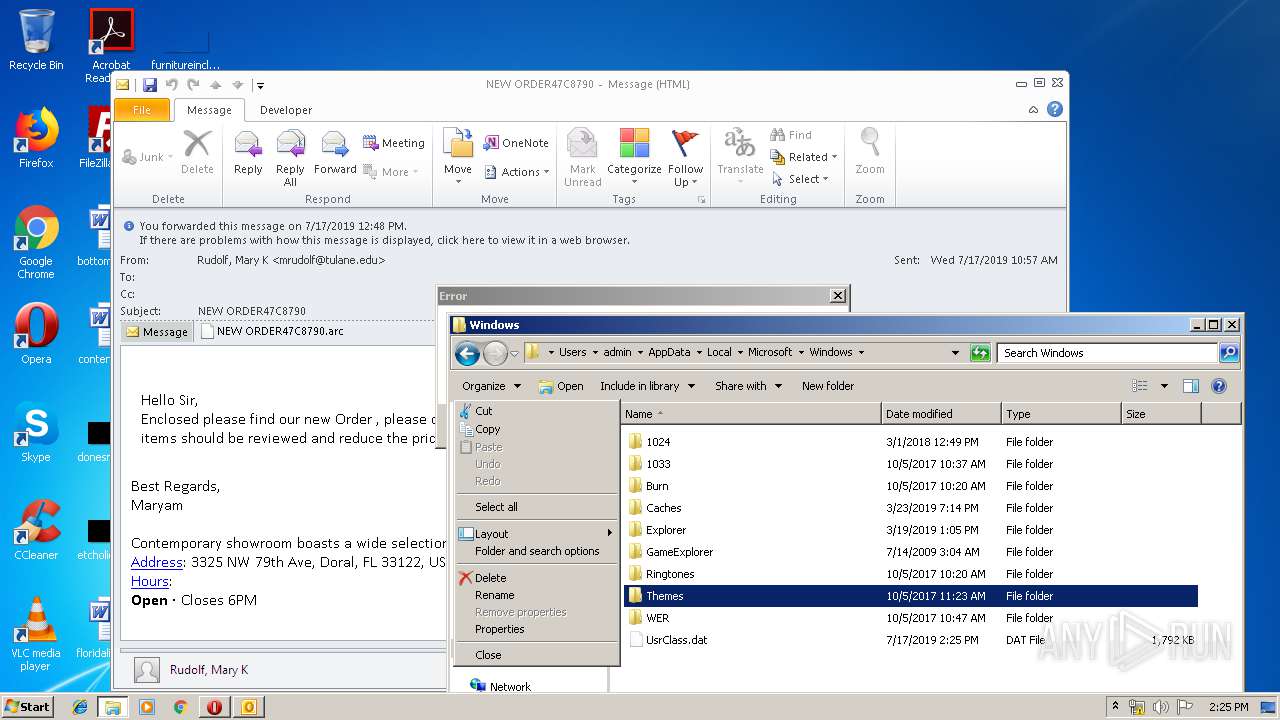
| File name: | NEW ORDER47C8790.msg |
| Full analysis: | https://app.any.run/tasks/1c5abf02-d349-46e3-8f9f-62573e2d49d7 |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 13:20:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 6342AE3C9487056BE3747BED5565A973 |
| SHA1: | 522677DC937A09273873FEA35D7CE19C74AEE2A4 |
| SHA256: | FE724F992090BC15B6761117592BCFC86612F38579FF01F7258D86252642D8BF |
| SSDEEP: | 6144:DYwo+YKi9usRWe00dElE362xuWBf3Wa/PVg2C7cDWx8fP1VGj:0++geEWBua3m2C7GWx8fDU |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 3848)
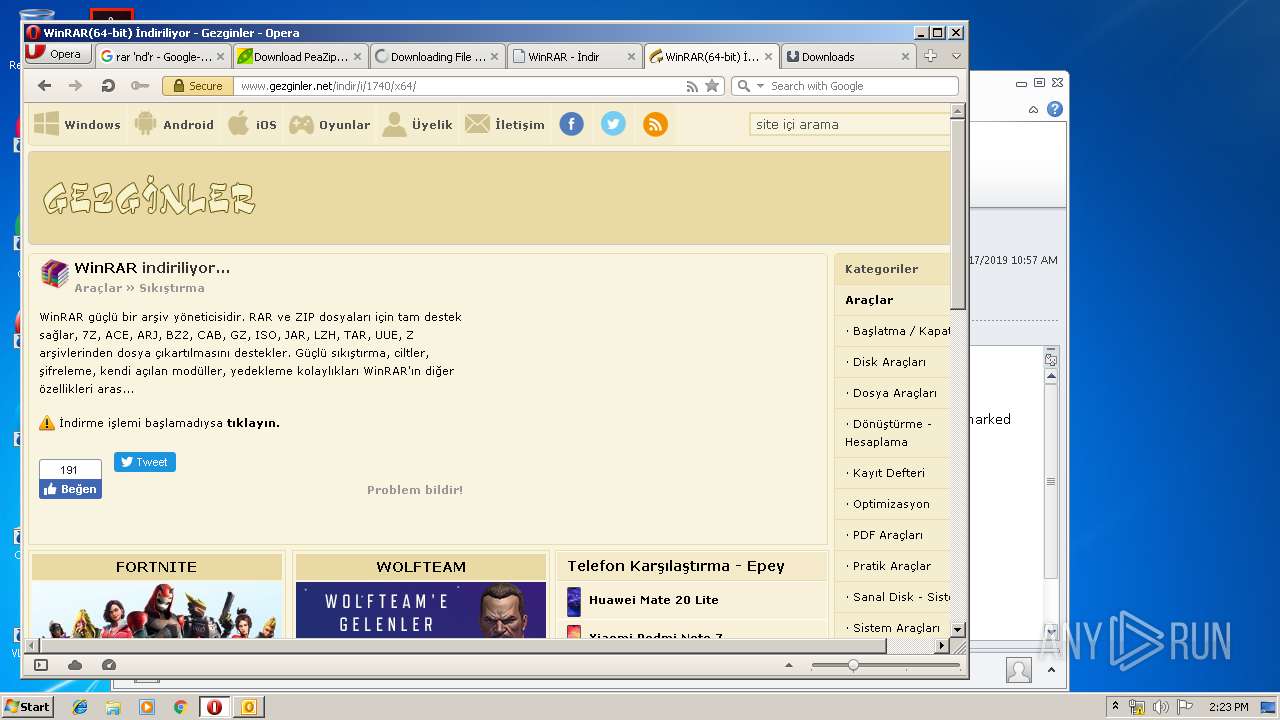
Downloads executable files from the Internet
- opera.exe (PID: 3944)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3848)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3848)
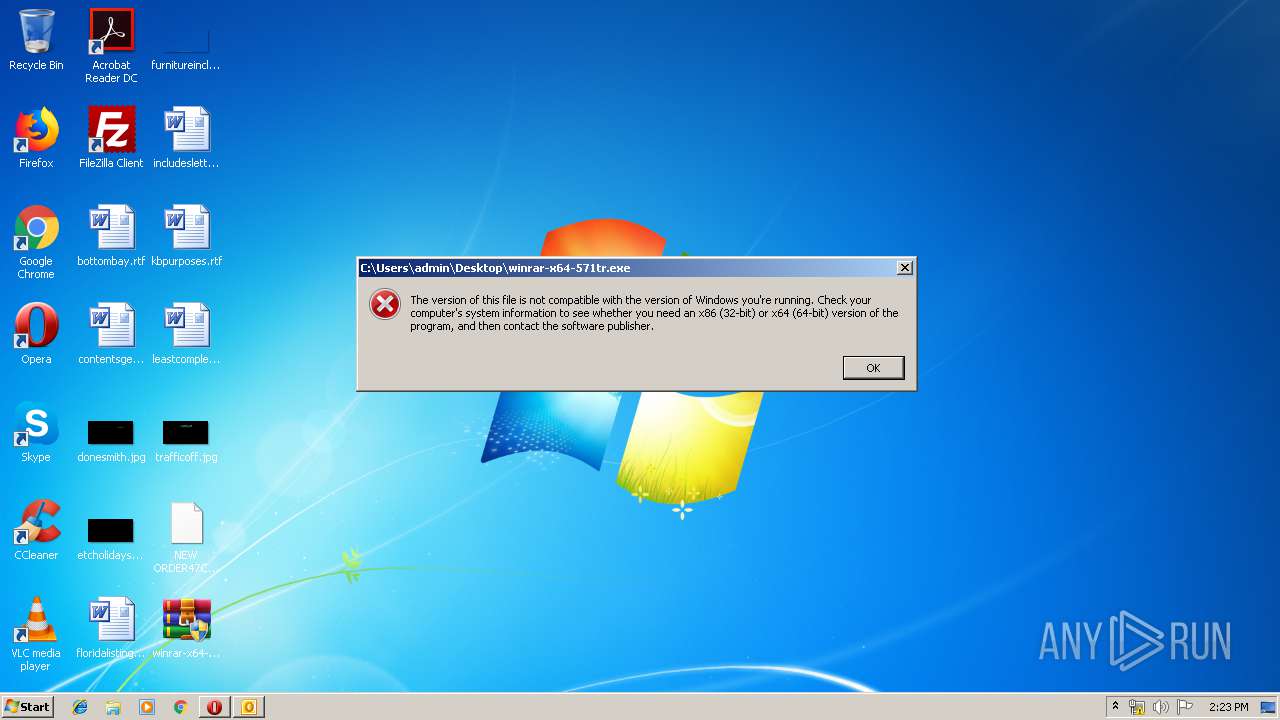
Executable content was dropped or overwritten
- opera.exe (PID: 3944)
INFO
Manual execution by user
- rundll32.exe (PID: 3008)
- explorer.exe (PID: 2832)
- opera.exe (PID: 3944)
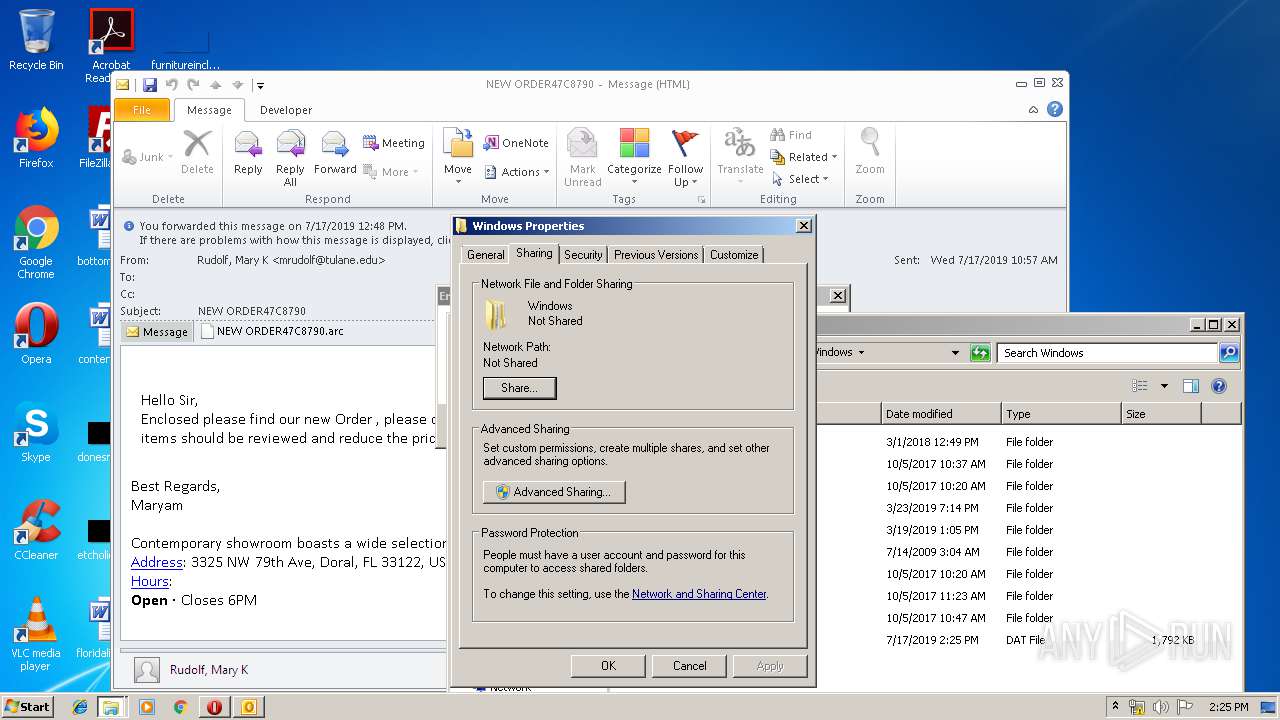
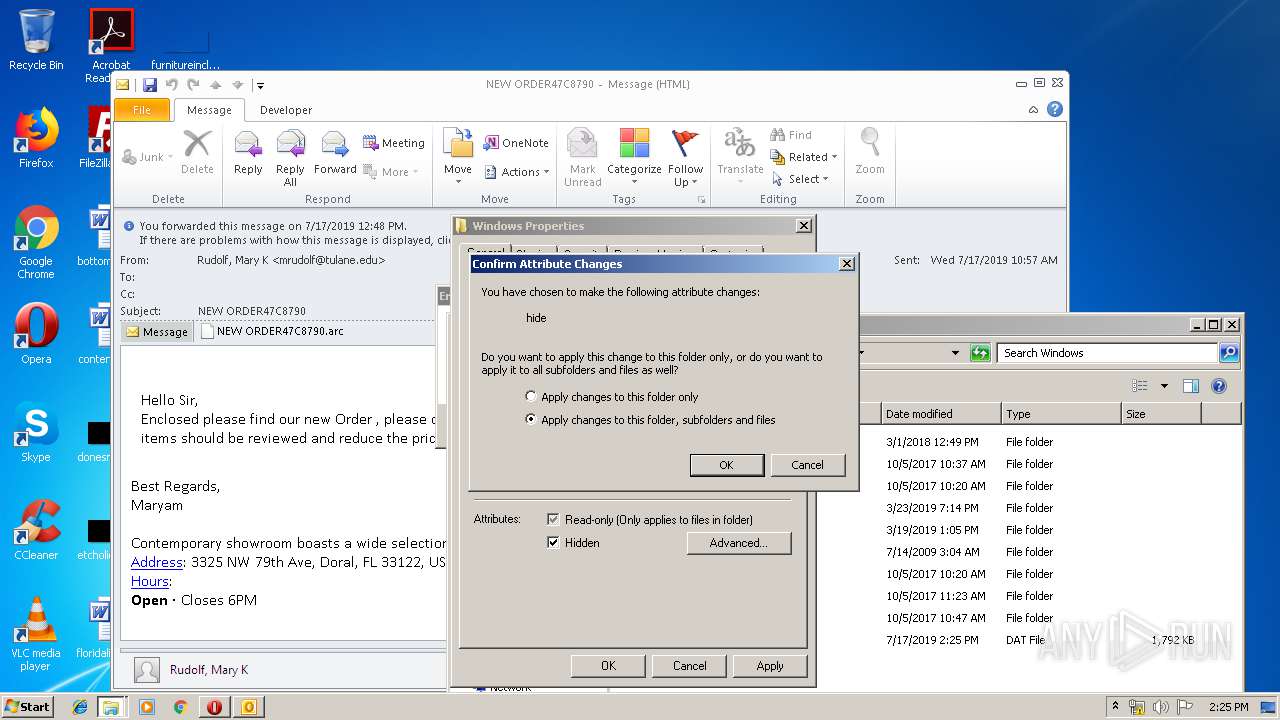
Modifies the open verb of a shell class
- rundll32.exe (PID: 3008)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3848)
Creates files in the user directory
- opera.exe (PID: 3944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
50
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3848 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\NEW ORDER47C8790.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3944 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Version: 1748 Modules
| |||||||||||||||
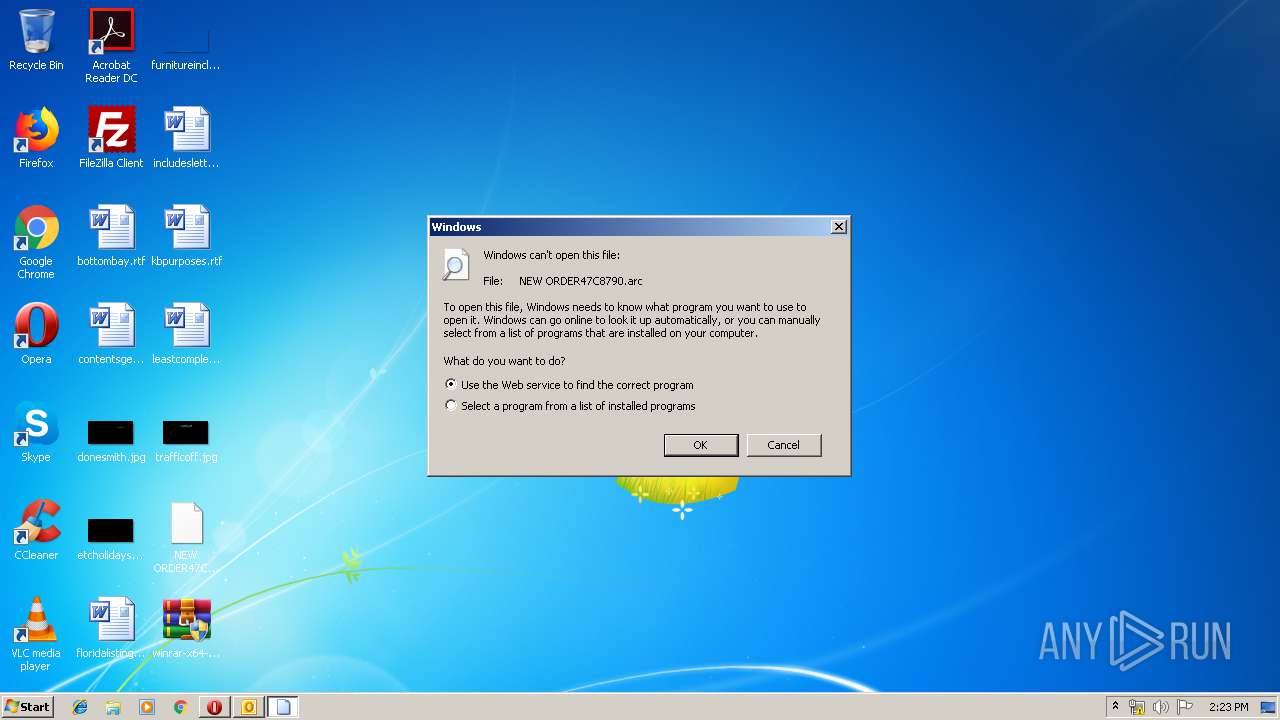
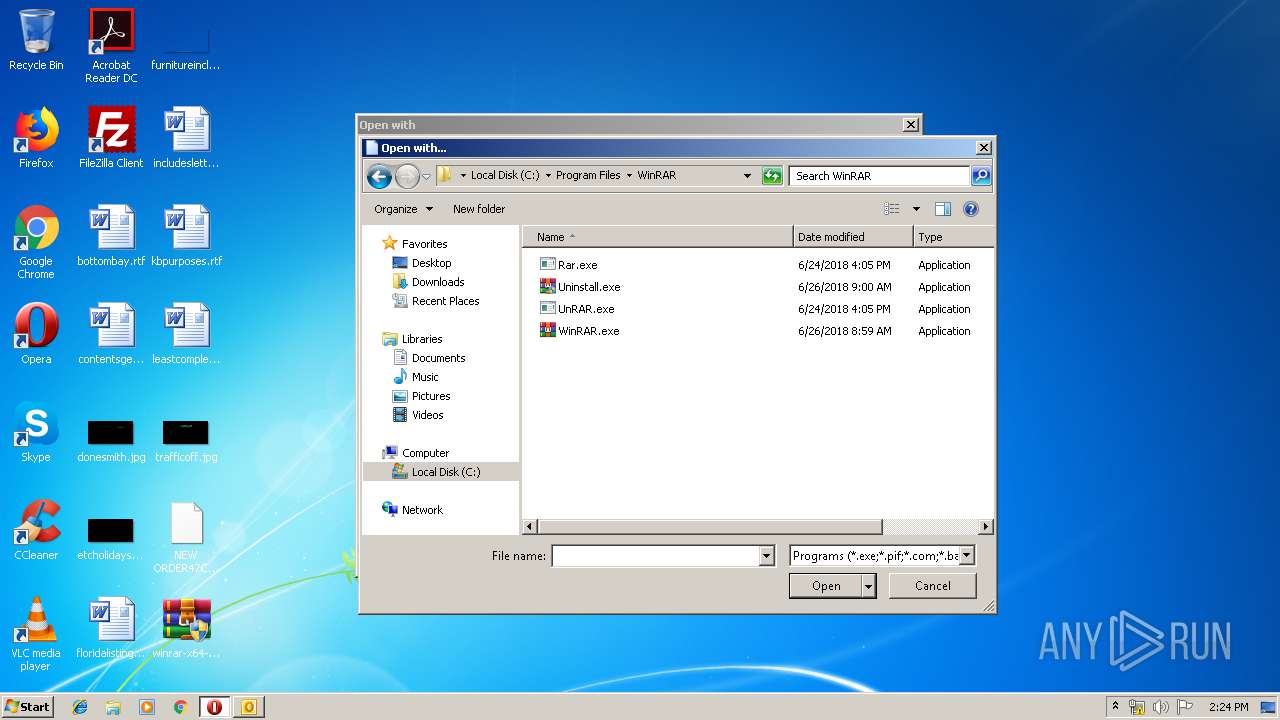
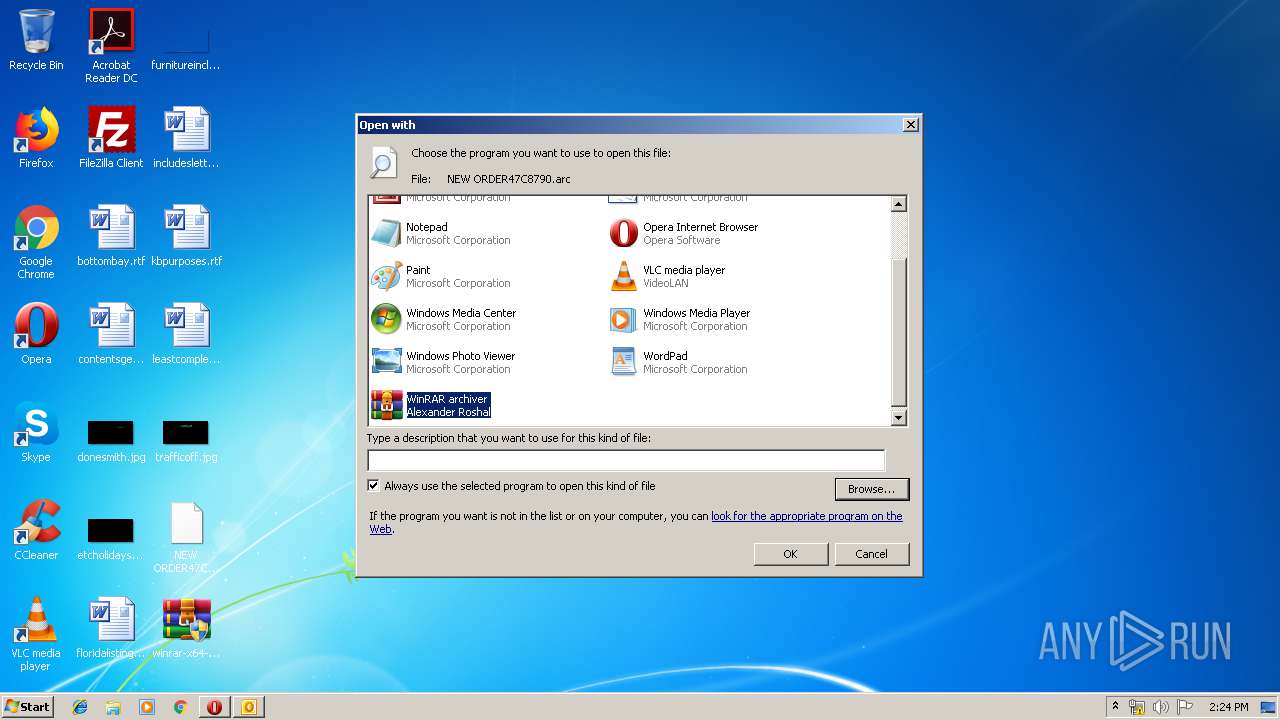
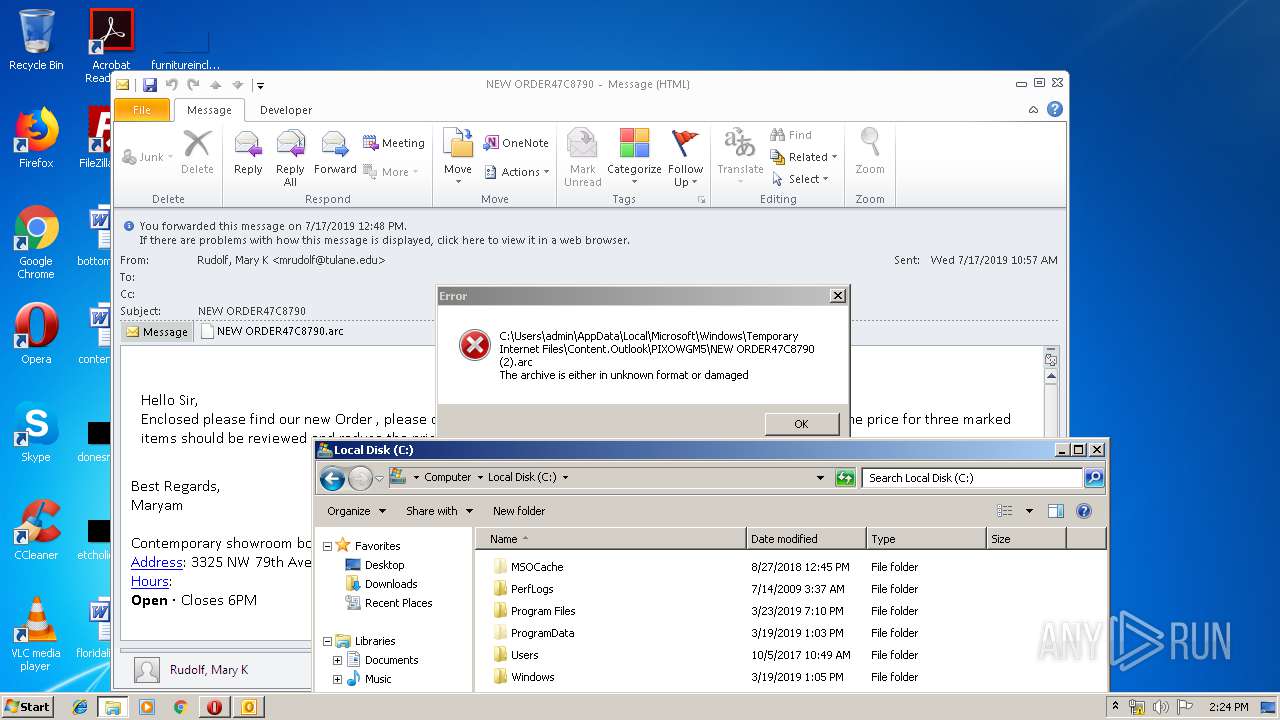
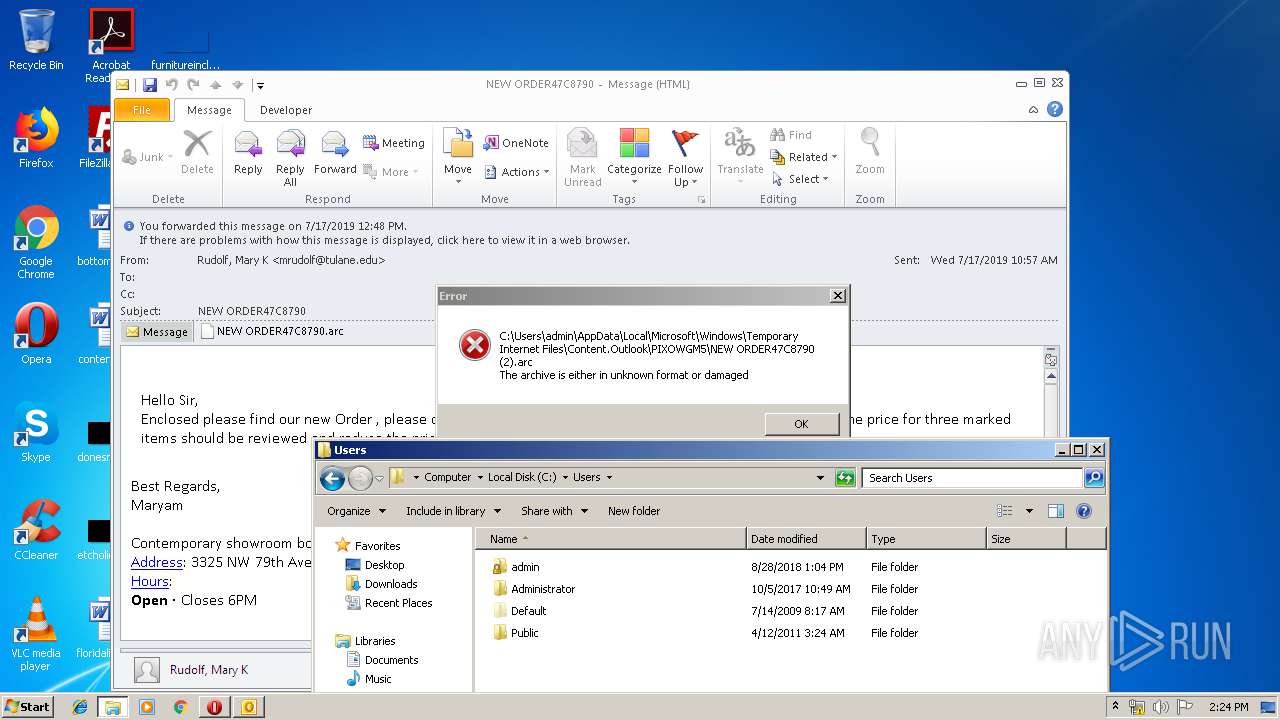
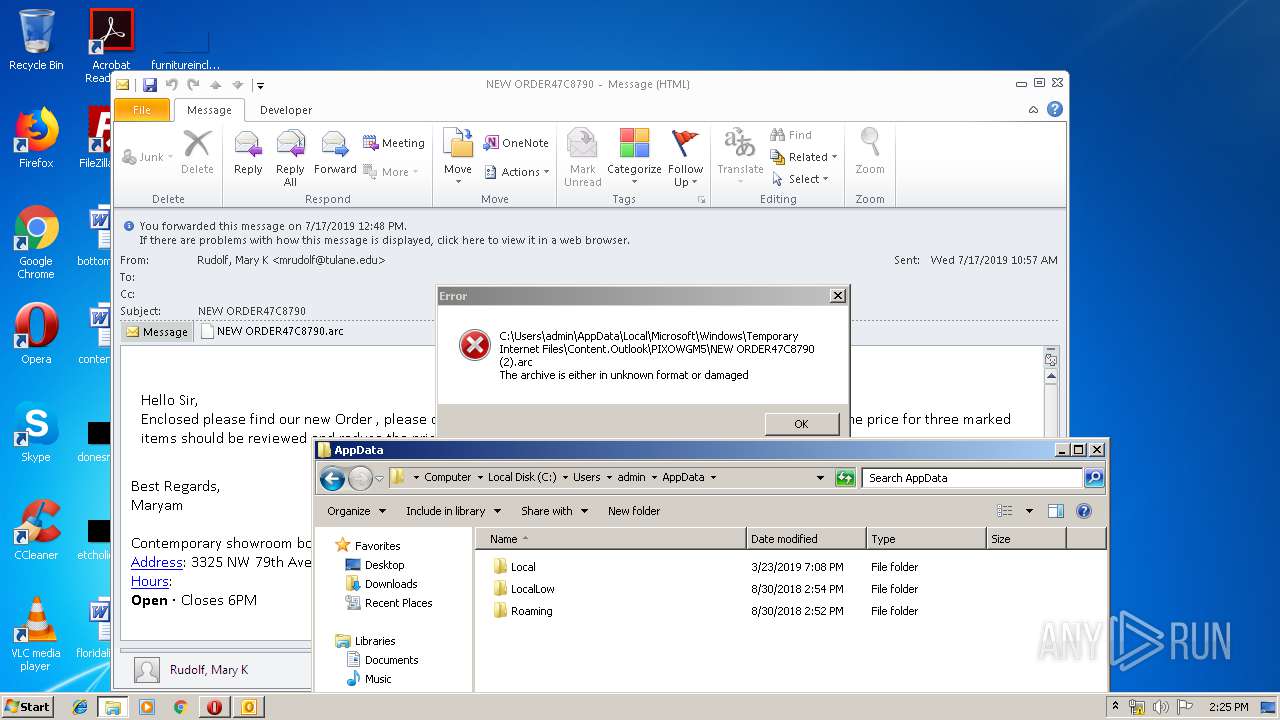
| 3008 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\NEW ORDER47C8790.arc | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1264 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\NEW ORDER47C8790.arc" | C:\Program Files\WinRAR\WinRAR.exe | — | rundll32.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.60.0 Modules
| |||||||||||||||
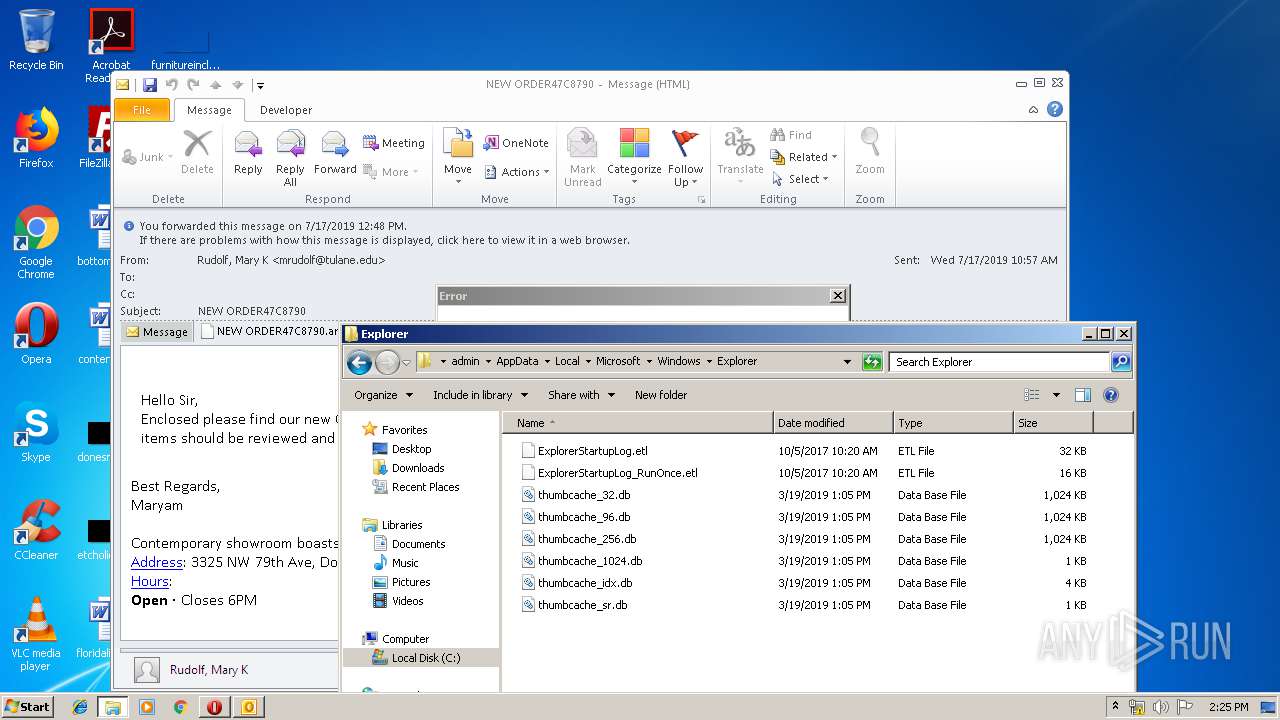
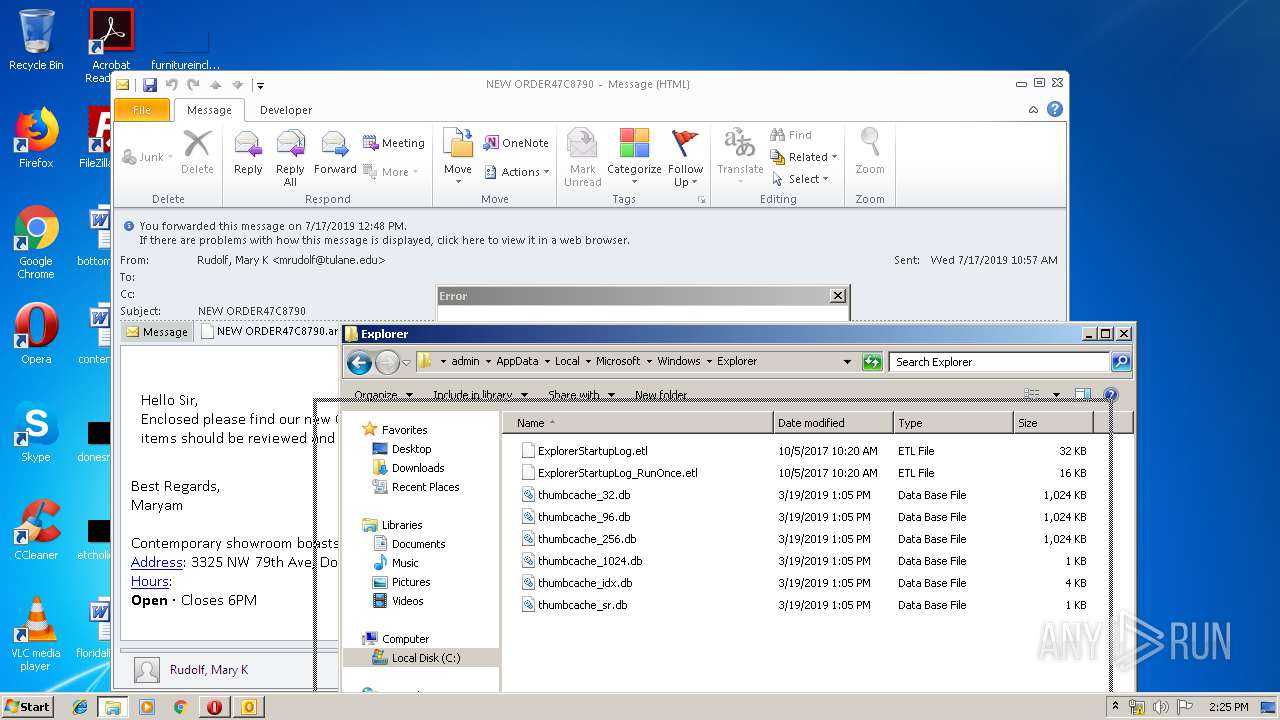
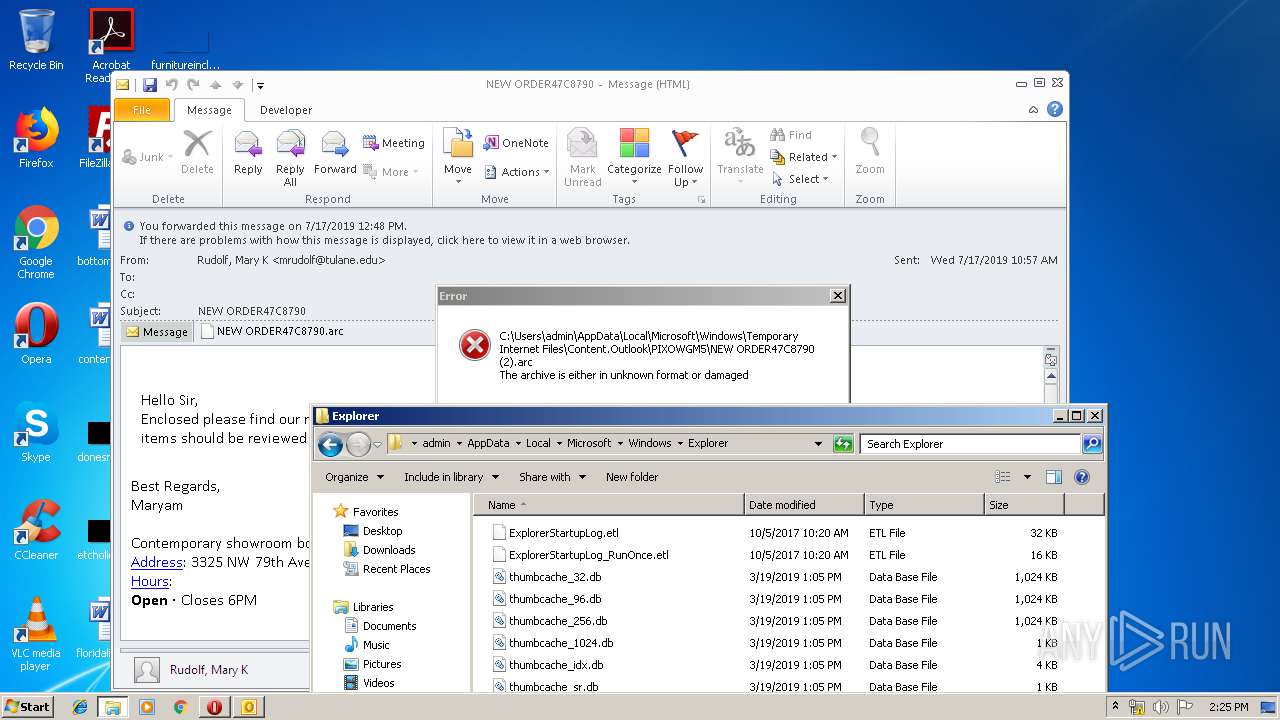
| 2388 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\PIXOWGM5\NEW ORDER47C8790 (2).arc" | C:\Program Files\WinRAR\WinRAR.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.60.0 Modules
| |||||||||||||||
| 2832 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 902
Read events
3 147
Write events
730
Delete events
25
Modification events
| (PID) Process: | (3848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | rx< |
Value: 72783C00080F0000010000000000000000000000 | |||
| (PID) Process: | (3848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 080F0000E227A77AA23CD50100000000 | |||
| (PID) Process: | (3848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220129920 | |||
| (PID) Process: | (3848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3848) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3848) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1324417045 | |||
Executable files
4
Suspicious files
171
Text files
236
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3848 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRF472.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3944 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr3F18.tmp | — | |
MD5:— | SHA256:— | |||
| 3944 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr3F57.tmp | — | |
MD5:— | SHA256:— | |||
| 3944 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 3848 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:6C7712F93FAF417E6556DCEE849B5812 | SHA256:D14D2407CFD27E51F8B3D64AEEB37E69A9AA5D077B7A9C337EE56158CAEDE50A | |||
| 3944 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:AC1143C2489180FB970457DDCBA702FB | SHA256:66BEE16036A6EC2AF18C534EC27EFB7515DD4C09080D3FE906A1D258074B4A75 | |||
| 3944 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:95BEE8C20724EE459EF395889B4D2AEC | SHA256:8DF1C221119102A60C30DE2FB610FC5C68B9FACBBAB9651672F8C6725E71350D | |||
| 3848 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{5D34949B-4CCB-46D2-B4F5-CC445C1E0A38}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:7D80C0A7E3849818695EAF4989186A3C | SHA256:72DC527D78A8E99331409803811CC2D287E812C008A1C869A6AEA69D7A44B597 | |||
| 3848 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_7CB0D5CC18B8C044A023978CF2BAE9BC.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 3944 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:66FBA6DDC0C059CD102C525C281F57AB | SHA256:92D38052D612BCC0F88D3D416ABB37E57A5E5C2CA45C207AC022B62BDD9F1EC3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
474
DNS requests
90
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3848 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
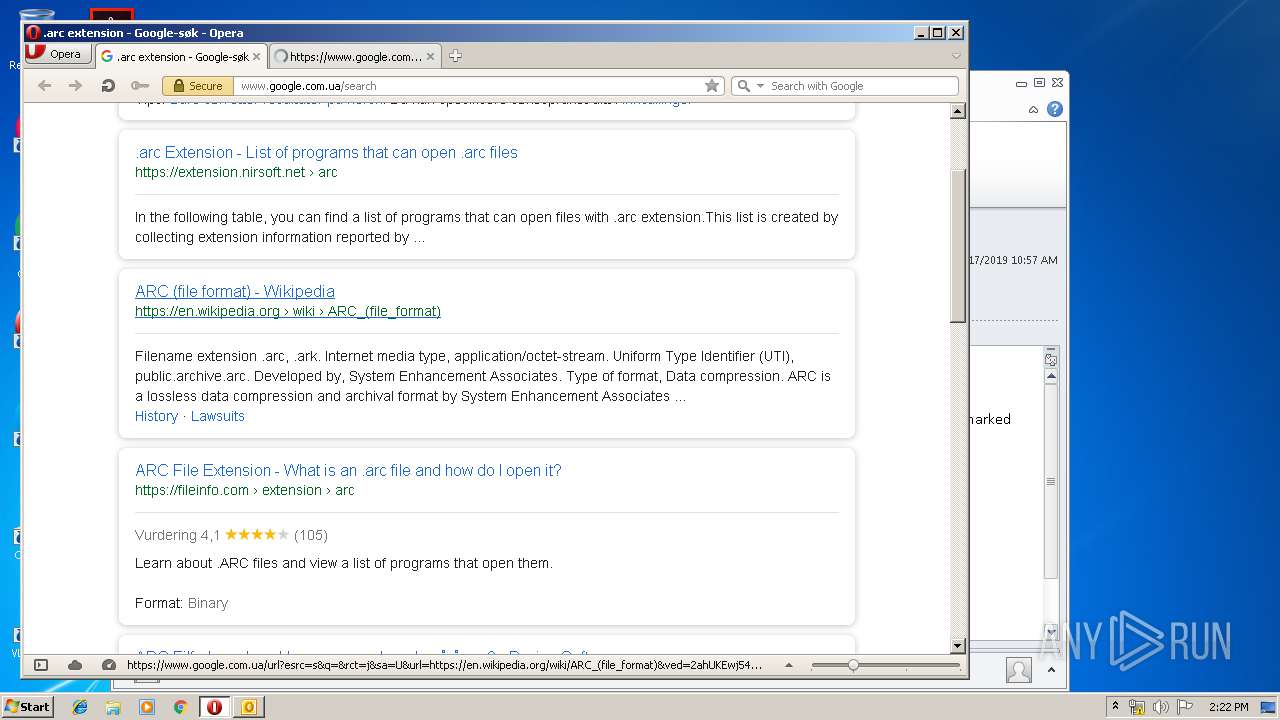
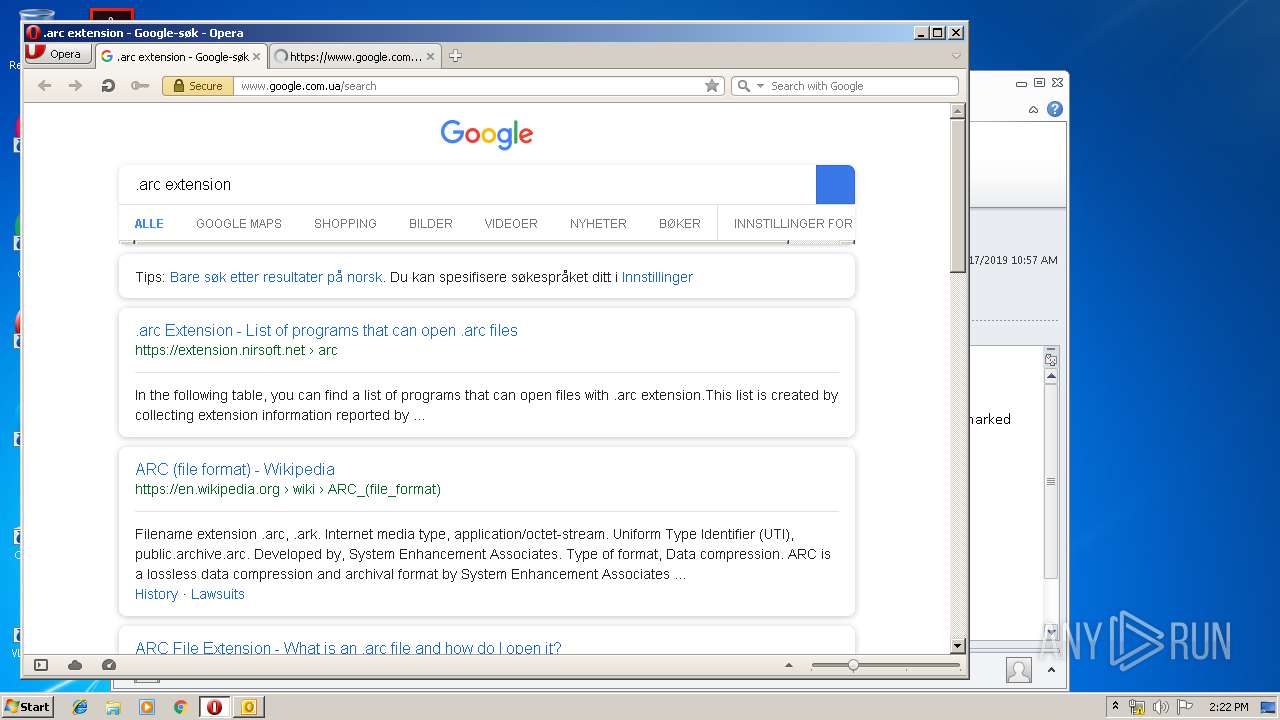
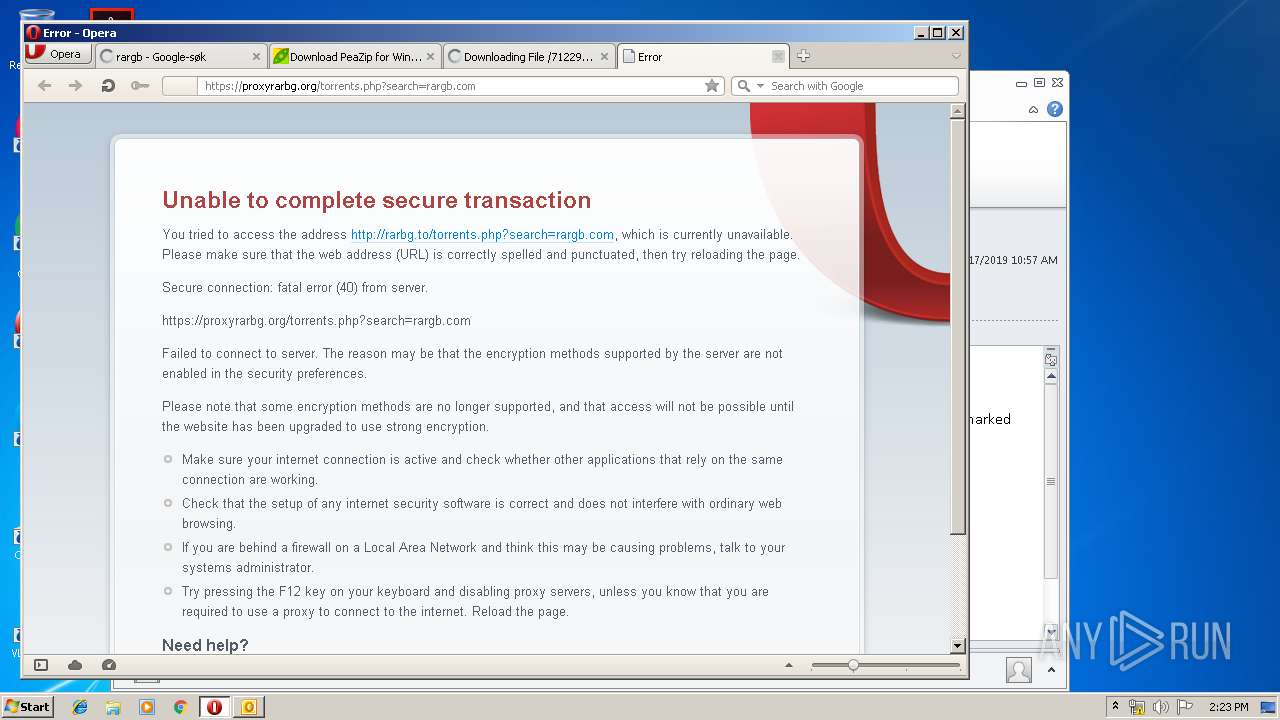
3944 | opera.exe | GET | 302 | 172.217.18.99:80 | http://www.google.com.ua/search?q=.arc+extension&sourceid=opera&ie=utf-8&oe=utf-8&channel=suggest | US | html | 327 b | whitelisted |
3944 | opera.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/GTSGIAG3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCEFitGyxwOiKji%2BOnlrLiyOg%3D | US | der | 471 b | whitelisted |
3944 | opera.exe | GET | 200 | 172.217.22.67:80 | http://crl.pki.goog/gsr2/gsr2.crl | US | der | 546 b | whitelisted |
3944 | opera.exe | GET | 302 | 172.217.18.99:80 | http://www.google.com.ua/search?client=opera&q=.arc+extension&sourceid=opera&ie=utf-8&oe=utf-8&channel=suggest | US | html | 343 b | whitelisted |
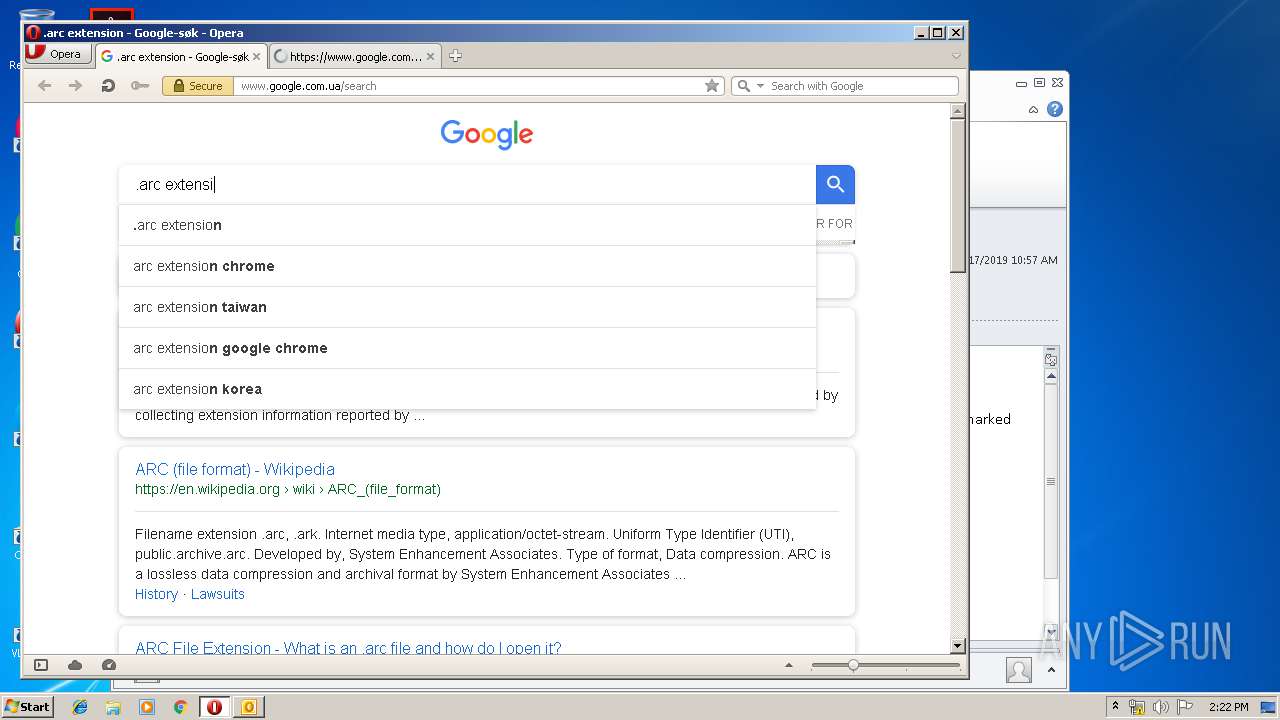
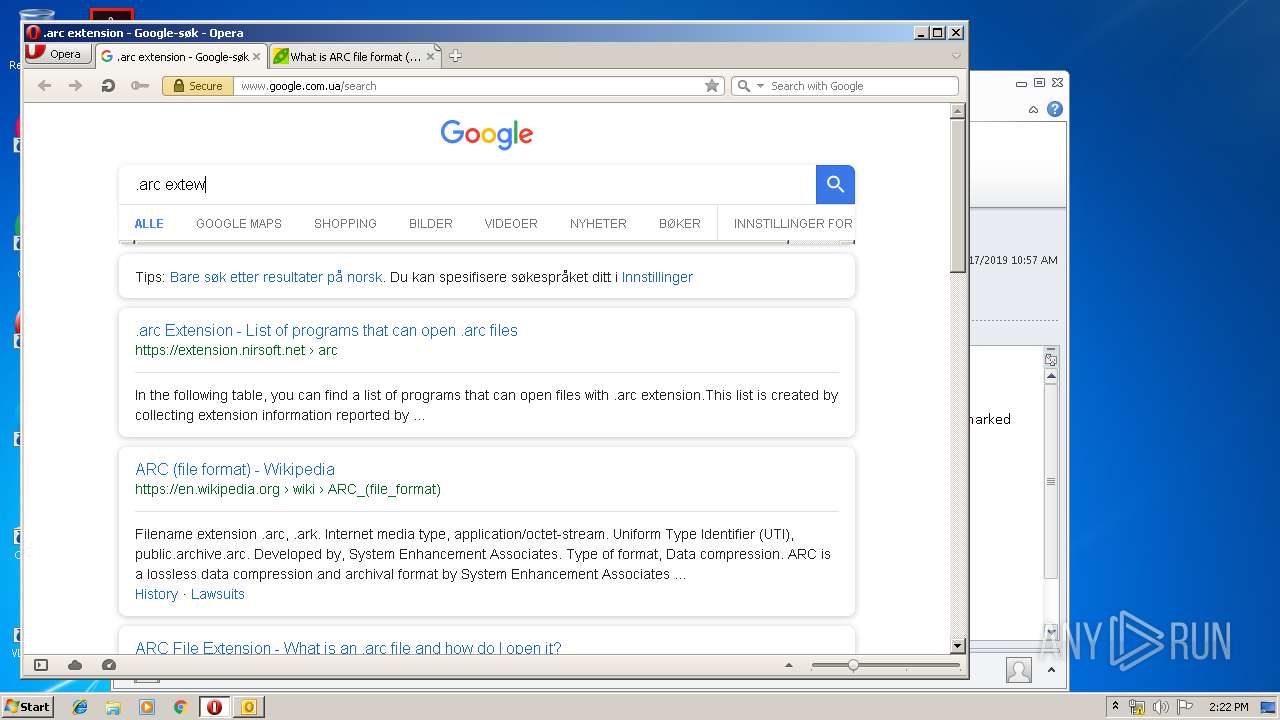
3944 | opera.exe | GET | 200 | 172.217.16.142:80 | http://clients1.google.com/complete/search?q=.arc+exte&client=opera-suggest-omnibox&hl=de | US | text | 110 b | whitelisted |
3944 | opera.exe | GET | 200 | 172.217.16.142:80 | http://clients1.google.com/complete/search?q=.arc&client=opera-suggest-omnibox&hl=de | US | text | 92 b | whitelisted |
3944 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertGlobalRootCA.crl | US | der | 581 b | whitelisted |
3944 | opera.exe | GET | 200 | 172.217.16.142:80 | http://clients1.google.com/complete/search?q=.arc+ex&client=opera-suggest-omnibox&hl=de | US | text | 128 b | whitelisted |
3944 | opera.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/GTSGIAG3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCEElcH9nzCXtybkcrFaERwzo%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3944 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3944 | opera.exe | 172.217.18.99:80 | www.google.com.ua | Google Inc. | US | whitelisted |
3944 | opera.exe | 172.217.16.142:80 | clients1.google.com | Google Inc. | US | whitelisted |
3944 | opera.exe | 172.217.18.99:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3944 | opera.exe | 185.26.182.112:80 | sitecheck2.opera.com | Opera Software AS | — | malicious |
3944 | opera.exe | 172.217.22.67:80 | crl.pki.goog | Google Inc. | US | whitelisted |
3944 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3848 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3944 | opera.exe | 172.217.16.195:443 | id.google.com.ua | Google Inc. | US | whitelisted |
3944 | opera.exe | 172.217.22.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
clients1.google.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
crl.pki.goog |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
id.google.com.ua |
| whitelisted |
id.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3944 | opera.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |