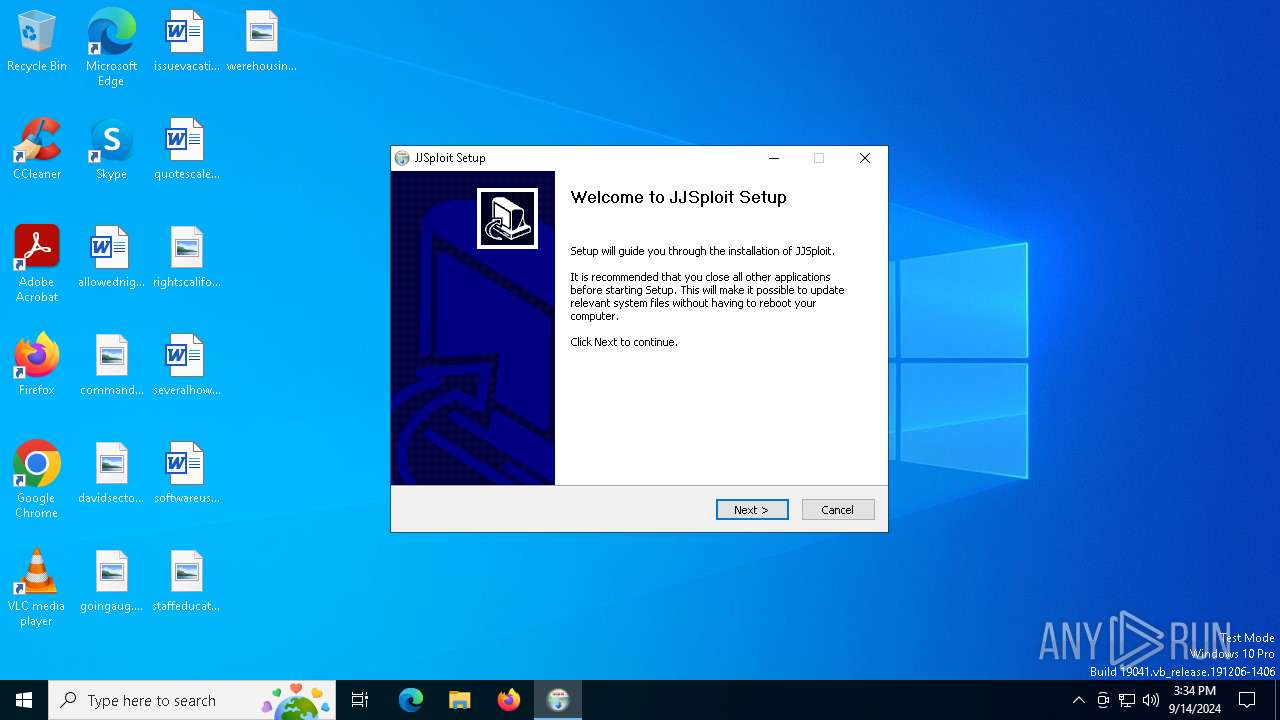
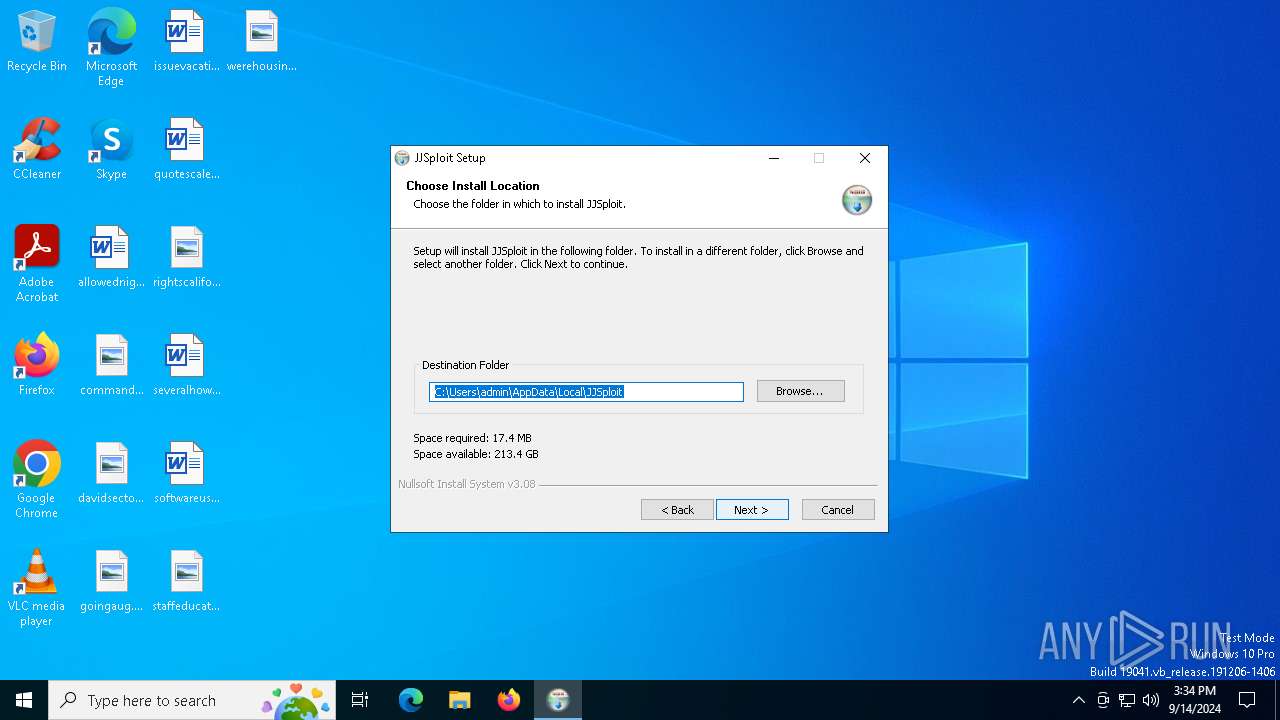
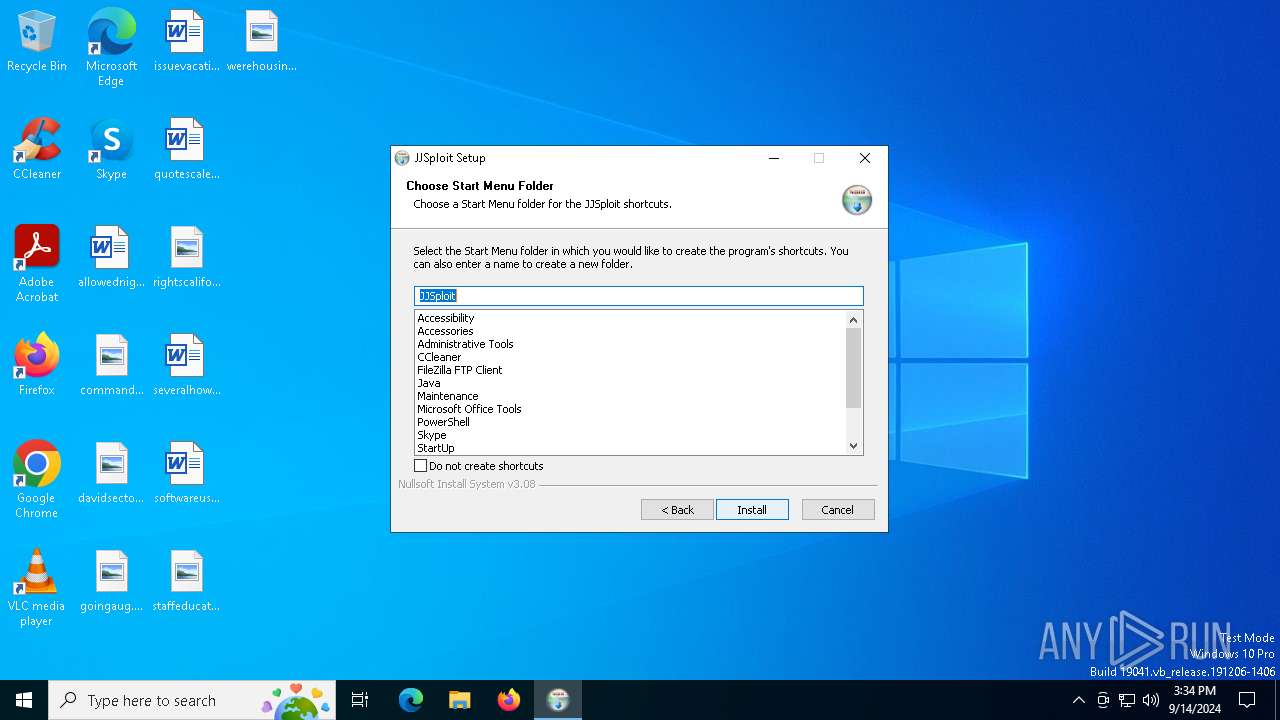
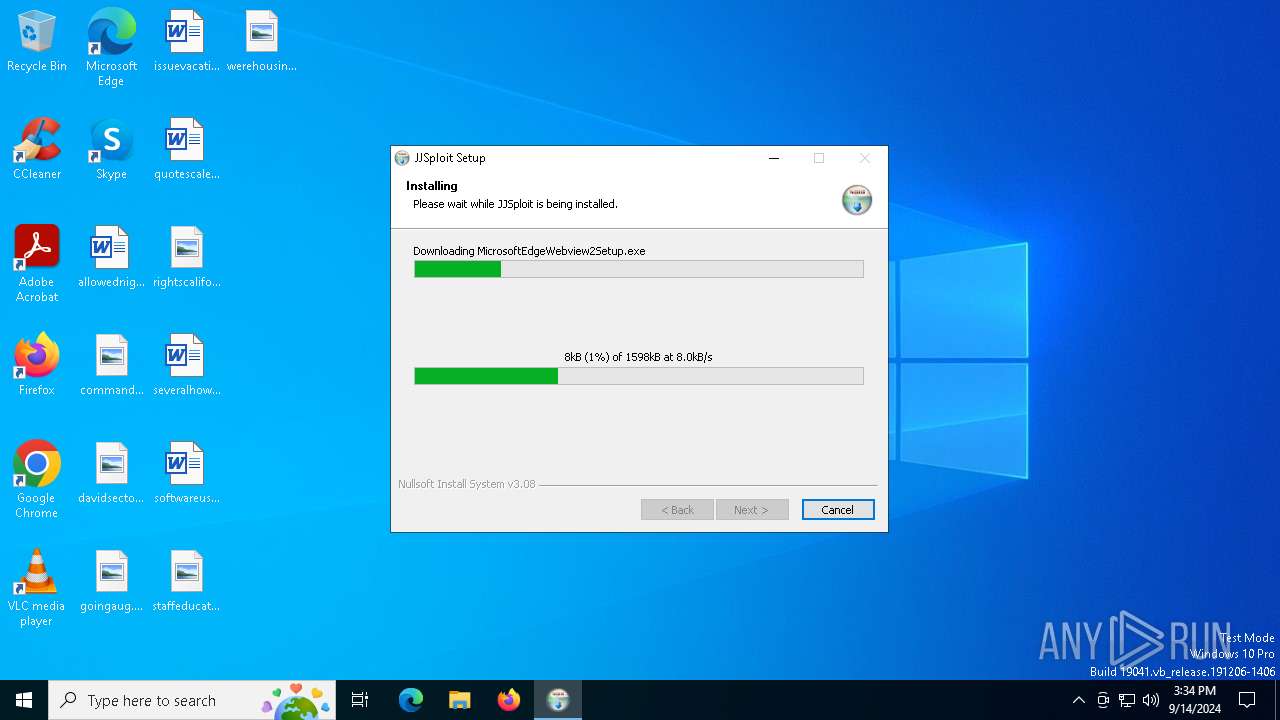
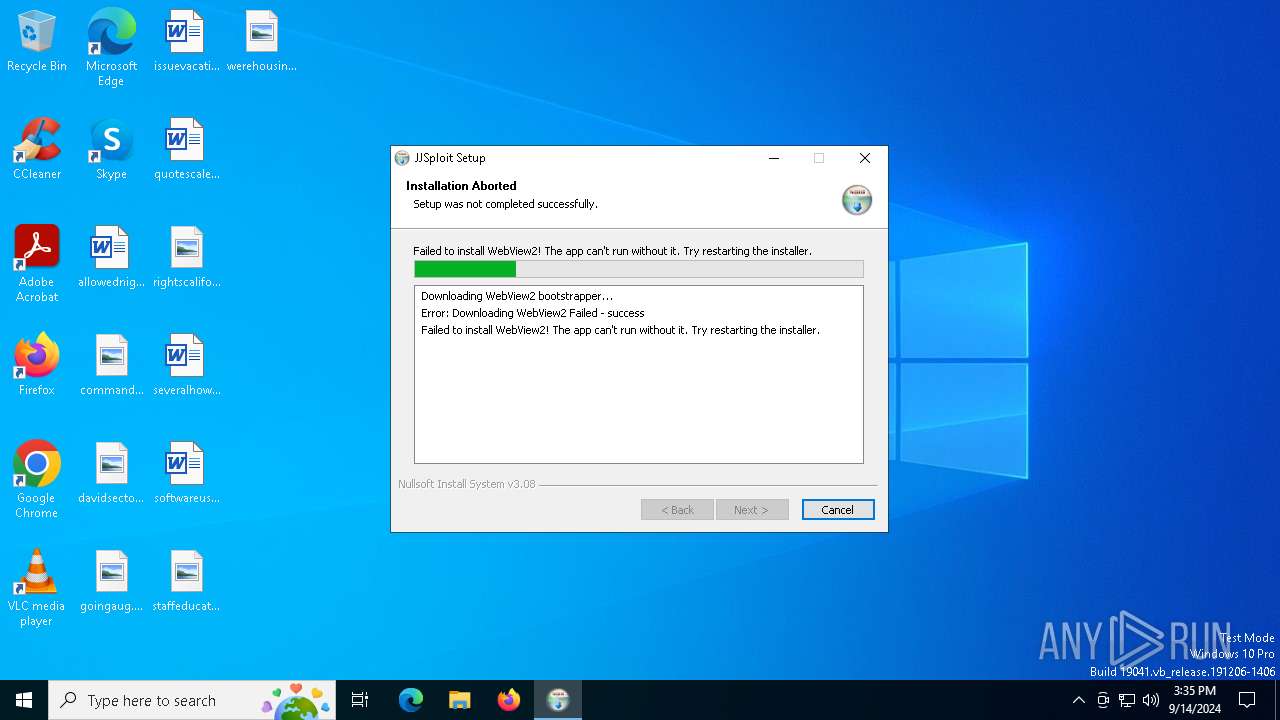
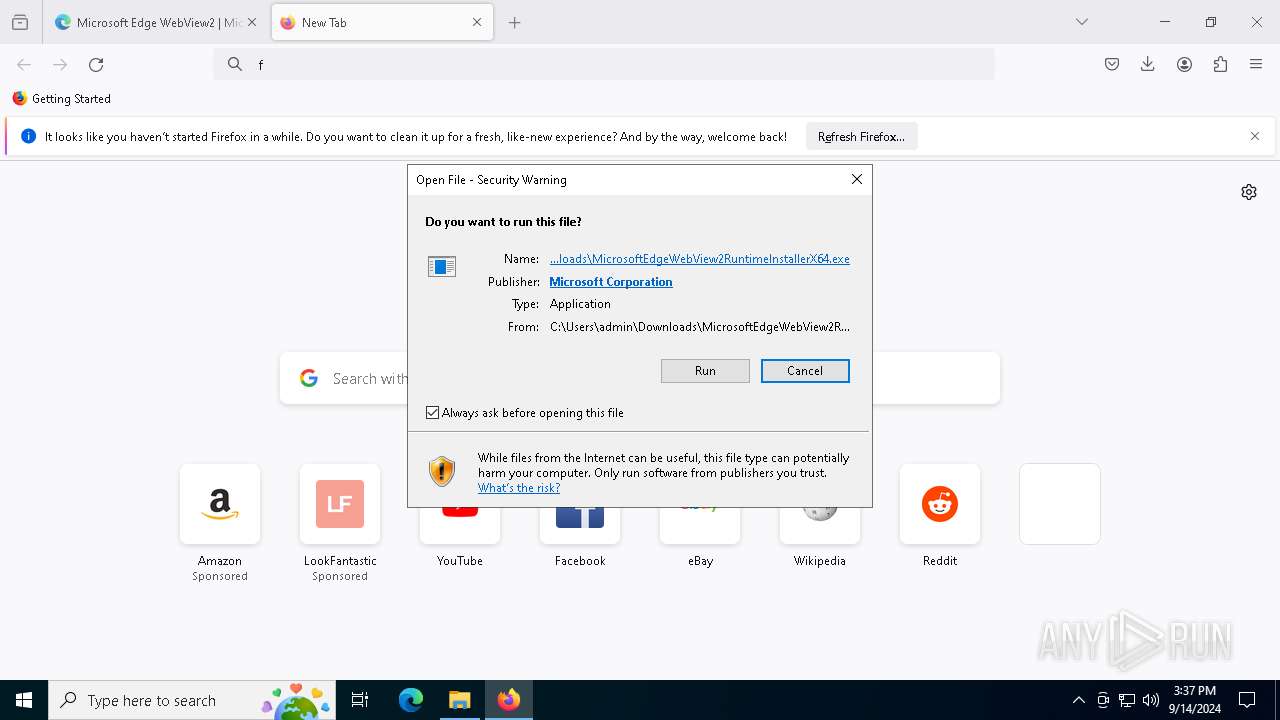
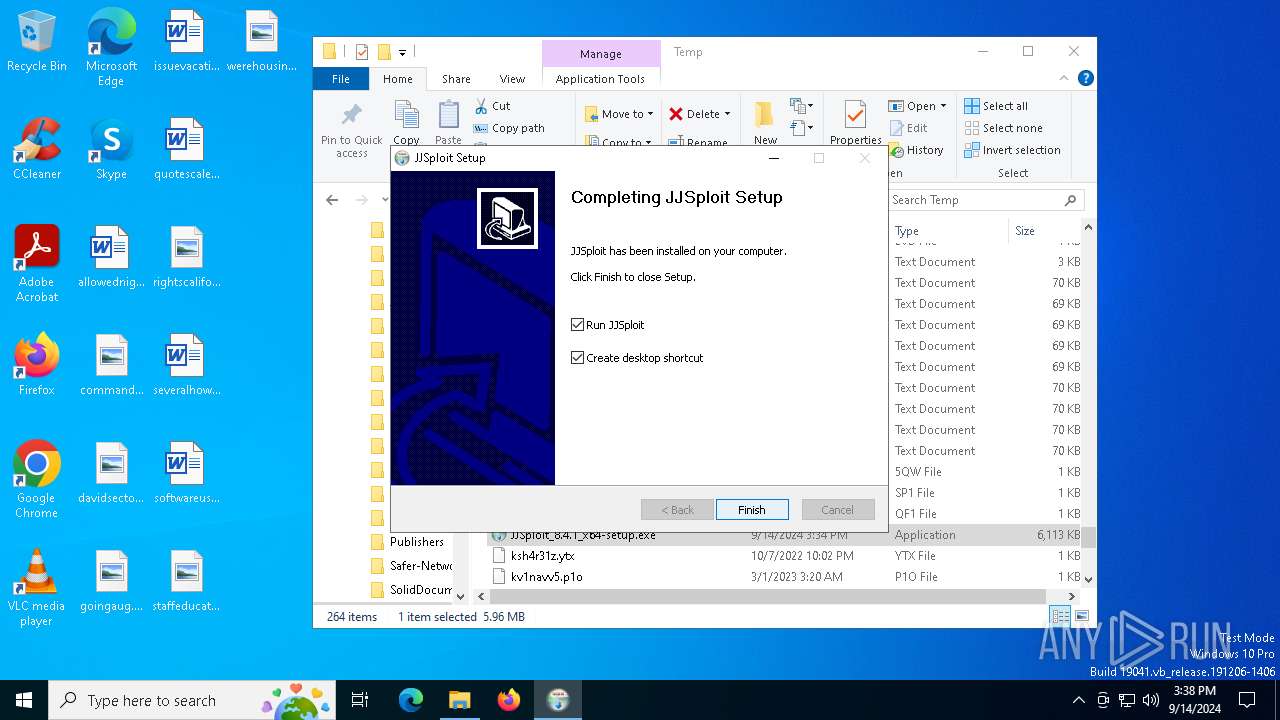
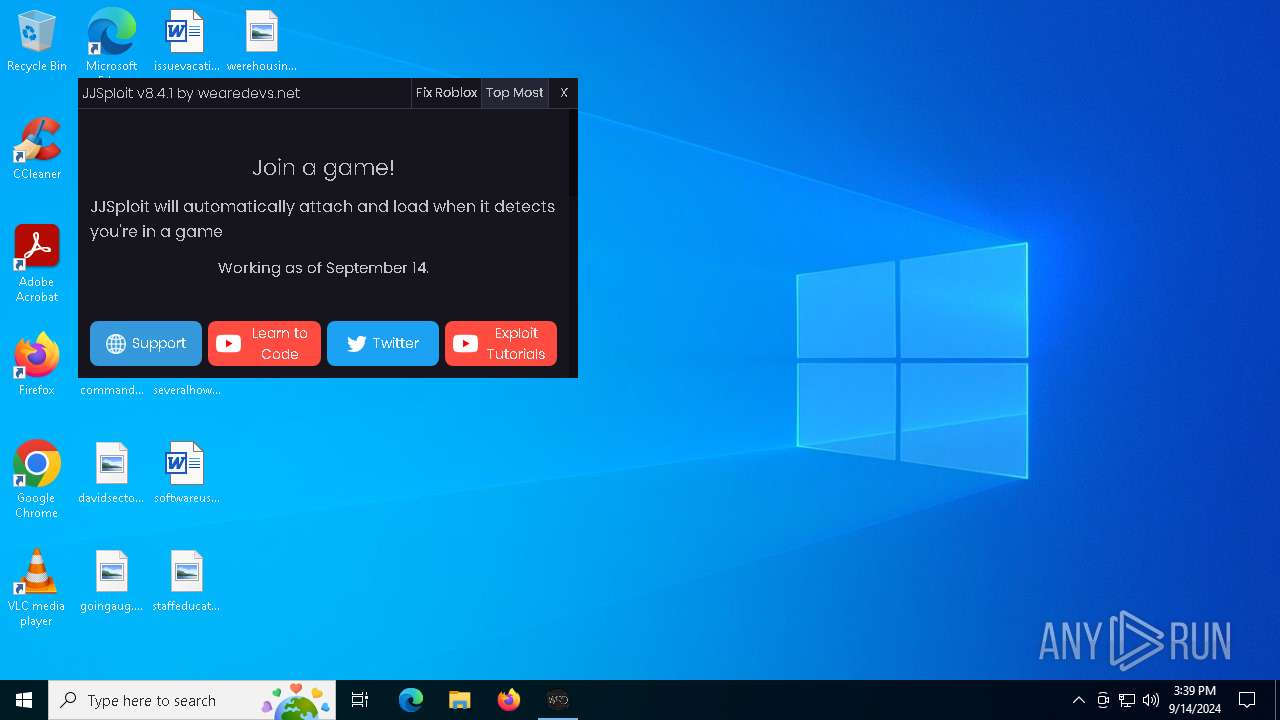
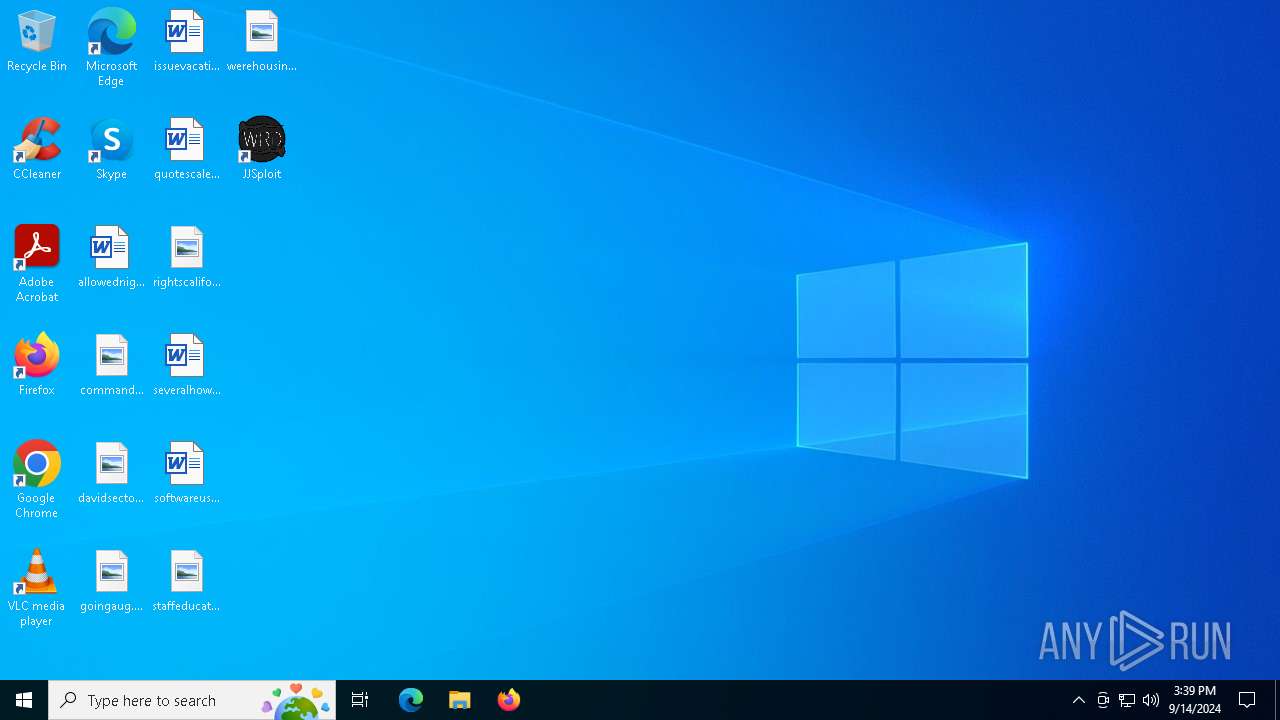
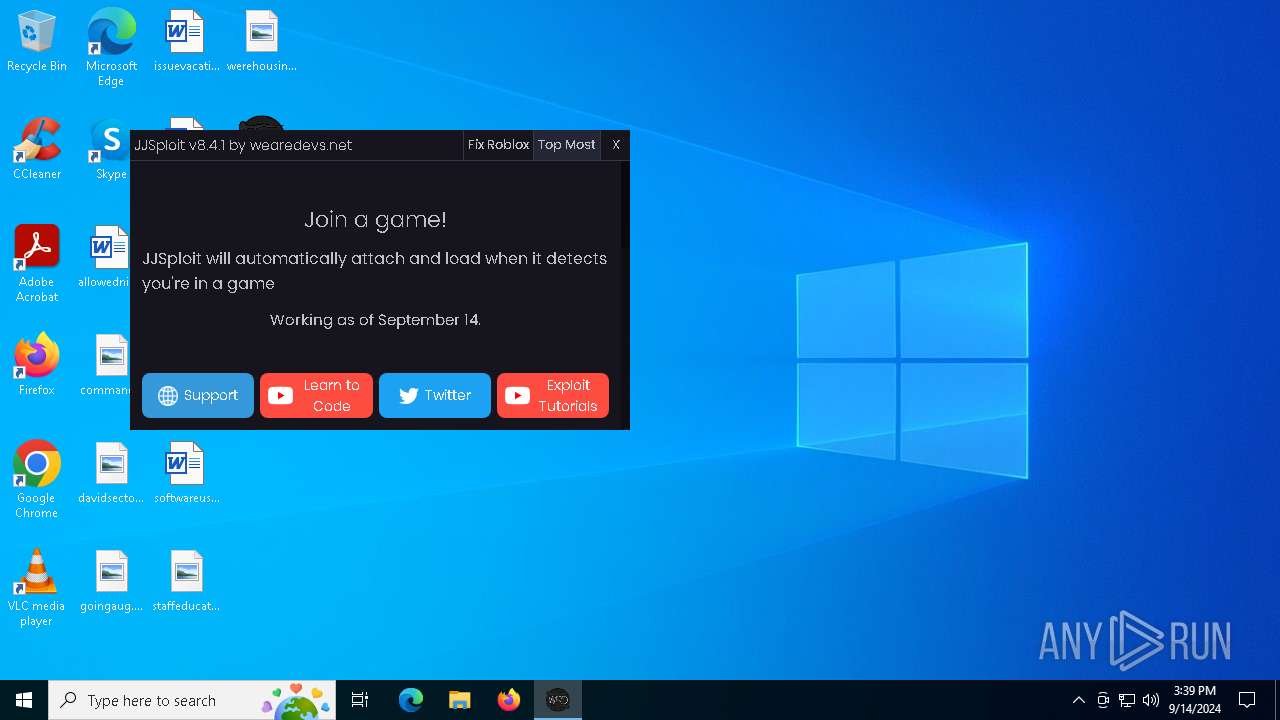
| File name: | JJSploit_8.4.1_x64-setup.exe |
| Full analysis: | https://app.any.run/tasks/08f1d1fb-43b7-4ea6-ac49-ae54e97e5255 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | September 14, 2024, 15:34:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 6818667184B5932F3E4F554ED1075FE8 |
| SHA1: | 59A7A5715BF48D4346EAA4A5CE93A87E15ADAC71 |
| SHA256: | FE43C0DAEBACE84ED84884B877150D609199C13D0BA9254D35A0D305F4F42440 |
| SSDEEP: | 98304:tJ8KYKqEWf288c4Q9muylFR6RKC6RTehf+cKZ8+8/IOaEAvh75fTunrsMxBawg2+:tzpkL+Yi4QGaRsHo |
MALICIOUS
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 6224)
The DLL Hijacking
- msedgewebview2.exe (PID: 7020)
- msedgewebview2.exe (PID: 6288)
SUSPICIOUS
Searches for installed software
- JJSploit_8.4.1_x64-setup.exe (PID: 4284)
- setup.exe (PID: 3980)
- JJSploit_8.4.1_x64-setup.exe (PID: 5524)
Process requests binary or script from the Internet
- JJSploit_8.4.1_x64-setup.exe (PID: 4284)
Potential Corporate Privacy Violation
- JJSploit_8.4.1_x64-setup.exe (PID: 4284)
Executable content was dropped or overwritten
- MicrosoftEdgeUpdate.exe (PID: 6224)
- JJSploit_8.4.1_x64-setup.exe (PID: 4284)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 5032)
- MicrosoftEdgeWebview_X64_128.0.2739.79.exe (PID: 4024)
- JJSploit_8.4.1_x64-setup.exe (PID: 5524)
- setup.exe (PID: 3980)
- JJSploit.exe (PID: 6768)
The process creates files with name similar to system file names
- JJSploit_8.4.1_x64-setup.exe (PID: 4284)
- JJSploit_8.4.1_x64-setup.exe (PID: 5524)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 6224)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6272)
- MicrosoftEdgeUpdate.exe (PID: 6012)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 5740)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2268)
Reads security settings of Internet Explorer
- MicrosoftEdgeUpdate.exe (PID: 6224)
- MicrosoftEdgeUpdate.exe (PID: 5540)
- msedgewebview2.exe (PID: 1776)
- msedgewebview2.exe (PID: 6480)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 6224)
Checks Windows Trust Settings
- MicrosoftEdgeUpdate.exe (PID: 5540)
Application launched itself
- setup.exe (PID: 3980)
- MicrosoftEdgeUpdate.exe (PID: 5540)
- msedgewebview2.exe (PID: 1776)
- msedgewebview2.exe (PID: 6164)
- msedgewebview2.exe (PID: 6480)
Creates a software uninstall entry
- setup.exe (PID: 3980)
- JJSploit_8.4.1_x64-setup.exe (PID: 5524)
Starts CMD.EXE for commands execution
- JJSploit.exe (PID: 6768)
The process checks if it is being run in the virtual environment
- JJSploit.exe (PID: 6768)
- JJSploit.exe (PID: 7508)
- JJSploit.exe (PID: 3784)
INFO
Checks supported languages
- JJSploit_8.4.1_x64-setup.exe (PID: 4284)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 5032)
- MicrosoftEdgeUpdate.exe (PID: 6224)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 5740)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2268)
- MicrosoftEdgeUpdate.exe (PID: 448)
- MicrosoftEdgeUpdate.exe (PID: 6012)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6272)
- MicrosoftEdgeUpdate.exe (PID: 5540)
- MicrosoftEdgeWebview_X64_128.0.2739.79.exe (PID: 4024)
- setup.exe (PID: 3980)
- MicrosoftEdgeUpdate.exe (PID: 6856)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- JJSploit_8.4.1_x64-setup.exe (PID: 5524)
- setup.exe (PID: 4672)
- JJSploit.exe (PID: 6768)
- msedgewebview2.exe (PID: 1776)
- msedgewebview2.exe (PID: 6628)
- msedgewebview2.exe (PID: 7020)
- msedgewebview2.exe (PID: 5220)
- msedgewebview2.exe (PID: 6932)
- msedgewebview2.exe (PID: 1688)
- identity_helper.exe (PID: 4160)
- identity_helper.exe (PID: 8156)
- JJSploit.exe (PID: 7508)
- msedgewebview2.exe (PID: 6164)
- msedgewebview2.exe (PID: 6976)
- msedgewebview2.exe (PID: 6424)
- msedgewebview2.exe (PID: 6480)
- msedgewebview2.exe (PID: 4040)
- msedgewebview2.exe (PID: 6288)
- msedgewebview2.exe (PID: 7272)
- msedgewebview2.exe (PID: 3316)
- JJSploit.exe (PID: 3784)
- msedgewebview2.exe (PID: 1224)
Manual execution by a user
- firefox.exe (PID: 2612)
- JJSploit_8.4.1_x64-setup.exe (PID: 5524)
- JJSploit.exe (PID: 6768)
- JJSploit.exe (PID: 7508)
- JJSploit.exe (PID: 3784)
Reads the computer name
- JJSploit_8.4.1_x64-setup.exe (PID: 4284)
- MicrosoftEdgeUpdate.exe (PID: 6224)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 6272)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 5740)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2268)
- MicrosoftEdgeUpdate.exe (PID: 448)
- MicrosoftEdgeUpdate.exe (PID: 6012)
- MicrosoftEdgeUpdate.exe (PID: 6856)
- MicrosoftEdgeUpdate.exe (PID: 5540)
- MicrosoftEdgeWebview_X64_128.0.2739.79.exe (PID: 4024)
- setup.exe (PID: 3980)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- JJSploit_8.4.1_x64-setup.exe (PID: 5524)
- msedgewebview2.exe (PID: 1776)
- JJSploit.exe (PID: 6768)
- msedgewebview2.exe (PID: 7020)
- msedgewebview2.exe (PID: 6932)
- identity_helper.exe (PID: 4160)
- JJSploit.exe (PID: 7508)
- msedgewebview2.exe (PID: 6164)
- identity_helper.exe (PID: 8156)
- msedgewebview2.exe (PID: 7272)
- msedgewebview2.exe (PID: 6480)
- msedgewebview2.exe (PID: 6288)
- JJSploit.exe (PID: 3784)
Create files in a temporary directory
- JJSploit_8.4.1_x64-setup.exe (PID: 4284)
- MicrosoftEdgeUpdate.exe (PID: 6224)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 5032)
- JJSploit_8.4.1_x64-setup.exe (PID: 5524)
- msedgewebview2.exe (PID: 1776)
- msedgewebview2.exe (PID: 6480)
Checks proxy server information
- JJSploit_8.4.1_x64-setup.exe (PID: 4284)
- MicrosoftEdgeUpdate.exe (PID: 448)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- msedgewebview2.exe (PID: 1776)
- JJSploit.exe (PID: 6768)
- JJSploit.exe (PID: 7508)
- msedgewebview2.exe (PID: 6480)
- JJSploit.exe (PID: 3784)
Application launched itself
- firefox.exe (PID: 2612)
- firefox.exe (PID: 1840)
- msedge.exe (PID: 6996)
- msedge.exe (PID: 7580)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 6224)
- MicrosoftEdgeUpdate.exe (PID: 5540)
- MicrosoftEdgeWebview_X64_128.0.2739.79.exe (PID: 4024)
- setup.exe (PID: 4672)
- setup.exe (PID: 3980)
- JJSploit_8.4.1_x64-setup.exe (PID: 5524)
- msedgewebview2.exe (PID: 1776)
- msedgewebview2.exe (PID: 6628)
- msedgewebview2.exe (PID: 6932)
- JJSploit.exe (PID: 6768)
- msedgewebview2.exe (PID: 6480)
- msedgewebview2.exe (PID: 7272)
The process uses the downloaded file
- firefox.exe (PID: 1840)
- MicrosoftEdgeWebView2RuntimeInstallerX64.exe (PID: 5032)
Executable content was dropped or overwritten
- firefox.exe (PID: 1840)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 448)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- msedgewebview2.exe (PID: 1776)
- identity_helper.exe (PID: 4160)
- identity_helper.exe (PID: 8156)
- msedgewebview2.exe (PID: 6480)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 6224)
- setup.exe (PID: 3980)
- msedgewebview2.exe (PID: 1776)
- msedgewebview2.exe (PID: 1688)
- msedgewebview2.exe (PID: 6976)
- msedgewebview2.exe (PID: 6480)
- msedgewebview2.exe (PID: 1224)
Reads the software policy settings
- MicrosoftEdgeUpdate.exe (PID: 448)
- MicrosoftEdgeUpdate.exe (PID: 5540)
- MicrosoftEdgeUpdate.exe (PID: 6852)
- JJSploit.exe (PID: 6768)
- JJSploit.exe (PID: 7508)
- JJSploit.exe (PID: 3784)
Reads the machine GUID from the registry
- MicrosoftEdgeUpdate.exe (PID: 5540)
- msedgewebview2.exe (PID: 1776)
- msedgewebview2.exe (PID: 6480)
Sends debugging messages
- msedgewebview2.exe (PID: 1776)
- msedgewebview2.exe (PID: 6164)
- msedgewebview2.exe (PID: 6424)
- msedgewebview2.exe (PID: 6480)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:56:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3640 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.4.1.0 |
| ProductVersionNumber: | 8.4.1.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Ulitity for game enhancement |
| FileVersion: | 8.4.1 |
| LegalCopyright: | - |
| ProductName: | JJSploit |
| ProductVersion: | 8.4.1 |
Total processes
231
Monitored processes
100
Malicious processes
16
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /ping PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48cmVxdWVzdCBwcm90b2NvbD0iMy4wIiB1cGRhdGVyPSJPbWFoYSIgdXBkYXRlcnZlcnNpb249IjEuMy4xOTUuMTkiIHNoZWxsX3ZlcnNpb249IjEuMy4xOTUuMTkiIGlzbWFjaGluZT0iMCIgc2Vzc2lvbmlkPSJ7QjdFNTY1NUItOTk3MC00QTk3LTgxNDMtODVCQzZFNUUxNUFCfSIgdXNlcmlkPSJ7RDBGRjlFRjYtOTI4QS00MzRCLTk3ODYtMzMxM0NGOTQyNEFEfSIgaW5zdGFsbHNvdXJjZT0idGFnZ2VkbWkiIHJlcXVlc3RpZD0iezAzMzkwNjJELUVFRkEtNDM4OC04MzNCLUEyRjc0QUNGNTg1Nn0iIGRlZHVwPSJjciIgZG9tYWluam9pbmVkPSIwIj48aHcgbG9naWNhbF9jcHVzPSI0IiBwaHlzbWVtb3J5PSI0IiBkaXNrX3R5cGU9IjIiIHNzZT0iMSIgc3NlMj0iMSIgc3NlMz0iMSIgc3NzZTM9IjEiIHNzZTQxPSIxIiBzc2U0Mj0iMSIgYXZ4PSIxIi8-PG9zIHBsYXRmb3JtPSJ3aW4iIHZlcnNpb249IjEwLjAuMTkwNDUuNDA0NiIgc3A9IiIgYXJjaD0ieDY0IiBwcm9kdWN0X3R5cGU9IjQ4IiBpc193aXA9IjAiIGlzX2luX2xvY2tkb3duX21vZGU9IjAiLz48b2VtIHByb2R1Y3RfbWFudWZhY3R1cmVyPSJERUxMIiBwcm9kdWN0X25hbWU9IkRFTEwiLz48ZXhwIGV0YWc9IiIvPjxhcHAgYXBwaWQ9IntGM0M0RkUwMC1FRkQ1LTQwM0ItOTU2OS0zOThBMjBGMUJBNEF9IiB2ZXJzaW9uPSIiIG5leHR2ZXJzaW9uPSIxLjMuMTk1LjE5IiBsYW5nPSIiIGJyYW5kPSIiIGNsaWVudD0iIj48ZXZlbnQgZXZlbnR0eXBlPSIyIiBldmVudHJlc3VsdD0iMSIgZXJyb3Jjb2RlPSIwIiBleHRyYWNvZGUxPSIwIiBzeXN0ZW1fdXB0aW1lX3RpY2tzPSIxNDE0NTMzNDg5NSIgaW5zdGFsbF90aW1lX21zPSI3ODEiLz48L2FwcD48L3JlcXVlc3Q- | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | MicrosoftEdgeUpdate.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.19 Modules
| |||||||||||||||
| 740 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://www.youtube.com/@WeAreDevsExploits | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x300,0x304,0x308,0x2f0,0x350,0x7fffd2c45fd8,0x7fffd2c45fe4,0x7fffd2c45ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 964 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2292 -parentBuildID 20240213221259 -prefsHandle 2284 -prefMapHandle 2272 -prefsLen 30537 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {bc18ffd1-e0d3-43a5-bc3c-8821517a91d1} 1840 "\\.\pipe\gecko-crash-server-pipe.1840" 248f4d7f910 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1224 | "C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\128.0.2739.79\msedgewebview2.exe" --type=renderer --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\net.wearedevs\EBWebView" --webview-exe-name=JJSploit.exe --webview-exe-version=8.4.1 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=2 --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --js-flags="--harmony-weak-refs-with-cleanup-some --expose-gc --ms-user-locale=" --field-trial-handle=3472,i,6051416706541561899,7346808288273675675,262144 --enable-features=MojoIpcz --disable-features=msPdfOOUI,msSmartScreenProtection,msWebOOUI --variations-seed-version --mojo-platform-channel-handle=3492 /prefetch:1 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\128.0.2739.79\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Version: 128.0.2739.79 Modules
| |||||||||||||||
| 1292 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5472 --field-trial-handle=2328,i,16905321161187040011,16808875228029119787,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1496 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5580 --field-trial-handle=2328,i,16905321161187040011,16808875228029119787,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1680 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1688 | "C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\128.0.2739.79\msedgewebview2.exe" --type=renderer --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\net.wearedevs\EBWebView" --webview-exe-name=JJSploit.exe --webview-exe-version=8.4.1 --embedded-browser-webview=1 --embedded-browser-webview-dpi-awareness=2 --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --js-flags="--harmony-weak-refs-with-cleanup-some --expose-gc --ms-user-locale=" --field-trial-handle=3376,i,1838664330931510092,17690955226238807964,262144 --enable-features=MojoIpcz --disable-features=msPdfOOUI,msSmartScreenProtection,msWebOOUI --variations-seed-version --mojo-platform-channel-handle=3404 /prefetch:1 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\128.0.2739.79\msedgewebview2.exe | — | msedgewebview2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge WebView2 Exit code: 0 Version: 128.0.2739.79 Modules
| |||||||||||||||
| 1776 | "C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\128.0.2739.79\msedgewebview2.exe" --embedded-browser-webview=1 --webview-exe-name=JJSploit.exe --webview-exe-version=8.4.1 --user-data-dir="C:\Users\admin\AppData\Local\net.wearedevs\EBWebView" --noerrdialogs --embedded-browser-webview-dpi-awareness=2 --disable-features=msWebOOUI,msPdfOOUI,msSmartScreenProtection --enable-features=MojoIpcz --lang=en-US --mojo-named-platform-channel-pipe=6768.3292.5360649583903876778 | C:\Users\admin\AppData\Local\Microsoft\EdgeWebView\Application\128.0.2739.79\msedgewebview2.exe | JJSploit.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge WebView2 Exit code: 0 Version: 128.0.2739.79 Modules
| |||||||||||||||
Total events
39 941
Read events
38 686
Write events
1 187
Delete events
68
Modification events
| (PID) Process: | (1840) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (1840) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6224) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | delete value | Name: | eulaaccepted |
Value: | |||
| (PID) Process: | (6224) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | path |
Value: C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | |||
| (PID) Process: | (6224) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | UninstallCmdLine |
Value: "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /uninstall | |||
| (PID) Process: | (6224) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{F3C4FE00-EFD5-403B-9569-398A20F1BA4A} |
| Operation: | write | Name: | pv |
Value: 1.3.195.19 | |||
| (PID) Process: | (6224) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{F3C4FE00-EFD5-403B-9569-398A20F1BA4A} |
| Operation: | write | Name: | name |
Value: Microsoft Edge Update | |||
| (PID) Process: | (6224) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{F3C4FE00-EFD5-403B-9569-398A20F1BA4A} |
| Operation: | write | Name: | pv |
Value: 1.3.195.19 | |||
| (PID) Process: | (6224) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Microsoft Edge Update |
Value: "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.19\MicrosoftEdgeUpdateCore.exe" | |||
| (PID) Process: | (6224) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate |
| Operation: | write | Name: | edgeupdate_task_name_c |
Value: MicrosoftEdgeUpdateTaskUserS-1-5-21-1693682860-607145093-2874071422-1001Core{417BC66A-7061-4C32-8329-F105A08D471B} | |||
Executable files
228
Suspicious files
723
Text files
206
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1840 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4284 | JJSploit_8.4.1_x64-setup.exe | C:\Users\admin\AppData\Local\Temp\nsx9E6D.tmp\nsDialogs.dll | executable | |
MD5:6C3F8C94D0727894D706940A8A980543 | SHA256:56B96ADD1978B1ABBA286F7F8982B0EFBE007D4A48B3DED6A4D408E01D753FE2 | |||
| 4284 | JJSploit_8.4.1_x64-setup.exe | C:\Users\admin\AppData\Local\Temp\nsx9E6D.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 4284 | JJSploit_8.4.1_x64-setup.exe | C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe | executable | |
MD5:D2EBD82A5D3FAC11D44D90D8DF253BB9 | SHA256:04B65AA7B23D0C7EBBD6E022A600FBC43C0EE896ED280E48AC59E17FB0A2311D | |||
| 1840 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4284 | JJSploit_8.4.1_x64-setup.exe | C:\Users\admin\AppData\Local\Temp\nsx9E6D.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 4284 | JJSploit_8.4.1_x64-setup.exe | C:\Users\admin\AppData\Local\Temp\nsx9E6D.tmp\StartMenu.dll | executable | |
MD5:D070F3275DF715BF3708BEFF2C6C307D | SHA256:42DD4DDA3249A94E32E20F76EAFFAE784A5475ED00C60EF0197C8A2C1CCD2FB7 | |||
| 4284 | JJSploit_8.4.1_x64-setup.exe | C:\Users\admin\AppData\Local\Temp\nsx9E6D.tmp\NSISdl.dll | executable | |
MD5:EE68463FED225C5C98D800BDBD205598 | SHA256:419485A096BC7D95F872ED1B9B7B5C537231183D710363BEEE4D235BB79DBE04 | |||
| 1840 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 4284 | JJSploit_8.4.1_x64-setup.exe | C:\Users\admin\AppData\Local\Temp\nsx9E6C.tmp | binary | |
MD5:FD269B87F303E35F60DE13238D4A6FD8 | SHA256:43A2786A8470536B9F1033F9877C0969B51BCC390EF2BAEA8C1D9D10A9E8BE74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
209
DNS requests
250
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6052 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4284 | JJSploit_8.4.1_x64-setup.exe | GET | 301 | 69.192.162.125:80 | http://go.microsoft.com/fwlink/p/?LinkId=2124703 | unknown | — | — | whitelisted |
4284 | JJSploit_8.4.1_x64-setup.exe | GET | 200 | 152.199.21.175:80 | http://msedge.sf.dl.delivery.mp.microsoft.com/filestreamingservice/files/657da03c-2d6c-4d00-893f-d6c129225760/MicrosoftEdgeWebview2Setup.exe | unknown | — | — | whitelisted |
1404 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6596 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6596 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1840 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1840 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1840 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
1840 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6052 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6652 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6052 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6052 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4284 | JJSploit_8.4.1_x64-setup.exe | 69.192.162.125:80 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
4284 | JJSploit_8.4.1_x64-setup.exe | 152.199.21.175:80 | msedge.sf.dl.delivery.mp.microsoft.com | EDGECAST | DE | whitelisted |
1404 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1404 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
msedge.sf.dl.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4284 | JJSploit_8.4.1_x64-setup.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
4 ETPRO signatures available at the full report
Process | Message |
|---|---|
msedgewebview2.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\net.wearedevs directory exists )
|
msedgewebview2.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\net.wearedevs\EBWebView directory exists )
|
msedgewebview2.exe | [0914/153932.649:ERROR:exception_handler_server.cc(529)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|
msedgewebview2.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\net.wearedevs\EBWebView directory exists )
|