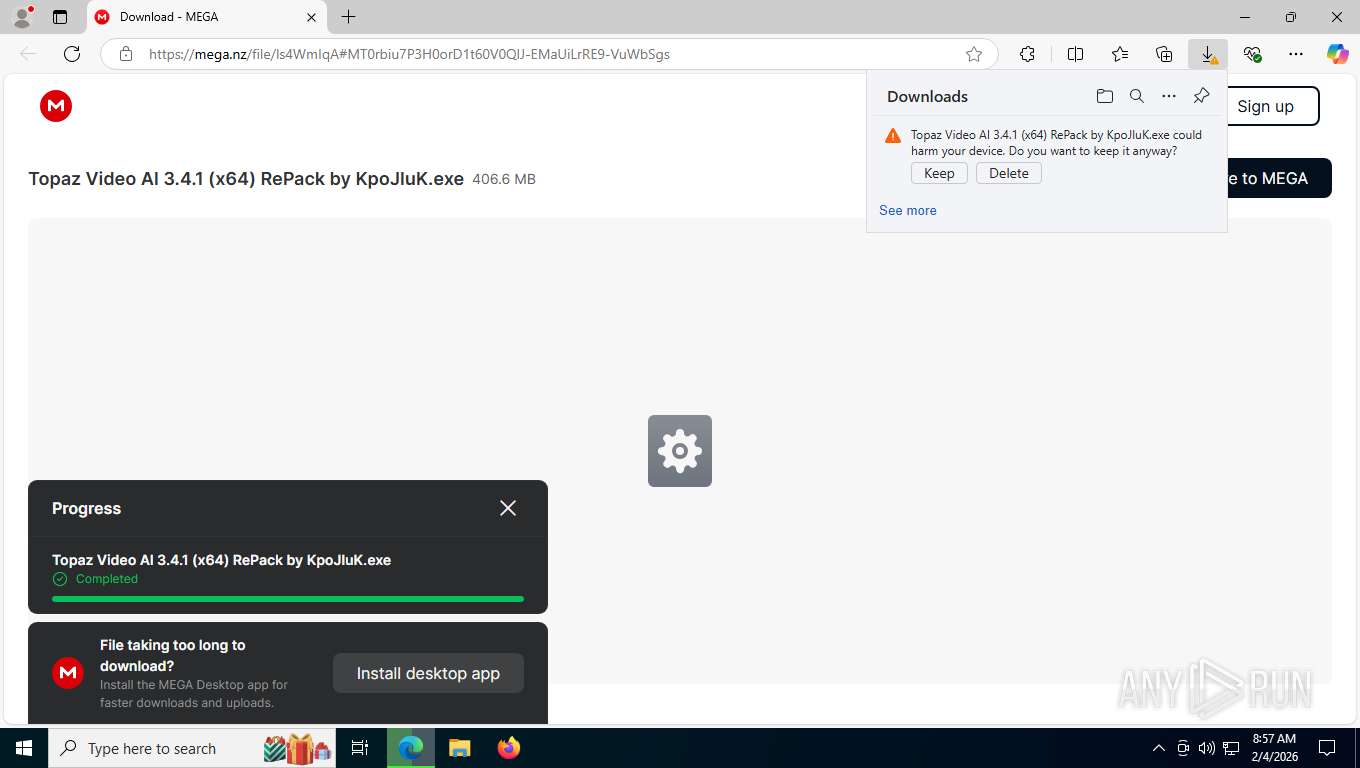
| URL: | https://mega.nz/file/ls4WmIqA#MT0rbiu7P3H0orD1t60V0QlJ-EMaUiLrRE9-VuWbSgs |
| Full analysis: | https://app.any.run/tasks/fa92a598-8cb7-4b53-bf19-eb780a7eafa3 |
| Verdict: | Suspicious activity |
| Analysis date: | February 04, 2026, 13:56:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 534CAD3D2601CD0ADE6F87DE17F9E024 |
| SHA1: | 95DF830AF0CF4EB9E6E159AF93566ABB7FB9FF9A |
| SHA256: | FE4096130E24A436ED87D55920555858A49F6AAA89C96FBDDBCEB33EA333A6B1 |
| SSDEEP: | 3:N8X/iFbs9GoI18QnQid:2rTQnP |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe (PID: 6108)
Application launched itself
- msiexec.exe (PID: 3400)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3400)
Process drops legitimate windows executable
- msiexec.exe (PID: 3400)
- Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe (PID: 6108)
Executable content was dropped or overwritten
- Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe (PID: 6108)
INFO
Checks supported languages
- identity_helper.exe (PID: 2600)
- msiexec.exe (PID: 8760)
- msiexec.exe (PID: 5876)
- msiexec.exe (PID: 3400)
- msiexec.exe (PID: 9072)
- msiexec.exe (PID: 4552)
- Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe (PID: 6108)
- crashpad_handler.exe (PID: 5632)
- Topaz Video AI.exe (PID: 684)
- login.exe (PID: 5152)
Reads Environment values
- identity_helper.exe (PID: 2600)
Executable content was dropped or overwritten
- msedge.exe (PID: 8508)
- msiexec.exe (PID: 412)
- msiexec.exe (PID: 3400)
Reads the computer name
- Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe (PID: 6108)
- msiexec.exe (PID: 8760)
- msiexec.exe (PID: 5876)
- msiexec.exe (PID: 3400)
- identity_helper.exe (PID: 2600)
- msiexec.exe (PID: 9072)
- msiexec.exe (PID: 4552)
- Topaz Video AI.exe (PID: 684)
- login.exe (PID: 5152)
Drops script file
- msedge.exe (PID: 7660)
Create files in a temporary directory
- Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe (PID: 6108)
- crashpad_handler.exe (PID: 5632)
- Topaz Video AI.exe (PID: 684)
There is functionality for taking screenshot (YARA)
- Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe (PID: 6108)
Process checks computer location settings
- Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe (PID: 6108)
- Topaz Video AI.exe (PID: 684)
The sample compiled with english language support
- Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe (PID: 6108)
- msedge.exe (PID: 8508)
- msiexec.exe (PID: 3400)
Reads security settings of Internet Explorer
- Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe (PID: 6108)
- Topaz Video AI.exe (PID: 684)
Checks proxy server information
- slui.exe (PID: 3332)
- Topaz Video AI.exe (PID: 684)
Application launched itself
- msedge.exe (PID: 8508)
Creates files or folders in the user directory
- Topaz Video AI.exe (PID: 684)
Manual execution by a user
- Topaz Video AI.exe (PID: 684)
Creates a software uninstall entry
- msiexec.exe (PID: 3400)
Reads the machine GUID from the registry
- Topaz Video AI.exe (PID: 684)
Creates files in the program directory
- Topaz Video AI.exe (PID: 684)
Reads the time zone
- Topaz Video AI.exe (PID: 684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
197
Monitored processes
46
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 412 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\RarSFX0\TopazVideoAI.msi" | C:\Windows\SysWOW64\msiexec.exe | Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 524 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6172,i,17884192079930246301,11980256953646476130,262144 --disable-features=HttpsFirstBalancedMode,HttpsFirstModeV2,HttpsOnlyMode,HttpsUpgrades --variations-seed-version --mojo-platform-channel-handle=6176 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 684 | "C:\Program Files\Topaz Labs LLC\Topaz Video AI\Topaz Video AI.exe" | C:\Program Files\Topaz Labs LLC\Topaz Video AI\Topaz Video AI.exe | explorer.exe | ||||||||||||
User: admin Company: Topaz Labs Integrity Level: MEDIUM Description: Topaz Video AI Exit code: 0 Version: 3,4,1,0 Modules
| |||||||||||||||
| 1180 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=6820,i,17884192079930246301,11980256953646476130,262144 --disable-features=HttpsFirstBalancedMode,HttpsFirstModeV2,HttpsOnlyMode,HttpsUpgrades --variations-seed-version --mojo-platform-channel-handle=7108 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1324 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6812,i,17884192079930246301,11980256953646476130,262144 --disable-features=HttpsFirstBalancedMode,HttpsFirstModeV2,HttpsOnlyMode,HttpsUpgrades --variations-seed-version --mojo-platform-channel-handle=6868 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1432 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5436,i,17884192079930246301,11980256953646476130,262144 --disable-features=HttpsFirstBalancedMode,HttpsFirstModeV2,HttpsOnlyMode,HttpsUpgrades --variations-seed-version --mojo-platform-channel-handle=6476 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1876 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4224,i,17884192079930246301,11980256953646476130,262144 --disable-features=HttpsFirstBalancedMode,HttpsFirstModeV2,HttpsOnlyMode,HttpsUpgrades --variations-seed-version --mojo-platform-channel-handle=4228 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2392 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --pdf-upsell-enabled --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=3 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3576,i,17884192079930246301,11980256953646476130,262144 --disable-features=HttpsFirstBalancedMode,HttpsFirstModeV2,HttpsOnlyMode,HttpsUpgrades --variations-seed-version --mojo-platform-channel-handle=3604 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2424 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=7572,i,17884192079930246301,11980256953646476130,262144 --disable-features=HttpsFirstBalancedMode,HttpsFirstModeV2,HttpsOnlyMode,HttpsUpgrades --variations-seed-version --mojo-platform-channel-handle=7136 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2600 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6272,i,17884192079930246301,11980256953646476130,262144 --disable-features=HttpsFirstBalancedMode,HttpsFirstModeV2,HttpsOnlyMode,HttpsUpgrades --variations-seed-version --mojo-platform-channel-handle=6212 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
16 837
Read events
15 527
Write events
1 292
Delete events
18
Modification events
| (PID) Process: | (412) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (412) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (412) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (412) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6108) Topaz Video AI 3.4.1 (x64) RePack by KpoJIuK.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.msi\OpenWithProgids |
| Operation: | write | Name: | Msi.Package |
Value: | |||
| (PID) Process: | (3400) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 480D00001394775CDE95DC01 | |||
| (PID) Process: | (3400) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: AAFCA3910139006C7C17EF9EA5D34E0560319F0552C7D03B2A274E2BA786CDA6 | |||
| (PID) Process: | (3400) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\C5EF2165D3502D95CB436D3FA72486B3 |
| Operation: | write | Name: | AA62829AD021B1047962770EC5E416E8 |
Value: C:\Program Files\Topaz Labs LLC\Topaz Video AI\Qt6QuickDialogs2.dll | |||
| (PID) Process: | (3400) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Components\A7C93EABB760DC654AE4188FCABCF227 |
| Operation: | write | Name: | AA62829AD021B1047962770EC5E416E8 |
Value: C:\Program Files\Topaz Labs LLC\Topaz Video AI\Qt6QuickDialogs2QuickImpl.dll | |||
Executable files
275
Suspicious files
451
Text files
1 456
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF1e52c1.TMP | — | |
MD5:— | SHA256:— | |||
| 8508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1e52d1.TMP | — | |
MD5:— | SHA256:— | |||
| 8508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1e52d1.TMP | — | |
MD5:— | SHA256:— | |||
| 8508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1e52d1.TMP | — | |
MD5:— | SHA256:— | |||
| 8508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1e52e0.TMP | — | |
MD5:— | SHA256:— | |||
| 8508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
210
TCP/UDP connections
111
DNS requests
90
Threats
32
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4624 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:pSx_yRNWRu7UgBDL5OHe7-lQ1zrcxjB0NcG-qOUtoRs&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
4624 | msedge.exe | GET | 200 | 150.171.27.11:443 | https://edge.microsoft.com/serviceexperimentation/v3/?osname=win&channel=stable&osver=10.0.19045&devicefamily=desktop&installdate=1661339457&clientversion=133.0.3065.92&experimentationmode=2&scpguard=0&scpfull=0&scpver=0 | unknown | text | 446 b | whitelisted |
4624 | msedge.exe | GET | 200 | 31.216.145.5:443 | https://mega.nz/secureboot.js?r=1769657656 | unknown | text | 128 Kb | unknown |
4624 | msedge.exe | GET | 200 | 31.216.145.5:443 | https://mega.nz/file/ls4WmIqA | unknown | html | 2.05 Kb | unknown |
4624 | msedge.exe | GET | 200 | 13.107.246.45:443 | https://api.edgeoffer.microsoft.com/edgeoffer/pb/experiments?appId=edge-extensions&country=US | unknown | binary | 82 b | whitelisted |
4624 | msedge.exe | GET | 200 | 104.18.22.222:443 | https://copilot.microsoft.com/c/api/user/eligibility | unknown | text | 25 b | whitelisted |
4624 | msedge.exe | GET | 200 | 2.16.241.209:443 | https://www.bing.com/bloomfilterfiles/ExpandedDomainsFilterGlobal.json | unknown | text | 128 Kb | whitelisted |
4624 | msedge.exe | GET | 200 | 31.216.145.5:443 | https://mega.nz/loading-sprite_light.png | unknown | image | 8.41 Kb | unknown |
4624 | msedge.exe | GET | 200 | 31.216.145.5:443 | https://mega.nz/favicon.ico?v=3 | unknown | image | 6.37 Kb | unknown |
4624 | msedge.exe | GET | 200 | 52.123.243.210:443 | https://config.edge.skype.com/config/v1/Edge/133.0.3065.92?clientId=4489578223053569932&agents=Edge%2CEdgeConfig%2CEdgeServices%2CEdgeFirstRun%2CEdgeFirstRunConfig&osname=win&client=edge&channel=stable&scpfre=0&osarch=x86_64&osver=10.0.19045&wu=1&devicefamily=desktop&uma=0&sessionid=66&mngd=0&installdate=1661339457&edu=0&soobedate=1504771245&bphint=2&fg=1&lbfgdate=1766135237&lafgdate=0 | unknown | text | 4.87 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
8176 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:137 | — | Not routed | — | whitelisted |
8536 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6768 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5568 | SearchApp.exe | 2.16.241.209:443 | www.bing.com | AKAMAI-ASN1 | NL | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
— | — | 204.79.197.203:80 | oneocsp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3412 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | Not routed | — | whitelisted |
4624 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
oneocsp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
mega.nz |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4624 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
4624 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
4624 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
4624 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
4624 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
4624 | msedge.exe | Misc activity | ET FILE_SHARING Observed DNS Query to Filesharing Service (mega .co .nz) |
4624 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
4624 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (mega .nz) |
4624 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
4624 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (mega .nz) |
Process | Message |
|---|---|
Topaz Video AI.exe | default font 9 "Segoe UI"
|
Topaz Video AI.exe | QT_MESSAGE_PATTERN: %{backtrace} is not supported by this Qt build
|
Topaz Video AI.exe | default font 10 "qrc:/elements/Roboto-Regular.ttf"
|
Topaz Video AI.exe | 2026-02-04-8:59:28.076 default info 684-7732 unknown unknown:0 - Creating directory and setting the path for logging "C:\\Users\\admin\\AppData\\Roaming\\Topaz Labs LLC\\Topaz Video AI\\logs\\"
|