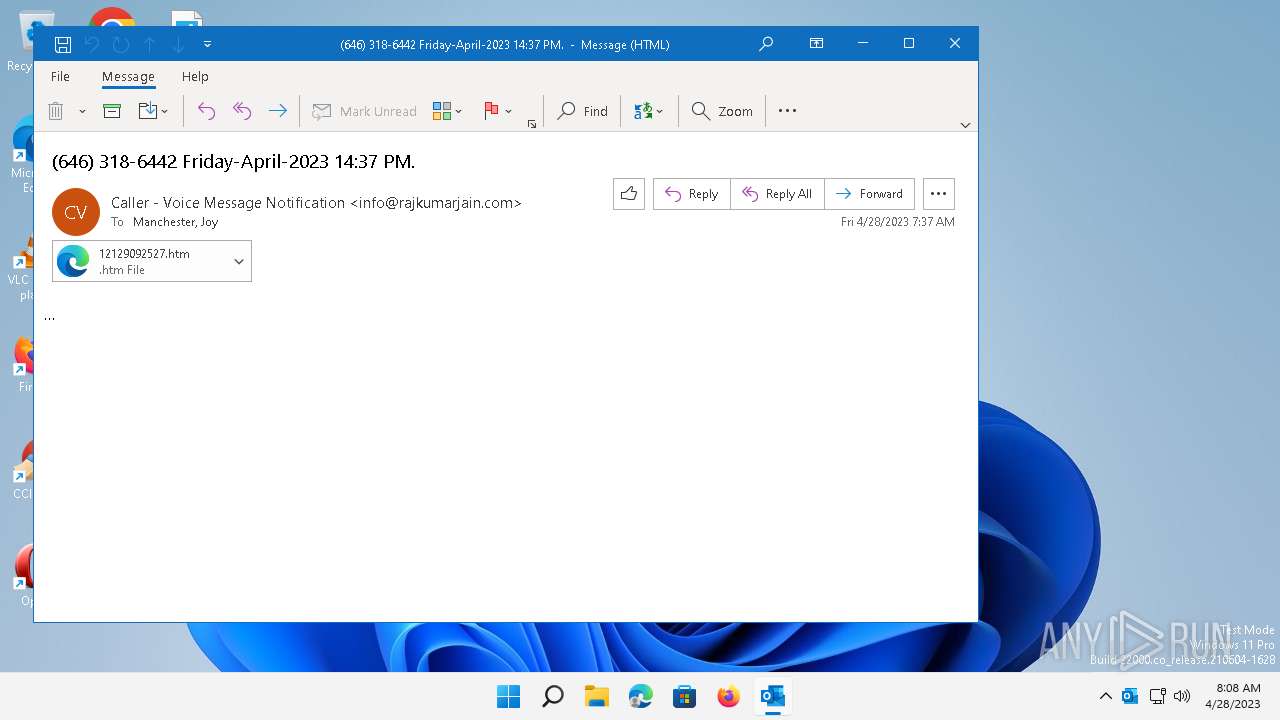
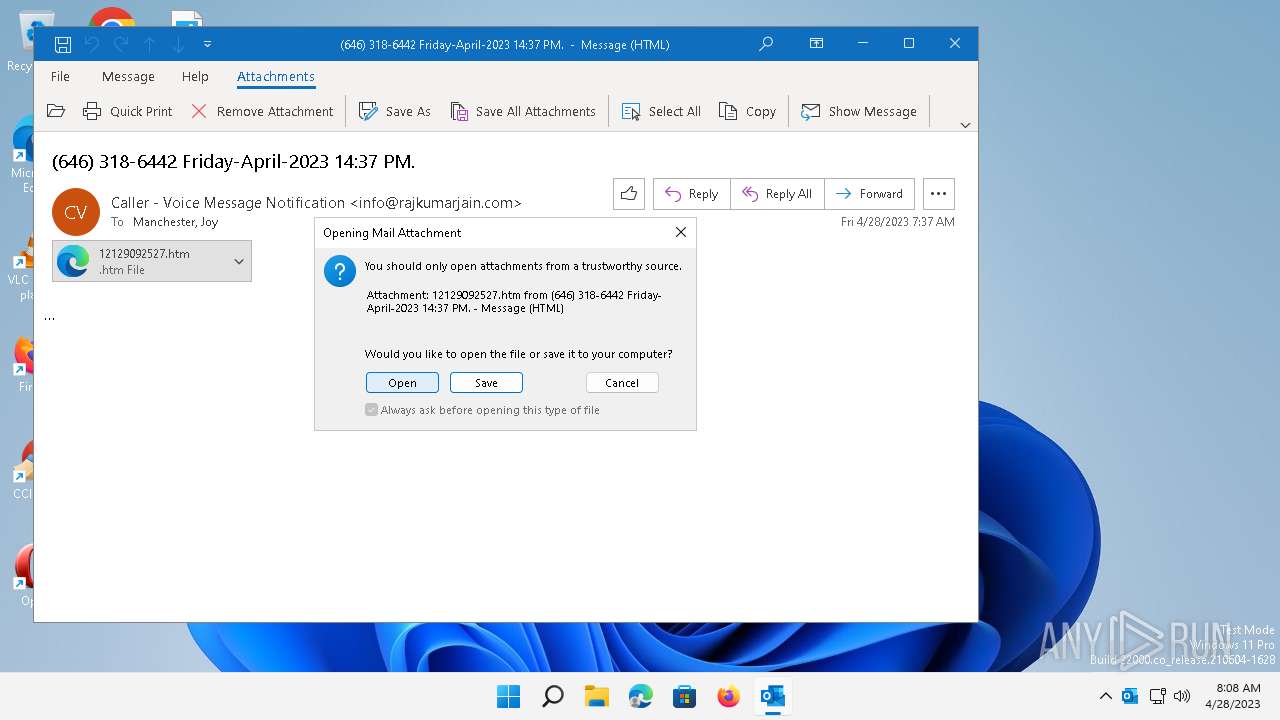
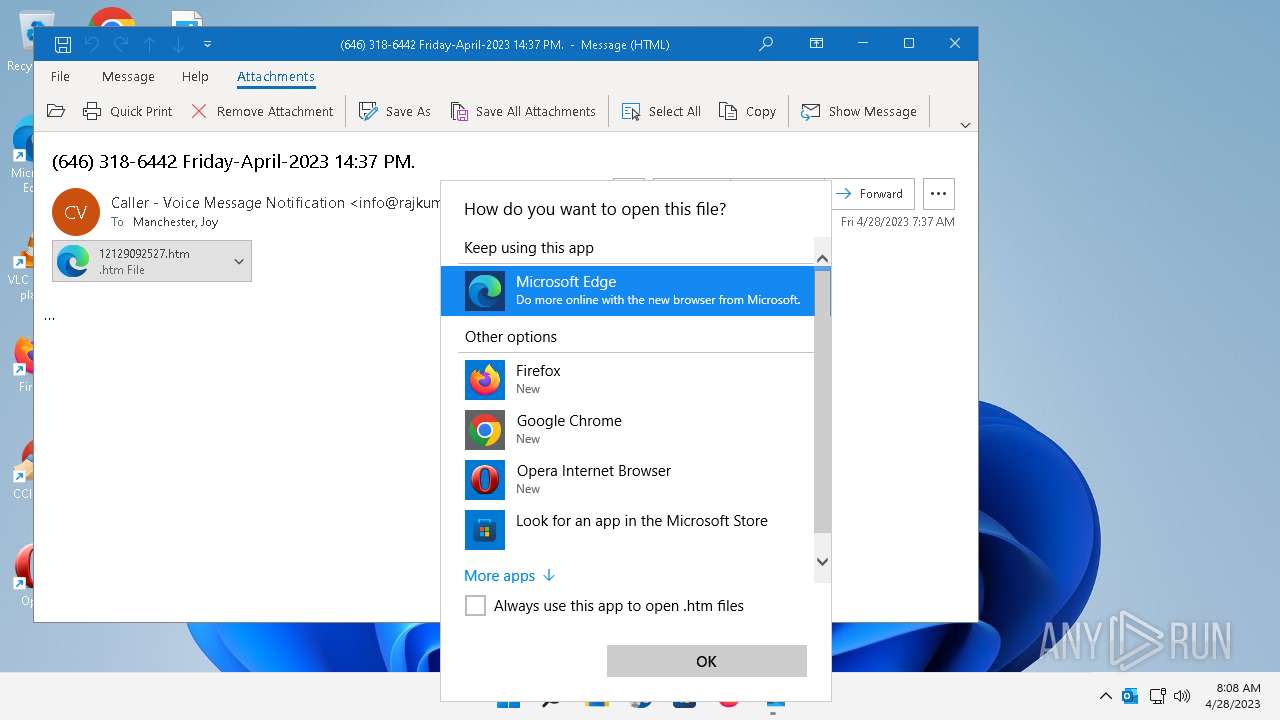
| File name: | (646) 318-6442 Friday-April-2023 1437 PM..msg |
| Full analysis: | https://app.any.run/tasks/88ad8462-8762-4b3a-b09c-6159a8af74ff |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2023, 15:08:17 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 4C2B95109CE64016E231C64EE9C16445 |
| SHA1: | 1514FCD99E59803DEB8740785FF54D1BE25B539D |
| SHA256: | FE3EAEDA5311140A80FAF2DD75CD53FEF719A9C2B1577A2B1B42A7AE3BF6F160 |
| SSDEEP: | 1536:ATCp/NFyncW0WT4fFlnidDfhpFeSzBG8C:ATCp/n6cfF1iiMBG8C |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- OpenWith.exe (PID: 3312)
Executes as Windows Service
- elevation_service.exe (PID: 3888)
INFO
Reads product name
- OUTLOOK.EXE (PID: 6796)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 6796)
- OpenWith.exe (PID: 3312)
Create files in a temporary directory
- chrome.exe (PID: 7144)
Reads the computer name
- elevation_service.exe (PID: 3888)
The process checks LSA protection
- OpenWith.exe (PID: 3312)
- elevation_service.exe (PID: 3888)
Application launched itself
- chrome.exe (PID: 7144)
Checks supported languages
- elevation_service.exe (PID: 3888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
145
Monitored processes
12
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3312 | C:\Windows\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3372 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=112.0.5615.50 --initial-client-data=0x110,0x114,0x118,0xec,0x11c,0x7ff8d5e4aa60,0x7ff8d5e4aa70,0x7ff8d5e4aa80 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 3888 | "C:\Program Files (x86)\Google\Chrome\Application\112.0.5615.50\elevation_service.exe" | C:\Program Files (x86)\Google\Chrome\Application\112.0.5615.50\elevation_service.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 5200 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.22000.1 --gpu-preferences=UAAAAAAAAADoAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAACQAAAAAAAAAAAAAAAAAAAAAAAAABgAAAAAAAAAGAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1504 --field-trial-handle=1844,i,9712279962574404196,8036770135510537694,131072 /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
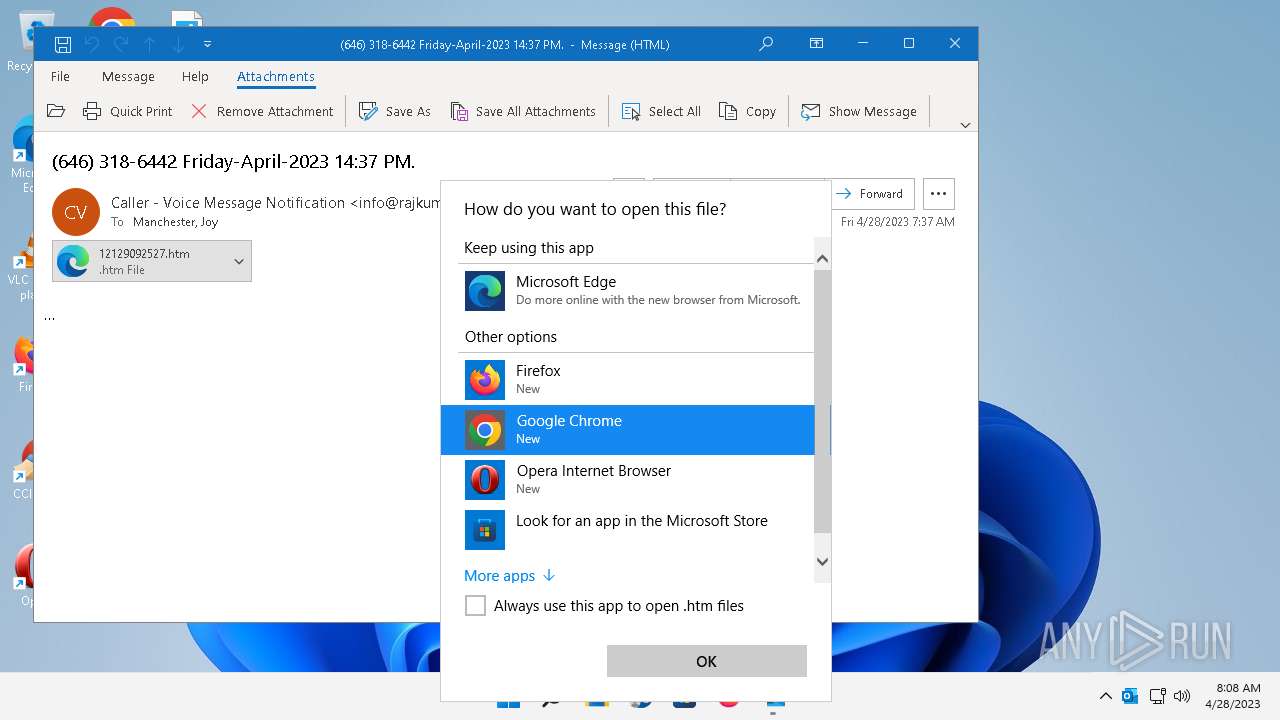
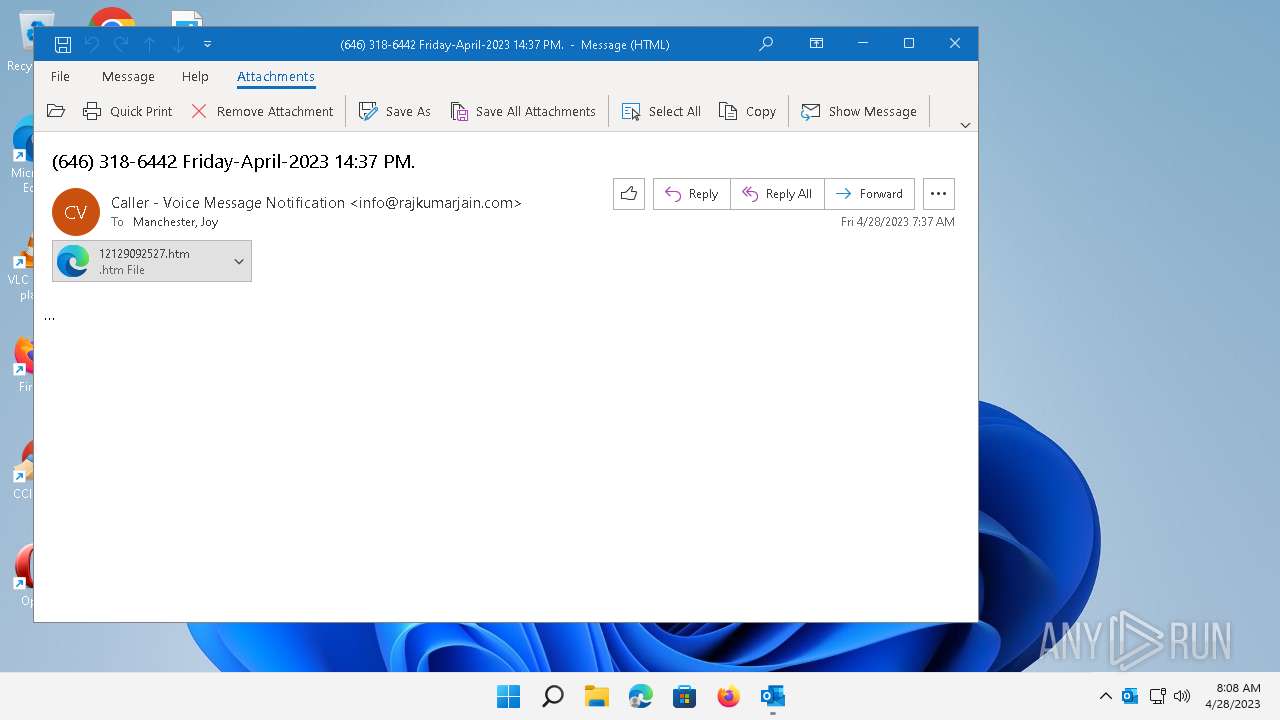
| 6796 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\(646) 318-6442 Friday-April-2023 1437 PM..msg" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.15601.20142 Modules
| |||||||||||||||
| 7144 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --single-argument C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AVGCM8PZ\12129092527.htm | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 7184 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAABgAAAAAAAAAGAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1836 --field-trial-handle=1844,i,9712279962574404196,8036770135510537694,131072 /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 7204 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2160 --field-trial-handle=1844,i,9712279962574404196,8036770135510537694,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 7280 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2208 --field-trial-handle=1844,i,9712279962574404196,8036770135510537694,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
| 7580 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3052 --field-trial-handle=1844,i,9712279962574404196,8036770135510537694,131072 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 112.0.5615.50 Modules
| |||||||||||||||
Total events
17 768
Read events
17 114
Write events
310
Delete events
344
Modification events
| (PID) Process: | (6796) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common |
| Operation: | write | Name: | SessionId |
Value: 70A1684DDDEB6841925B66857825C887 | |||
| (PID) Process: | (6796) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\GracefulExit\OUTLOOK\1240 |
| Operation: | delete value | Name: | 0 |
Value: 0B0E10EDDA01A76CDCB347A1CAC8431B26DB1646CFB89785DDD7BDEC016A0410240044F17964AE9D01008500A907556E6B6E6F776EC906022222CA0D4201A200C2190000C50E8908C60FCDC0FD94DDD7BDEC01C91003783634C511D809D2120B6F00750074006C006F006F006B002E0065007800650000 | |||
| (PID) Process: | (6796) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\GracefulExit\OUTLOOK\1240 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6796) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6796 |
| Operation: | write | Name: | 0 |
Value: 0B0E105D68496DDC54804EB372571CF5458D39230046EBE3EFD1B4BCDEEC016A0410240044F17964AE9D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C5118C35D2120B6F00750074006C006F006F006B002E0065007800650000 | |||
| (PID) Process: | (6796) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6796) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6796) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6796) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6796) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01A012000000001000AE4EF13C07000000000000000700000000000000 | |||
| (PID) Process: | (6796) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
48
Text files
88
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6796 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - No Account.pst | — | |
MD5:— | SHA256:— | |||
| 7144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6796 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:C542A7B2DA6F9E8E3AE8795076F70403 | SHA256:56D222AA0522948E294FA1A80D8A377AF9F5BCC7C2E210DB00B3F2B521130936 | |||
| 6796 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FORMS\FRMDATA64.DAT | binary | |
MD5:AF1EA7B68D3850DC6370F22F4923DE67 | SHA256:6CC4471957DA1E617326E5E61E9701E6CC1A962EF42143C3175AE90CBFDF4F27 | |||
| 6796 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\73E9A311-A36E-4522-A9DA-44FFA0A743FC | xml | |
MD5:9D9746984AB6F66139B4BA0E72DABA0D | SHA256:32EA4842CDC082E9C0537AC662A92904E6B719E6111F5B0B855C79936C9519AD | |||
| 6796 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:08D10A52880DE331526EE194CCA48F18 | SHA256:4CA3986FE1BDE76E6DB63DD4735F53BA63C9B1E536F740423CF8A3676CF80458 | |||
| 6796 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\AVGCM8PZ\12129092527 (002).htm | html | |
MD5:D595969B98A6CC0EE3BB050C4C2D82CF | SHA256:A0B7603C3EE4E36BA9AB4BB29276A838341514FCE0BCC2383BFCBFB3135576A5 | |||
| 7144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:858B51004CDB48854BA078F75A43ECFB | SHA256:78A581395DB475C3703E4EEF3E3067BC30404B0B4685D10A768BBE1463883FE5 | |||
| 7144 | chrome.exe | C:\USERS\ADMIN\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\VARIATIONS | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 6796 | OUTLOOK.EXE | C:\USERS\ADMIN\APPDATA\LOCAL\MICROSOFT\TOKENBROKER\CACHE\5475CB191E478C39370A215B2DA98A37E9DC813D.TBRES | binary | |
MD5:3FAD30617C6A177A15507B76D43444E1 | SHA256:756A8EF75F8A16CCA0FB10E9B250A33BB2DDE30B0C49CC75BCC96ABDC1C1AD4D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
41
DNS requests
47
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6024 | svchost.exe | GET | 304 | 8.238.34.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0e302285a99826c9 | US | — | — | whitelisted |
6024 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
7204 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
6796 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | US | der | 471 b | whitelisted |
1480 | svchost.exe | GET | 200 | 13.107.4.52:80 | http://www.msftconnecttest.com/connecttest.txt | US | text | 22 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6796 | OUTLOOK.EXE | 52.109.32.24:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | suspicious |
6796 | OUTLOOK.EXE | 52.113.195.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
6796 | OUTLOOK.EXE | 52.109.8.44:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
6532 | svchost.exe | 23.35.236.109:443 | fs.microsoft.com | AKAMAI-AS | DE | malicious |
1480 | svchost.exe | 13.107.4.52:80 | www.msftconnecttest.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6796 | OUTLOOK.EXE | 52.109.16.60:443 | ols.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
6024 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6024 | svchost.exe | 8.238.34.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
6796 | OUTLOOK.EXE | 52.109.28.62:443 | odc.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | suspicious |
6024 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
ols.officeapps.live.com |
| whitelisted |
login.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
odc.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1480 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |