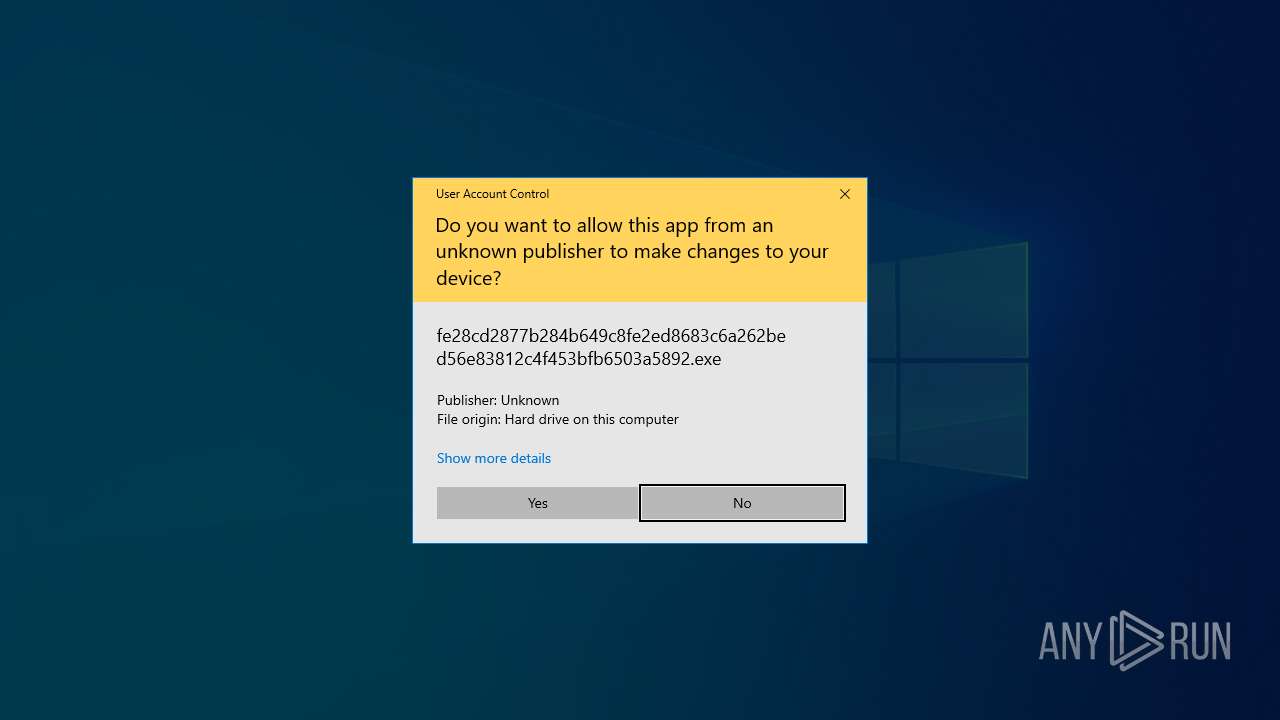
| File name: | fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe |
| Full analysis: | https://app.any.run/tasks/b7bfe415-ac8b-4d7c-bd05-98ccbeb7cc96 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 07:24:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 8A60E9F5DE7C6A200A57E4CCCC25F72D |
| SHA1: | 1291E5190EC2822090C764CFCCEB63142E4EE85B |
| SHA256: | FE28CD2877B284B649C8FE2ED8683C6A262BED56E83812C4F453BFB6503A5892 |
| SSDEEP: | 6144:c0/1Thw5w4qjPRrf2VrRZHMrbLcPNnpjpmuFYwNfMWP3:HcPNnpjpmuFLF |
MALICIOUS
MOFKSYS has been found (auto)
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 6824)
JEEFO has been detected
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 6824)
- icsys.icn.exe (PID: 7820)
- svchost.exe (PID: 7884)
- explorer.exe (PID: 7844)
Changes the autorun value in the registry
- explorer.exe (PID: 7844)
- svchost.exe (PID: 7884)
SUSPICIOUS
Starts application with an unusual extension
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 6824)
Executable content was dropped or overwritten
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 6824)
- icsys.icn.exe (PID: 7820)
- spoolsv.exe (PID: 7868)
- explorer.exe (PID: 7844)
Starts itself from another location
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 6824)
- icsys.icn.exe (PID: 7820)
- explorer.exe (PID: 7844)
- spoolsv.exe (PID: 7868)
- svchost.exe (PID: 7884)
The process creates files with name similar to system file names
- icsys.icn.exe (PID: 7820)
- spoolsv.exe (PID: 7868)
INFO
The sample compiled with english language support
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 6824)
- icsys.icn.exe (PID: 7820)
- explorer.exe (PID: 7844)
- spoolsv.exe (PID: 7868)
Create files in a temporary directory
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 6824)
- icsys.icn.exe (PID: 7820)
- explorer.exe (PID: 7844)
- spoolsv.exe (PID: 7868)
- svchost.exe (PID: 7884)
- spoolsv.exe (PID: 7904)
Checks supported languages
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 6824)
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 896)
- icsys.icn.exe (PID: 7820)
- spoolsv.exe (PID: 7868)
- svchost.exe (PID: 7884)
- spoolsv.exe (PID: 7904)
- explorer.exe (PID: 7844)
- identity_helper.exe (PID: 8056)
Checks proxy server information
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 896)
Reads the computer name
- fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe (PID: 896)
- svchost.exe (PID: 7884)
- identity_helper.exe (PID: 8056)
Manual execution by a user
- msedge.exe (PID: 7000)
- WINWORD.EXE (PID: 1616)
Application launched itself
- msedge.exe (PID: 7000)
Launch of the file from Registry key
- explorer.exe (PID: 7844)
- svchost.exe (PID: 7884)
Reads Environment values
- identity_helper.exe (PID: 8056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:04:01 07:08:22+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 106496 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x290c |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| ProductName: | Project1 |
| FileVersion: | 1 |
| ProductVersion: | 1 |
| InternalName: | TJprojMain |
| OriginalFileName: | TJprojMain.exe |
Total processes
181
Monitored processes
44
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 896 | c:\users\admin\desktop\fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe | C:\Users\admin\Desktop\fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe | fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1012 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=25 --mojo-platform-channel-handle=6728 --field-trial-handle=2436,i,12641338500128605388,6028969490883425136,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1348 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2704 --field-trial-handle=2436,i,12641338500128605388,6028969490883425136,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\hotelsfrance.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2088 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2432 --field-trial-handle=2436,i,12641338500128605388,6028969490883425136,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2092 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7720 --field-trial-handle=2436,i,12641338500128605388,6028969490883425136,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4068 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6280 --field-trial-handle=2436,i,12641338500128605388,6028969490883425136,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4244 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6672 --field-trial-handle=2436,i,12641338500128605388,6028969490883425136,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5588 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2304 --field-trial-handle=2436,i,12641338500128605388,6028969490883425136,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 5720 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6716 --field-trial-handle=2436,i,12641338500128605388,6028969490883425136,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
18 927
Read events
18 532
Write events
371
Delete events
24
Modification events
| (PID) Process: | (6824) fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\VB and VBA Program Settings\Explorer\Process |
| Operation: | write | Name: | LO |
Value: 1 | |||
| (PID) Process: | (7000) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7000) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7000) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7000) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: D277C898EB942F00 | |||
| (PID) Process: | (7000) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: B1ADCF98EB942F00 | |||
| (PID) Process: | (7000) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7000) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328516 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E3D960CC-9937-4487-B22A-BE229BA8402C} | |||
| (PID) Process: | (7000) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328516 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {794ABE65-9C85-4ED3-8B65-691D037A9B5D} | |||
| (PID) Process: | (7000) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328516 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {01E6705D-73AB-4B50-B8C0-9AB323CA7AAF} | |||
Executable files
5
Suspicious files
577
Text files
174
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7000 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10de9a.TMP | — | |
MD5:— | SHA256:— | |||
| 7000 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7000 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10de8a.TMP | — | |
MD5:— | SHA256:— | |||
| 7000 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7000 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10de8a.TMP | — | |
MD5:— | SHA256:— | |||
| 7000 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6824 | fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe | C:\Users\admin\Desktop\fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe | executable | |
MD5:A13DAA35FD7B873F87379A94B97168E2 | SHA256:99784F28E4E95F044D97E402BBF58F369C7C37F49DC5BF48E6B2E706181DB3B7 | |||
| 7000 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Code Cache\js\index-dir\temp-index | binary | |
MD5:01F0B29822F7C00694ABF3150276196A | SHA256:C5CA04147E678498F16E8DED9EFB227591ABF40A3AFC5E65248D019D9B9198D9 | |||
| 7000 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10deb9.TMP | — | |
MD5:— | SHA256:— | |||
| 7000 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF10def8.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
135
DNS requests
95
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5796 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7600 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7600 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1616 | WINWORD.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1616 | WINWORD.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1616 | WINWORD.EXE | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1616 | WINWORD.EXE | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5796 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
776 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5796 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
896 | fe28cd2877b284b649c8fe2ed8683c6a262bed56e83812c4f453bfb6503a5892.exe | 10.0.2.37:80 | — | — | — | unknown |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5588 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5588 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5588 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5588 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5588 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5588 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |