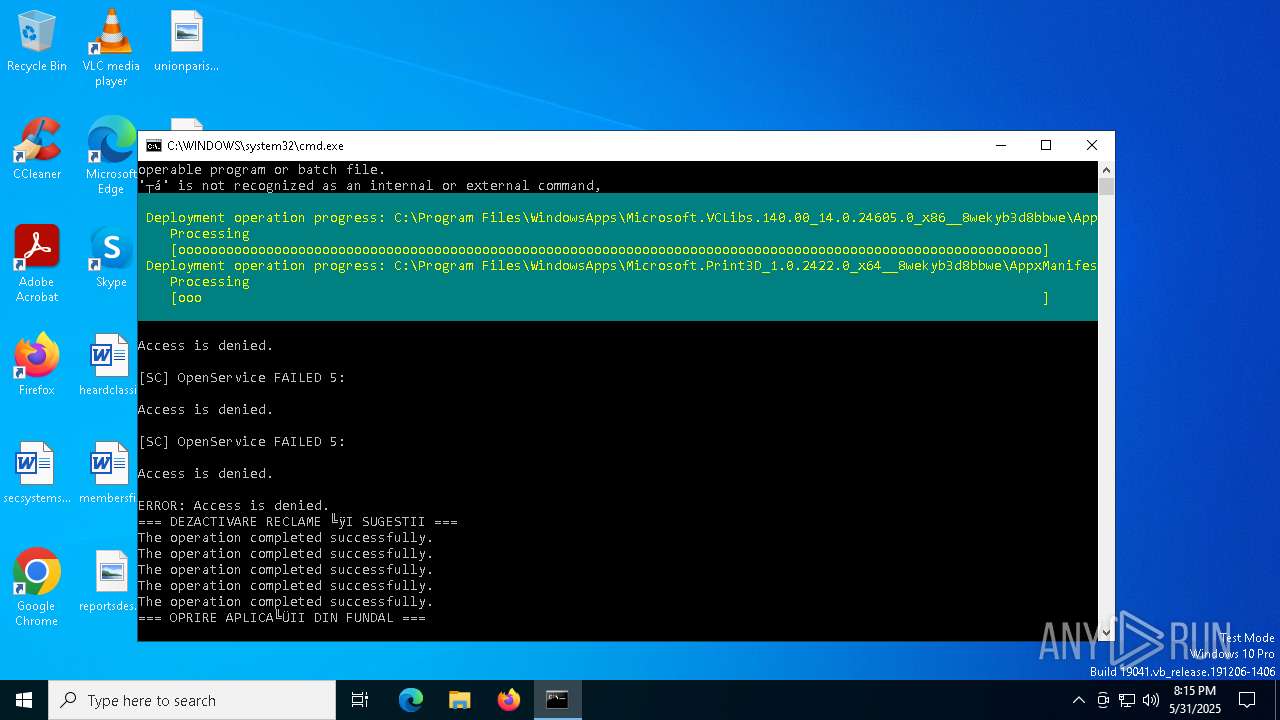
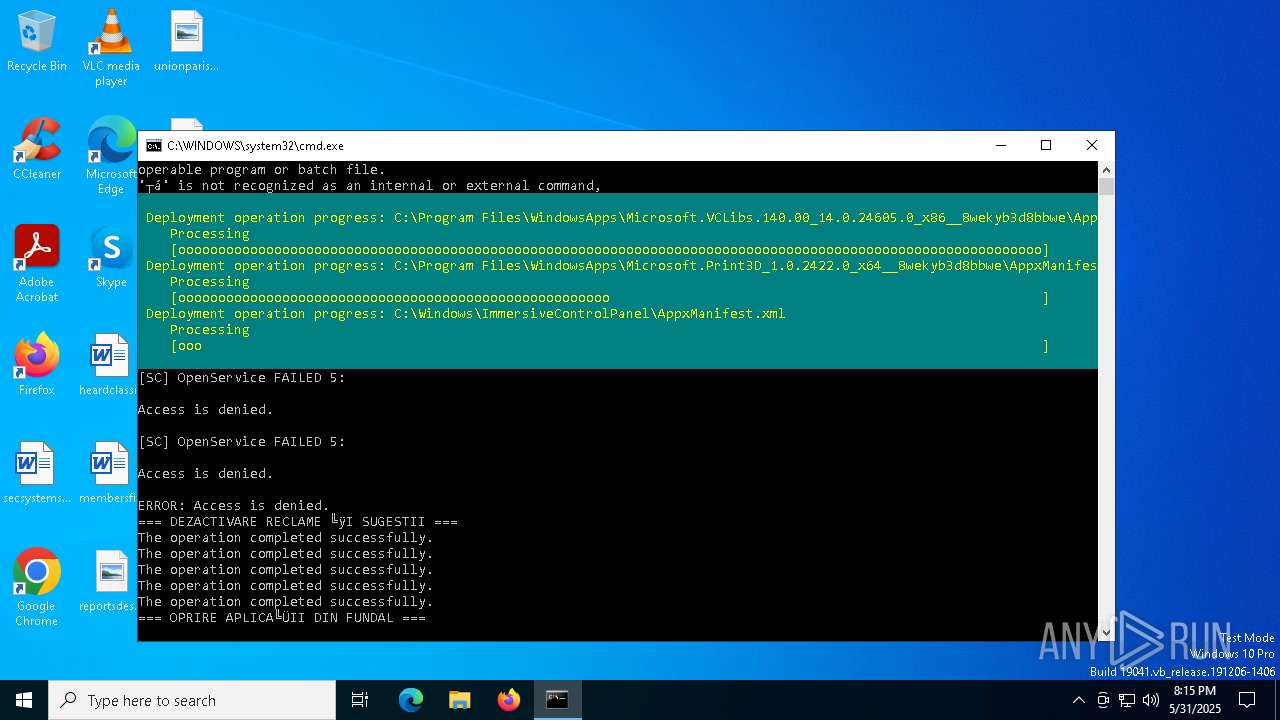
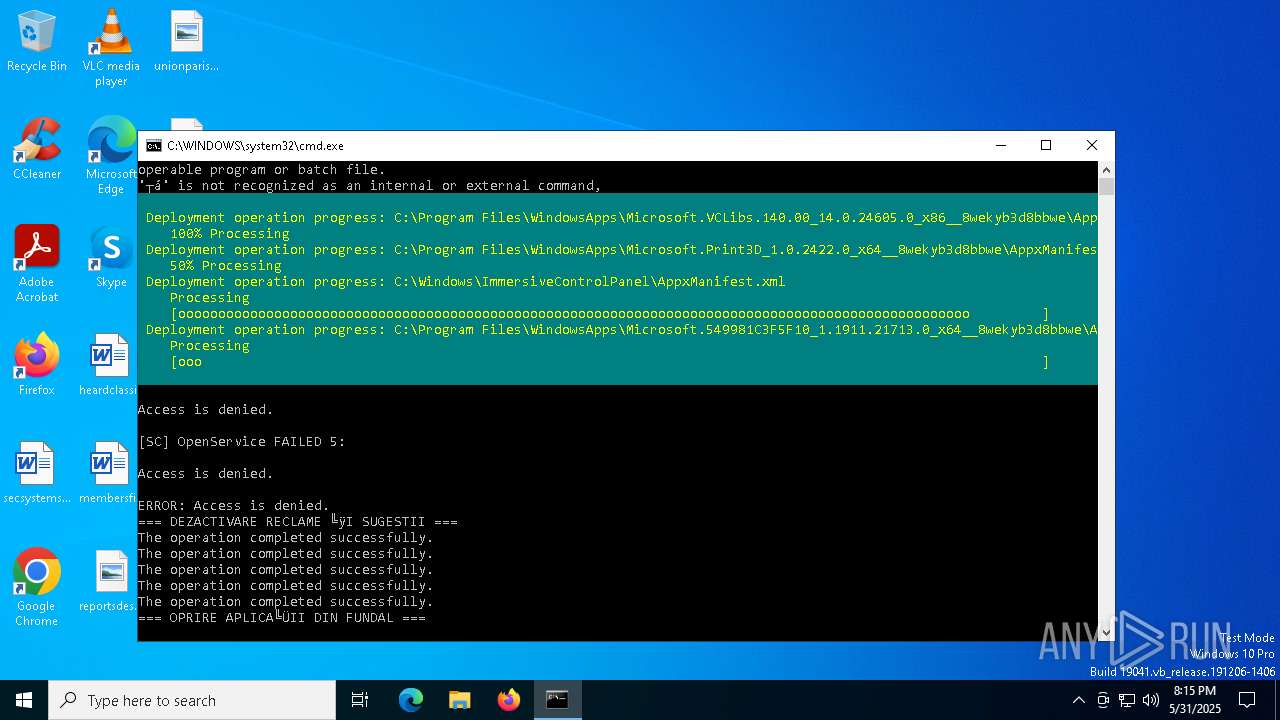
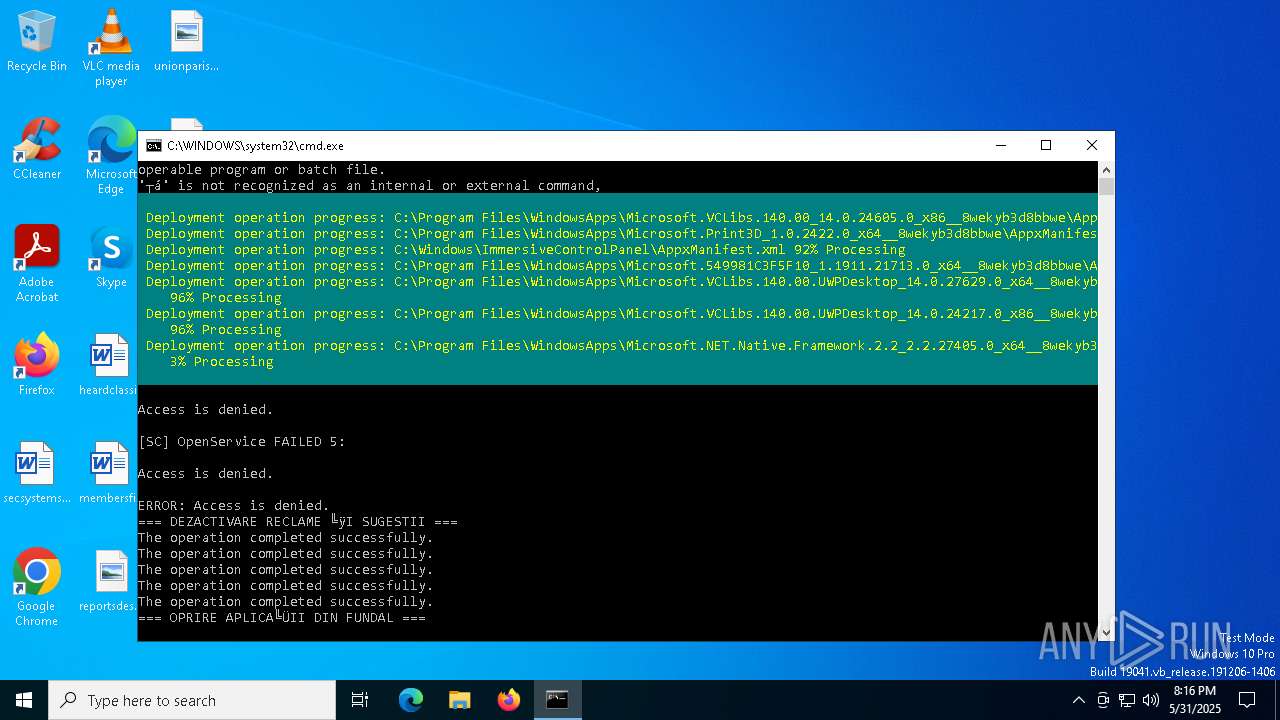
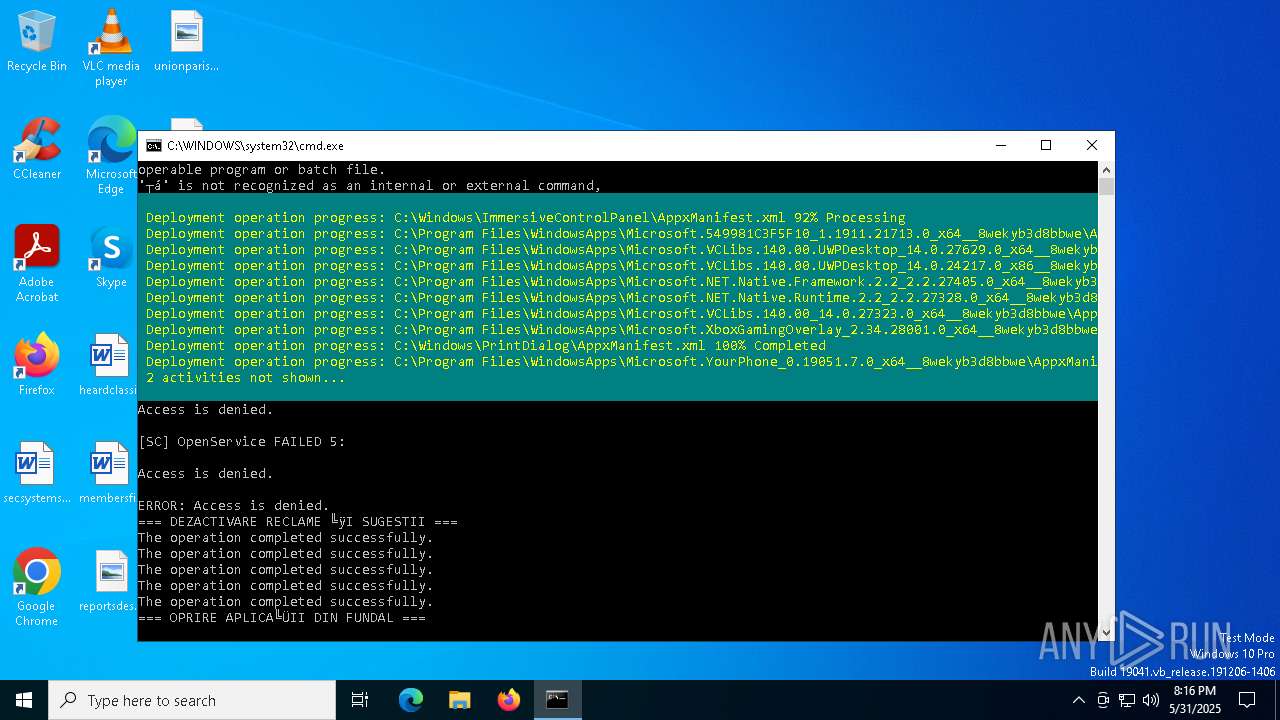
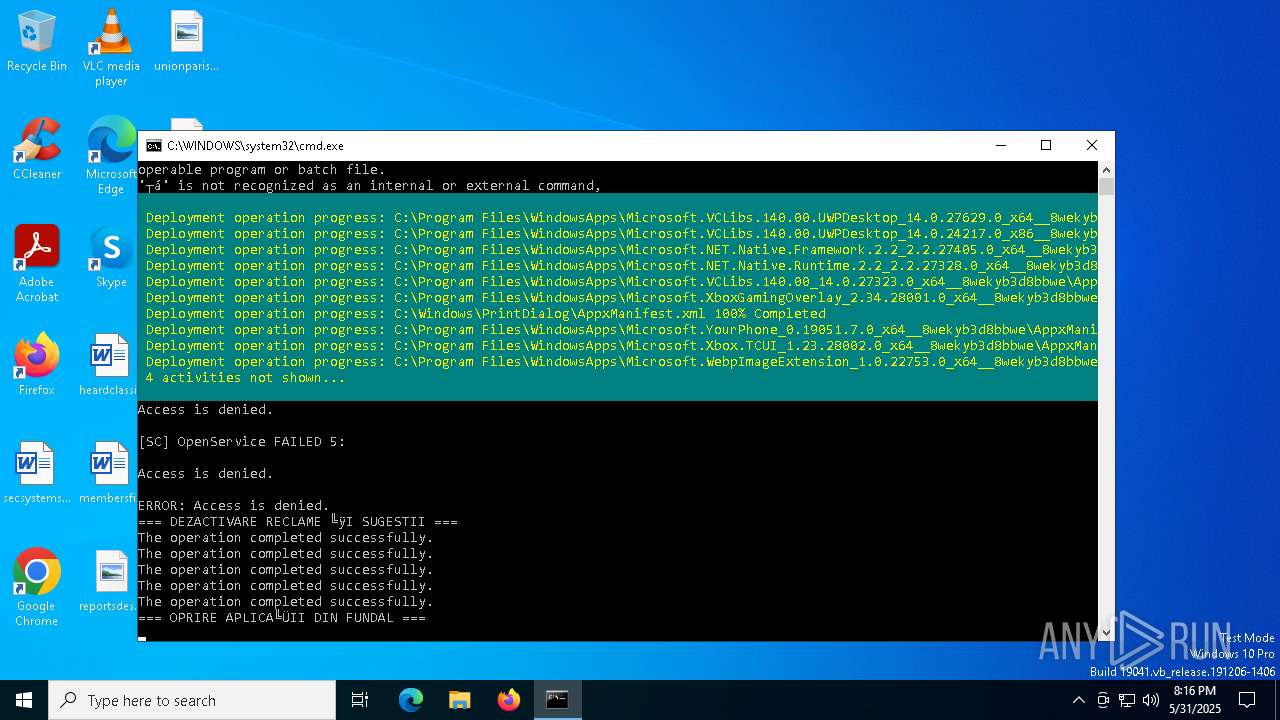
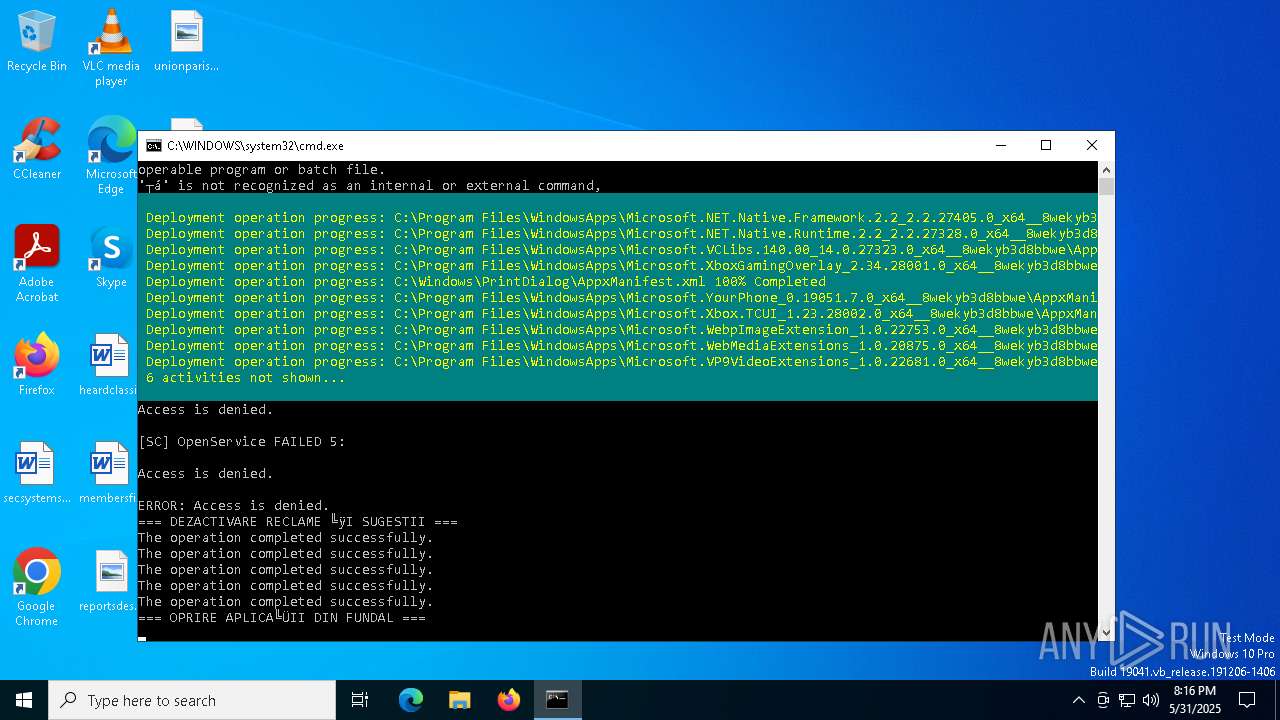
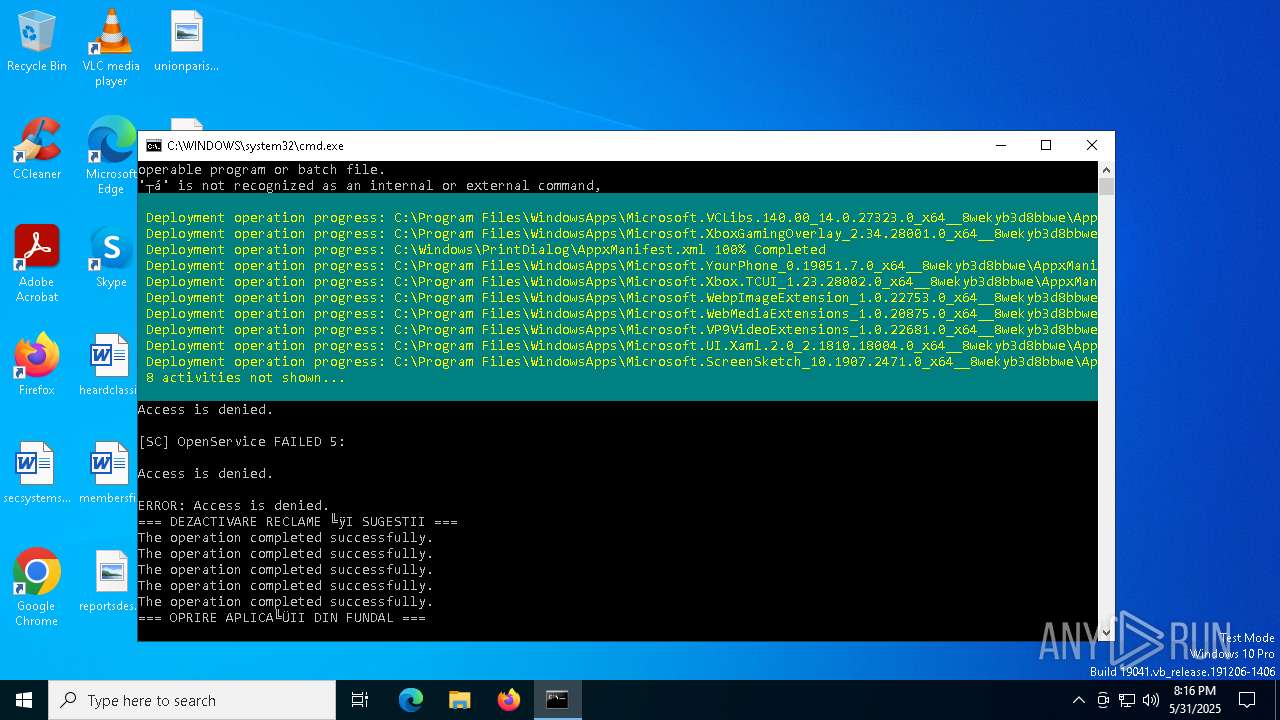
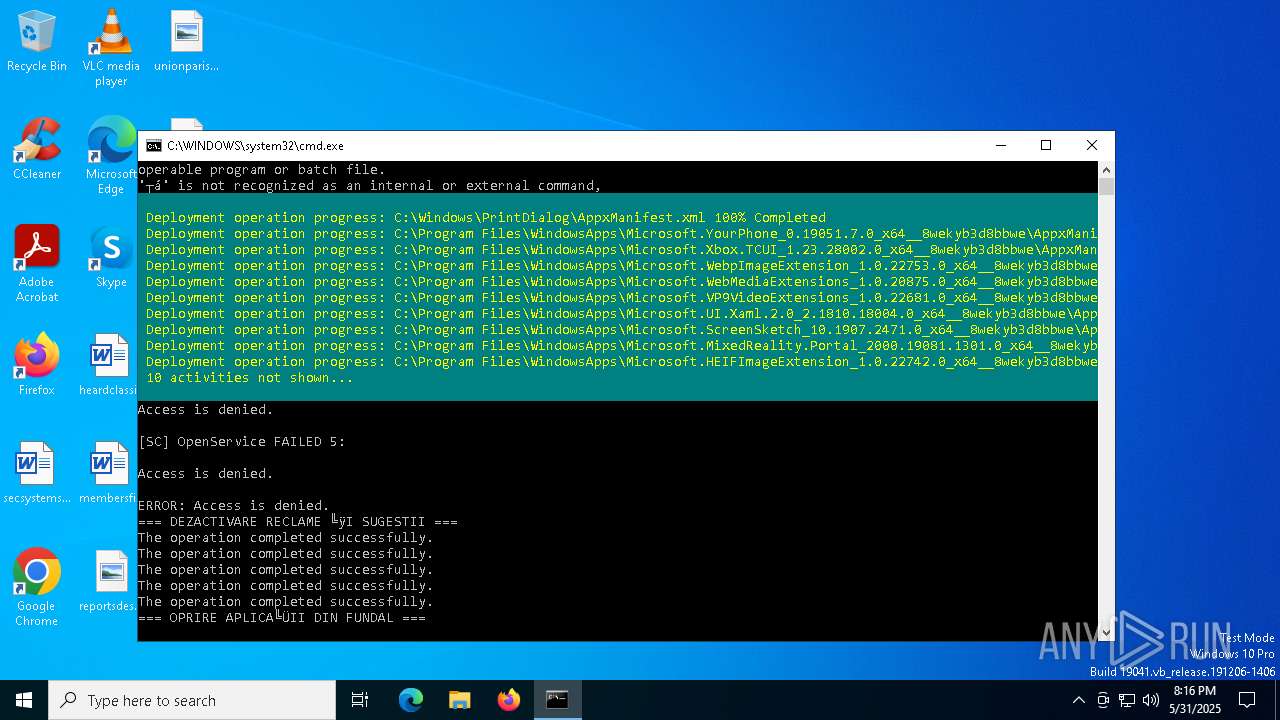
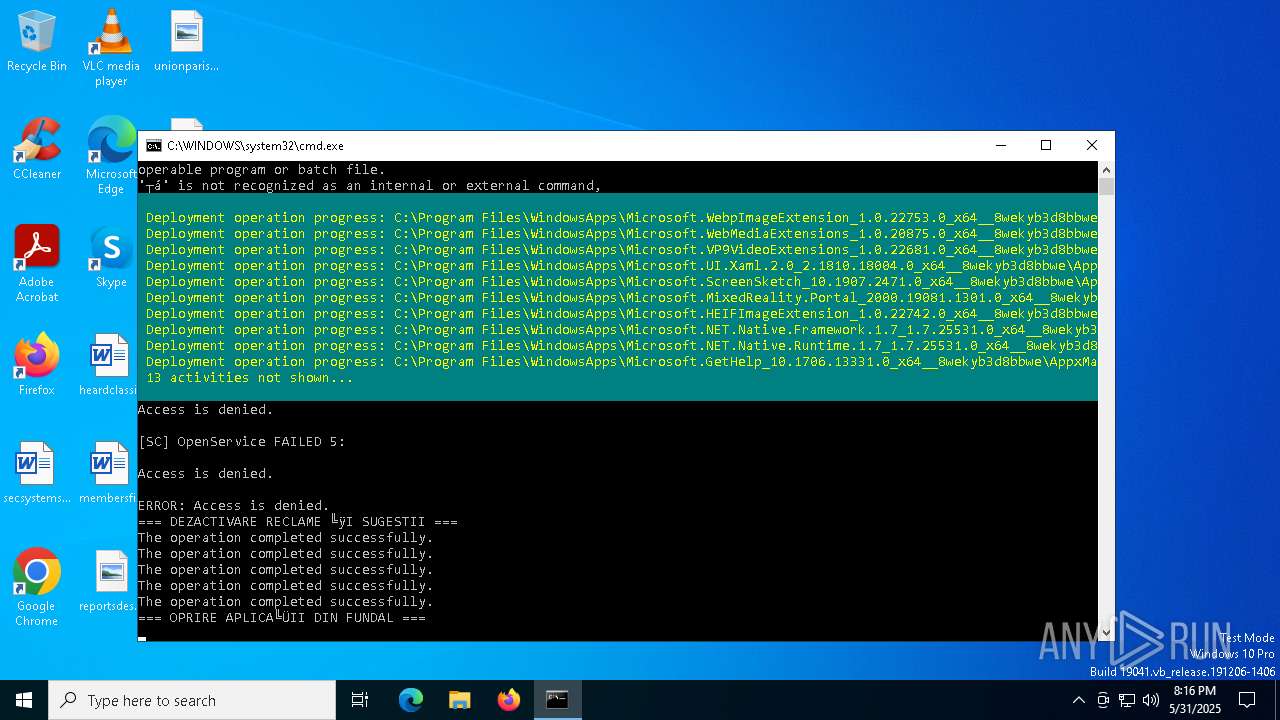
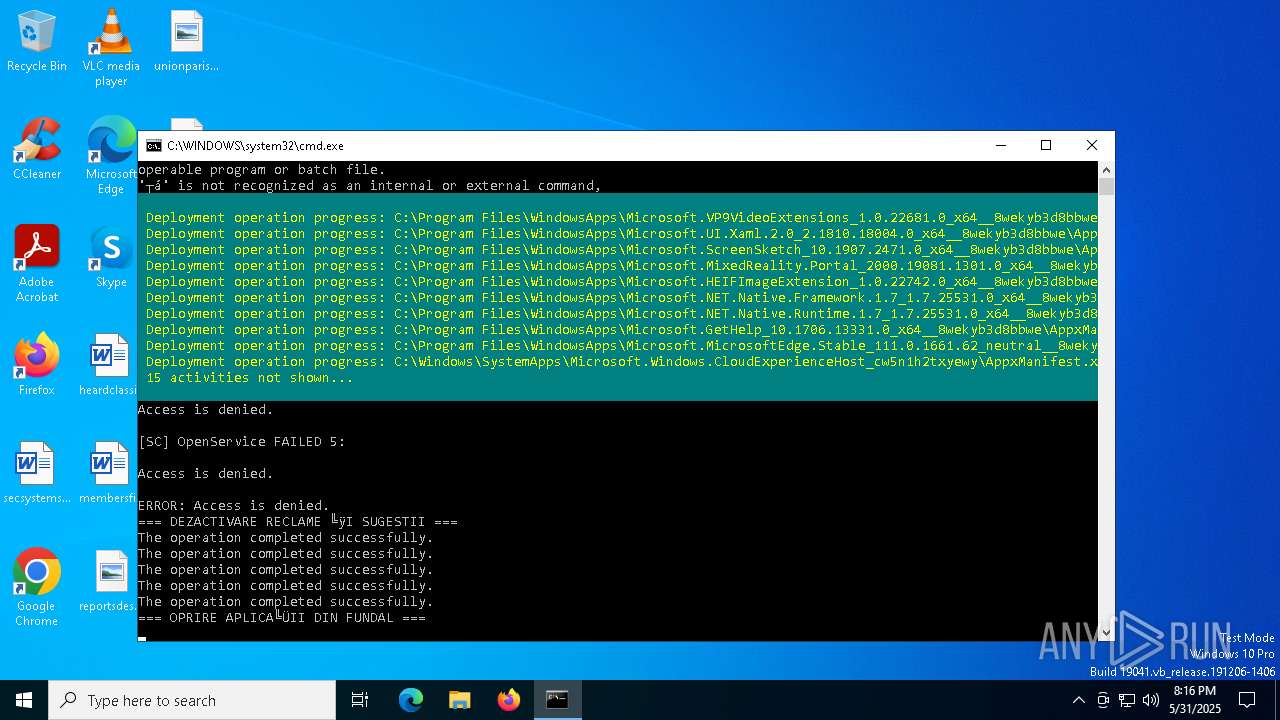
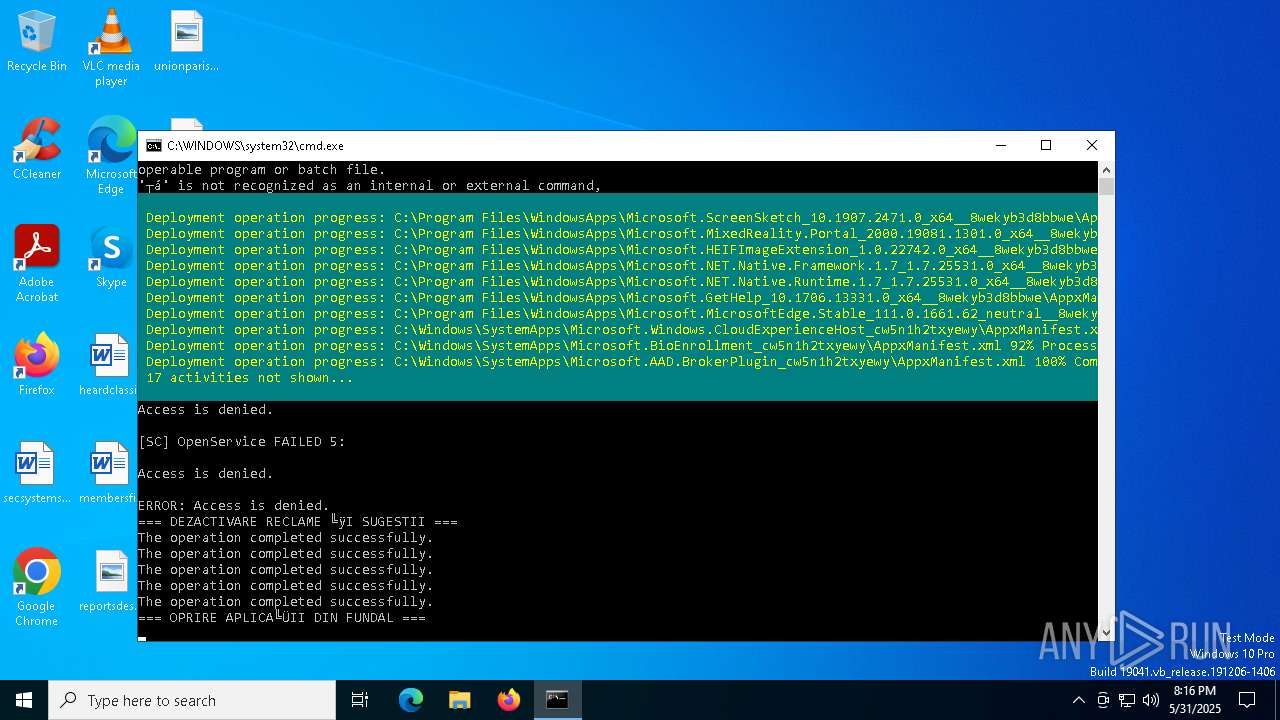
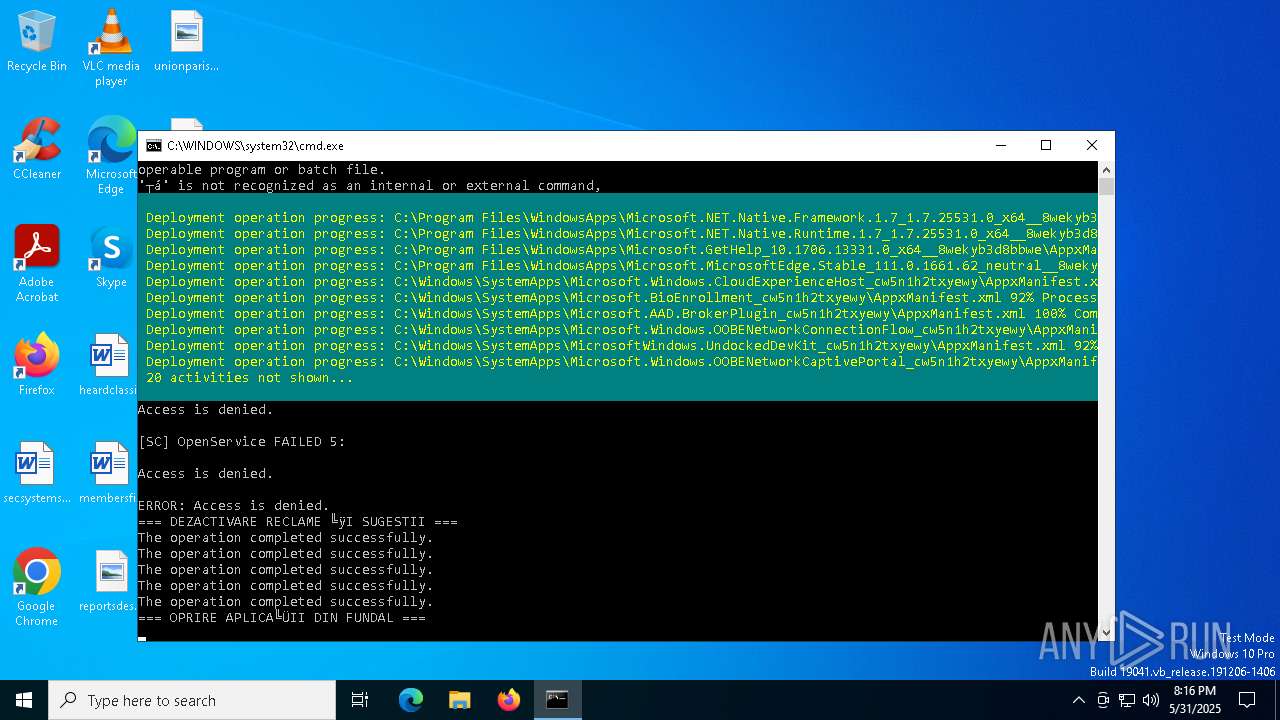
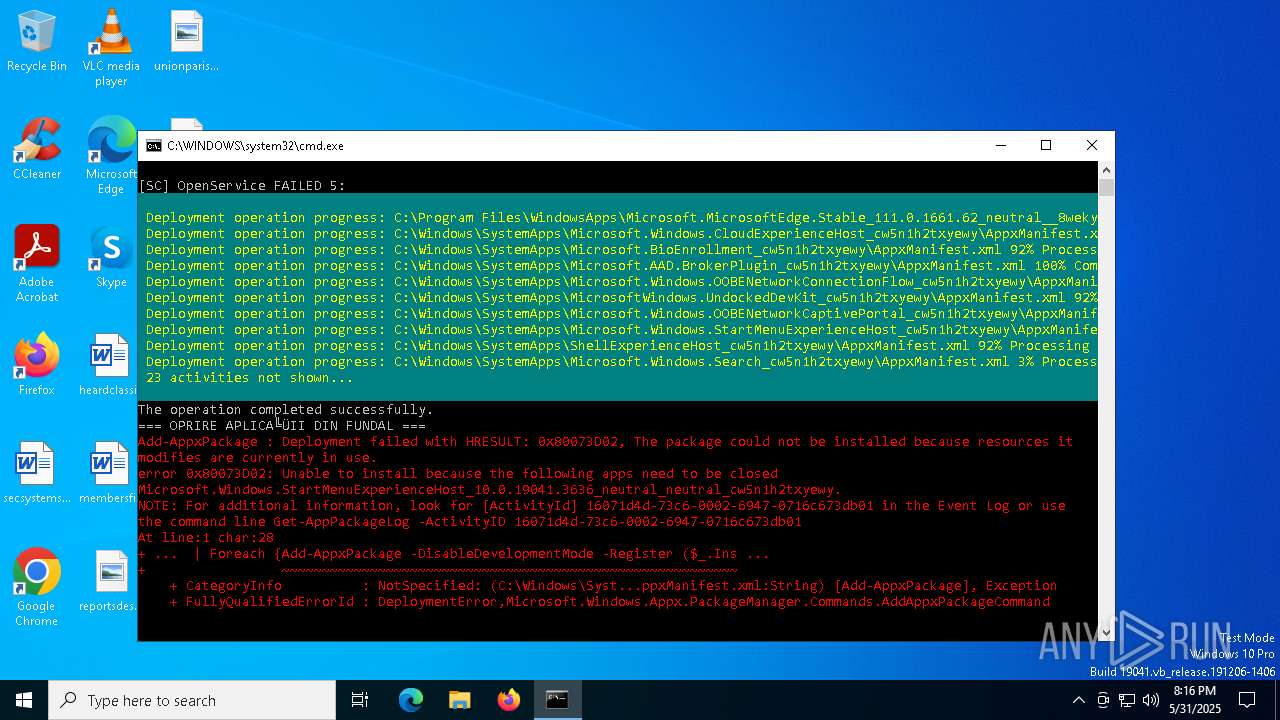
| File name: | Optimizare_Windows11.bat |
| Full analysis: | https://app.any.run/tasks/e2f082a2-00da-4a91-8b5c-82df5f9d4c25 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2025, 20:15:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, Unicode text, UTF-8 text |
| MD5: | BEA10FE6C3DCCBAED14DD892555A3C3C |
| SHA1: | 60E529D25A1E0FCF55F1C8D71D7329A3F4CD57EB |
| SHA256: | FD9612F0126F1BBCF4B1DC2BF212F9F457DE4C7E070E66AA7BCF30F242749C0D |
| SSDEEP: | 48:mJk1XzgBD2plUSFv5r1zQGYKTYKxzYcYcIc7fSen4gozlgt1VAsMOBAH70qI:Ak1XzGD2pXRrVJYKTYKxzYcYcr7nqzkP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 6044)
- net.exe (PID: 1324)
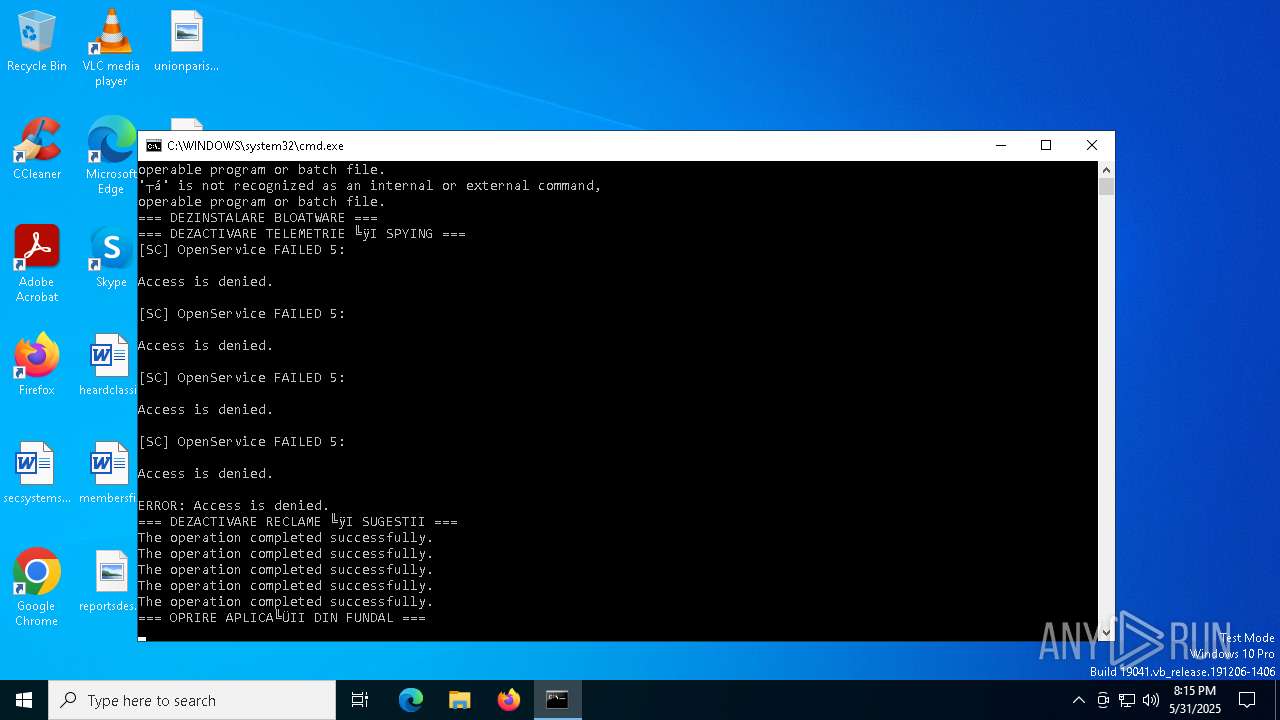
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6044)
Windows service management via SC.EXE
- sc.exe (PID: 8140)
- sc.exe (PID: 7456)
Starts SC.EXE for service management
- cmd.exe (PID: 6044)
Stops a currently running service
- sc.exe (PID: 8092)
- sc.exe (PID: 7612)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6044)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
149
Monitored processes
26
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 760 | powershell -command "Get-AppxPackage 3dbuilder | Remove-AppxPackage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | powershell -command "Get-AppxPackage getstarted | Remove-AppxPackage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | net session AICI ┬á (Scrieti voie asta ┬áin notped net session ) | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2652 | powershell -Command "Get-AppxPackage | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register ($_.InstallLocation + '\AppxManifest.xml')}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | C:\WINDOWS\system32\net1 session AICI ┬á (Scrieti voie asta ┬áin notped net session ) | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2892 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5608 | reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager" /v RotatingLockScreenOverlayEnabled /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5988 | powershell -command "Get-AppxPackage zune | Remove-AppxPackage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
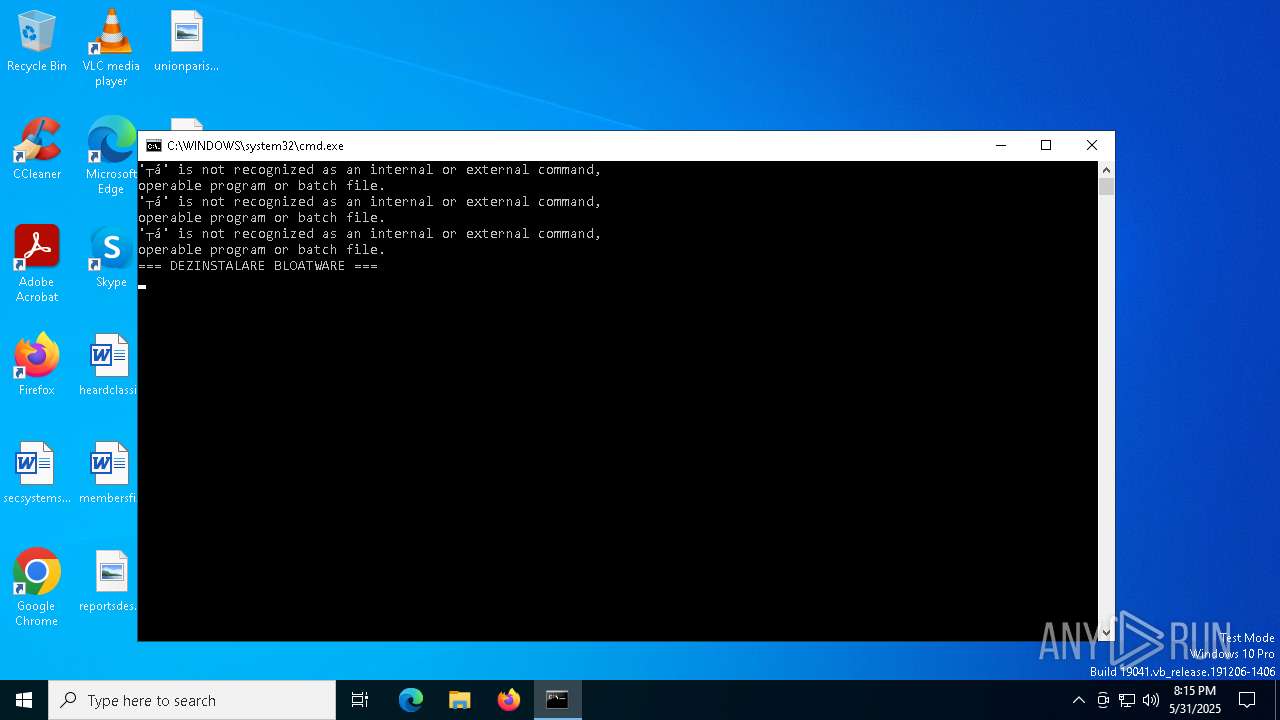
| 6044 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Optimizare_Windows11.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6572 | powershell -command "Get-AppxPackage bing | Remove-AppxPackage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
52 834
Read events
52 829
Write events
5
Delete events
0
Modification events
| (PID) Process: | (7860) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager |
| Operation: | write | Name: | SubscribedContent-310093Enabled |
Value: 0 | |||
| (PID) Process: | (5608) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager |
| Operation: | write | Name: | RotatingLockScreenOverlayEnabled |
Value: 0 | |||
| (PID) Process: | (7424) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager |
| Operation: | write | Name: | SubscribedContent-338388Enabled |
Value: 0 | |||
| (PID) Process: | (7892) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\ContentDeliveryManager |
| Operation: | write | Name: | RotatingLockScreenEnabled |
Value: 0 | |||
| (PID) Process: | (7448) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\UserProfileEngagement |
| Operation: | write | Name: | ScoobeSystemSettingEnabled |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5988 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1mwwikxp.nsy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7656 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rey0nhzi.duz.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 760 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4zoiibf2.ec5.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1056 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_l422bitg.1s4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1056 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_agr3jo5y.k3n.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7304 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dtqigi11.ucm.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7864 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wvolqipl.ncd.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7864 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zxxi2ugl.r5i.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7504 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_d0a43ytd.njx.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6572 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i2eptsqf.yw5.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
20
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5056 | RUXIMICS.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5056 | RUXIMICS.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5056 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5056 | RUXIMICS.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5056 | RUXIMICS.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
780 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2892 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |