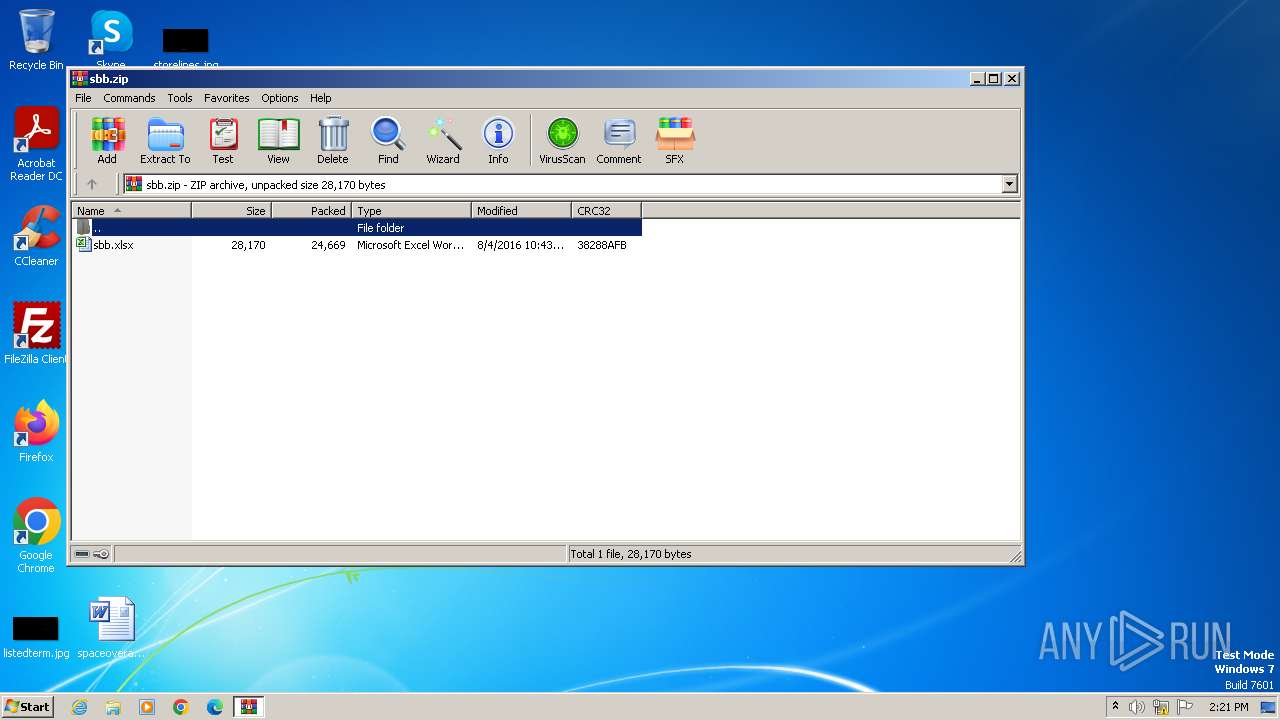
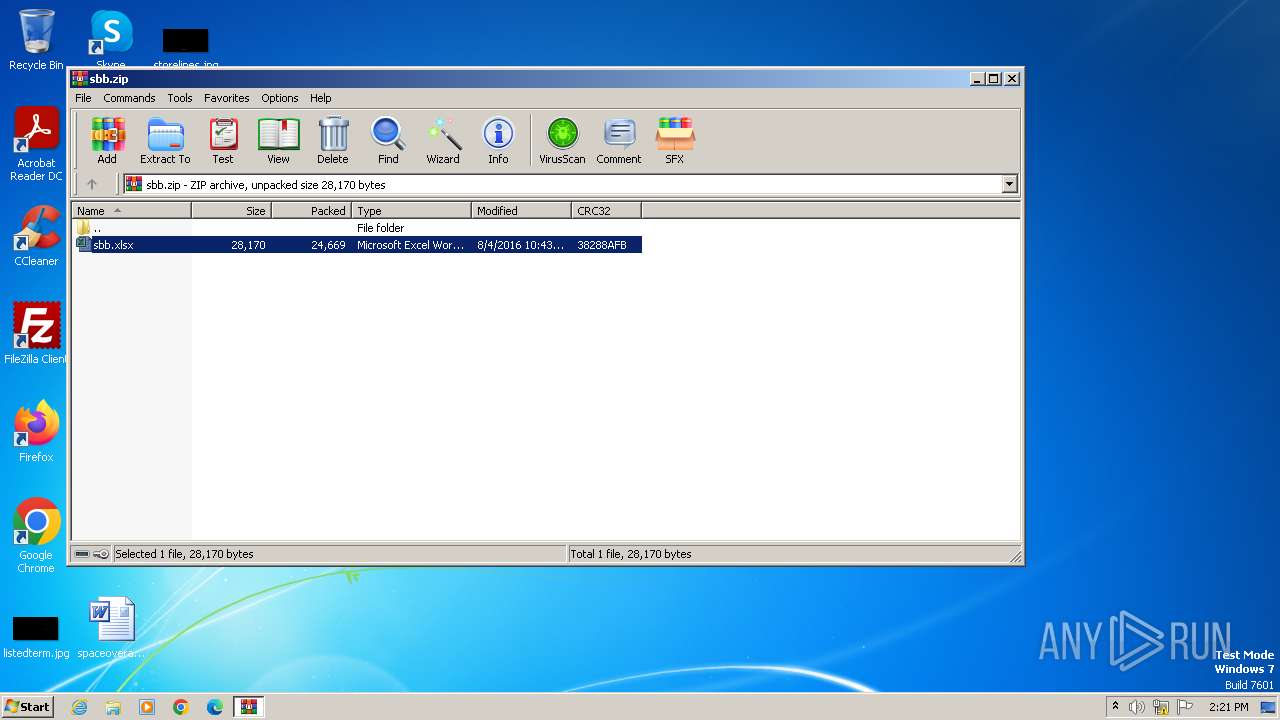
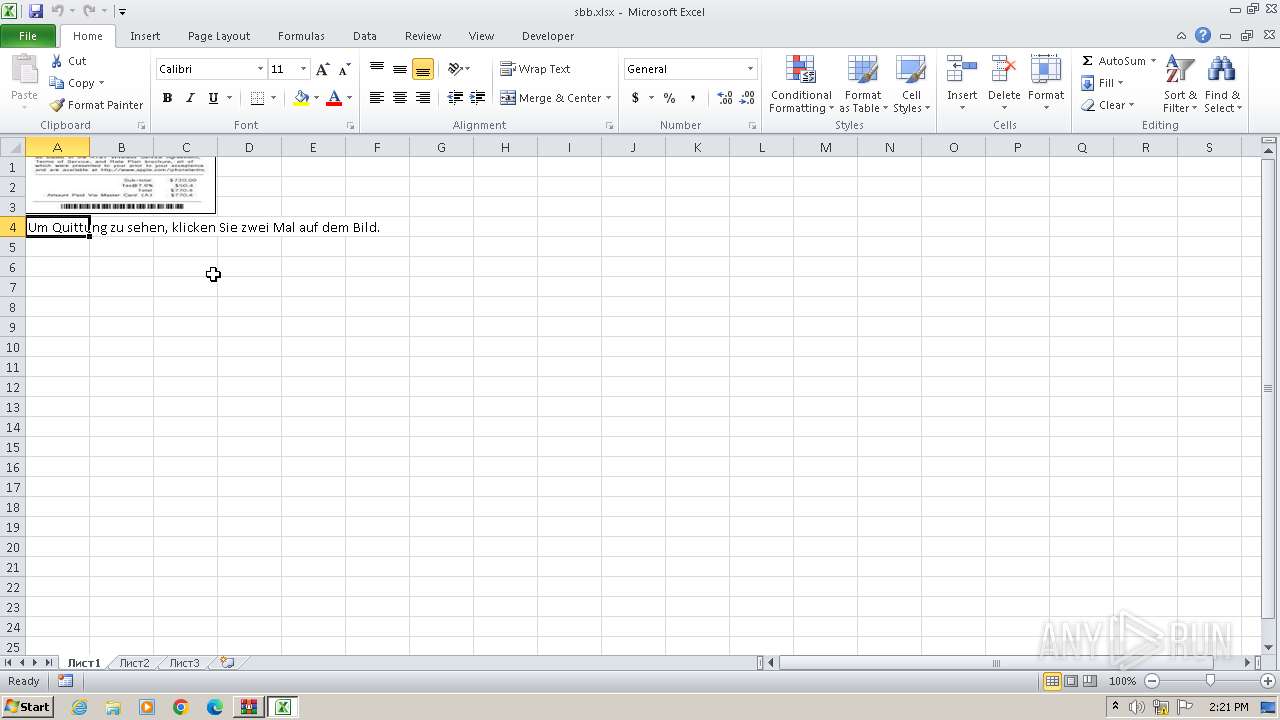
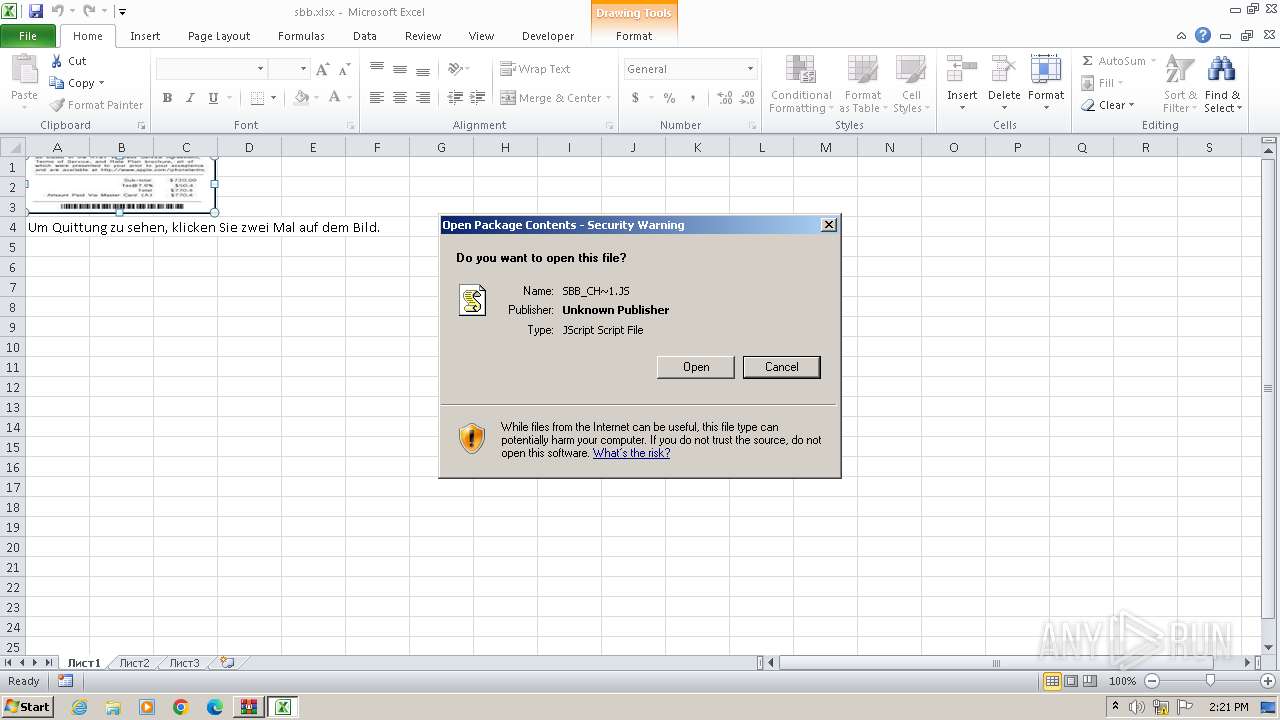
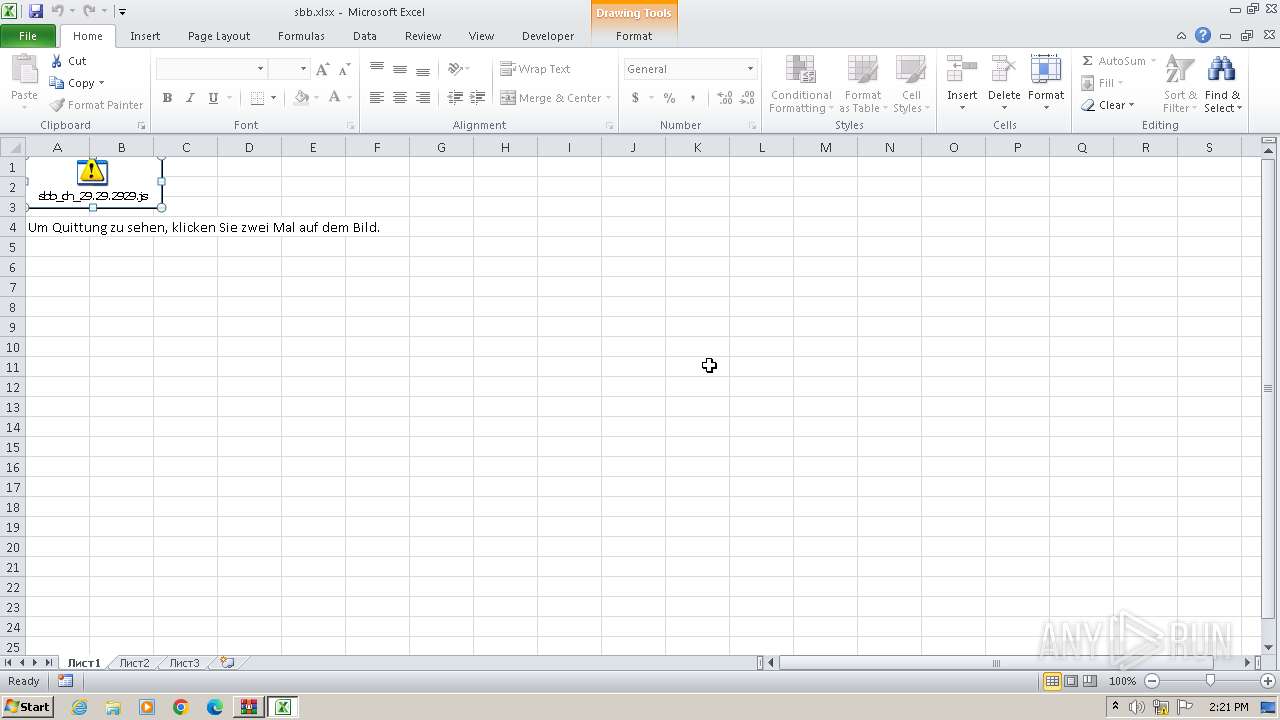
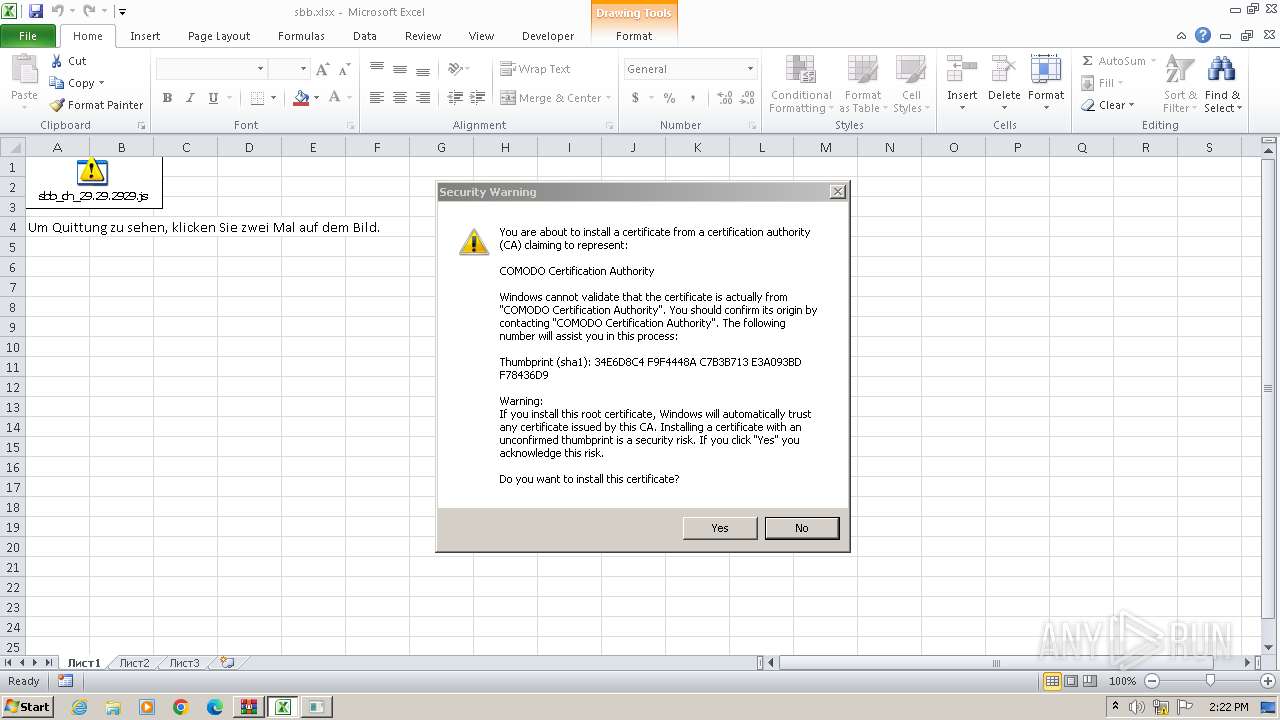
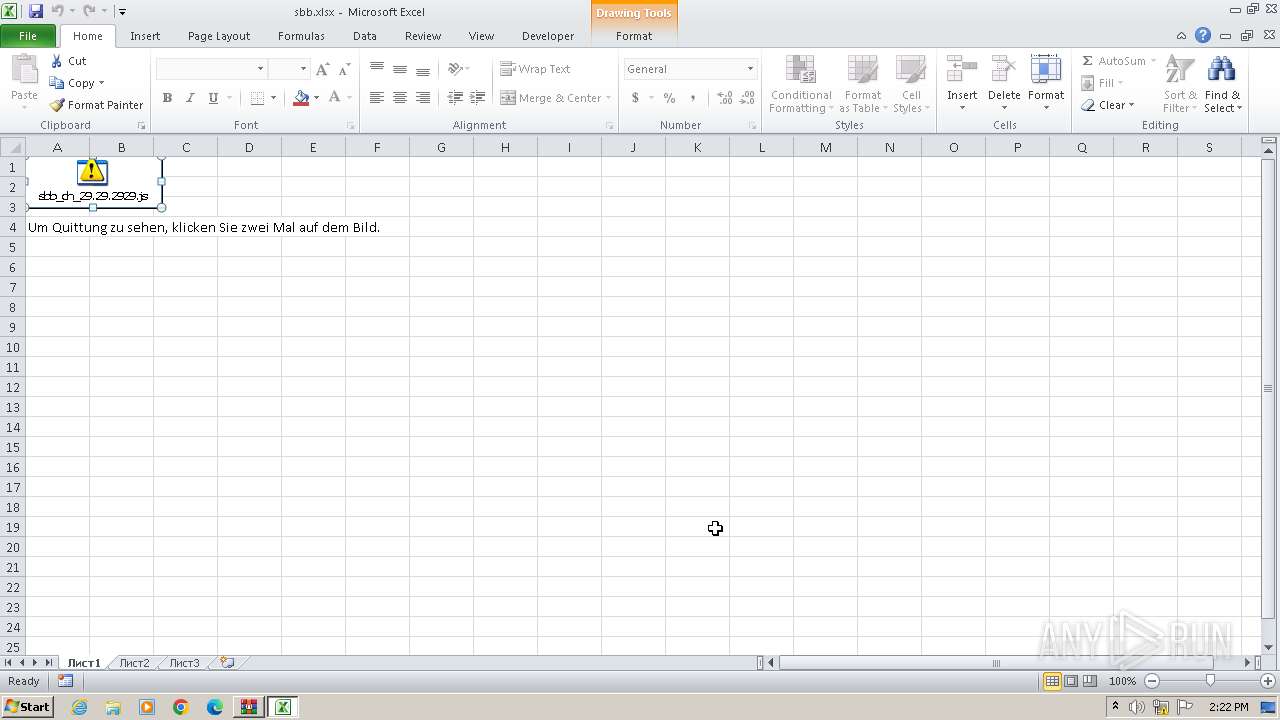
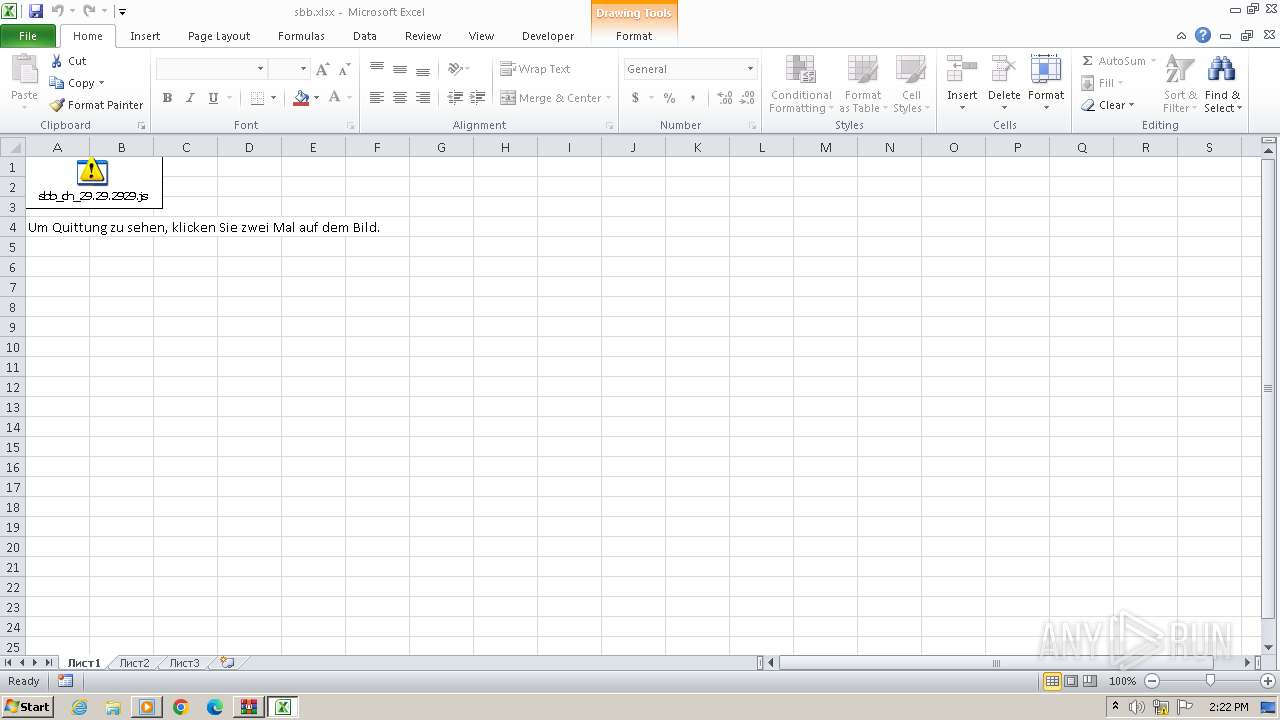
| File name: | sbb.zip |
| Full analysis: | https://app.any.run/tasks/a7cb40f1-9da2-4893-a467-b739c2efc43f |
| Verdict: | Malicious activity |
| Analysis date: | April 30, 2024, 13:21:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E3B8CF3E1885A9EB785688C1C4BAD529 |
| SHA1: | 43EFA66E10573FC9D711E086B6E27E2C3E11448F |
| SHA256: | FD8ACAD5370AB0CC1664BAB1EE2706447E994D4BEB875D5ACC538B44291B573F |
| SSDEEP: | 768:lWa0u++yNJqYNfejLHjh2lp2NnzsVqKh4ebsHdg:lsFNJpNkfh2l46Vzh46sHu |
MALICIOUS
Unusual execution from MS Office
- EXCEL.EXE (PID: 4028)
Gets %appdata% folder path (SCRIPT)
- wscript.exe (PID: 124)
Gets TEMP folder path (SCRIPT)
- wscript.exe (PID: 124)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 124)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 124)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 124)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 124)
Unusual connection from system programs
- wscript.exe (PID: 124)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 124)
Checks whether a specified folder exists (SCRIPT)
- wscript.exe (PID: 124)
Opens a text file (SCRIPT)
- wscript.exe (PID: 124)
Actions looks like stealing of personal data
- wscript.exe (PID: 124)
Deletes a file (SCRIPT)
- wscript.exe (PID: 124)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 124)
SUSPICIOUS
The process executes JS scripts
- EXCEL.EXE (PID: 4028)
Reads settings of System Certificates
- certutil.exe (PID: 692)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 124)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 124)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 124)
Uses TASKKILL.EXE to kill Browsers
- wscript.exe (PID: 124)
Checks for external IP
- wscript.exe (PID: 124)
Device Retrieving External IP Address Detected
- wscript.exe (PID: 124)
Reads the Internet Settings
- wscript.exe (PID: 124)
- rundll32.exe (PID: 2708)
- rundll32.exe (PID: 304)
Reads Microsoft Outlook installation path
- rundll32.exe (PID: 2708)
- rundll32.exe (PID: 304)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 124)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 124)
Changes charset (SCRIPT)
- wscript.exe (PID: 124)
Reads data from a file (SCRIPT)
- wscript.exe (PID: 124)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 124)
Runs shell command (SCRIPT)
- wscript.exe (PID: 124)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3980)
The process uses the downloaded file
- EXCEL.EXE (PID: 4028)
- FlashUtil32_32_0_0_453_ActiveX.exe (PID: 3584)
Checks proxy server information
- wscript.exe (PID: 124)
- rundll32.exe (PID: 2708)
- rundll32.exe (PID: 304)
Manual execution by a user
- iexplore.exe (PID: 2260)
- rundll32.exe (PID: 2708)
- wmpnscfg.exe (PID: 2484)
- rundll32.exe (PID: 304)
Application launched itself
- iexplore.exe (PID: 2260)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 2708)
- rundll32.exe (PID: 304)
Reads the computer name
- wmpnscfg.exe (PID: 2484)
Checks supported languages
- wmpnscfg.exe (PID: 2484)
Reads the bytes from the current stream and writes them to another stream(SCRIPT)
- wscript.exe (PID: 124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:08:05 04:43:48 |
| ZipCRC: | 0x38288afb |
| ZipCompressedSize: | 24669 |
| ZipUncompressedSize: | 28170 |
| ZipFileName: | sbb.xlsx |
Total processes
56
Monitored processes
14
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\SBB_CH~1.JS" | C:\Windows\System32\wscript.exe | EXCEL.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 304 | "C:\Windows\system32\rundll32.exe" shell32.dll,Control_RunDLL inetcpl.cpl,,4 | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | "C:\Windows\System32\taskkill.exe" /F /im iexplore.exe | C:\Windows\System32\taskkill.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2260 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 692 | "C:\Windows\System32\certutil.exe" -addstore -f -user "ROOT" "C:\Users\admin\AppData\Local\Temp\cert.der" | C:\Windows\System32\certutil.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
| 1680 | "C:\Windows\System32\taskkill.exe" /F /im firefox.exe | C:\Windows\System32\taskkill.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2260 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2316 | "C:\Windows\System32\taskkill.exe" /F /im chrome.exe | C:\Windows\System32\taskkill.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2484 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2708 | "C:\Windows\system32\rundll32.exe" shell32.dll,Control_RunDLL inetcpl.cpl,,4 | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
57 309
Read events
56 626
Write events
429
Delete events
254
Modification events
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\sbb.zip | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
81
Text files
243
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4028 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRB344.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 124 | wscript.exe | C:\Users\admin\AppData\Local\Temp\cert.der | binary | |
MD5:F71620B34287228CC2F47EAD67C8F839 | SHA256:84B9EAF464DB84027C3518408E8A74EF0D922F596CD7F9EFC7BBFB3168D8E2A3 | |||
| 568 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\polyfills-a40ef1678bae11e696dba45124eadd70[1].js | binary | |
MD5:99442AEC5788BCCAC9B2F0EAD2AFDD6B | SHA256:7CB5A87A6C0D05AAB2245CBF6A26ADAD80CD322540D5F6360DDE621BF922743F | |||
| 4028 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\SBB_CH~1.JS | binary | |
MD5:8B2EF48B351BD42D39EC9B8EA81CBE1F | SHA256:E30911AA372A348A675C595584B2BCBB786FDC9482ADB52B72ACFA01D9AF47E2 | |||
| 4028 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\SBB_CH~1.JS:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 124 | wscript.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:A4C0253717519EB0B07D5D8DD14F5D02 | SHA256:115B88AA451EA9D5CD010C60DB4B97759E55ECE806CF6C4EBA737C6290C0D044 | |||
| 2260 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
| 124 | wscript.exe | C:\Users\admin\AppData\Local\Temp\psf.ps1 | binary | |
MD5:7ED6126CEEF36FBE8D6AEFAC0B9AA2EF | SHA256:E05D102184297D1D25AD1676E4682A2F6A6F45A04A4BA51A6A03718564B8D2D0 | |||
| 568 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\NPT3CSDC.htm | html | |
MD5:4F8E702CC244EC5D4DE32740C0ECBD97 | SHA256:9E17CB15DD75BBBD5DBB984EDA674863C3B10AB72613CF8A39A00C3E11A8492A | |||
| 124 | wscript.exe | C:\Users\admin\AppData\Local\Temp\ps.ps1 | binary | |
MD5:858F0B6985956DE8FE89C4858377F1F4 | SHA256:BCE95ECD0C33A1A14FF5F9C8956B01E2401F6C52CF5455EBAFD083C22B490630 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
286
DNS requests
51
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
124 | wscript.exe | GET | 200 | 104.26.13.205:80 | http://api.ipify.org/ | unknown | — | — | unknown |
568 | iexplore.exe | GET | 301 | 125.212.247.176:80 | http://tinhte.vn/ | unknown | — | — | unknown |
2260 | iexplore.exe | GET | 304 | 173.222.108.147:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?714da040d5683210 | unknown | — | — | unknown |
124 | wscript.exe | GET | 200 | 104.26.13.205:80 | http://api.ipify.org/ | unknown | — | — | unknown |
124 | wscript.exe | GET | 200 | 104.26.13.205:80 | http://api.ipify.org/ | unknown | — | — | unknown |
124 | wscript.exe | GET | 200 | 104.26.13.205:80 | http://api.ipify.org/ | unknown | — | — | unknown |
124 | wscript.exe | GET | 200 | 104.26.13.205:80 | http://api.ipify.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
124 | wscript.exe | 104.26.13.205:80 | api.ipify.org | CLOUDFLARENET | US | unknown |
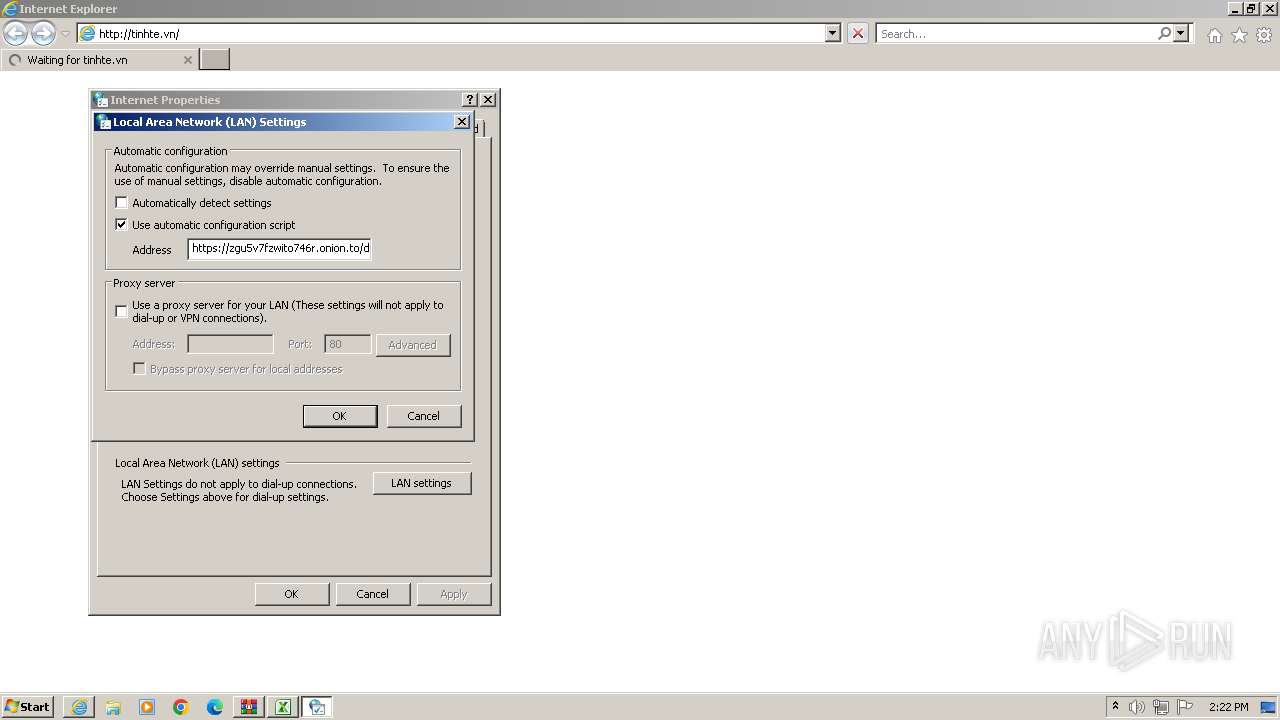
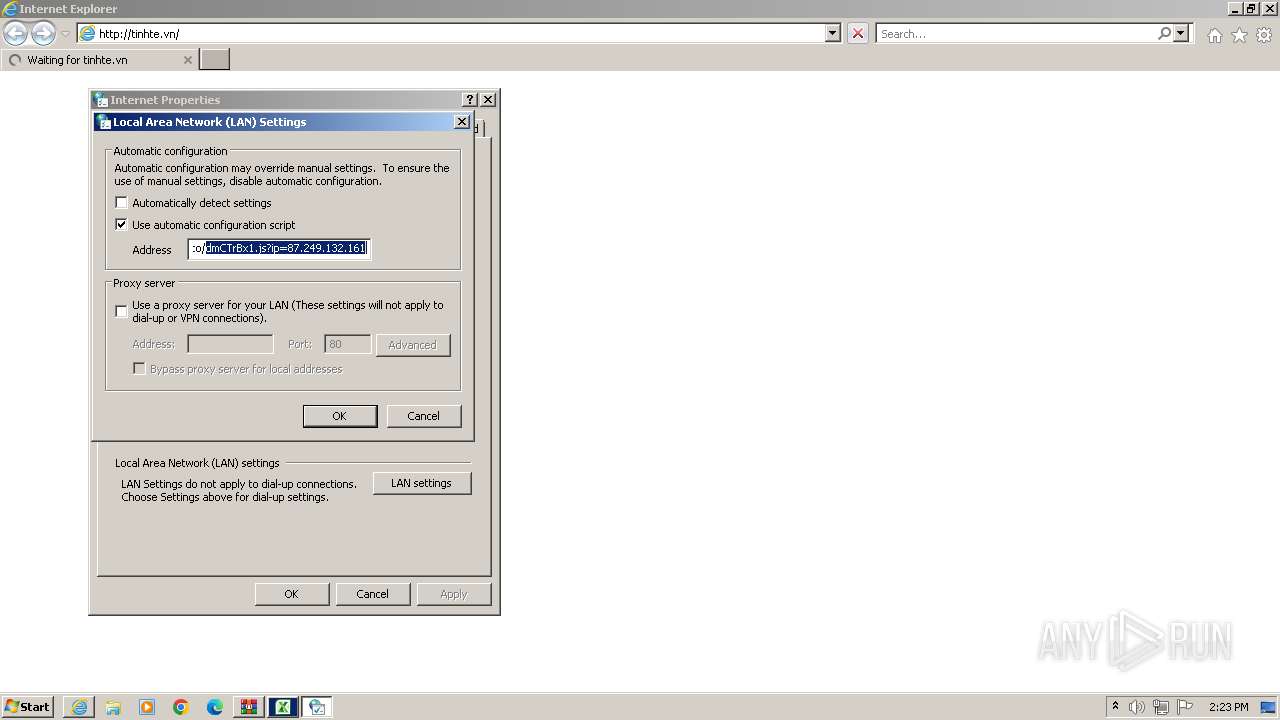
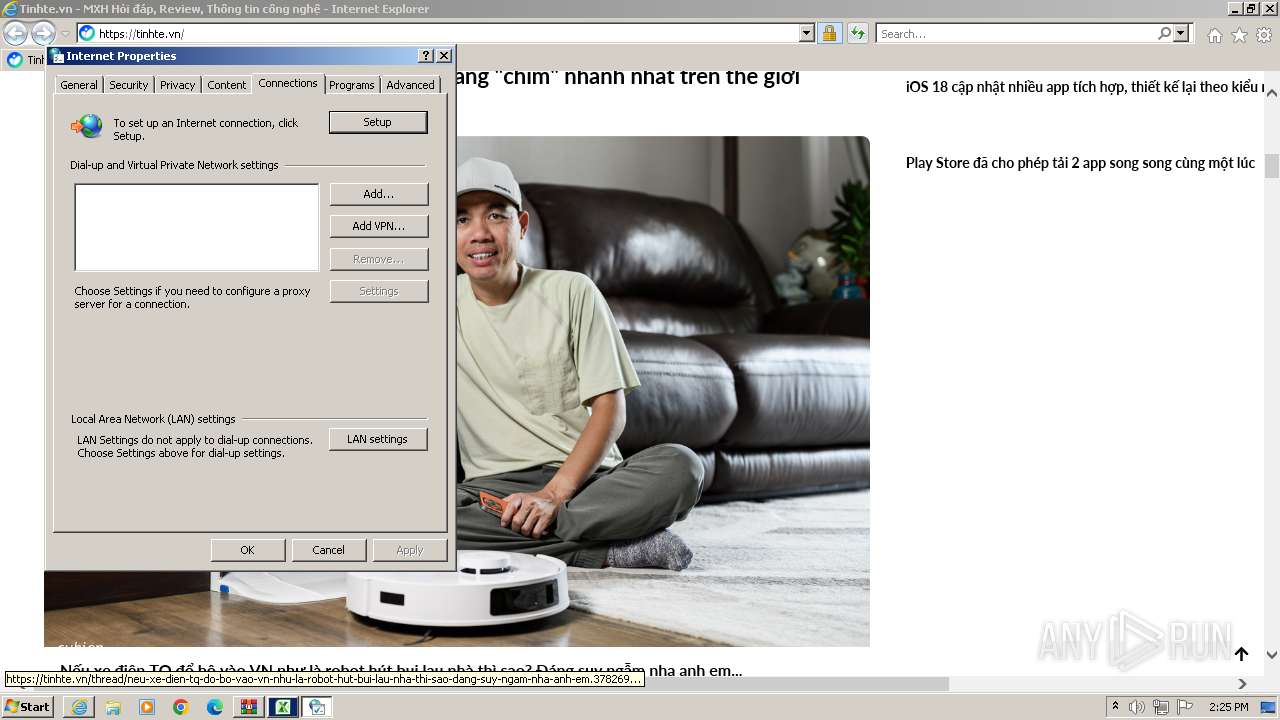
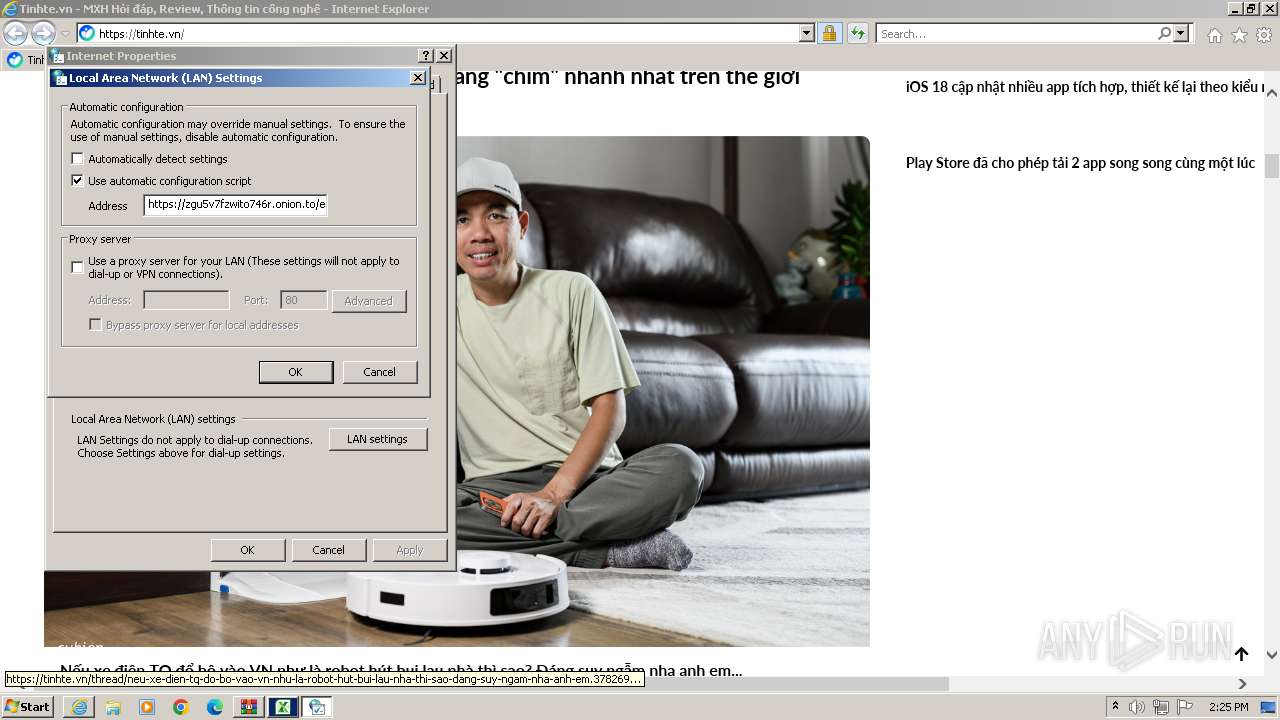
2260 | iexplore.exe | 49.13.77.253:443 | zgu5v7fzwito746r.onion.to | Hetzner Online GmbH | DE | unknown |
2260 | iexplore.exe | 2.19.120.21:443 | www.bing.com | Akamai International B.V. | DE | unknown |
568 | iexplore.exe | 13.107.5.80:443 | api.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
568 | iexplore.exe | 125.212.247.176:80 | tinhte.vn | CHT Compamy Ltd | VN | unknown |
840 | svchost.exe | 49.13.77.253:443 | zgu5v7fzwito746r.onion.to | Hetzner Online GmbH | DE | unknown |
568 | iexplore.exe | 125.212.247.176:443 | tinhte.vn | CHT Compamy Ltd | VN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.ipify.org |
| shared |
zgu5v7fzwito746r.onion.to |
| unknown |
www.bing.com |
| whitelisted |
tinhte.vn |
| whitelisted |
api.bing.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
124 | wscript.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup api.ipify.org |
124 | wscript.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
124 | wscript.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] Received IP address from server as result of HTTP request |
1088 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1088 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to .onion proxy Domain (onion.to) |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup api.ipify.org |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
— | — | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] Received IP address from server as result of HTTP request |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup api.ipify.org |