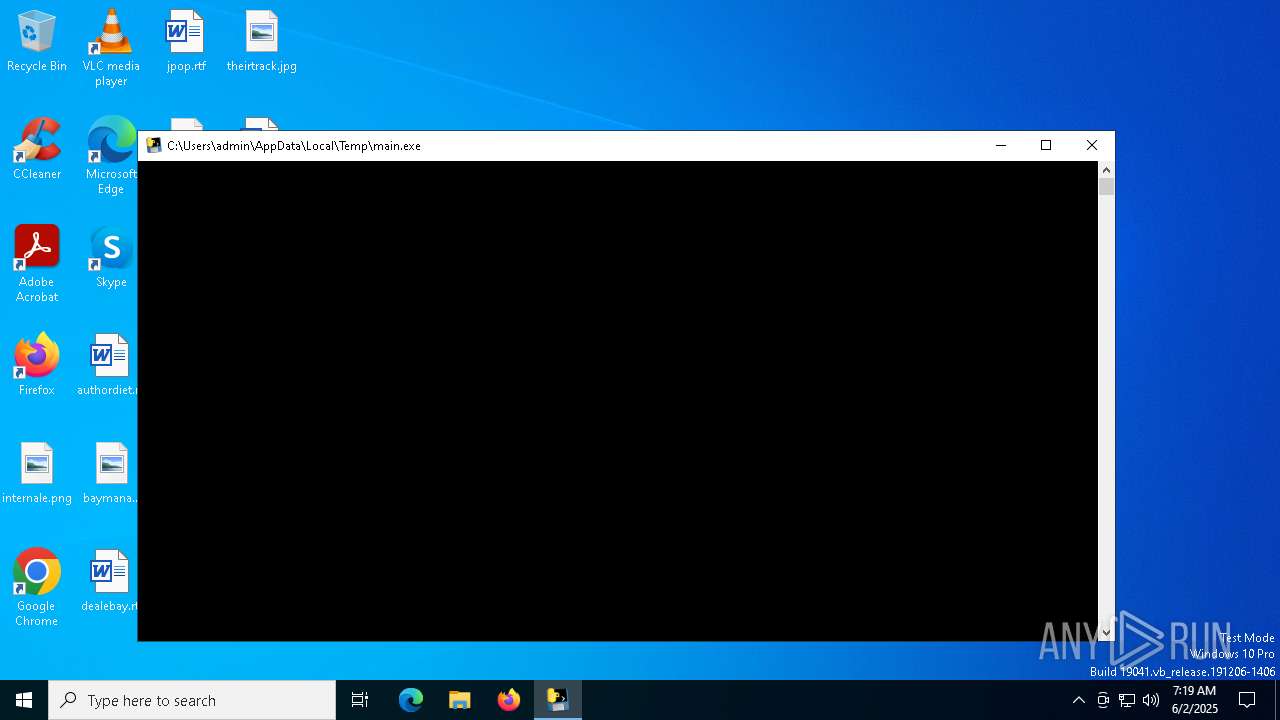
| File name: | main.exe |
| Full analysis: | https://app.any.run/tasks/99e71fb1-826d-4ab1-b28b-996aca87dfb8 |
| Verdict: | Malicious activity |
| Analysis date: | June 02, 2025, 07:19:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 987D476240E9343B40DDB26B3CCAFF5F |
| SHA1: | 25785BEE6CF3A6D9E1BC9D79F7384BD2DA74A433 |
| SHA256: | FD7655BC6CCBEE5034BEFF9409E3F55224759E2E2529AA4CCA4BAACCA5B7A3C7 |
| SSDEEP: | 98304:E/0CLEb/ONAnYRO4Y6ZhkDQet54nHZUj0v0QLFZfQpyJoic3yjHFGZWEpEy7IQRr:YAP881mwI/kisikP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- main.exe (PID: 7148)
The process drops C-runtime libraries
- main.exe (PID: 7148)
Executable content was dropped or overwritten
- main.exe (PID: 7148)
Process drops python dynamic module
- main.exe (PID: 7148)
Application launched itself
- main.exe (PID: 7148)
Loads Python modules
- main.exe (PID: 5304)
Starts CMD.EXE for commands execution
- main.exe (PID: 5304)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2316)
- cmd.exe (PID: 6920)
- cmd.exe (PID: 6416)
- cmd.exe (PID: 660)
- cmd.exe (PID: 7852)
- cmd.exe (PID: 668)
Lists computer manufacturer and model
- cmd.exe (PID: 6416)
INFO
Checks supported languages
- main.exe (PID: 7148)
- main.exe (PID: 5304)
Reads the computer name
- main.exe (PID: 7148)
- main.exe (PID: 5304)
Create files in a temporary directory
- main.exe (PID: 7148)
The sample compiled with english language support
- main.exe (PID: 7148)
Checks proxy server information
- main.exe (PID: 5304)
- slui.exe (PID: 4724)
Reads the software policy settings
- slui.exe (PID: 4724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:02 07:18:56+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 178688 |
| InitializedDataSize: | 153600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
139
Monitored processes
16
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | C:\WINDOWS\system32\cmd.exe /c "powershell -command "(Get-WmiObject Win32_BIOS).SerialNumber"" | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | C:\WINDOWS\system32\cmd.exe /c "powershell -command "(Get-WmiObject Win32_VideoController).Name"" | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2316 | C:\WINDOWS\system32\cmd.exe /c "powershell -command "(Get-WmiObject Win32_DiskDrive).Model"" | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3996 | powershell -command "(Get-WmiObject Win32_Processor).Name" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5304 | "C:\Users\admin\AppData\Local\Temp\main.exe" | C:\Users\admin\AppData\Local\Temp\main.exe | main.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 5968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6252 | powershell -command "(Get-WmiObject Win32_DiskDrive).Model" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6416 | C:\WINDOWS\system32\cmd.exe /c "powershell -command "(Get-WmiObject Win32_ComputerSystem).Manufacturer"" | C:\Windows\System32\cmd.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6724 | powershell -command "(Get-WmiObject Win32_BIOS).SerialNumber" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 610
Read events
29 610
Write events
0
Delete events
0
Modification events
Executable files
57
Suspicious files
2
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7148 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71482\_socket.pyd | executable | |
MD5:566CB4D39B700C19DBD7175BD4F2B649 | SHA256:77EBA293FE03253396D7BB6E575187CD026C80766D7A345EB72AD92F0BBBC3AA | |||
| 7148 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71482\_ctypes.pyd | executable | |
MD5:29873384E13B0A78EE9857604161514B | SHA256:3CC8500A958CC125809B0467930EBCCE88A09DCC0CEDD7A45FACF3E332F7DB33 | |||
| 7148 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71482\_decimal.pyd | executable | |
MD5:21FCB8E3D4310346A5DC1A216E7E23CA | SHA256:9A0E05274CAD8D90F6BA6BC594261B36BFBDDF4F5CA6846B6367FE6A4E2FDCE4 | |||
| 7148 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71482\_lzma.pyd | executable | |
MD5:D63E2E743EA103626D33B3C1D882F419 | SHA256:7C2D2030D5D246739C5D85F087FCF404BC36E1815E69A8AC7C9541267734FC28 | |||
| 7148 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71482\_bz2.pyd | executable | |
MD5:684D656AADA9F7D74F5A5BDCF16D0EDB | SHA256:A5DFB4A663DEF3D2276B88866F6D220F6D30CC777B5D841CF6DBB15C6858017C | |||
| 7148 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71482\_hashlib.pyd | executable | |
MD5:3E540EF568215561590DF215801B0F59 | SHA256:0ED7A6ED080499BC6C29D7113485A8A61BDBA93087B010FCA67D9B8289CBE6FA | |||
| 7148 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71482\_ssl.pyd | executable | |
MD5:689F1ABAC772C9E4C2D3BAD3758CB398 | SHA256:D3A89AA7E4A1DF1151632A8A5CAF338C4DDDB674EC093BFDBC122ADC9DB28A97 | |||
| 7148 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71482\_wmi.pyd | executable | |
MD5:47E6FD132F44A4FEB595BD0FDA3C4E1C | SHA256:4C47A733FB3CD748008A97A1C1C2DEC925849388E4F9E160D8A1C3FF37F42026 | |||
| 7148 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71482\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:059E5BA3DD03713D26DF8883746391A7 | SHA256:490126ABFA9F5D7A87268A78A0A511E6749AE52CC1114FDA0460ECEDDF0756F6 | |||
| 7148 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI71482\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:FC009A82F0FAB71E2C8ADF7F60F489C8 | SHA256:D2ADD358A45999E95F67D923F1B4F5A27F5A1A895225121909D716EDF5AE13E7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.26:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5736 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5736 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
8184 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.26:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5408 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5304 | main.exe | 188.114.96.3:443 | imgui.space | CLOUDFLARENET | NL | unknown |
6544 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
imgui.space |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |