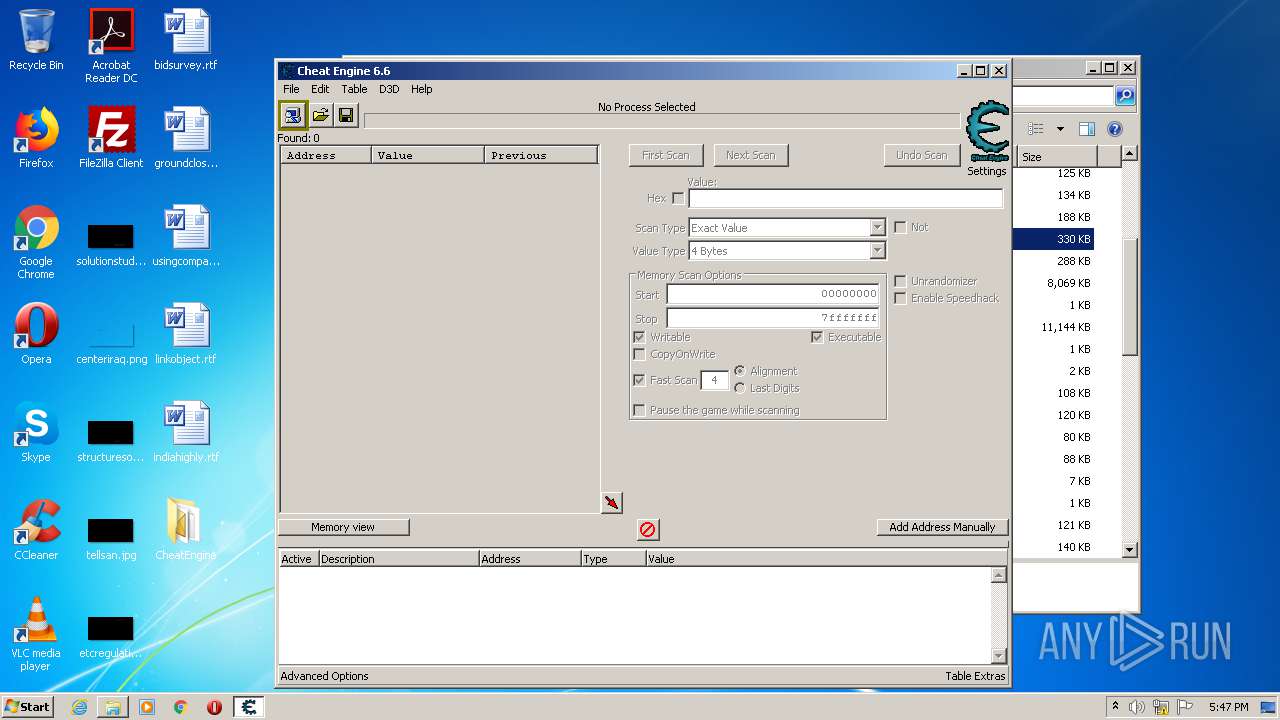
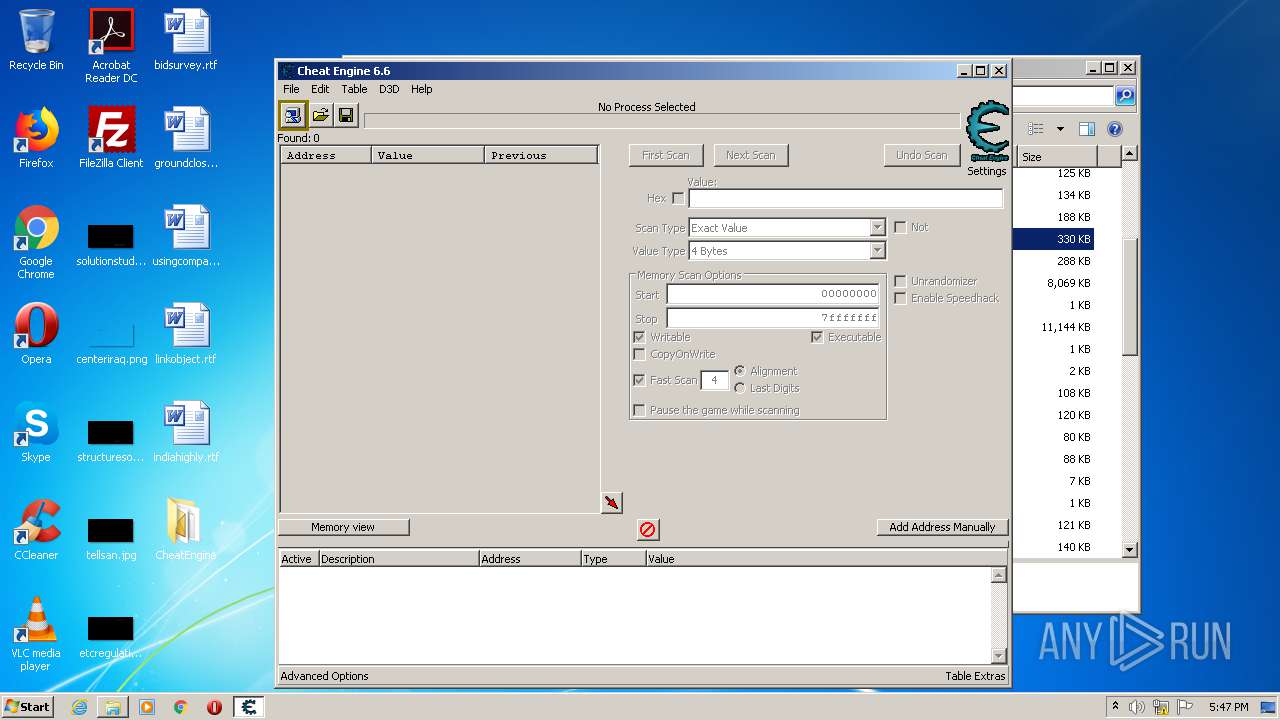
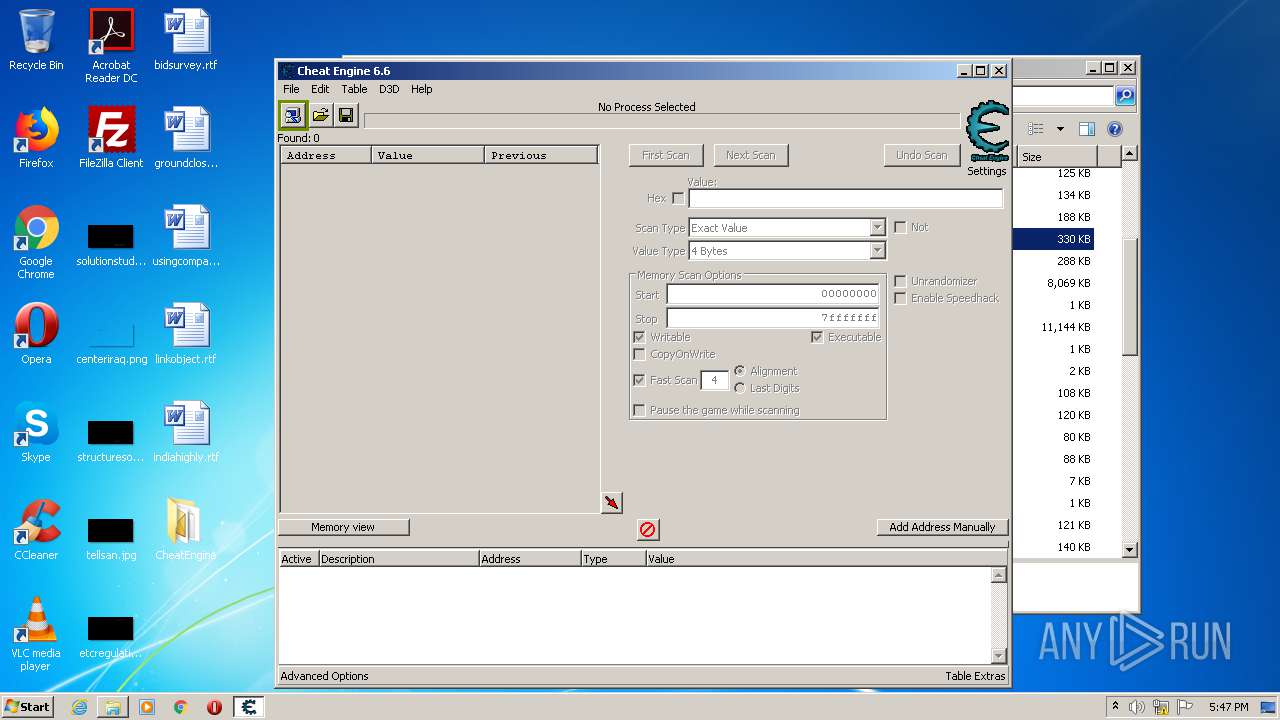
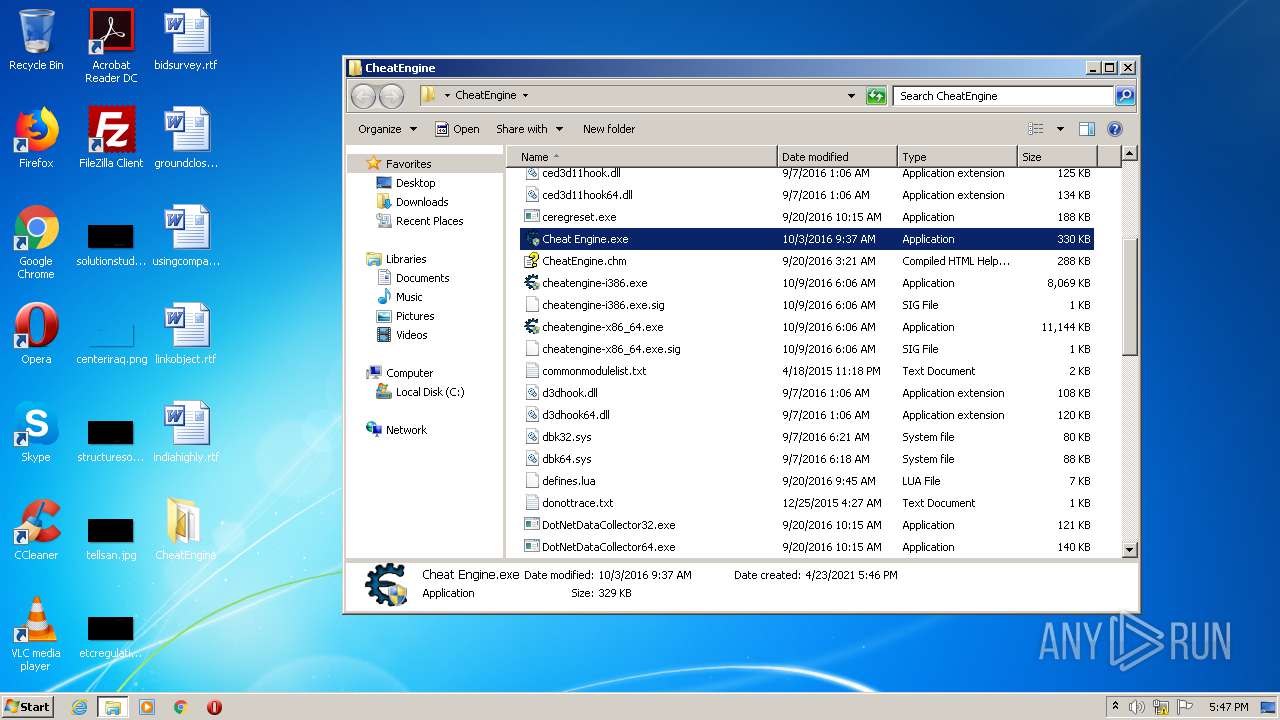
| File name: | CheatEngine.zip |
| Full analysis: | https://app.any.run/tasks/3f2b5bcc-311c-4117-8832-2d6011e287c3 |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2021, 16:45:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | BBF128FCB9ABE7595741214179BA672E |
| SHA1: | 664CED6B12EAB81BFEBBDB6CBE75996184B7CB9B |
| SHA256: | FD6F7E8E7A351FE3E0FC0B2997B1AE3606FFEF62647C5E677DF4BDC9A9AC6334 |
| SSDEEP: | 393216:ckT2HEJmHYUrPmG2f45GacbEU8HfbSKh3B595v3sn/T9H1uKH70nB1kkQSZrXaGM:k/4yPZ2sjYz8Hfua39Bsnb9HEKbG7ks0 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3204)
- cheatengine-i386.exe (PID: 1232)
- cheatengine-i386.exe (PID: 3628)
- cheatengine-i386.exe (PID: 1660)
Application was dropped or rewritten from another process
- Cheat Engine.exe (PID: 2272)
- cheatengine-i386.exe (PID: 1232)
- Cheat Engine.exe (PID: 2708)
- Cheat Engine.exe (PID: 2900)
- Cheat Engine.exe (PID: 984)
- cheatengine-i386.exe (PID: 3628)
- cheatengine-i386.exe (PID: 1052)
- cheatengine-i386.exe (PID: 1660)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2552)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2552)
Drops a file with too old compile date
- WinRAR.exe (PID: 2552)
INFO
Manual execution by user
- Cheat Engine.exe (PID: 2708)
- Cheat Engine.exe (PID: 2272)
- Cheat Engine.exe (PID: 2900)
- Cheat Engine.exe (PID: 984)
- cheatengine-i386.exe (PID: 1052)
- cheatengine-i386.exe (PID: 1660)
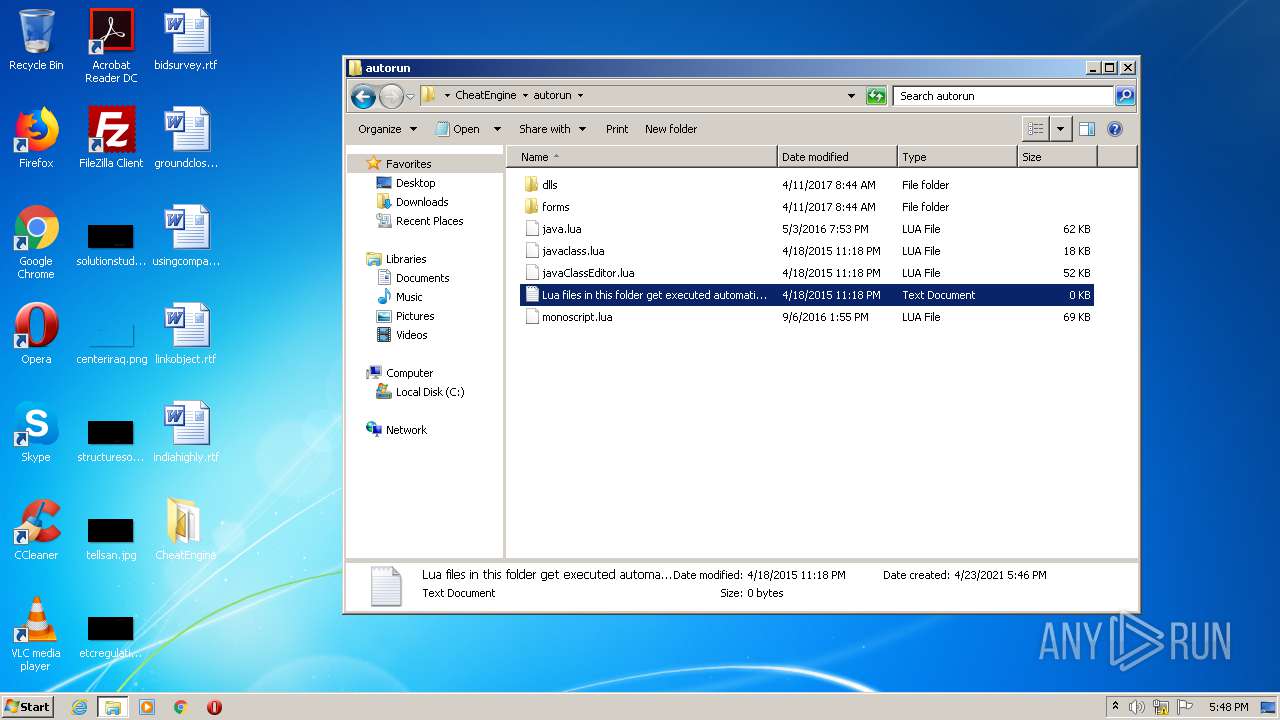
- NOTEPAD.EXE (PID: 2852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2021:04:23 18:38:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | CheatEngine/ |
Total processes
61
Monitored processes
11
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Users\admin\Desktop\CheatEngine\Cheat Engine.exe" | C:\Users\admin\Desktop\CheatEngine\Cheat Engine.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 6.3.0.0 Modules
| |||||||||||||||
| 1052 | "C:\Users\admin\Desktop\CheatEngine\cheatengine-i386.exe" | C:\Users\admin\Desktop\CheatEngine\cheatengine-i386.exe | — | explorer.exe | |||||||||||
User: admin Company: Cheat Engine Integrity Level: MEDIUM Description: Cheat Engine Exit code: 3221226540 Version: 6.6.0.4880 Modules
| |||||||||||||||
| 1232 | "C:\Users\admin\Desktop\CheatEngine\cheatengine-i386.exe" | C:\Users\admin\Desktop\CheatEngine\cheatengine-i386.exe | Cheat Engine.exe | ||||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Cheat Engine Exit code: 0 Version: 6.6.0.4880 Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\Desktop\CheatEngine\cheatengine-i386.exe" | C:\Users\admin\Desktop\CheatEngine\cheatengine-i386.exe | explorer.exe | ||||||||||||
User: admin Company: Cheat Engine Integrity Level: HIGH Description: Cheat Engine Exit code: 0 Version: 6.6.0.4880 Modules
| |||||||||||||||
| 2272 | "C:\Users\admin\Desktop\CheatEngine\Cheat Engine.exe" | C:\Users\admin\Desktop\CheatEngine\Cheat Engine.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 6.3.0.0 Modules
| |||||||||||||||
| 2552 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\CheatEngine.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2708 | "C:\Users\admin\Desktop\CheatEngine\Cheat Engine.exe" | C:\Users\admin\Desktop\CheatEngine\Cheat Engine.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 6.3.0.0 Modules
| |||||||||||||||
| 2852 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\CheatEngine\autorun\Lua files in this folder get executed automatically.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2900 | "C:\Users\admin\Desktop\CheatEngine\Cheat Engine.exe" | C:\Users\admin\Desktop\CheatEngine\Cheat Engine.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 6.3.0.0 Modules
| |||||||||||||||
| 3204 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 039
Read events
985
Write events
54
Delete events
0
Modification events
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CheatEngine.zip | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
46
Suspicious files
4
Text files
41
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2552 | WinRAR.exe | C:\Users\admin\Desktop\CheatEngine\allochook-i386.dll | executable | |
MD5:— | SHA256:— | |||
| 2552 | WinRAR.exe | C:\Users\admin\Desktop\CheatEngine\allochook-x86_64.dll | executable | |
MD5:— | SHA256:— | |||
| 2552 | WinRAR.exe | C:\Users\admin\Desktop\CheatEngine\autorun\dlls\MonoDataCollector64.dll | executable | |
MD5:43BBEAC528D0F7379C6708FCB9406FF0 | SHA256:881C052F66543E4722E99C496B611412B3A7A869D0E02ADA9AB2C144297F1E15 | |||
| 2552 | WinRAR.exe | C:\Users\admin\Desktop\CheatEngine\autorun\dlls\64\CEJVMTI.dll | executable | |
MD5:CEFC5C56720CA850CCB20FAF47733BD2 | SHA256:F107DD69B4115864D289F364FAFC0E045FD3E9FC4BDE5586CE8C1BCF59CC65A7 | |||
| 2552 | WinRAR.exe | C:\Users\admin\Desktop\CheatEngine\autorun\dlls\src\Java\CEJVMTI\CEJVMTI\dllmain.cpp | text | |
MD5:66EFA1B79D7AEF68DFA369074ABC9CAA | SHA256:542E67D6247001859B6BB38C2AA085F5446371EB2F2385546E12D0BF275DE503 | |||
| 2552 | WinRAR.exe | C:\Users\admin\Desktop\CheatEngine\autorun\dlls\32\CEJVMTI.dll | executable | |
MD5:B02FA5C8EEFBCD010AAAC97A94FF62BB | SHA256:7BD0D77FD790215BB67337F9F210B05AAAB0193D105B8FF86EC422E9875EB033 | |||
| 2552 | WinRAR.exe | C:\Users\admin\Desktop\CheatEngine\autorun\dlls\src\Common\Pipe.h | text | |
MD5:86AC093E951A8CFA7FE1E020E8A61026 | SHA256:B7758C2F97AB776B02FCAAB9D253277A96DCB318C66DD72D294A417290AAD761 | |||
| 2552 | WinRAR.exe | C:\Users\admin\Desktop\CheatEngine\autorun\dlls\src\Java\CEJVMTI\CEJVMTI\CEJVMTI.h | text | |
MD5:20AF26E2AB559DDC6CA1929834DA003E | SHA256:18C5FB7CB71EB7B2D1835CE44B24E09213AA885C1407E4E2401FBD2D74970D8E | |||
| 2552 | WinRAR.exe | C:\Users\admin\Desktop\CheatEngine\autorun\dlls\src\Java\CEJVMTI\CEJVMTI\CEJVMTI.cpp | text | |
MD5:021AA48BED78C67E3A7969BE8BC0BB5B | SHA256:C9EF523D9ABCAC32BC86CC5E316C03749B64EC4BCE0343289C05E9366639696D | |||
| 2552 | WinRAR.exe | C:\Users\admin\Desktop\CheatEngine\autorun\dlls\src\Java\CEJVMTI\CEJVMTI\stdafx.cpp | text | |
MD5:2B573B5A4D6EC77A3138EC43A1B260C9 | SHA256:4CFBA14A6F738DD17BE066C3A8F595B84C0C33C1774C83736987B9EE8C0DF16B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
cheatengine-i386.exe | Offset of LBR_Count=760 |
cheatengine-i386.exe | sizeof fxstate = 512 |
cheatengine-i386.exe | TSymhandler.create |
cheatengine-i386.exe | TSymhandler.create 1 |
cheatengine-i386.exe | TSymhandler.create 2 |
cheatengine-i386.exe | TSymhandler.create 3 |
cheatengine-i386.exe | TSymbolListHandler.create 1 |
cheatengine-i386.exe | TSymbolListHandler.create 2 |
cheatengine-i386.exe | TSymbolListHandler.create exit |
cheatengine-i386.exe | TSymhandler.create exit |