| File name: | TestAgent64.exe |
| Full analysis: | https://app.any.run/tasks/27aa7c5b-2ac8-4302-9725-81596e9d0751 |
| Verdict: | Malicious activity |
| Analysis date: | June 05, 2025, 07:00:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 03A239AF360ADDE2651938C882610AFC |
| SHA1: | 039F5585C4293472496B157DDA4FFA7EBF35EE7C |
| SHA256: | FD643D6653D359C85AD9B1ED7E0BDFD348391C5182AF1E45602CF7B4E9A16052 |
| SSDEEP: | 98304:66eO3YuuLq1neGrQib3Ha4lQRlvQdBZpieeykzEIjysMI3nf/BSz/sRmIp43PGlh:B9rJrWpY3MoQuy93AUR8EAWM624kQ0Y |
MALICIOUS
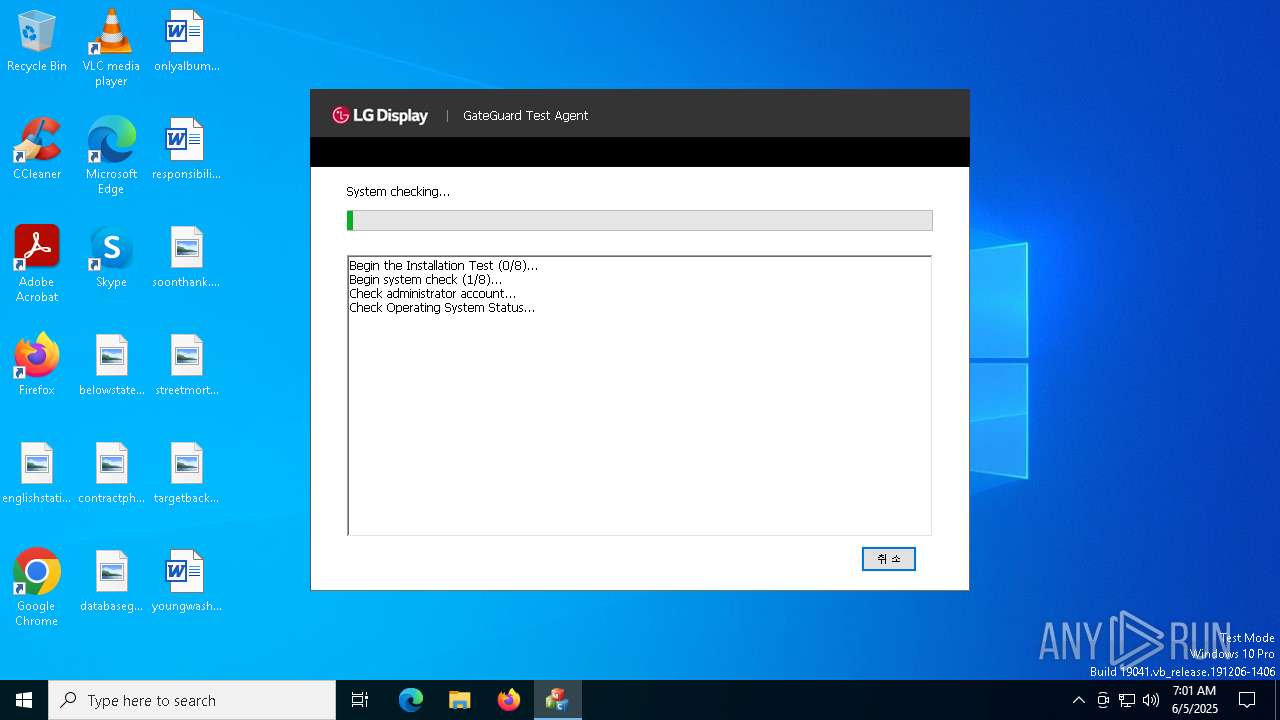
Executing a file with an untrusted certificate
- dccsetup.exe (PID: 3268)
- dccd.exe (PID: 7804)
- dccctrl.exe (PID: 5596)
- dccd.exe (PID: 8088)
Starts NET.EXE for service management
- dccsetup.tmp (PID: 6148)
- net.exe (PID: 8140)
Application was injected by another process
- UserOOBEBroker.exe (PID: 1248)
- dllhost.exe (PID: 6176)
- TextInputHost.exe (PID: 6864)
- svchost.exe (PID: 4684)
- RuntimeBroker.exe (PID: 1036)
- ApplicationFrameHost.exe (PID: 6952)
- RuntimeBroker.exe (PID: 5368)
- ctfmon.exe (PID: 956)
- SearchApp.exe (PID: 2924)
- StartMenuExperienceHost.exe (PID: 1968)
- dllhost.exe (PID: 6896)
- dwm.exe (PID: 6568)
- svchost.exe (PID: 4952)
- svchost.exe (PID: 6608)
- explorer.exe (PID: 5492)
- svchost.exe (PID: 4544)
- sihost.exe (PID: 4984)
- fontdrvhost.exe (PID: 912)
- fontdrvhost.exe (PID: 2360)
- RuntimeBroker.exe (PID: 6160)
Runs injected code in another process
- dccd.exe (PID: 8088)
SUSPICIOUS
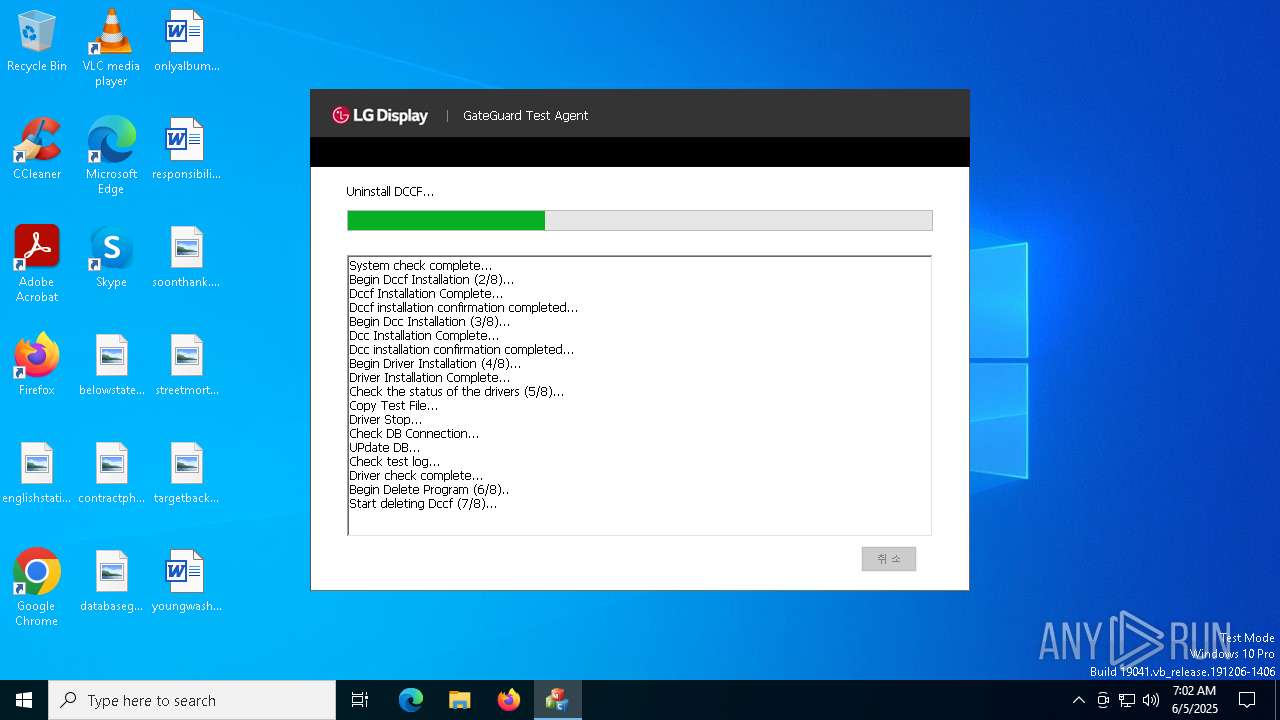
Executable content was dropped or overwritten
- TestAgent64.exe (PID: 8012)
- dccsetup.exe (PID: 3268)
- dccsetup.tmp (PID: 6148)
- dccd.exe (PID: 8088)
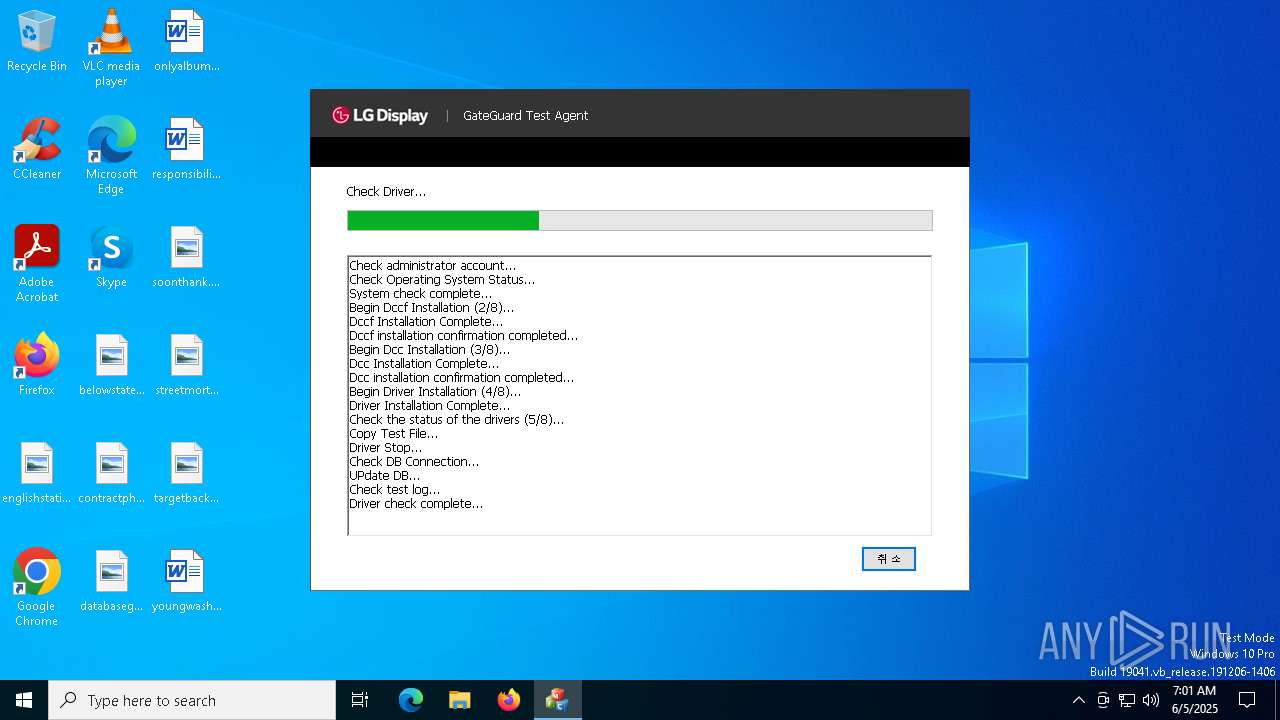
Executes as Windows Service
- dccf.exe (PID: 5552)
- dccd.exe (PID: 8088)
Reads the Windows owner or organization settings
- dccsetup.tmp (PID: 6148)
Drops a system driver (possible attempt to evade defenses)
- dccsetup.tmp (PID: 6148)
- dccd.exe (PID: 8088)
Starts SC.EXE for service management
- dccd.exe (PID: 7804)
Reads security settings of Internet Explorer
- dccd.exe (PID: 7804)
- dccsetup.tmp (PID: 6148)
Reads the date of Windows installation
- dccd.exe (PID: 7804)
Restarts service on failure
- sc.exe (PID: 7508)
Creates or modifies Windows services
- dccd.exe (PID: 8088)
There is functionality for taking screenshot (YARA)
- dccf.exe (PID: 5552)
Creates files in the driver directory
- dccd.exe (PID: 8088)
INFO
Create files in a temporary directory
- TestAgent64.exe (PID: 8012)
- dccsetup.exe (PID: 3268)
- dccsetup.tmp (PID: 6148)
- TestAgent.exe (PID: 7812)
Checks supported languages
- TestAgent64.exe (PID: 8012)
- TestAgent.exe (PID: 7812)
- dccf.exe (PID: 6044)
- dccf.exe (PID: 5552)
- dccsetup.exe (PID: 3268)
- dccsetup.tmp (PID: 6148)
- pcdtool.exe (PID: 7404)
- dccd.exe (PID: 7804)
- dccd.exe (PID: 8088)
- dccctrl.exe (PID: 5596)
The sample compiled with english language support
- TestAgent64.exe (PID: 8012)
- dccsetup.tmp (PID: 6148)
- dccd.exe (PID: 8088)
The sample compiled with korean language support
- TestAgent64.exe (PID: 8012)
Reads the computer name
- TestAgent.exe (PID: 7812)
- dccf.exe (PID: 6044)
- dccf.exe (PID: 5552)
- dccsetup.tmp (PID: 6148)
- dccd.exe (PID: 7804)
- dccd.exe (PID: 8088)
Creates files in the program directory
- TestAgent.exe (PID: 7812)
- dccf.exe (PID: 5552)
- dccsetup.tmp (PID: 6148)
- dccd.exe (PID: 8088)
The sample compiled with russian language support
- dccsetup.tmp (PID: 6148)
The sample compiled with german language support
- dccsetup.tmp (PID: 6148)
Process checks computer location settings
- dccd.exe (PID: 7804)
- dccsetup.tmp (PID: 6148)
Detects InnoSetup installer (YARA)
- dccsetup.exe (PID: 3268)
Compiled with Borland Delphi (YARA)
- dccsetup.exe (PID: 3268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:12:05 22:50:52+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24064 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fa |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
148
Monitored processes
40
Malicious processes
25
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 912 | "fontdrvhost.exe" | C:\Windows\System32\fontdrvhost.exe | wininit.exe | ||||||||||||
User: UMFD-0 Company: Microsoft Corporation Integrity Level: LOW Description: Usermode Font Driver Host Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 956 | "ctfmon.exe" | C:\Windows\System32\ctfmon.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CTF Loader Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | C:\Windows\System32\RuntimeBroker.exe -Embedding | C:\Windows\System32\RuntimeBroker.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Runtime Broker Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1248 | C:\Windows\System32\oobe\UserOOBEBroker.exe -Embedding | C:\Windows\System32\oobe\UserOOBEBroker.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: User OOBE Broker Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1968 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | svchost.exe | ||||||||||||
User: admin Integrity Level: LOW Modules
| |||||||||||||||
| 2360 | "fontdrvhost.exe" | C:\Windows\System32\fontdrvhost.exe | winlogon.exe | ||||||||||||
User: UMFD-5 Company: Microsoft Corporation Integrity Level: LOW Description: Usermode Font Driver Host Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | dccd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2924 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | /VERYSILENT | C:\Users\admin\AppData\Local\Temp\LGD_SVNO\dccsetup.exe | TestAgent.exe | ||||||||||||
User: admin Company: Digitalsense Co., Ltd. Integrity Level: HIGH Description: dcc Setup Exit code: 0 Version: 2.3.6.3971 Modules
| |||||||||||||||
| 4544 | C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup -s CDPUserSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 598
Read events
3 577
Write events
16
Delete events
5
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000A031C |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (956) ctfmon.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Input\TypingInsights |
| Operation: | write | Name: | Insights |
Value: 02000000071DE8C131CC8360A3D6D9C1330A686B165ABA2E235F5A5C | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000A0314 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000A0314 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000E00F6 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000E00F6 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000001402DE |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000001402DE |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:000000000006028C |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (4984) sihost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppModel\SystemAppData\Microsoft.Windows.Search_cw5n1h2txyewy |
| Operation: | write | Name: | WasEverActivated |
Value: 1 | |||
Executable files
46
Suspicious files
5
Text files
9
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8012 | TestAgent64.exe | C:\Users\admin\AppData\Local\Temp\LGD_SVNO\gxcore.dll | executable | |
MD5:7B4BC821B51A6AE4C9BFB6EA5391AF99 | SHA256:CBA62F7F43AC0154363DD6DAE0B5231B07283F4D85BD72B2A74E141F40585493 | |||
| 8012 | TestAgent64.exe | C:\Users\admin\AppData\Local\Temp\LGD_SVNO\dccsetup.exe | executable | |
MD5:0E017448B38A8BED8C6AA42A44F94E9F | SHA256:FDD5E664CAE97E8EAB7ECFA8CC14E50978EC0BDADB6FB904BA3127EF745D7440 | |||
| 8012 | TestAgent64.exe | C:\Users\admin\AppData\Local\Temp\LGD_SVNO\dccd.dic | text | |
MD5:D031A2F575331614259395BB3C0AD3EB | SHA256:586B1611BF9BCB1F70B93A2E06F0FA8C6A9544C277038B9FE75E8DEB77CCE2E3 | |||
| 8012 | TestAgent64.exe | C:\Users\admin\AppData\Local\Temp\LGD_SVNO\dccsetup.ini | ini | |
MD5:DB38754FE39FD222434626C249EFF178 | SHA256:A57AF70DA4E4EAD96CE23AB3301624BAE6FDA23291CCCE6B643D0E480D5CE314 | |||
| 8012 | TestAgent64.exe | C:\Users\admin\AppData\Local\Temp\LGD_SVNO\dccf.exe | executable | |
MD5:D93AB8DCAAC51C576D773FC04641E0C7 | SHA256:E44AF75C30DCB035DF8CDF9C8AA7F59FD782A252AD6A10E497F255EC4EE57C84 | |||
| 8012 | TestAgent64.exe | C:\Users\admin\AppData\Local\Temp\LGD_SVNO\LangEng.dll | executable | |
MD5:7E92FA08A791542102BFC259ECBDC05C | SHA256:ECE176A8AF3BD82943F8464504A72C894034BDC92CE34DCC8B36677B7D5C018A | |||
| 3268 | dccsetup.exe | C:\Users\admin\AppData\Local\Temp\is-DRPIF.tmp\dccsetup.tmp | executable | |
MD5:90FC739C83CD19766ACB562C66A7D0E2 | SHA256:821BD11693BF4B4B2B9F3C196036E1F4902ABD95FB26873EA6C43E123B8C9431 | |||
| 6148 | dccsetup.tmp | C:\Users\admin\AppData\Local\Temp\is-UACBO.tmp\dccd.dic | text | |
MD5:D031A2F575331614259395BB3C0AD3EB | SHA256:586B1611BF9BCB1F70B93A2E06F0FA8C6A9544C277038B9FE75E8DEB77CCE2E3 | |||
| 6176 | dllhost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AppData\Indexed DB\edb.chk | binary | |
MD5:60F0D919AAFA07FDDB72CE01EDBC9832 | SHA256:79E61D407A24A9648A8FA8247F16E30466949EF181873BCDD2EBD9CCD444DB24 | |||
| 6148 | dccsetup.tmp | C:\Users\admin\AppData\Local\Temp\is-UACBO.tmp\pcdtool.exe | executable | |
MD5:703E94540C5AE9FEF8F38CB2F3009BE9 | SHA256:2A4B05717D75FFA35349E212BAE81A1F3D5C50F328F9E61509D0FF7274CEA7CC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
30
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.20.245.135:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
132 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
132 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 2.20.245.135:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |