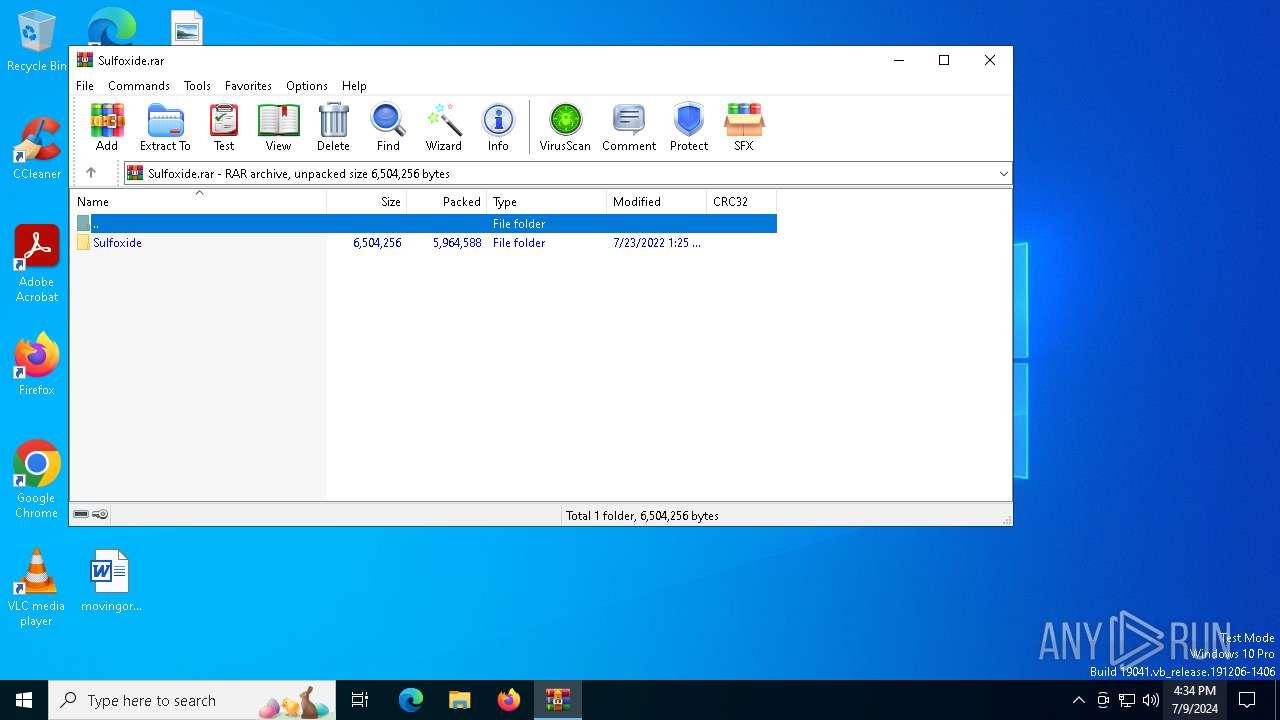
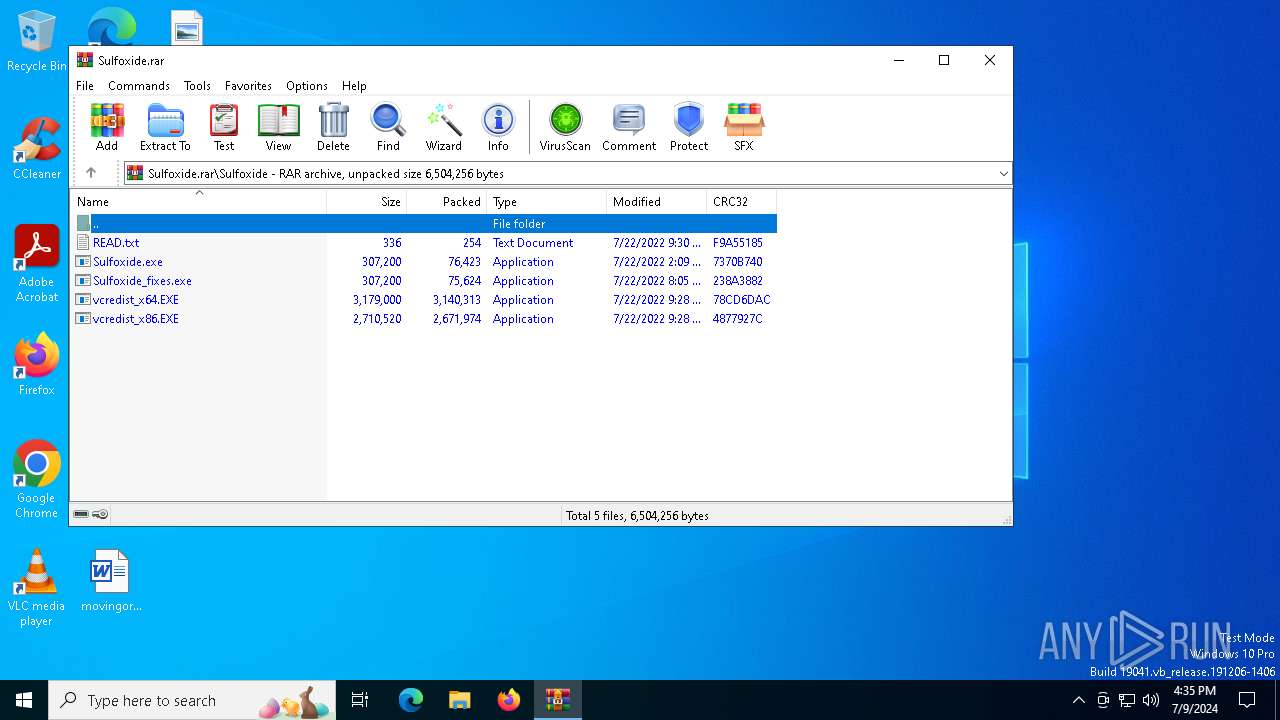
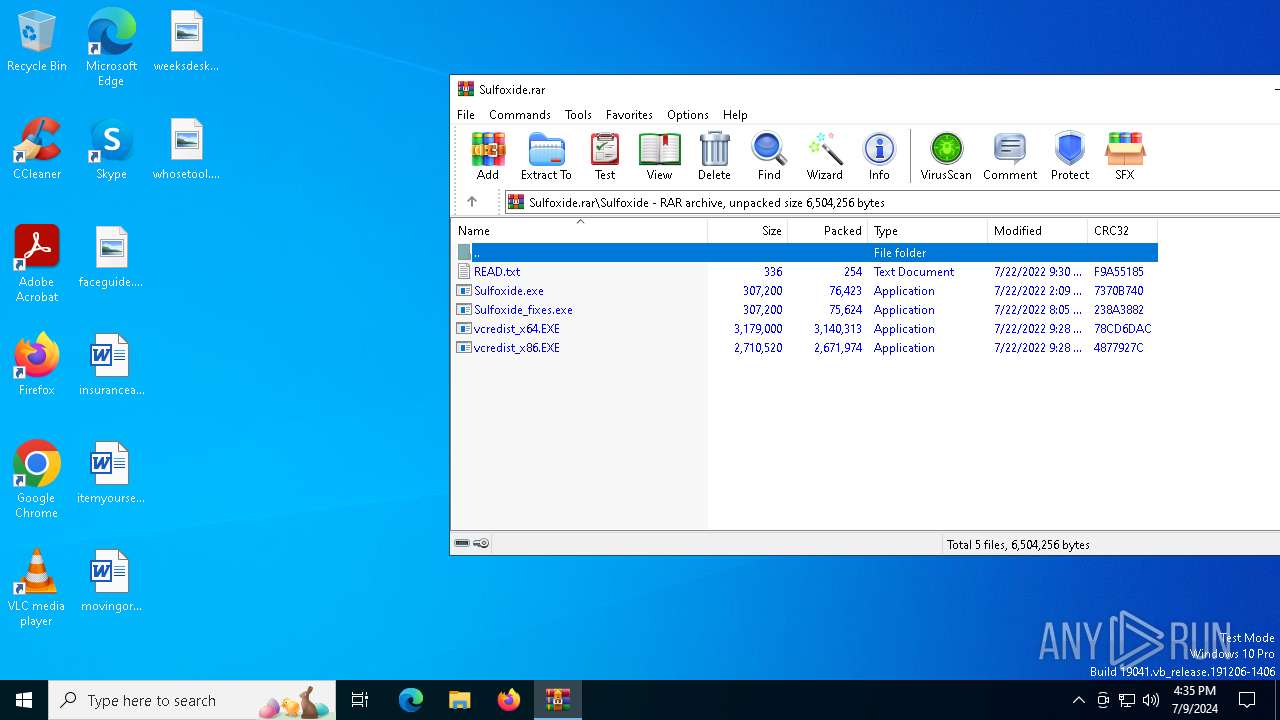
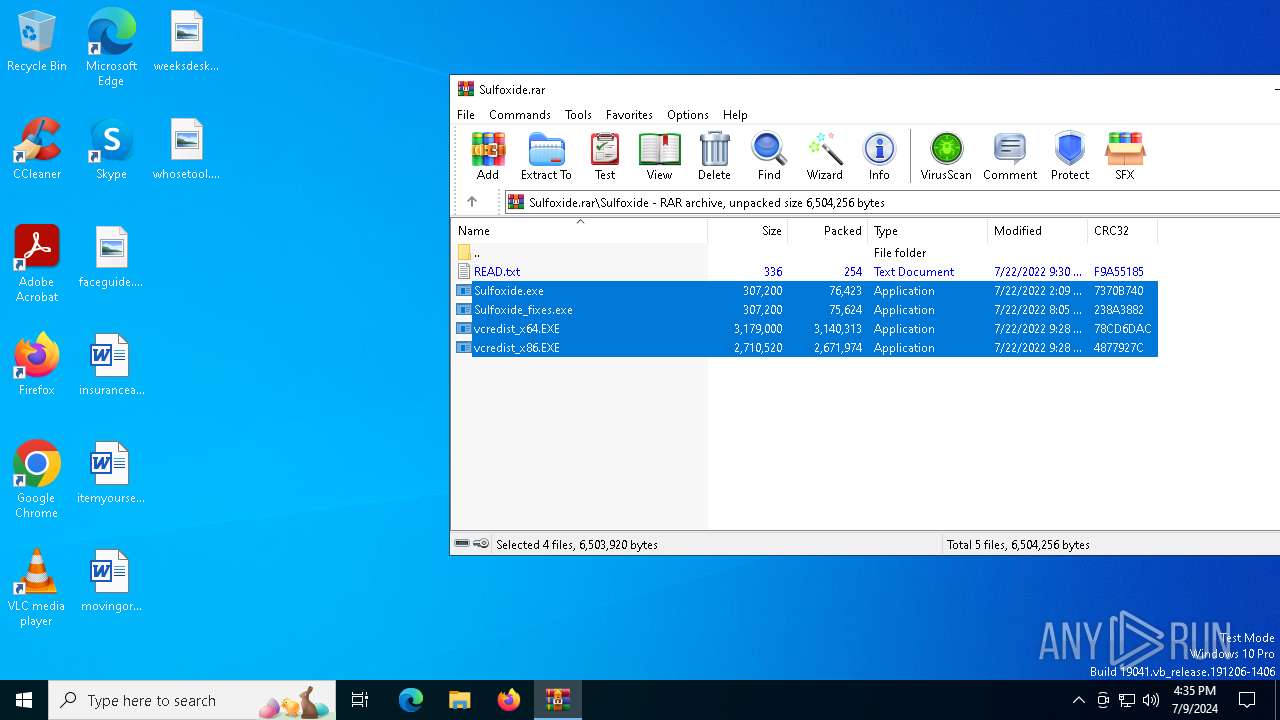
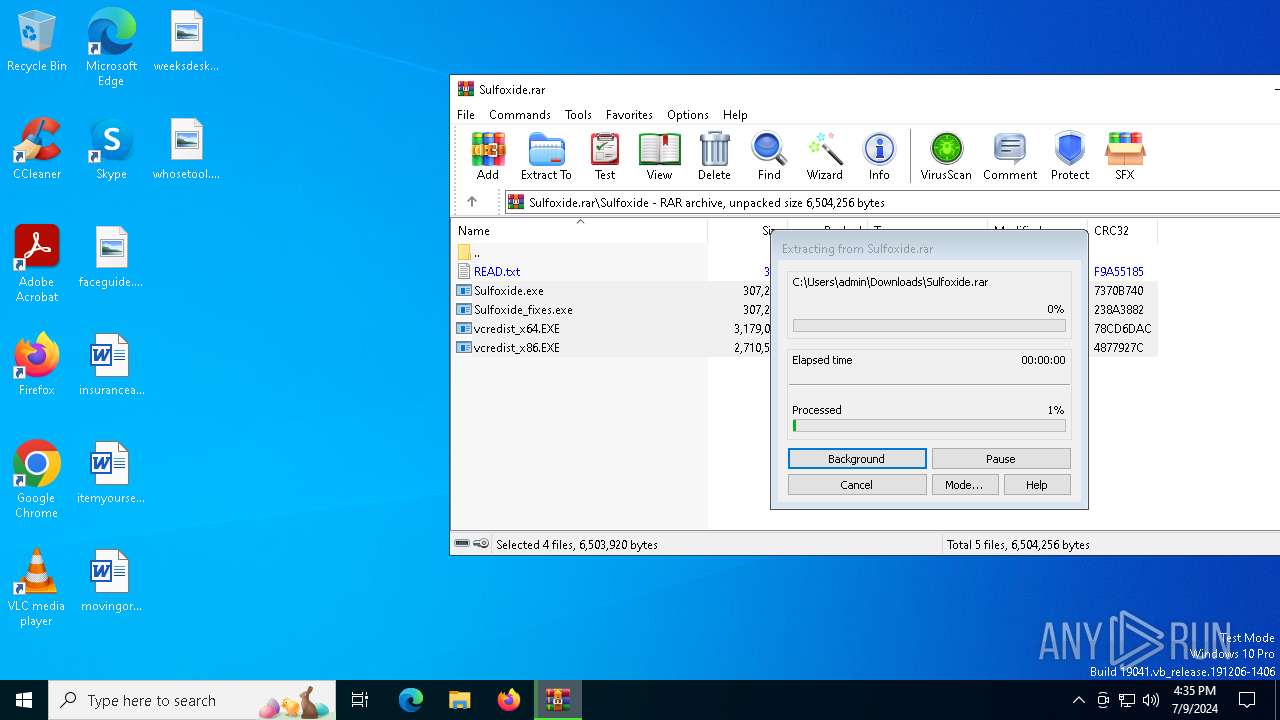
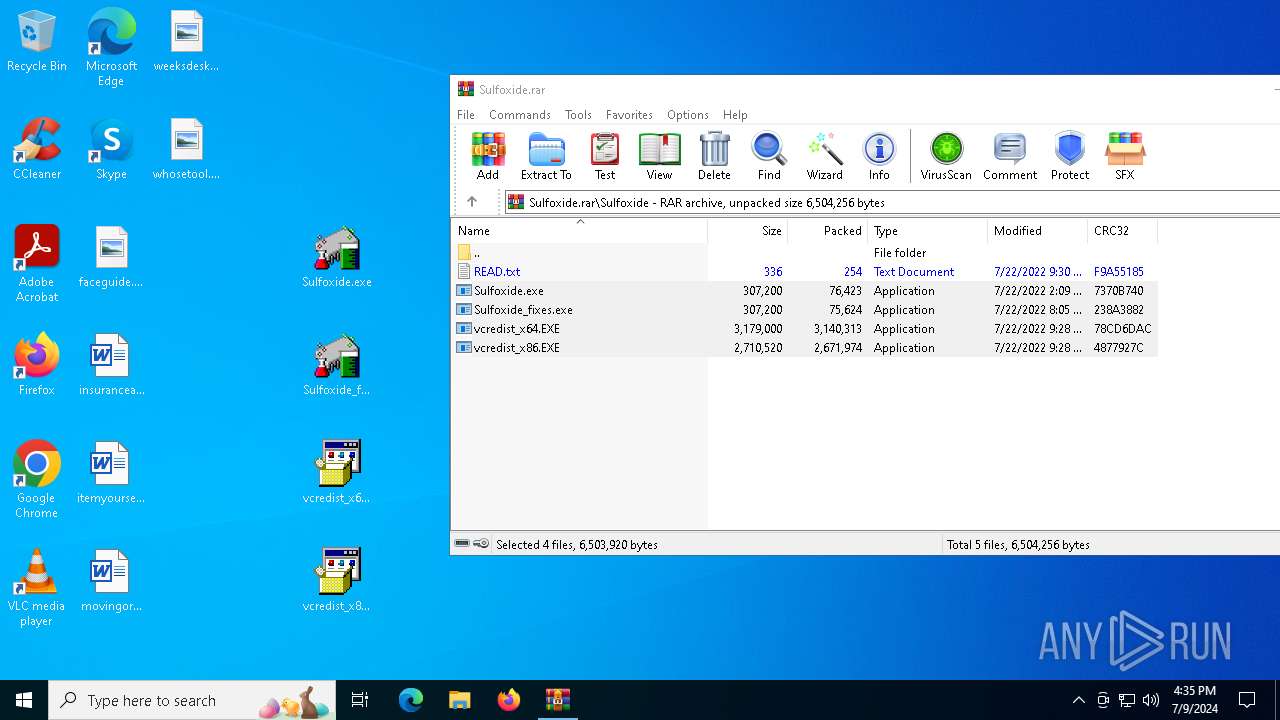
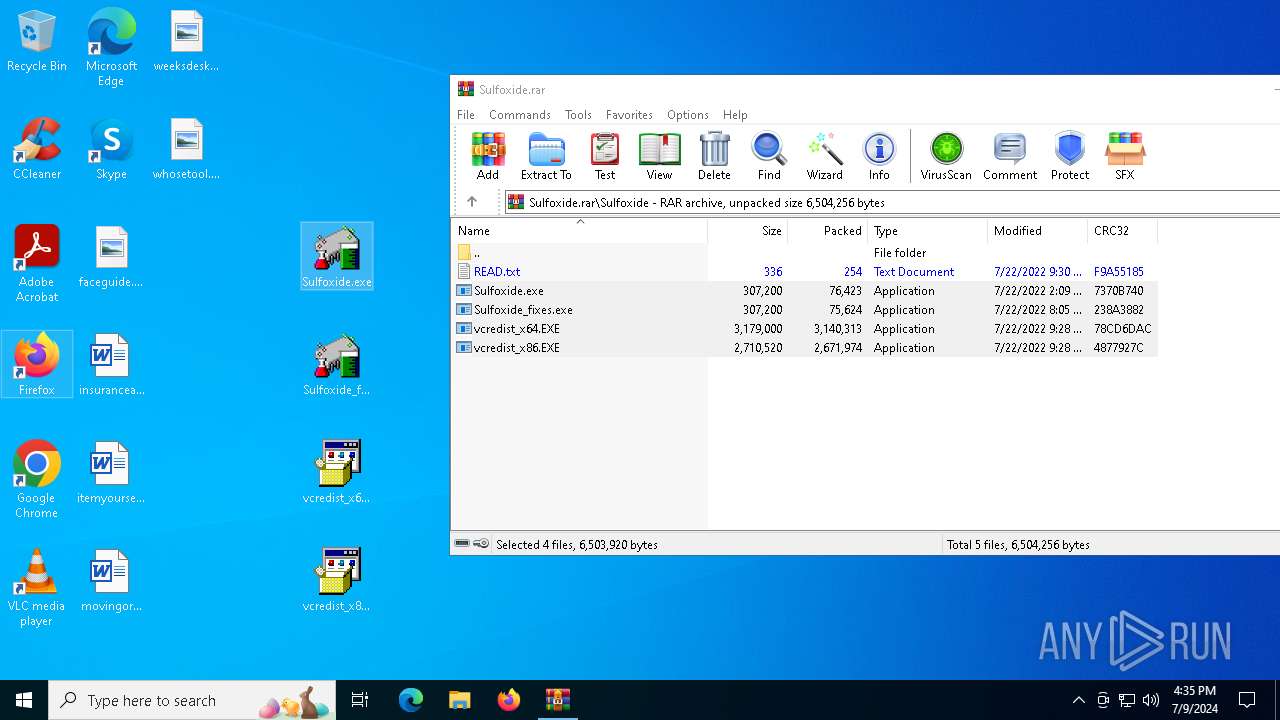
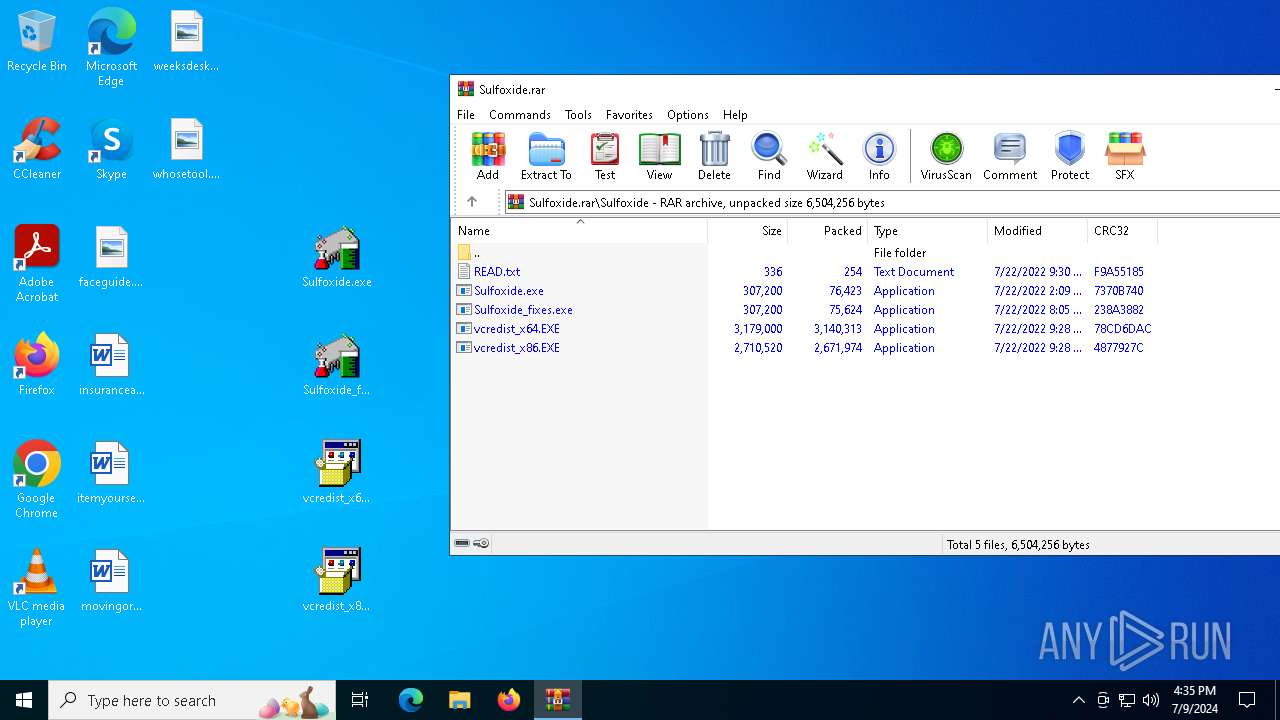
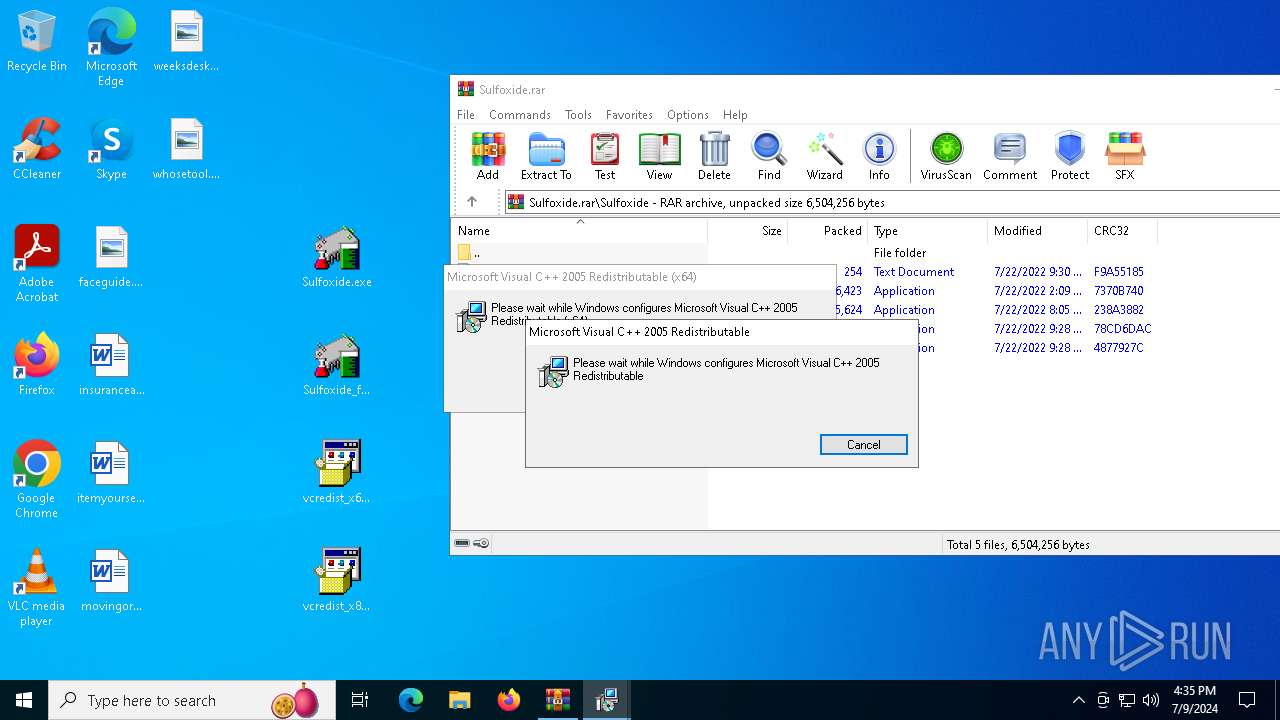
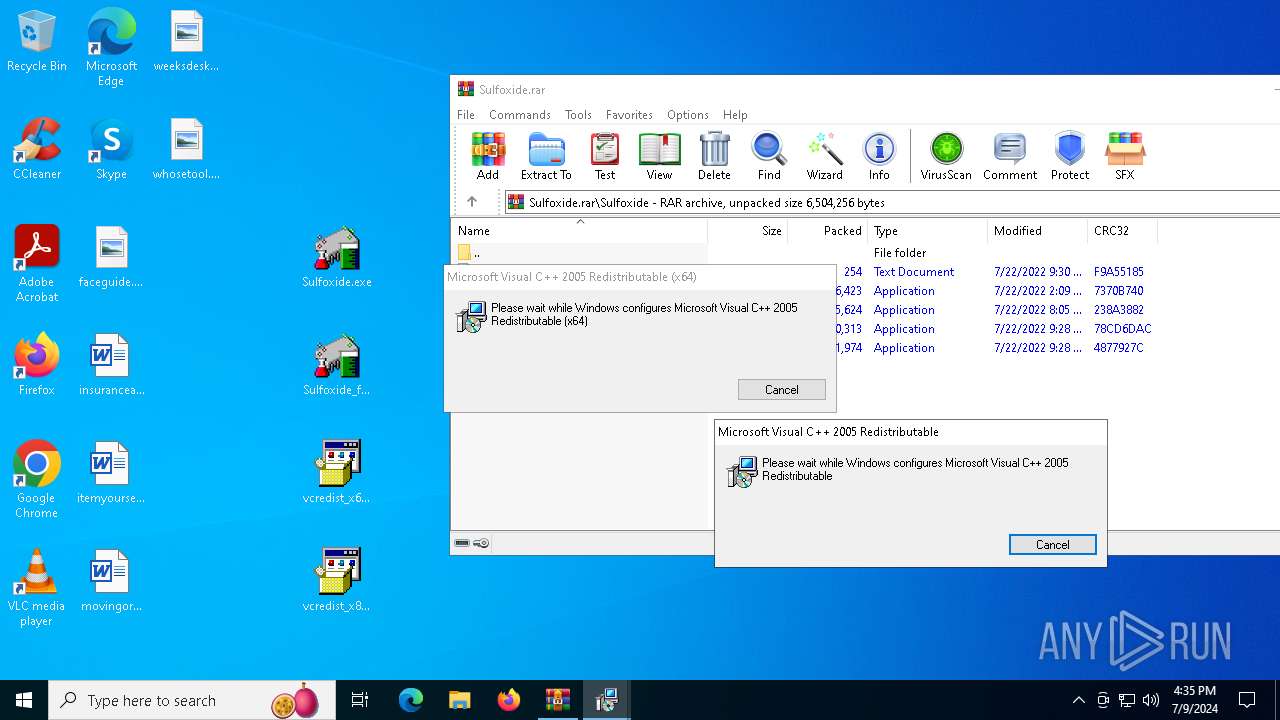
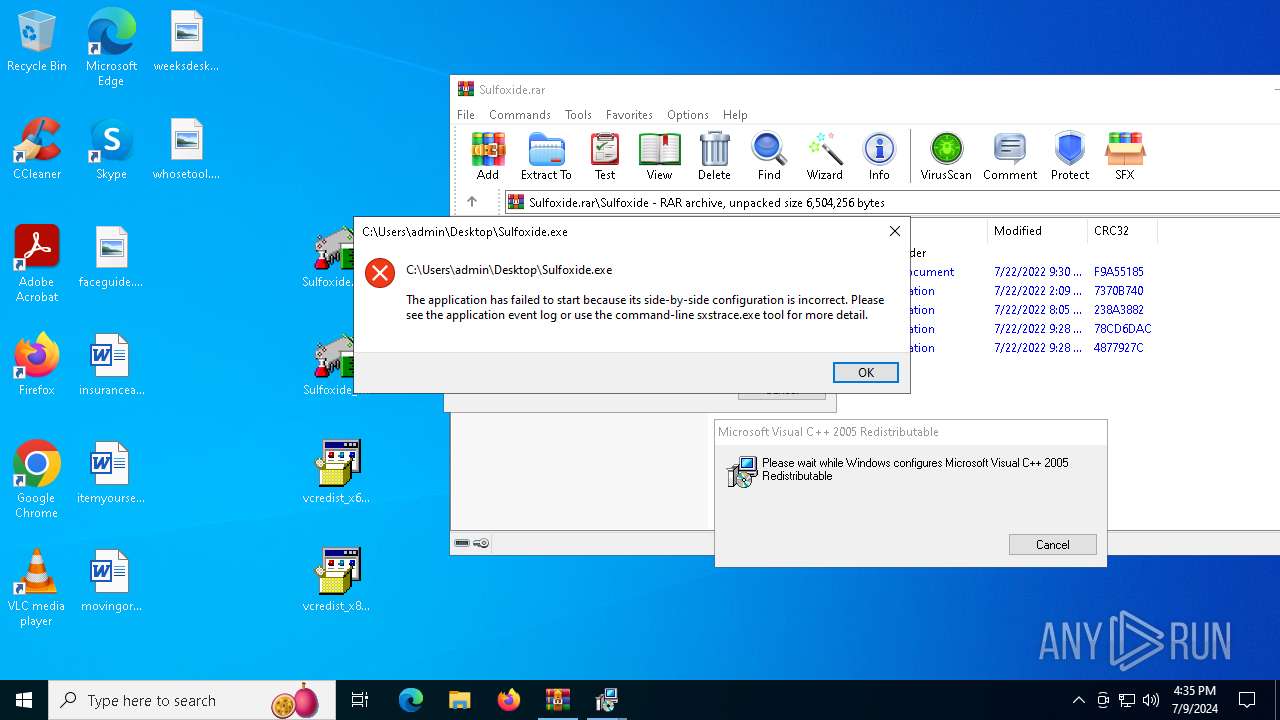
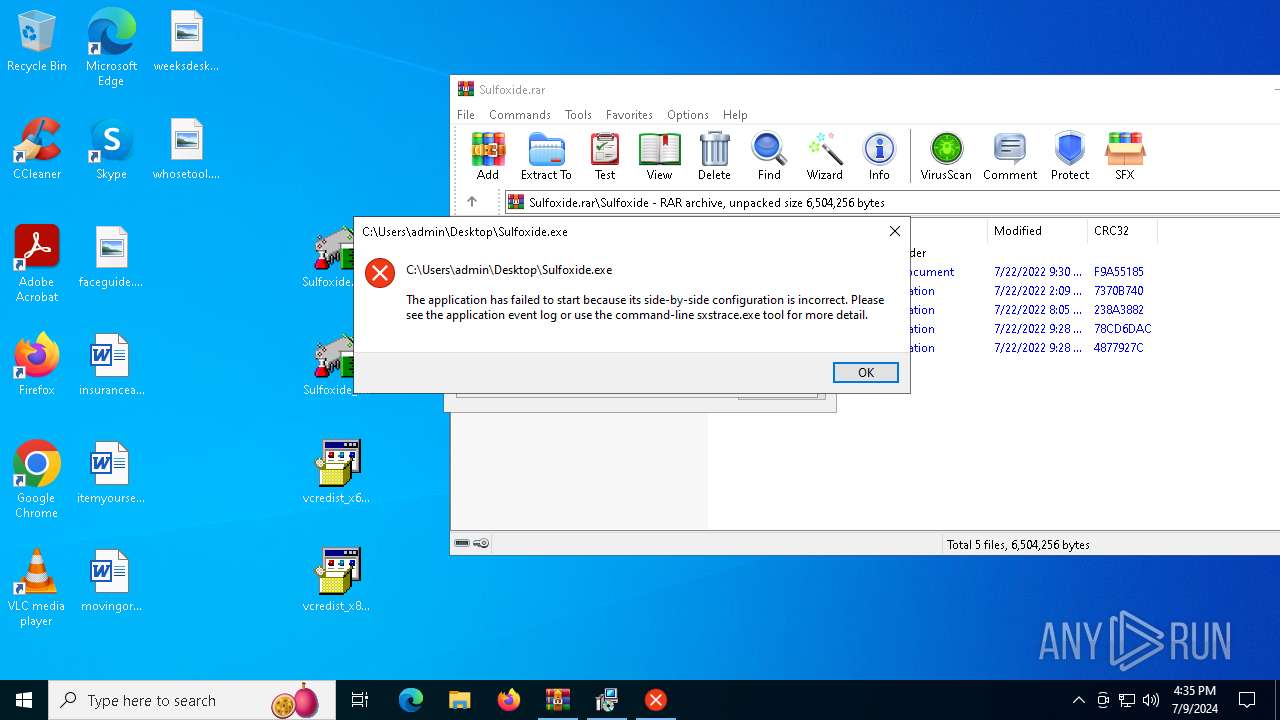
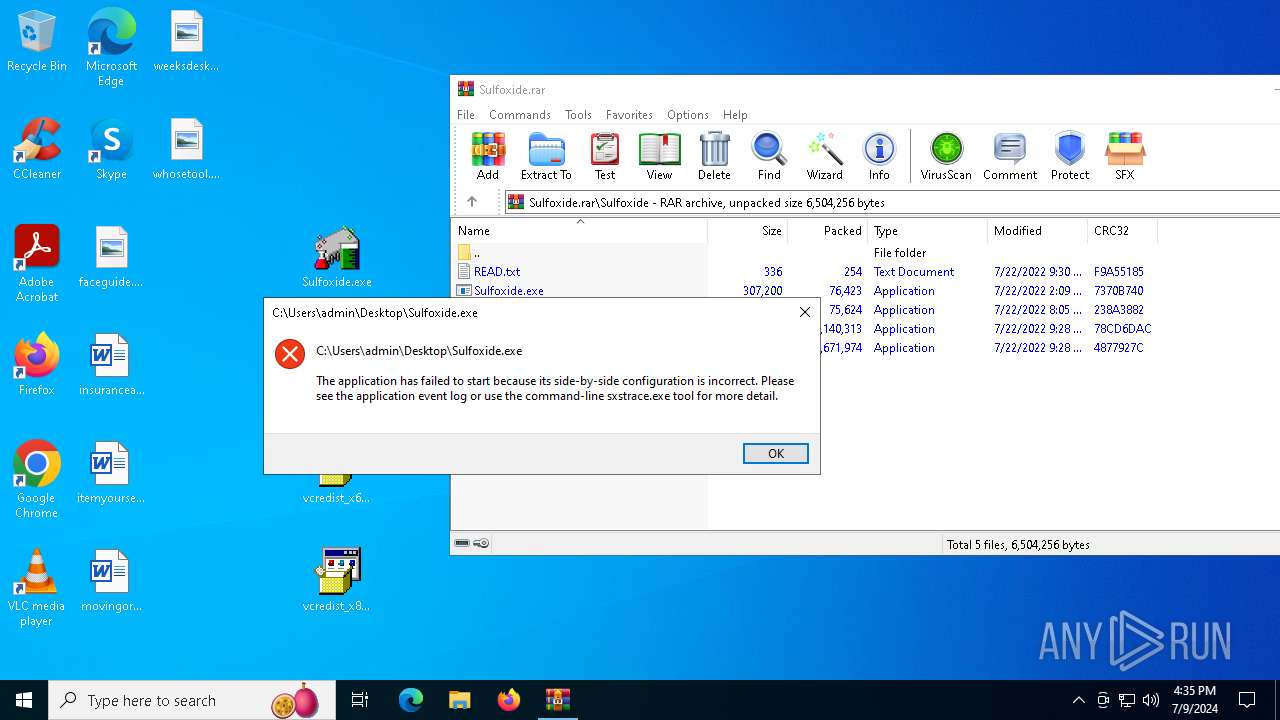
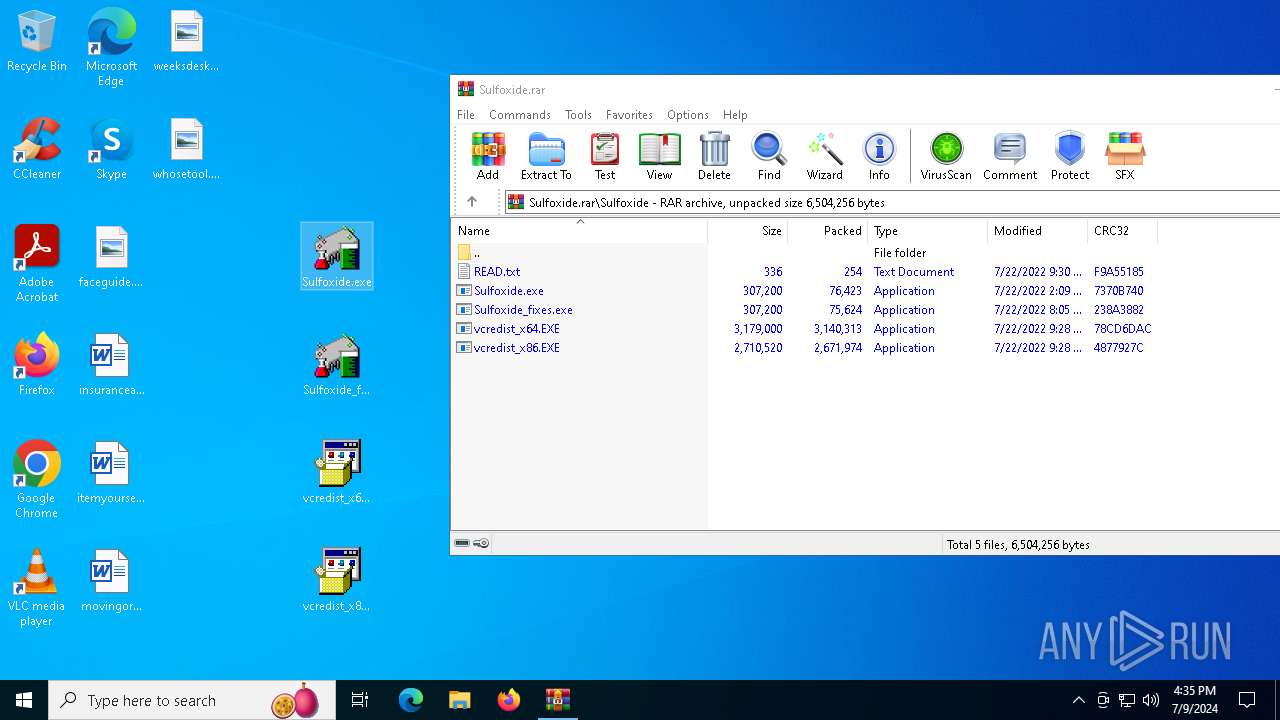
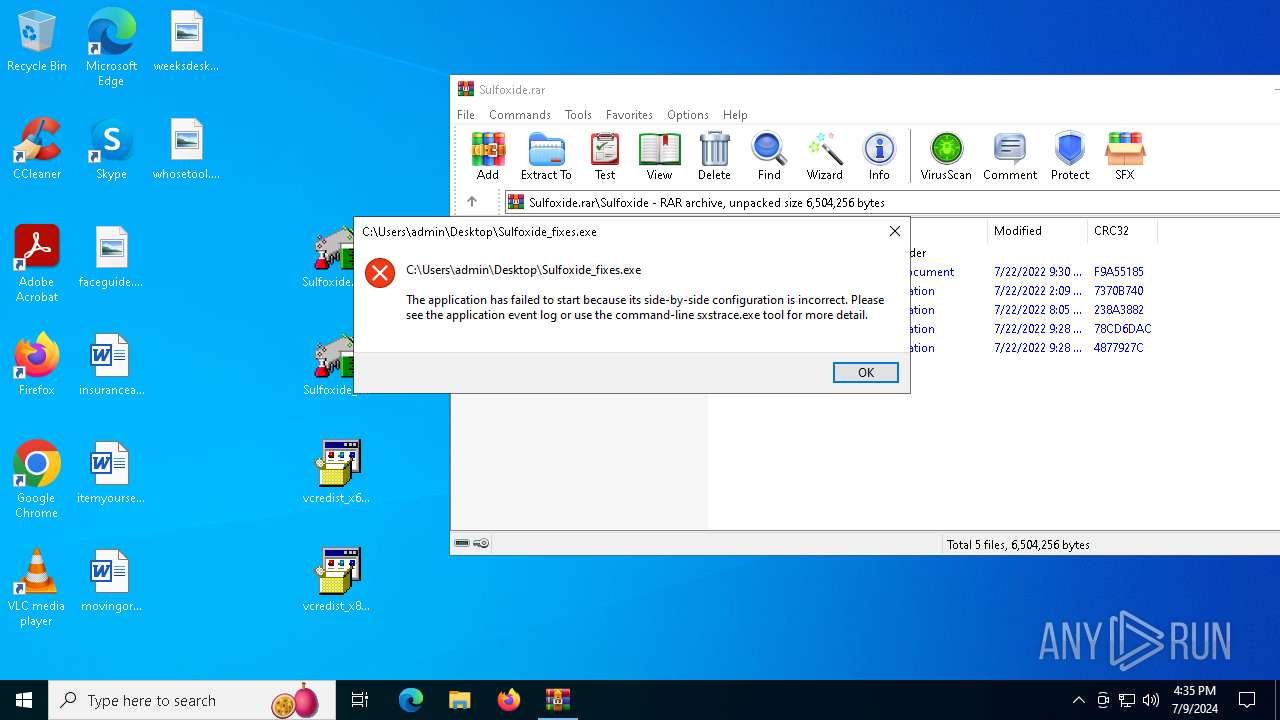
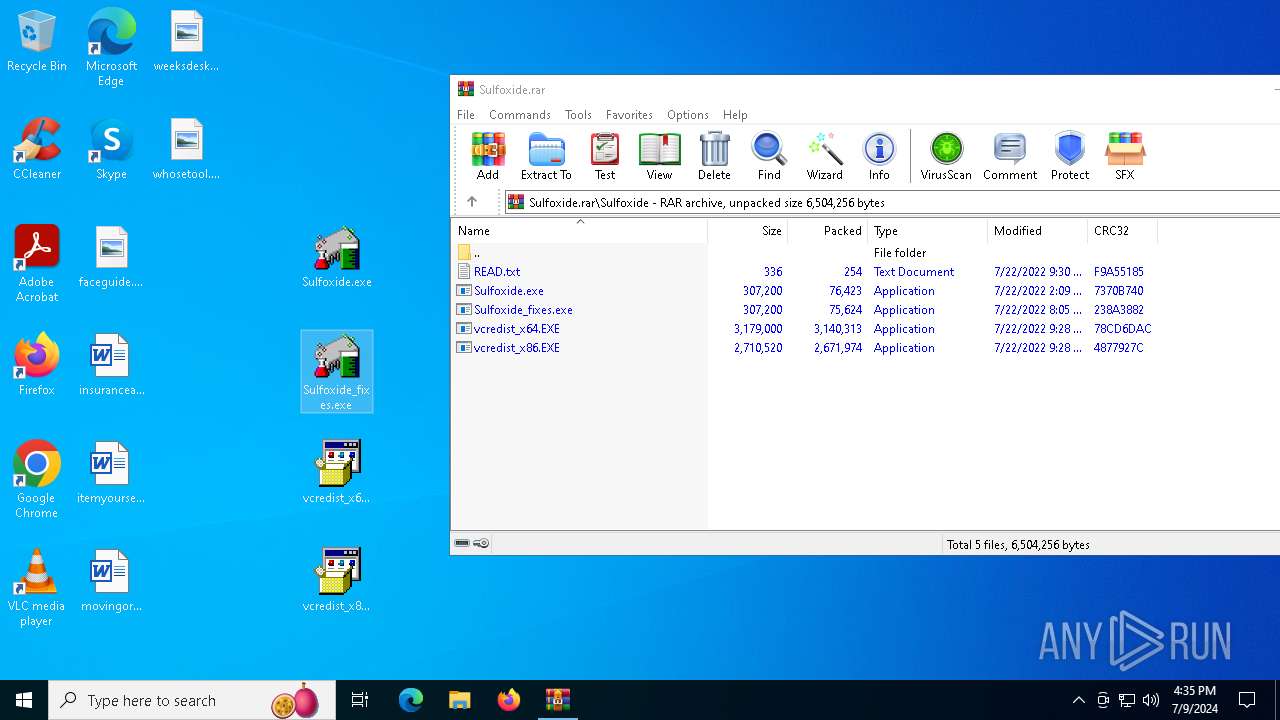
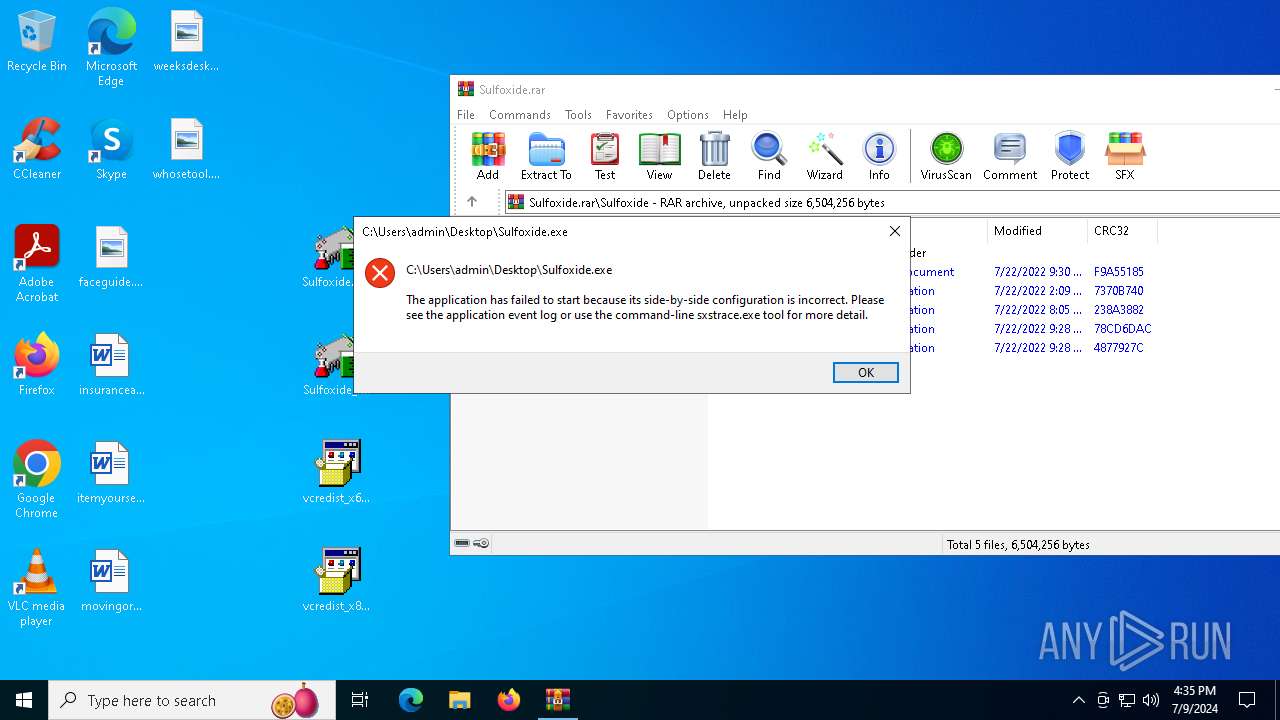
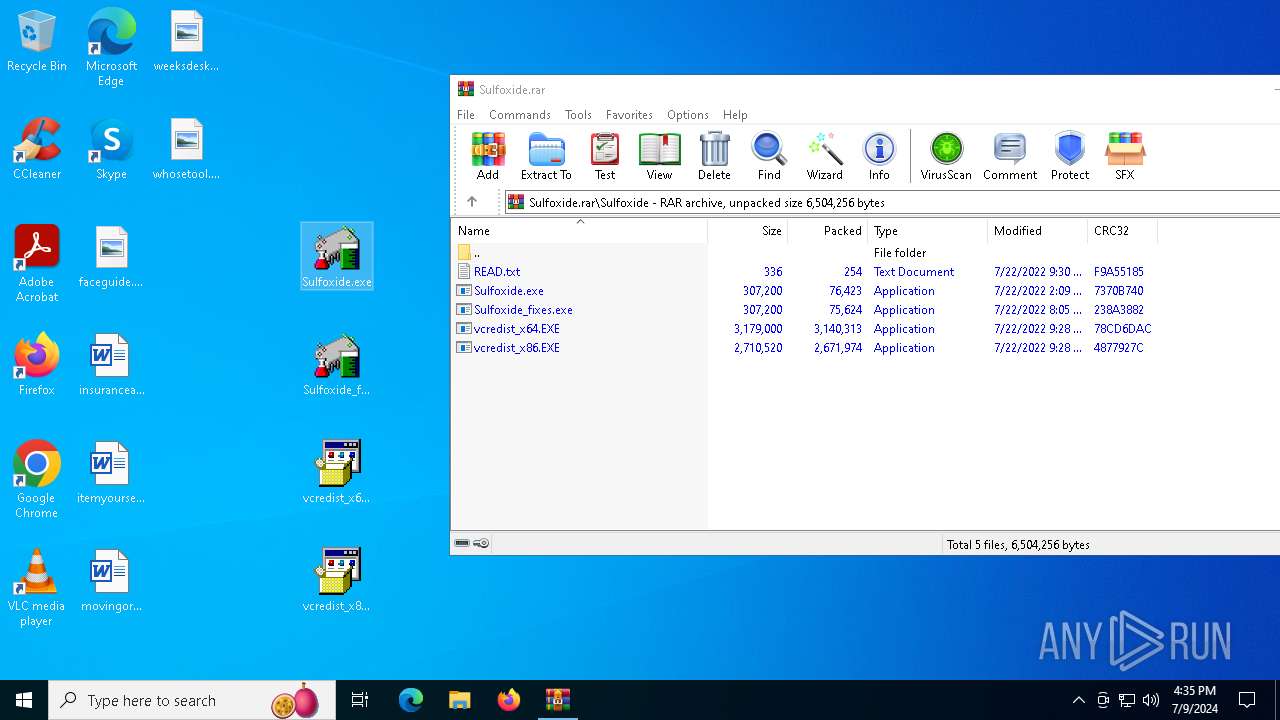
| File name: | Sulfoxide.rar |
| Full analysis: | https://app.any.run/tasks/f1d35129-94c3-4341-a99c-afdbb3b0610b |
| Verdict: | Malicious activity |
| Analysis date: | July 09, 2024, 16:34:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D6ED1A5C6F7B661A1A04D19195533549 |
| SHA1: | F2E8BD5C81DE77A0CF1F0A96AE2B00DC811F1216 |
| SHA256: | FD4C7FF96814A3520C5F53FBF83DC7008C68E78BEAF895ECE1887AF04B4B95DD |
| SSDEEP: | 98304:NH5dIuC6BF88jUXE0GcBU7V8P54nSpZhU1dyF6Fgzw8jdbGUGOurXHg1EviejuEm:82AbyAACj4Qf |
MALICIOUS
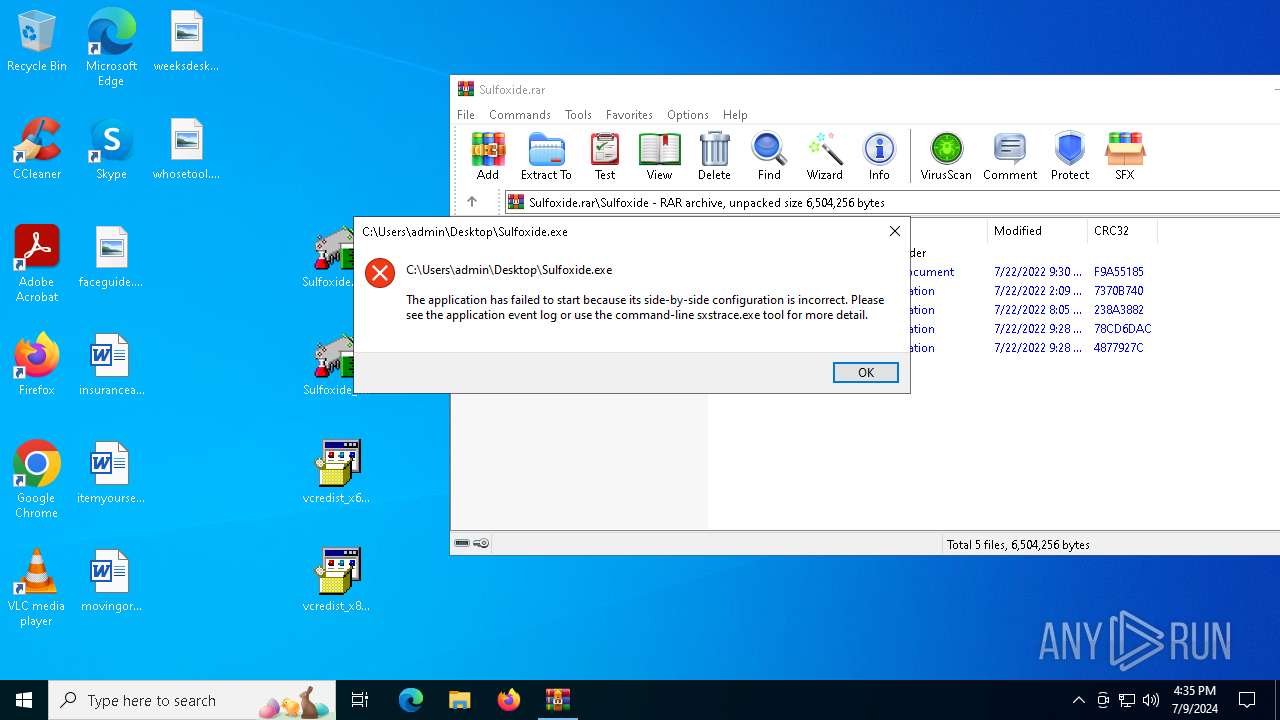
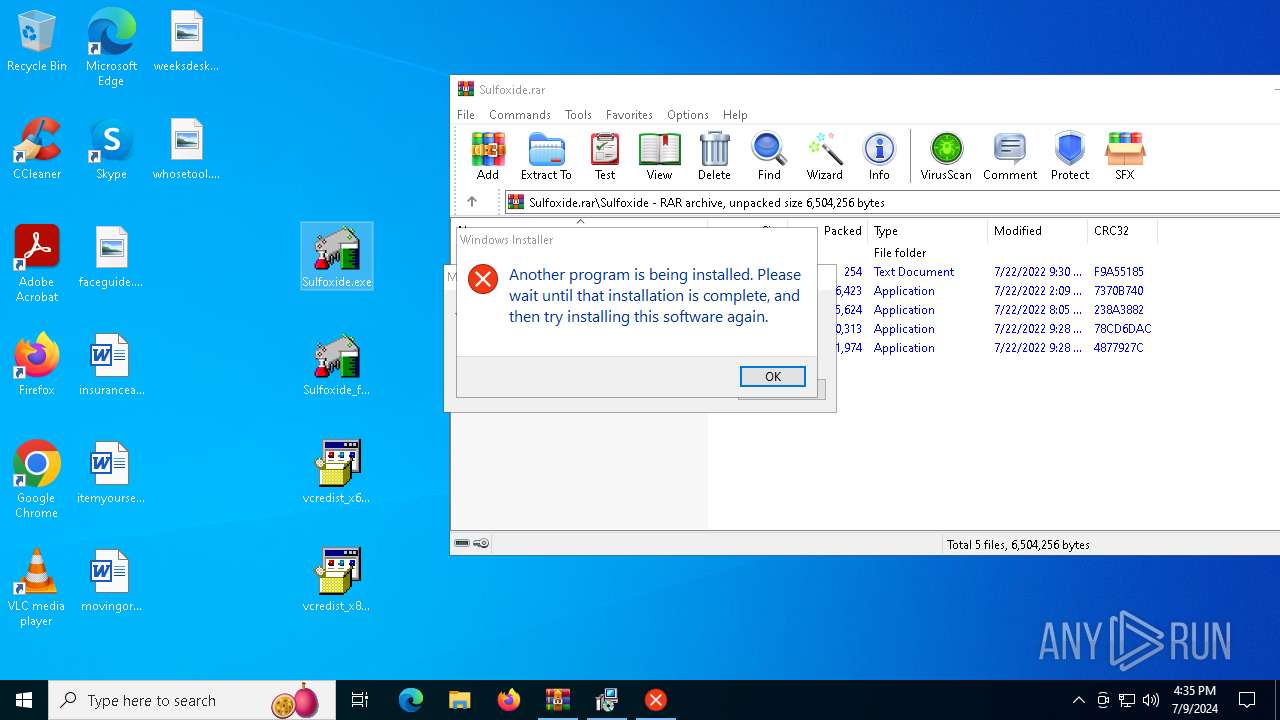
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3628)
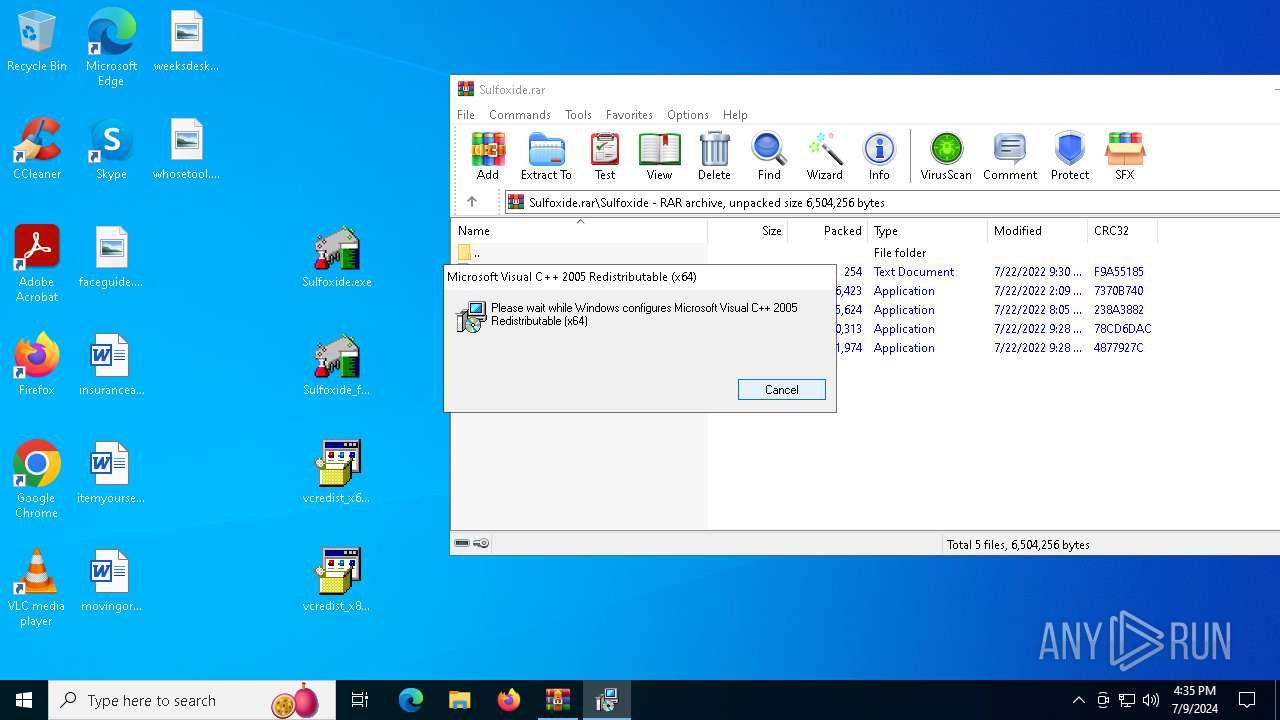
- vcredist_x64.EXE (PID: 6160)
- vcredist_x86.EXE (PID: 6800)
- msiexec.exe (PID: 6744)
- TiWorker.exe (PID: 5912)
Changes the autorun value in the registry
- vcredist_x64.EXE (PID: 6160)
- vcredist_x86.EXE (PID: 6800)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3628)
- TiWorker.exe (PID: 5912)
- msiexec.exe (PID: 6744)
Starts a Microsoft application from unusual location
- vcredist_x64.EXE (PID: 6160)
- vcredist_x86.EXE (PID: 6800)
Executable content was dropped or overwritten
- vcredist_x64.EXE (PID: 6160)
- vcredist_x86.EXE (PID: 6800)
- TiWorker.exe (PID: 5912)
Executes as Windows Service
- VSSVC.exe (PID: 6852)
Checks Windows Trust Settings
- msiexec.exe (PID: 6744)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6744)
The process drops C-runtime libraries
- msiexec.exe (PID: 6744)
- TiWorker.exe (PID: 5912)
INFO
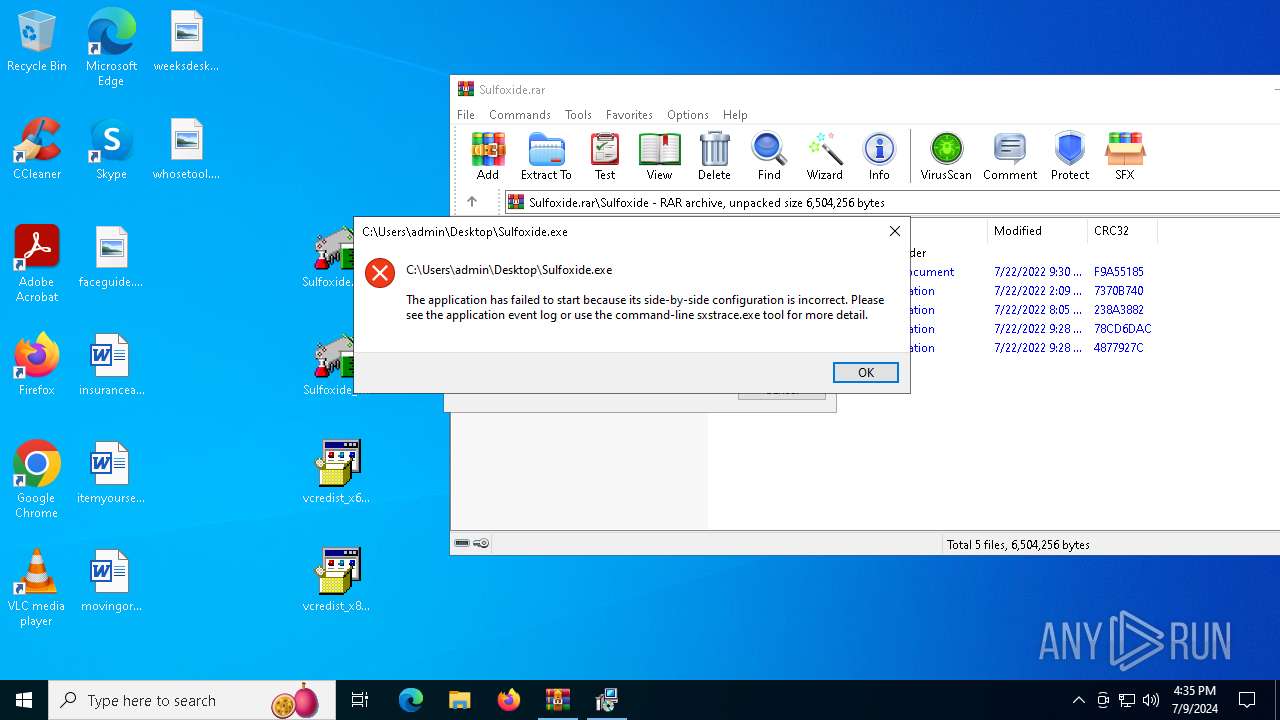
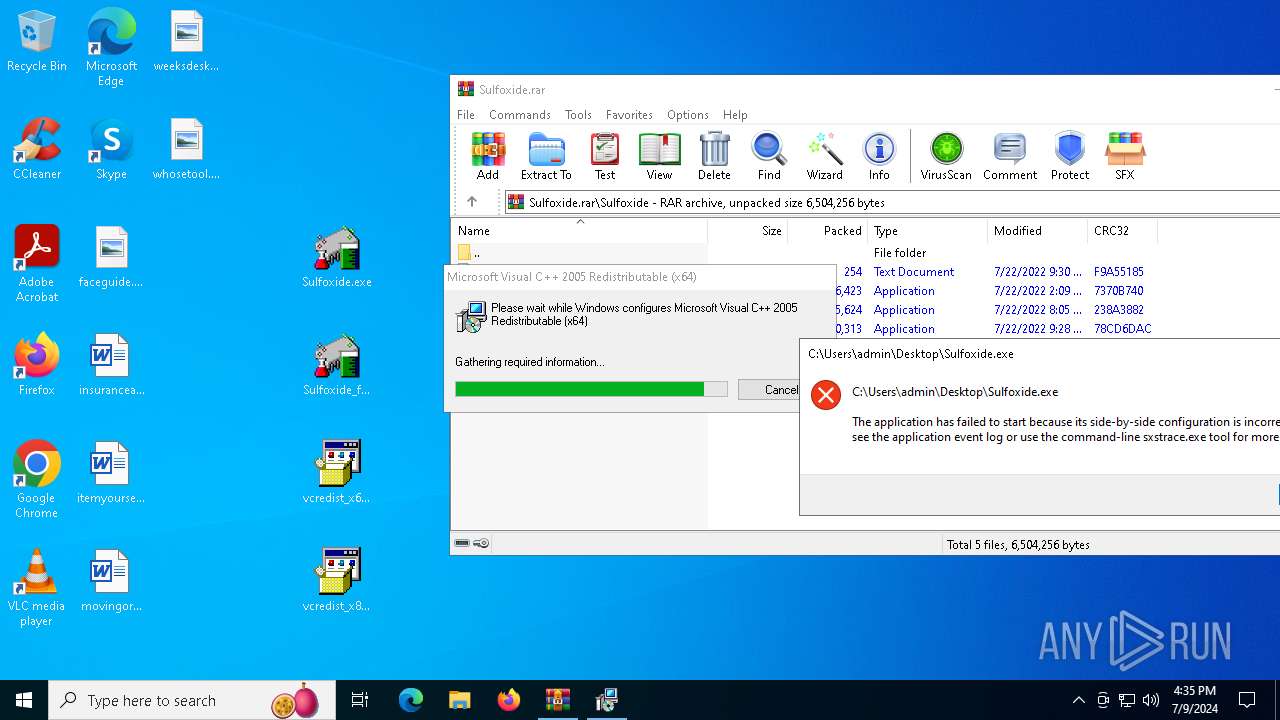
Manual execution by a user
- Sulfoxide.exe (PID: 992)
- vcredist_x64.EXE (PID: 6160)
- vcredist_x86.EXE (PID: 6800)
- Sulfoxide.exe (PID: 6280)
- Sulfoxide.exe (PID: 7152)
- Sulfoxide_fixes.exe (PID: 2808)
- Sulfoxide.exe (PID: 2912)
Reads the computer name
- vcredist_x64.EXE (PID: 6160)
- msiexec.exe (PID: 6744)
- msiexec.exe (PID: 5564)
- vcredist_x86.EXE (PID: 6800)
Checks supported languages
- vcredist_x64.EXE (PID: 6160)
- msiexec.exe (PID: 6744)
- vcredist_x86.EXE (PID: 6800)
- msiexec.exe (PID: 5564)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3628)
- msiexec.exe (PID: 6744)
Create files in a temporary directory
- vcredist_x64.EXE (PID: 6160)
- vcredist_x86.EXE (PID: 6800)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6664)
- msiexec.exe (PID: 7120)
Reads the software policy settings
- msiexec.exe (PID: 6664)
- msiexec.exe (PID: 7120)
- msiexec.exe (PID: 6744)
Checks proxy server information
- msiexec.exe (PID: 6664)
Creates files or folders in the user directory
- msiexec.exe (PID: 6664)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
162
Monitored processes
18
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 652 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 992 | "C:\Users\admin\Desktop\Sulfoxide.exe" | C:\Users\admin\Desktop\Sulfoxide.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3222601730 Modules
| |||||||||||||||
| 2808 | "C:\Users\admin\Desktop\Sulfoxide_fixes.exe" | C:\Users\admin\Desktop\Sulfoxide_fixes.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3222601730 | |||||||||||||||
| 2912 | "C:\Users\admin\Desktop\Sulfoxide.exe" | C:\Users\admin\Desktop\Sulfoxide.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3222601730 | |||||||||||||||
| 3628 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Downloads\Sulfoxide.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5564 | C:\Windows\syswow64\MsiExec.exe -Embedding F1D24BDC0D344A21BAC1B28624B4AE3F | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5912 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) | |||||||||||||||
| 6160 | "C:\Users\admin\Desktop\vcredist_x64.EXE" | C:\Users\admin\Desktop\vcredist_x64.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Version: 6.00.2900.2180 (xpsp_sp2_rtm.040803-2158) Modules
| |||||||||||||||
| 6168 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 6280 | "C:\Users\admin\Desktop\Sulfoxide.exe" | C:\Users\admin\Desktop\Sulfoxide.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3222601730 Modules
| |||||||||||||||
Total events
18 281
Read events
18 090
Write events
180
Delete events
11
Modification events
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Sulfoxide.rar | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3628) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6160) vcredist_x64.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
| (PID) Process: | (6744) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000066FACFFB1DD2DA01581A0000B01A0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
64
Suspicious files
24
Text files
77
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6744 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3628.21310\Sulfoxide\Sulfoxide.exe | executable | |
MD5:EBB8E4550DA773A639557E3BF7D1B29E | SHA256:84C052915829E69E49D0482F1C0EDDE678B3ECE6AC74CA8D1FE3F0DBE1C05EB0 | |||
| 6744 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{a2d08a71-1722-4397-b5e4-aa8ee8b61d01}_OnDiskSnapshotProp | binary | |
MD5:D57D0626A0938898D1F1E107721D417B | SHA256:5A86ED42FC148C72A7BB663626981116F5EAEF1BB83DE7A55158DF98705F7895 | |||
| 6160 | vcredist_x64.EXE | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\vcredis1.cab | compressed | |
MD5:77A9BFF5AF149160775741E204734D47 | SHA256:20A26ED9A1EDF7763A9B515522C5E29720048A482C7FBC8B7FF6BBDD27E61038 | |||
| 6744 | msiexec.exe | C:\WINDOWS\Installer\1d7060.msi | executable | |
MD5:6DBDF338A0A25CDB236D43EA3CA2395E | SHA256:200FEF5D4994523A02C4DAA00060DB28EB289B99D47FC6C1305183101E72BDEB | |||
| 6744 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:D57D0626A0938898D1F1E107721D417B | SHA256:5A86ED42FC148C72A7BB663626981116F5EAEF1BB83DE7A55158DF98705F7895 | |||
| 6664 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7B2238AACCEDC3F1FFE8E7EB5F575EC9 | binary | |
MD5:A26DCBB948DA05EC8AF97885DBD149B0 | SHA256:3CEB4A8069B2B9E5FDF508EF67D5AF5B9D3E6A7B417919953A89FA9773E16440 | |||
| 3628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3628.21310\Sulfoxide\Sulfoxide_fixes.exe | executable | |
MD5:1C93ABA8D33DE352B56173F2DBF218B8 | SHA256:39DA041A23FDAB1324E58DDF546D05E211D0C2B568813A95A76550499CA36CA9 | |||
| 6800 | vcredist_x86.EXE | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\vcredis1.cab | compressed | |
MD5:CC064D4B81619991DE8131A86AD77681 | SHA256:913EE5A1CAE3E5A1872B3A5EFAAA00C58E4BEB692492B138F76967DA671B0477 | |||
| 3628 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3628.21310\Sulfoxide\vcredist_x64.EXE | executable | |
MD5:E231FBCCE2C2CB16DCC299D36C734DF3 | SHA256:4487570BD86E2E1AAC29DB2A1D0A91EB63361FCAAC570808EB327CD4E0E2240D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
73
DNS requests
26
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4452 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4452 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3540 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
6664 | msiexec.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/CSPCA.crl | unknown | — | — | unknown |
3516 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3516 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
4052 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4452 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1280 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1968 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4452 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
4452 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4656 | SearchApp.exe | 104.126.37.123:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
arc-ring.msedge.net |
| unknown |
fp-afd.azurefd.net |
| unknown |
l-ring.msedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4656 | SearchApp.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |