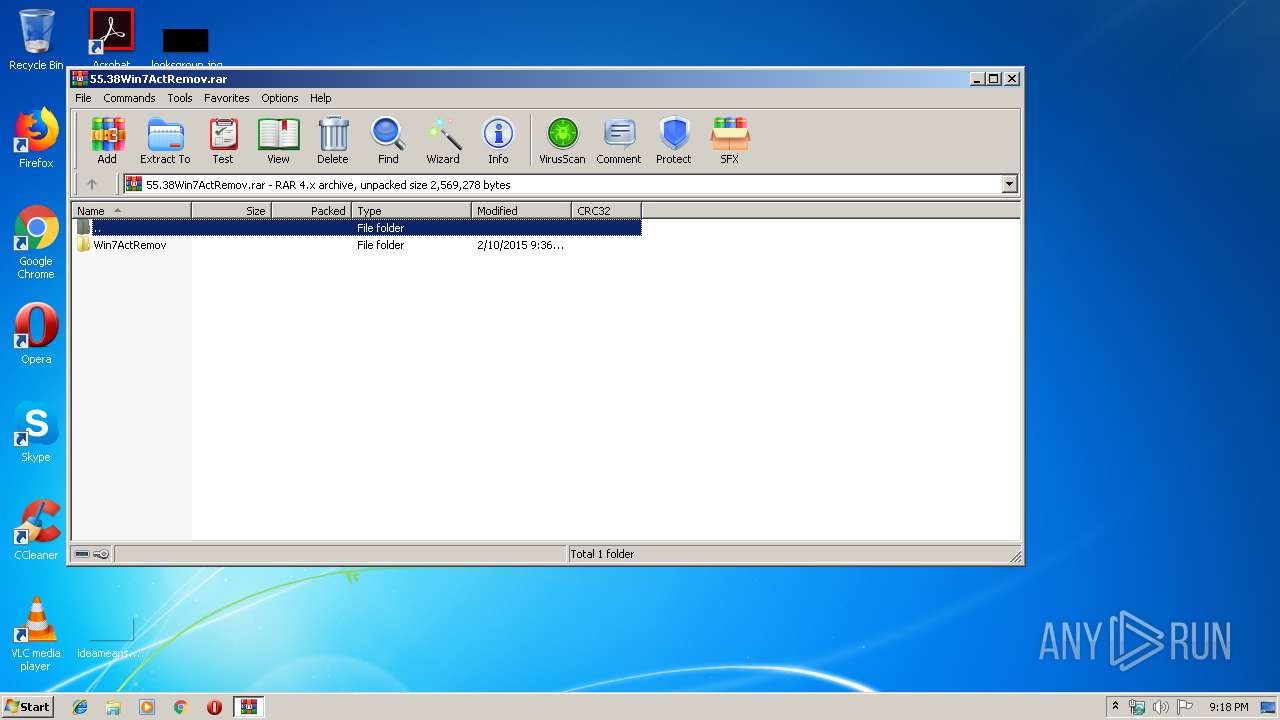
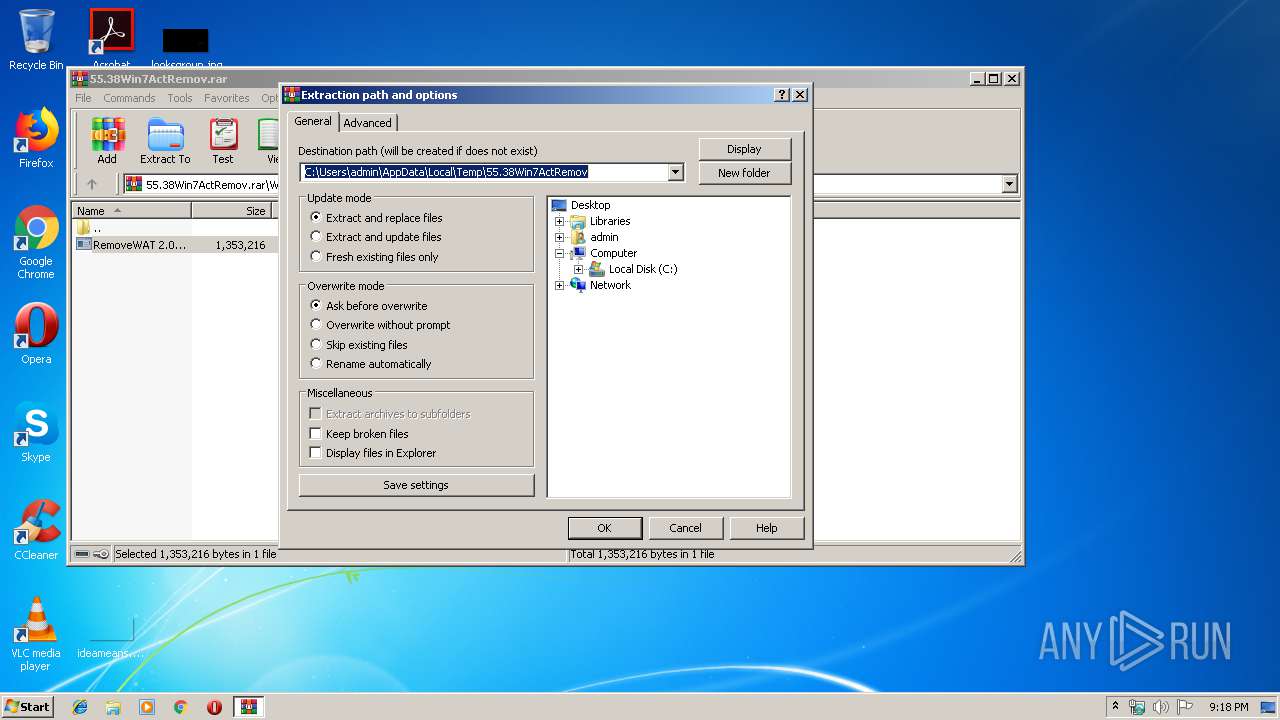
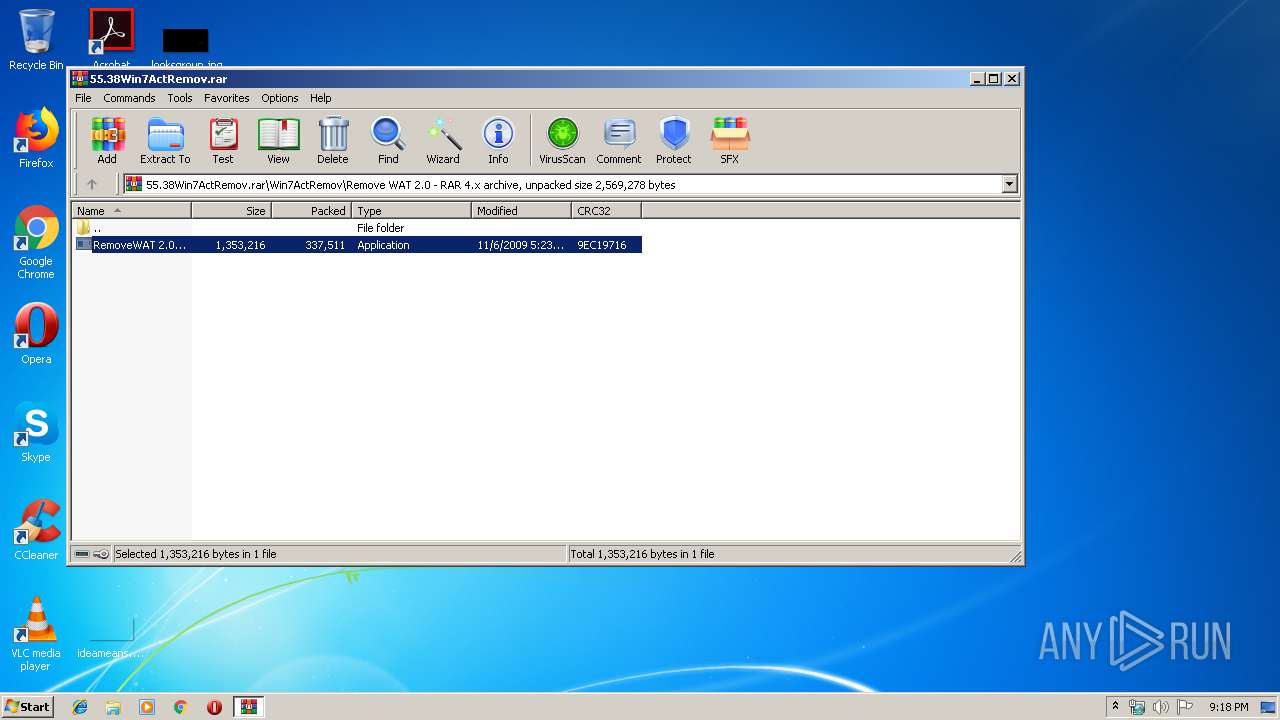
| File name: | 55.38Win7ActRemov.rar |
| Full analysis: | https://app.any.run/tasks/e1b66a15-bfb5-4521-bd91-c77752913c5c |
| Verdict: | Malicious activity |
| Analysis date: | May 06, 2019, 20:17:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 4588A8B6D096C84217C785248AAC11FE |
| SHA1: | B68902AA20B0F0D29D06E031D14428C2957CE786 |
| SHA256: | FD478DF8DF078670D29B8E1C109A44CD90941D09A8978F087A87FFF0B382DBAC |
| SSDEEP: | 24576:eI/1cMTIkmdDiSTs3BEy/ghjVFj2oalLSHs8tmBeqP9aOood5n6Pk1ja:rBjmBxvElLSM8tseqvzJ1ja |
MALICIOUS
Application was dropped or rewritten from another process
- RemoveWAT 2.0.exe (PID: 2484)
- watermark.exe (PID: 2452)
- userw.exe (PID: 2920)
Loads the Task Scheduler COM API
- explorer.exe (PID: 2304)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2972)
- RemoveWAT 2.0.exe (PID: 2484)
- watermark.exe (PID: 2452)
- userw.exe (PID: 2920)
- cmd.exe (PID: 1856)
- cmd.exe (PID: 3100)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 1856)
- cmd.exe (PID: 3100)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1856)
Starts CMD.EXE for commands execution
- RemoveWAT 2.0.exe (PID: 2484)
- watermark.exe (PID: 2452)
- cmd.exe (PID: 3100)
Creates files in the Windows directory
- RemoveWAT 2.0.exe (PID: 2484)
- cmd.exe (PID: 3100)
Removes files from Windows directory
- cmd.exe (PID: 1856)
- mcbuilder.exe (PID: 4000)
Starts SC.EXE for service management
- cmd.exe (PID: 1856)
Application launched itself
- cmd.exe (PID: 3100)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 1180923 |
|---|---|
| UncompressedSize: | 1216062 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2009:11:17 13:25:27 |
| PackingMethod: | Normal |
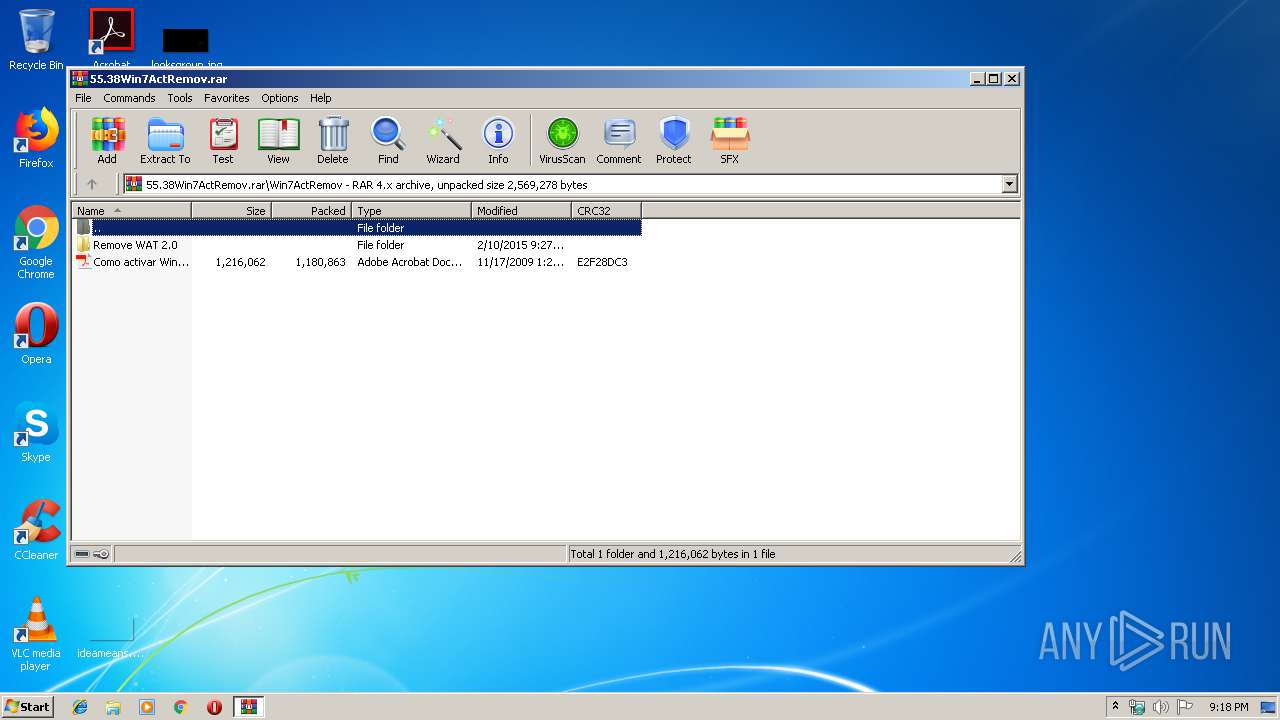
| ArchivedFileName: | Win7ActRemov\Como activar Windows 7.pdf |
Total processes
70
Monitored processes
32
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1856 | "C:\Windows\System32\cmd.exe" /c TASKKILL /F /IM wlms.exe & takeown /F %windir%\System32\wlms\wlms.exe & icacls %windir%\System32\wlms\wlms.exe /deny *S-1-1-0:RX & %windir%\watermark.exe & mcbuilder.exe & del %windir%\watermark.exe & sc config sppsvc start= Demand & takeown /F %windir%\System32\sppcomapi.dll & icacls %windir%\System32\sppcomapi.dll /deny *S-1-1-0:RX & takeown /F %windir%\System32\sppuinotify.dll & icacls %windir%\System32\sppuinotify.dll /deny *S-1-5-19:RX & takeown /F %windir%\System32\SLUI.exe & icacls %windir%\System32\SLUI.exe /deny *S-1-5-18:RX & icacls %windir%\System32\SLUI.exe /deny *S-1-5-20:F & takeown /F %windir%\SYSWOW64\slmgr.vbs & icacls %windir%\SYSWOW64\slmgr.vbs /grant *S-1-5-32-544:F & ren %windir%\SYSWOW64\slmgr.vbs slmgr.vbs.disabled & takeown /F %windir%\System32\slmgr.vbs & icacls %windir%\System32\slmgr.vbs /grant *S-1-5-32-544:F & ren %windir%\System32\slmgr.vbs slmgr.vbs.disabled & TASKKILL /F /IM explorer.exe & takeown /F %windir%\System32\systemcpl.dll & icacls %windir%\System32\systemcpl.dll /grant *S-1-5-32-544:F & ren %windir%\System32\systemcpl.dll systemcpl.dll.bak & IF EXIST %windir%\SYSWOW64 (takeown /F %windir%\System32\slwga.dll & icacls %windir%\System32\slwga.dll /grant *S-1-5-32-544:F & takeown /F %windir%\SysWOW64\slwga.dll & icacls %windir%\SysWOW64\slwga.dll /grant *S-1-5-32-544:F & ren %windir%\System32\slwga.dll slwga.dll.bak & ren %windir%\SysWOW64\slwga.dll slwga.dll.bak & move %windir%\slwga32.dll %windir%\SysWOW64\slwga.dll & move %windir%\64slwga.dll %windir%\System32\slwga.dll & ren %windir%\System32\systemcplx64.dll systemcpl.dll & DEL %windir%\System32\systemcplx86.dll & start explorer.exe) ELSE (takeown /F %windir%\System32\slwga.dll & icacls %windir%\System32\slwga.dll /grant *S-1-5-32-544:F & ren %windir%\System32\slwga.dll slwga.dll.bak & move %windir%\32slwga.dll %windir%\System32\slwga.dll & del %windir%\64slwga.dll & ren %windir%\System32\systemcplx86.dll systemcpl.dll & DEL %windir%\System32\systemcplx64.dll & start explorer.exe) | C:\Windows\System32\cmd.exe | RemoveWAT 2.0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1924 | takeown /F C:\Windows\System32\sppuinotify.dll | C:\Windows\system32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2160 | icacls C:\Windows\System32\wlms\wlms.exe /deny *S-1-1-0:RX | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2244 | sc config sppsvc start= Demand | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2304 | explorer.exe | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | icacls C:\Windows\System32\systemcpl.dll /grant *S-1-5-32-544:F | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2452 | C:\Windows\watermark.exe | C:\Windows\watermark.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
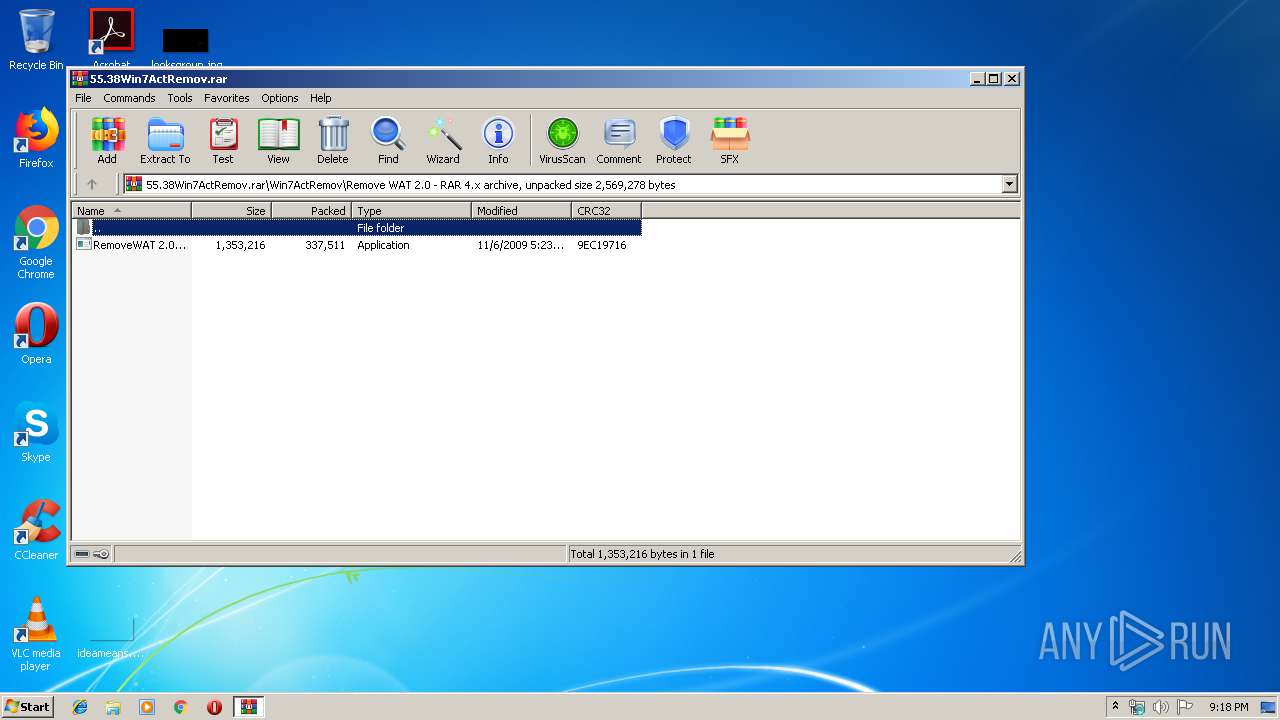
| 2484 | "C:\Users\admin\Desktop\RemoveWAT 2.0.exe" | C:\Users\admin\Desktop\RemoveWAT 2.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: RemoveWAT Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 2620 | ICACLS "C:\Windows\System32\en-US\user32.dll.mui" /GRANT "admin":F | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2760 | icacls C:\Windows\System32\sppuinotify.dll /deny *S-1-5-19:RX | C:\Windows\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 023
Read events
1 907
Write events
114
Delete events
2
Modification events
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\55.38Win7ActRemov.rar | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (2484) RemoveWAT 2.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
15
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2920 | userw.exe | C:\Users\admin\AppData\Local\Temp\7080.tmp\user32.dll1.mui | — | |
MD5:— | SHA256:— | |||
| 4000 | mcbuilder.exe | C:\Windows\rescache\wip\ResCache.hit | — | |
MD5:— | SHA256:— | |||
| 4000 | mcbuilder.exe | C:\Windows\rescache\wip\Segment0.cmf | — | |
MD5:— | SHA256:— | |||
| 4000 | mcbuilder.exe | C:\Windows\rescache\wip\Segment0.toc | — | |
MD5:— | SHA256:— | |||
| 4000 | mcbuilder.exe | C:\Windows\rescache\wip\Segment1.cmf | — | |
MD5:— | SHA256:— | |||
| 4000 | mcbuilder.exe | C:\Windows\rescache\wip\Segment1.toc | — | |
MD5:— | SHA256:— | |||
| 4000 | mcbuilder.exe | C:\Windows\rescache\wip\ResCache.dir | — | |
MD5:— | SHA256:— | |||
| 4000 | mcbuilder.exe | C:\Windows\rescache\rc0003 | — | |
MD5:— | SHA256:— | |||
| 2484 | RemoveWAT 2.0.exe | C:\Windows\System32\systemcplx86.dll | executable | |
MD5:— | SHA256:— | |||
| 3100 | cmd.exe | C:\Windows\System32\en-US\user32.dll.mui | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report