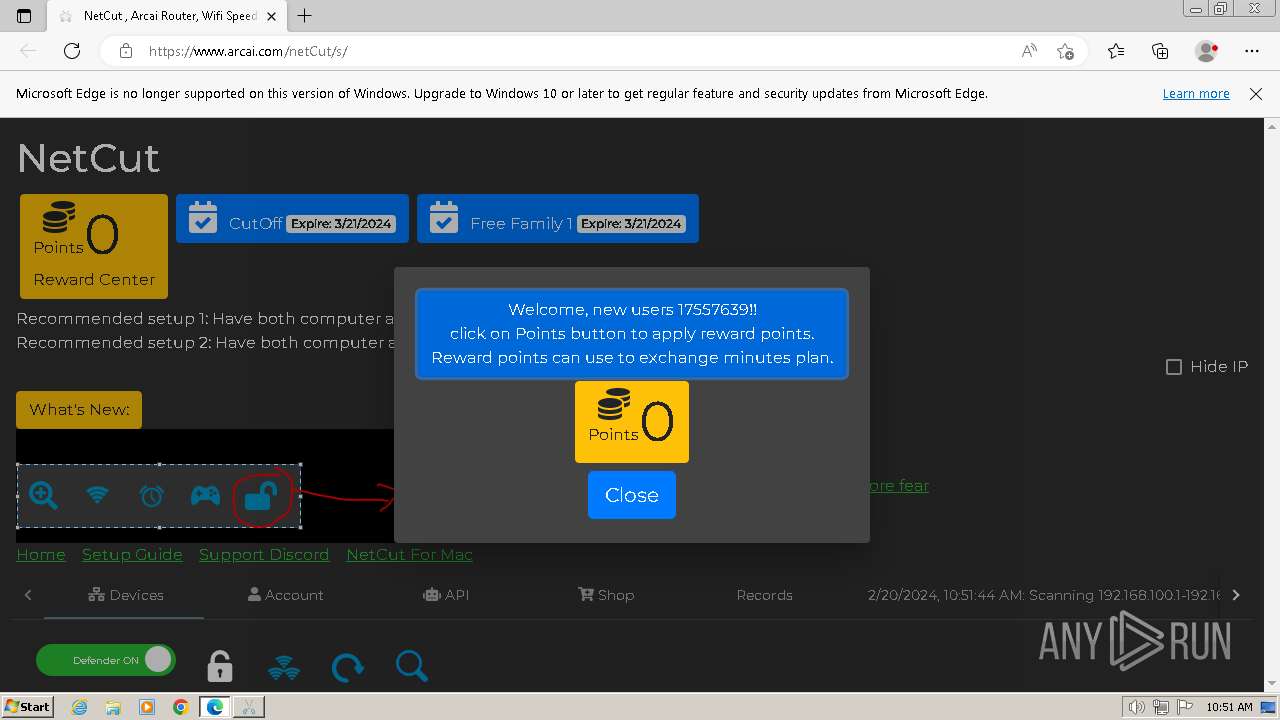
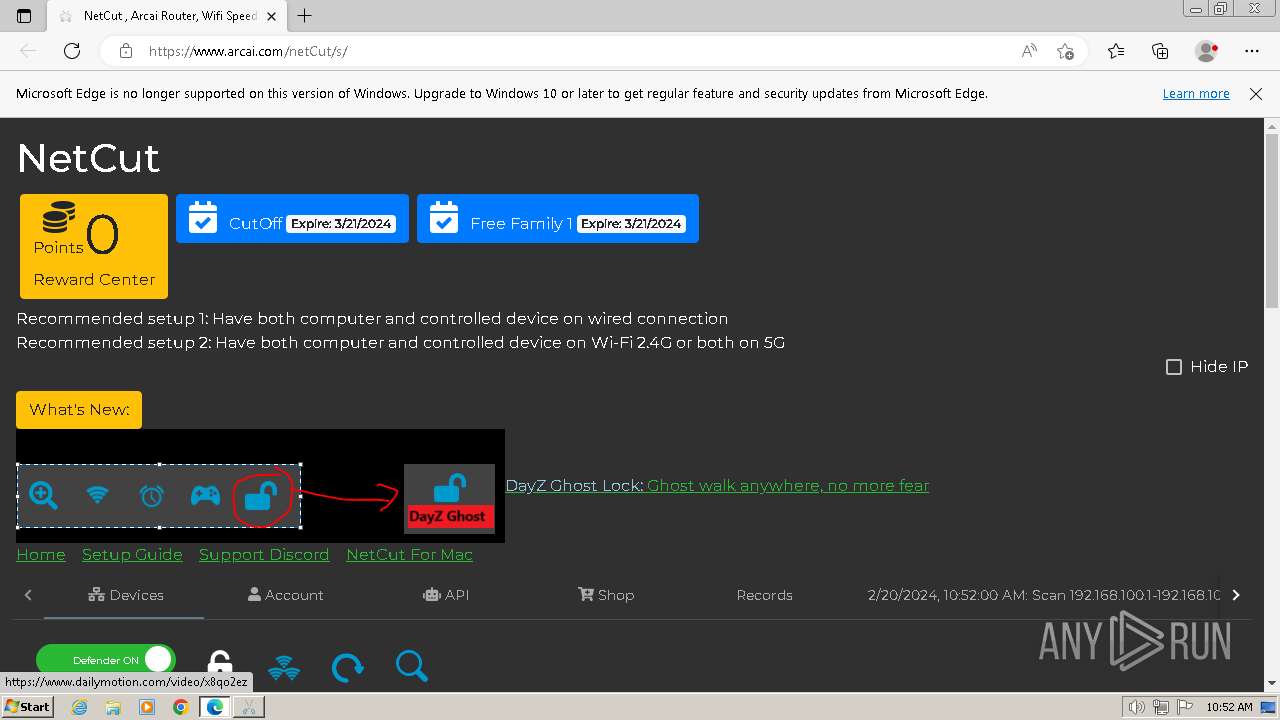
| File name: | netcut.exe |
| Full analysis: | https://app.any.run/tasks/c848fe34-0282-4066-a198-78cdf7a4dc0a |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2024, 10:50:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | EFF9A9BB4DAF455F0E3196AD605B1C7E |
| SHA1: | 742617EF0997A78A32A887E7CC70F28C946F423D |
| SHA256: | FD407FE24278F1A9448A33945CD4F94EAE4A74207F1069158051B39E753454E9 |
| SSDEEP: | 98304:2+cD4dngixOW2K3XiSUXuHti4nFr+23RFvZkPAFI2b/drv/9r/4dqTypdM+XQLAS:/5xa1GTT |
MALICIOUS
Drops the executable file immediately after the start
- netcut.exe (PID: 3700)
- netcut.exe (PID: 3948)
- netcut.tmp (PID: 3464)
- WinPcap_4_1_3.exe (PID: 3092)
- netcut_windows.exe (PID: 2372)
Creates a writable file in the system directory
- WinPcap_4_1_3.exe (PID: 3092)
- netcut_windows.exe (PID: 2372)
- netcut_windows.exe (PID: 3660)
Starts NET.EXE for service management
- WinPcap_4_1_3.exe (PID: 3092)
- net.exe (PID: 3940)
SUSPICIOUS
Executable content was dropped or overwritten
- netcut.exe (PID: 3700)
- netcut.exe (PID: 3948)
- netcut.tmp (PID: 3464)
- WinPcap_4_1_3.exe (PID: 3092)
- netcut_windows.exe (PID: 2372)
Reads the Windows owner or organization settings
- netcut.tmp (PID: 3464)
Process drops legitimate windows executable
- netcut.tmp (PID: 3464)
The process drops C-runtime libraries
- netcut.tmp (PID: 3464)
Starts SC.EXE for service management
- netcut.tmp (PID: 3464)
Malware-specific behavior (creating "System.dll" in Temp)
- WinPcap_4_1_3.exe (PID: 3092)
Drops a system driver (possible attempt to evade defenses)
- WinPcap_4_1_3.exe (PID: 3092)
Creates files in the driver directory
- WinPcap_4_1_3.exe (PID: 3092)
The process creates files with name similar to system file names
- WinPcap_4_1_3.exe (PID: 3092)
Creates or modifies Windows services
- WinPcap_4_1_3.exe (PID: 3092)
Creates a software uninstall entry
- WinPcap_4_1_3.exe (PID: 3092)
Executes as Windows Service
- aips.exe (PID: 2064)
Starts CMD.EXE for commands execution
- aips.exe (PID: 2064)
Connects to unusual port
- netcut_windows.exe (PID: 2372)
- netcut_windows.exe (PID: 3660)
Reads the Internet Settings
- netcut.tmp (PID: 3656)
Reads security settings of Internet Explorer
- aips.exe (PID: 2064)
INFO
Checks supported languages
- netcut.exe (PID: 3700)
- netcut.tmp (PID: 3656)
- netcut.tmp (PID: 3464)
- netcut.exe (PID: 3948)
- WinPcap_4_1_3.exe (PID: 3092)
- aips.exe (PID: 3488)
- netcut_windows.exe (PID: 2168)
- netcut_windows.exe (PID: 2372)
- wmpnscfg.exe (PID: 3632)
- netcut_windows.exe (PID: 3660)
- aips.exe (PID: 2064)
Create files in a temporary directory
- netcut.exe (PID: 3700)
- netcut.exe (PID: 3948)
- WinPcap_4_1_3.exe (PID: 3092)
Reads the computer name
- netcut.tmp (PID: 3656)
- netcut.tmp (PID: 3464)
- WinPcap_4_1_3.exe (PID: 3092)
- aips.exe (PID: 3488)
- aips.exe (PID: 2064)
- netcut_windows.exe (PID: 2372)
- netcut_windows.exe (PID: 3660)
- wmpnscfg.exe (PID: 3632)
Creates files in the program directory
- netcut.tmp (PID: 3464)
- WinPcap_4_1_3.exe (PID: 3092)
- netcut_windows.exe (PID: 2372)
- netcut_windows.exe (PID: 3660)
Creates files or folders in the user directory
- netcut.tmp (PID: 3464)
Creates a software uninstall entry
- netcut.tmp (PID: 3464)
Reads Environment values
- WinPcap_4_1_3.exe (PID: 3092)
Reads the machine GUID from the registry
- netcut_windows.exe (PID: 2372)
- aips.exe (PID: 2064)
- netcut_windows.exe (PID: 3660)
Application launched itself
- msedge.exe (PID: 2888)
Manual execution by a user
- wmpnscfg.exe (PID: 3632)
Checks proxy server information
- aips.exe (PID: 2064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 133120 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
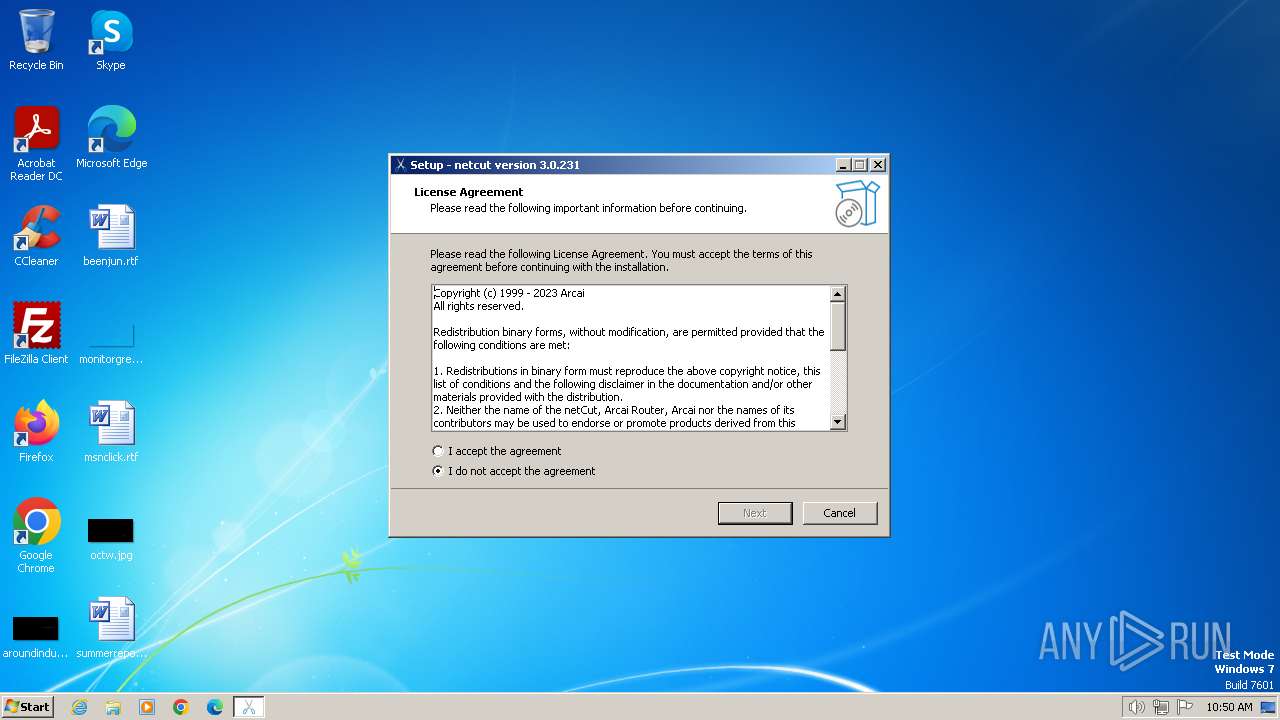
| Comments: | This installation was built with Inno Setup. |
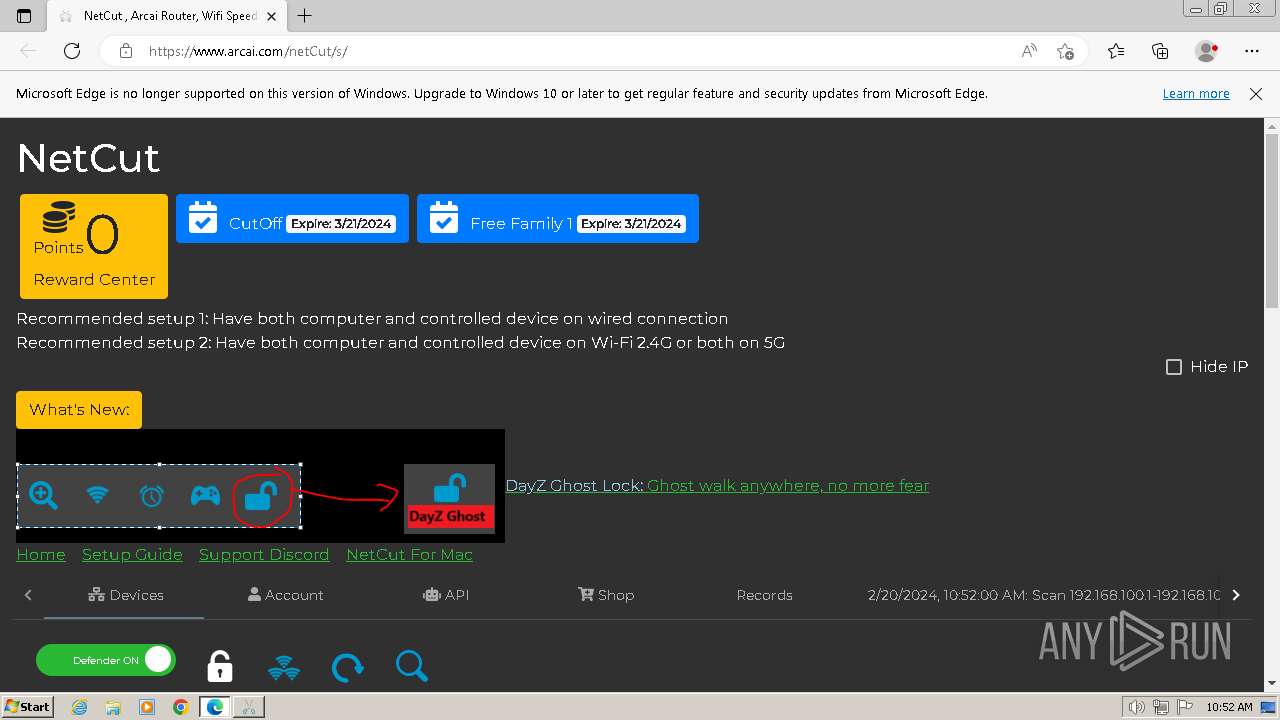
| CompanyName: | arcai.com |
| FileDescription: | netcut Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | netcut |
| ProductVersion: | 3.0.231 |
Total processes
92
Monitored processes
46
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 844 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1488 --field-trial-handle=1272,i,13648856121715021246,5600016336314210819,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 864 | "C:\Windows\system32\sc.exe" stop aips | C:\Windows\System32\sc.exe | — | netcut.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 880 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x69eaf598,0x69eaf5a8,0x69eaf5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 924 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --mojo-platform-channel-handle=4808 --field-trial-handle=1272,i,13648856121715021246,5600016336314210819,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1408 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3524 --field-trial-handle=1272,i,13648856121715021246,5600016336314210819,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1628 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4504 --field-trial-handle=1272,i,13648856121715021246,5600016336314210819,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1928 | C:\Windows\system32\cmd.exe /c "C:\Program Files\arcai.com\netcut_windows.exe" -v | C:\Windows\System32\cmd.exe | — | aips.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1292 --field-trial-handle=1272,i,13648856121715021246,5600016336314210819,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.PageScreenshotProcessor --lang=en-US --service-sandbox-type=entity_extraction --mojo-platform-channel-handle=4824 --field-trial-handle=1272,i,13648856121715021246,5600016336314210819,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\arcai.com\aips.exe" | C:\Program Files\arcai.com\aips.exe | services.exe | ||||||||||||
User: SYSTEM Company: Arcai.com Integrity Level: SYSTEM Description: Arp Intelligent Protection Service Exit code: 0 Version: 214 Modules
| |||||||||||||||
Total events
15 691
Read events
15 573
Write events
98
Delete events
20
Modification events
| (PID) Process: | (3464) netcut.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 880D0000242E8099EA63DA01 | |||
| (PID) Process: | (3464) netcut.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 095A210CF6D0C66C3B8E2B94AEC50CB0CF036141494468AB991EB064C4D2719D | |||
| (PID) Process: | (3464) netcut.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3464) netcut.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\arcai.com\aips.exe | |||
| (PID) Process: | (3464) netcut.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: BD4608858B3F977D90EAEDA07F11254124A73B282ACFC5218F131EB5802A15B0 | |||
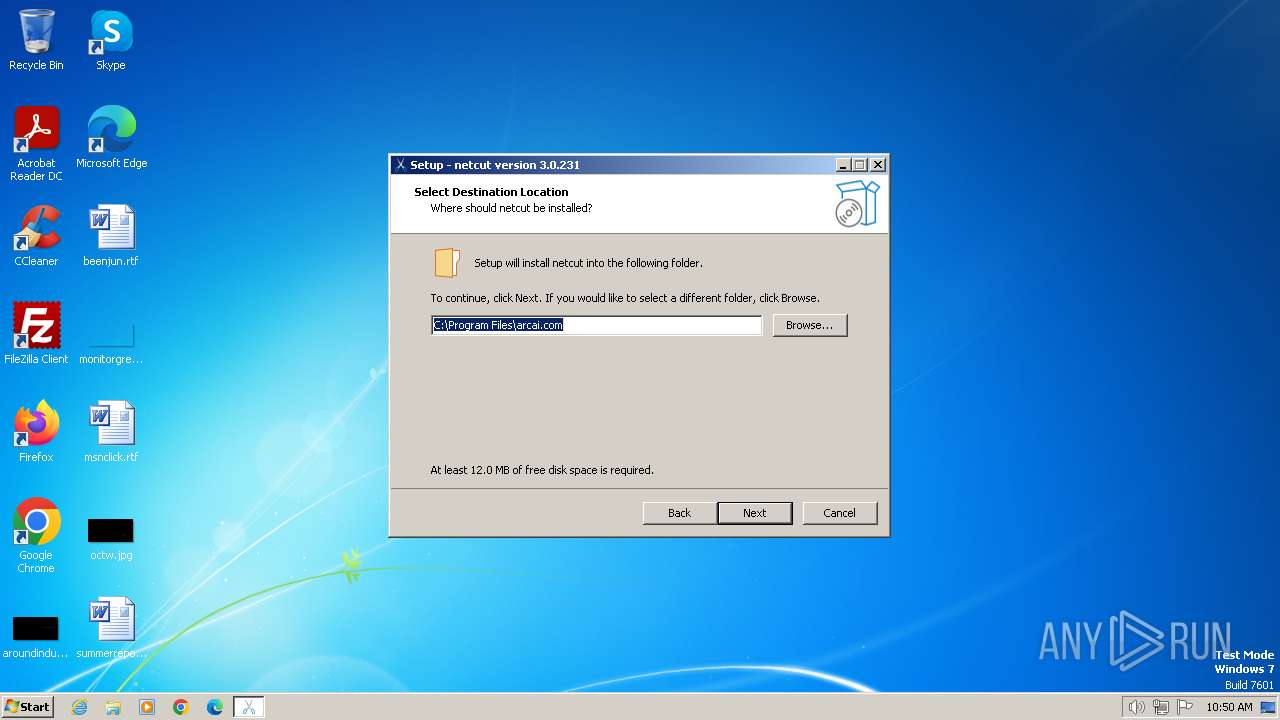
| (PID) Process: | (3464) netcut.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{6BE5152F-0885-4AA5-8385-4AD2D8472C71}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (3464) netcut.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{6BE5152F-0885-4AA5-8385-4AD2D8472C71}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\arcai.com | |||
| (PID) Process: | (3464) netcut.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{6BE5152F-0885-4AA5-8385-4AD2D8472C71}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\arcai.com\ | |||
| (PID) Process: | (3464) netcut.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{6BE5152F-0885-4AA5-8385-4AD2D8472C71}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: netcut | |||
| (PID) Process: | (3464) netcut.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{6BE5152F-0885-4AA5-8385-4AD2D8472C71}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
Executable files
28
Suspicious files
170
Text files
84
Unknown types
93
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3464 | netcut.tmp | C:\Program Files\arcai.com\is-UK5MI.tmp | executable | |
MD5:F3BC4FDA56B356923921BA3420C35F69 | SHA256:D1C10EF9BFC265E6C9273ED2DA26E1EA2BBBC13BD5204556B62295063D31D9AD | |||
| 3464 | netcut.tmp | C:\Program Files\arcai.com\is-85RAK.tmp | executable | |
MD5:1C7F149E8BE8DED2299311BB34396D87 | SHA256:B54D8E04864F0BF2E0559A38EF47EDA25B1D71A49600CF3649F87234F56DF119 | |||
| 3464 | netcut.tmp | C:\Program Files\arcai.com\unins000.exe | executable | |
MD5:1C7F149E8BE8DED2299311BB34396D87 | SHA256:B54D8E04864F0BF2E0559A38EF47EDA25B1D71A49600CF3649F87234F56DF119 | |||
| 3464 | netcut.tmp | C:\Program Files\arcai.com\netcut_windows.exe | executable | |
MD5:6E87E248D16EC5DD57EB225DDB96C52D | SHA256:2FF69D8777F0D819D268683035C9C1D744490DC5195954B7615FEBE5003B31E3 | |||
| 3464 | netcut.tmp | C:\Program Files\arcai.com\aips.exe | executable | |
MD5:F3BC4FDA56B356923921BA3420C35F69 | SHA256:D1C10EF9BFC265E6C9273ED2DA26E1EA2BBBC13BD5204556B62295063D31D9AD | |||
| 3464 | netcut.tmp | C:\Program Files\arcai.com\is-0P3RB.tmp | executable | |
MD5:034CCADC1C073E4216E9466B720F9849 | SHA256:86E39B5995AF0E042FCDAA85FE2AEFD7C9DDC7AD65E6327BD5E7058BC3AB615F | |||
| 3464 | netcut.tmp | C:\Program Files\arcai.com\is-Q35P3.tmp | text | |
MD5:527FA19FEF2324A6FA9EBE504B13A957 | SHA256:B4A61D49CB5140083D583278BF4E15E46FFE3BF0B916B89F0916C5374166D0E3 | |||
| 3464 | netcut.tmp | C:\Program Files\arcai.com\macdata | text | |
MD5:527FA19FEF2324A6FA9EBE504B13A957 | SHA256:B4A61D49CB5140083D583278BF4E15E46FFE3BF0B916B89F0916C5374166D0E3 | |||
| 3464 | netcut.tmp | C:\Program Files\arcai.com\msvcp120.dll | executable | |
MD5:FD5CABBE52272BD76007B68186EBAF00 | SHA256:87C42CA155473E4E71857D03497C8CBC28FA8FF7F2C8D72E8A1F39B71078F608 | |||
| 3464 | netcut.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\netcut\Uninstall netcut.lnk | lnk | |
MD5:24B4293485ABDA64305FDE156D384EEA | SHA256:BCAD0D4C3121502B22775A63293A9E7220CEC4ECA5E65D8AACAFC9A26BC5DD49 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
231
DNS requests
349
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2064 | aips.exe | GET | 200 | 188.114.97.3:80 | http://www.arcai.com/netCut/Update3.php?query=bmFtZT1uZXRjdXRfd2luZG93cy5leGU6dmVyc2lvbj0yMzE= | unknown | text | 12 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2888 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
844 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
844 | msedge.exe | 188.114.97.3:443 | www.arcai.com | — | — | unknown |
844 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2372 | netcut_windows.exe | 188.114.97.3:443 | www.arcai.com | CLOUDFLARENET | NL | unknown |
2372 | netcut_windows.exe | 172.105.129.132:443 | load.arcai.com | Linode, LLC | US | unknown |
844 | msedge.exe | 64.233.167.84:443 | accounts.google.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
www.arcai.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
load.arcai.com |
| unknown |
accounts.google.com |
| shared |
js.stripe.com |
| shared |
fonts.googleapis.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |