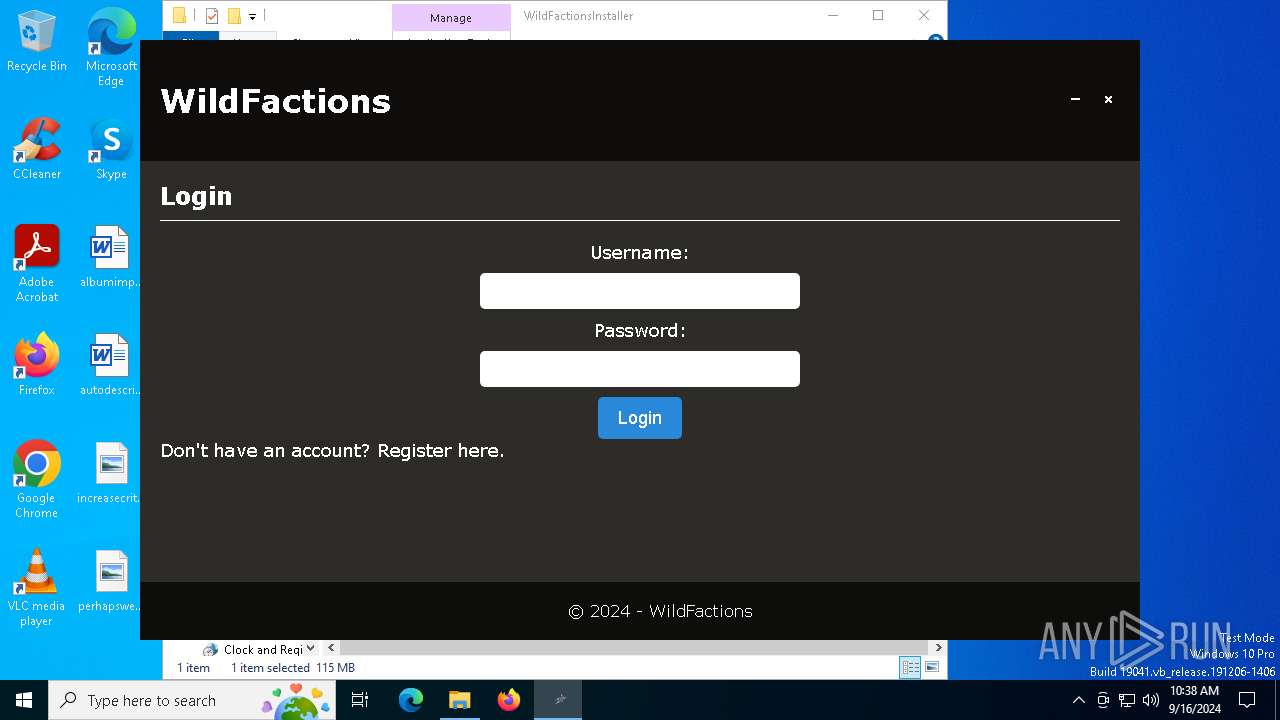
| URL: | https://wildfactions.com/ptbr/baixar/WildFactionsInstaller.rar |
| Full analysis: | https://app.any.run/tasks/91a2a2f8-4c21-4ed0-8038-989bd4e9f262 |
| Verdict: | Malicious activity |
| Analysis date: | September 16, 2024, 10:35:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 12199A08C0208470CB4A2FFDCC282602 |
| SHA1: | B5F053EFA6385C8E8CF92CFF1871669C0589BAD4 |
| SHA256: | FD3AF61F56088B2BF19403B9DD0FF5D1D8794F56640E7501683F05BDB7F29589 |
| SSDEEP: | 3:N8dPYGNWLdlRWfLReq8XLO:2dEQfLReFXLO |
MALICIOUS
Changes powershell execution policy (Unrestricted)
- ss_launcher.exe (PID: 1680)
- ss_launcher.exe (PID: 4252)
SUSPICIOUS
Executable content was dropped or overwritten
- WildFactionsInstaller.exe (PID: 5980)
- Update.exe (PID: 5400)
- ss_launcher.exe (PID: 1680)
- WildFactionsInstaller.exe (PID: 6884)
- Update.exe (PID: 2992)
- ss_launcher.exe (PID: 4252)
Reads security settings of Internet Explorer
- Update.exe (PID: 5400)
Starts itself from another location
- Update.exe (PID: 5400)
- Update.exe (PID: 2992)
Application launched itself
- ss_launcher.exe (PID: 5900)
- ss_launcher.exe (PID: 1680)
- ss_launcher.exe (PID: 3980)
- ss_launcher.exe (PID: 4252)
Starts CMD.EXE for commands execution
- ss_launcher.exe (PID: 1680)
- NETSTAT.EXE (PID: 1488)
- NETSTAT.EXE (PID: 1712)
- ss_launcher.exe (PID: 4252)
- NETSTAT.EXE (PID: 6912)
- NETSTAT.EXE (PID: 3028)
Starts application with an unusual extension
- cmd.exe (PID: 3032)
- cmd.exe (PID: 2008)
Get information on the list of running processes
- ss_launcher.exe (PID: 1680)
- cmd.exe (PID: 6160)
- cmd.exe (PID: 5712)
- ss_launcher.exe (PID: 4252)
- cmd.exe (PID: 6352)
- cmd.exe (PID: 6472)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 5740)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 6260)
- cmd.exe (PID: 6164)
- cmd.exe (PID: 3696)
- cmd.exe (PID: 6872)
The process hides Powershell's copyright startup banner
- ss_launcher.exe (PID: 1680)
- ss_launcher.exe (PID: 4252)
The process bypasses the loading of PowerShell profile settings
- ss_launcher.exe (PID: 1680)
- ss_launcher.exe (PID: 4252)
Starts POWERSHELL.EXE for commands execution
- ss_launcher.exe (PID: 1680)
- ss_launcher.exe (PID: 4252)
Runs PING.EXE to delay simulation
- ss_launcher.exe (PID: 1680)
- ss_launcher.exe (PID: 4252)
Uses NETSH.EXE to obtain data on the network
- powershell.exe (PID: 5980)
- cmd.exe (PID: 6412)
- powershell.exe (PID: 4404)
- cmd.exe (PID: 1164)
Uses QUSER.EXE to read information about current user sessions
- query.exe (PID: 5540)
- query.exe (PID: 1712)
Found regular expressions for crypto-addresses (YARA)
- ss_launcher.exe (PID: 1680)
- ss_launcher.exe (PID: 4252)
Possible usage of Discord/Telegram API has been detected (YARA)
- ss_launcher.exe (PID: 1680)
- ss_launcher.exe (PID: 4252)
Executes as Windows Service
- WmiApSrv.exe (PID: 6852)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 4128)
- cmd.exe (PID: 6756)
INFO
Application launched itself
- msedge.exe (PID: 2208)
Checks supported languages
- identity_helper.exe (PID: 2992)
- WildFactionsInstaller.exe (PID: 5980)
- Update.exe (PID: 5400)
- ss_launcher.exe (PID: 6524)
- ss_launcher.exe (PID: 6724)
- ss_launcher.exe (PID: 6164)
- ss_launcher.exe (PID: 4708)
- squirrel.exe (PID: 6056)
- ss_launcher.exe (PID: 5900)
Reads Environment values
- identity_helper.exe (PID: 2992)
Reads the computer name
- identity_helper.exe (PID: 2992)
- Update.exe (PID: 5400)
- squirrel.exe (PID: 6056)
- ss_launcher.exe (PID: 5900)
- ss_launcher.exe (PID: 6724)
- ss_launcher.exe (PID: 6524)
- ss_launcher.exe (PID: 6164)
Manual execution by a user
- WinRAR.exe (PID: 460)
- WildFactionsInstaller.exe (PID: 5980)
- WildFactionsInstaller.exe (PID: 6884)
The process uses the downloaded file
- msedge.exe (PID: 6100)
- WinRAR.exe (PID: 460)
- Update.exe (PID: 5400)
Creates files or folders in the user directory
- WildFactionsInstaller.exe (PID: 5980)
- Update.exe (PID: 5400)
- squirrel.exe (PID: 6056)
Reads the machine GUID from the registry
- Update.exe (PID: 5400)
- squirrel.exe (PID: 6056)
- ss_launcher.exe (PID: 5900)
Create files in a temporary directory
- Update.exe (PID: 5400)
Process checks computer location settings
- Update.exe (PID: 5400)
Checks proxy server information
- ss_launcher.exe (PID: 5900)
Changes the display of characters in the console
- cmd.exe (PID: 3032)
- cmd.exe (PID: 2008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(1680) ss_launcher.exe
Discord-Webhook-Tokens (1)1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Discord-Info-Links
1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Get Webhook Infohttps://discord.com/api/webhooks/1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleKushner | Quick Cookies
fields
namePasswords
value[Download](https://gofile.io/d/eCDzFY)
inlinefalse
nameCookies
value[Download](https://gofile.io/d/KIzGgS)
inlinefalse
content_scan_version0
timestamp2024-09-16T10:38:08.368000+00:00
edited_timestamp2024-09-16T10:38:09.351540+00:00
flags0
components (0)
id1285187964472791091
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleStealing... 🥷 DESKTOP-JGLLJLD
timestamp2024-09-16T10:38:08.021000+00:00
footer
textDESKTOP-JGLLJLD | Kushner | Simplicity
icon_urlhttps://media.discordapp.net/attachments/1207817856868425728/1207818276680372384/fd6304558f538086e4fa80b06a403c2a.jpg?ex=66e8b36d&is=66e761ed&hm=328ac59516dd1574c60988f1de2ae2052999b6471193d76defc701a84e5e5adf&format=webp&
proxy_icon_urlhttps://media.discordapp.net/attachments/1207817856868425728/1207818276680372384/fd6304558f538086e4fa80b06a403c2a.jpg?ex=66e8b36d&is=66e761ed&hm=328ac59516dd1574c60988f1de2ae2052999b6471193d76defc701a84e5e5adf&
timestamp2024-09-16T10:38:08.368000+00:00
edited_timestampnull
flags0
components (0)
id1285187964472791091
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
Discord-Webhook-Tokens (1)1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Discord-Info-Links
1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Get Webhook Infohttps://discord.com/api/webhooks/1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Discord-Webhook-Tokens (1)1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Discord-Info-Links
1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Get Webhook Infohttps://discord.com/api/webhooks/1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleKushner | Quick Cookies
fields
namePasswords
value[Download](https://gofile.io/d/eCDzFY)
inlinefalse
nameCookies
value[Download](https://gofile.io/d/KIzGgS)
inlinefalse
content_scan_version0
timestamp2024-09-16T10:38:08.368000+00:00
edited_timestamp2024-09-16T10:38:09.351540+00:00
flags0
components (0)
id1285187964472791091
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleStealing... 🥷 DESKTOP-JGLLJLD
timestamp2024-09-16T10:38:08.021000+00:00
footer
textDESKTOP-JGLLJLD | Kushner | Simplicity
icon_urlhttps://media.discordapp.net/attachments/1207817856868425728/1207818276680372384/fd6304558f538086e4fa80b06a403c2a.jpg?ex=66e8b36d&is=66e761ed&hm=328ac59516dd1574c60988f1de2ae2052999b6471193d76defc701a84e5e5adf&format=webp&
proxy_icon_urlhttps://media.discordapp.net/attachments/1207817856868425728/1207818276680372384/fd6304558f538086e4fa80b06a403c2a.jpg?ex=66e8b36d&is=66e761ed&hm=328ac59516dd1574c60988f1de2ae2052999b6471193d76defc701a84e5e5adf&
timestamp2024-09-16T10:38:08.368000+00:00
edited_timestampnull
flags0
components (0)
id1285187964472791091
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleKushner | Quick Cookies
fields
namePasswords
value[Download](https://gofile.io/d/eCDzFY)
inlinefalse
nameCookies
value[Download](https://gofile.io/d/KIzGgS)
inlinefalse
content_scan_version0
timestamp2024-09-16T10:38:08.368000+00:00
edited_timestamp2024-09-16T10:38:09.351540+00:00
flags0
components (0)
id1285187964472791091
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleKushner | Quick Cookies
fields
namePasswords
value[Download](https://gofile.io/d/eCDzFY)
inlinefalse
nameCookies
value[Download](https://gofile.io/d/KIzGgS)
inlinefalse
content_scan_version0
timestamp2024-09-16T10:38:08.368000+00:00
edited_timestamp2024-09-16T10:38:09.351540+00:00
flags0
components (0)
id1285187964472791091
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleStealing... 🥷 DESKTOP-JGLLJLD
timestamp2024-09-16T10:38:08.021000+00:00
footer
textDESKTOP-JGLLJLD | Kushner | Simplicity
icon_urlhttps://media.discordapp.net/attachments/1207817856868425728/1207818276680372384/fd6304558f538086e4fa80b06a403c2a.jpg?ex=66e8b36d&is=66e761ed&hm=328ac59516dd1574c60988f1de2ae2052999b6471193d76defc701a84e5e5adf&format=webp&
proxy_icon_urlhttps://media.discordapp.net/attachments/1207817856868425728/1207818276680372384/fd6304558f538086e4fa80b06a403c2a.jpg?ex=66e8b36d&is=66e761ed&hm=328ac59516dd1574c60988f1de2ae2052999b6471193d76defc701a84e5e5adf&
timestamp2024-09-16T10:38:08.368000+00:00
edited_timestampnull
flags0
components (0)
id1285187964472791091
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
(PID) Process(4252) ss_launcher.exe
Discord-Webhook-Tokens (1)1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Discord-Info-Links
1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Get Webhook Infohttps://discord.com/api/webhooks/1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Discord-Webhook-Tokens (1)1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Discord-Info-Links
1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Get Webhook Infohttps://discord.com/api/webhooks/1275770852851322933/Q1mP670nG45zyjhLcKiBttv-YUd6ENMNqLyZPaf-lFWoYAa0AgD3DEooR7HquvrPTbNo
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleKushner | Quick Cookies
fields
namePasswords
value[Download](https://gofile.io/d/seTU0K)
inlinefalse
nameCookies
value[Download](https://gofile.io/d/vhxJYh)
inlinefalse
content_scan_version0
timestamp2024-09-16T10:40:06.686000+00:00
edited_timestamp2024-09-16T10:40:07.906076+00:00
flags0
components (0)
id1285188460734447616
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleKushner | Quick Cookies
fields
namePasswords
value[Download](https://gofile.io/d/seTU0K)
inlinefalse
nameCookies
value[Download](https://gofile.io/d/vhxJYh)
inlinefalse
content_scan_version0
timestamp2024-09-16T10:40:06.686000+00:00
edited_timestamp2024-09-16T10:40:07.906076+00:00
flags0
components (0)
id1285188460734447616
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleStealing... 🥷 DESKTOP-JGLLJLD
timestamp2024-09-16T10:40:06.292000+00:00
footer
textDESKTOP-JGLLJLD | Kushner | Simplicity
icon_urlhttps://media.discordapp.net/attachments/1207817856868425728/1207818276680372384/fd6304558f538086e4fa80b06a403c2a.jpg?ex=66e95c2d&is=66e80aad&hm=bbb3b794536ef9de300c3bcf63ddd8a413ceab1172051db3dfc3bb7feb36bda3&format=webp&
proxy_icon_urlhttps://media.discordapp.net/attachments/1207817856868425728/1207818276680372384/fd6304558f538086e4fa80b06a403c2a.jpg?ex=66e95c2d&is=66e80aad&hm=bbb3b794536ef9de300c3bcf63ddd8a413ceab1172051db3dfc3bb7feb36bda3&
timestamp2024-09-16T10:40:06.686000+00:00
edited_timestampnull
flags0
components (0)
id1285188460734447616
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleStealing... 🥷 DESKTOP-JGLLJLD
timestamp2024-09-16T10:40:06.292000+00:00
footer
textDESKTOP-JGLLJLD | Kushner | Simplicity
icon_urlhttps://media.discordapp.net/attachments/1207817856868425728/1207818276680372384/fd6304558f538086e4fa80b06a403c2a.jpg?ex=66e95c2d&is=66e80aad&hm=bbb3b794536ef9de300c3bcf63ddd8a413ceab1172051db3dfc3bb7feb36bda3&format=webp&
proxy_icon_urlhttps://media.discordapp.net/attachments/1207817856868425728/1207818276680372384/fd6304558f538086e4fa80b06a403c2a.jpg?ex=66e95c2d&is=66e80aad&hm=bbb3b794536ef9de300c3bcf63ddd8a413ceab1172051db3dfc3bb7feb36bda3&
timestamp2024-09-16T10:40:06.686000+00:00
edited_timestampnull
flags0
components (0)
id1285188460734447616
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleKushner | Quick Cookies
fields
namePasswords
value[Download](https://gofile.io/d/seTU0K)
inlinefalse
nameCookies
value[Download](https://gofile.io/d/vhxJYh)
inlinefalse
content_scan_version0
timestamp2024-09-16T10:40:06.686000+00:00
edited_timestamp2024-09-16T10:40:07.906076+00:00
flags0
components (0)
id1285188460734447616
channel_id1275770822253871135
author
id1275770852851322933
usernameKushner | Simplicity
avatar267280f9b43feed91fdd7bd4b8ed7fd8
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1275770852851322933
Total processes
318
Monitored processes
179
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5628 --field-trial-handle=2456,i,2616800318873130901,9067003586709700842,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6724 --field-trial-handle=2456,i,2616800318873130901,9067003586709700842,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 208 | powershell.exe -NoProfile -NoLogo -InputFormat Text -NoExit -ExecutionPolicy Unrestricted -Command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | ss_launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 236 | C:\WINDOWS\system32\route.exe print | C:\Windows\System32\ROUTE.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Route Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 368 | taskkill /IM msedge.exe /F | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 368 | "C:\Users\admin\AppData\Local\app_kush_com\app-1.0.0\ss_launcher.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\ss_launcher" --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=2376 --field-trial-handle=1700,i,16086580863103348011,3666782219280592894,262144 --enable-features=kWebSQLAccess --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version /prefetch:2 | C:\Users\admin\AppData\Local\app_kush_com\app-1.0.0\ss_launcher.exe | — | ss_launcher.exe | |||||||||||
User: admin Company: kush Inc. Integrity Level: LOW Description: ss_launcher Exit code: 0 Version: 1.0.0 | |||||||||||||||
| 368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 460 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\WildFactionsInstaller.rar" C:\Users\admin\Downloads\WildFactionsInstaller\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 508 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2452 --field-trial-handle=2456,i,2616800318873130901,9067003586709700842,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 1 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
7 994
Read events
7 976
Write events
18
Delete events
0
Modification events
| (PID) Process: | (2208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2208) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: A451826BD0802F00 | |||
| (PID) Process: | (2208) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: AE98886BD0802F00 | |||
| (PID) Process: | (2208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459552 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {813B883B-B413-4AF0-BE78-EDFAD624E9B1} | |||
| (PID) Process: | (2208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459552 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {645FA4E3-343F-4530-9D6A-FA5CC190BD50} | |||
| (PID) Process: | (2208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (2208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
Executable files
26
Suspicious files
424
Text files
184
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF129e7a.TMP | — | |
MD5:— | SHA256:— | |||
| 2208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF129e6b.TMP | — | |
MD5:— | SHA256:— | |||
| 2208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF129e7a.TMP | — | |
MD5:— | SHA256:— | |||
| 2208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF129e7a.TMP | — | |
MD5:— | SHA256:— | |||
| 2208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF129e1d.TMP | — | |
MD5:— | SHA256:— | |||
| 2208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF129e7a.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
89
DNS requests
62
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6416 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4060 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4060 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6900 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/85cb4666-0aaf-4393-9c3a-aa0e3c026076?P1=1726621441&P2=404&P3=2&P4=UL8uGBiFd%2bRjWokMZm3DsWh1YPA7I1RhiqNvNM%2bVb9%2f3eihGpb%2bu8oUSl0THee%2fh7VXAGJ9gJPU8E%2b%2f31IAEFA%3d%3d | unknown | — | — | whitelisted |
2248 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6900 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/85cb4666-0aaf-4393-9c3a-aa0e3c026076?P1=1726621441&P2=404&P3=2&P4=UL8uGBiFd%2bRjWokMZm3DsWh1YPA7I1RhiqNvNM%2bVb9%2f3eihGpb%2bu8oUSl0THee%2fh7VXAGJ9gJPU8E%2b%2f31IAEFA%3d%3d | unknown | — | — | whitelisted |
6900 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/85cb4666-0aaf-4393-9c3a-aa0e3c026076?P1=1726621441&P2=404&P3=2&P4=UL8uGBiFd%2bRjWokMZm3DsWh1YPA7I1RhiqNvNM%2bVb9%2f3eihGpb%2bu8oUSl0THee%2fh7VXAGJ9gJPU8E%2b%2f31IAEFA%3d%3d | unknown | — | — | whitelisted |
6900 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/85cb4666-0aaf-4393-9c3a-aa0e3c026076?P1=1726621441&P2=404&P3=2&P4=UL8uGBiFd%2bRjWokMZm3DsWh1YPA7I1RhiqNvNM%2bVb9%2f3eihGpb%2bu8oUSl0THee%2fh7VXAGJ9gJPU8E%2b%2f31IAEFA%3d%3d | unknown | — | — | whitelisted |
6900 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/85cb4666-0aaf-4393-9c3a-aa0e3c026076?P1=1726621441&P2=404&P3=2&P4=UL8uGBiFd%2bRjWokMZm3DsWh1YPA7I1RhiqNvNM%2bVb9%2f3eihGpb%2bu8oUSl0THee%2fh7VXAGJ9gJPU8E%2b%2f31IAEFA%3d%3d | unknown | — | — | whitelisted |
6900 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/85cb4666-0aaf-4393-9c3a-aa0e3c026076?P1=1726621441&P2=404&P3=2&P4=UL8uGBiFd%2bRjWokMZm3DsWh1YPA7I1RhiqNvNM%2bVb9%2f3eihGpb%2bu8oUSl0THee%2fh7VXAGJ9gJPU8E%2b%2f31IAEFA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7072 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2248 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4880 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2208 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4880 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4880 | msedge.exe | 13.107.253.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4880 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4880 | msedge.exe | 94.245.104.56:443 | api.edgeoffer.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
wildfactions.com |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgeservices.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
— | — | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
— | — | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
— | — | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
— | — | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
— | — | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
— | — | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
— | — | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |