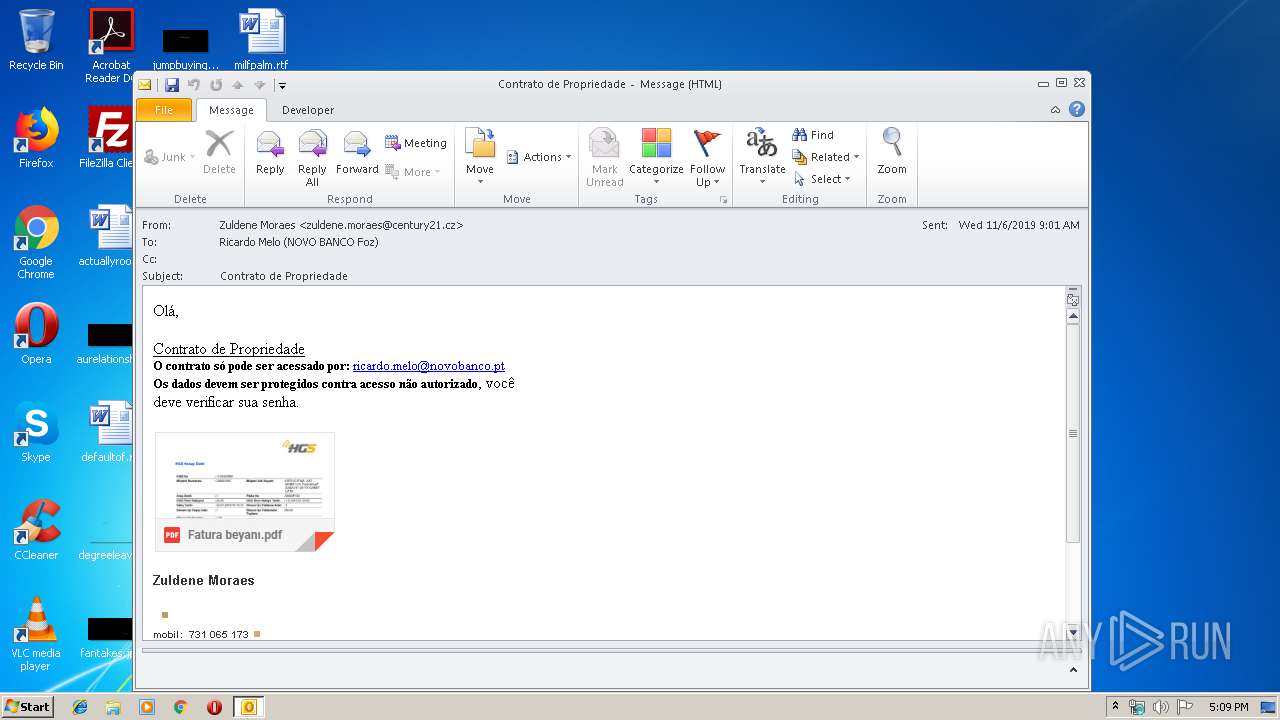
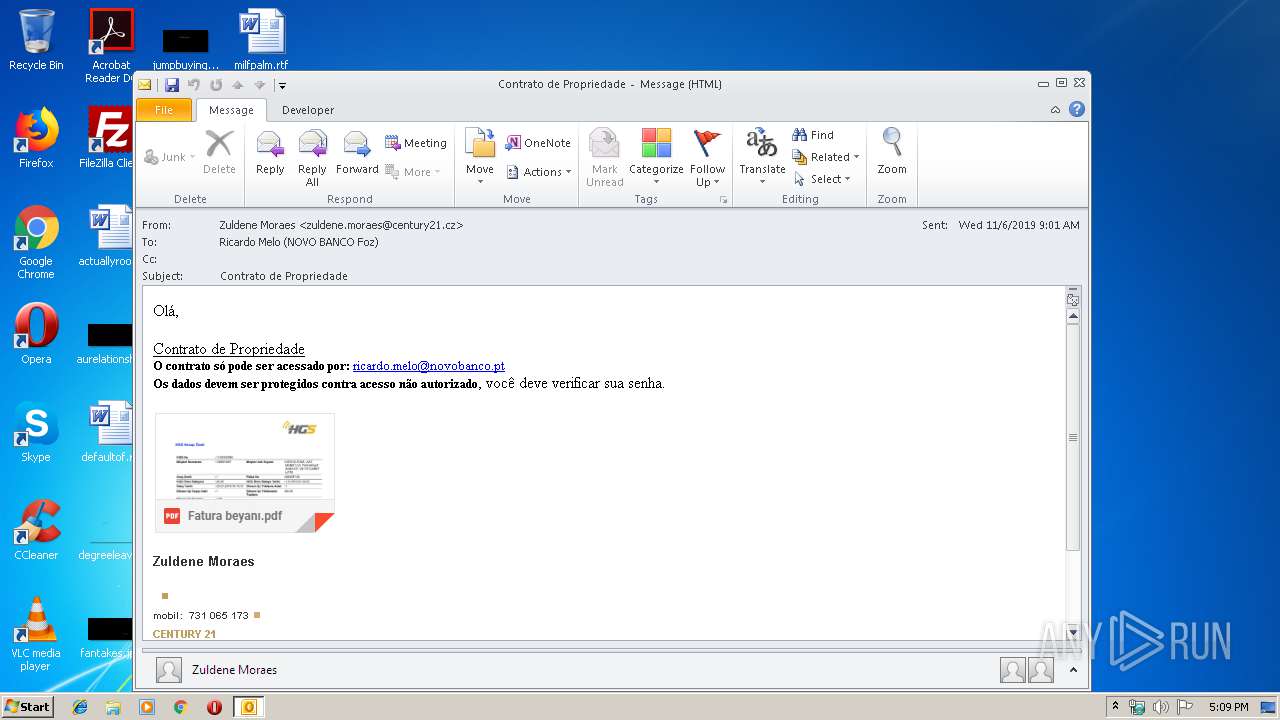
| File name: | Contrato de Propriedade.msg |
| Full analysis: | https://app.any.run/tasks/5ec49e3b-1f49-4ee3-9a71-aaf8b8696dd7 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2019, 17:09:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 86ECEECAD8AFD26CF77FBA36E9BBC3D8 |
| SHA1: | 037DCCB04A1778E4C8A2F60E1258821098A87D63 |
| SHA256: | FD1E2E516CB128378A25827D1D270EA11CAE8962A42CA2FF41D0C4B03C808984 |
| SSDEEP: | 768:3TH4lM1KUo6tfbD4vdvvDL68cev+3nL18nx3n+Bm6oKw6ulZezBTMQeb4K/s:3AUo6tjD4lLGWvwSeFolcl3I5 |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 1952)
SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 1952)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 1952)
Creates files in the user directory
- OUTLOOK.EXE (PID: 1952)
INFO
Changes internet zones settings
- iexplore.exe (PID: 328)
Reads Internet Cache Settings
- iexplore.exe (PID: 3300)
- iexplore.exe (PID: 1524)
Application launched itself
- iexplore.exe (PID: 328)
Creates files in the user directory
- iexplore.exe (PID: 3300)
Reads internet explorer settings
- iexplore.exe (PID: 3300)
- iexplore.exe (PID: 1524)
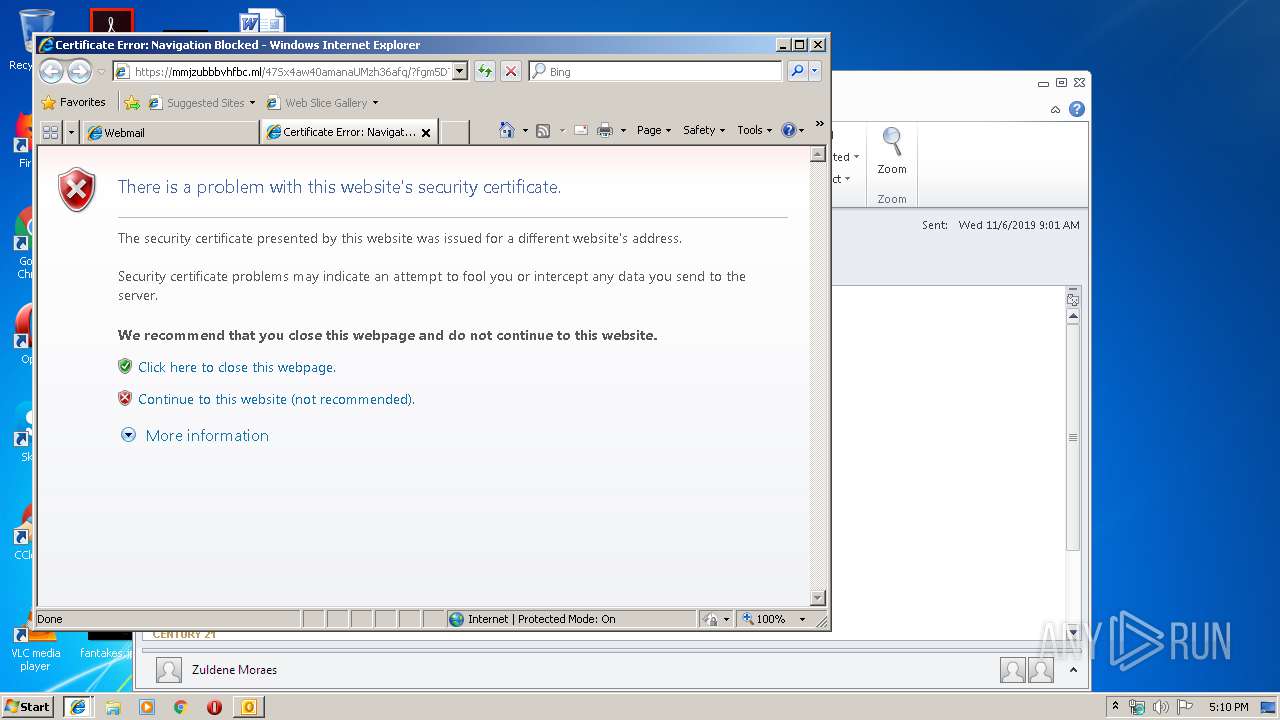
Reads settings of System Certificates
- iexplore.exe (PID: 328)
Changes settings of System certificates
- iexplore.exe (PID: 328)
Adds / modifies Windows certificates
- iexplore.exe (PID: 328)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
39
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
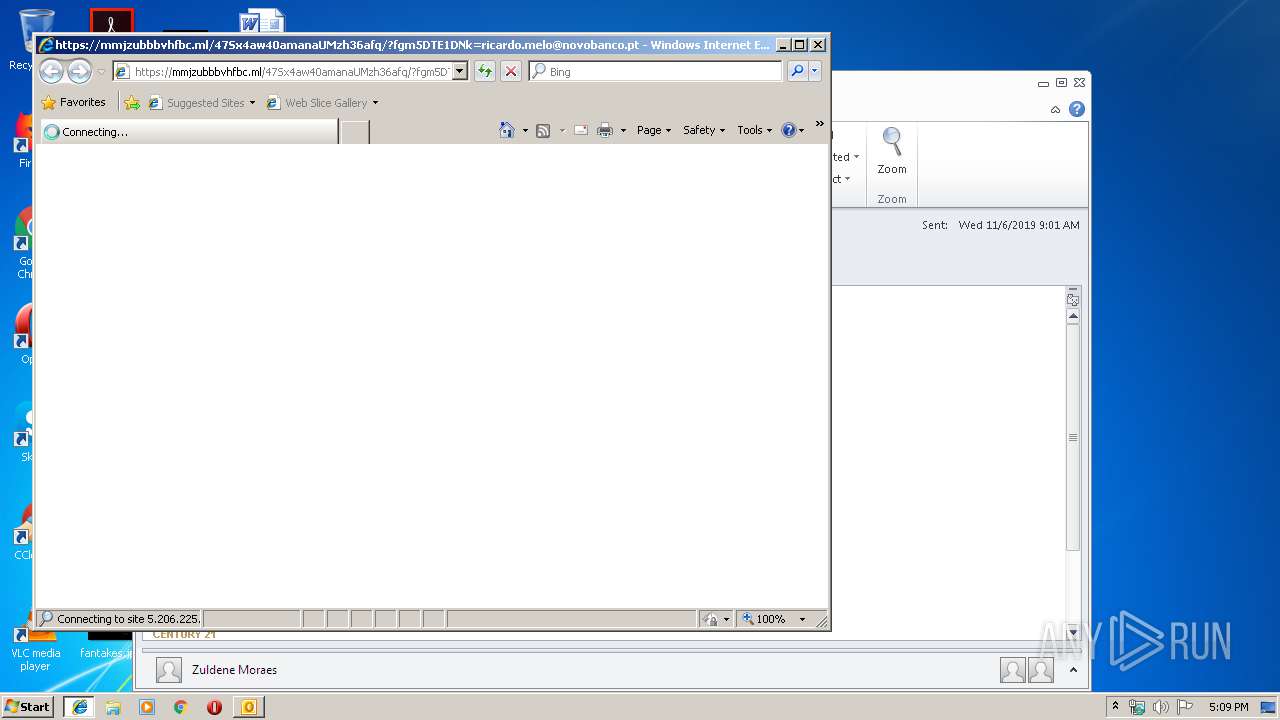
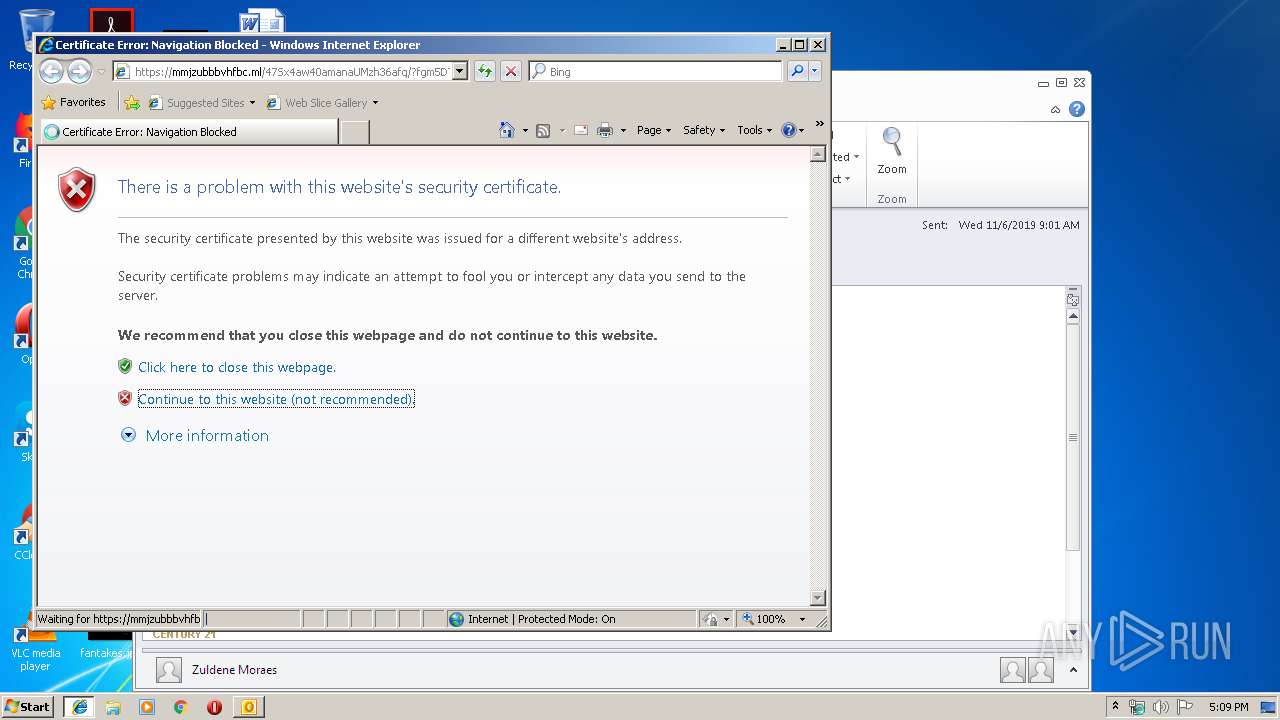
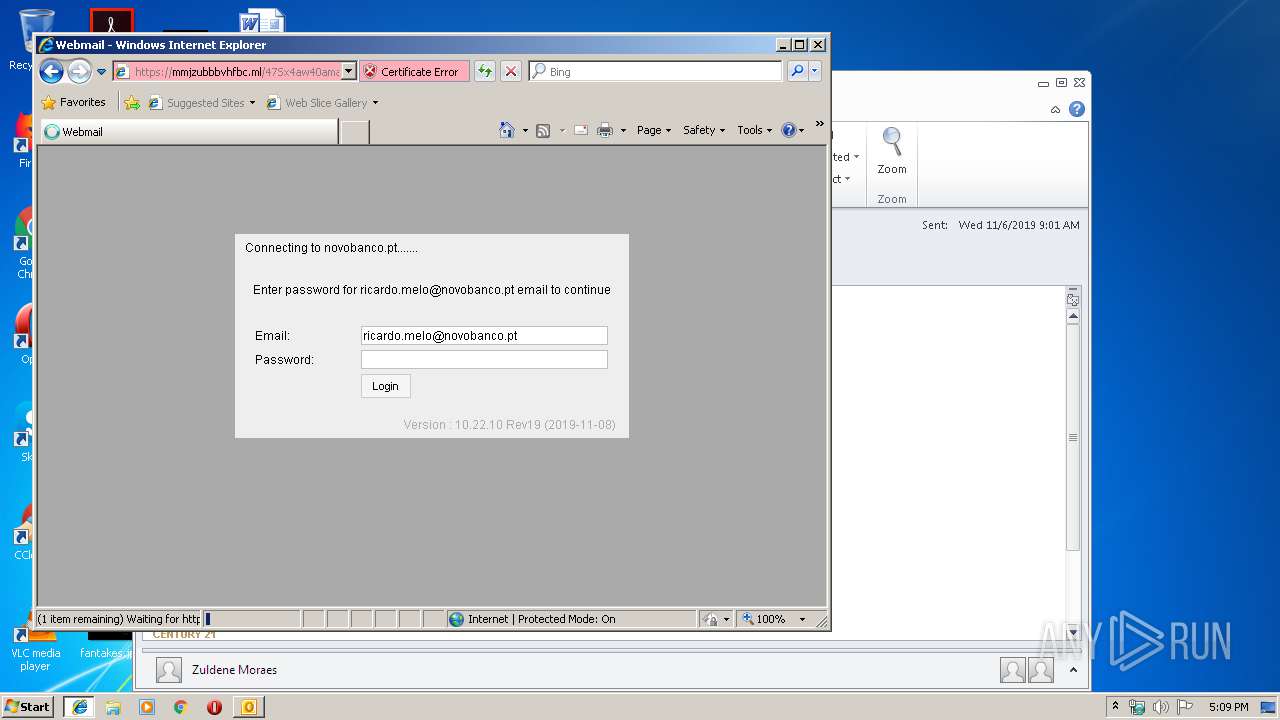
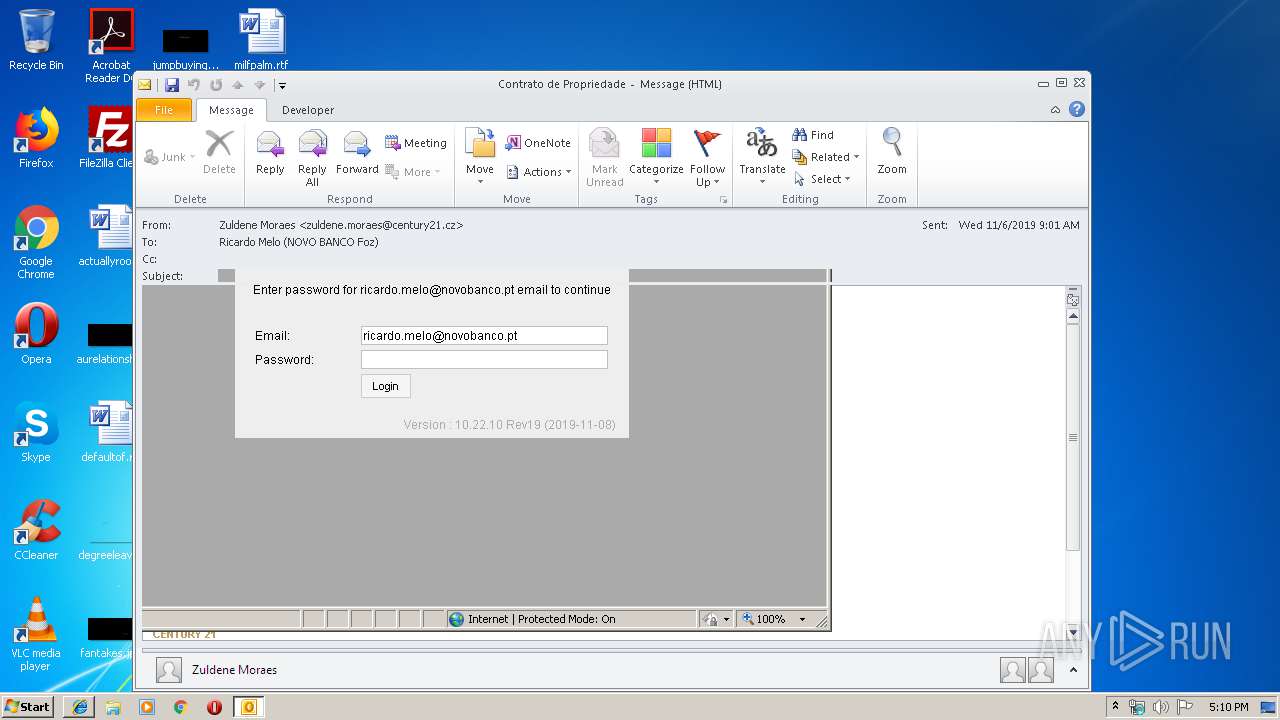
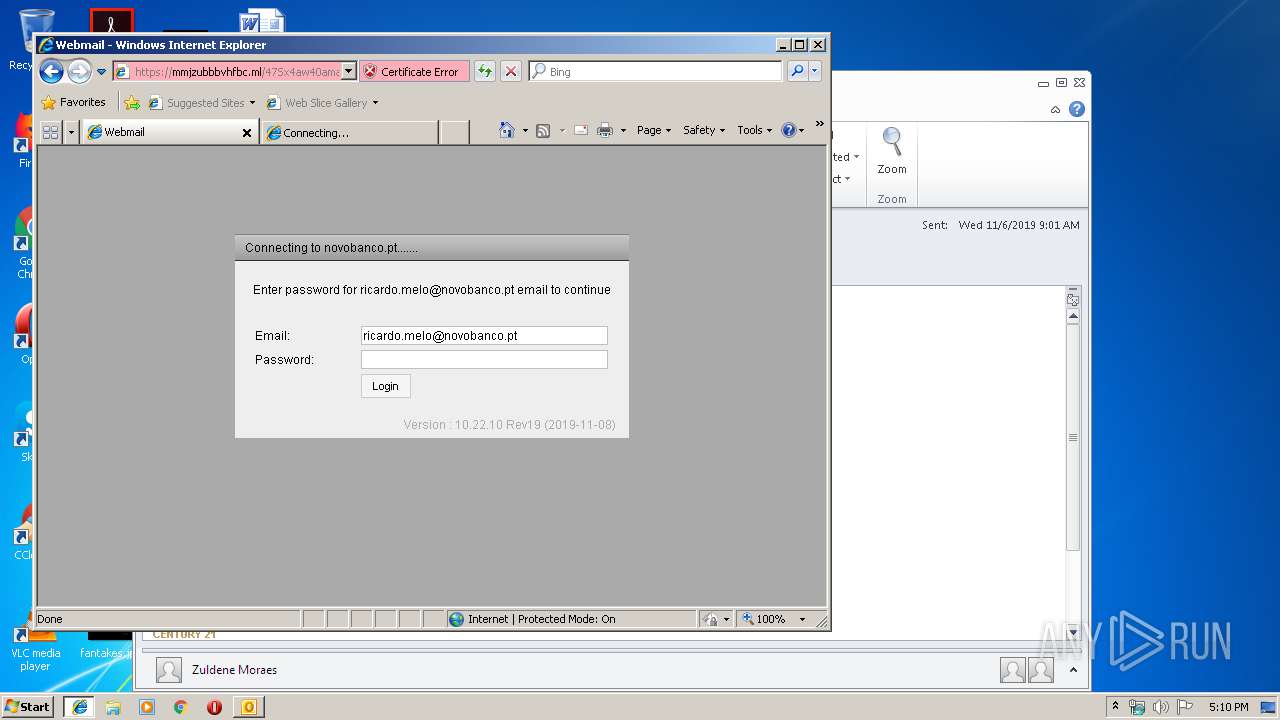
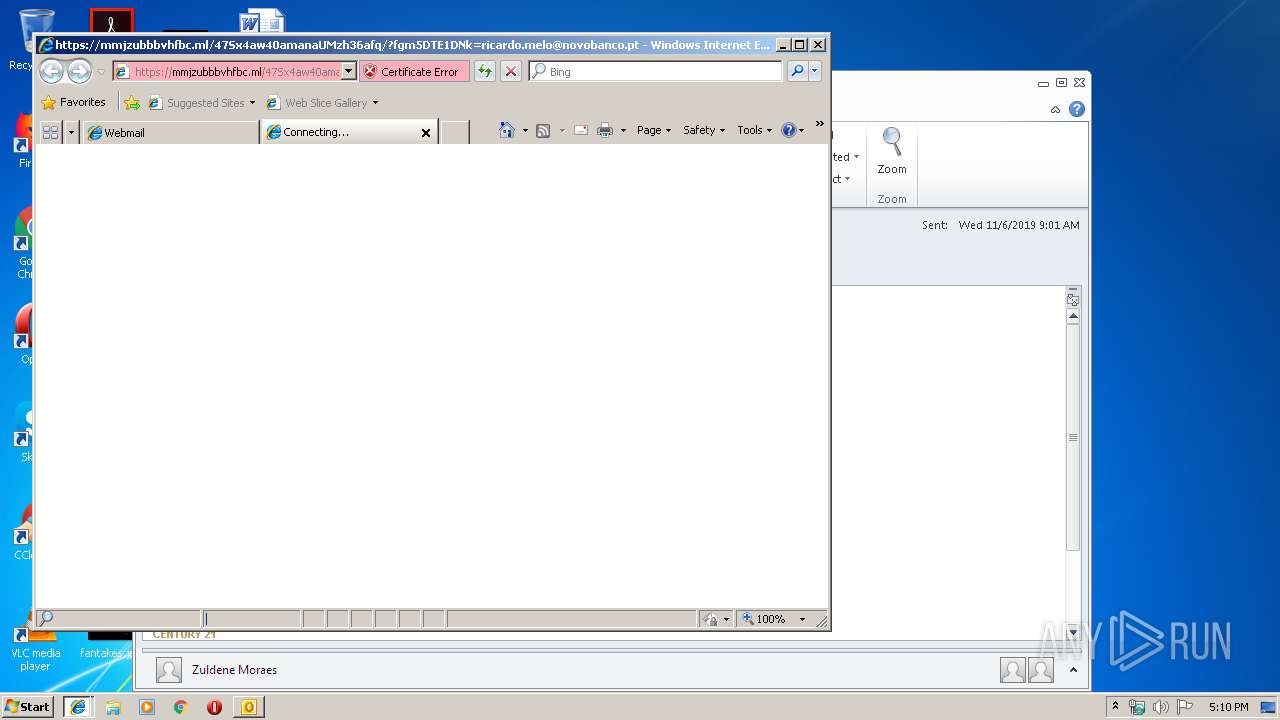
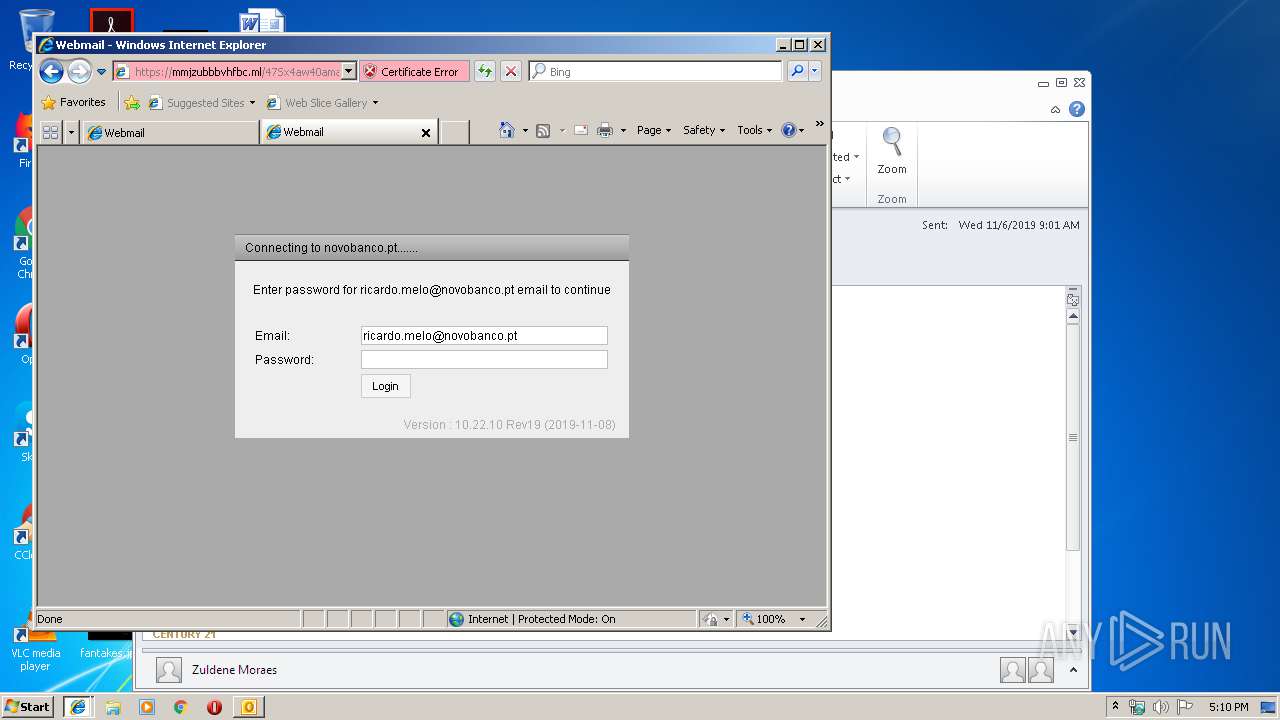
| 328 | "C:\Program Files\Internet Explorer\iexplore.exe" https://mmjzubbbvhfbc.ml/47Sx4aw40amanaUMzh36afq/?fgm5DTE1DNk=ricardo.melo@novobanco.pt | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1524 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:328 CREDAT:6404 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1952 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Contrato de Propriedade.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3300 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:328 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 104
Read events
1 462
Write events
622
Delete events
20
Modification events
| (PID) Process: | (1952) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1952) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1952) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1952) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1952) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1952) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1952) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1952) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1952) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1332215988 | |||
| (PID) Process: | (1952) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshot |
Value: 1033;1046;1036;1031;1040;1041;1049;3082;1042;1055 | |||
Executable files
0
Suspicious files
0
Text files
57
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1952 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRA860.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 328 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 328 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1952 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1952 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\66FE7BDA.dat | image | |
MD5:— | SHA256:— | |||
| 1952 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1952 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_RssRule_2_FEC6987CA125A1429FD5FB83532D4BDE.dat | xml | |
MD5:D8B37ED0410FB241C283F72B76987F18 | SHA256:31E68049F6B7F21511E70CD7F2D95B9CF1354CF54603E8F47C1FC40F40B7A114 | |||
| 1952 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_WorkHours_1_433D584C0F19AD48A4223F73BA820563.dat | xml | |
MD5:807EF0FC900FEB3DA82927990083D6E7 | SHA256:4411E7DC978011222764943081500FFF0E43CBF7CCD44264BD1AB6306CA68913 | |||
| 3300 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\3GNXYIF1\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
| 1952 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_7EF60ABDD1002D48ADCE4337D5EBFDED.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
12
DNS requests
4
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1952 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
328 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1952 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
— | — | 5.206.225.48:443 | mmjzubbbvhfbc.ml | Dotsi, Unipessoal Lda. | NL | suspicious |
3300 | iexplore.exe | 5.206.225.48:443 | mmjzubbbvhfbc.ml | Dotsi, Unipessoal Lda. | NL | suspicious |
— | — | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1524 | iexplore.exe | 5.206.225.48:443 | mmjzubbbvhfbc.ml | Dotsi, Unipessoal Lda. | NL | suspicious |
328 | iexplore.exe | 5.206.225.48:443 | mmjzubbbvhfbc.ml | Dotsi, Unipessoal Lda. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
mmjzubbbvhfbc.ml |
| suspicious |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ml Domain |
3300 | iexplore.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.ml) in TLS SNI |
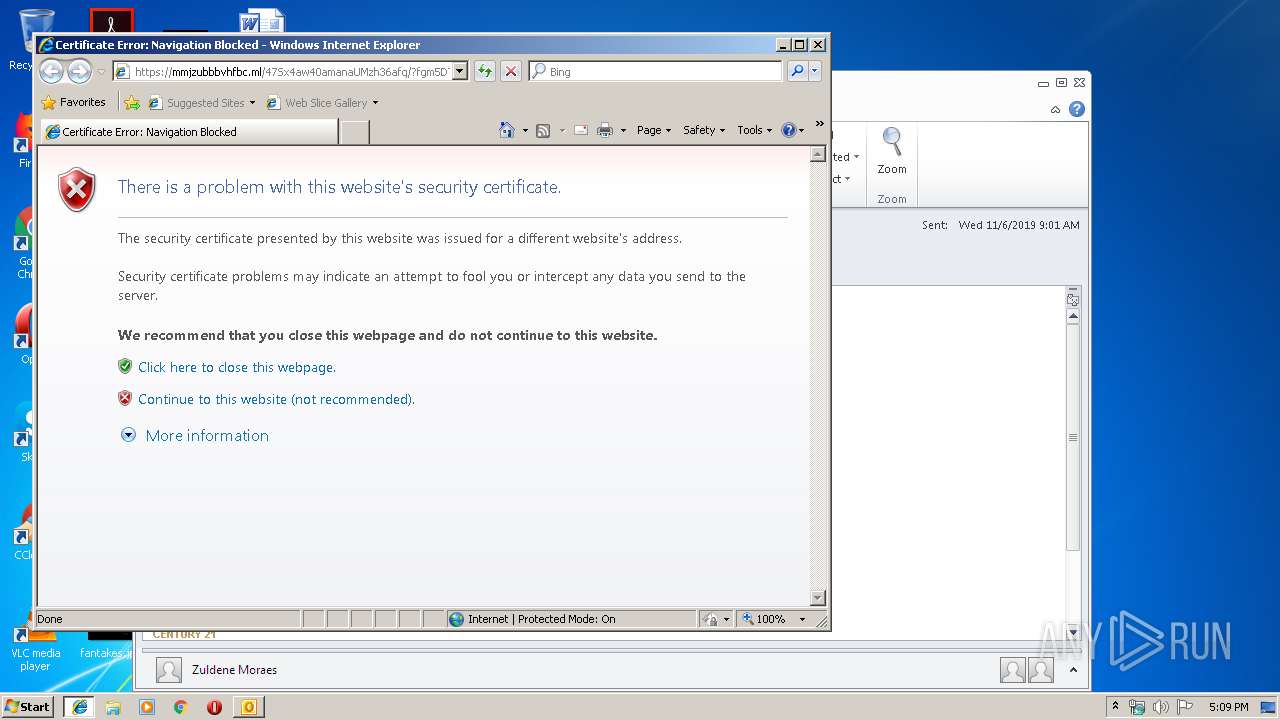
3300 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |
328 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |
1524 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.ga) |