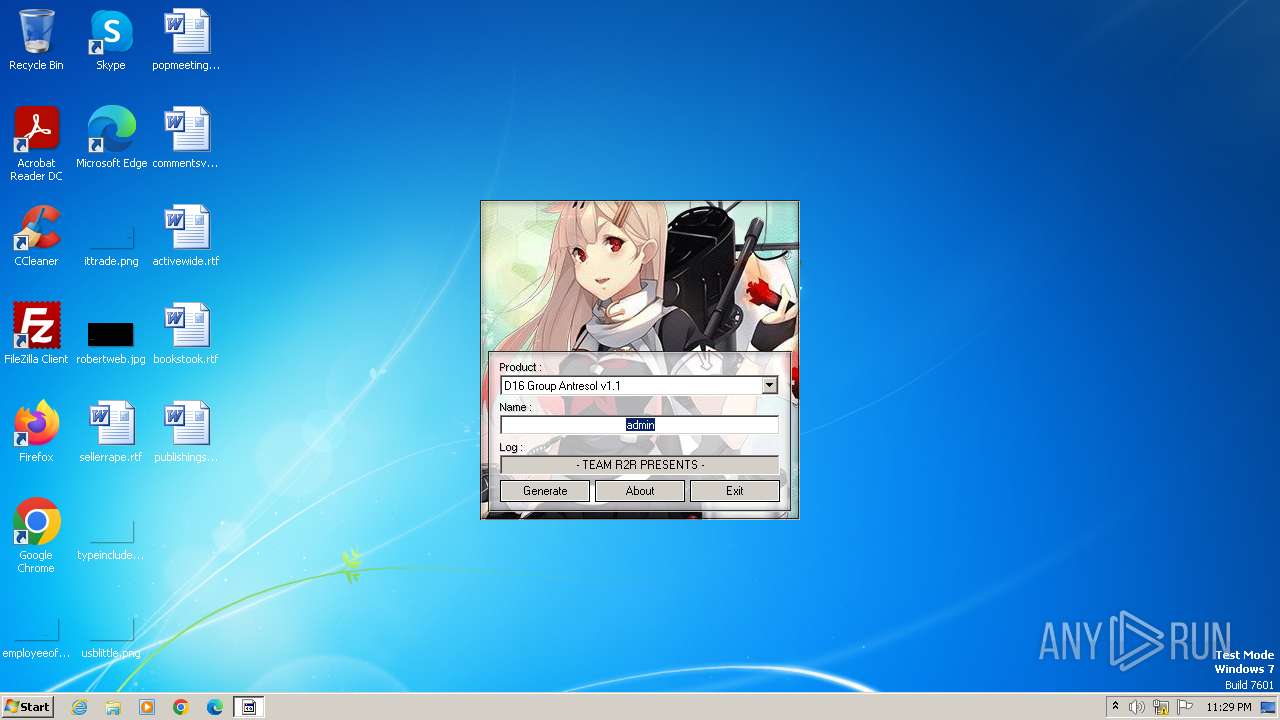
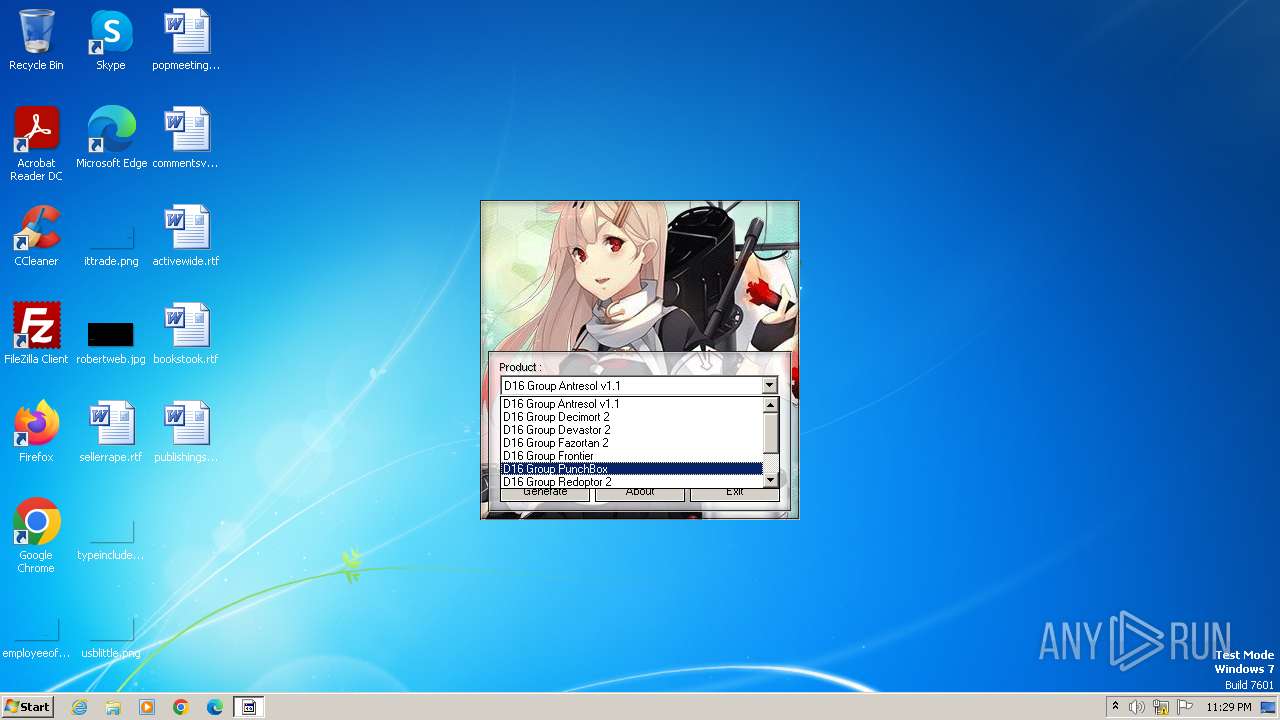
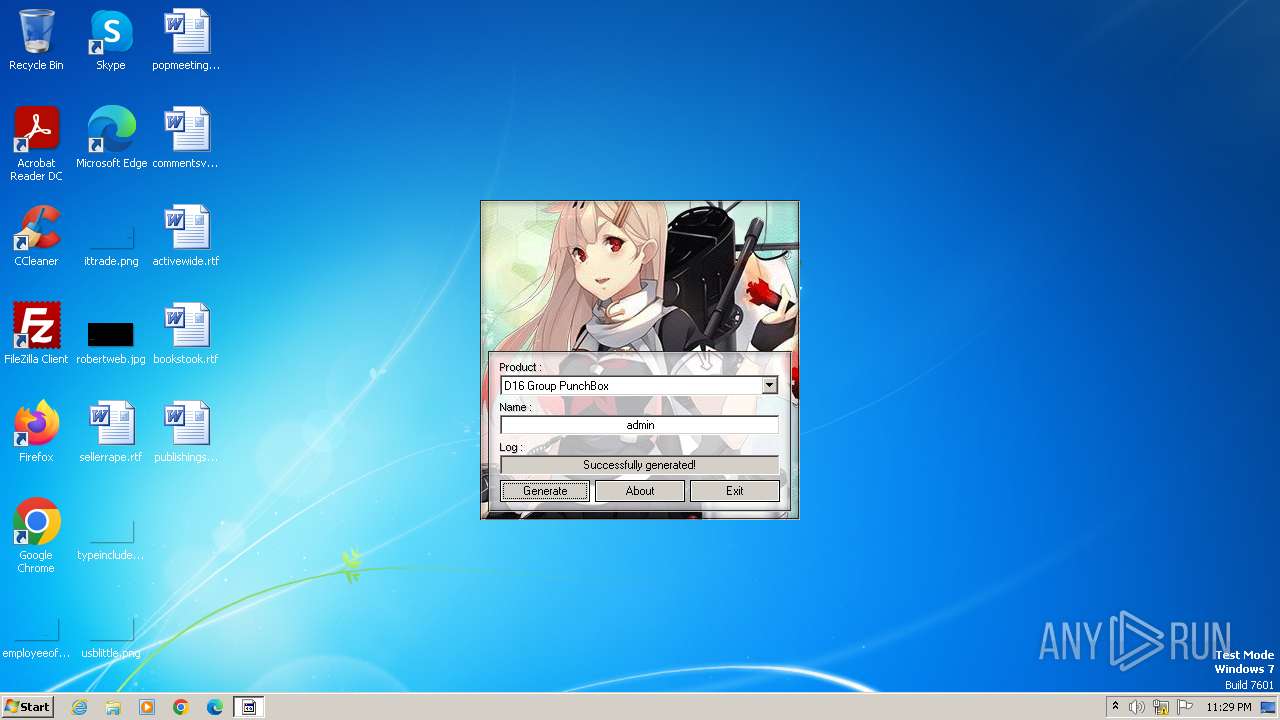
| File name: | D16_RSA_KeyGen.exe |
| Full analysis: | https://app.any.run/tasks/08c51a4e-cb1c-4c83-9d3f-9d987e989734 |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2023, 23:29:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 8814584A2304AB3A9716668DC09B3E92 |
| SHA1: | 00C4A98395263AC4166457A7451D1A5E3051D1A1 |
| SHA256: | FD12A9314D220ACCADEF562A7903EBA24751B02E2773CCFE2D105A5853C91251 |
| SSDEEP: | 24576:G03sUkCKxdhKfeubWjlXAEgfoAfL0TSJYy9E:G03sUkCQdhKfeuSZXAEgfoAz0TSJYy9E |
MALICIOUS
Drops the executable file immediately after the start
- D16_RSA_KeyGen.exe (PID: 3564)
SUSPICIOUS
Reads the Internet Settings
- keygen.exe (PID: 3420)
INFO
Reads the computer name
- D16_RSA_KeyGen.exe (PID: 3564)
- keygen.exe (PID: 3420)
Checks supported languages
- keygen.exe (PID: 3420)
- D16_RSA_KeyGen.exe (PID: 3564)
Reads the machine GUID from the registry
- keygen.exe (PID: 3420)
Create files in a temporary directory
- D16_RSA_KeyGen.exe (PID: 3564)
- keygen.exe (PID: 3420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:30 04:57:38+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25088 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x3328 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
42
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3420 | C:\Users\admin\AppData\Local\Temp\keygen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | — | D16_RSA_KeyGen.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225547 Modules
| |||||||||||||||
| 3456 | "C:\Users\admin\AppData\Local\Temp\D16_RSA_KeyGen.exe" | C:\Users\admin\AppData\Local\Temp\D16_RSA_KeyGen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3564 | "C:\Users\admin\AppData\Local\Temp\D16_RSA_KeyGen.exe" | C:\Users\admin\AppData\Local\Temp\D16_RSA_KeyGen.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2 192
Read events
2 131
Write events
56
Delete events
5
Modification events
| (PID) Process: | (3420) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3420) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000020000000700000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3420) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3420) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 6 | |||
| (PID) Process: | (3420) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 2 | |||
| (PID) Process: | (3420) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | FFlags |
Value: 1 | |||
| (PID) Process: | (3420) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | IconSize |
Value: 48 | |||
| (PID) Process: | (3420) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | ColInfo |
Value: 00000000000000000000000000000000FDDFDFFD100000000000000000000000040000001800000030F125B7EF471A10A5F102608C9EEBAC0A000000A000000030F125B7EF471A10A5F102608C9EEBAC0C00000050000000A66A63283D95D211B5D600C04FD918D00B0000007800000030F125B7EF471A10A5F102608C9EEBAC0E00000078000000 | |||
| (PID) Process: | (3420) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Sort |
Value: 000000000000000000000000000000000100000030F125B7EF471A10A5F102608C9EEBAC0A00000001000000 | |||
| (PID) Process: | (3420) keygen.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlg\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | GroupView |
Value: 0 | |||
Executable files
3
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3564 | D16_RSA_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\R2RJUCE.dll | executable | |
MD5:66D3DC009D5CFEB5157DDC08DC5443D0 | SHA256:B4A6CAB1DE8CDC2B704F0BCC34D51644D82ECDA4AA346DBA232CD7623786F3A9 | |||
| 3564 | D16_RSA_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\bgm.xm | binary | |
MD5:7210C7ECF074A6BA57E13C2E939A9B10 | SHA256:99FBACA2EBDD04C7503CB280D0841529F8A3F2B3E1F2DAE57624AA0A3220345D | |||
| 3564 | D16_RSA_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\BASSMOD.dll | executable | |
MD5:E4EC57E8508C5C4040383EBE6D367928 | SHA256:8AD9E47693E292F381DA42DDC13724A3063040E51C26F4CA8E1F8E2F1DDD547F | |||
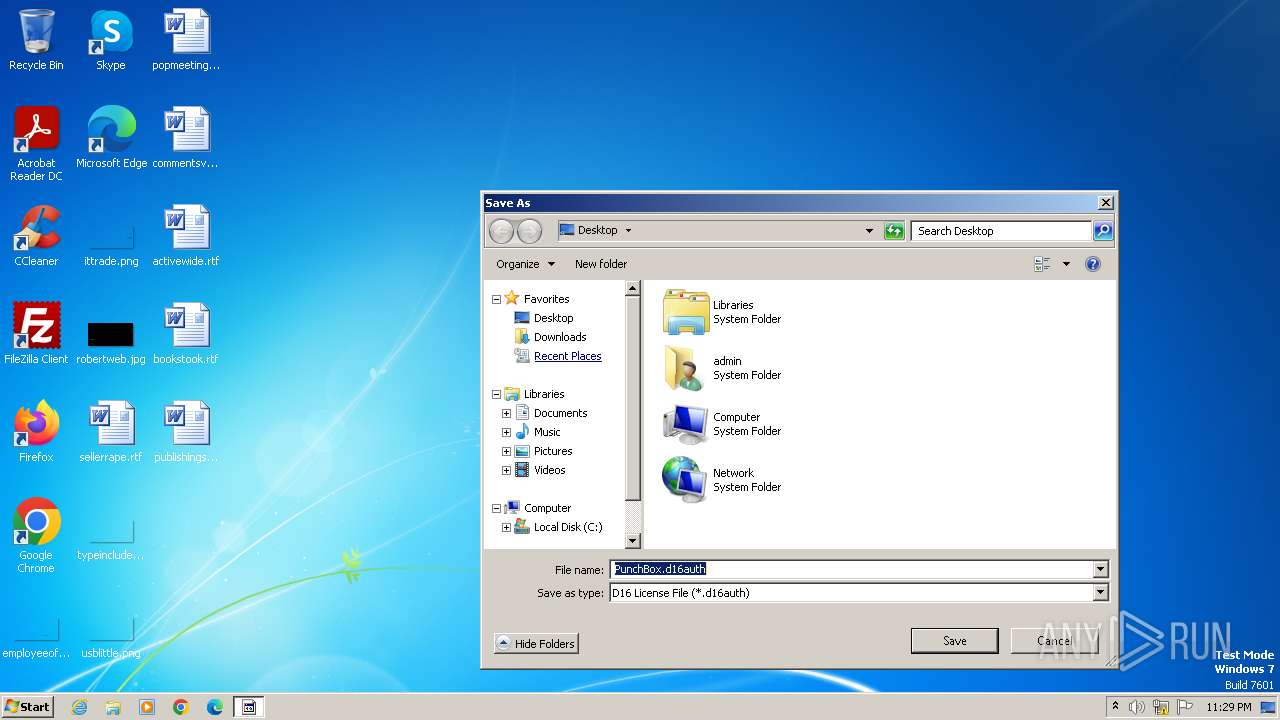
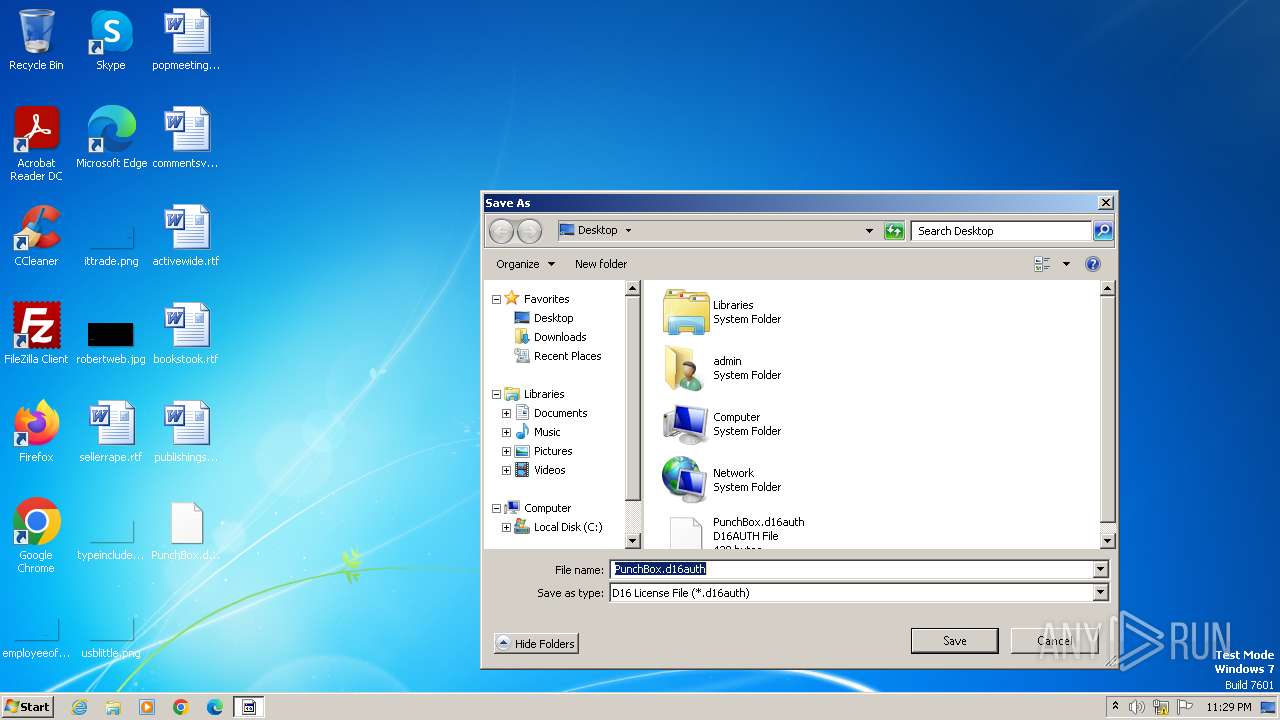
| 3420 | keygen.exe | C:\Users\admin\Desktop\PunchBox.d16auth | text | |
MD5:EEA80690FE7DD55E8D4FD530F5B81C6A | SHA256:15F6C88F08BB5B48F4A40EC4BE2B57396F0AF35DBA5146CB7CA2E35295D3D353 | |||
| 3564 | D16_RSA_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | executable | |
MD5:F9293900CBFF93F3B2E5D52758AF23E8 | SHA256:5291213BA91189C3B0A8F2A5E75988EF417F932CEC445C7D9785B7A26E44064B | |||
| 3420 | keygen.exe | C:\Users\admin\AppData\Local\Temp\~DFE96F48553F0A2A4D.TMP | binary | |
MD5:7452270995B975C9E350547D6F6CC557 | SHA256:B325D397AF40D651666E0BCCC79B2E477EC5F1C0A788B9136A187F63B6F5F5F1 | |||
| 3564 | D16_RSA_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\nsh6EFC.tmp | binary | |
MD5:4E41F6094D14B17F4A67518C0A566C4A | SHA256:49F762F3A635F986DC2066B352044B1D9397BBD0CC4169E16BAE936FCC28DE51 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |