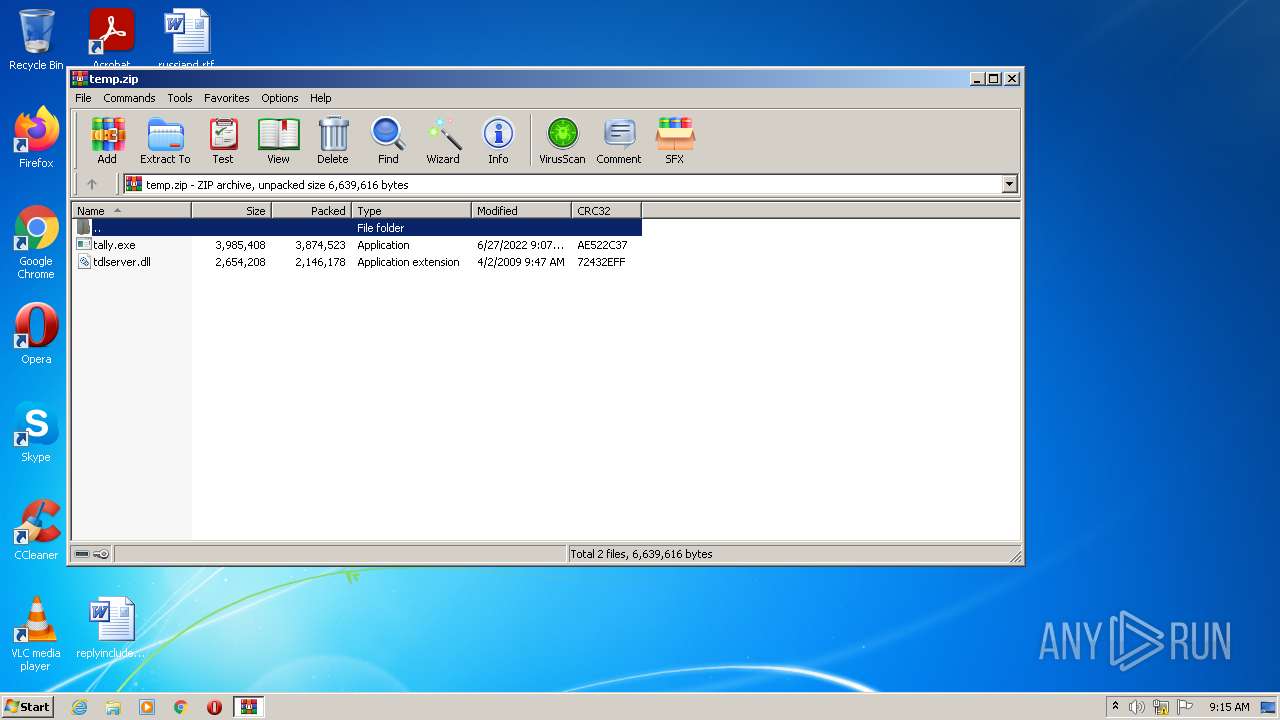
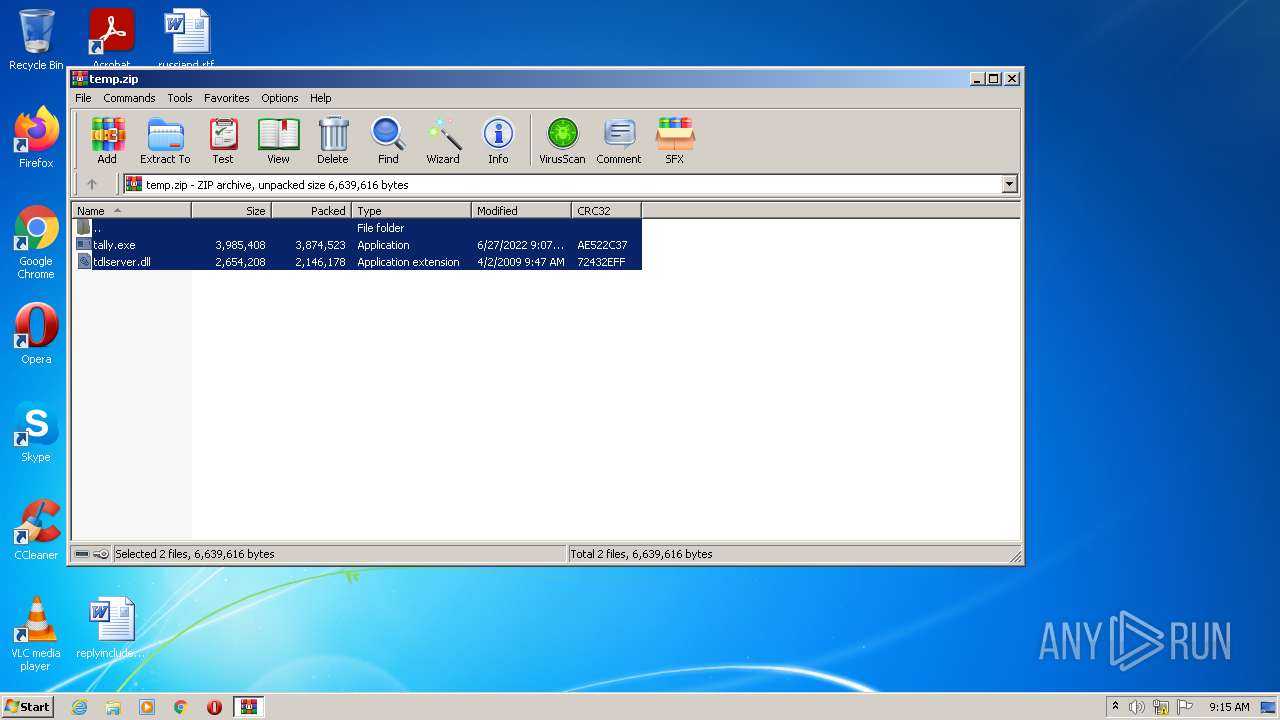
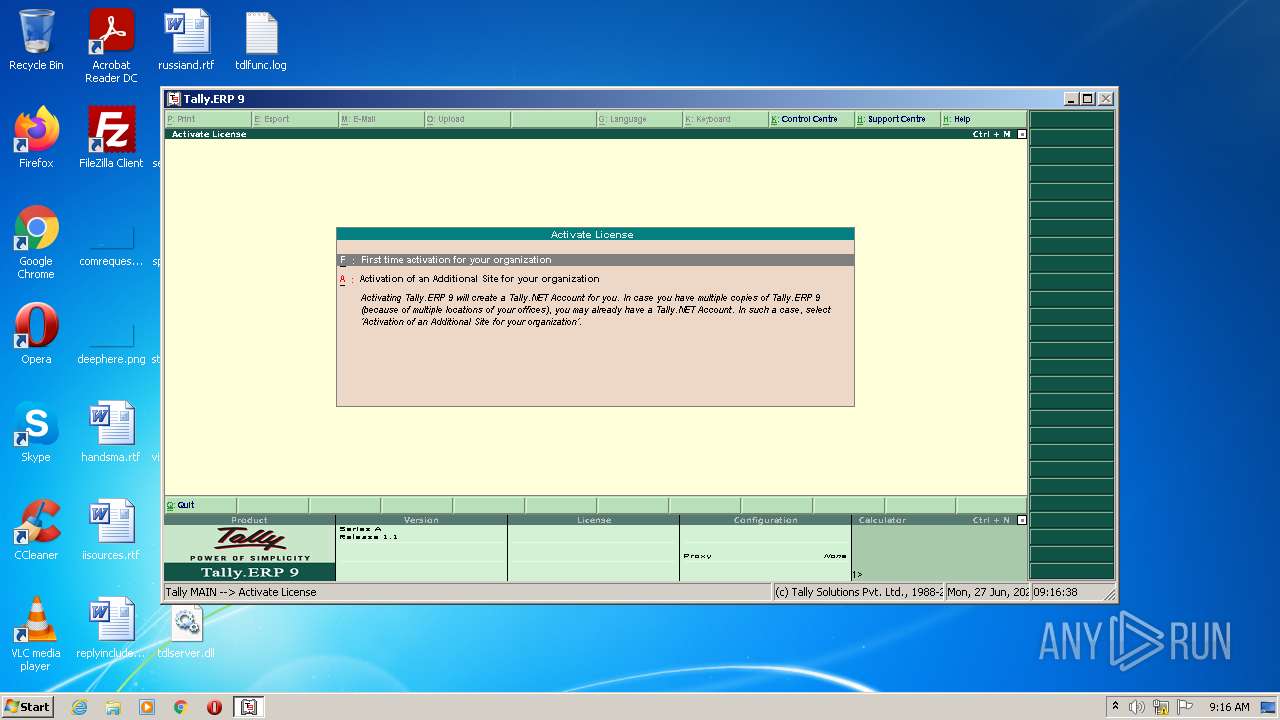
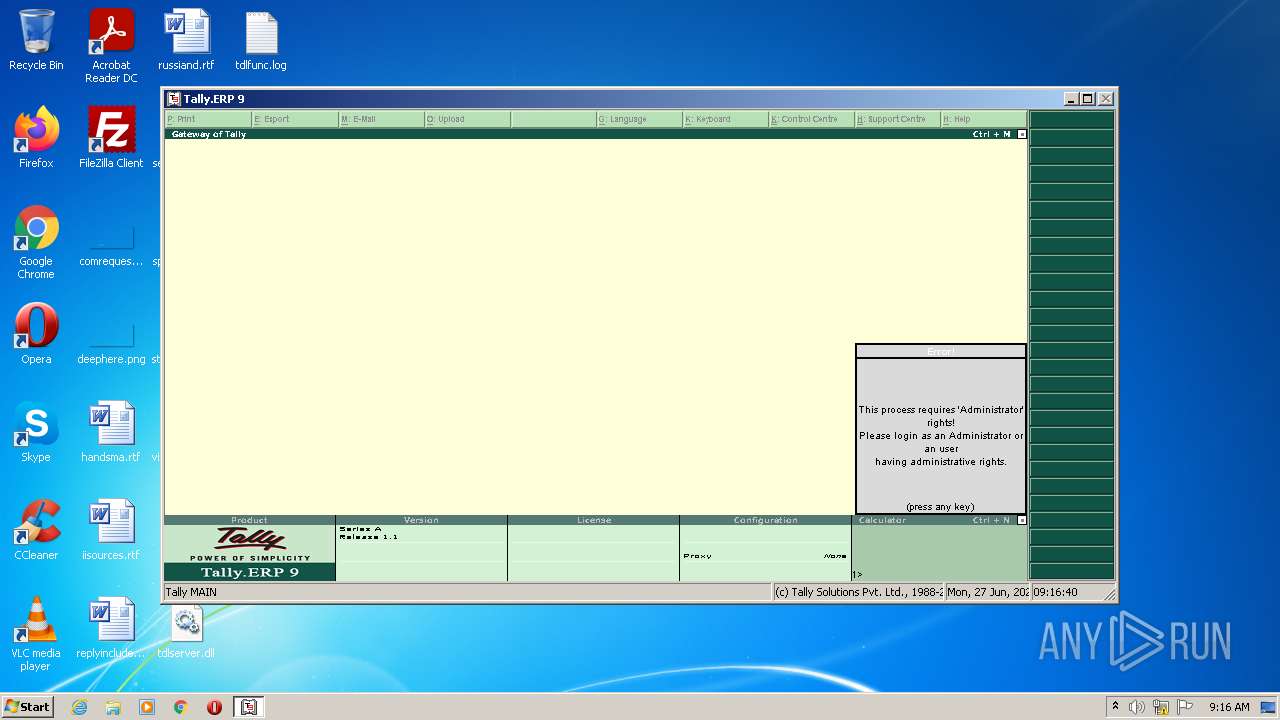
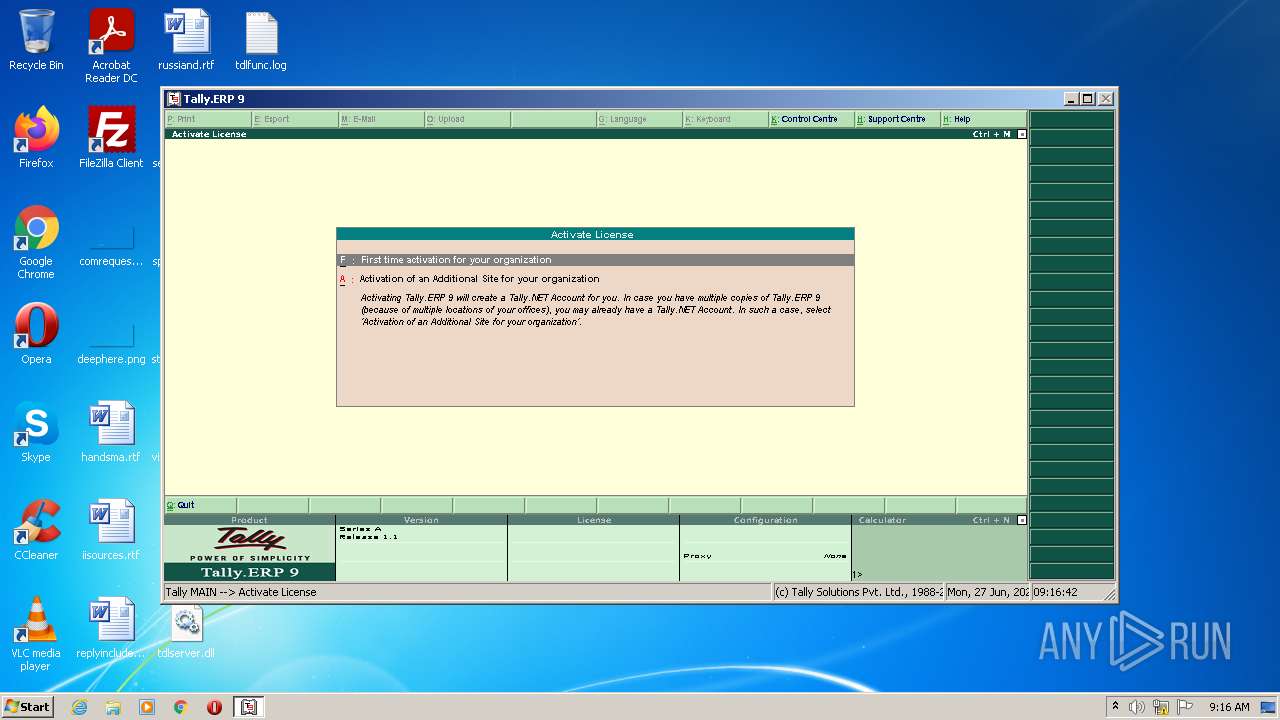
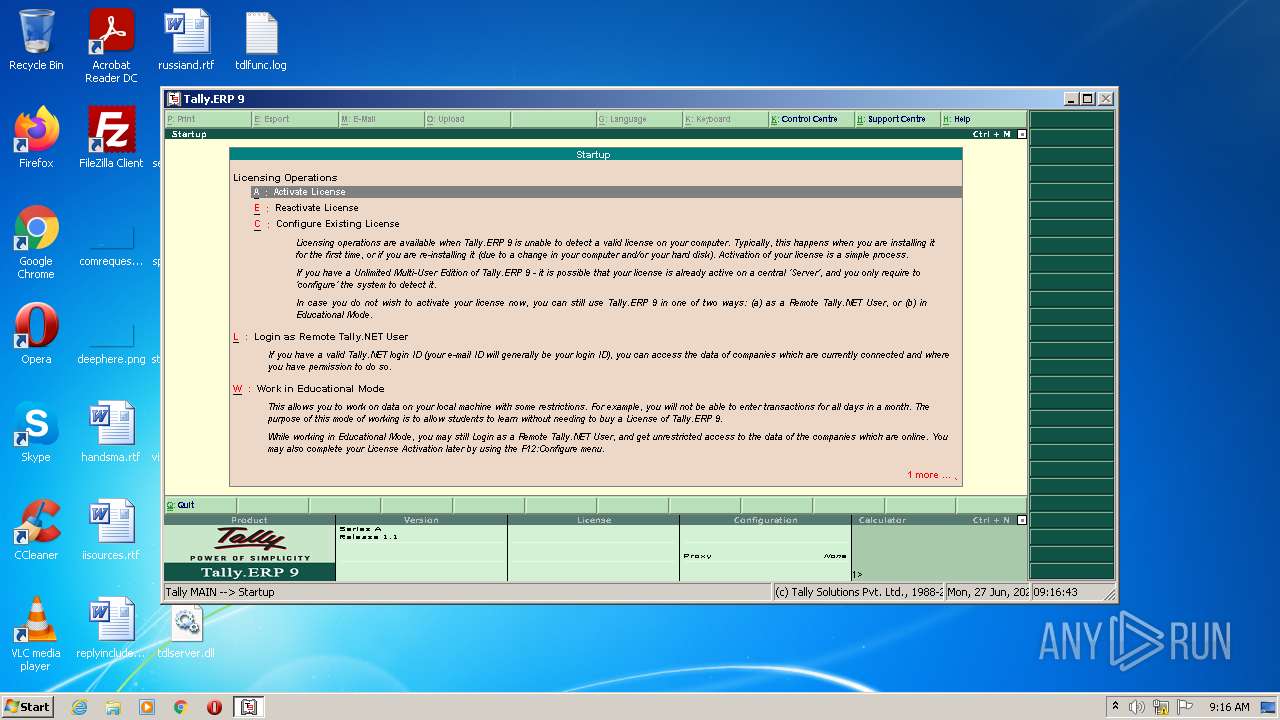
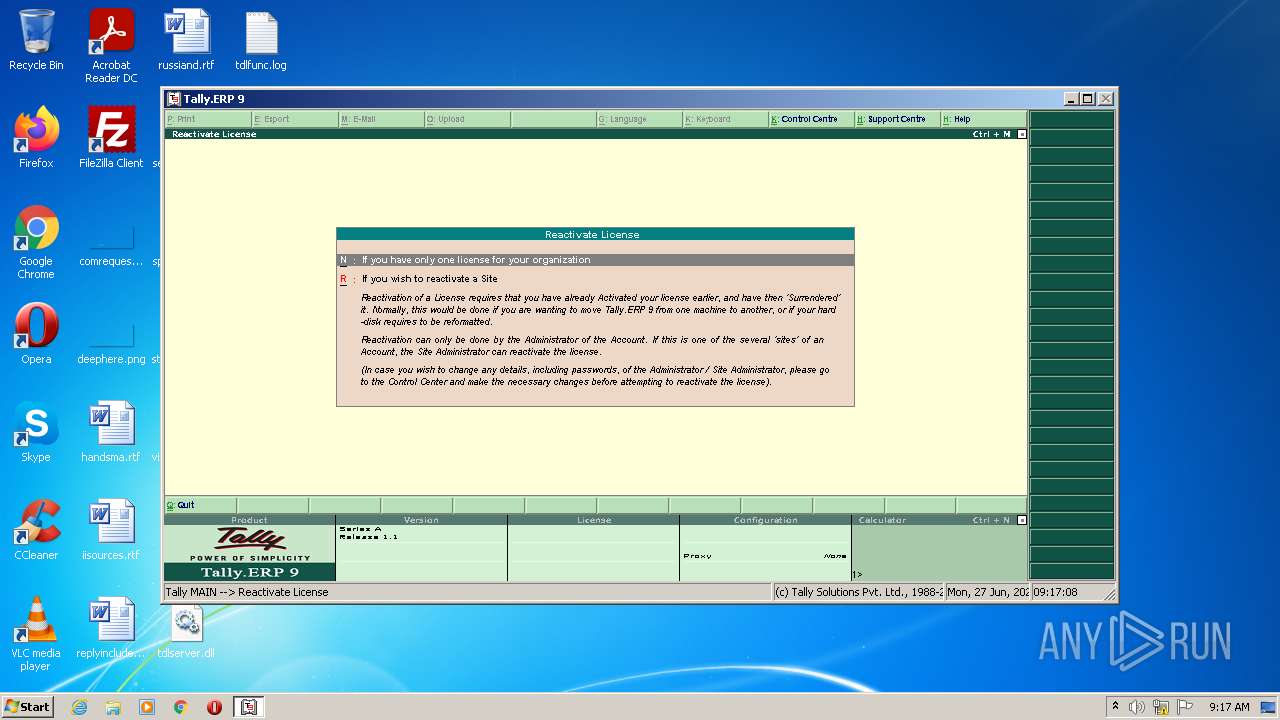
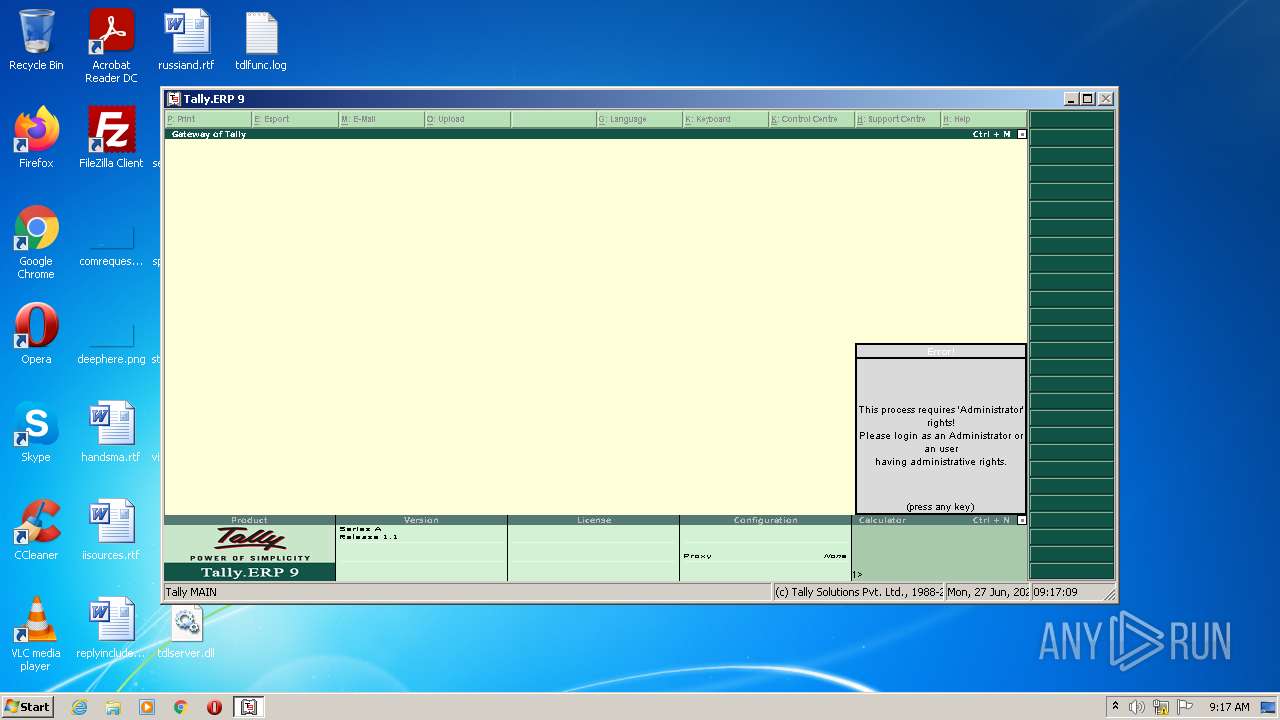
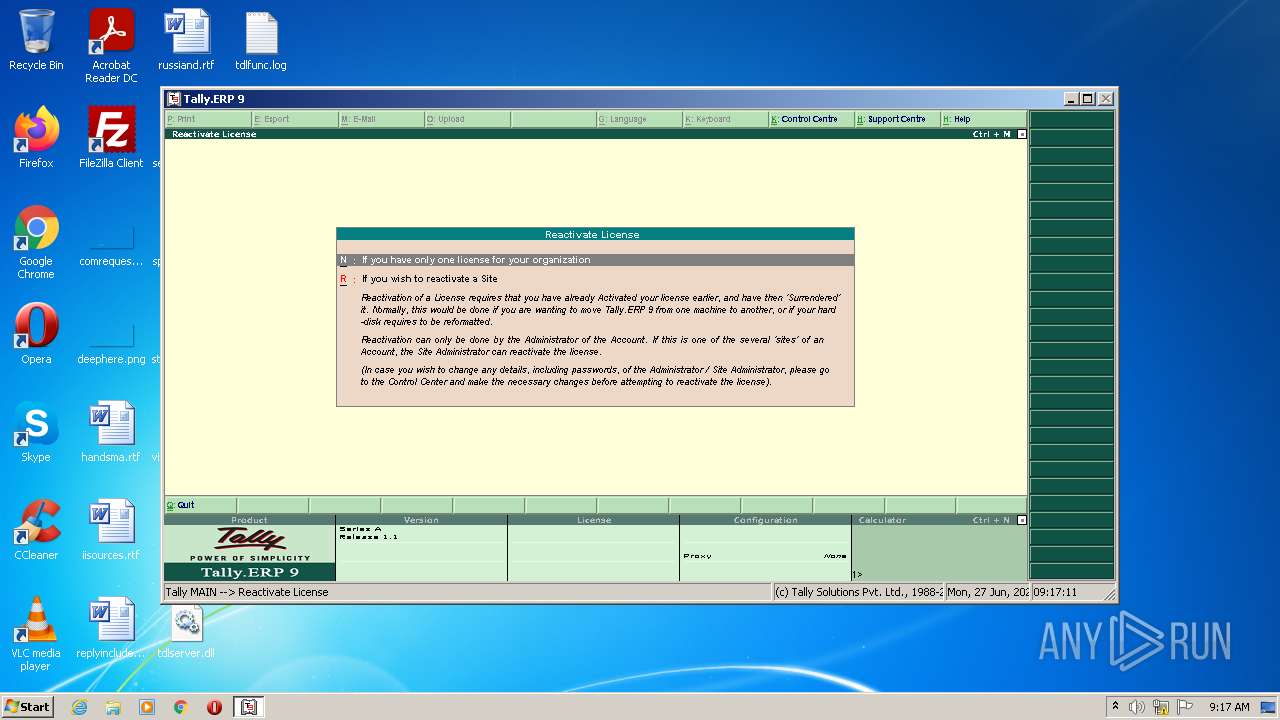
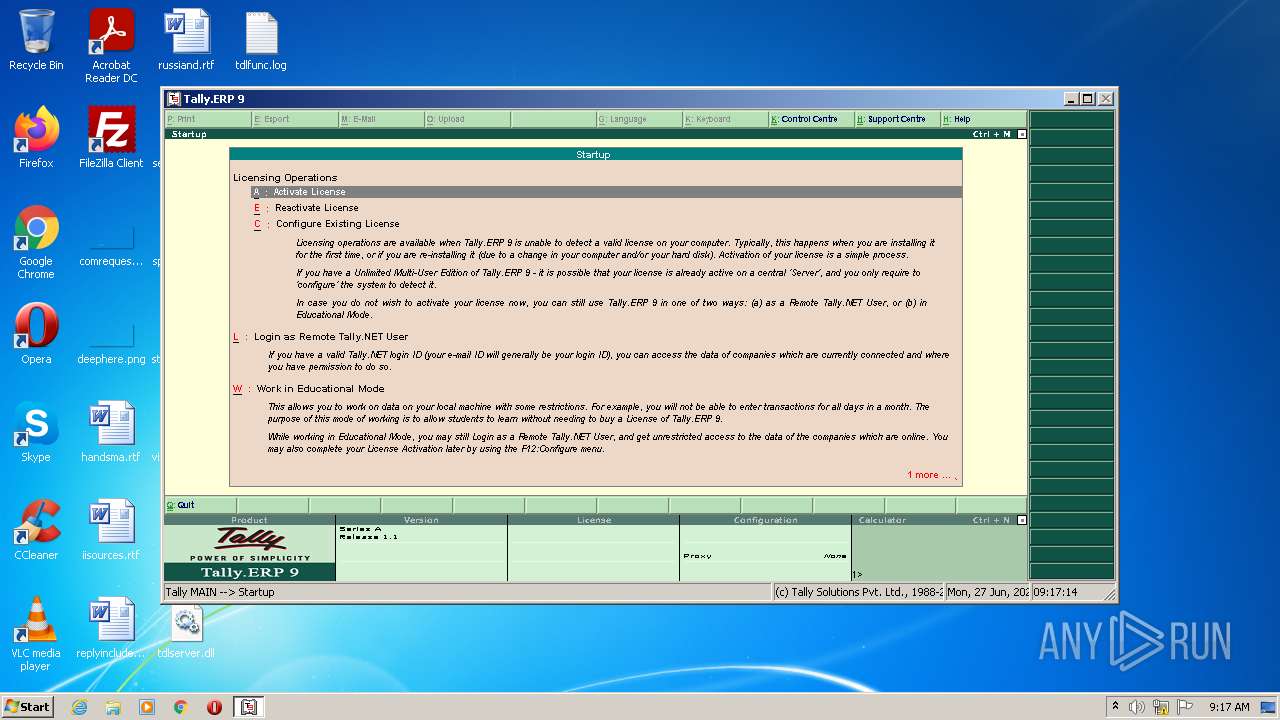
| File name: | temp.zip |
| Full analysis: | https://app.any.run/tasks/1b6edff5-f596-4f53-9473-93b59c938d5e |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 08:15:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 83195A6F21640194A50B43D652961D60 |
| SHA1: | 12B8D616FCB65823F8FB8B1FEBAD5023CCC80E7E |
| SHA256: | FCF98D06F11A92CF43621F9E0AE4F47706578E7F610B117F41E7D0221981700E |
| SSDEEP: | 98304:ikbifE3IB9pzqu287kI0mjKzFfj0T3QXc15pbiA3s5AMosKQp:NmcYpwBj0T31PpbiI5Qp |
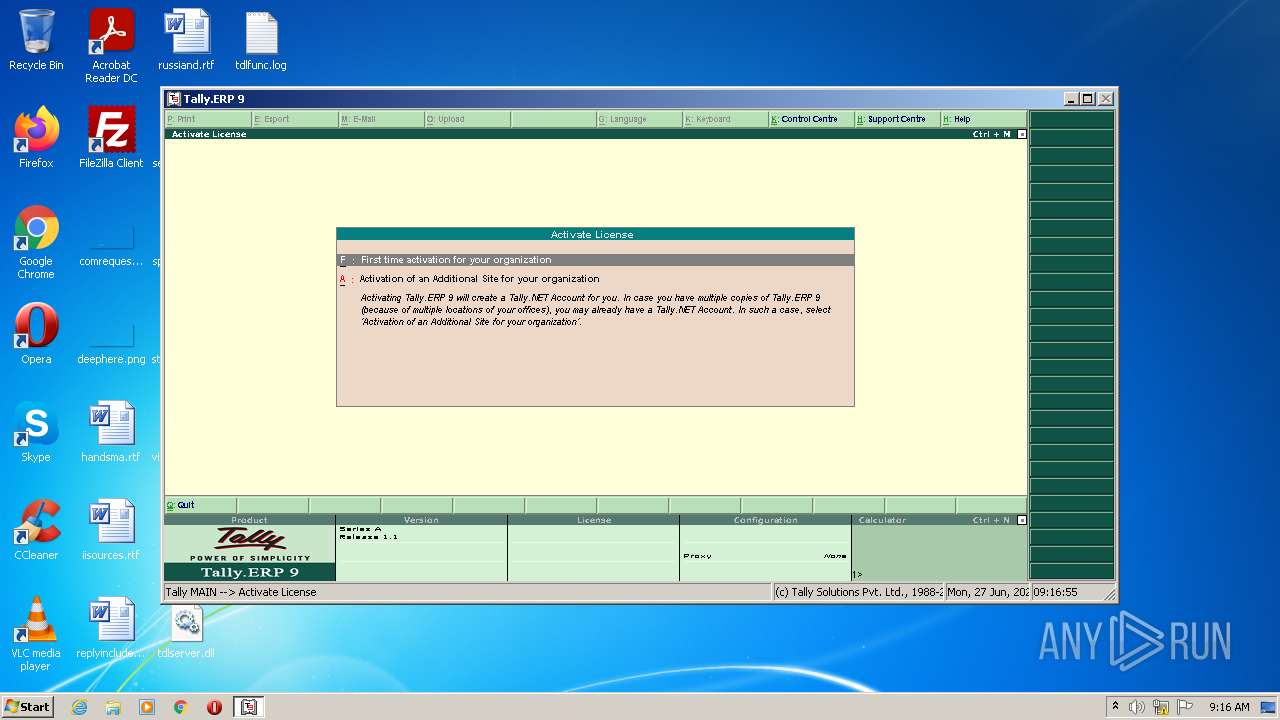
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2284)
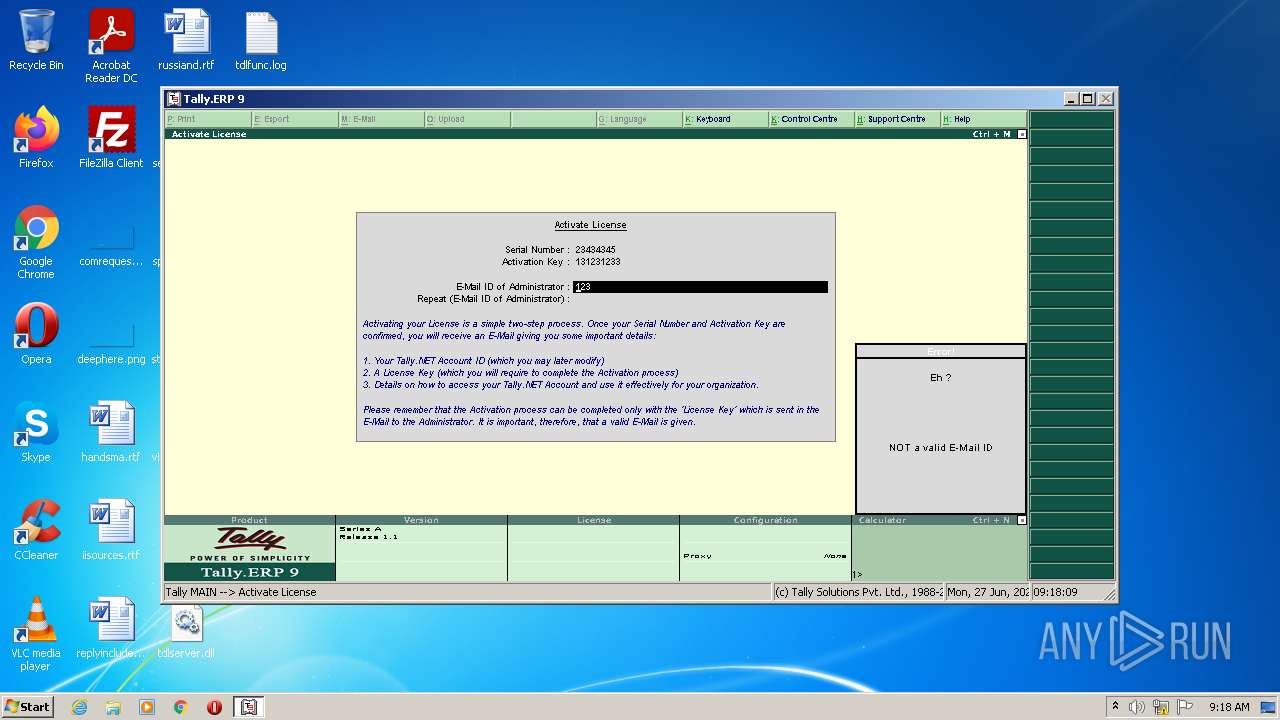
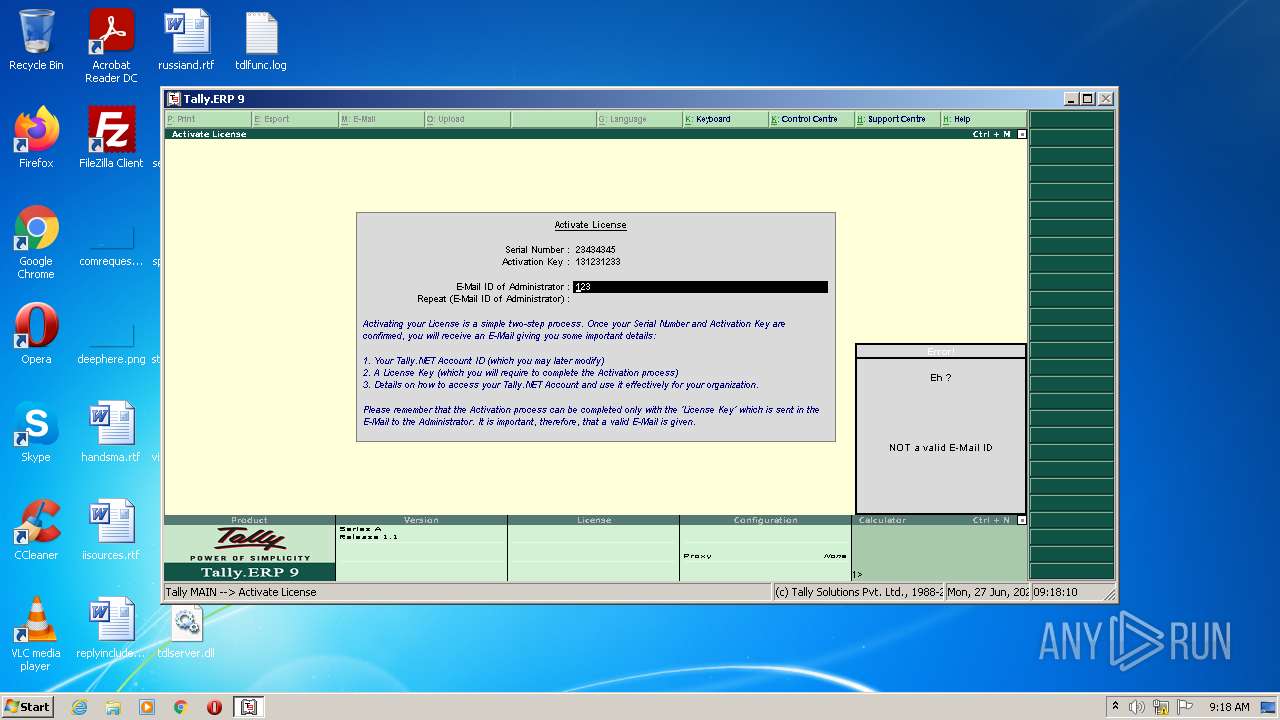
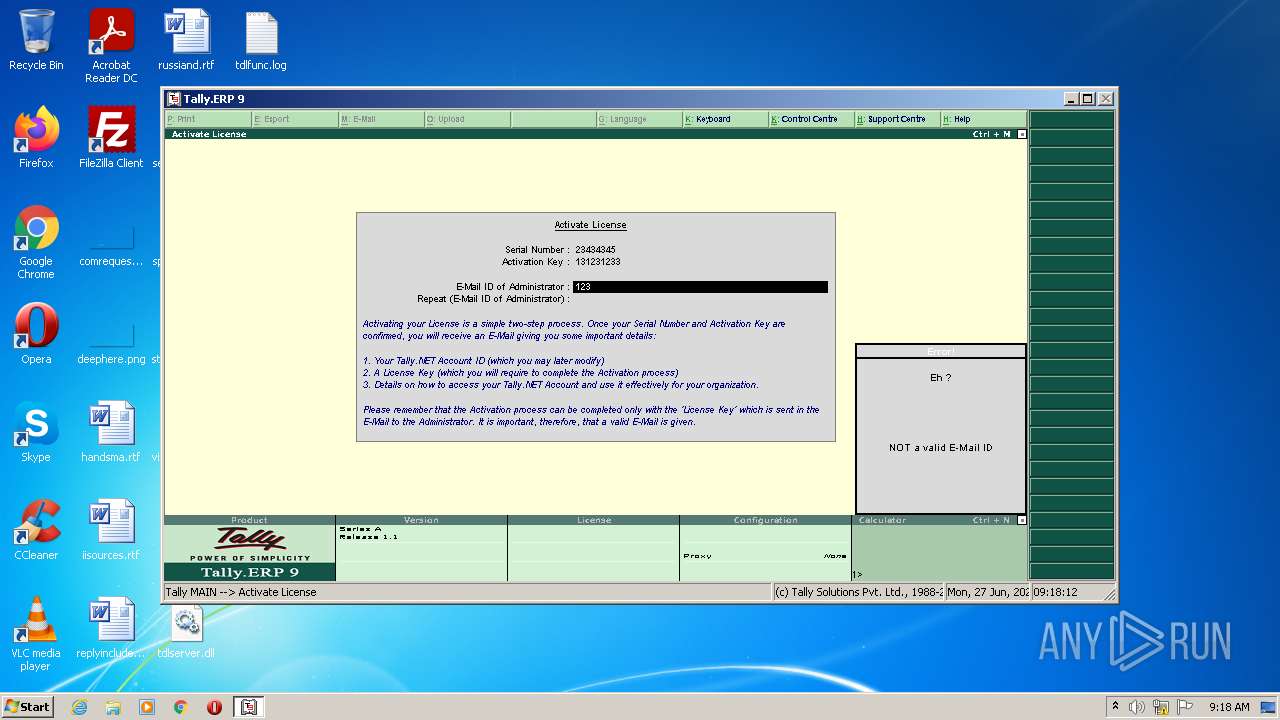
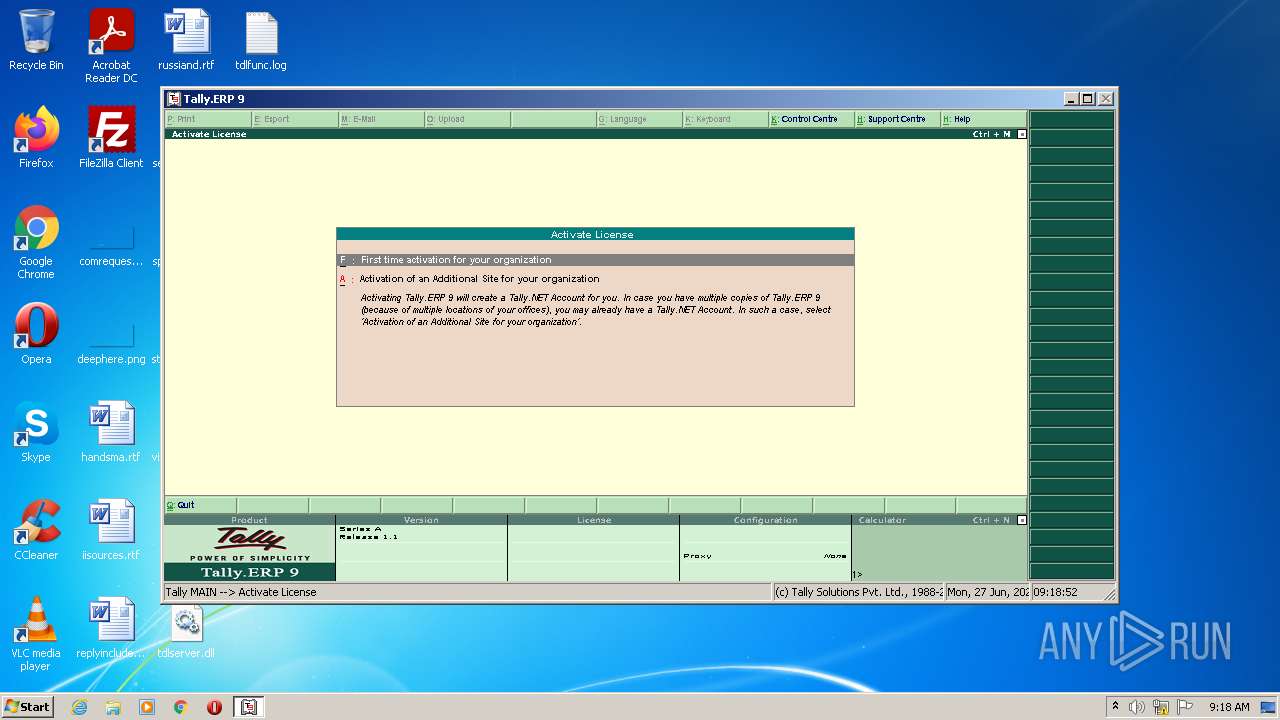
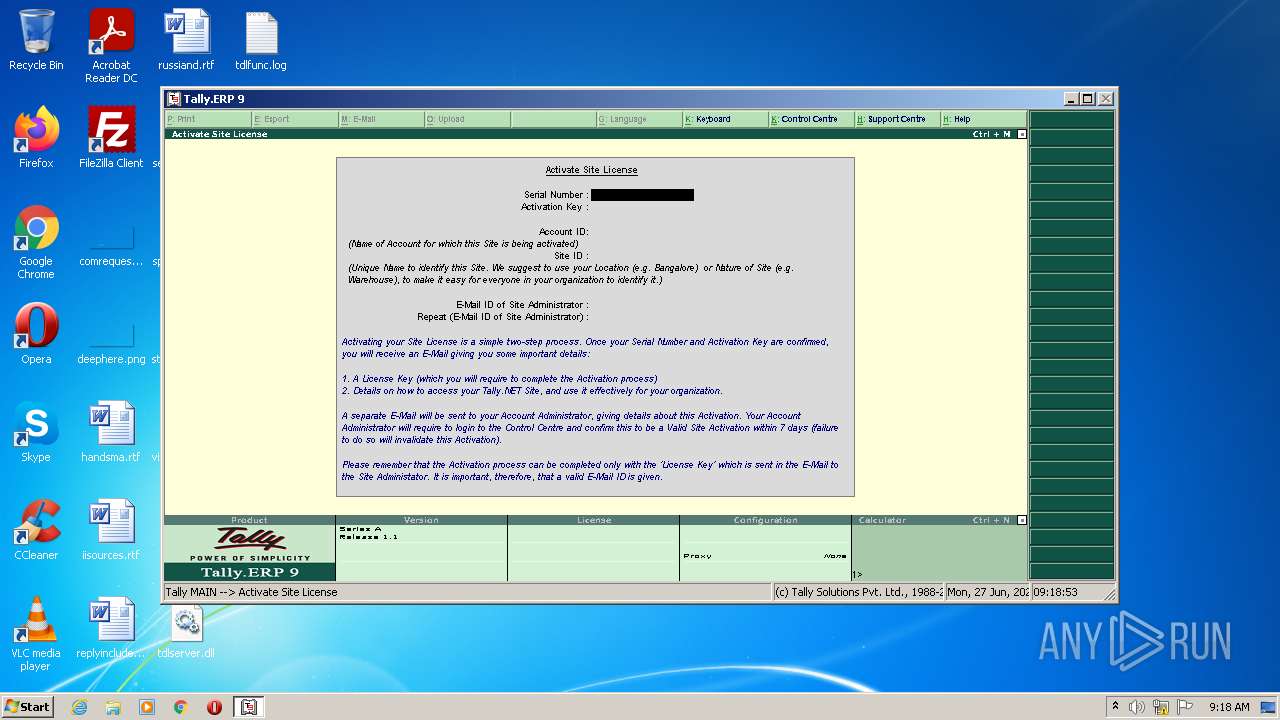
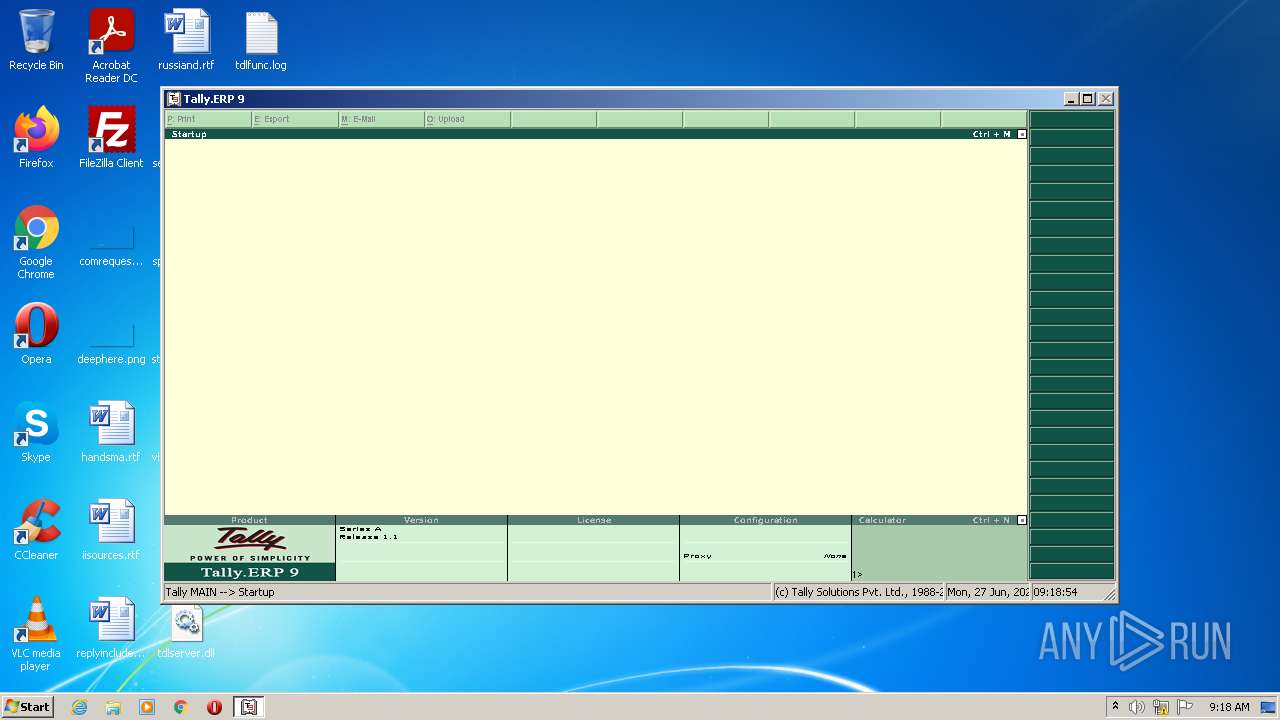
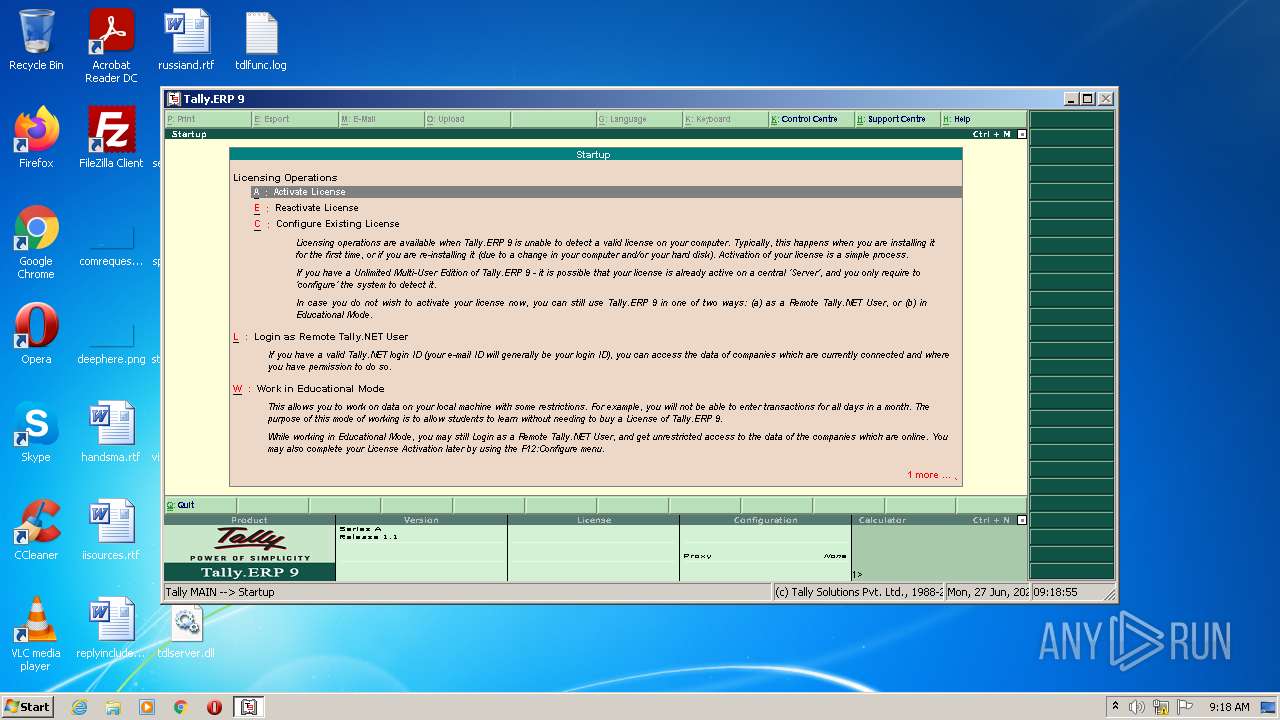
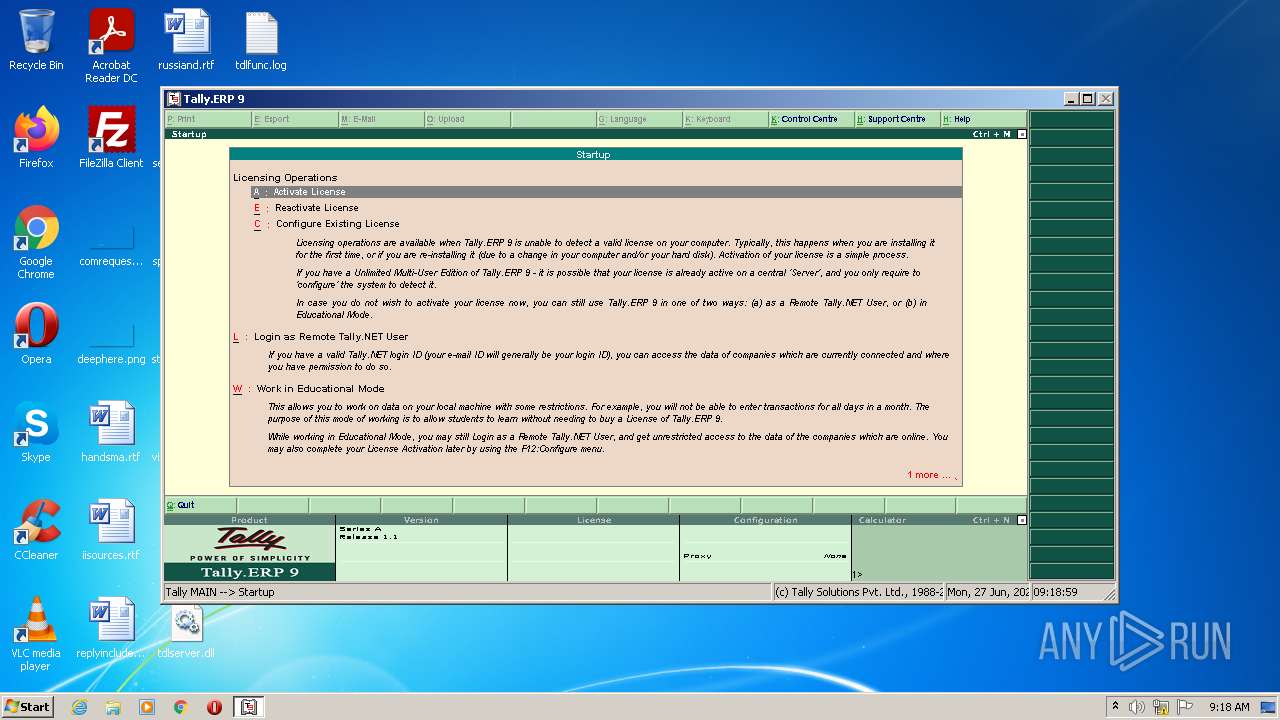
- tally.exe (PID: 2552)
- tally.exe (PID: 1036)
Application was dropped or rewritten from another process
- tally.exe (PID: 1036)
- tally.exe (PID: 2552)
Drops executable file immediately after starts
- WinRAR.exe (PID: 2984)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2984)
- tally.exe (PID: 2552)
- tally.exe (PID: 1036)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2984)
Reads the computer name
- WinRAR.exe (PID: 2984)
- tally.exe (PID: 2552)
- tally.exe (PID: 1036)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2984)
Reads Environment values
- tally.exe (PID: 2552)
- tally.exe (PID: 1036)
Reads Windows owner or organization settings
- tally.exe (PID: 2552)
- tally.exe (PID: 1036)
Reads Windows Product ID
- tally.exe (PID: 2552)
- tally.exe (PID: 1036)
Reads CPU info
- tally.exe (PID: 2552)
- tally.exe (PID: 1036)
Reads the Windows organization settings
- tally.exe (PID: 1036)
- tally.exe (PID: 2552)
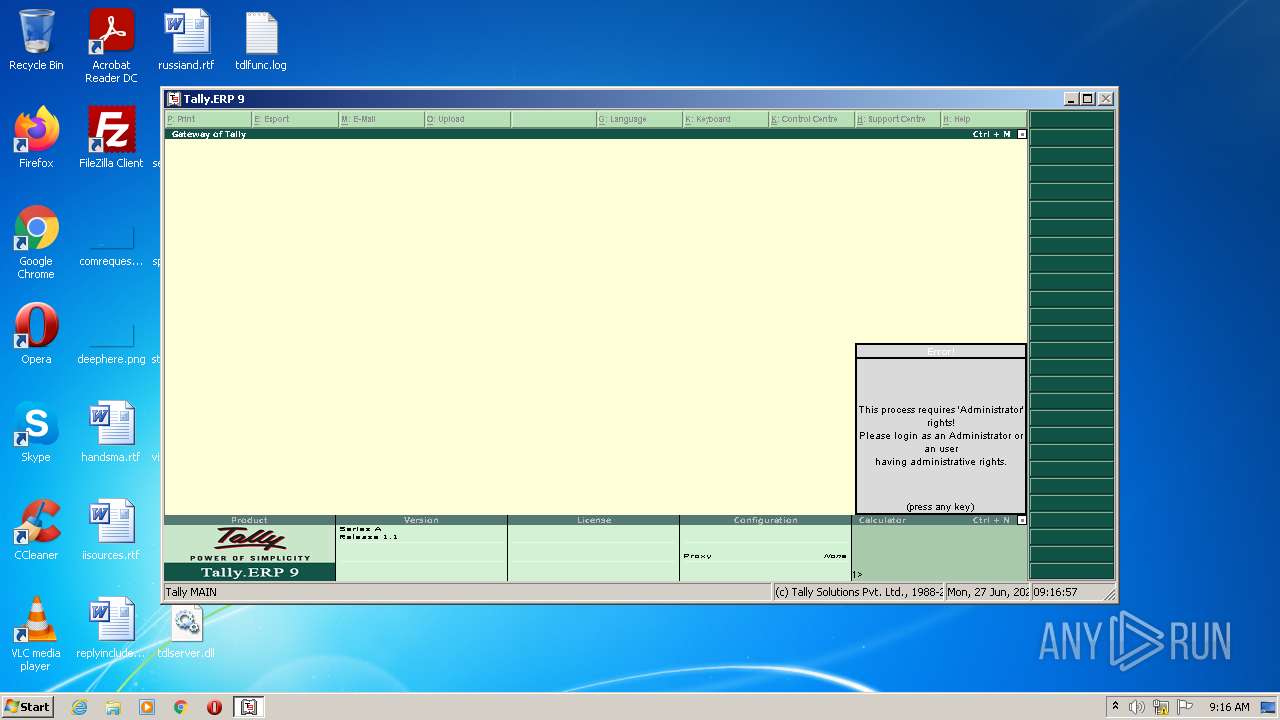
Removes files from Windows directory
- tally.exe (PID: 1036)
Creates files in the Windows directory
- tally.exe (PID: 1036)
INFO
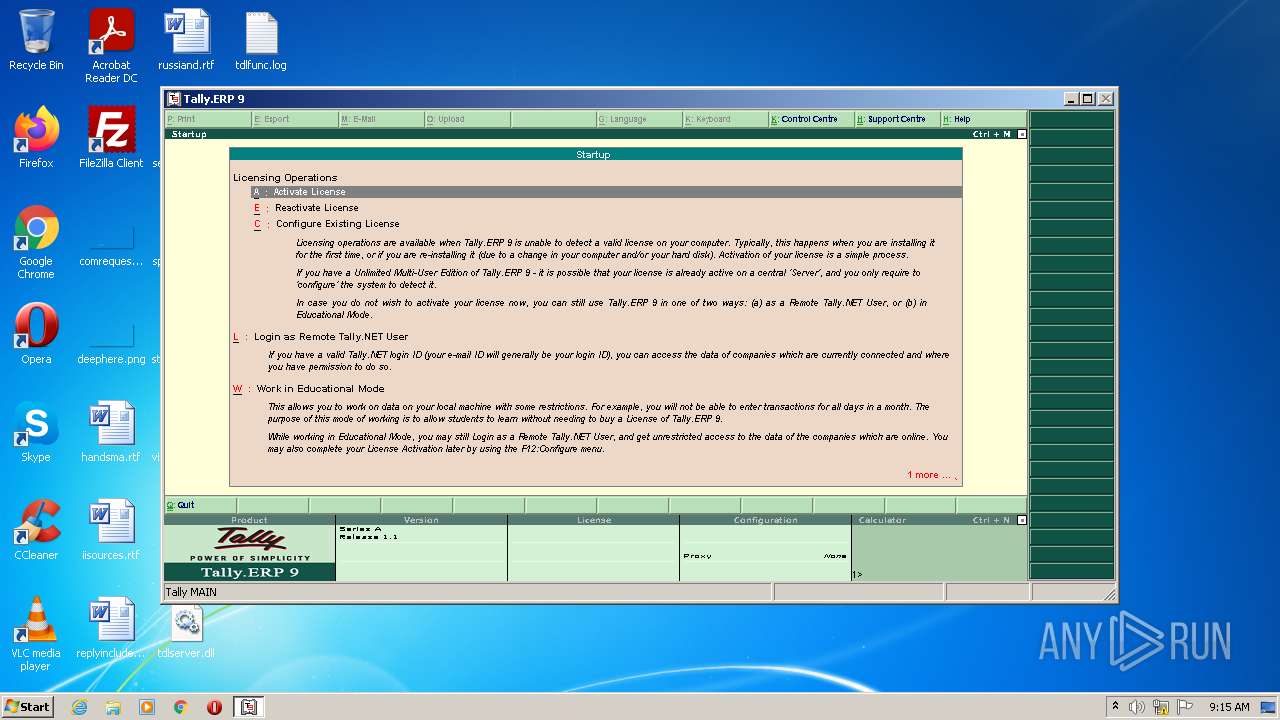
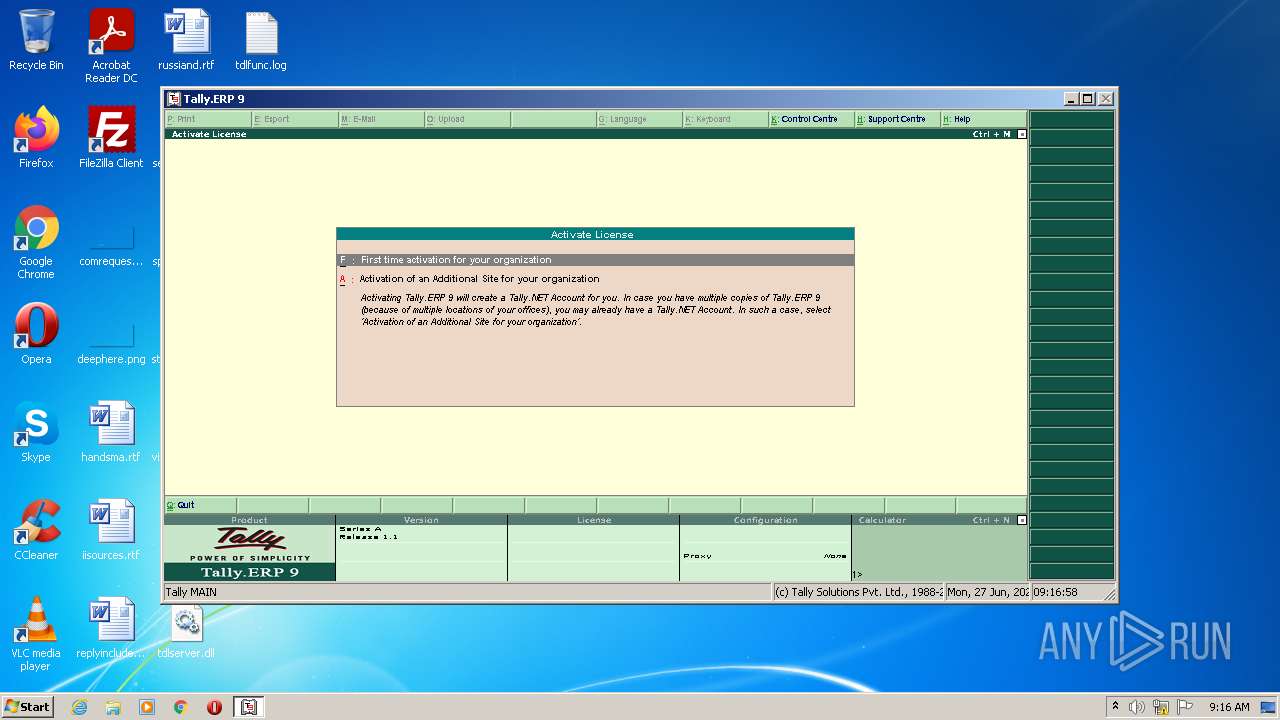
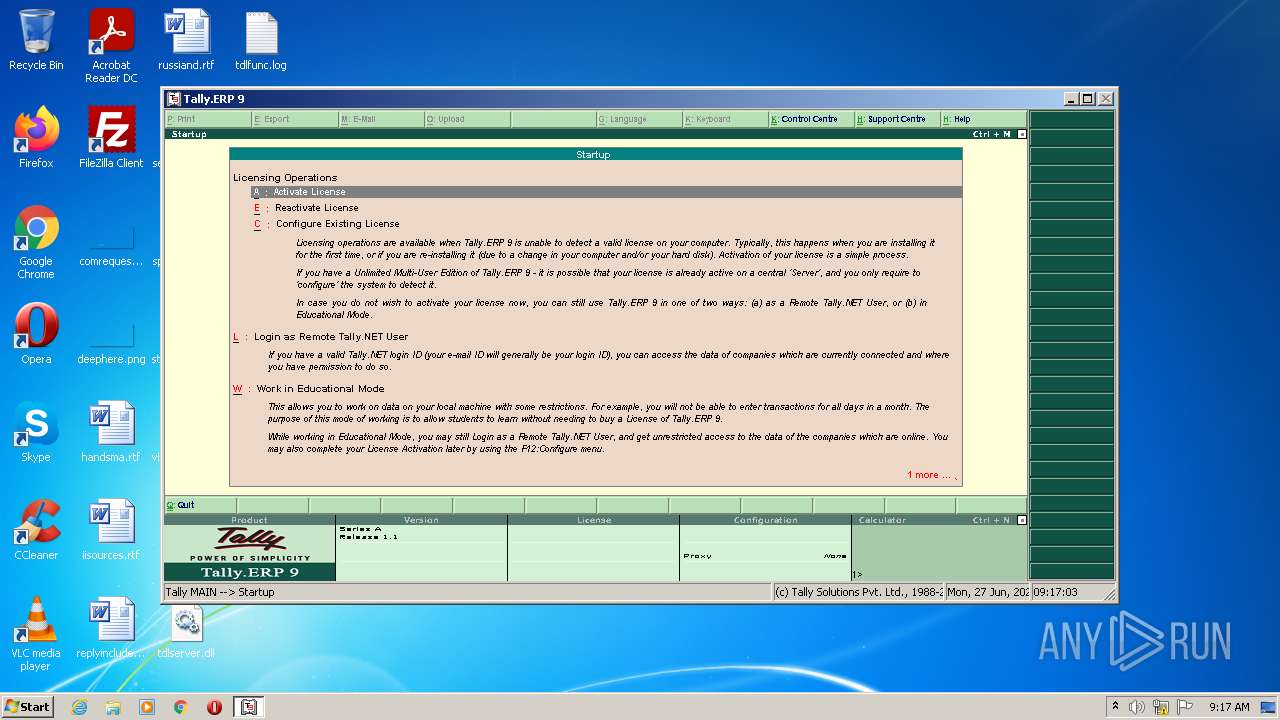
Manual execution by user
- tally.exe (PID: 2552)
- tally.exe (PID: 1036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | tally.exe |
|---|---|
| ZipUncompressedSize: | 3985408 |
| ZipCompressedSize: | 3874523 |
| ZipCRC: | 0xae522c37 |
| ZipModifyDate: | 2022:06:27 13:37:17 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0008 |
| ZipRequiredVersion: | 20 |
Total processes
44
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | "C:\Users\admin\Desktop\tally.exe" | C:\Users\admin\Desktop\tally.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2284 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2552 | "C:\Users\admin\Desktop\tally.exe" | C:\Users\admin\Desktop\tally.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2984 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\temp.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 561
Read events
1 536
Write events
23
Delete events
2
Modification events
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\temp.zip | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2984 | WinRAR.exe | C:\Users\admin\Desktop\tdlserver.dll | executable | |
MD5:B50F39B6BBA7BC7263061CB1C3BE2C07 | SHA256:E072B9A7882D18E2DCA4AB60BA2C2BC84007F949F77D90E7A2FBEB7FBA21DC66 | |||
| 2552 | tally.exe | C:\Users\admin\Desktop\tallycfg.tsf | binary | |
MD5:— | SHA256:— | |||
| 1036 | tally.exe | C:\Windows\system.ini | binary | |
MD5:03375244B38BF39ECEE5C747522946C2 | SHA256:75DBCE8DEC27DD350841A4161130BF0797CF5F9A1F405E17EBDB30F897A79192 | |||
| 2552 | tally.exe | C:\Users\admin\Desktop\tally.ini | text | |
MD5:— | SHA256:— | |||
| 2552 | tally.exe | C:\Users\admin\Desktop\tally_chk.tsf | binary | |
MD5:8214D1003F68A7D9B0356C0CBD7EEE1A | SHA256:E61C21CA716B3B1AEFB7D1198F83679C4CA4D596E5792275DD6203B49216237D | |||
| 2552 | tally.exe | C:\Users\admin\Desktop\tdlfunc.log | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 1036 | tally.exe | C:\Users\admin\Desktop\tally_chk.tsf | binary | |
MD5:8214D1003F68A7D9B0356C0CBD7EEE1A | SHA256:E61C21CA716B3B1AEFB7D1198F83679C4CA4D596E5792275DD6203B49216237D | |||
| 2984 | WinRAR.exe | C:\Users\admin\Desktop\tally.exe | executable | |
MD5:D0C60FAE72EA3749F04B711B88230107 | SHA256:5FCF9C420BE4DB25D94B3159F2B1A03FED59A0BFC9BEA718D779DD9E69B6248E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
tally.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2007 Oreans Technologies ---
------------------------------------------------
|
tally.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2007 Oreans Technologies ---
------------------------------------------------
|