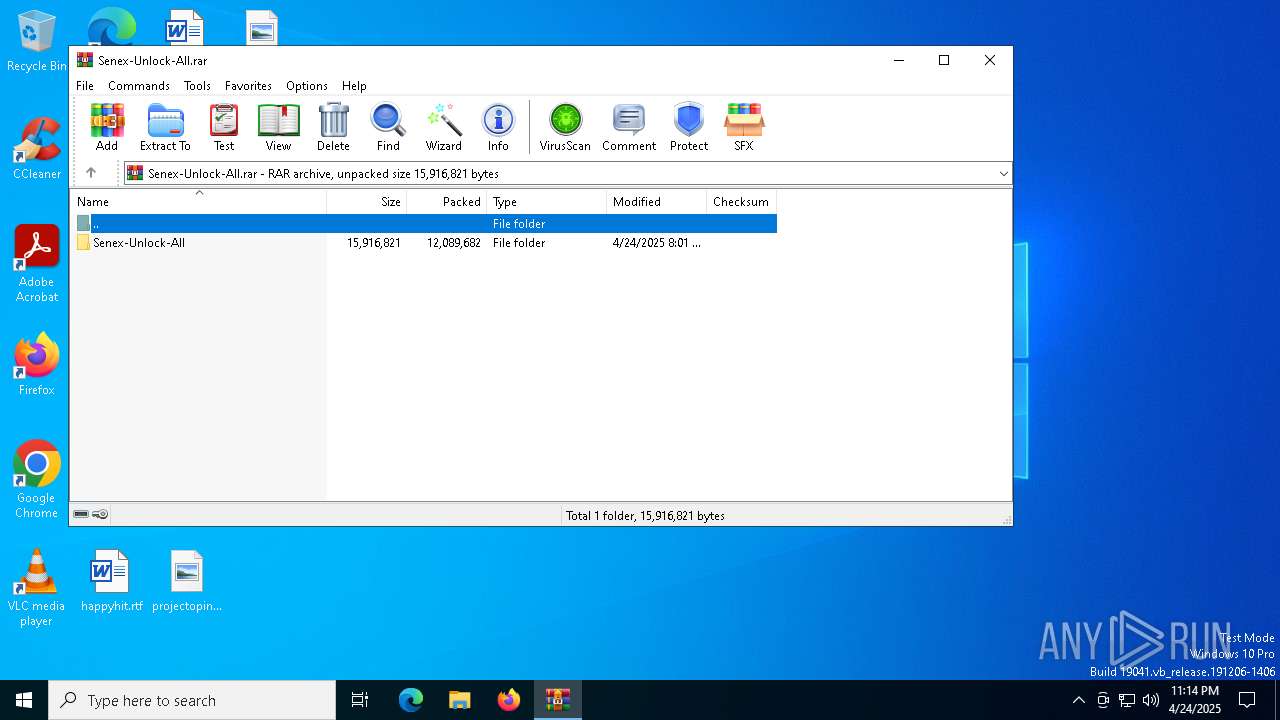
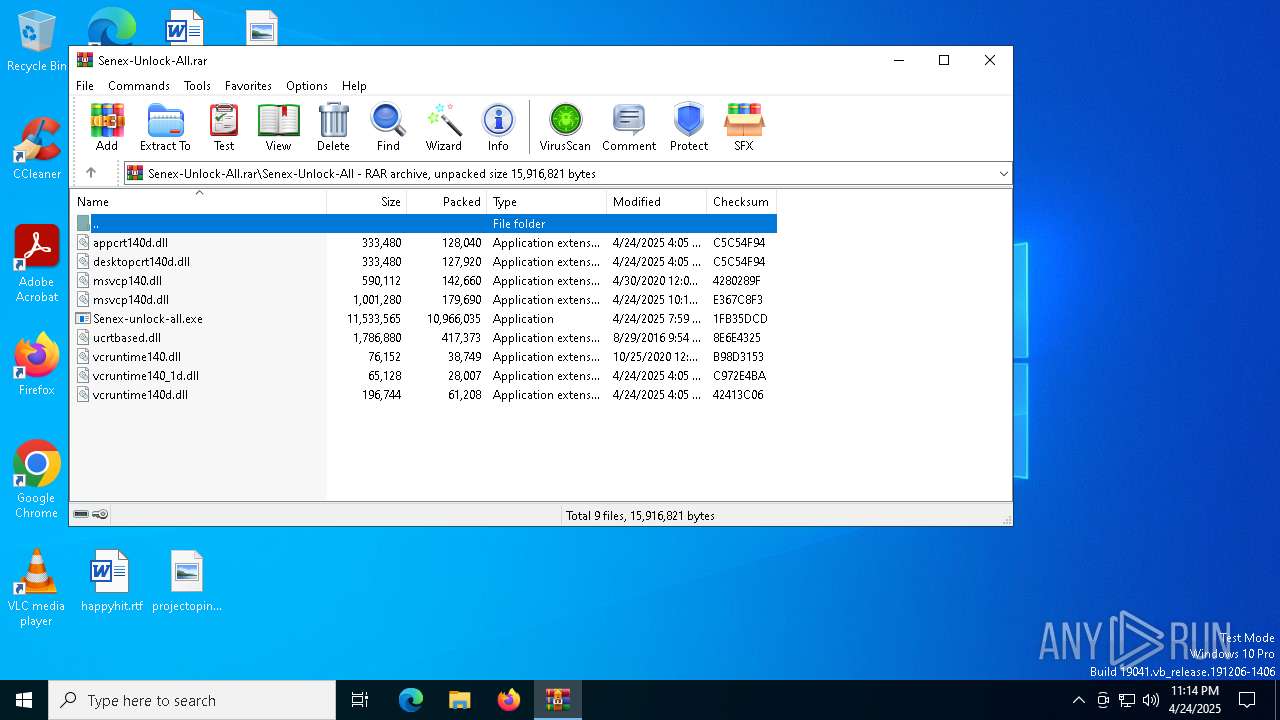
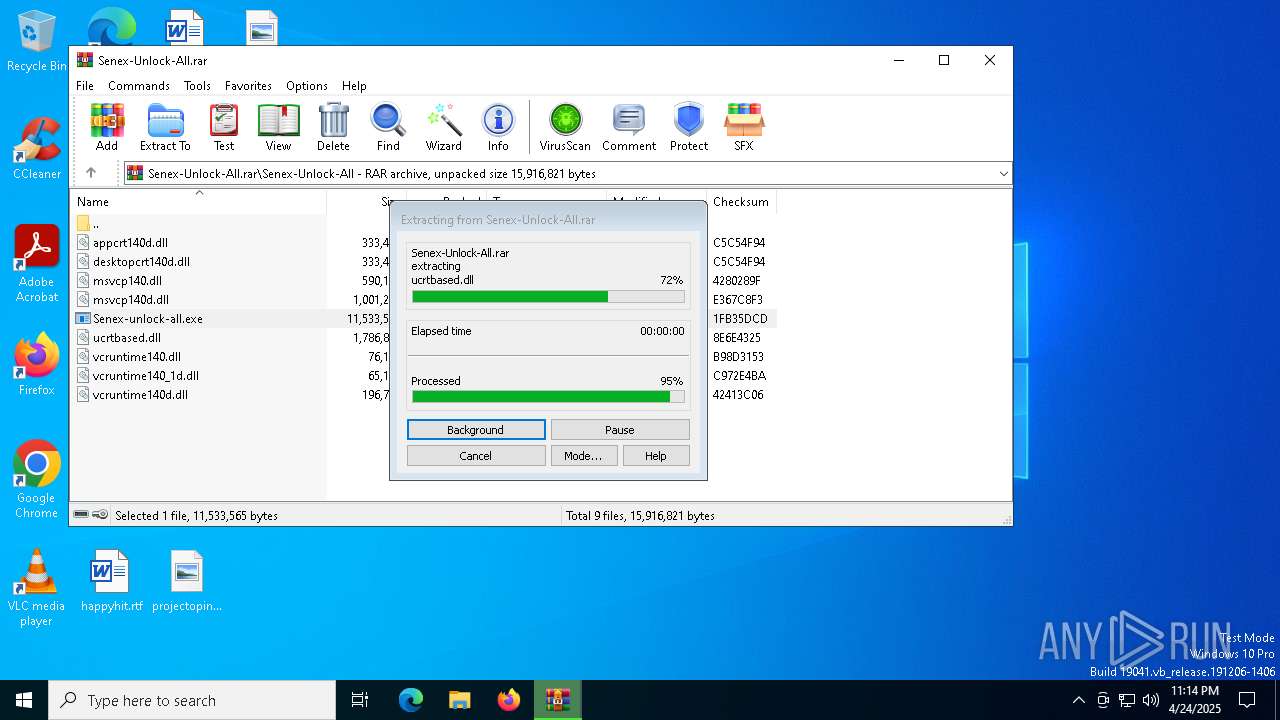
| File name: | Senex-Unlock-All.rar |
| Full analysis: | https://app.any.run/tasks/4ad6a4cf-2c81-4b8d-9d35-4f5ed4eb61bb |
| Verdict: | Malicious activity |
| Analysis date: | April 24, 2025, 23:13:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 4363B3CD0886557F3A25B88A06BD938B |
| SHA1: | 9AC0F7061C6AE2314BBF92D77EBF84BE6720262A |
| SHA256: | FCA0D45EAAF05F6F88E29ABBA576EC8B6413A615DDB14AC8A9459BD5DF2E307B |
| SSDEEP: | 196608:1EUS9HqfN+u3nXgFwu1cXbW7BbTwqrMPx:KUS9Kl+u3QFwuCgbrMp |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- WinRAR.exe (PID: 5680)
Reads the BIOS version
- Senex-unlock-all.exe (PID: 6644)
Starts CMD.EXE for commands execution
- Senex-unlock-all.exe (PID: 6644)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5680)
Process drops legitimate windows executable
- WinRAR.exe (PID: 5680)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5680)
VMProtect protector has been detected
- Senex-unlock-all.exe (PID: 6644)
The sample compiled with english language support
- WinRAR.exe (PID: 5680)
Checks supported languages
- Senex-unlock-all.exe (PID: 6644)
Themida protector has been detected
- Senex-unlock-all.exe (PID: 6644)
Checks proxy server information
- slui.exe (PID: 5116)
Reads the software policy settings
- slui.exe (PID: 5116)
Process checks whether UAC notifications are on
- Senex-unlock-all.exe (PID: 6644)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 128040 |
| UncompressedSize: | 333480 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Senex-Unlock-All/appcrt140d.dll |
Total processes
154
Monitored processes
13
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | cmd.exe /c del C:\Windows\ShellExperiences\pasted_dll.dll | C:\Windows\System32\cmd.exe | — | Senex-unlock-all.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Senex-unlock-all.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4408 | cmd.exe /c del C:\Windows\ShellExperiences\hook.exe | C:\Windows\System32\cmd.exe | — | Senex-unlock-all.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4620 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 4724 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5680 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Senex-Unlock-All.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6132 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\Senex-unlock-all.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\Senex-unlock-all.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
2 709
Read events
2 701
Write events
8
Delete events
0
Modification events
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Senex-Unlock-All.rar | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5680) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
9
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\msvcp140.dll | executable | |
MD5:7B92A6CB5D2CAD407C457AB12D2B211D | SHA256:3C6A772319FFF3EE56D4CEDBE332BB5C0C2F394714CF473C6CDF933754114784 | |||
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\desktopcrt140d.dll | executable | |
MD5:C1C1A788693F849F94CAAB764AF7A7BB | SHA256:00A2D004496DACD67D50E81E6D64AE801F6B2ACF68F2404A8241D7E4FDEA3109 | |||
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\msvcp140d.dll | executable | |
MD5:37DC8CC78ECBCD12F27E665B70BAEFA7 | SHA256:B53ADD5B7BD6BB11FECC7BE159885D0B75736D02423C11EDC6EEB6F4BEA80F6C | |||
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\Senex-unlock-all.exe | executable | |
MD5:4DFD5E9A4B66656741D2D5C9BE5D75B1 | SHA256:BF4C574C374821DDCBAAD4D4ECB5CCF593486BC9BBD4A0B6A32A6886CD345405 | |||
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\ucrtbased.dll | executable | |
MD5:C3130CFB00549A5A92DA60E7F79F5FC9 | SHA256:EEE42EABC546E5AA760F8DF7105FCF505ABFFCB9EC4BF54398436303E407A3F8 | |||
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\vcruntime140d.dll | executable | |
MD5:6DFEEAE14AB3AFB0535822B5E9B70E3E | SHA256:B77FA384C1BBFD7F97710F02EF224373B67E7B004F3F9BB27A35F5C6D0AD3C44 | |||
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\vcruntime140_1d.dll | executable | |
MD5:DD688165A01CFFF888D86A283FF4E2FF | SHA256:5DBECBB35DB026C6B8FE745857B8B165F0F6AEB21DC4CE7BFB6A48AA6327B43E | |||
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\appcrt140d.dll | executable | |
MD5:C1C1A788693F849F94CAAB764AF7A7BB | SHA256:00A2D004496DACD67D50E81E6D64AE801F6B2ACF68F2404A8241D7E4FDEA3109 | |||
| 5680 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5680.26526\Senex-Unlock-All\vcruntime140.dll | executable | |
MD5:A075828073369628BCCA8A80FA225744 | SHA256:DBC5559CA8D99F045C5511F56A2C4DD156D2672D189935E242284A835C0D7F92 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
39
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3180 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3180 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |