| File name: | Confirm Unsubscribe%3A removed from our lists NOW(1).eml |
| Full analysis: | https://app.any.run/tasks/21ada6eb-0929-4498-bb69-2283256d5996 |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 16:27:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 9A70CD9CE8E973577A3A1DE36862AE2F |
| SHA1: | 9DD5F68A01AAC5531EF44266242BED050FD24031 |
| SHA256: | FC87D84D1FE3EAA9ADE44A45080DBE2F6BE0AA68625C9CD56CD45CC70A87B462 |
| SSDEEP: | 96:sT/Rm/5+FR//ZoOz/e+/wB9mThUAMueOLQmLbhLbf6Vf+EAeDqTjgk4Ncz1KlC2T:sTo/y/F/Bo+TRXdYw8zczUlC31gyS |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 3428)
Application launched itself
- OUTLOOK.EXE (PID: 3428)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 3428)
Reads internet explorer settings
- CLVIEW.EXE (PID: 3212)
Reads Internet Cache Settings
- CLVIEW.EXE (PID: 3212)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3292)
- OUTLOOK.EXE (PID: 3428)
- CLVIEW.EXE (PID: 3212)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
35
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3212 | "C:\Program Files\Microsoft Office\Office14\CLVIEW.EXE" "OUTLOOK" "Microsoft Outlook" | C:\Program Files\Microsoft Office\Office14\CLVIEW.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Help Viewer Exit code: 0 Version: 14.0.6015.1000 Modules
| |||||||||||||||
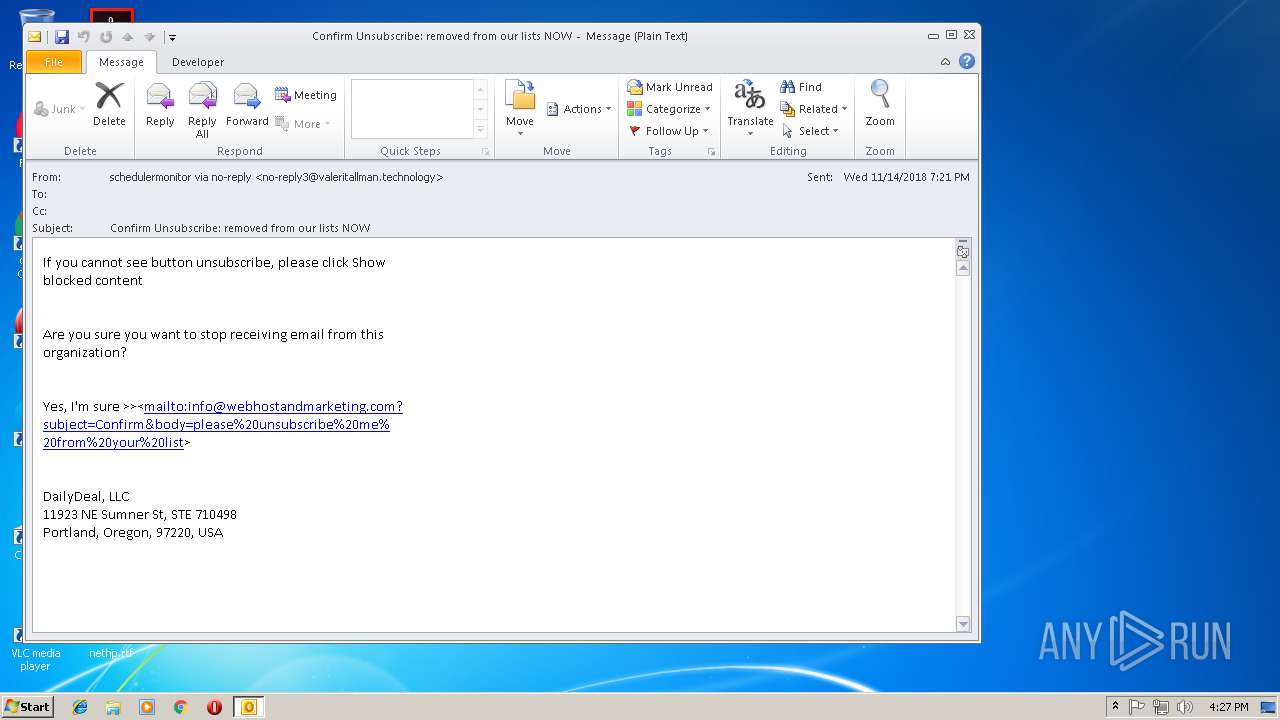
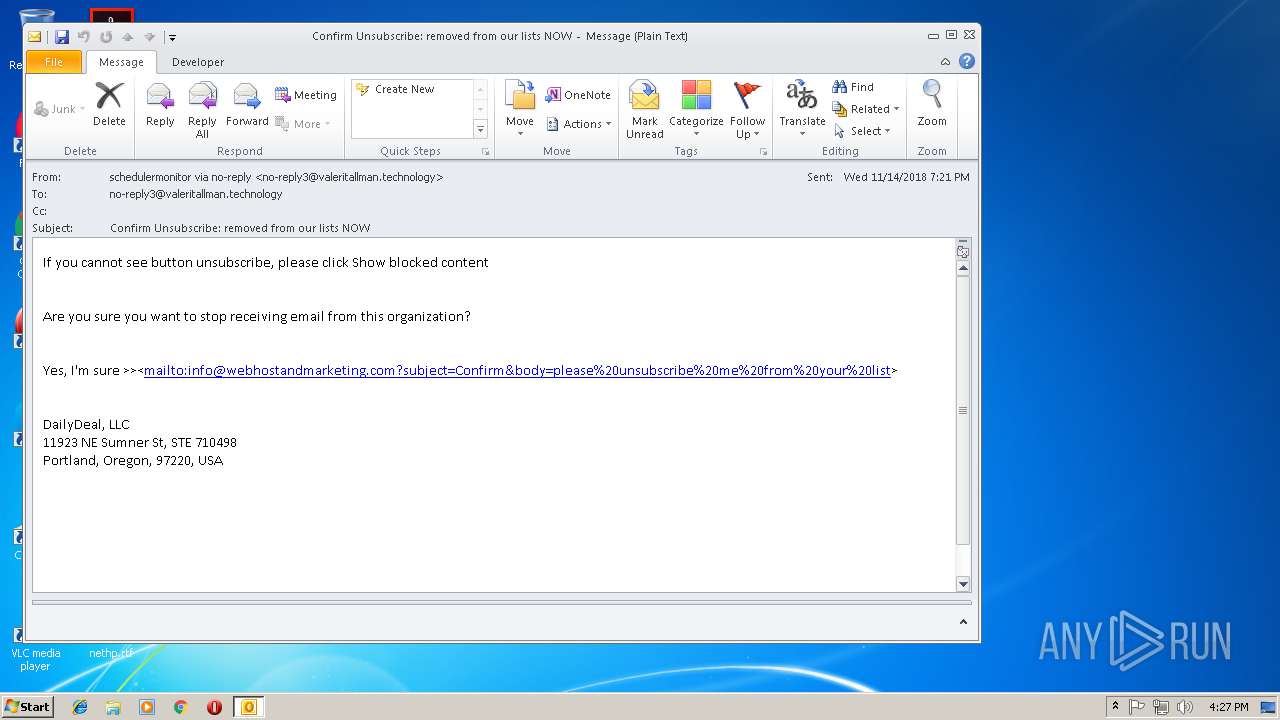
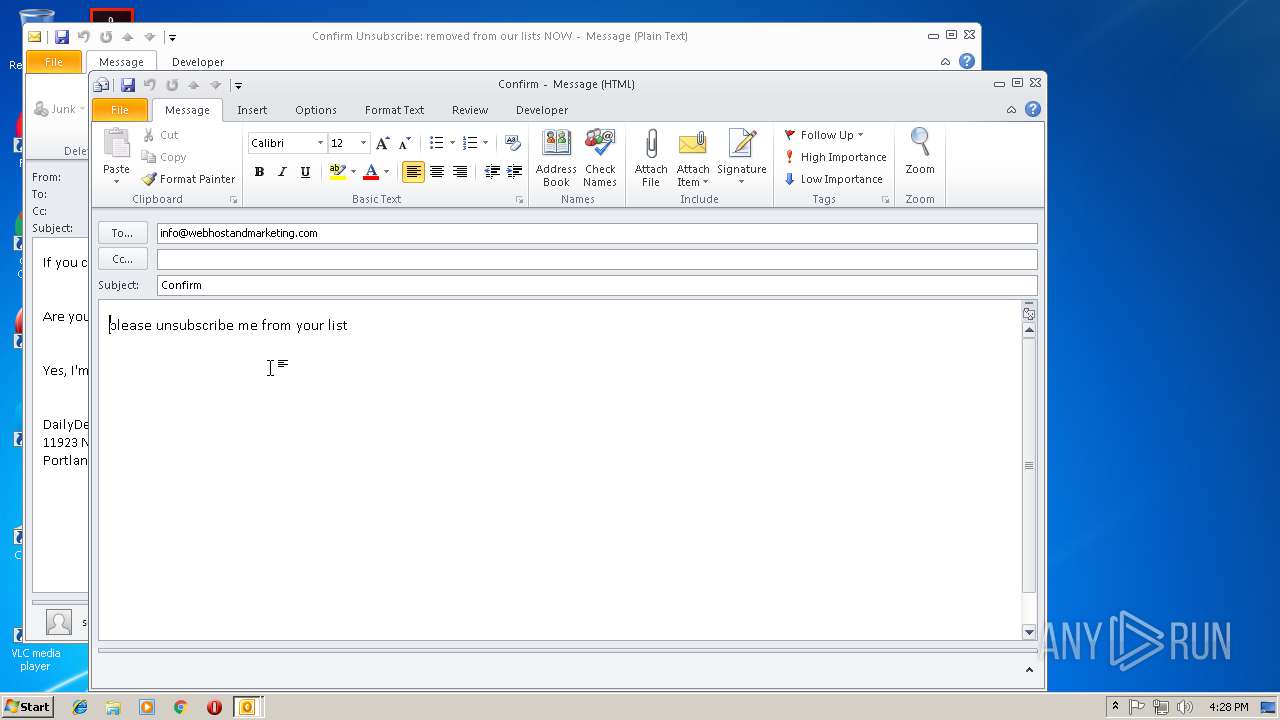
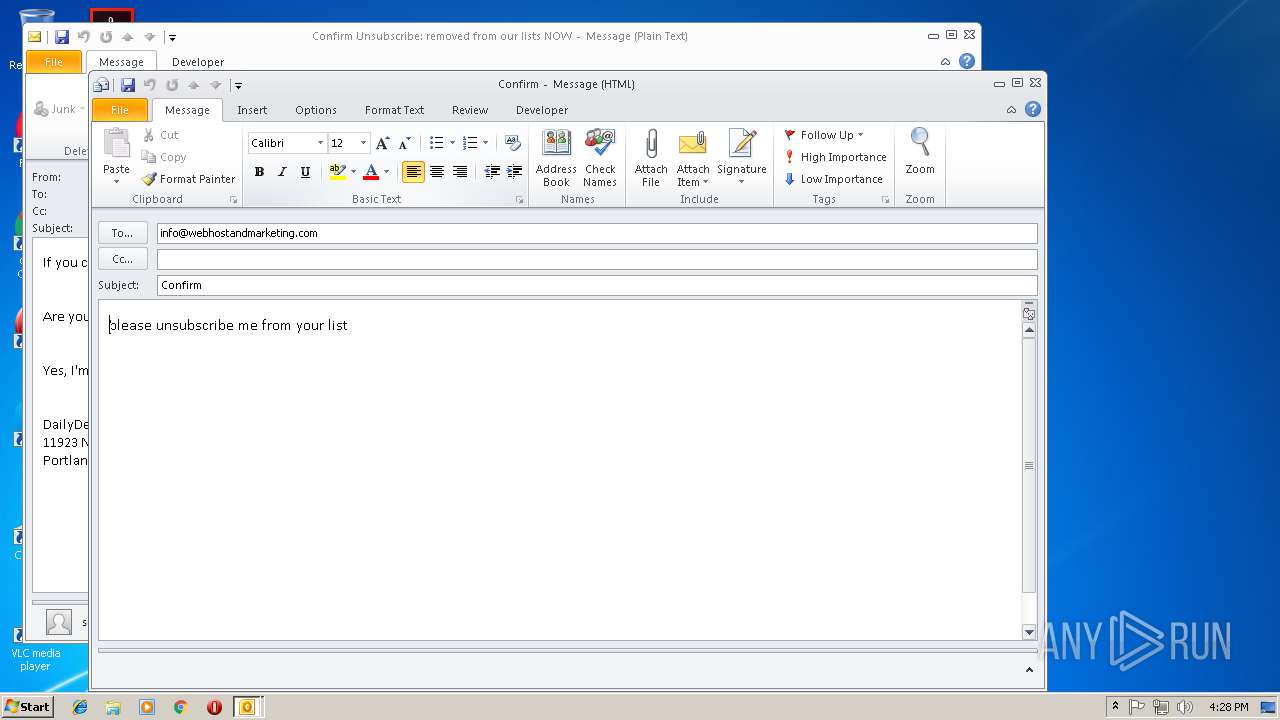
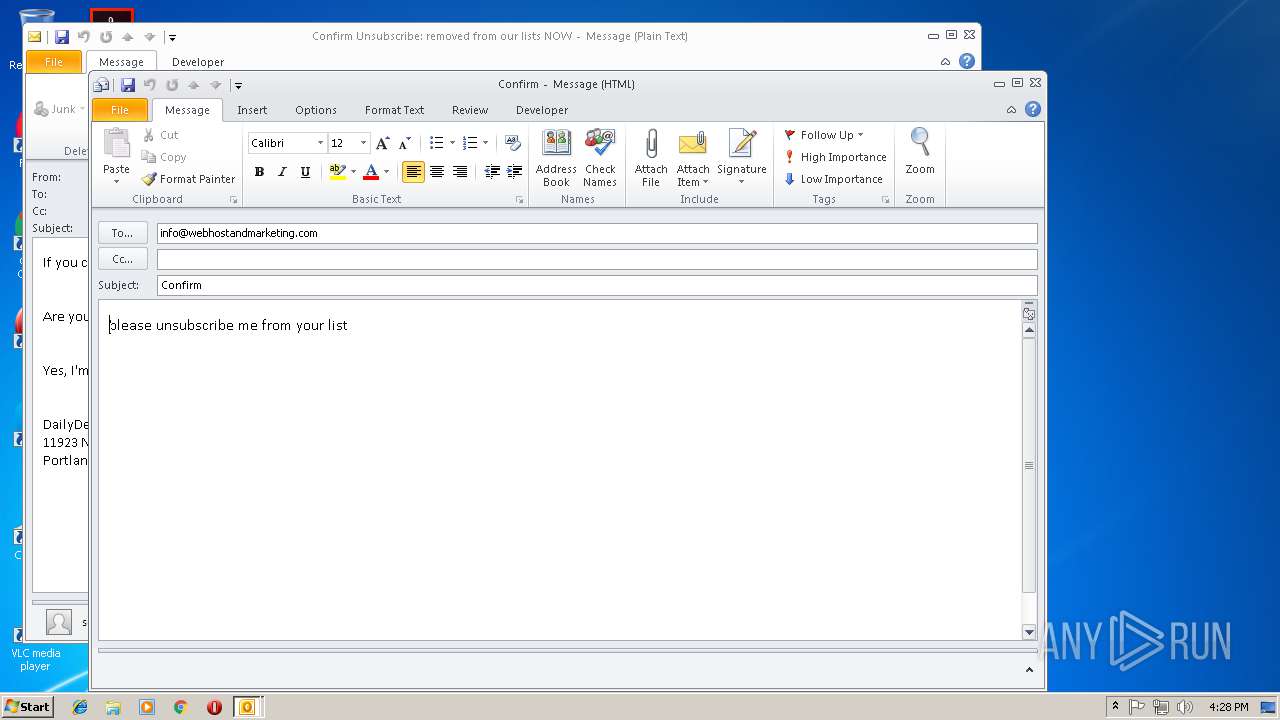
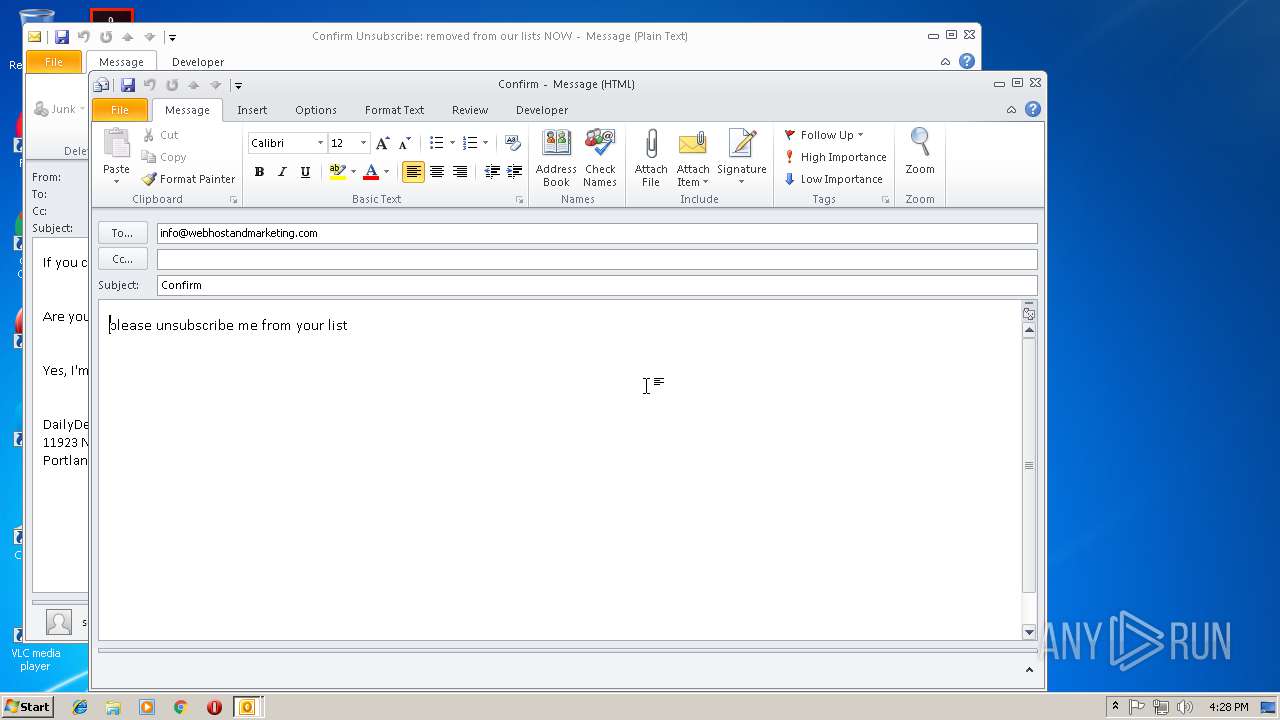
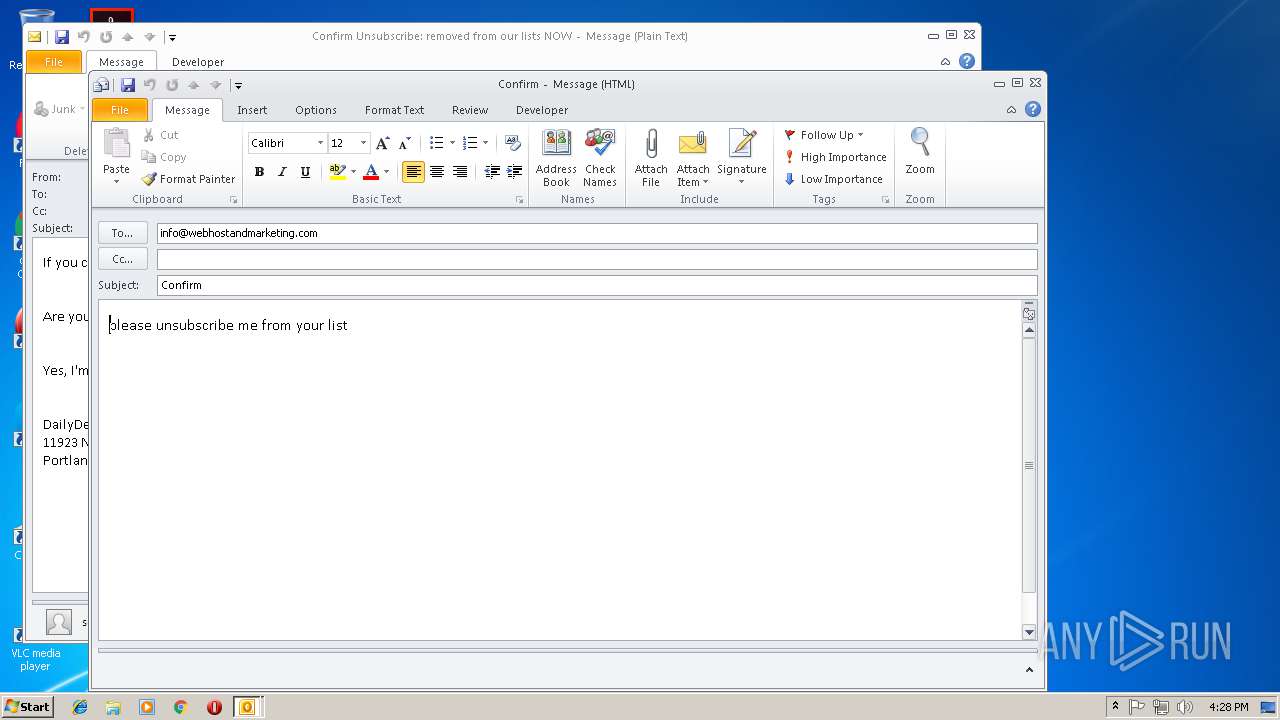
| 3292 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" -c IPM.Note /m "mailto:info@webhostandmarketing.com?subject=Confirm&body=please%20unsubscribe%20me%20from%20your%20list" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3428 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\045f7ca8-f417-4224-945e-8b1d83eff112.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
1 611
Read events
1 151
Write events
426
Delete events
34
Modification events
| (PID) Process: | (3428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | y3b |
Value: 79336200640D0000010000000000000000000000 | |||
| (PID) Process: | (3428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 640D00004CB4F01F007DD40100000000 | |||
| (PID) Process: | (3428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 219778560 | |||
| (PID) Process: | (3428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3428) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3428) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1299120149 | |||
Executable files
0
Suspicious files
4
Text files
97
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3428 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9769.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3292 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRFFD7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3212 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT6EBF.tmp | — | |
MD5:— | SHA256:— | |||
| 3212 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT6EC0.tmp | — | |
MD5:— | SHA256:— | |||
| 3212 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT6ED1.tmp | — | |
MD5:— | SHA256:— | |||
| 3212 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT6ED2.tmp | — | |
MD5:— | SHA256:— | |||
| 3212 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT6ED3.tmp | — | |
MD5:— | SHA256:— | |||
| 3212 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT6EE3.tmp | — | |
MD5:— | SHA256:— | |||
| 3212 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT6EE4.tmp | — | |
MD5:— | SHA256:— | |||
| 3212 | CLVIEW.EXE | C:\Users\admin\AppData\Local\Temp\IMT6EE5.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3428 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3428 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |