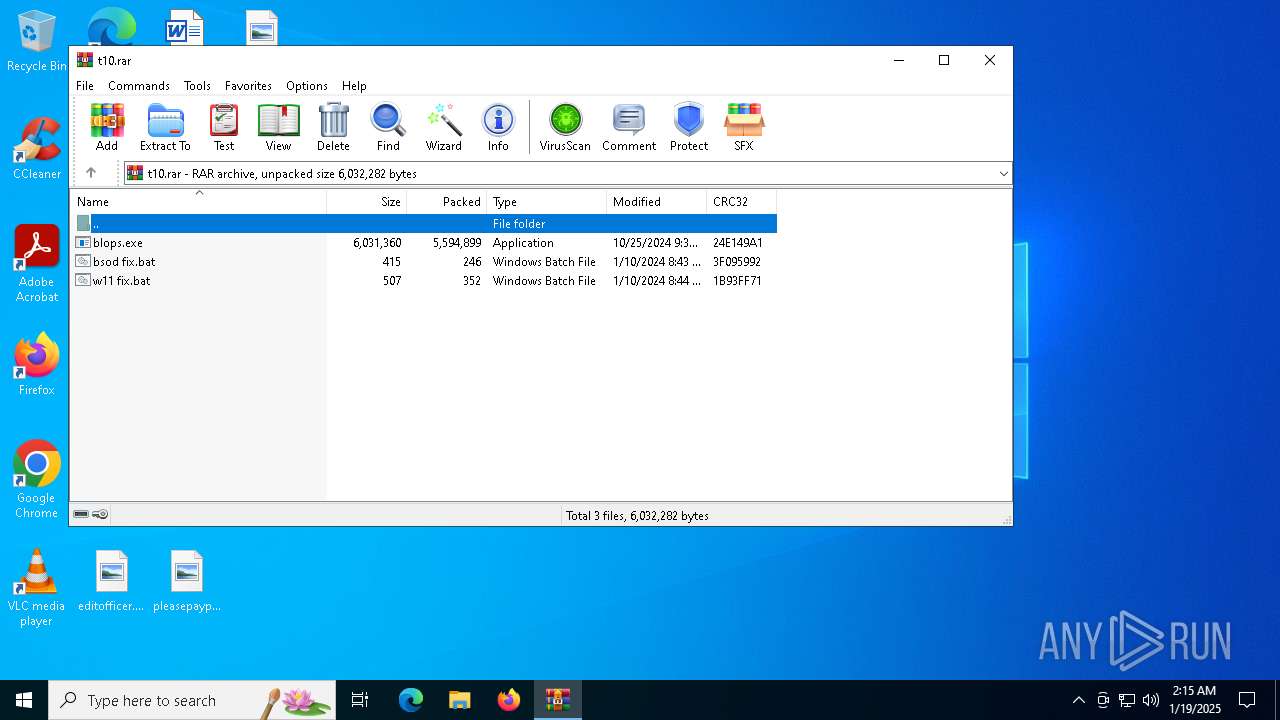
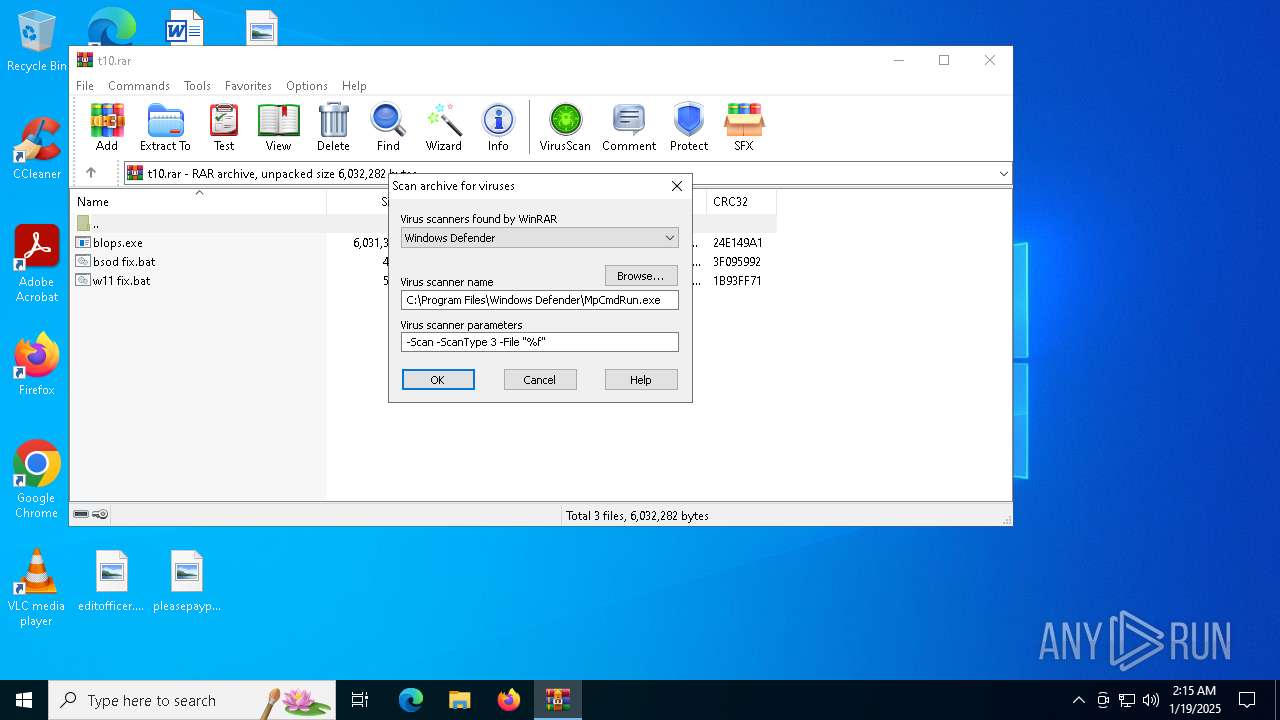
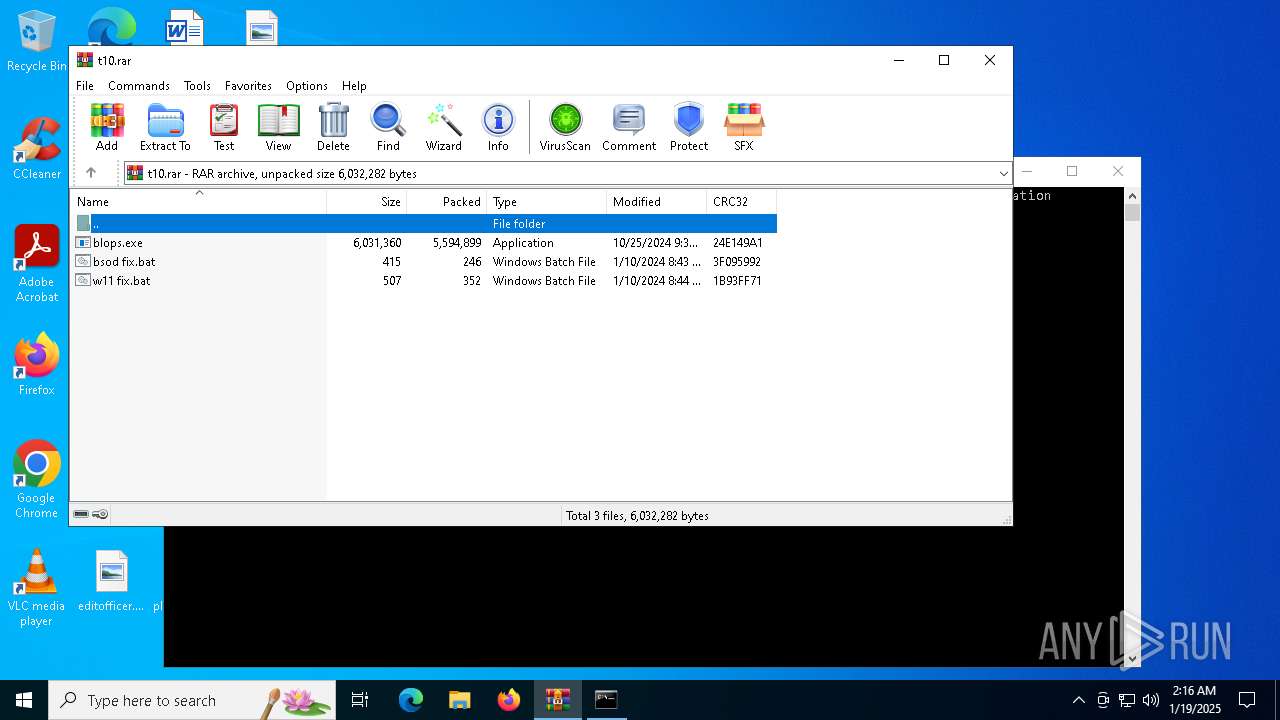
| File name: | t10.rar |
| Full analysis: | https://app.any.run/tasks/62f1a8e2-3050-4740-8443-095fb0c0cbff |
| Verdict: | Malicious activity |
| Analysis date: | January 19, 2025, 02:15:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A222BD71BDAB35A93BA21295FD216EC6 |
| SHA1: | 694E6B7989CB15D987AD0E2D127AFB94637D670D |
| SHA256: | FC84BE70E85351C4E63168014DBB676874A3E1FB27F1D9ED570CA005B9A67021 |
| SSDEEP: | 98304:m1oIFzb7l/ZATqIVHHM4El6YrVbBCehfYzi7FwVB3P1qyHQvEcCFlpzJin2RxkTe:+B368uvt |
MALICIOUS
No malicious indicators.SUSPICIOUS
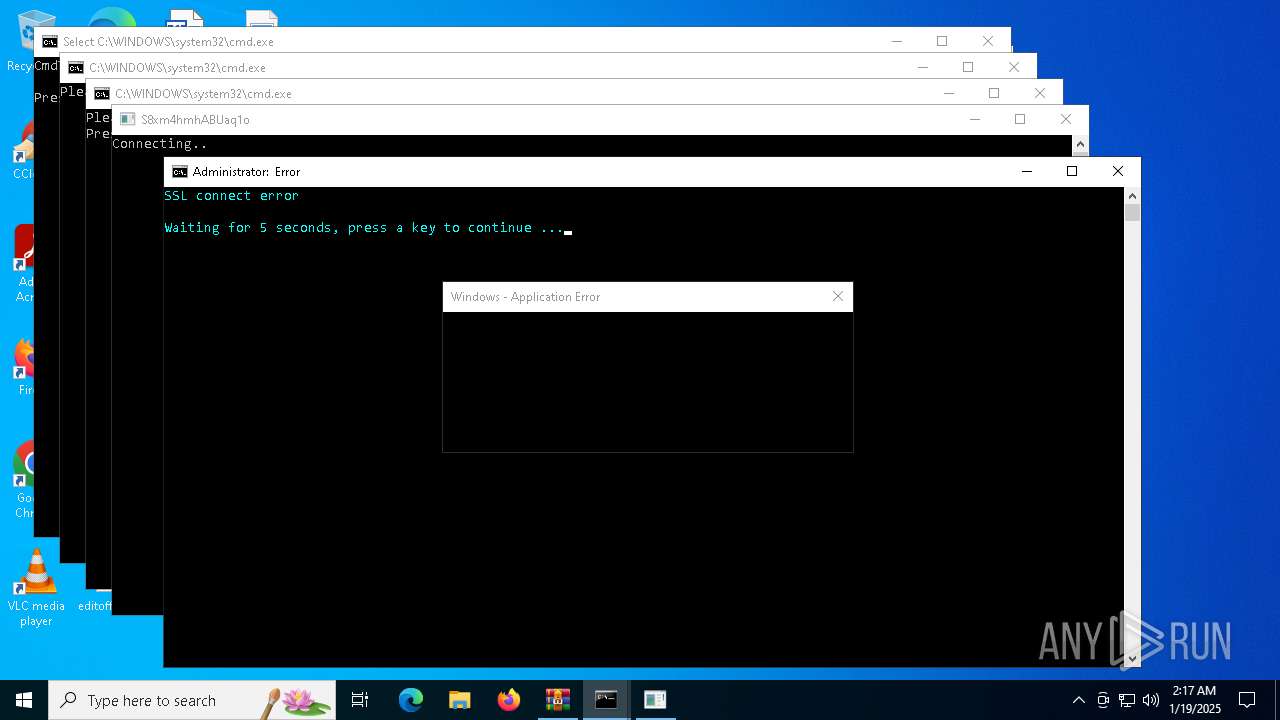
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4392)
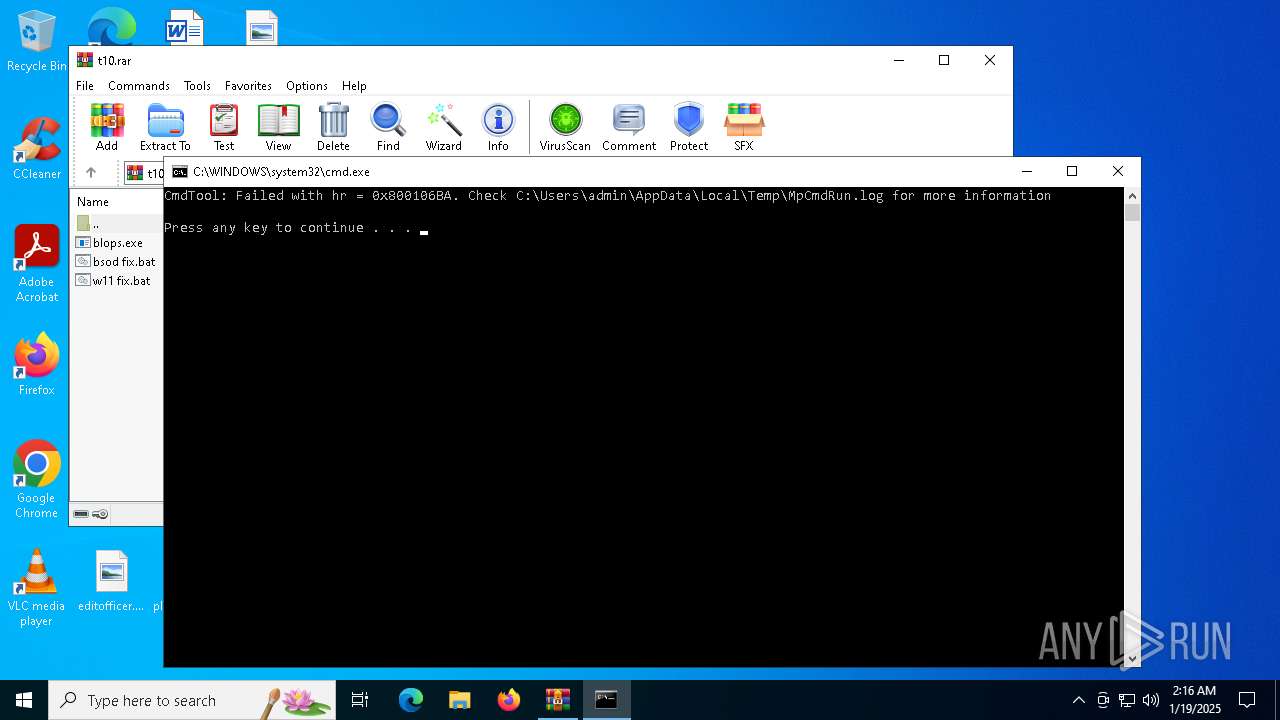
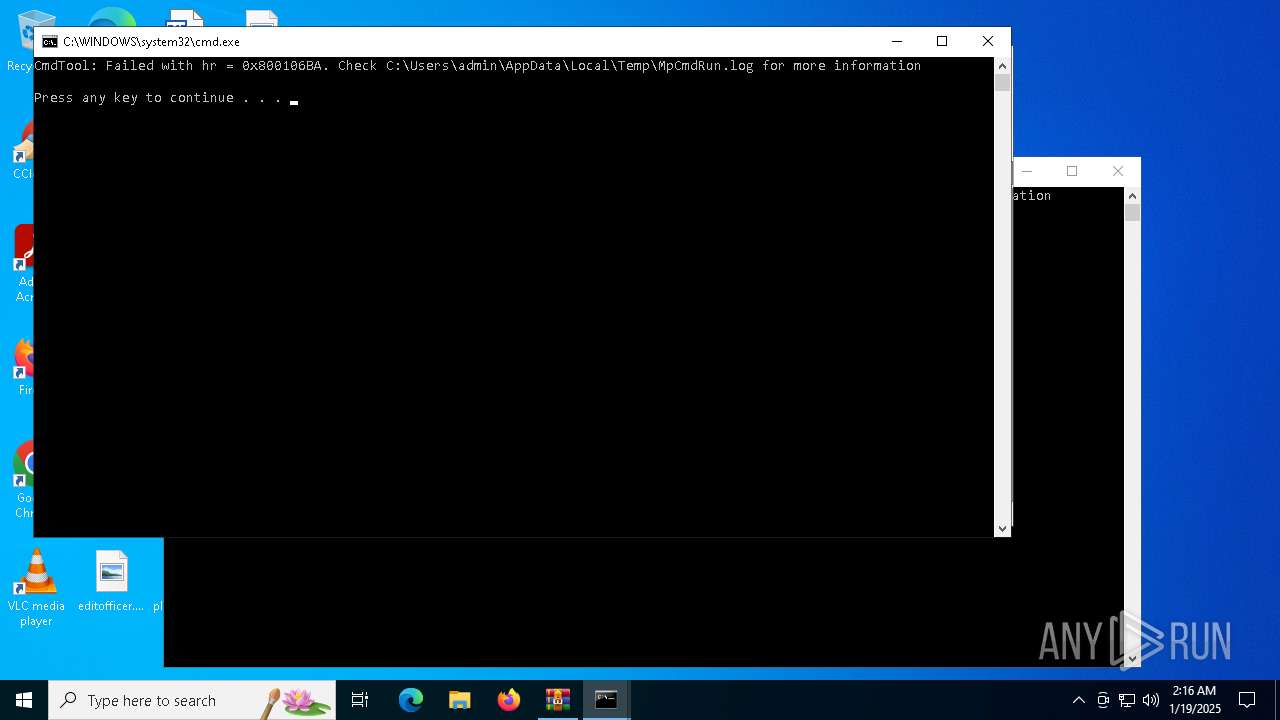
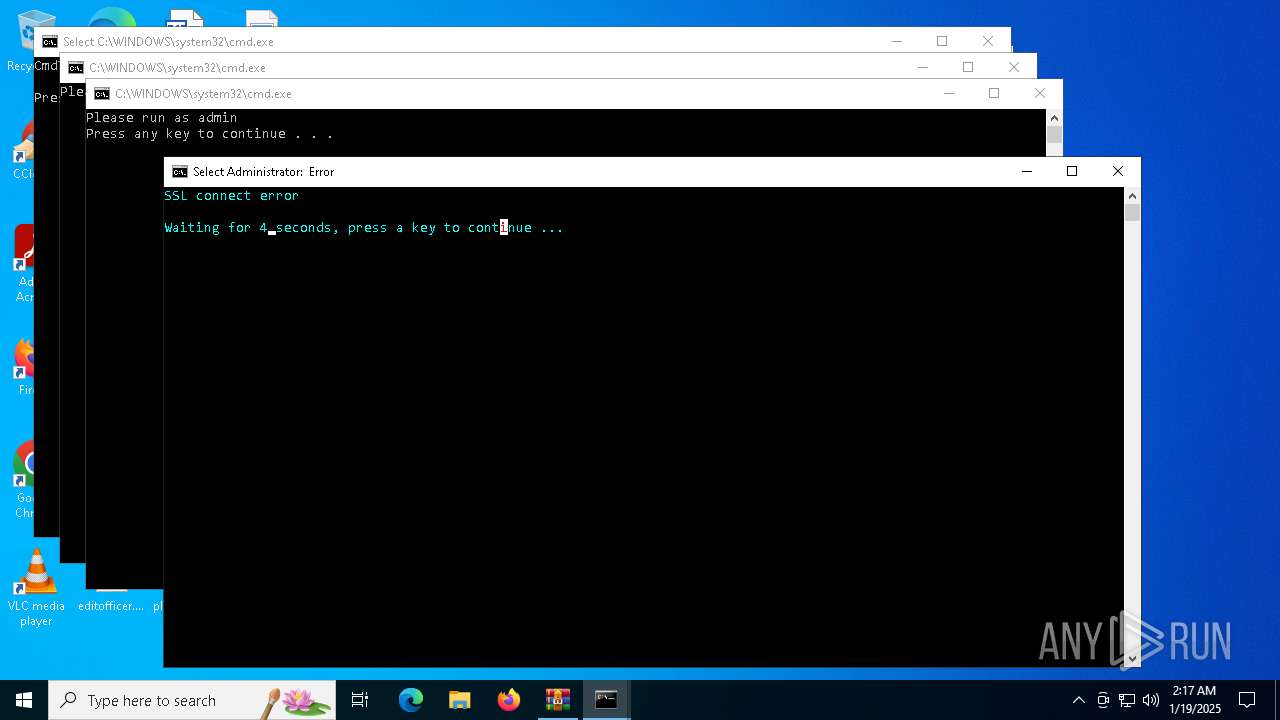
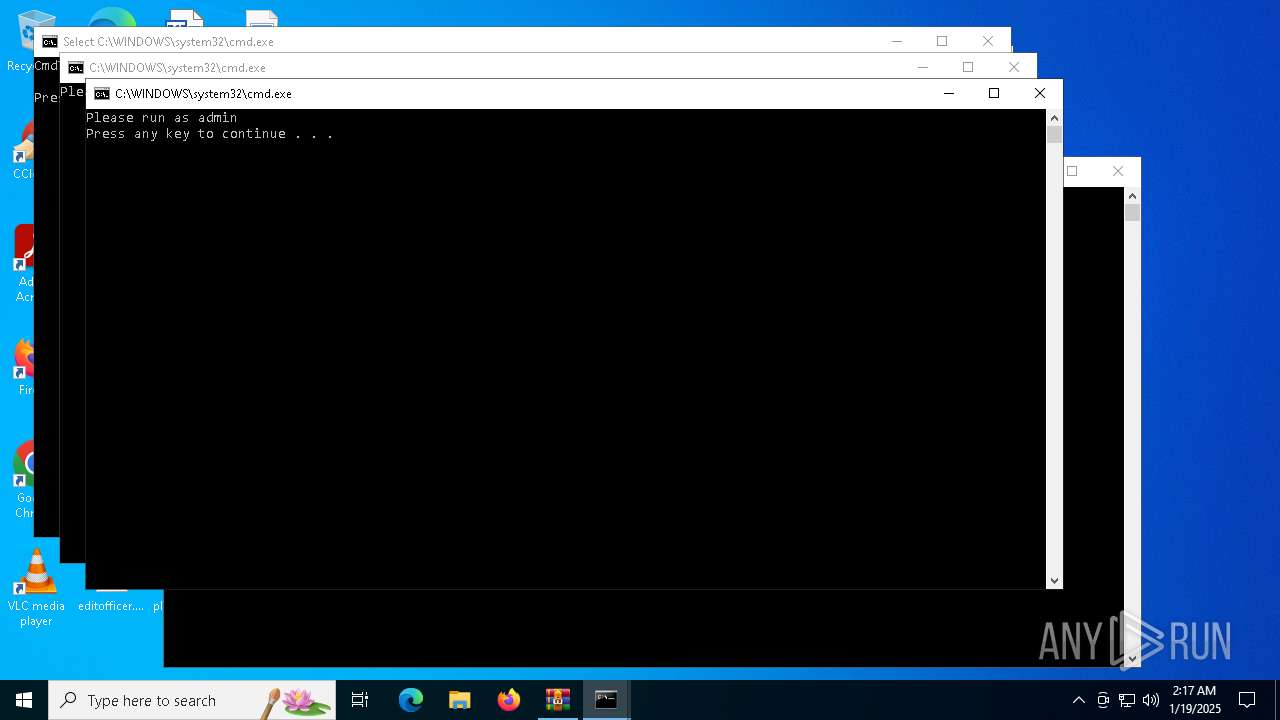
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4392)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4392)
- blops.exe (PID: 1620)
- cmd.exe (PID: 4716)
Starts NET.EXE to display or manage information about active sessions
- cmd.exe (PID: 3420)
- net.exe (PID: 2940)
- cmd.exe (PID: 236)
- net.exe (PID: 2600)
Application launched itself
- cmd.exe (PID: 4716)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5208)
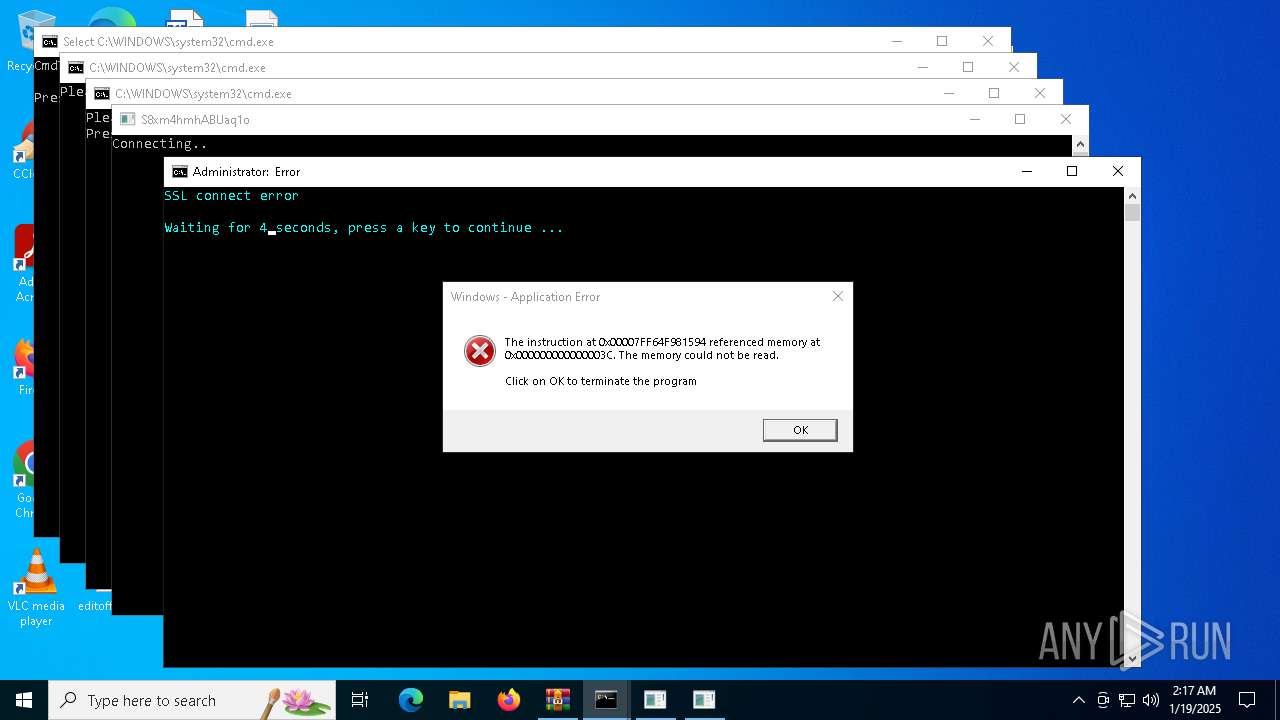
Executes application which crashes
- blops.exe (PID: 1620)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 4392)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4392)
Create files in a temporary directory
- MpCmdRun.exe (PID: 4204)
Checks supported languages
- MpCmdRun.exe (PID: 4204)
- MpCmdRun.exe (PID: 3524)
- blops.exe (PID: 1620)
Reads the computer name
- MpCmdRun.exe (PID: 4204)
- MpCmdRun.exe (PID: 3524)
- blops.exe (PID: 1620)
Manual execution by a user
- cmd.exe (PID: 3420)
- cmd.exe (PID: 236)
- blops.exe (PID: 1416)
- blops.exe (PID: 1620)
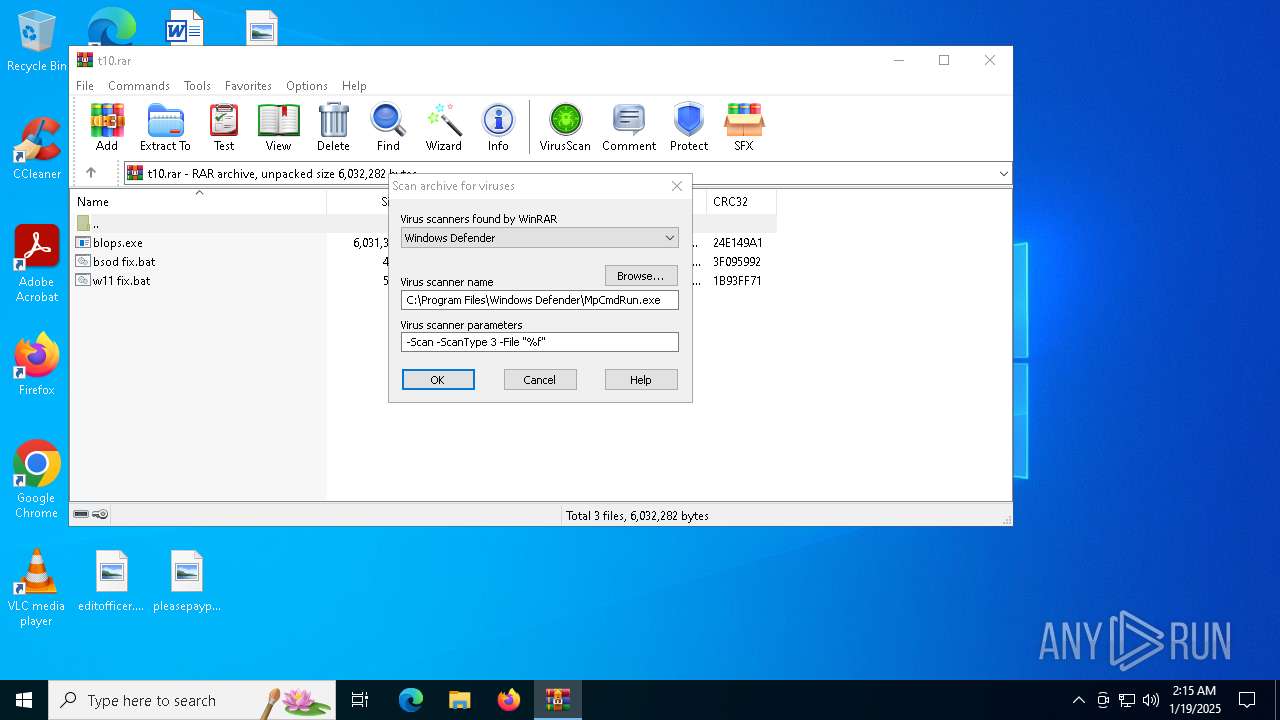
Gets the hash of the file via CERTUTIL.EXE
- certutil.exe (PID: 4648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 5594899 |
| UncompressedSize: | 6031360 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | blops.exe |
Total processes
146
Monitored processes
28
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\bsod fix.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1416 | "C:\Users\admin\Desktop\blops.exe" | C:\Users\admin\Desktop\blops.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1620 | "C:\Users\admin\Desktop\blops.exe" | C:\Users\admin\Desktop\blops.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 1792 | timeout /t 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | NET SESSION | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2940 | net session | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3172 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4392.29080\Rar$Scan29492.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3420 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\w11 fix.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 732
Read events
2 719
Write events
13
Delete events
0
Modification events
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\t10.rar | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
| (PID) Process: | (4648) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
Executable files
2
Suspicious files
0
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4204 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:BFCB444EC494E9E18E310427BD90DC45 | SHA256:32B83C2755B88934A22930599E744FE77D37BC93C49A1212E7E7101FCEF218CD | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.27042\t10.rar\blops.exe | executable | |
MD5:C2D8EF9AF7A8028D05C77FEEBB9F166B | SHA256:1ED90EEE9CCFFEBE87ADB8799D6C4FDB946D48BF95EF9CE2E5F37307EBD9F938 | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.29080\Rar$Scan29492.bat | text | |
MD5:529A94D87155B06043258254BAEDEB6D | SHA256:97D0563D4F6A7321137CB3AEFBA21691802986297AFFDC2E4B13E7437FE6228F | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.29080\t10.rar\blops.exe | executable | |
MD5:C2D8EF9AF7A8028D05C77FEEBB9F166B | SHA256:1ED90EEE9CCFFEBE87ADB8799D6C4FDB946D48BF95EF9CE2E5F37307EBD9F938 | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.29080\t10.rar\w11 fix.bat | text | |
MD5:6FB44052DC5A85A097FEEB91D7A81712 | SHA256:7EC1B31DE3B0114C266DF0B475C5C582A504C7C38F7127949DF27F78A5D1C026 | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.29080\t10.rar\bsod fix.bat | text | |
MD5:392F331DC1744FBE560A2A17D7CA838F | SHA256:318AE14FD3712848ED06C109D36A9DF600964E1D827581F980C121D52A7B5DF5 | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.27042\Rar$Scan9116.bat | text | |
MD5:ED6651A667A6C055877EAF200F364351 | SHA256:75E74FEBAF579C16FAD88FB36789D52594EA7276AD03CAFB999DE9894E4A3967 | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.27042\t10.rar\w11 fix.bat | text | |
MD5:6FB44052DC5A85A097FEEB91D7A81712 | SHA256:7EC1B31DE3B0114C266DF0B475C5C582A504C7C38F7127949DF27F78A5D1C026 | |||
| 4392 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4392.27042\t10.rar\bsod fix.bat | text | |
MD5:392F331DC1744FBE560A2A17D7CA838F | SHA256:318AE14FD3712848ED06C109D36A9DF600964E1D827581F980C121D52A7B5DF5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
21
DNS requests
7
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2220 | svchost.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2220 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 104.126.37.178:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2220 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2220 | svchost.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2220 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
keyauth.win |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain in DNS Lookup (keyauth .win) |
1620 | blops.exe | Potentially Bad Traffic | ET INFO KeyAuth Open-source Authentication System Domain (keyauth .win) in TLS SNI |