| File name: | FAKTURA.docx |
| Full analysis: | https://app.any.run/tasks/244163b0-9e19-443f-aeb8-0f2ce7b5da0d |
| Verdict: | Malicious activity |
| Analysis date: | June 05, 2024, 13:32:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 27A4F3AC566C40A82AE4059A3661112F |
| SHA1: | F1D760423DA2245150A931371AF474DDA519B6C9 |
| SHA256: | FC7D5515E60D6ECF3B89DE74A2593466FECF1BC6C7CA95403A31FDC4360C1800 |
| SSDEEP: | 12288:lOnR2aaqtsItaqtsIKaqtsIGaqtsIuJrxHtaqtsIRaqtsIIaqtsIzaqtsIZkG1Eu:lkwaaBItaBIKaBIGaBIUFHtaBIRaBIIr |
MALICIOUS
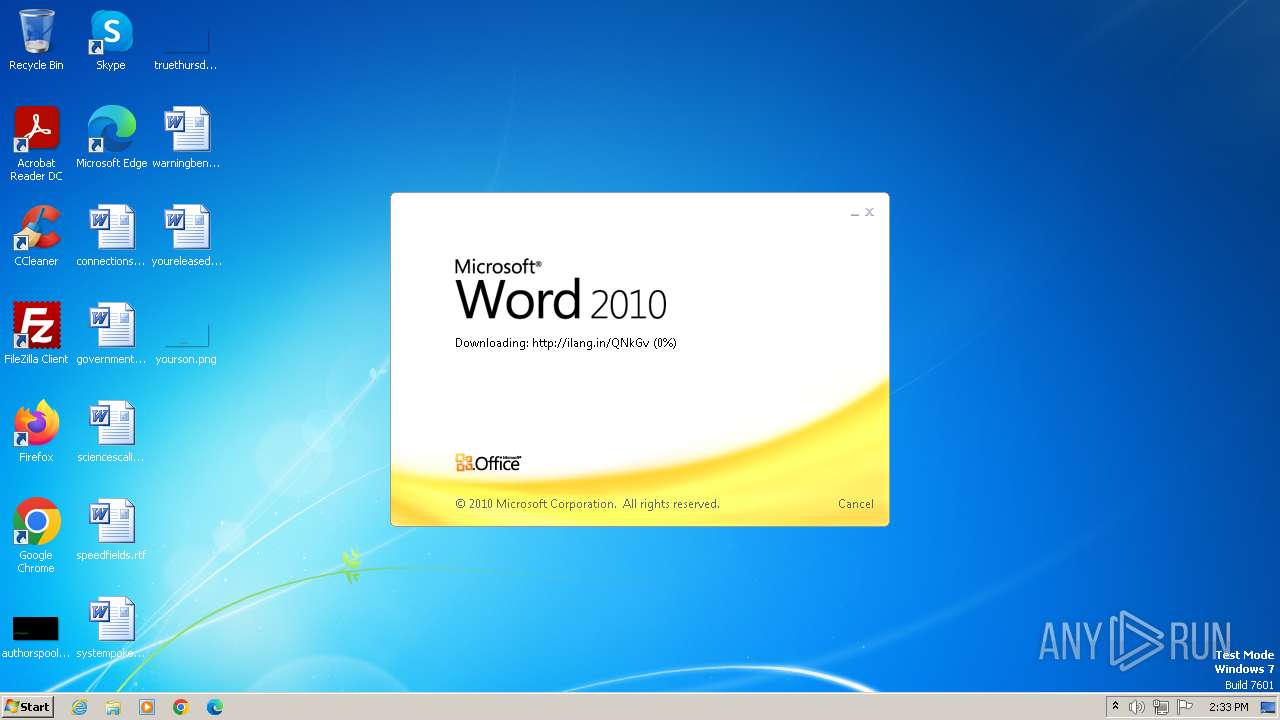
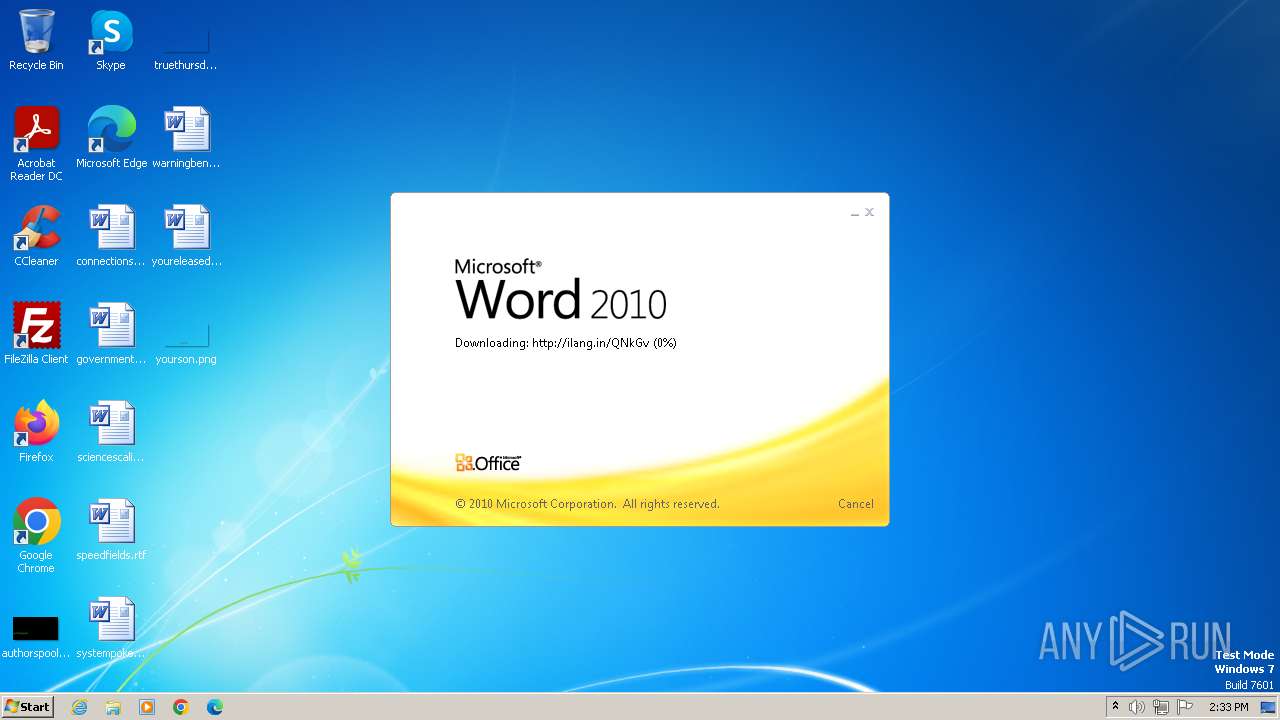
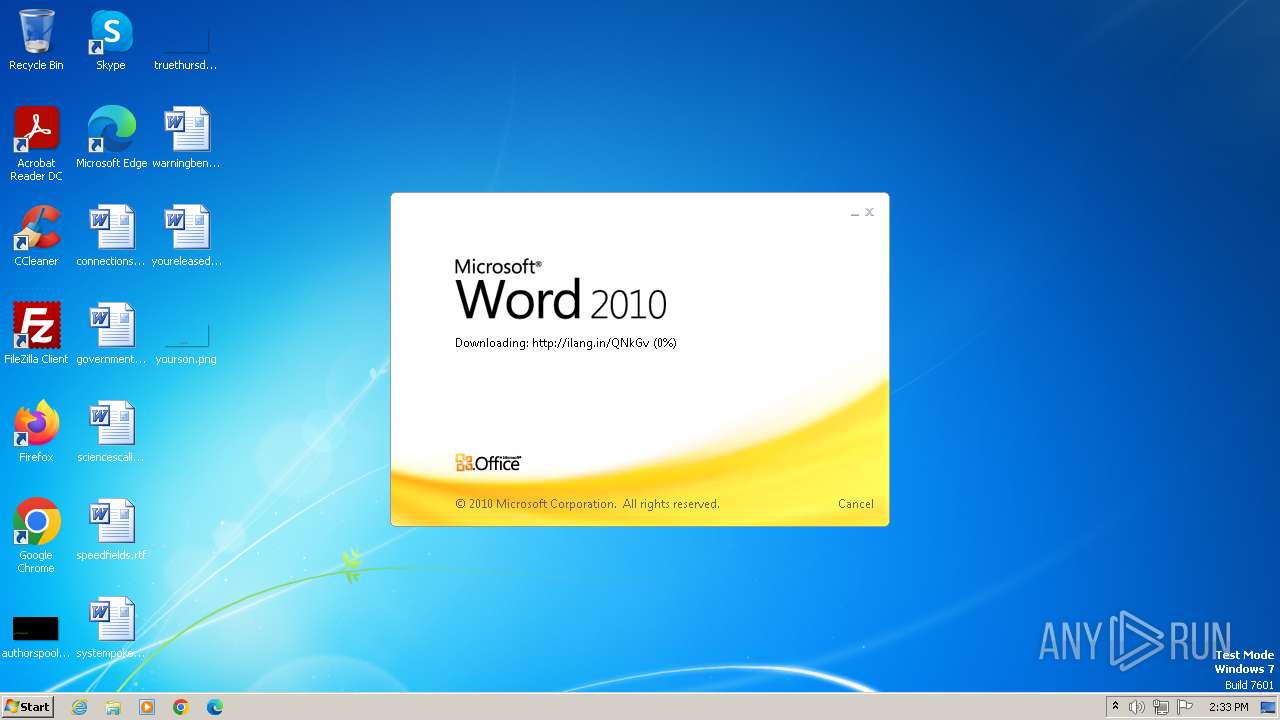
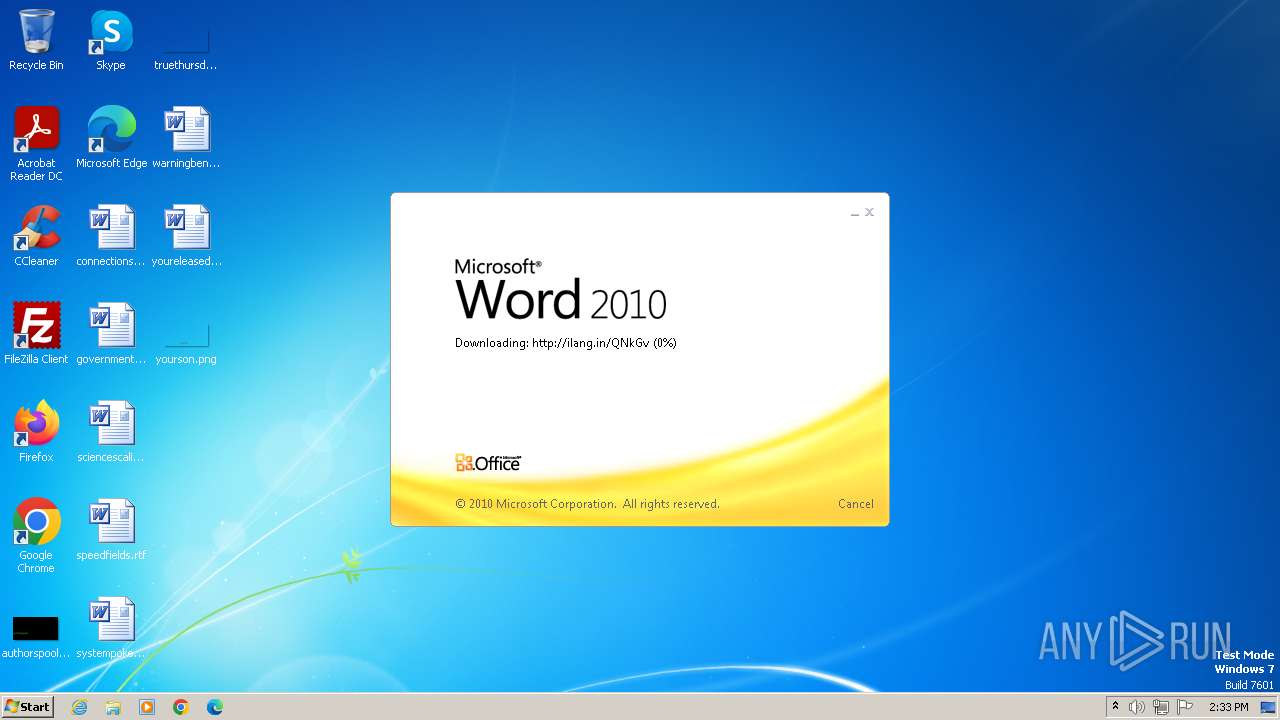
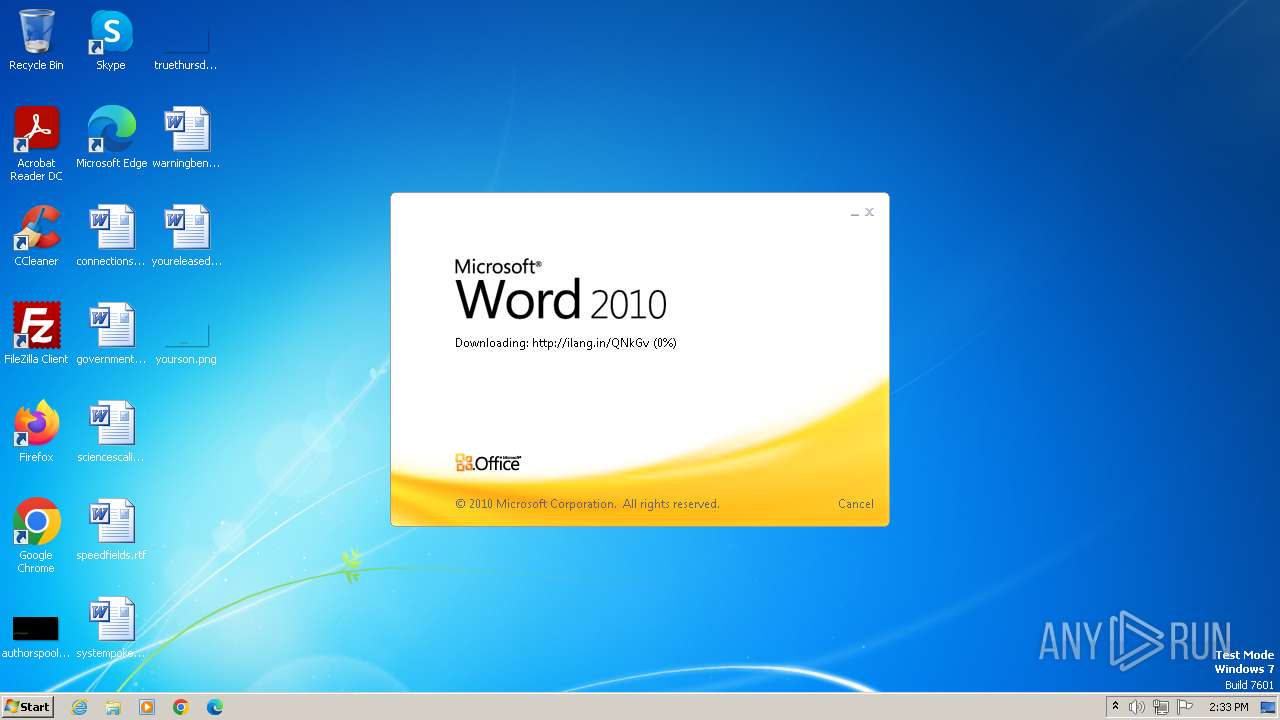
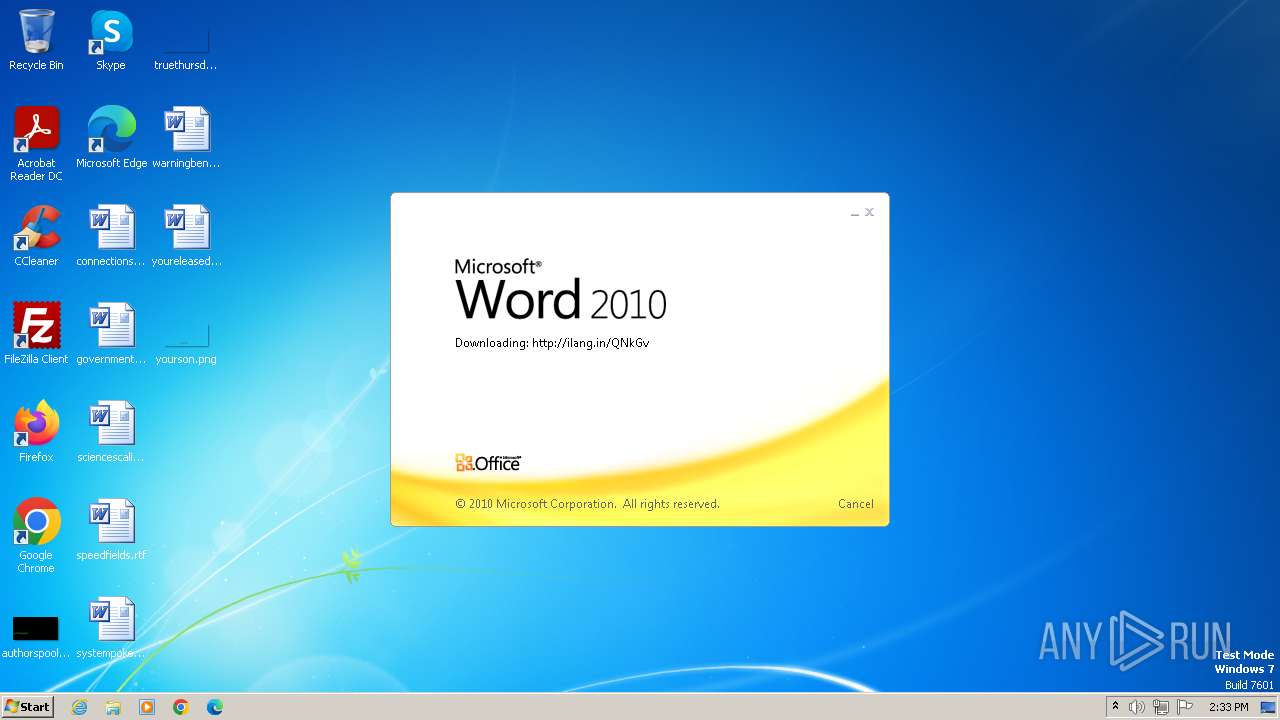
CVE-2017-0199 detected
- WINWORD.EXE (PID: 3980)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- wmpnscfg.exe (PID: 820)
Reads the computer name
- wmpnscfg.exe (PID: 820)
Manual execution by a user
- wmpnscfg.exe (PID: 820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:05 13:03:44 |
| ZipCRC: | 0x7fcf3406 |
| ZipCompressedSize: | 365 |
| ZipUncompressedSize: | 1460 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal.dotm |
|---|---|
| TotalEditTime: | 5 minutes |
| Pages: | 1 |
| Words: | 53 |
| Characters: | 304 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 2 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | Grizli777 |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 356 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 12 |
| Keywords: | - |
| LastModifiedBy: | 91974 |
| RevisionNumber: | 23 |
| CreateDate: | 2023:11:10 01:33:00Z |
| ModifyDate: | 2024:05:15 06:47:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | 91974 |
| Description: | - |
Total processes
34
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 820 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3980 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\FAKTURA.docx | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 942
Read events
2 853
Write events
72
Delete events
17
Modification events
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | ,r? |
Value: 2C723F008C0F0000010000000000000000000000 | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3980) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
10
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR41FC.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:3DD09E18CF410B7E55179447B9B7A3BD | SHA256:20FC181B3DD2919DEB7C20C7E7E006110AD35461208C880854D96A92FD63A1A3 | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:C830FD3995564FFF2EE8858FBE752465 | SHA256:2B37C2401C05C01A4FF51DAFB028DF7BD0A0DFAADC93445B87F6C42B1DC6D533 | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:348BC8B70FD9C11A8271145DC617B7A7 | SHA256:4F01573C91820E54A5E390B16C8FD4E4AD91972B1983CCB3DFA7F25AECCBD1FC | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$AKTURA.docx | binary | |
MD5:AAD175A1ACBB5EE58FE0F96C1F186212 | SHA256:1175A314E3375EE5F3EC4BCD5143A8D8B26B44A1A2E4D0F07352B284738C83D7 | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-{59555499-18C6-4C36-8EE0-619BE4E59992}.FSD | binary | |
MD5:C61FF114D4A887CDB51DEB778D37EBBA | SHA256:43510B7AB2DB537F3D66F73FFFECB08891E174A69DB0D17C733E1A7A1657103B | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSF-{0E1EEE64-E8C6-4E2A-9759-63CF07FD8988}.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSF-CTBL.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{716129C2-A306-4431-A611-8A7CF60B534D} | binary | |
MD5:348BC8B70FD9C11A8271145DC617B7A7 | SHA256:4F01573C91820E54A5E390B16C8FD4E4AD91972B1983CCB3DFA7F25AECCBD1FC | |||
| 3980 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{B4E69226-8C3A-466C-B0EE-F9F53301E924} | binary | |
MD5:C830FD3995564FFF2EE8858FBE752465 | SHA256:2B37C2401C05C01A4FF51DAFB028DF7BD0A0DFAADC93445B87F6C42B1DC6D533 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
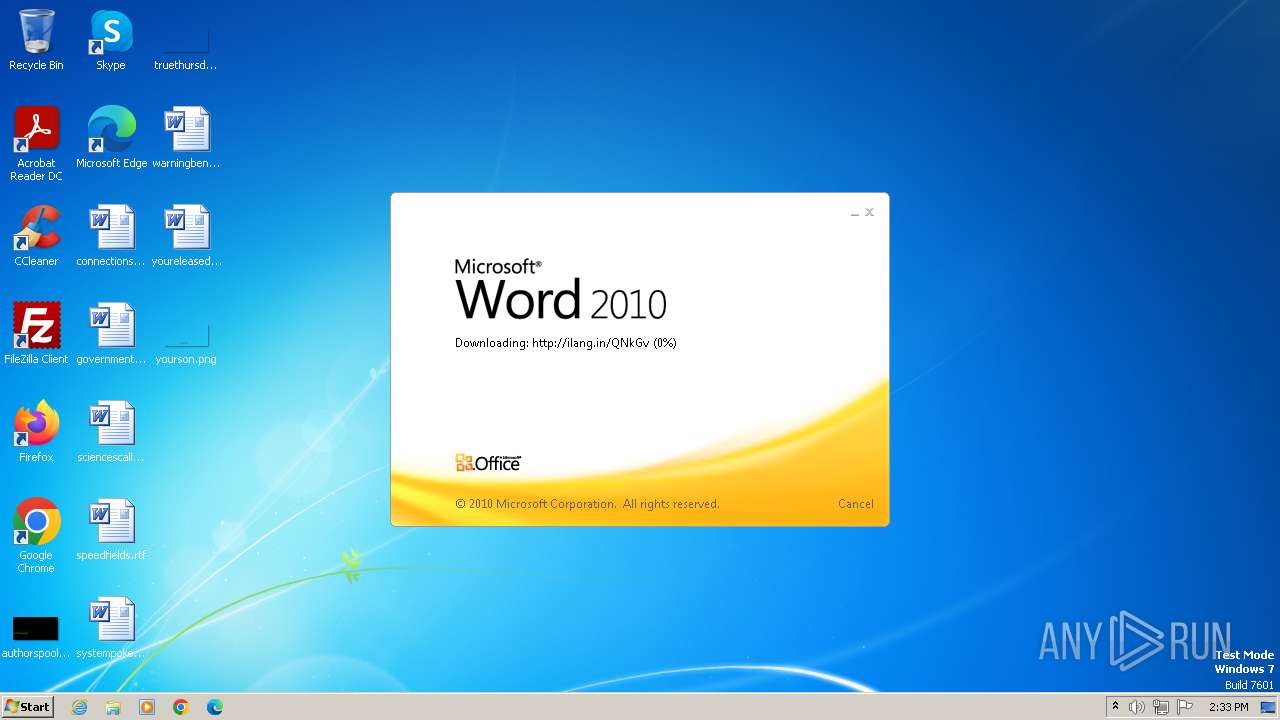
3980 | WINWORD.EXE | OPTIONS | — | 194.163.41.117:80 | http://ilang.in/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3980 | WINWORD.EXE | 194.163.41.117:80 | ilang.in | Hostinger International Limited | SG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ilang.in |
| unknown |